Responsible disclosure of vulnerabilities is a key aspect of security research. Often, the difficulty in responsible disclosure is balancing competing interests - assisting a vendor with patching their product and notifying the general public to prevent a 0-day situation. It is uncomfortable to acknowledge that if a white hat team has discovered a vulnerability in a high value target, it stands to reason their adversaries may also be trying to exploit the same issue. Researchers must carefully balance the needs and capabilities of vendors to fix a product with the safety and security of our customers and the community as a whole.
Talos has been measuring the timelines, industry responsiveness, and end results with regard to our responsible disclosure policy and today, we are announcing a few changes. The full text of the Vendor Vulnerability Reporting and Disclosure Policy can be found here:
http://www.cisco.com/c/en/us/about/security-center/vendor-vulnerability-policy.html.
These changes include timeline adjustments based on vendor feedback and industry changes since we last addressed our Disclosure Policy.
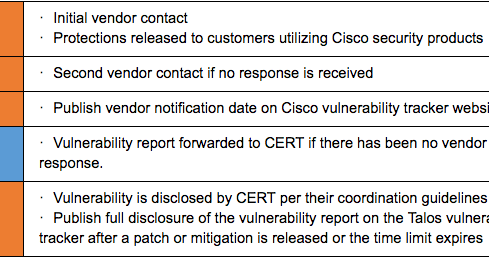
Timeline Adjustments Today Talos is announcing a timeline change in policy to reflect a 90 day disclosure window. This change was made based on several factors, including: vendor feedback, average time to patch (from our Vulnerability Development team data), and improving the protection of everyday users on the Internet by ensuring viable vulnerability disclosure takes place over a suitable time period . Below we have outlined several key steps in the updated Disclosure Policy. Whenever appropriate Cisco Talos will review timeline objectives with the vendor in order to sufficiently provide time for patching to take place. This will be reviewed on a case by case basis to ensure that there is a progression in patching.. Extenuating circumstances, such as threats of any nature, may result in adjustments to disclosures and timelines either forward or backward.
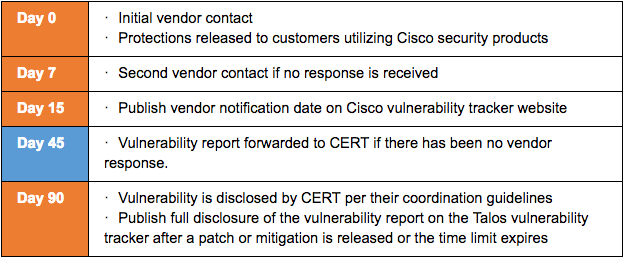
If a vendor has remained unresponsive forty-five days after the initial contact, the vulnerability report will also be supplied to the Carnegie Mellon Computer Emergency Response Team (CERT). In compliance with the CERT vulnerability disclosure guidelines, the vendor will then have approximately forty-five days before public disclosure of the vulnerability information.
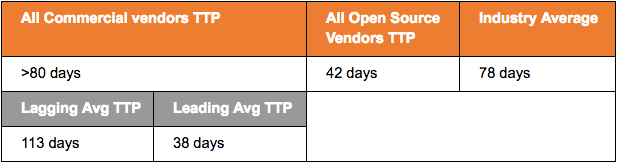
Let’s take a look at what we found in terms of vendor timelines and time-to-patch (TTP). Across the vendor space, the overall average was 78 days to patch. At first glance, Commercial vendors seem much slower than their Open Source counterparts. However, breaking that down further reveals some interesting information:
|
| Data pulled from sample of 143 Talos bug reports. |
There is a bit more nuance here than the top line data indicates. To illustrate that, Commercial vendors are subdivided into Leading (within the policy timeframe) and Lagging (taking longer than the established timeframe). Interestingly, several large commercial vendors of consumer software were found in the Leading category. The most responsive of these vendors were noted as “Quick Turn-around Commercial” vendors in our data - and they share some common traits. All are large commercial vendors of popular consumer software, have taken a public stance on product security, and have active bug-bounty programs. This indicates these companies have invested heavily in product security and take that security seriously. They are competitive with Open Source companies in terms of time to patch. It is encouraging that the number of companies in this category increasing, although the Lagging end of the Commercial space still managed to drag the overall average down from ~40 to 78 days. Anecdotally, an Open Source vendor set a new “speed record” and provided a same-day fix during this time period.
Industry Movement There is a trend toward the positive in our data. Obviously, vendors are realizing the serious economic impact that a true 0-day can have on their customers. Additionally, the loss of goodwill in the marketplace can cause irreparable damage to both the vendor and their customers. As vendors trend toward prioritizing updates, patches, and fixes, we have taken note. The changes in our Disclosure Policy reflect the timelines that are tenable to vendors, and bring our process into alignment with similar programs in the industry.
Our goal with the updates to this policy are clear and simple – working better together with vendors and the security community to mitigate as many threats as possible. Of all people, we understand that every vulnerability is unique.
For full details, please the official policy documentation here:
http://www.cisco.com/c/en/us/about/security-center/vendor-vulnerability-policy.html