This week has been a busy one for high-profile malware. A pair of new types of malware - Gauss and FinFisher - have people around the world worried, and media churning out concerned articles as fast as they can be written. Fortunately, the VRT has you covered, so you can spend the weekend relaxing instead of trying to ensure that you're safe from these threats.
Gauss is a recently discovered malware platform specifically designed to collect and steal credentials from targeted users for various email and instant messaging accounts, social networks, and banking systems. Gauss is "modular malware." It contains various modules and ActiveX controls to do its bidding and its payload is fully encrypted. Based on the data released by Kaspersky Labs, the vast majority of Gauss infections have been found in Lebanon, Israel, and Palestine. This surprisingly small geographic region indicates it's likely a targeted attack.
Behavioral analysis reveals the malicious command and control domains for Gauss:
[a-c].guest-access.net
[a-c].dotnetadvisor.info
[a-c].bestcomputeradvisor.com
[a-c].datajunction.org
[a-c].secuurity.net
[a-c].gowin7.com
Snort SIDs 23799 through 23804 cover attempts to contact these known malicious C&C servers. Additionally, SID 23824 covers the HTTP request made after resolving the C&C, which is unique enough to ensure a minimal to nonexistent false positive rate. As these rules have yet to be released, we're providing them here so that you can load them over the weekend if your organization is concerned:
alert udp $HOME_NET any -> any 53 (msg:"BLOCKLIST DNS request for known malware domain guest-access.net - Gauss"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|0C|guest-access|03|net|00|"; fast_pattern:only; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service dns; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23799; rev:1;)
alert udp $HOME_NET any -> any 53 (msg:"BLOCKLIST DNS request for known malware domain dotnetadvisor.info - Gauss"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|0D|dotnetadvisor|04|info|00|"; fast_pattern:only; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service dns; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23800; rev:1;)
alert udp $HOME_NET any -> any 53 (msg:"BLOCKLIST DNS request for known malware domain bestcomputeradvisor.com - Gauss"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|13|bestcomputeradvisor|03|com|00|"; fast_pattern:only; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service dns; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23801; rev:1;)
alert udp $HOME_NET any -> any 53 (msg:"BLOCKLIST DNS request for known malware domain datajunction.org - Gauss"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|0C|datajunction|03|org|00|"; fast_pattern:only; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service dns; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23802; rev:1;)
alert udp $HOME_NET any -> any 53 (msg:"BLOCKLIST DNS request for known malware domain secuurity.net - Gauss"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|09|secuurity|03|net|00|"; fast_pattern:only; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service dns; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23803; rev:1;)
alert udp $HOME_NET any -> any 53 (msg:"BLOCKLIST DNS request for known malware domain gowin7.com - Gauss"; flow:to_server; byte_test:1,!&,0xF8,2; content:"|06|gowin7|03|com|00|"; fast_pattern:only; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service dns; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23804; rev:1;)
alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"BOTNET-CNC Gauss malware check-in"; flow:to_server,established; content:"/userhome.php?sid="; nocase; http_uri; content:"&uid="; distance:0; nocase; http_uri; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, service http; reference:url,gauss.crysys.hu/; reference:url,www.securelist.com/en/blog/208193767/Gauss_Nation_state_cyber_surveillance_meets_banking_Trojan; classtype:trojan-activity; sid:23824; rev:1;)
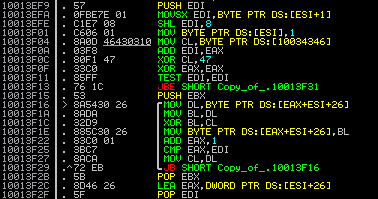
Detecting Gauss locally is arguably harder. Of the two sample DLLs the VRT has come across, both used the following decryption routine:
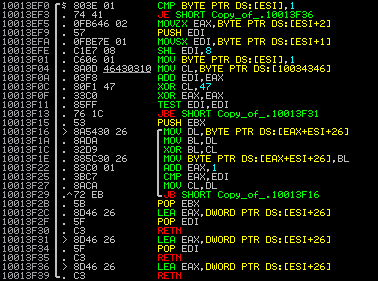
Detecting the above decryption subroutine provides reliable local detection for the samples we have encountered and should cover other variants. ClamAV signatures W32.Trojan.Gauss-1 through W32.Trojan.Gauss-15 are what you need to ensure are enabled for AV coverage.
FinFisher, a piece of lawful intercept malware first discussed by Rapid7, uses a heavily encoded protocol for communicating with its C&C servers. While analysts are still working on cracking that data, it has an easily detectable signature of either 8 or 16 static bytes at the start of its packet types, which makes for a pair of trivial Snort signatures:
alert tcp $HOME_NET any -> $EXTERNAL_NET [22,53,80,443] (msg:"BOTNET-CNC FinFisher initial outbound connection attempt"; flow:to_server,established; content:"|0C 00 00 00 40 01 73 00|"; fast_pattern:only; metadata:impact_flag red; reference:url,community.rapid7.com/community/infosec/blog/2012/08/08/finfisher; classtype:trojan-activity; sid:23825; rev:1;)
alert tcp $HOME_NET any -> $EXTERNAL_NET [22,53,80,443] (msg:"BOTNET-CNC FinFisher outbound connection attempt"; flow:to_server,established; content:"|5C 00 00 00 A0 02 72 00 0C 00 00 00 40 04 FE 00|"; fast_pattern:only; metadata:impact_flag red; reference:url,community.rapid7.com/community/infosec/blog/2012/08/08/finfisher; classtype:trojan-activity; sid:23826; rev:1;)
ClamAV coverage is equally trivial, as the malware contains a batch file in clear text that is used to remove the initial binaries dropped on the system. If you've got Trojan.FinFisher enabled, you're golden.