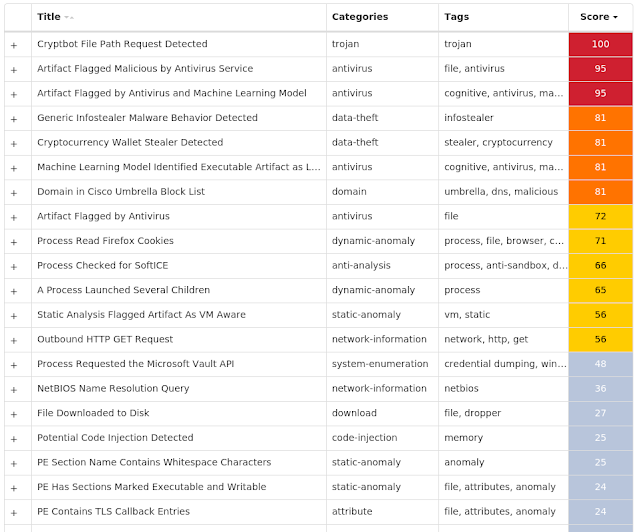
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 17 and July 24. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Formbook-8866958-0
Dropper
Formbook is an information stealer that attempts to collect sensitive information from an infected machine by logging keystrokes, stealing saved web browser credentials, and monitoring information copied to the clipboard.
Win.Dropper.Tofsee-8964103-0
Dropper
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control.
Win.Worm.Socks-8977376-0
Worm
Socks is a generic worm that spreads itself via autorun.inf files and downloads follow-on malware to infected systems.
Win.Dropper.HawkEye-8997282-0
Dropper
HawkEye is an information-stealing malware that specifically targets usernames and passwords stored by web browsers and mail clients on an infected machine. It is commonly spread via email and can also propagate through removable media.
Win.Dropper.Ramnit-8988791-0
Dropper
Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also has the ability to steal browser cookies and attempts to hide from popular antivirus software.
Win.Malware.Cryptbot-8991879-1
Malware
Cryptbot is an information-stealing trojan that attempts to siphon passwords and other credentials on an infected machine. It typically masquerades as legitimate software to trick users into installing it.
Threat Breakdown Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\INTELLIFORMS\STORAGE2
26
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX
26
<HKLM>\SOFTWARE\WOW6432NODE\MOZILLA\MOZILLA FIREFOX\20.0.1 (EN-US)\MAIN
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676\00000001
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676\00000002
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9375CFF0413111D3B88A00104B2A6676\00000003
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\0A0D020000000000C000000000000046
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\13DBB0C8AA05101A9BB000AA002FC45A
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\33FD244257221B4AA4A1D9E6CACF8474
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\3517490D76624C419A828607E2A54604
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\4C8F4917D8AB2943A2B2D4227B0585BF
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\5309EDC19DC6C14CBAD5BA06BDBDABD9
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\82FA2A40D311B5469A626349C16CE09B
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\8503020000000000C000000000000046
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9207F3E0A3B11019908B08002B2A56C2
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\9E71065376EE7F459F30EA2534981B83
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\A88F7DCF2E30234E8288283D75A65EFB
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\C02EBC5353D9CD11975200AA004AE40E
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\D33FC3B19A738142B2FC0C56BD56AD8C
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\DDB0922FC50B8D42BE5A821EDE840761
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\DF18513432D1694F96E6423201804111
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\ECD15244C3E90A4FBD0588A41AB27C55
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS MESSAGING SUBSYSTEM\PROFILES\OUTLOOK\F86ED2903A4A11CFB57E524153480001
26
Mutexes Occurrences 8-3503835SZBFHHZ
26
8PL479TAXGU0FHAZ
26
S-1-5-21-2580483-10283421113525
24
S-1-5-21-2580483-15841774155802
5
S-1-5-21-2580483-17201774155802
4
S-1-5-21-2580483-19521774155802
3
S-1-5-21-2580483-17841774155802
2
S-1-5-21-2580483-20401774155802
2
S-1-5-21-2580483-19161774155802
2
S-1-5-21-2580483-6361774155802
2
S-1-5-21-2580483-19321774155802
2
S-1-5-21-2580483-17081774155802
1
S-1-5-21-2580483-12601774155802
1
S-1-5-21-2580483-3281774155802
1
S-1-5-21-2580483-7241774155802
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 63[.]250[.]47[.]83
23
34[.]102[.]136[.]180
11
194[.]36[.]166[.]10
10
184[.]168[.]131[.]241
8
199[.]59[.]242[.]153
8
51[.]75[.]108[.]121
8
13[.]52[.]160[.]194
7
185[.]230[.]60[.]96
6
89[.]46[.]105[.]38
5
193[.]46[.]197[.]109
5
151[.]101[.]192[.]119
5
141[.]8[.]225[.]75
4
23[.]20[.]239[.]12
4
66[.]235[.]200[.]3
4
162[.]241[.]244[.]34
4
210[.]224[.]185[.]225
4
23[.]234[.]27[.]100
4
86[.]104[.]44[.]39
4
198[.]54[.]117[.]210/31
3
23[.]231[.]239[.]10
3
104[.]27[.]174[.]249
3
204[.]79[.]197[.]200
2
185[.]230[.]60[.]211
2
198[.]49[.]23[.]144/31
2
209[.]17[.]116[.]160
2
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences www[.]glamotd[.]com
23
api[.]w[.]org
12
gmpg[.]org
12
www[.]astonfly[.]info
10
www[.]theclippersofficial[.]com
10
www[.]stoxcrypto[.]com
10
www[.]novaeramotoboysportoalegre[.]com
9
www[.]intera-canada[.]com
9
www[.]fristcreditunion[.]com
8
www[.]mysticadventuresails[.]com
8
browsehappy[.]com
7
www[.]startboostcapital[.]com
7
www[.]methvenonthemove[.]com
7
www[.]joshkaeding[.]com
7
www[.]cloudyans[.]com
7
www[.]gtitdunproductions[.]com
6
www[.]annualtransmission[.]technology
6
www[.]theedgebizconnect[.]com
6
www[.]myweddingbeautiful[.]com
6
www[.]pepper[.]guide
6
www[.]q83pfq[.]biz
6
www[.]azasianow[.]com
6
www[.]xnyppw[.]com
6
www[.]mannionexpertseniorcare[.]com
6
www[.]www750456[.]com
6
*See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%\Microsoft\Windows\WebCache\WebCacheV01.tmp
26
%APPDATA%\8PL479TA
26
%APPDATA%\8PL479TA\8PLlog.ini
26
%APPDATA%\8PL479TA\8PLlogim.jpeg
26
%APPDATA%\8PL479TA\8PLlogrc.ini
26
%APPDATA%\8PL479TA\8PLlogri.ini
26
%APPDATA%\8PL479TA\8PLlogrv.ini
26
%TEMP%\DB1
24
%APPDATA%\8PL479TA\8PLlogrf.ini
24
%APPDATA%\8PL479TA\8PLlogrg.ini
24
%TEMP%\Kwnuxv4rh
2
%TEMP%\Kwnuxv4rh\certmgrg0h.exe
1
%ProgramFiles(x86)%\Mox4\taskhost1b5x.exe
1
%TEMP%\Mox4\taskhost1b5x.exe
1
%ProgramFiles(x86)%\Hylu8\updatebbp.exe
1
%TEMP%\Hylu8\updatebbp.exe
1
%ProgramFiles(x86)%\Byjop\confignnul.exe
1
%TEMP%\Byjop\confignnul.exe
1
%ProgramFiles(x86)%\D_nu0\wincx58f.exe
1
%TEMP%\D_nu0\wincx58f.exe
1
%ProgramFiles(x86)%\Tpjst4zi\configzxqlgb.exe
1
%TEMP%\Tpjst4zi\configzxqlgb.exe
1
%ProgramFiles(x86)%\Kwnuxv4rh\servicesg0h.exe
1
%TEMP%\Kwnuxv4rh\servicesg0h.exe
1
%ProgramFiles(x86)%\Xdbcpkzi\gdijv1hb.exe
1
*See JSON for more IOCs
File Hashes 00a0094d11c7ce21216f479dbc3b37df812f46eecb7a8baa10dceeff8b7fc864
0d1259096242c800bb9b2b5dd036582036685e83b6d9347b7ed9df522be20805
0e6172900041e5025a6001500f9aa12998b8dd75641f6f7950a21c8e0fb516b3
1361c2b2d05259699ae35fbadb6f6e3083b2c375fd2f6f64caff31651b2321ba
15bd77b74ca028f72d350e87f18062d63eb6fee6aec65775f5e24862cef225d1
2ad3d8e923074c817424cbaaa4472ea3b8e47b4fd675b78a9d4b0b352fbf35b6
39458342b048fc5370f6067fdbd643389e4224ce975b823666ca1e85da787312
3c05af41a392ad8969df9d9e20d2a9f01efc8e46ac605872cdee2ef708b7be60
3c63a1e1d5b46b6bd9dfb2c51bb08b6adccf0d15b84251c3e4ddbc05c7e6be9d
3fad736a2fc7451753a963916f4e4905b24b513254e53f63e6c036f080cb10b1
402b4871f364293d14b55f5cfe75aa0e4d76c38d480d83877c2be96724678686
4281e69f6ac697ad7387167118c6d9a8a6fc347df56fe19d11535c61a3040f9c
5e1c2460cd6027332f8db798a30501aa899379f67136189f6fec75cbb376925f
638bb5dc4d10ed89a33b8fa09d058a0b9e28dfac6795b91b73dc0d1abd93dfde
72e72e8daaf16cf30e2526304f288e1cbb43c3ec8be3b8614bd7775e72762a24
7342ca1d5c98e486168bd2dab2f638770015a36e79c7268072c1ea15bd1ac64d
855deaea6afba9dc1e12a95a5f7f6e59a678369332d269c4d65d457c18b77ee2
943f26c1fdebfaf93bbf41209c930911a2560338858602ed5947fe507b5514e2
aec0796263f2a23f0f6d2350ef57cd3ffc633f46be9f4bb20e17b749e701370b
b65cdfbd27bdf43688145b400a28fe90cd85682a6860907f5c727c763d8e6ebe
cff693dfc81698f2f5f2fa9c14fd0ce225a417e72dbdaf8a9c5c81701d81a75d
d4277a4c78adcc0813346bf30d61e9b8f27c0b8448db0f38cb024d79d74afbf6
d63470edb6e570d779a965d33fcb6bbf5115912e8942752f5d4bc3156933f93c
db93564a03edf3774d2d9f33df9a2dc76e3d8b235e631907fc8f425e2d055b0b
f5a3917eda90a6b22edd559c5db6112cfb7039f300071145fe4cbe8dbd1f8e36*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Dropper.Tofsee-8964103-0 Indicators of Compromise IOCs collected from dynamic analysis of 35 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
22
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
20
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
20
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
20
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
20
<HKCU>\SOFTWARE\MICROSOFT\A1890984
Value Name: PatchTime
5
<HKCU>\SOFTWARE\MICROSOFT\A1890984
Value Name: PGDSE
5
<HKCU>\SOFTWARE\MICROSOFT\A1890984
Value Name: GPU
5
<HKCU>\SOFTWARE\MICROSOFT\A1890984
Value Name: Servers
5
<HKCU>\SOFTWARE\MICROSOFT\A1890984
Value Name: CDN
5
Mutexes Occurrences (null)\69884752-95BE-4032-8AF1-B300F0E2CB97-Mutex
7
Global\SetupLog
5
Global\WdsSetupLogInit
5
Global\h48yorbq6rm87zot
5
Global\Mp6c3Ygukx29GbDk
5
Global\ewzy5hgt3x5sof4v
5
Global\xmrigMUTEX31337
5
WininetConnectionMutex
5
1dc907539dc8fc57e6b3cbf1a276ccce
5
Global\1dc907539dc8fc57e6b3cbf1a276ccce
5
25ba6ebb3e470993540ebc62e98a51e2
5
Global\25ba6ebb3e470993540ebc62e98a51e2
5
<random, matching [a-zA-Z0-9]{5,9}>
5
\Sessions\1\BaseNamedObjects\Global\h48yorbq6rm87zot
4
FstCNMutex
3
GJLAAZGJI156R
3
I-103-139-900557
3
J8OSEXAZLIYSQ8J
3
LXCV0IMGIXS0RTA1
3
MKS8IUMZ13NOZ
3
OLZTR-AFHK11
3
OPLXSDF19WRQ
3
PLAX7FASCI8AMNA
3
RGT70AXCNUUD3
3
TEKL1AFHJ3
3
*See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
20
43[.]231[.]4[.]7
20
69[.]55[.]5[.]252
20
85[.]114[.]134[.]88
20
217[.]172[.]179[.]54
20
5[.]9[.]72[.]48
20
130[.]0[.]232[.]208
20
144[.]76[.]108[.]82
20
185[.]253[.]217[.]20
20
45[.]90[.]34[.]87
20
157[.]240[.]18[.]174
16
104[.]47[.]54[.]36
13
83[.]151[.]238[.]37
13
209[.]85[.]201[.]104/31
12
12[.]167[.]151[.]119
11
99[.]181[.]79[.]1
9
209[.]85[.]201[.]99
9
34[.]205[.]21[.]41
9
172[.]253[.]122[.]104/31
9
209[.]85[.]201[.]147
8
209[.]85[.]201[.]103
8
104[.]47[.]53[.]36
7
209[.]85[.]201[.]106
7
216[.]239[.]32[.]21
6
66[.]171[.]248[.]178
6
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences microsoft-com[.]mail[.]protection[.]outlook[.]com
20
252[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
20
252[.]5[.]55[.]69[.]in-addr[.]arpa
20
252[.]5[.]55[.]69[.]bl[.]spamcop[.]net
20
252[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
20
252[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
20
252[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
20
schema[.]org
12
119[.]151[.]167[.]12[.]in-addr[.]arpa
11
ip05[.]gntl[.]co[.]uk
11
tube[.]pool[.]gntl[.]co[.]uk
11
video-weaver[.]hel01[.]hls[.]ttvnw[.]net
9
auth[.]api[.]np[.]ac[.]playstation[.]net
8
lh3[.]googleusercontent[.]com
6
vsblobprodscussu5shard60[.]blob[.]core[.]windows[.]net
5
vsblobprodscussu5shard35[.]blob[.]core[.]windows[.]net
5
www[.]sendspace[.]com
5
api[.]sendspace[.]com
5
gfixprice[.]space
5
ordinarygame[.]site
5
s2[.]ipinfo[.]pw
5
iv0001-npxs01001-00[.]auth[.]np[.]ac[.]playstation[.]net
4
www[.]google[.]com[.]au
4
e6355[.]b[.]akamaiedge[.]net
4
ip[.]pr-cy[.]hacklix[.]com
4
*See JSON for more IOCs
Files and or directories created Occurrences \Device\ConDrv
22
%SystemRoot%\SysWOW64\config\systemprofile
20
%SystemRoot%\SysWOW64\config\systemprofile:.repos
20
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
20
%System32%\config\systemprofile:.repos
20
%TEMP%\<random, matching '[a-z]{8}'>.exe
20
%System32%\<random, matching '[a-z]{8}\[a-z]{6,8}'>.exe (copy)
18
%LOCALAPPDATA%\Microsoft\Windows\WebCache\WebCacheV01.tmp
7
%SystemRoot%\Logs\CBS\CBS.log
5
%SystemRoot%\rss
5
%SystemRoot%\rss\csrss.exe
5
%TEMP%\csrss
5
%TEMP%\csrss\dsefix.exe
5
%TEMP%\csrss\patch.exe
5
%System32%\drivers\Winmon.sys
5
%System32%\drivers\WinmonFS.sys
5
%System32%\drivers\WinmonProcessMonitor.sys
5
%SystemRoot%\windefender.exe
5
%TEMP%\Symbols
5
%TEMP%\Symbols\ntkrnlmp.pdb
5
%TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02
5
%TEMP%\Symbols\ntkrnlmp.pdb\9E22A5947A15489895CE716436B45BE02\download.error
5
%TEMP%\Symbols\pingme.txt
5
%TEMP%\Symbols\winload_prod.pdb
5
%TEMP%\Symbols\winload_prod.pdb\B7B16B17E078406E806A050C8BEE2E361
5
*See JSON for more IOCs
File Hashes 048fa8555de0792fc219580672e896ea3945de1f90f09910a3166e307825edc0
08d57e06535cd452f061aff0eefd2dc8ea88ce60630fca365efbc95a5eee8007
08ecec4c732190e56000173c05210bfa300053916246d3a3f11ad10965260b14
0cdec5533004f71f78b19346292438aae43ba146e3152982a8b21783d466f74e
11416b9fce27d1d0a11ba8ceb4fa0132861c2a050fccff4b3a64b0278c016576
3f8a044ff54c10f96ac46ba48203fe4aa6e9a6b4ee2b81ec5fd8611c215efb48
4141cfb28e05e048e10924157ba8daf94c858dc2d5207d04a6792a961a78c80b
4acb44a8ba011dc5aed1ab037506c51cb943fb722bd682dce35020ac03b9f07d
4e2a6d003590bbdbde4f912aa9bf0f0450e3e68a241d1f29c7259b003580eaf6
4efc60638df5e3c46aa8de0bfa3d9677898c4bf705a9c0eec36183a271662876
59f0d8b3450d9caa89f1b3954587c5a1986375f867dd16709a2309293e30f09a
6a5624f3bac8dea8ba1e75d7a0b3cfffe08ff68fce1ca335e435492c654b9f87
7a91c94a0161eb50cad7446f42e96d4f3c6c43ad2ed9bec4af3817184dd2c106
83db79b4a01382653496ed19fe36f0d8dcdbb4b0c58b22a751806c161f8bfe9f
8f3e31759ed8a358d0706dbb59cbc3f984e14b122cf2d284572e535c885115e7
96f5ecab2a4f688eb3062a507f771dd9a548cdb06b804c1f0d94587cf3a3dafb
978b002cb763f1c52cbc776f2f12a630fedf86682edebfebeeec20f00ceea781
9dbe3b532d0d4b1ae06ee92a8ae4d0e344f0c088502508a270769d2ebdbe8a2d
aa8b89d47a629c5939047f0b3bb0c220e7d5bcdfa5f76b2ee5a62d586257c3ca
b03458e88ffc5f4cbd998284d2eabcbb815b47c309c7aefef1fe45695f387dbb
be2c8e761c1f27e139e9abeae0a8fc3fbeda1e5598b354f2390f182a7f08ea45
ced17b2923a4007955d26395bb1a53d0dafe27900f72e94489c492ac22d7d173
cfc1d5b68437f46c72dc2dbf9aa12322307e066dbc3bc74d49750fe75c830eab
d0eea3587e65ee8925d44b5add80fcca787608e1902a6250139c3145e21b103a
d49281327943efe38097e5ba85a483d15478488cf13ffabc8c6ffab30b66b00a*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
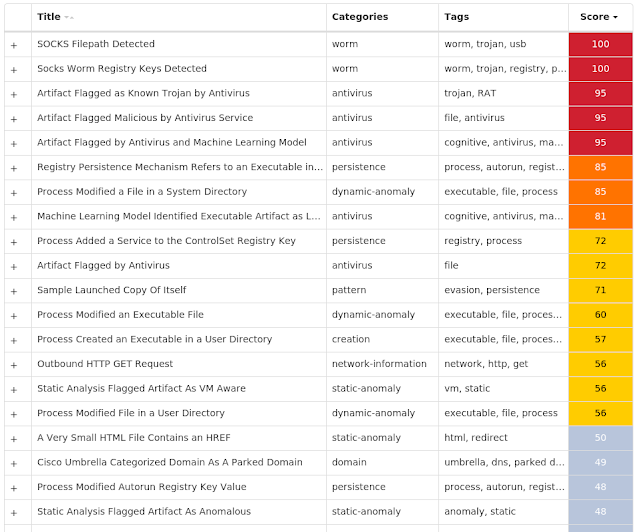
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Worm.Socks-8977376-0 Indicators of Compromise IOCs collected from dynamic analysis of 218 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntuser
218
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE
Value Name: ImagePath
218
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ntuser
218
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: autoload
218
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: autoload
218
Mutexes Occurrences z111xc
218
z3sd
218
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 23[.]20[.]239[.]12
218
204[.]79[.]197[.]200
2
Domain Names contacted by malware. Does not indicate maliciousness Occurrences fewfwe[.]com
218
www[.]hugedomains[.]com
203
Files and or directories created Occurrences %SystemRoot%\SysWOW64\drivers\spools.exe
218
%LOCALAPPDATA%\Microsoft\Windows\WebCache\WebCacheV01.tmp
218
%HOMEPATH%\Local Settings\Application Data\cftmon.exe
218
%HOMEPATH%\ftpdll.dll
218
%SystemRoot%\SysWOW64\ftpdll.dll
218
%LOCALAPPDATA%\cftmon.exe
218
%SystemRoot%\SERVIC~2\Local Settings\AppData\Local\Temp\MpCmdRun.log
21
File Hashes 001957ffcab5266760b3557afa7a077d8b166354deb1c0a44bcb264a51a7fd5a
00ad3bc9ef01f7062fdd56c88455cc424e0d628a60af7c828818210f75e87ab8
03d3565ffb95c782d784799dc25fabaa40305656bd4ac8eaec8e9755b53e3db9
03d70bae1fed6adc499a2039b0c2a54f319f1418b22dcf0eb83e3899e84eb272
04c5d2c156f483aaeb8b7f139a820fe44a865561d2e72e349a6db382935b11af
057d3d93f01f47d7dfb6929d228b326dde57cd93f792eb2a3f8f05a79095fa27
06fafb59c893ec6f4e54605d4a0ab8d18b650ba9bd673c01b0185234247756e6
08855770401430c9cd45ddcfffed68d3a6d3998f6f1e9ba72a6383f76a4e1c0b
09061b24f2719f33ee7070dc2558ba0660b9296b1f62bcfe3896743d73ba6798
098bb8c5041ca9a7b3d2d7847ad6f04ab4d7a487a33993eea919fa7158552bf6
0aae1649239311b00fff8b50d3a93f31ded9a3e003d22d94c6644239d6b65854
0e30ad29a435dd37ae615a090f7517f1a41c01af8c52e8573a7c62256b19d5eb
0ec334ca11c86430dc8926cf88370624f2056fa33d4d7875a02d8b20951a4ecd
0f5d29b145207fa49116f998b7f38feda1adebeebb9b9d3176179ff5b591440e
10a173525f1891752207500e31969d70b9b3aba4fac5ae9a9b4bb0186081cad9
10f8ffc5b80c5b1054240fe2141133616d9886a7476348618ccfbaf36bde6384
11672fcb6691791d1e01b6ee3c2898dc1278b8cc5f000f45b9dd4b51400c432a
11b78d58598364f15f7002940c580bf4fb14cbbcd38184be12ce934e4c062f9d
12fdd75830bda17cbbc7897b592e315df8844d5b1036d5d7a940f87951c1e5c9
132cbbb6f60b13ae62af80331061c2e9015e27e0bcbf38e76ebe77bbc9bd989f
133088aebb720a8334fcd037f29c55b40dbcd3c7e9fe16ed4e15aa1900837fc0
14b6f8d982557eb3e9a371b78f61795a3309fd6704116d84aae331dc2f2b442c
14e36b503e2f1709d488d52870fedacfb8658748e44def4a594127ac6ead0bf3
160a1061f5044d3345a9bb7dd7b52a904a212e8c54d0fd1d3a052f85632bed26
16f9d844fad95b50705ff36039e4d3c1458302acdd815ff90af90e95d9eea2b1*See JSON for more IOCs
Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
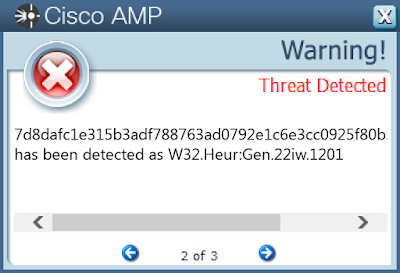
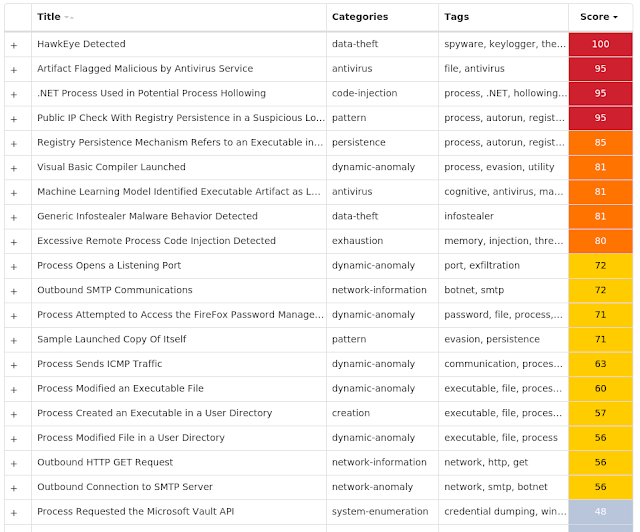
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Dropper.HawkEye-8997282-0 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: Hidden
7
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: Registry Key Name
3
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\75E0ABB6138512271C04F85FDDDE38E4B7242EFE
Value Name: Blob
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Update
1
Mutexes Occurrences Local\https://docs.microsoft.com/
2
Global\bbccd540-cb7c-11ea-887e-00501e3ae7b6
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]16[.]154[.]36
5
77[.]88[.]21[.]158
5
204[.]79[.]197[.]200
3
13[.]107[.]21[.]200
2
104[.]16[.]155[.]36
2
151[.]101[.]0[.]133
2
151[.]101[.]130[.]217
2
152[.]199[.]4[.]33
2
65[.]55[.]44[.]109
2
20[.]36[.]253[.]92
2
151[.]101[.]192[.]133
2
23[.]5[.]230[.]228
2
172[.]217[.]2[.]110
2
23[.]217[.]148[.]78
2
94[.]100[.]180[.]160
1
140[.]82[.]113[.]4
1
34[.]232[.]187[.]93
1
34[.]226[.]71[.]106
1
140[.]82[.]112[.]4
1
172[.]253[.]63[.]155
1
172[.]253[.]63[.]157
1
136[.]143[.]182[.]56
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com
7
smtp[.]yandex[.]com
5
prooemiac
3
schema[.]org
2
www[.]google-analytics[.]com
2
stats[.]g[.]doubleclick[.]net
2
github[.]com
2
avatars1[.]githubusercontent[.]com
2
az725175[.]vo[.]msecnd[.]net
2
aka[.]ms
2
avatars3[.]githubusercontent[.]com
2
developercommunity[.]visualstudio[.]com
2
cdn[.]speedcurve[.]com
2
w[.]usabilla[.]com
2
smtp[.]zoho[.]com
1
smtp[.]mail[.]ru
1
naszut4
1
spouter7
1
tonle
1
inseparable
1
overdignify
1
rafiq8
1
jovenes3
1
Files and or directories created Occurrences %APPDATA%\pid.txt
7
%APPDATA%\pidloc.txt
7
%TEMP%\holdermail.txt
7
%TEMP%\holderwb.txt
7
\Sys.exe
5
\autorun.inf
5
E:\autorun.inf
5
%TEMP%\SysInfo.txt
5
%APPDATA%\Windows Update.exe
5
E:\Sys.exe
5
%TEMP%\subfolder
3
%TEMP%\subfolder\filename.exe
3
%TEMP%\subfolder\filename.vbs
3
%LOCALAPPDATA%\Microsoft\Windows\WebCache\WebCacheV01.tmp
3
%APPDATA%\WindowsUpdate.exe
1
File Hashes 0d4e850f6a4dfa6dc74f8770d6293c37a2a1df3bcf8bbac8ed5eebd7041cdf2e
4496ce4c4eb7baa7ba7cac5a30d632db25143d89462ee4a885fbaf3752caec8d
5983ce394d98d07d267d563496f4d444eaeb17e5fd9d2dd517b92145598d27ec
5c2d0070ab7f93ddee20bbb6f38e60d994bcc3e256658c31a6ce8a033767a81e
7d8dafc1e315b3adf788763ad0792e1c6e3cc0925f80b5bde41509858470b432
88f75d07e5f0b4f18651380e891d02b4980de66351c97a7bd766a9e6065452d8
93b1a9aa9be7e72eaed6ba8de581f9e73020fe70f021912e2e3ec956bd5171d9
94a3fbed738a7683435d72e0082c6c56a8472fb289ecda7e93055d69fb7f0117
dcab4d6f0691ce5b507470e879ffb9abfbe4039a52ebe0f4d5293e901c53e458
f264c1d4f641bb0063a6760ac36dcf6df08f01398bdf013e70ce14bfeea0322eCoverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
WSA
N/A
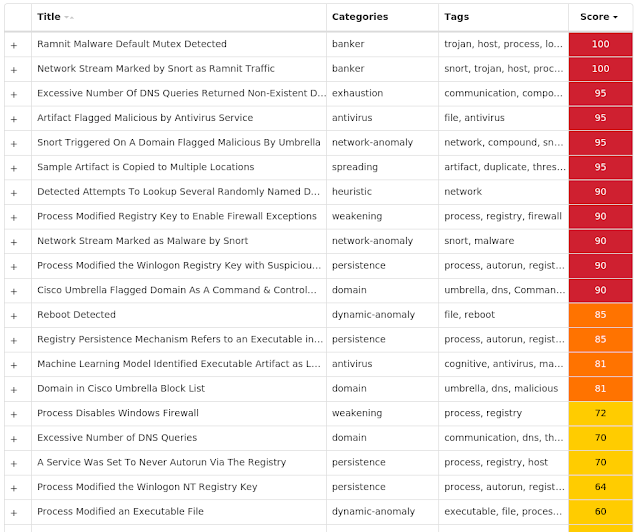
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Dropper.Ramnit-8988791-0 Indicators of Compromise IOCs collected from dynamic analysis of 23 samples Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusOverride
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallDisableNotify
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallOverride
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UacDisableNotify
8
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DoNotAllowExceptions
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION
Value Name: jfghdug_ooetvtgk
8
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: JudCsgdy
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: Start
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
8
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
8
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
8
<HKU>\.DEFAULT\SOFTWARE\CLASSES\LOCAL SETTINGS\MUICACHE\66\52C64B7E
Value Name: LanguageList
4
<HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\75E0ABB6138512271C04F85FDDDE38E4B7242EFE
Value Name: Blob
3
<HKCU>\Software\Microsoft\<random, matching '[A-Z][a-z]{3,11}'>
3
<HKCU>\SOFTWARE\MICROSOFT\IAM
Value Name: Server ID
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: aclutxml
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: parent.exe
1
Mutexes Occurrences \x7774\x616f\x766b\x6b62\x6866\x626b
23
{7930D12C-1D38-EB63-89CF-4C8161B79ED4}
8
Frz_State
3
Sandboxie_SingleInstanceMutex_Control
3
df7689e6-c49f-4a86-82e8-6809a406872a
3
<32 random hex characters>
3
Local\{31F7CC8D-DC06-8BF4-6EF5-D0EF82F90493}
1
Local\{73A713E4-3646-1D08-D857-CAA18C7B9E65}
1
Local\{C955B29C-9464-E306-E60D-08C77A91BCEB}
1
{FECD2115-459D-E06D-BF12-491463668D88}
1
{3686B563-1D48-D82A-57CA-A18C7B9E6580}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 172[.]217[.]7[.]174
10
208[.]100[.]26[.]245
8
35[.]225[.]160[.]245
7
72[.]26[.]218[.]70
7
217[.]20[.]116[.]137
6
195[.]201[.]179[.]192
6
37[.]220[.]31[.]41
3
195[.]201[.]179[.]207
2
208[.]67[.]222[.]222
1
217[.]20[.]116[.]138
1
217[.]20[.]116[.]140
1
172[.]217[.]7[.]142
1
80[.]211[.]164[.]74
1
176[.]53[.]118[.]122
1
3[.]18[.]65[.]24
1
139[.]59[.]85[.]151
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences lpkdvolbaca[.]com
6
uaseqxra[.]com
6
pdfueilv[.]com
6
fxejmhvyijoyxjcmly[.]com
6
jqibggawcw[.]com
6
wpaaihqbubcnmmrs[.]com
6
jxrlpxdwnpc[.]com
6
wsajnxcqredi[.]com
6
fajsnjrkxqdnuecblmg[.]com
6
dqbbdvdqayfhvvv[.]com
6
bvvimdtiuuceto[.]com
6
wsmkwcyfetd[.]com
6
mheaamwwb[.]com
6
ovfdnnqivoh[.]com
6
limyhsqxryqauxxcfkc[.]com
6
iyquaulnfx[.]com
6
urenesqsfqnugs[.]com
6
qkhrrpcreyq[.]com
6
eyarffmarxwm[.]com
6
djgtardir[.]com
6
lwbgroaagnnrevjm[.]com
6
umgrhdfoijvjn[.]com
6
mekgwuqaxakwwi[.]com
6
bqetqsrvrn[.]com
6
nuveqyhlk[.]com
6
*See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%\bolpidti
8
%LOCALAPPDATA%\bolpidti\judcsgdy.exe
8
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe
8
%APPDATA%\93547108
8
%APPDATA%\93547108\csrss.exe
8
%APPDATA%\93547108\csrss.exe:Zone.Identifier
8
%LOCALAPPDATA%\c0598c70215326fb56d5a33092df3c688d2c1a8b
3
%LOCALAPPDATA%\c0598c70215326fb56d5a33092df3c688d2c1a8b\container.dat
3
%LOCALAPPDATA%\c0598c70215326fb56d5a33092df3c688d2c1a8b\container.dat.tmp
3
%LOCALAPPDATA%\c0598c70215326fb56d5a33092df3c688d2c1a8b\fcb72db2-3076-4d18-be42-468add95d18d
3
%LOCALAPPDATA%\Microsoft\Windows\WebCache\WebCacheV01.tmp
2
%APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\prefs.js
1
\{5D9E0C27-180C-9720-0AE1-CCBBDEA5C01F}
1
%TEMP%\per
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\webappsstore.exe
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\parent.exe
1
%APPDATA%\Microsoft\Cicprov
1
%APPDATA%\Microsoft\Cicprov\api-draw.exe
1
%APPDATA%\96804751\csrss.exe
1
%APPDATA%\96804751\csrss.exe:Zone.Identifier
1
%TEMP%\upd9b628443.bat
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\Internet Explorer.exe
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\Music.dui
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\content-prefs.utq
1
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\desktop.tyi
1
*See JSON for more IOCs
File Hashes 06056e94b799f81695fb2f9175dd970027d5492faf40caaf943d0cd5b294099f
067b3cd1b068a83ace195fade2f015cb8b6d223c5e873fe12b4807ce523722b2
12b9cc6d62fdbfacff577022bef01922c62cc99a04b20fa700bb9f1ae279a8d8
1afe893aae8c764a9eaab06dc805d16d2ce185279b4e18467dda0fee37ef48a4
1e6a2f8c6f4dc130539c09057f103be2f93f12af85977d1d2f8c4d5640ce146e
25f0452d608d18b671d8f9d3d7b94bddd94d8265f35a95068bfe7d54053e7edb
34262cf747d821b6edce8286980b367c290663c3105da779d8af4f7381e609c6
3b40a6b6962aeff1c0ffe2562c57de86d0c55c5545e70a87c65be0cb9f71bef1
3c829ebb8347e074f1fee7a6398f586b2523cf728bdb7ab3e1d5f147a5d591be
3cd579592b9e6f86bd9276d48fb8ff553f567e7ceb792489de17406fdf6108ba
59739397835d75a78e69590fcb916ffc563f3943fcba62961e555a25152580d1
6960a764f20ce7baa46508a8b231c25047fc9ff79cfe9a7e3d803f1751fc194a
7543be2459a25cd65bbc5f1c5ce93146ab2830094c58cbf12e9a07099f8a8fe6
9090cfe08fa1cfd3b5af5343fdc3cb37eb33bc7a1a6a1303acab400c7e0de70e
90d2f7545fc3bb66d424a0f7132539aed354b4680aaaf693467245e53b439439
a0ef6e383e9dba6ad1e07f58e836c987acef9d538563e96ba2d5e6453d9dcf48
baf95ce5370f18a51f23d473df8c3ec161c00249fd76480074e11e3eaf7785ab
d16f881c9cb7dd6da4cd7646a13baaed31553a6f4ed5408e1bb850c7b34211e0
d6fb602c065740a922e1d4a7c67a50acbcfcf3cc58f4464e78fe26a2dbf52889
dacc9a5c1db7ed213bbd0c509d99d4ec2a83a5def1733849485ee7448c9074a6
ea26a14263f52e2c90410fc6d4aea9a2816659282443d5d99ebab1667f2049a9
f08af083ed36b451ddb9b5c44fed95d2107c690bb8c186afb5361240b48321b7
fb1529c46b1c0f29dbbdff4b7bc488a59f7ea20a1eb1a4e56109882aa3bb868dCoverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK Win.Malware.Cryptbot-8991879-1 Indicators of Compromise IOCs collected from dynamic analysis of 10 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 208[.]95[.]112[.]1
10
Domain Names contacted by malware. Does not indicate maliciousness Occurrences lerm04[.]info
10
ip-api[.]com
7
Files and or directories created Occurrences %LOCALAPPDATA%\Google\Chrome\User Data\Default\CookiesCopy
10
%LOCALAPPDATA%\Google\Chrome\User Data\Default\LoginDataCopy
10
%LOCALAPPDATA%\Google\Chrome\User Data\Default\WebDataCopy
10
%LOCALAPPDATA%\Microsoft\Windows\INetCache\IE\FNF9BE4O\line[1].txt
10
%ProgramData%\AxzkSfMRh4p4\US___2020_07_21___15_44___QE6bVOKN75eQhqTKLUoL.zip
1
%ProgramData%\AxzkSfMRh4p4\moz_cookies.db
1
%ProgramData%\pD6a2hXB7LDzBC\1723651.txt
1
%ProgramData%\pD6a2hXB7LDzBC\43561237N.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\CC_List.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\Cookies\MozillaFirefox_F7OZJjY.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\Cookies_List.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\Forms_List.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\Information.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\Passwords_List.txt
1
%ProgramData%\pD6a2hXB7LDzBC\Files\Screensh0t.jpg
1
%ProgramData%\pD6a2hXB7LDzBC\US___2020_07_21___15_41___oDXCZ3dBBRYRTKcq.zip
1
%ProgramData%\pD6a2hXB7LDzBC\moz_cookies.db
1
%ProgramData%\HP5iYyWrQmAdqOVk\1723651.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\43561237N.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\Files\CC_List.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\Files\Cookies\MozillaFirefox_komHeBY.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\Files\Cookies_List.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\Files\Forms_List.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\Files\Information.txt
1
%ProgramData%\HP5iYyWrQmAdqOVk\Files\Passwords_List.txt
1
*See JSON for more IOCs
File Hashes 00e1e236c747887543cccf20962ccd8de0cb5e4b3b9cfa52ea3610650efced31
1d480c6b93e963f1b69407fdcffbd9206702ee7b19acfdd3e8c80d8f1068ee1d
1ff359e37943658f48286551bf66c91a7e653358cbe285ece15a160367057913
9480baf6745ca47a0ca78aa4b795c70b6418d3470386e0a96aa9de1c7787a665
c693cba8320a572aea33c79b7554de9d5161bcf27edb12602081bc26cc9f3fb5
ce4476127d28aa62a4a5b378019ce51f5961f3043c2830cbabccf8f6201fe541
e562347adba7f3f67c52c15417730d9d8f9cc547d1dda4ef9a1efff173b609ff
e6c60ddf7694cc97cf37db1ddac4bbff54411ac51123e956f19c8fbe383a222e
eb650e5eae54aac2752e88be105b7bb29727c791dd03b7be6e64bc527225f49a
ed9de62bedaf93108c81b00b54969a13024f509462a9c97f0e99cb73fe66c902Coverage Product Protection AMP
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
WSA
Screenshots of Detection AMP ThreatGrid MITRE ATT&CK