Today, as we do every week, Talos is giving you a glimpse into the most prevalent threats we’ve observed this week — covering the dates between Aug. 17 and 24. As with previous roundups, this post isn’t meant to be an in-depth analysis. Instead, we will summarize the threats we’ve observed by highlighting key behavioral characteristics and indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive, and current is as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
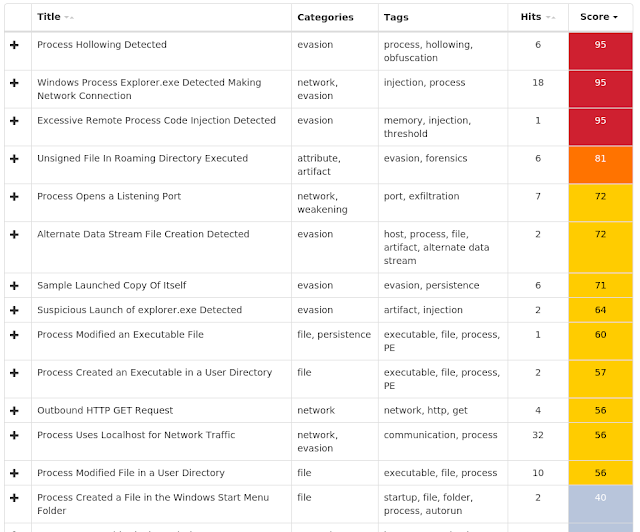
The most prevalent threats highlighted in this round up are:
- Win.Dropper.Delf-6652911-0
Dropper
This family is a generic malware that is generally the first step of a more deep infection. Once the payload is executed on the machine, it downloads and runs new binaries. The malware is interested in credentials and focuses its attention on well-known applications such as Outlook, Thunderbird and Firefox, among others. - Win.Malware.Generic-6652641-0
Malware
These samples are generic trojans that establish persistence using the autorun key, contact a command and control (C2) server, and try to steal information from the infected host. - Win.Dropper.Generickdz-6652226-0
Dropper
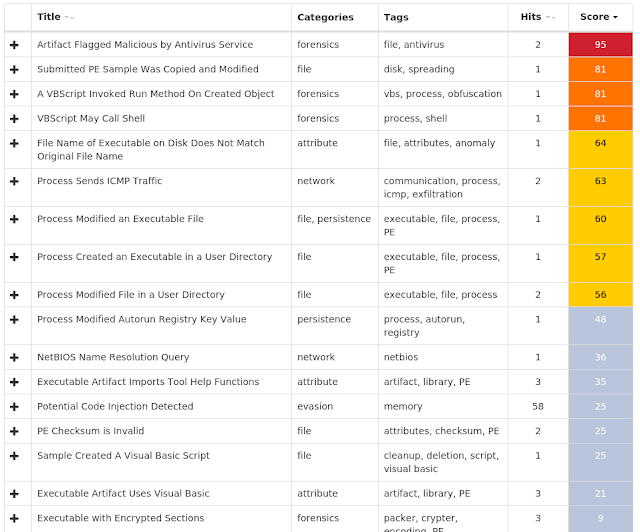
This family is a generic malware that is generally the first step of a deeper infection. Once the payload is executed on the machine, it downloads and runs new binaries, such as Gandcrab. - Win.Dropper.Ponystealer-6652151-0
Dropper
This malware is a dropper for PonyStealer, a bot that attempts to steal passwords from web browsers, email clients, instant messaging applications, and other software. - Win.Dropper.Zbot-6651705-0
Dropper
Zeus (aka Zbot) is a trojan horse malware package used to carry out many malicious tasks. It is often used to steal banking information by man-in-the-browser keystroke logging and form grabbing. - PUA.Win.Adware.Ibryte-6651661-0
Adware
Ibryte appears to be a dropper for adware. It reaches out after installation to download adware and prompts to install them, including anti-virus programs and media players. - Win.Dropper.Razy-6651608-0
Dropper
Razy is oftentimes a generic detection name for a Windows trojan. Although more recent cases have found it attributed to ransomware that uses the .razy file extension when writing encrypted files to disk, these samples are the former case. They collect sensitive information from the infected host, format and encrypt the data, and send it to a C2 server. - Win.Dropper.Cloud-6651616-0
Dropper
The initial binary contains an AutoIt script. The script is obfuscated. It creates several in-memory DLL structures with AutoIt's DllStructCreate and DllStructSetData. The script then executes the shellcode injected into these DLL structures. - PUA.Win.Adware.Dotdo-6651541-0
Adware
This adware that sets up a proxy to deliver advertisements to the machine's browser. In some variants, the adware also prevents security software from being downloaded to hinder removal of the adware. - Win.Dropper.Fareit-6651429-0
Dropper
Fareit is malware designed to steal sensitive information, such as stored login information. You can read more about it on our blog.
Threats
Win.Dropper.Delf-6652911-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- 3749282D282E1E80C56CAE5A IP Addresses
- 216[.]146[.]43[.]71
- 103[.]63[.]2[.]227 Domain Names
- checkip[.]dyndns[.]org
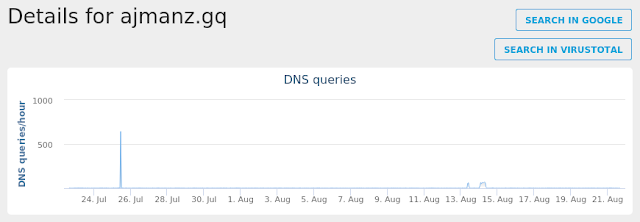
- ajmanz[.]gq Files and or directories created
- %LocalAppData%\Temp\P8g.exe
- %LocalAppData%\Temp\-1260536341.bat File Hashes
- 11392aee8e563b31a4dd14051611148e6ec0d03b2ebcceb37631f27e4bbfcd88
- 12baa8549b752fb6446d498a6d9e1f1ca1b5cbefc97ae9902010a79d15165c6e
- 23fd50159c2daee2a9495400a08c67e92378b287b6635e30efb18b4f16acbf74
- 2b5f4ab8058a74d55a02d8cc6a0a8367263a1068472a2ad63092c2f1a8c825a0
- 2f30c3be0665864ce736acfc093553cc5b0af50146688b0b783982a336ca95c0
- 306a4a7a9a936a2e7aea01f9ae79e595aef2080abcf350a3c7ece41811509e84
- 41192d3dd2635bcd40c92ff46913842b00ac28e5f3d743ea9c79328070ed52cb
- 44114d762126e81487716a964ca2fe0d0fd0e4dba3dea72d619b0f4b32a26ead
- 45c4d4333c17ad765dfa4094e7552e11434b09c4a4274431ceb04bdbb362eddc
- 55ce8c73a62ccee965d023e48243d1f982c77d9fa9c34fd17f2893dd873681b0
- 5f4db44965a523643ad99b7fa7d28221d124a2e2c8c4be8273208b5819db78a0
- 6209350a55e20a0e38a65c0075c66f5e650926f9cce4ee31edb4f69aadaf5f11
- 63b2702c9458be0c53ac24668116946a584b5a96fe9c3379d2477374dc2ae014
- 76180cb564deace04d7c027d17c3297221d72abdd59dec55025507d92458076b
- 8650fb73b188371b1ee7c009b03267c03c3870e673f10d273291ee670d006ccc
- 89dbccfdb0048341d5b3ddb2af5bd8af2fff80a50799545c043bfbeee0d2fef5
- 8f3aaf0ed0a63e6156ab338ebe95e607b779c4ef1d3f99b2a9bf4f1ac25cf857
- a3be5e9da533c35fd20bdbc1a8c4f6821c6117f63f29c6f844a4af93e2bb5a16
- a6d7fc06cbf14af546b91253b55951fea195716bd40196226510b4dfc4a3cf59
- ab740b4fa20b8d8c27dfba02e04d6b4f772cd3b44aa2f1d4d1e3f76ea4631f29
- c57e8eb0fa71df68e6f1f8b4274d1b87f33ad7fab2ea9c3c9b9cf1ef7b572dc6
- d6ec082e1da8b63e3384bce47f2b058af2acd88526964db194ce794bc5830298
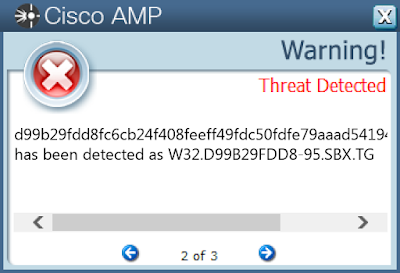
- d99b29fdd8fc6cb24f408feeff49fdc50fdfe79aaad541947f291ce2505a16b8
- e59d68db3399185b85bff7a0538fbf6d52a81783f9cfcd48a851be7a5d00e374
- e91767a779860ae57b777a1e8b6c97022556c8b36c908bba99c5b68157abd46b
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Malware.Generic-6652641-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\Microsoft\Office\15.0\Outlook\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Internet Explorer\IntelliForms\Storage2
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Firefox\
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Thunderbird\ Mutexes
- 91RB0O61SEBW01Fz
- O51OB0RQTC73272z IP Addresses
- 255[.]255[.]255[.]255
- 209[.]15[.]20[.]214
- 217[.]70[.]184[.]50
- 75[.]130[.]124[.]158
- 205[.]178[.]189[.]131
- 183[.]90[.]245[.]33
- 52[.]204[.]47[.]183
- 91[.]195[.]240[.]82
- 195[.]201[.]179[.]80
- 67[.]228[.]43[.]214 Domain Names
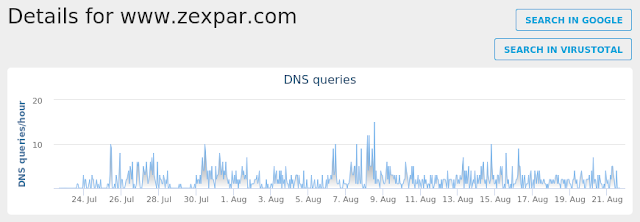
- www[.]zexpar[.]com
- www[.]themonkeygrindervintage[.]com
- www[.]unsubchef[.]com
- www[.]xn--vhq6e39ls7w[.]net
- www[.]marryingmaldonado[.]com
- www[.]shiqiyingli[.]com
- www[.]mywdn[.]com
- www[.]win[.]link
- www[.]risu-nursery[.]com
- www[.]sicknessfitness[.]com
- www[.]saurabh[.]online
- www[.]1113sophie[.]info
- www[.]kacakbahisfirmasi[.]com
- www[.]cryptocoindigital[.]com
- www[.]41230319[.]net Files and or directories created
- %AppData%\O51OB0RQ\O51log.ini
- %AppData%\O51OB0RQ\O51logim.jpeg
- %AppData%\O51OB0RQ\O51logrv.ini File Hashes
- 01ff22b56231012c85e52d2b78024bd4b9c7bc33fc73bb3e2a83a5840911002f
- 04f33361dc741051ae4b67475d747d8e4b60e0add47e0a2a03137a5423edf511
- 09578c66fa6950eb62bd7d0890546a3640878a7347ebd986911dddd9f305b867
- 0a4b87f413a8c8812977a80601790ecfa4429a4dc844db644a6716dce37f3240
- 10909a5c51633fe85233e741ed870b43c01c497a16f28baec778586bd4a5e577
- 149ef4c77df95084d134c13fa6a09b7695926fadf685cf3c8bf02946618125c1
- 15de8d526570f470f010c7dd88d1863bef27f4c62fce08fcd82d1f6651577089
- 163eda0df0d03eb61e15bf9e36339bb0bc76e587bcdb0aa8d6c747d039e93e29
- 17bcfff4f3284163944c5a027a1fef4969d2f5f53dc7437bc3b4204c35de09ab
- 1b0b85e1822dbd3db1b7e3459a5e0b00c195cb08f37b0ad814cc1f63aacf7252
- 1e4f76adc700b02c55bd1c5a084356babb407f242dece68cf9ba5ebf61f1d508
- 1fc76f62000f876b6994859ae31112b789851ff02750f621159ed18c303eec3e
- 203e94abc7b9c527b65c2217c7e2105b429c8a3552e126d1eca91fff0e41ec8d
- 22f482a7cee3ae84ef6e261f3cce4693534a58fd73d846b26870bf933ee80232
- 2a49c01fdd02032dd24b7b1c1fcb9b3aa335d269e69fa8f2a4a4424b1f3079d0
- 30580ba2618aa386ec975baf0b749d342c4ead3be18dd3d42dfbf7aab7321d0c
- 306bea0dfa73d5f76beec04ae3ba1fe4457c343f758c181ca90f91344853560e
- 34f40b1487afaa02bb6e0bc9c2ac5ceb0842acd09a3143a368f3c1959d9667fe
- 38fecd8713e3914e745e751e9c6c5d62d8caef09c46ce4742f5583ce463b0d55
- 3f00f59978a2af3e8f8076c4d33a626f8c4d26ef6a4bc7ae1c72544755fa5dd8
- 407252416a323a0dc9435d8b418137c211892db049b6e1797e2f2f506f6d7145
- 426a170dea0f17f430ec265efadeafad52afcf0355ebc5696259d155a48aef40
- 4a29cce7f2f330b801afbd3f1490f786e0786dc651100eface068576e52bc948
- 4e5249655b852066bb5f6213b638574625a7b60b2c6dfac3bb2e80ec9f72bc2d
- 4f27d56cd4f2aad7b16d568a14fad510ba816319f14006b247b09ba2c6b5d881
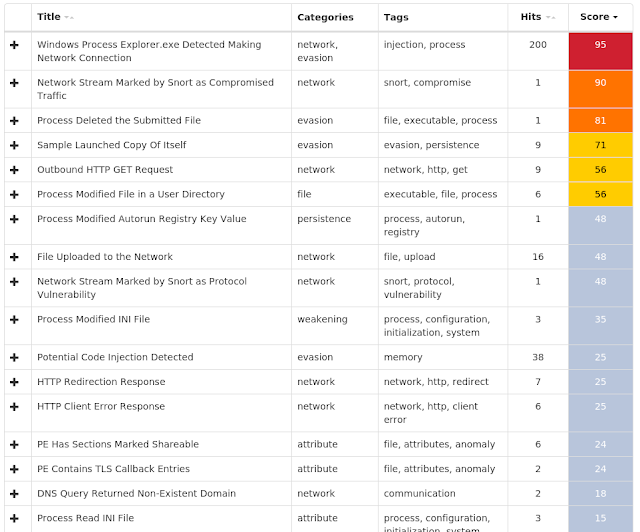
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Dropper.Generickdz-6652226-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CurrentControlSet\Services\VSS\Diag\Shadow Copy Optimization Writer
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: 2951328147.exe Mutexes
- N/A IP Addresses
- 93[.]125[.]99[.]121
- 94[.]231[.]109[.]239
- 87[.]236[.]16[.]31
- 80[.]77[.]123[.]23
- 89[.]252[.]187[.]72
- 87[.]236[.]16[.]29
- 77[.]104[.]144[.]25
- 87[.]236[.]19[.]51
- 95[.]213[.]173[.]173
- 87[.]236[.]16[.]208 Domain Names
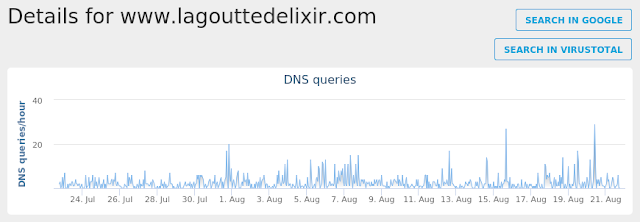
- www[.]lagouttedelixir[.]com
- www[.]cakav[.]hu
- www[.]mimid[.]cz
- www[.]fabbfoundation[.]gm
- relectrica[.]com[.]mx
- topstockexpert[.]su
- unnatimotors[.]in
- vjccons[.]com[.]vn
- royal[.]by
- www[.]toflyaviacao[.]com[.]br Files and or directories created
- \$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$I9DT02V.lnk.id-98B68E3C.[backmydata@cock.li].bip
- %UserProfile%\Desktop\KRAB-DECRYPT.txt File Hashes
- 03a05565633d1a7b916339b179d2998ba0f2391a5f804076eac1bdabd58073db
- 0d25e78ac27d0ae33177d32ba505eb27b662e5b47eb349e3bc90ff4922912100
- 17d8faad65cc55ba4145d3948f2d6d8af553a20863b8e31332390e0b264fe304
- 19a55c08e9253b1cfb5e75ba0cc963006c4e121e6f0ae165b25c243c66f74971
- 27ef40a53faad7f9d08ff2e8e2649f878a3965b4e5edaf052a6fd63c52fe3da6
- 282482f92deecb3e6bb43aa72c39151bccc672907b4bd7e9afb51ded04ac949b
- 28738ba1c8191f4d4119e651436f3ab9740ee22fea8a3b877a0c1f90a7744d93
- 2bf26fe0f26585989ff9c23160867c05fbb817f6565266ce9faeda9291b4b89b
- 344fa6fe96fba331c89ca98a6b739813370519355720670d5d468a49fd9191f9
- 354f463a00be356335dfb1fd6d95f9888a2df87f2299a2ec78366ed983700294
- 3f6fba76a23b0bd34b239cb66df5d491e2ea4a3c199dee39e5f3bd1b303f201e
- 557e03989b74264f90a6e6e8843b7f1e2da369b83e571b31cb051fc19ec005ca
- 565b34697c4d45072a94a442419110f80192ac7cd093a2d695e36505c6a38574
- 81b55b7be0d97d2da88fc1bbb78300ed2dbded9785c8d66db42197b15707136b
- 8b1bb0d2446648f30b9b4847816556fc5a4ca2c3636f612cdb76a5b75c23a00c
- abcf13758ac9ae41a26efaa28431aab8fa704f34f13c629b47c87188ed75ea4b
- b334e0410ccb3f5a27d39ba2f55a87f491a9c18ab9fd7b935d88a4702c7412e2
- c73f8c3f7133426f096b19b3354d3a4512f193c74cf36fc57878c27b318a91b8
- c96689d58b7f9978aea91266888a76d7887932b65a4a257fb8bc9095469a4415
- cba59594fdd4ca6932d28404abc4b0b7b41f873a45f2d47ffe5292e81094a99f
- d5c1c03969093df8ded59a8f030b52a6e0b50a16b72874edeb0b1afe1341a09f
- f0dab3e88bce05940f6bab366953093efc1393e76d6390225da335f70f674743
- f9b03b0475e4d75742e6404e2726fc418f1af36feeded66d0d6fa05cc1dc52ab
Coverage

Screenshots of Detection AMP
ThreatGrid
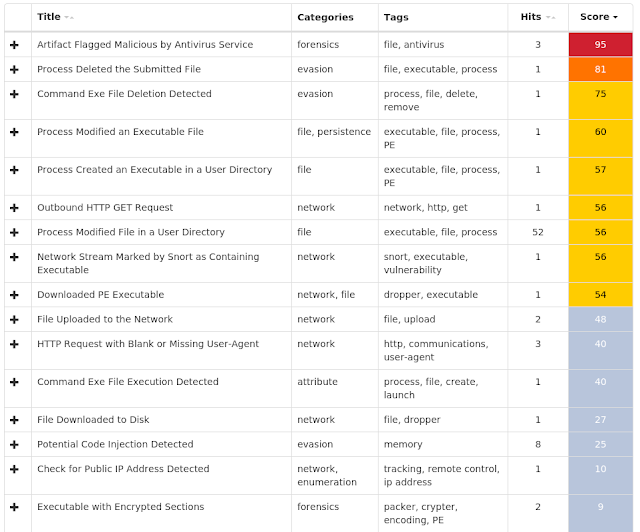
Umbrella
Win.Dropper.Ponystealer-6652151-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\RunOnce Mutexes
- N/A IP Addresses
- 45[.]76[.]142[.]81 Domain Names
- salako[.]net Files and or directories created
- %LocalAppData%\Temp\Xazern\xauzcer.exe
- %LocalAppData%\Temp\Xazern\xauzcer.vbs File Hashes
- 09dee688fc80457daa589b91ad03e7ba97f886f906fd6b0cfe3007871af29b95
- 33be45cba28b09e3898172e85677970fa8be1efcdabf46b763e4d1e040cee857
- 3671ae9c4921bd8dcd9d5e4cb3328615fbd50d6150e19b2ffa7c8d7d82d44840
- 429f93e374501717c87819fb9da3438817f6bbb2f4078fe8b8f3bc39ce720998
- 42bfe2c5da9a771a2aa3fd92e0ab8ad306d9469db287e223fb06a5b2f6411c9e
- 4bf08911cf7b7111429f7e6cce41816b34098755a3b04ee74f1b4d3638f367d3
- 6b814d2ce74af70810c0a462dfad452489862cd4aab1d51cec38b15b3e4e207a
- 7aaed756dc1d45f2123909cde875ae3468b321235ae94034990b1f41e9ff6f70
- adc247428e07b419c929f8483f99c062beddfdd172af7cdcd40176abd0c1a7ed
- c376469a6e1e1c5bd0a455b2a3e0436d2cf8e2f9bf7a482726ad393ccc3945d3
Coverage

Screenshots of Detection AMP
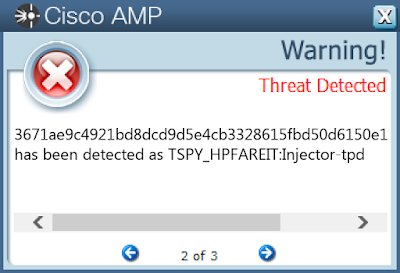
ThreatGrid
Umbrella
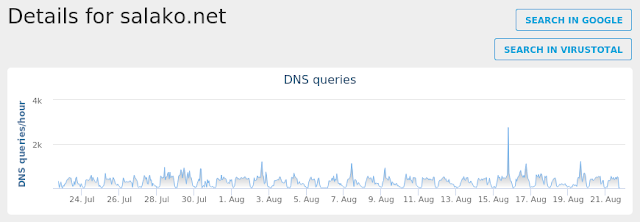
Win.Dropper.Zbot-6651705-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Run
- <HKCU>\SOFTWARE\MICROSOFT\Loxu Mutexes
- {8EEEA37C-5CEF-11DD-9810-2A4256D89593} IP Addresses
- N/A Domain Names
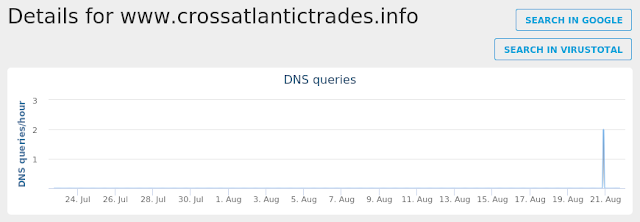
- www[.]crossatlantictrades[.]info Files and or directories created
- %AppData%\Zyiv\opxoh.uzo
- %AppData%\Ihvywo\ratib.exe
- %LocalAppData%\Temp\tmpb488b983.bat File Hashes
- 1ba6b7755498310936c49e2b704d8aa5d22848d845aeecff0a7c680466ff6010
- 3213b7273cec771dce3f249d069d955c71472e049c6d5471d7a1094ee48b03bc
- 3eed5033e3d096b0430ddba825e5ab883e6277e1bb7b8d26fac512b508572830
- 45f3c9a100dc1bef357158a3c648dabbb5002169b65c30e22d6cf84a622d7f2f
- 523993e65033cbd402d4b7d5a460be0a91f83c7f849ecc2d594f77d3c6d7ec3f
- 61a138b11a4720e5a48c4f9e7134cc812db28189d603fe2971a4f1c3af7bc94b
- 860f2a54c4541c8c4f288223f586171bcf7bd34f516e2945ef2a677c422fb9ed
- a27334fbd63647786367229c83fa4726f8accb19c9daa1585e6396fb010312d6
- a4a5bcb01343e9597e6a2e683eb23f457c2c8136ed0a93f2e9d65629824458e0
- b8db41e6dfffda29c0776b25c9ca1a9cd3e171fde6a940b269de942a121bb650
Coverage

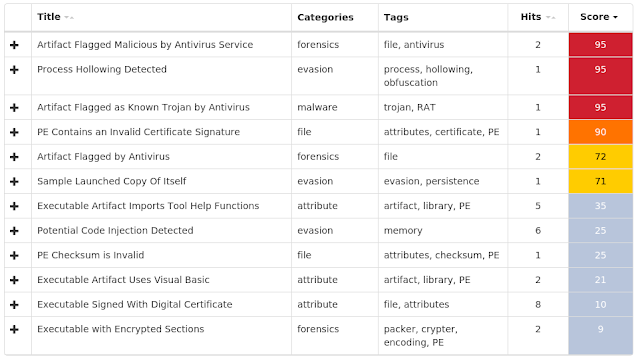
Screenshots of Detection AMP
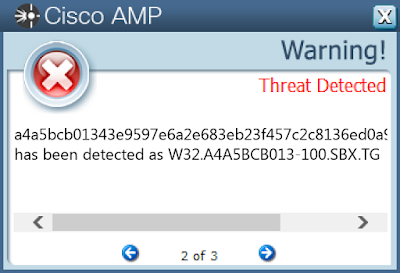
ThreatGrid
Umbrella
PUA.Win.Adware.Ibryte-6651661-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\RAS AUTODIAL\Default Mutexes
- N/A IP Addresses
- 204[.]11[.]56[.]48
- 185[.]53[.]179[.]7 Domain Names
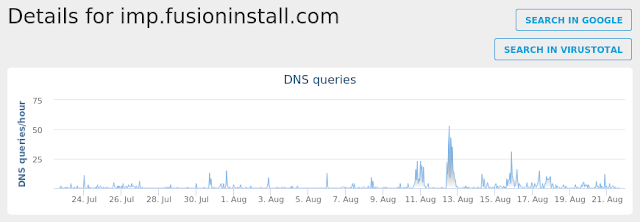
- imp[.]fusioninstall[.]com
- downloadfastfree[.]com
- install[.]oinstaller2[.]com
- secure[.]oinstaller6[.]com Files and or directories created
- %LocalAppData%\Temp\nsy34B9.tmp\image.png
- %LocalAppData%\Temp\nsy34B9.tmp\nsisdl.dll File Hashes
- 0cc4df786af790678de7d97a9f8b3219113b21f5bac09bb6c9bdae6f465f9bcd
- 1897bf161100612c0d15e16b5b7dd80060fb91ee651346c80728ec83f01d7f45
- 5bb6145d308cfd1996c3255f0e5939b74c7f252aff90d160ccb1e005254b20de
- 5ee45058a8b7c48ef494003aa0f132d1c403ada040da8ca97ae004e57e1bb0cc
- 608778c41ca1522c315889cf5e3c0f1c2f114c881f3254044740f2aa34461e11
- 69ff0daad305242e0f30e431b7d3d717496a16ebdecd639c5deb42f504ac4fc6
- 73f7c7ef6e2866b9647106ec68696e8e3c7d4a88dd3cd4f979894da25e3caa90
- 861ea30e5b455525de47bf4818fe8b9a27aa05a494535feb999455b3c80390d8
- 9c74e5e01edbafcfae16ceaa240138e50ff5e7d4ef81809cb052212c313ad781
- cb79344e72e17249005a0087be94a84698604d9ba0ff394d56299b85d7f4818f
Coverage

Screenshots of Detection AMP
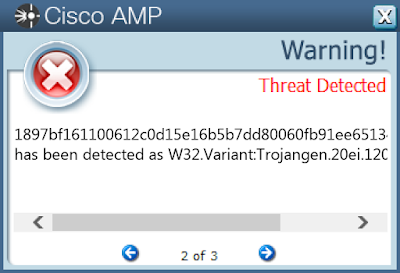
ThreatGrid
Umbrella
Win.Dropper.Razy-6651608-0
Indicators of Compromise
Registry Keys
- <HKLM>\Software\Wow6432Node\Microsoft\Tracing\RASAPI32
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: Windows Update Mutexes
- N/A IP Addresses
- 104[.]16[.]16[.]96
- 213[.]180[.]204[.]38
- 217[.]66[.]226[.]116
- 104[.]16[.]18[.]96
- 104[.]16[.]19[.]96
- 65[.]154[.]166[.]201 Domain Names
- whatismyipaddress[.]com
- smtp[.]yandex[.]com
- ns7[.]hadara[.]ps
- smtp[.]zoho[.]com Files and or directories created
- %AppData%\pid.txt
- %AppData%\pidloc.txt
- %LocalAppData%\Temp\holdermail.txt
- %LocalAppData%\Temp\bhvDCAA.tmp
- %LocalAppData%\Temp\holderwb.txt
- %AppData%\WindowsUpdate.exe File Hashes
- 00ca8e4068f0759ef4e7828cbac93cc8e6768891c8c4cd8f6d642514464f8302
- 16fc7578dae6e8014d5d074e13b2adde3fbd2553bbefee50202f5bf60e547fbd
- 1b9d906012164cf39573d4f8651165742d02ee30ade241947f2917f533da345a
- 232f90e65054b1d251a88b963dd9b05289657e6930b3770d8ff58636ff0e487e
- 42ef9786694483987e92146817745bab9e56209cc35051f158c5ccc6bffa51b7
- 4476a70d770a83f111902b7b0308dbb5cc749f747f2dcca1e1c9a2f0d884b2a0
- 4bd8522ff7e8cf87a89667cf1e0b42a26889487c16fdc6abe69d0ac823e25b6a
- 603487769c60730c697f30717b2093f84451557b251e2d187cdb1842e8db9d4e
- 634f44b01ae79874f4b08ff130a6ab8a04fdd7196812a4300bb55039d56638ca
- 63573bfd0e8c03f42b9194a77acb7da2765396ad4e9ec75b1b853a7245d58600
- 735d19fbf1a9f8a34bcb445d204e51e854c1463072ac01149a8e67c08b97307d
- 75af93db078e56bea18101170b02ce450a9e0216f2b8c3dcff23b83ba76f3a56
- 760065e0657bfb7a952c199fe8a6f15a2bbd5843f1902a4d37c8411d7b9c9d9b
- 777c42471101c9048be523cced54a807c56fab6504e0cc578f4934b4c56c4de9
- 7d113888ef4821c893a078acd7d7e40bd44f150aa4b575987ee4fb802ce35224
- 8fa0f87391d3ee93f16ae5c6a5ea116d2a67d0a2b5c60ed801e53e96aa9a32d8
- a4bf29f13f50d6f4f0e0bfa95af5e89944d0297271b34b77b9a4c915e6ca2b55
- c9dd220291b6542aa9ef92e2872f02de4c323c47f9b4e9730a1c97aab2e2c763
- cfdb62ff82215a70edc66f5593cc06d2e0a0f3d842af5b726a95a5debb765176
- d1dce43c9ff30383a0928cc2423a7370636088a8135c94f905ad37c7dae910aa
- d2ddd1c35d5037984c0885dd411c64361f97738fa041590794e23f073bb1e0ab
- e00e64c5b25507d7323653736da4cd9775816fea7bfd67f9532462b1ec531b32
- eabe6d32b9e2ec97c2fe909e5d0f3a89f974c63dcc2ce43bce5a9c0121ca781e
- f793a4aa08d82d3f3719a8fb376df98f2d2d8dc102af7a0d479bc479c26649a1
Coverage

Screenshots of Detection AMP
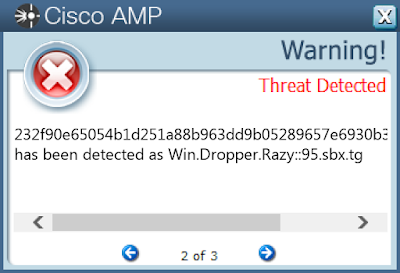
ThreatGrid
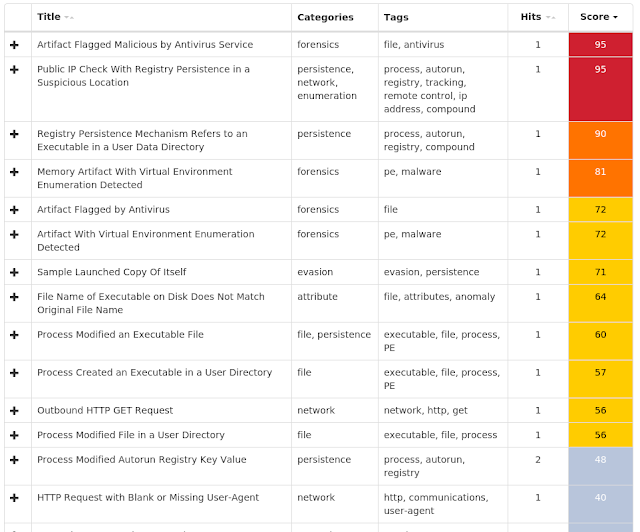
Umbrella
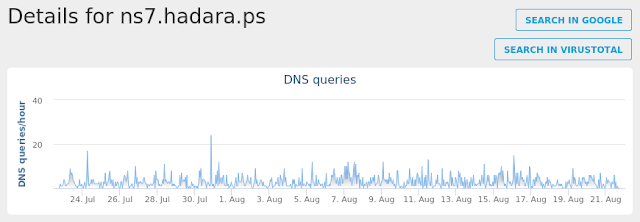
Win.Dropper.Cloud-6651616-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- DENEK IP Addresses
- 204[.]95[.]99[.]176 Domain Names
- spectrun2008[.]no-ip[.]org
- joaosgk03[.]sytes[.]net Files and or directories created
- %LocalAppData%\Temp\Pa7Y5giSl017
- %LocalAppData%\Temp\aut6F2A.tmp File Hashes
- 1497ef726ad9a29b9b64cf16c21fb5b80610e52683de177f9d9ece346788dfc0
- 1dd1fc2ed544f68ba727ed4a02caf935e45ecfa86b02944fbd937680025f2379
- 21ed019435f9541eafae5ef372ac33fdb1c967ecbbd17919d31f152bf858888f
- 485e5121db35bec9dccc93580c470779c01bdad591df7c1d7a40473c0ffd6e73
- 4b7aa109189b3f2738747216ba49d0bb4c9b97b44df3932ad1189b74dcb409c1
- 557c69500e9cdecd65c402f309b414abc9777fe9fd36236eeaf9d533025f6e66
- 58115870df165c7031e5304cba8e059366ae1ee935484f67154ccacf0eae62ee
- a9427d85c27aea20ba8fdecd7d6dae561dc676dd2e106261e8108fcc4005ed97
- c771d4c4de77633786c355722f784bac0665cd457ff19c6441ef99730b8d76f3
- df0a6ff9574bb522ca340fd83a24cc096f1c3ea36b66097155862b71f4383c34
- e4b90714b55aaa69027eaf3e0bf52a3f392aa09e3e4463744d5e8d3ed64837f7
- f66dcfa6695042e6050dee3cea7948a80b217e8345919f6b90cef22f1ecddc4a
- f9c5dcf920e1ba39fbe35cc7dc9dcabea6c6f67d533559c06664aa3665cd4bd4
Coverage

Screenshots of Detection AMP
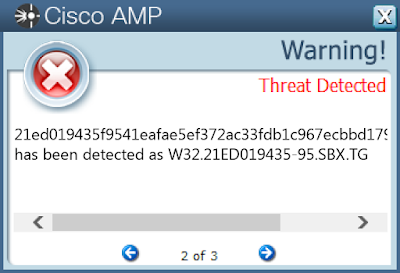
ThreatGrid
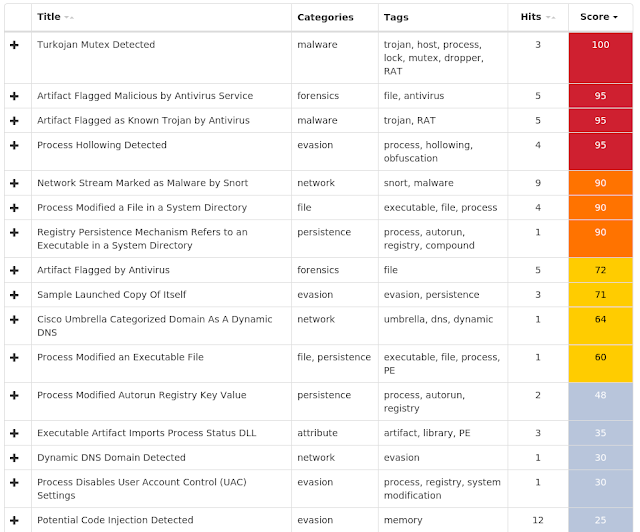
Umbrella
PUA.Win.Adware.Dotdo-6651541-0
Indicators of Compromise
Registry Keys
- <HKLM>\Software\Microsoft\Tracing\po3v5cyhl_RASAPI32
- <HKLM>\Software\Microsoft\Tracing\po3v5cyhl_RASMANCS
- <HKLM>\Software\Microsoft\Tracing\3v5cyhl_RASMANCS Mutexes
- N/A IP Addresses
- 198[.]54[.]117[.]200
- 52[.]205[.]106[.]49
- 34[.]202[.]10[.]177Domain Names
- www[.]lubricantshaffey[.]win
- s841[.]datarating[.]com Files and or directories created
- %LocalAppData%\Temp\nsnBDF8.tmp\sph9d7jl1.exe
- %LocalAppData%\Temp\nsnBDF8.tmp\extss.txt
- %LocalAppData%\Temp\nsnBDF8.tmp\po3v5cyhl.exe
- %LocalAppData%\Temp\nsnBDF8.tmp\dsph9d7jl1.exe File Hashes
- 16aa5f4db1485896a6dfd2cef40a6243c0371a213c18d2832c7a9070b7e9002a
- 434a7a324719c74ce3fa0dfd96bfdc14379ca8a0af954247320a1a76e80f995c
- 70fd79d11821428a90b1c3869f846329af646e014887d72b1f4df531f8d33ab7
- 8a4f468b126f0c309f5a64cd694a503aa7269d03372d3946e643005b30986475
- 99ba03979407568ba6b1ed32184a043661608e039c9a3511c9a910a31dcd0ccf
- 9adbf86b70ad8d487a1f67b4650b68b0dc03bdc84a7e84b1654fe8ff61a7cb88
- b105d0c22989e4856995573a59ff1034ee6ef4ead24c2573ca688da4c94c60ee
- cd18a0939f808496f5e05d3b996ed2a8d13dc94261ce329ac209ae086e7b9d5d
- d399c525b8da116f8ab17333b78a88f20401ddd960405631e2cc52e7054bbcc4
- da1842c44891d3ca1229ef8b8959edd4f974d21c700fec7ca64f3124a6493be4
- dc7d530a26e005dd8766fd52c5d62c06c458a9018828a3ec4c8f80832ebae221
- fae36f1c522c56bace27be915fd9e23748ec01ac9e87810348cbdfcf53a2a87b
- fb388f3cd64b8a65db9584f1526eef8d4b876b5bc61c8674b4caf8bccf78a4e4
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Dropper.Fareit-6651429-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- NMYQsgquQO IP Addresses
- 78[.]47[.]139[.]102
- 212[.]112[.]245[.]170
- 154[.]35[.]32[.]5
- 193[.]23[.]244[.]244
- 62[.]210[.]204[.]55
- 185[.]106[.]154[.]118
- 51[.]15[.]44[.]251 Domain Names
- myexternalip[.]com Files and or directories created
- %AppData%\tor\lock
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\cc.exe.vbs
- %AppData%\tor\cached-microdescs.new
- %AppData%\tor\unverified-microdesc-consensus File Hashes
- 02c77b65bd25f4708f6b7f82b60689f3ace02639e4d262f172633e73f1e18071
- 0587813e2d50a8bc2a3b6cca7749c3d134b51826ae7f13f832eeffc283306110
- 06af72696ebe7994f9542af787dd5cb357b4348248c72038c7880fbeb67110be
- 079f068987d7c53e2e47c39b89ca6f412a7a17e34992eaa33757aa99e29a47d8
- 0ba6e0f83d3c3239cef5f30d2600c2e4d3e9b9ddb45a40cfbfcd86622a47b610
- 0e12f2bc801777198026a86c920edac32b1eb874670730cf3f033a8e9fdba2b0
- 13c96d7301e2b6bf3c9c9cde9199bbb538caee0ca068a9f54190af1f43059400
- 16f755b71840a1e6c8de8a4bc6920cf2af1e8e821c2a77df2e3151dbba679a13
- 195e09cca7a53e51250418e1c75157d5aab8269186dc68ba98fb5e934c2bc15c
- 1b8e74fa84432c944ec2b239ab67abfac39b496a1e96dca7c0a7e92255457ecd
- 1e53faedd0d111860b9eeabac7d61f0306c1d516fec0d11d043e83b361ab8e95
- 202a7444df57d7f3846d3b58a2a887f28dc64d2727569af2255b26aa395ac441
- 2128405a27110cf86a1f9f41ca06717ad3c9a2598302cdf19531932e51c4ece4
- 222ad72cf417a849ec0d96199345cbe7340d3978d3c396dd45444f12ae8415e5
- 22e4fde98af07c792e71e81a003f5472c868e5a05eb7c45c4eac9622d4c03345
- 2623021afd3dca853fa09e36d31539ff55b9843cbec915dd64375ca31943ddca
- 2666e5aae4ecb9ed923a4e16d5c9af953bd4a2082295df3724b7bf2697b36616
- 27990924f27b7fc60db6fef7323ee841507f94c2fdd3bc27a446d537fb3989cc
- 28083fe9ca79c1e20e4fc1f38cb8cdc7061bcef37e255bca5971e33feadb414f
- 28bcac13100c3b048b9ce179f7896a729889af0b3461306f1f7d48f1baa3b212
- 2b8825719d8001c42affc76b776d266aed8055cb40eced293632515f8841664d
- 2d7a16ee5f9c2bfd89651b044accd40a49581bb5dd1ca8a58d46f986ea73be72
- 2ff7012e08a2a95c39e56df2e0a5f8d9d6c82e1da218d89e35d4da770b8c6d54
- 32ee9fdd809fc9e467f23b69bf961d9a79a5dae849219df99da1e443a621a015
- 413f4a778b3edd7577b62165d567b2c438d1bbde941c0fe05875e775bd13ac4d
Coverage

Screenshots of Detection AMP
ThreatGrid