The goal of malicious activity is to compromise the system to install some unauthorized software. Increasingly that goal is tied to one thing: the user. Over the past several years, we as an industry improved exploit mitigation and the value of working exploits has increased accordingly. Together, these changes have had an impact on the threat landscape. We still see large amounts of active exploitation, but enterprises are getting better at defending against them.
This has left adversaries with a couple of options, develop or buy a working exploit that will defeat today's protections, which can be costly, or pivot to enticing a user to help you. In today's threat landscape, adversaries are always trying to develop and implement the most effective lures to try and draw users into their infection path. They've tried a multitude of different tactics in this space, but one always stands out — current events.
In today's world, everyone's thoughts immediately go to COVID-19 and Black Lives Matter, since both stories have dominated the threat landscape over the last several months, but this is something that organically happens frequently on the threat landscape. So much so that organizations should include it in their threat hunting activities. This blog is going to walk through the why and how.
Current events as lures
For as long as adversaries have been trying to lure users to infecting themselves, they've been leveraging current events. This can take lots of forms and sometimes can be calendar-based. These include things like tax season, holidays and shopping events like Black Friday. Every year, we see this type of activity spike around these respective events. This isn't just a U.S.-focused event, either. In the past, we've covered tax scams that targeted a wide array of countries in both North America and Europe. In some cases, these scams were in the native language but, as is usually the case, the majority were in English.
These annual events are things that security organizations will see regularly, and therefore should be prepared to handle. This would include processes and procedures around hunting these threats and how to prepare employees with training prior to applicable periods of activity.
There is a second class of lures that are being used effectively and they are tied to what is going on in society today. Right now, that is overwhelmingly tied to two things: COVID-19 and racial injustice. Both are global news stories that touch virtually everyone on the planet — a reach that wide and effective is impossible for criminals to ignore, and cyber criminals are no exception. Over the last several months, virtually every threat Talos has written about has used COVID as a lure in one campaign or another. This isn't restricted to just crimeware or financially motivated malware. We've also seen it used in more targeted attacks such as PoetRAT. This shows how effective this can be as a lure. Early in the pandemic, we covered how quickly we saw adversaries move to coronavirus lures and now we've seen most commodity malware families be delivered using COVID-19 or coronavirus effectively.
These lures tied to events as they happen are difficult to anticipate, but security organizations need to have procedures in place to handle these shifts, ideally flexing the list of words and events used in hunting based on current events in the news. Let's start by running through some use cases from the last several months that touch on not only COVID lures but also tax season and racial injustice.
Recent case studies
PoetRAT
PoetRAT is a remote access trojan that Talos discovered earlier this year. This RAT was being delivered with a wide variety of lures, one of which you can see below.
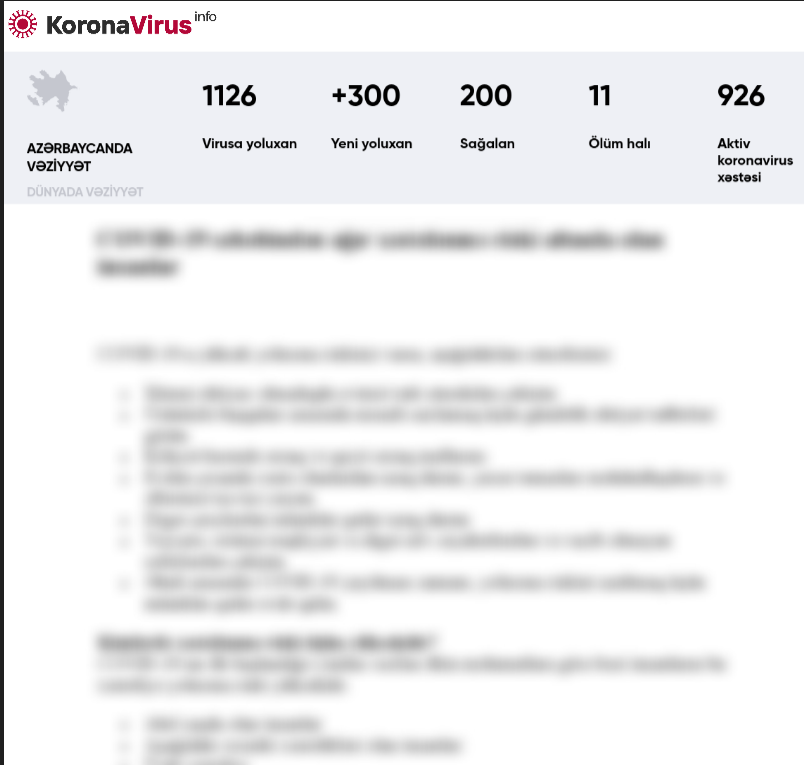
This was an example of the coronavirus-themed campaigns we uncovered. There are multiple reasons to cover this specific threat and the first is it's a targeted attack. Specifically, it targeted citizens of Azerbaijan. Despite this being a targeted attack, we still find lures tied to COVID and coronavirus. Another interesting aspect is it shows this is not an English-focused vector, as this campaign is in the native language. One common misconception is that current event lures are only used by commodity actors. But we know all actors from small criminal organizations to state-sponsored actors have used, and will continue to use, current event lures. The reason is they are effective — plain and simple.
This threat has some unique characteristics one of which is the RAT payload is embedded in the word document itself. For more details on how PoetRAT operates and our detailed technical analysis, click here.
Astaroth
Astaroth is a highly sophisticated stealer that has been seen exclusively targeting Brazil. Astaroth is best noted for its high level of evasion, anti-analysis checks, and techniques that are being used. This is a malware family that has been delivered inside of Brazil, using a variety of lures including coronavirus, shown below.

This campaign was purporting to be part of the Brazilian Ministry of Health and provides users with what appears to be recommendations around what protections were put in place for coronavirus. This is primarily a financially motivated or crimeware threat that was targeting Brazilian banking credentials. This again shows the global reach of these lures, as these emails are written in Portuguese. For full details on how Astaroth operates and the evasion and anti-analysis technical analysis, click here.
Trickbot
Trickbot is a widely distributed modular banking trojan that we have covered extensively in the past and was historically associated with some of the Ryuk ransomware campaigns. It is commonly delivered via malspam and as an additional payload via other malware variants. The example related to Black Lives Matter has been pretty widely covered. However, below is one of the examples of this campaign. As you can see the body is pretty simple and there is an XLS or DOC file attached depending on the version of the campaign you are analyzing.
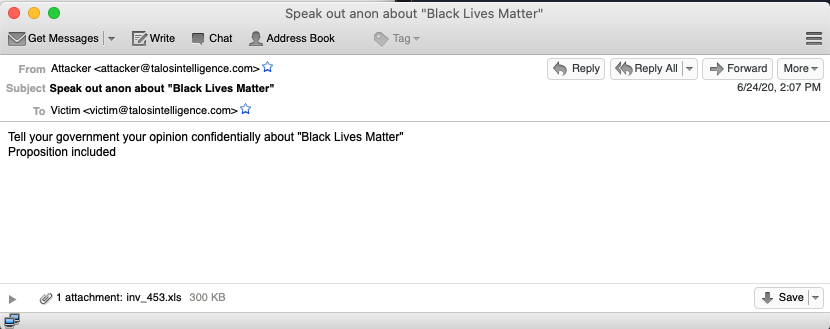
Once a user opens the attached spreadsheet, they are presented with a blurry image we commonly see associated with macro-based malspam. One thing that makes this slightly different is there isn't any information regarding enabling macros or content and only has a print button on the document. As you can see if a user clicks the print button a fake error pop up is triggered. In the background Trickbot is being downloaded and executed on the system, compromising it.
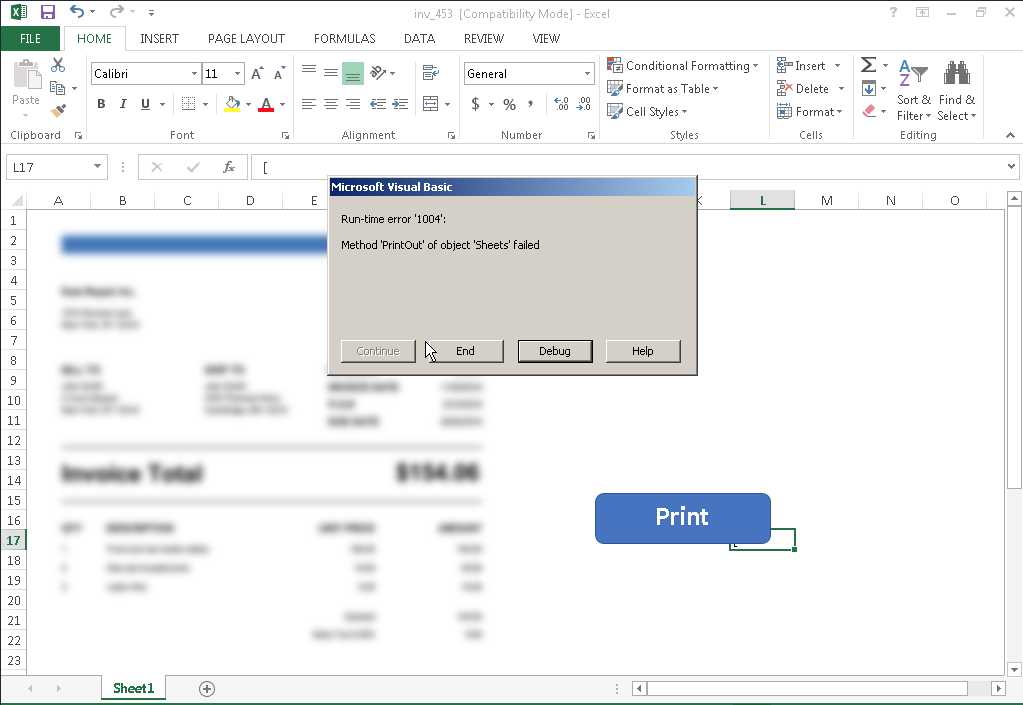
This is yet another example of how we see commodity malware taking advantage of whatever current event is top of mind for their potential victims. By keeping the lures fresh the adversaries can continue to successfully deliver their malware payloads to unsuspecting victims.
There are a couple of hunting avenues an organization could take to find these types of emails. First would be searching the subject lines looking for keywords. Additionally, you can search the bodies of emails for the same keywords to widen the search. In this instance, either option would have returned this result. Finally, searching for attachment names for the target keywords is paramount. Casting a wide net around potential hunting locations will likely net you the best results. As you can see in this example, searching on the subject and body would have had a positive result, but searching on filename alone would have missed the attempt.
Lokibot
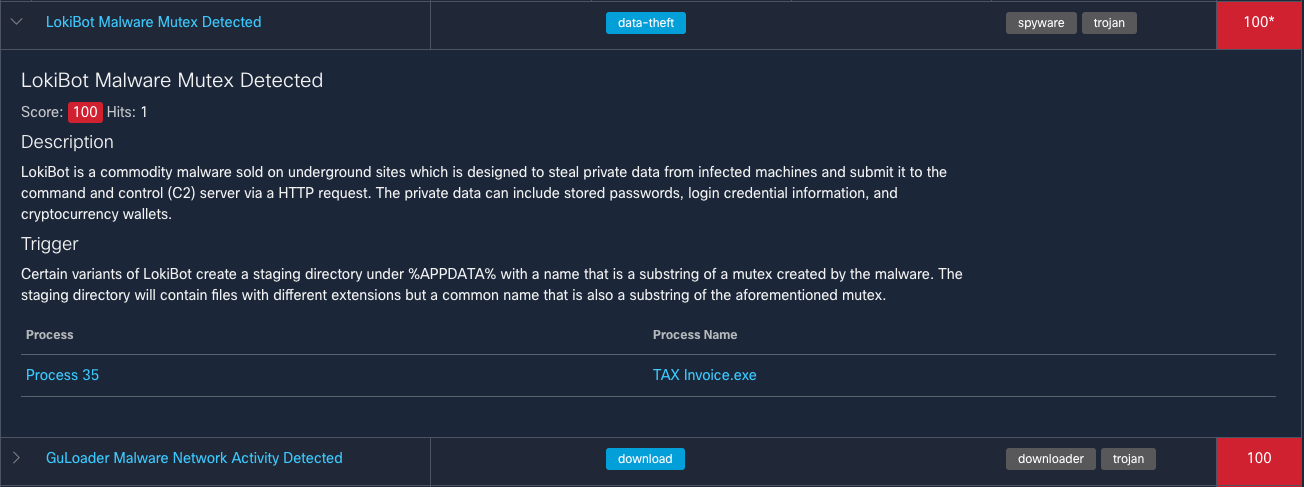
Lokibot is a widely distributed commodity stealer that we've covered on multiple occasions in the past. It is commonly distributed via malspam campaigns using various lures. A few days ago, we identified a campaign that was leveraging a common current event lure, taxes. Despite many tax lures revolving around the actual tax season, there are also campaigns that run periodically related to taxes.
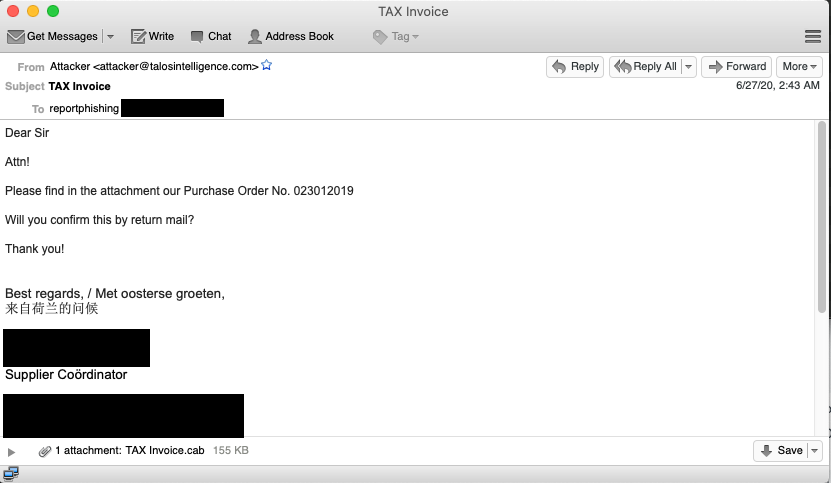
The example shown above has a .cab file attached that contains a single executable (TAX Invoice.exe). When executed on the system, the file leverages GuLoader to drop Lokibot, infecting the end system. One thing of note for this year, at least for the United States, is the extended window of tax season. Due to COVID-19, tax season was extended by several months to July 15 and, as such, the period where adversaries may use tax lures is going to increase.
Crimeware campaigns
There is such a wide variety of English language-based crimeware campaigns tied to coronavirus that we wrote an entire blog around it. At this point, it would be more difficult to identify the commodity malware campaigns that DID NOT use coronavirus as a lure than listing the ones that have. We've analyzed campaigns related to Nanocore RAT, Emotet, and random wipers. For the full details of some of the campaigns we've seen, click here.
The examples have primarily focused around COVID-19 largely because that is most of the activity we are seeing. That is not to imply that this is the only lure that exists or will be used. During various other times of the year, we will see these campaigns kick up as news events break around the world. However, because COVID-19 is such a unique lure we went so far as to write-up some of our recommendations in this threat landscape. Now, let's focus on how we can take the knowledge that attackers will leverage current events and operationalize them.
Operational impact
Current events are something that security organizations need to be prepared to face. There are a number of ways that organizations can handle these tasks and one of the most basic is user education.
Organizations are well served to send reminders to employees educating them about the types of lures they are facing. Examples of this could be sending out an email before tax season reminding employees that you should be skeptical of any documents or links that are purporting to be related to taxes. These types of simple training emails can reduce the effectiveness of these lures on your enterprise. Additionally, consider sending out supplemental notices when sudden current events emerge like the current COVID related lures you will see now. Currently, organizations are trying to communicate with their employees in a variety of ways. It's important these organizations include security messaging as part of this.
The other ways in which organizations need to prepare center around security operations and tasks those teams should handle. The first thing is working on identifying what events do you commonly see adversaries leveraging:
- Do you commonly get tax emails, or do you receive a higher volume of emails around sale periods like Black Friday?
- How many of your incidents in the last four months can be traced back to a lure related to COVID or Coronavirus?
- Going back historically, look at incidents that were tied to current events and see if patterns start to emerge.
- Start building a list of these events or terms, keeping in mind some of the events may be vertical or industry-specific. Once you have a solid list of current events you are wanting to track, then you need to make that information useful to operations. There are a couple of different ways this can be done, but you could start by building these keywords into hunting activities. Analysts should be pouring through your internal telemetry looking for indications of these types of attacks and running them down, whether they are successful or not. For most organizations, focusing on basic security tenets and implementing best practices may yield far better results, as this type of operationalization of data is likely more suited for mature security teams.
The primary attack vector for these types of attacks remains to be email-based. Therefore, one of the most important protections an organization can have in place is some form of email security. These technologies can do things like preventing malicious attachments from hitting inboxes and, in some cases, can run unknown files in sandbox environments to try and limit the exposure of the end-users to malicious content. Ensuring that your organization has some email security implemented and it is configured correctly to maximize its effectiveness is paramount to your success in this space.
Absent email-based security, the other key technology to leverage for these attacks would be endpoint security or anti-malware protection. This is the final line of defense for most organizations and is key to preventing users from successfully infecting the system based on these lures. In an ideal world when a user furthers the infection it is quickly stopped by your endpoint solution and analysts are alerted to the activity.
Another thing organizations can do is build alerting or detection frameworks that involve these current events, including leveraging various threat intelligence feeds. Make sure you are tracking those keywords in things like emails or messaging platforms. Build logic into your SIEM to alert when you see potential lures related to these current events. Obviously, these tasks can see relatively high false positives, but it's an opportunity to train junior analysts on the processes for investigations as well as a chance for you to work with the potential victims to educate them of the threats that they face.
Taking this a step further, if the organization is maintaining an active list of the groups and threats that target your organization, start tracking for when they switch tactics. Use your existing threat intelligence to identify those groups that are potentially targeting you. As they pivot and move you should be able to stay ahead of any new lure-based attacks by handling detection further down the infection path. As discussed previously this type of intelligence work would likely only be undertaken by those with a more mature security organization.
Finally, organizations should use these same types of tactics when conducting testing. This can include things like phish tests or the more aggressive red teaming tasks that organizations are increasingly implementing. By including several current event lures, you can both evaluate how well you are prepared to handle these incidents and how well your messaging is working around educating the users. Keep in mind that these tend to be polarizing topics that result in strong emotional responses to the content. Using these as lures in an environment can result in the same reaction from your users. It's the reason the bad guys are using them and you should ensure that all levels of management are aware of the plans and approve, before moving forward.
Taken together these steps can really help drive down the success rate of these types of attacks and hopefully improve the overall operational security of your users, by educating them about the lures they are going to face and testing that they have actually listened to the message.
Conclusion
Adversaries are always working to find the best, most effective way to compromise systems and increasingly, that relies on the user. As such, these miscreants are constantly working to try and find the most effective lures to get users to infect themselves. Current events will always be a vital part of the threat landscape and something that organizations should have procedures and processes in place to help mitigate.
Security teams big and small should be working to help mitigate the threat of current event lures, on relatively regular intervals. Including it in your training and ongoing user education is paramount. Sending an email warning your users of attacks leveraging a specific lure, may stop some users from getting infected, or might get them to report something that already happened.
However, there are many other areas that organizations need to leverage to help mitigate these threats. This includes proactive hunting exercises using these keywords as anchors. Set out to hunt through your internal telemetry and find the threats that both succeeded and failed. Use them as content for your ongoing education and show users the common ways these things can be abused by adversaries.
Finally, for more mature security organizations, try to leverage these current events against your own users. Have your red team start focusing on running current event-based campaigns using things like email and messaging platforms and report the results back up through the management chain. As you continue to routinely run these campaigns you should be able to track how your training and education is improving your success rates, or not. The point is that if you ignore these lures you are doing your organization a disservice. These lures are going to continue and the sooner you start making that part of your operational security plan, the better suited you will be to avoid a catastrophe.