Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Feb. 15 and Feb. 22. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
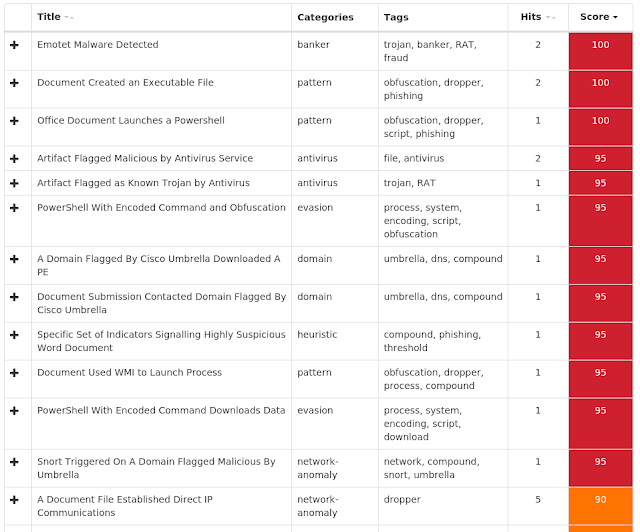
The most prevalent threats highlighted in this roundup are:
- Doc.Downloader.Emotet-6861668-0
Downloader
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails. - Win.Packed.Nymaim-6860565-0
Packed
Nymaim is malware that can be used to deliver ransomware and other malicious payloads. It uses a domain generation algorithm to generate potential command and control (C2) domains to connect to additional payloads. - Win.Malware.Icloader-6860563-0
Malware
Icloader is a generic malware that largely behaves like adware. The samples are packed and have evasive checks to hinder the analysis and conceal the real activities. This family can inject code in the address space of other processes and upload files to a remote server. - Win.Malware.Bublik-6860562-0
Malware
Bublik is a downloader that targets Windows hosts. Although it's primarily used as malware to distribute various banking trojans, it's also capable of extracting and exfiltrating sensitive information from the host. - Win.Ransomware.Razy-6860532-0
Ransomware
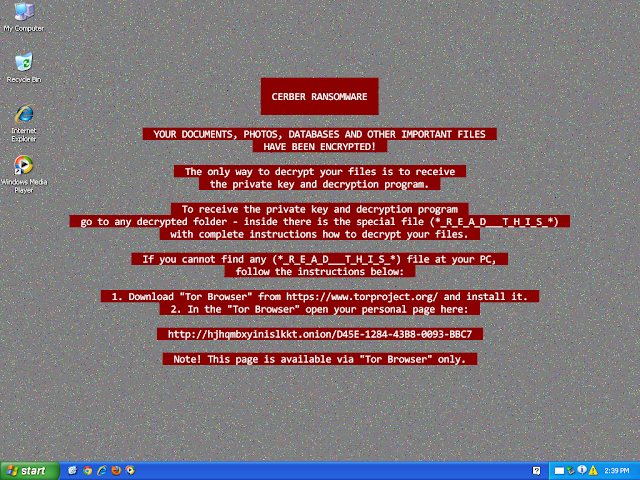
Razy is oftentimes a generic detection name for a Windows trojan. They collect sensitive information from the infected host, format and encrypt the data, and send it to a C2 server. In this case, some of the samples in certain identified clusters can be attributed as Cerber samples, although the detection remains the same. - Win.Worm.Vobfus-6860533-0
Worm
Vobfus is a worm that copies itself to external drives and attempts to gain automatic code execution via autorun.inf files. It also modifies the registry so that it will launch when the system is booted. Once installed, it attempts to download follow-on malware from its command and control (C2) servers.
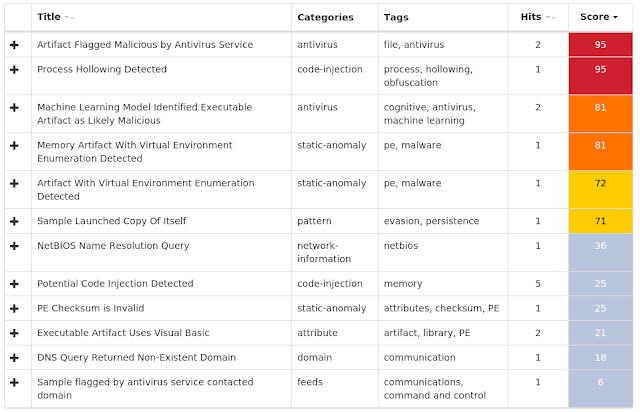
Threats
Doc.Downloader.Emotet-6861668-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Global\PowerShell_CommandAnalysis_Lock_S-1-5-21-2580483871-590521980-3826313501-500 IP Addresses contacted by malware. Does not indicate maliciousness
- 189[.]236[.]235[.]73
- 70[.]184[.]86[.]103
- 76[.]113[.]130[.]72
- 117[.]52[.]20[.]53
- 66[.]216[.]234[.]131 Domain Names contacted by malware. Does not indicate maliciousness
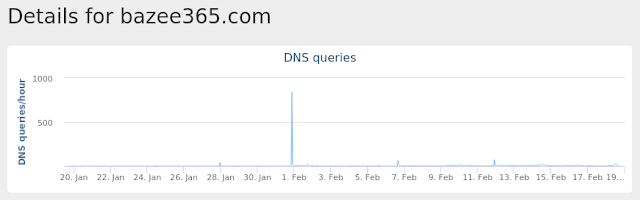
- bazee365[.]com
- serhatevren[.]godohosting[.]com
- mediarox[.]com Files and or directories created
- %UserProfile%\405.exe
- %WinDir%\SysWOW64\E7LYsu6obSo.exe
- %LocalAppData%\Temp\kfcdv0jf.wos.psm1
- %LocalAppData%\Temp\lu4nllxj.0of.ps1
- %UserProfile%\Documents\20190218\PowerShell_transcript.PC.gVgu3PJN.20190218204843.txt File Hashes
- 0349453748c3c3fe4631e5c17665a702f7ca1ba8cc2c7508a91d686e17d41098
- 069185a0da074e0ece155c5cda364e5092b2573131fdc2c95002b18c44937a1d
- 0946a30abd52ef463b6a390efba6595d2a7917df95d3739df77e3ca57d1ecc8b
- 0966f1271c4cdd0f66bca3520ffe406d4ba14aaa06a7b14aa505c78958fead20
- 09fe30dd8b953d25af163fc4db119afd7387cc4b5109f331e1651927bf61cc63
- 0a091593757cd2d16b4ca2ed1806b73f1222f4367d6d78e0df8ee98c247ef1f6
- 0b6003563af9034d9a22f96adb0559f04b3753d0d4d9e6e76dd49504a427317e
- 0f25037f951fd8f0f1c2f4b94ec84d3aa8daa3f7d5774056136769ecb800dc6e
- 106b4d87576a07cc74f8ba9519d9730b50dc7309e69d0e7764822af981d98e61
- 1328ac0cb151437871e7f39f72b20c13fb9fc292adb78054f30a8f958404e4c6
- 1caa72377c62835653e1c1b062e418c62b689f8b6e600b739201a1300bae1bf5
- 265a6869c2a2f0b3f35b316eda5e78492ae2a574530c39a1673845245a342d67
- 27b0bd35f9ee7752e45d40707a3a777d20c8563e7067007101ec8de9d1c271da
- 2a1ca1f2eb72dd935b9ae4594eb332d9ee7363b70f1fa40e6b3a1a4dbdb44e1f
- 2cc2fbcac3c4262c49e3ad49903d4e9ebc5fbaaf9a2ad65ff53f808380b70a12
- 2dda30d522c1b72d38f8609a3bde18de25aa57ad7ba7d90cffdfc0db5cf6e977
- 327c64ca7348a0e2e4651a332776d10216cd77f77761766a12094cabe446ca4d
- 335b40ff58a6cf92f16ad95349e2cb9dc42d71654cebaff642fbbc168749bf26
- 380111d3408eed7a855ef759d4304570286eb4478d35b0ad1f35cb17b853b353
- 4392d56f6bda858b04d0a4cfe1112fba4a80c56bd916618b804e02b703465dea
- 4a5fe09fd3f776a86ecdbfdd0c6fe9abfd962a16444ec8bdd2dd03704fbdac6d
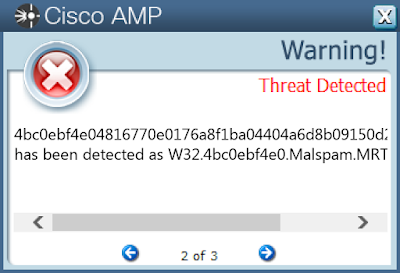
- 4bc0ebf4e04816770e0176a8f1ba04404a6d8b09150d21bcfaf3387ffed06606
- 4be4a46ef25e71de87371345da22d043385a72a479adf2ed56326cd69b2d500d
- 4db8c7a64afa55409a39042cd1ba8561230da23185f0b62a6e2243ad3efef4be
- 52a1a1863cc969cd93d48371e9d24e59cb691a8442477a4d8b1c25c51e71eb13
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Malware
Win.Packed.Nymaim-6860565-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
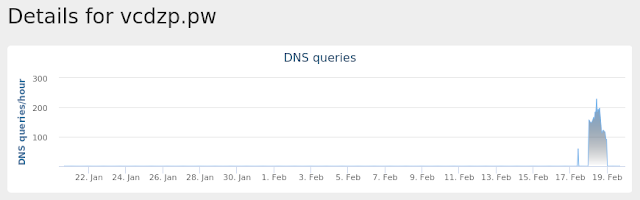
- wmmjykpublbk[.]com
- yvnnzvdcqs[.]com
- yugejra[.]in
- xriuhkmec[.]pw
- zhvar[.]net Files and or directories created
- %AllUsersProfile%\ph
- %AllUsersProfile%\ph\eqdw.dbc
- %AllUsersProfile%\ph\fktiipx.ftf
- %LocalAppData%\Temp\gocf.ksv
- %LocalAppData%\Temp\kpqlnn.iuy File Hashes
- 016fcb5281374301a886e62512c80bace5093baa28317392fa47b41c3fc9c209
- 04f643c92239dd1c24928a3da8a7ffc6974223fdce4c64f74ed16f77e606d1a9
- 06fa8ba73421f80a6b6a872832bc5fd37dd045280dfbab48d18af291c4f3a0b6
- 086685fc1ad9812ad986639b77db52cf570c63fef36b6220dfae184a4da20aa9
- 0e37a6e0bc2078eb99991da03dd81d85a169b0646637b8d16240887e8fb50f57
- 0fd6c83045db3b972b5329f11e6160251b53d1cbbf61f8b065421b8231982f2c
- 0ff32246d64c9529c01cd62b5ce2474ba77f11422d4aa14becf0b34ebc1d9b40
- 139572026f38ccfb8fb615a0a202d9b315cca46bb0ae31870e60aaa1b7db1d23
- 1655c03b41b2a5ac72829eb3b4867de87c3643f2e7cdaefb9e88392f8dff916d
- 175398f6a76bfb59c31c9c46c2d7c452be9f146451197042c5e0ef39a42f07b8
- 179c96674980e6ed485fe00d82141c3729274b5d6e13129801d445c981264e23
- 1a47d3a4951a6955fee9f29e0e6629b6e29dd4db58378e7ffa8aca948688175e
- 1b6d29d704243956e14ea5a259398b9e0b52544bc8ba3b6ca1c172273416517b
- 1cb1a09aec8926e8df8dd7edb1ccc63ea7192330ee36704ae3b2b706a6630cb8
- 1d99c9bfce431b2422370607430efd5b155b76ad58dc615d79076b8e0f2a7e6a
- 1e07e0277acf86c37ef6753ba1a2532e933044c7656ecc063c236c585b83c26f
- 1e5d95ea42bfc038d4513fa688336cd73622ed707ed188d66aed4cf6ac1086a1
- 1eec7c86d30be19611b16bd5e17fd747da9df96fa2907ca23acf1801b6c383c9
- 20d599362a7f80b9964569df6e07d2f18e434be47fc01dafa7e7d73831677a42
- 216a5552de53349bbaee2f121538c7b66783f1752a3d190f5b978fae27a77ed0
- 21c85e5768071487832d29e9661f68033e9f7baa30597535ded88439cb67796b
- 231d98cb92d4affea6db88d42b31f8b0d001a933c97ce2e670423fc1d185d6fe
- 2361248d5291c923b8763530dd5c551accda742d6e7d15660534ab56aff11ffe
- 23e28028a5392440dc99a040a0043cb3de50bdd678ed26777b72437819657d14
- 2472ef7f75de9881f4c6269de9093721147918a3ae94fed19e8078d9f42695ce
Coverage

Screenshots of Detection AMP
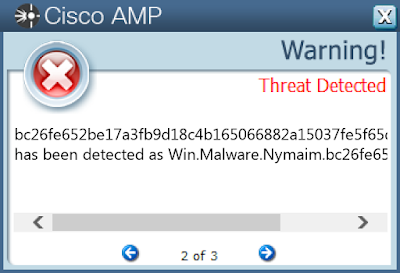
ThreatGrid
Umbrella
Win.Malware.Icloader-6860563-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\localNETService Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %AllUsersProfile%\localNETService\localNETService.exe
- %LocalAppData%\Temp\tsc131118.dat File Hashes
- 01d804f3bb30a0082396eaecdcdd0e9e329ea3ee585b8e0fa4f24210be9b644e
- 02f50ce46cb615461dbf0edf1b795f76a0cd8e9126ef8938a6a02266a98ecbbc
- 0827b4fed47eb0605a345f1e733b3b1937756c28254913fc8a36d4ba28b83541
- 0d572da25a4bc1db88843cc8610fe56e4a336dbe322c26248b594f7622113cf5
- 0e3a72fdb86ff31b61661a473db0863143c0f7c8e8aa659b7cf318ec6756e1ab
- 0ef73d5cc5afb4c6ad73cfd27724af99b562e0dab76485aa73414bd25fa0eac0
- 106b0659bddd2b26246fc00b929e8004dffe15fb9389fc7bae7cc1bec7f76a62
- 164966f0b65f4c0816a6b2af88f4846f15e92b0c2f4b76dee98baf875e4deede
- 20b1446c4d8190ecd749d995113c5bc6ce8375da14c73f7ee3c8f717e6d42e07
- 288a80d10c4d1a42eef45f92c1fd786009c10f8a54b1cebdf6790c6f1d0b06b8
- 29fb858feaf6614d5e5eccf68f7fe3446b11fcac0067b2bd1e24a53a23f2b9cc
- 2d7bda9823c838009d950022e78b9abf49246be6dd25c72c32eae10f43276c3b
- 2fa1d8b8719ea8528bde7c3ecd421d79a1e5ecf63612ec52b4c8cedfb5f6e1ed
- 2feec8571fb27548f20dc65efa838283c0f7be39dd8502bacd7472148f1f32b1
- 30361d76097bc679434e488157c98625d6961a936340947894f7f105c3d406b0
- 338d97248b5ff7489157822d0b0c413d550a46ce6da712e2fb838290bf7697a5
- 34099d3b62bb8baefde01a72f6921063d81dcd33c2512df3755aedd5524f19cf
- 349c06fedb963107c3dc825075c9517eb05df25091bcbb9d6407843b745409da
- 36064556c3b25426b42b43e8ebdd7b9ca3b6d02a54f0eb20ccbce62e4818a6da
- 39afaf2f57b8a1c6ed2ebe4072d0e81832d94d31e1c1f3a016cd65b500e14d62
- 3c603d3673c795fc13f7440c38908ea9cc4283a3d79e9f03bf2bb775162e0a8d
- 465fa07297f1aefff4acdc99cdc1e17583f57d29a0437f21e94c967ee2b6e838
- 4c4807efed90553e868ef794b9d7218ab7a635c1d95f6e56c45b8c0e6ecb1bee
- 4ca27d52b58f33e8a99d68509cb9487417844ea5501056177ebac910eb329c1f
- 4eb6179bff74cbc8625448c010aeabadf5bb7ee1fe1329e80f54f062f67af426
Coverage

Screenshots of Detection AMP
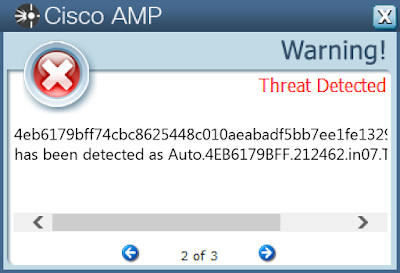
ThreatGrid
Win.Malware.Bublik-6860562-0
Indicators of Compromise
Registry Keys
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE\IndexTable
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE\LruList
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3 Mutexes
- Global\e02ef461-32f6-11e9-a007-00501e3ae7b5 IP Addressescontacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %LocalAppData%\CrashDumps
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\7A9E.dmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\7e9a_appcompat.txt File Hashes
- 0077f54220e81d1351a81a51f7089e1e0344b0e0c7e1db2baed69fc42d212eef
- 02f3a6dd7ec83508d644551b34f082a47597d91b70befc75662fa7afd2c1a4b8
- 0f155a227bf791b43ee66c51e5c3d6ff7edb46a70476239e7e3eac2af083b942
- 253c1e82213e8075144aaa722abe1786110d36c845f3ab62a67383ac53d33298
- 2565901fbf675dc8bf6bcff213ddde8f274a96f016dad4ed8d6bb04131fe2ae3
- 2623f7ef229170bed9265f02b4570b272b2913154800d42a493404d8fb412500
- 267298bf98507e02c999c1d38407d3f295d86f48f40e98fd33e8735861886011
- 3244e9cc8b1d9d3cc7d5073544bfa675876d423e57edadbcb033b949a8c811c0
- 327ffee4d88231c1b3efed3baed72a736fe7e1a3cacd02a83059774dca35e9e2
- 34e85051b9718edc52253faccd1a85e09ccdb118ae289a24c5b3eb660abd4b63
- 39854854e613965c6cf22e0380163f187867e6d1e25b8b85890c62fab1cf0224
- 3ab69a728aafea29c3a1de3a419efd93b889aafc7eacaeb3a3f9d7c632dfa8c1
- 3ee8339543fd72e79f03c5878520e9d0058e11ee49765e9ca73a7236e9c7b8ce
- 4342cc9cb045b6c87fb822345e7dee6d9e46bec385de4ae7be1ff6ce6061572f
- 444dd5b17528c2dbd05d8afb1bf633b4cde0855deb0338a52a17df67e7efcf06
- 4c56d62c2af1fda0af9be1f377ad7d737e7db306e7dc684df5a7c0163f10ebf2
- 4de35a78adab9e0f79a88a1452916719f42641155de80f6c90e5a152561cdaa3
- 4f011f91715575b91312eb8a29509d9c2aa4950127efc98e88d44d08ce143efc
- 52a6cbca15c3805effa45b474a732f9b74d38d35a78e3763380735cc6a685f63
- 5a73cda9b407ce518c1d5a9c4965d6287e2e2b4193e8fa702542c684c050c130
- 6fd9000a376b03dac177252a2e2879aa70c3f3365fff351d637f7b36aa2df385
- 7081050e0504735e2f48c098f5758a5a01c8972011478b6c5b2fcc5e33ea4932
- 8265acaed3a210ec5999474da742f447a23b407d5a0bc9ce1c42a48f609e6b61
- 852d1d4ee1c4a04fc7ea5b849d6c663725fa89ae6358e251325c636e81a47a5b
- 895e9a298dce50a19cd158de7f8a504d07948713a042e356d4207d6650815fd0
Coverage

Screenshots of Detection AMP
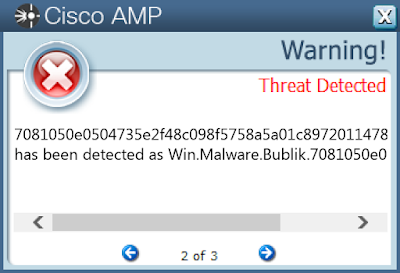
ThreatGrid
Win.Ransomware.Razy-6860532-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups Mutexes
- Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7
- shell.{381828AA-8B28-3374-1B67-35680555C5EF} IP Addresses contacted by malware. Does not indicate maliciousness
- 178[.]33[.]163[.]80 Domain Names contacted by malware. Does not indicate maliciousness
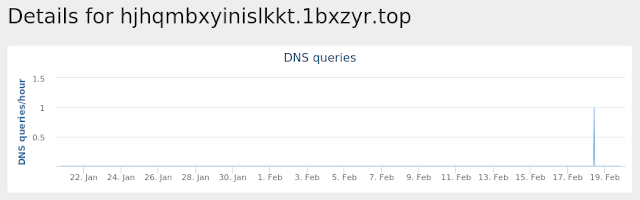
- hjhqmbxyinislkkt[.]1j9r76[.]top
- hjhqmbxyinislkkt[.]1bxzyr[.]top Files and or directories created
- %UserProfile%\documents\_R_E_A_D___T_H_I_S___9FWW7OX_.txt
- %UserProfile%\documents\_R_E_A_D___T_H_I_S___MHSXUD0_.hta File Hashes
- 00cd7c1116f489b0cb66d67b3fde935928f891ae96656b6cba08563e3bc37e36
- 00d74b27e8660696a3e9f23585fd484e01c96c6ce6fed3a06082adffea90423c
- 01b9a1ab489f0499eeb7e8d67d75b42faad1c6fe6f4a1e4353f2e79c5d92f5cd
- 02b7190116a9bb98467f28d92495c1bee74c60af05fb58fff8199909260bacd9
- 04331cdca654e951f24f524d5d624f7137a197c99ab63aa9aafab67b56fec248
- 05863f8c9b9608169db2678d0cae1bce91a80819c091b9b762dd05cab2dac6ce
- 05c0678a044fab83eb77232a298f9114df78b1084b709a2dae59fded201919e4
- 071e548c39279c6ca7fed247213cd877ddf2fa106e5b8892a85cad4d2605ade0
- 07a40a71471037198a9e8c5c5a4e45e52115f772f598a2db0eb8bb187c914c40
- 07ce564ba06045026ce86faa30ff216f21398427e300131f202896441fbdf1fb
- 07d6477d260ce2bc3477902ece2c2bb6e290f1b36f04594c40292b049d42c6fb
- 08b07947fdf606f894e94678574056641da5db8f4db7f5774449fd21bebad29d
- 09fffb50fd033e16a63834d62e2ab5b3227abc57252e87509398cf6ad8b06458
- 0ae803d152f2cb6bb68e10c0c9244b4aac63a11a43153f2285c2b674fe9fc657
- 0b77399249b1ce25a8e408de81e3e46951a5eed52043069d1e48a407c0a05a47
- 0bd766bfedd04e188ee3885d523f6cd170d0c36bc159bb82d3772b51d8a36022
- 0c26799f75d7d16b8ebdf13ec6940cf3182af53e9cd451540901769380de6079
- 0d5d73215146991e0b32224281c6b8bc01248674f993d5d9fc90f5bed45d0d2e
- 0e23f0c0cab7a1e82a2909ee3abce4f88dbd7c54b7a748bd7966b9b1997ed09b
- 0f5d5c8840b06cf60283ad399e55b6bbe7f20edcfb26d332fa72c4103e155e68
- 1360e01b934cbc6ba2db60091ee38fd23efc5321a5aaf17563dc61a7824cad96
- 144506736eac91ec05d88315c8b74f2582a5238e48b41a716d55190b5942befc
- 16256930f1ee4e254193804f4741a81b427537e666aced7ff823ed582359ce2d
- 165010fd8c29e7947144e776dbe81a84816a322c29c72ac21dbf6d436648e382
- 17304b3bfb5ab40bc65b53ec39294bdbaa8e032dff44f2032a0b5a7c0b96879f
Coverage

Screenshots of DetectionAMP
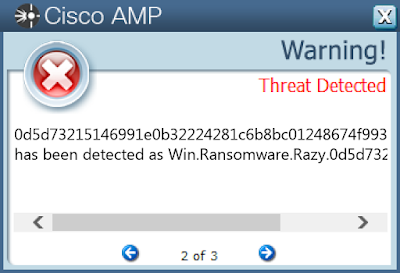
ThreatGrid
Umbrella
Malware
Win.Worm.Vobfus-6860533-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Local\ZonesLockedCacheCounterMutex IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- 49161[.]dnst2[.]net
- 49161[.]DNST2[.]NET
- 88818[.]dnst2[.]net Files and or directories created
- N/A File Hashes
- 002c51db9009f2207dd0398defbc9a9f391f327f07105b19ea5c7c9c69ffd674
- 0096449116e4ebcd77a9e7c43723e793765974813475ed99aac513bc3d71b5b5
- 012ce7db1325159874f9b8925e524ce18b2c62dd230f1b2a674543bd74856137
- 0133c6d934996d6ea32ef17d0a6df96dc86a4b45d9e51e702230b167d87a9ed7
- 02b3e2b1723573274b6e91e53cd973ed8d5e242f3ddb44369deac8cfb2368778
- 06ef151d2aab329341ce68ce7a8b2e7c3b463ca940f47cdd6ce51a864af3266d
- 075e36642d1e37cc11c500a2cd2f3ad3fb2af73bce45a1b6e905078f00adac18
- 098cee9f87724372cad66c0d7797c8f3cc6832aded95235513799aa8f6061d2c
- 0b7af27bf47a48843e14aae81cd6f8c99e82da02c352f34d50d0fb2cca03b66f
- 11ef099b691e051efb1eca27aa5d8606157b0e7f0eb83216733e48f82c52ffc1
- 139c385377c85ac709c77857adfbed6ac46e0e5f57e4b947d730ab871cea6154
- 1b456b78b84fcc6137bc85f0203e29e558c3888c74d610a0ecce19c9008197d4
- 1da4ccd179876bcc378ebc4b1f3597e393e3b976cd0f0a7c24c51b9855d3fa91
- 21cc803b77f7413c781bcc21a7681470ad926289c28f6d126efb899aac482988
- 21ecefddb6898cc39ae277c119f47a84869afa5a798e70dcb58059dcb75c87bb
- 25fd3bf11d2ab30e74ccb67cc0ba7563ccbd0a1502b077da80d13239c9ea3b02
- 269f9b6e264729a3ff2c71abcb320e07d4ff4e76acf6be1b294c6a4b687beebd
- 27d60e838ac4e142d5799628e95138a959bdc9358af047937f1d42f45ab093ca
- 27e3fb1689f0fb0ab76d217909cd52a78dd290ce12a13ffe234542c675769eeb
- 283293ffdb4838e037561e8ac0df74cdd9181ef046ffb3e5ae0ae2d3614f4b27
- 2d2fab79f6d87e2994a60e3a982804fb8d05aa75dc13e9b4bdc9705a9db6247a
- 2d60ca16f74ffe613981c2c27d40992f3d309cbe7b4a693f1fb632590f06e278
- 2f3f0fabb06ce1a8d3c5bc6c120473a2f597f4050fd4b92747c766ac3af07881
- 30755cf5b6934d725fd87dc667fe82b3fd4964d6c55cfdcb327a29e95dd3435d
- 313fbcc0ce24e2c0d2c5c6870842feac4f1f2722101037f0c421ac0a9185ea16
Coverage

Screenshots of Detection AMP
ThreatGrid