A new vulnerability has been discovered that affects Internet Explorer 6, 7, 8 and 9 on Windows XP, Vista, 7, Windows Server 2003 and 2008 . It is still unpatched at the time of this blog post.
Late Sunday Eric Romang reported that the Nitro cybercrimal gang, which just a few weeks ago was responsible for a series of attacks that was taking advantage of the "Java 0-day" (CVE-2012-4681) , was hosting some suspicious files on their servers. Upon further investigation, Eric found that running one of the said files led to code execution in the context of the logged in user on his fully patched Windows system.
Dr. Zulfikar Ramzan, Chief Scientist of Sourcefire's Cloud Technology Group, describes the recent Internet Explorer Zero Day vulnerability in this video:
The vulnerability is a "use-after-free" and exploiting it starts with the creation of an array with a large number of DOM objects:
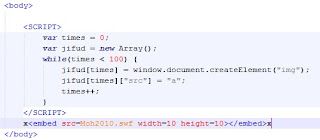
In the public exploit (see screen shot above), a for loop is used to created a large number of image objects in the array. An image element is used in this case, but any type of object could have worked.
Later in the script, the use of the "selectall" execCommand is made to select all the DOM objects created, thus creating a reference to all the objects in the array. After all the objects have been selected, a function needs to rewrite the objects stored in the array to an address on the heap (could be obfuscated). The references are no longer properly resolved once the objects are rewritten, which allows for improper address dereference.

Snort rules 24210 and 24212 detect the execCommand use-after-free attempt. On the ClamAV side, the signature JS.Exploit.CVE_2012_4969.gen provides coverage.
As information related to this vulnerability is widely available, and given that a module has been released for the Metasploit framework, we encourage users to use Microsoft's Enhanced Mitagation Experience Toolkit or even better, consider not using Internet Explorer (or applications that make use of Internet Explorer) on the affected platforms until a patch is released.
Late yesterday, Microsoft released a security advisory to address reports that attacks are being leveraged against this 0-day vulnerability.