Today, Talos is publishing a glimpse into the most prevalent threats we've observed between February 16 and February 23. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this round up are:
- Win.Packer.Givelet-6454616-0
Packer
Givlet is a packer that compresses and obfuscates a malware payload. It has been used to pack ransomware like GandCrab. - Win.Packer.WizzPack-6454612-0
Packer
This .NET packer has been seen being used by Wizzcaster adware which will install unwanted applications. - Win.Trojan.Generic-6454586-1
Dropper
These samples drop additional malicious files on the infected system, including cryptominers. They also use registry keys for persistence. And perform some host environment checks to evade sandboxes. - Win.Trojan.Generic-6454615-0
Worm
Win.Trojan.Generic-6454615-0 is a trojan that will contact a CnC server and try to steal information from the infected host. - Win.Trojan.GenInjector-6443827-0
Trojan
This family is highly polymorphic and malicious. It injects into another address space and it uses process hollowing techniques. Moreover, it gains persistence through the Windows registry and it complicates the analysis with several anti-debugging tricks. This particular cluster is able to contact SMTP servers and sends spam messages. - Win_Trojan_Regrun_6454954_0
Trojan
Win.Trojan.Regrun-6454954-0 is a trojan that will install itself in order to ensure persistance, and will modify several settings on the victim machine in order to conceal itself (file extension and file hiding configuration), hook certain actions (registering itself as a file handler), disable Windows Shell, register itself as SafeBoot alternate shell, disable the registry editor, and other actions to prevent the user from repairing the infected system. - Win.Trojan.Startpage-6455053-0
Trojan
This trojan changes the browser's start page. The start page can be a single site or a set of sites that will be opened when the browser is first opened. - Xls.Dropper.Powershell-6454576-0
Office Macro Dropper
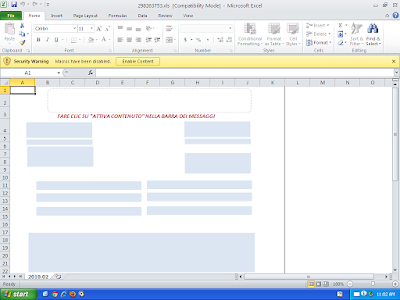
Excel workbooks that use the Italian message 'FARE CLIC SU "ATTIVA CONTENUTO" NELLA BARRA DEI MESSAGGI' with an unreadable image to convince users to run the macro. Powershell is used to download and run a malicious executable.
Threats
Win.Packer.Givelet-6454616-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value: qdobxoamsza Mutexes
- Global\pc_group=WORKGROUP&ransom_id=4a6a799098b68e3c IP Addresses
- 193[.]0[.]179[.]152
- 151[.]248[.]118[.]75
- 5[.]154[.]191[.]67 Domain Names
- gandcrab[.]bit Files and or directories created
- %AppData%\Microsoft\motopn.exe File Hashes
- 10f2ed852befc9c9c15e5231b2167bbec66e3700c44bcf324312a32e932fa819
- 1257a5650f02a4cbff43c190452517e17f4aa46284b7063162e4a54d318aff79
- 14944d9db8baace4d7fb97cdf285009b5e0472bd6aa4d9cb530a1f3893287682
- 17d14ca09aa5f447fca0d8d5d1ae9dee5731846588d1c15987eb3de5cd57e90d
- 184ccb64f12601a3797e9c73ce77c89d05b50f2a668f94ec8cfd1c7414906c0e
- 18635915a4453bd1c68de152c139326023a165c0ae191ef501a6425615aa5d84
- 18dd0a662f77ca2ec235b3ae761cf7f4e6a3adb3fe32b2c994c080b6b7f10389
- 19519e38242877d2a689efaddecb8b8699d122051cd4b189de6466a83422f7c3
- 19cebd1722376f2c62a1922214903052a964ad1d2505fa698376c5f3b4d0594b
- 19e5e3d8fbf0db27d943090114c88051294bb918f0c9ce2d4894d9c8c290c21b
- 1ddca770b20bf8748a2a0435cf4f7316167ee4dbc7311fd3fd8e9600c79fc7ec
- 1e7eebcaf485682da709a94fb1c679555a9090592cfe54564f5eb396c7458044
- 1eae0edf899f881fd86f0500b58f9b6497d5b94a99ac439307d61c0f24cb1573
- 2155517a296dd90f86ef3bb09455444c387d9b1384bb435c997105acd88a281f
- 29ce80f75b8877e22cdcdf3fbecb01d2d1a65161f18311facdbbd090769b5ee6
- 29ff9ee8e9d85e836de88304ee4251ff373bcec4abc5c45496192952ad08a0a5
- 32ee0ff7fbec042edbb9420e522eda1a126e1872da2b7a13b0627a03be4d1d59
- 336e7c9dfef94fecf00c1c0b2a539c7332453e72367efc0b25c5115d90d94180
- 3570b95ea454efd6735bf4942d69521d608ab7d0c9745cfa636f1107acc6a23c
- 3732c9fd5ff38c31fda2492dd81584819f12cce5731f7361f536bdf8040c724d
Coverage

Screenshots of Detection AMP
ThreatGrid
Win.Packer.WizzPack-6454612-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- RasPbFile IP Addresses
- 94[.]23[.]252[.]37
- 46[.]105[.]121[.]115
- 94[.]23[.]199[.]17 Domain Names
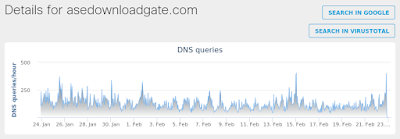
- asedownloadgate[.]com Files and or directories created
- \Program Files\S941OEL096\uninstaller.exe.config
- \Program Files\S941OEL096\S941OEL09.exe
- %SystemDrive%\Program Files\P56VHIGDGI\P56VHIGDG.exe.config
- %SystemDrive%\Program Files\P56VHIGDGI\P56VHIGDG.exe
- \Program Files\S941OEL096\uninstaller.exe
- \Program Files\S941OEL096\S941OEL09.exe.config
- %SystemDrive%\Program Files\P56VHIGDGI\uninstaller.exe
- %SystemDrive%\Program Files\P56VHIGDGI\uninstaller.exe.config File Hashes
- a7bca25940ec920dbbcc05ef606b1d0a1192d46de612b432a1072d3aa1fa5a07
- 22a96cc3fcc81a7475fc4c6253fd8e39bda56bd97afc5c98864c1eab9c2f625f
- c9bd472f6fa6af9f0ba855967c4a061e6e559e48734b4e85c30742a14274a5f8
- ea4ddb43aa08c17216262c7251fb47d6f8c2c3f2369c6efed6c7914d9f0e16c1
- 17873809b8b5c0df00a414ed8ac4ccd356d46bb5726d79552c3e5d5f0e63c889
- e63962df00ffdc4e99d59019b588c0b34a0c56368bedb9736cb684274fac3833
- 3c7d21d1ae2103a9610f3073c3e805ef76adfc978c13c19585830d2e17d3c912
- 9eea6555c0fbc9753b5a7f68d367269872538850b326a2eea3ad4c26fe910073
- 0c0124adc78b717b24505119f4faa70b1ce9fd217d7c5fee574b77eccd13d755
- 11d808a9eb56223bdb3e1a66a3d55a8ea12f077bb5ee2db66d193cb779a02f62
- a085a4dac6d01166072c7296ec4e4089e50a45ed0027a691854c62ed0c5be611
- e05db1be09272fb01803d46ca5b9b55e324776058a87f9695e1b39f8f9bd3e17
- f8f7422827e5874604c69ab1d2de11d893f7432a6b346b1a6d0feddce700d24d
- 2815d64f1dcbb9ea459b969da34c7d319440c854fcee7d5b12b138f5540f7a10
- f6bddc85724ff45d2b64f17685dcce98c7e5f7435d9b268debd523cbebc14260
- 899a119818fbdd16989380e5e4a62998e2d68865dc5f5dba82c2931e6d20bcbd
- f2dbc26b7b7dd8f552e954ce4e8b685a9600506a633a90c2735a303aec80e0a0
- 4727f0952de54fb024c30de9188d2e6e81ee0a675f229159013b6d753e985a6e
- 8e8bdb56d72a73da3d4367a59ca2235495fc7837aa48dd15201a6a0ff1a8d7ef
- c59a5a9e3cb8bc3794d17a480e4709b1b96b28a469c2a1ff1d9ab4972f7a043d
Coverage
Screenshots of Detection AMP
ThreatGrid
Umbrella
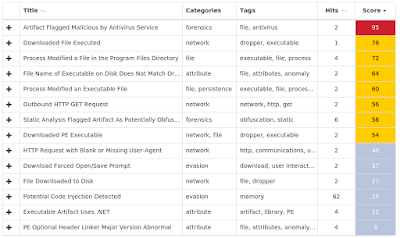
Win.Trojan.Generic-6454586-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: AudioHD
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe Mutexes
- Local\MSCTF.Asm.MutexDefault1 IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %TEMP%\svchost.exe
- %AppData%\AudioHDriver\AudioHD.exe
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\AudioHD.url File Hashes
- 013ede62c35998c847f9248bcede46dce801480743a064d488341f95094c0d4e
- 166ee27653415896013b0e775c03ffc27db5a7b6daa7a4c78976fdd7bc166416
- 1f1ec9a132226bc4eac25a6e999cc9b937718cb356c8d41b2bb08266ca1c5a38
- 2d1cfd1ae428729b32af03264179cb7640d4aa7b1e3c299cb106a77cfe42d216
- 38cf958875c3eb34a07f15163e7ceb8294ada5eccb765aa37ea69aba4fe79cd8
- 3b0e9faf07e32d593b54cdfebd725707988bdaa7d81ab2ab396630384127fdc9
- 3ff03a32f5a944c6655789bbfa124a7d52bb17df771c975685a5dce69c124d04
- 45b40df9bc6508a11c7fdf06de88a039485dca91d985fb667a91a4af35a08b2a
- 4ca97c879d841e79a5588f350cea663272bdfab1a1e7761b109c6bc72da523fe
- 5943eb982b5def7773628c728369398d5722c39f67b978c10782311eb00a50bf
- 9414096ebca4dd3e948014b7348578e5adfec4729e5a9f15f6b06dfffbd13408
- a6a9ec0af4abe94b72e557f4b9c9d4d0b59b4296aca3175a1551b84efefed856
- ab1c0fd38656ae73d1ec96bb5b3ee5e354022feca924653c606ad5dbc3ae0c47
- fddbec3a6e8fca4f3f388ff5856b8030005339967ffda594035f9353f5c71bd2
Coverage
Screenshots of Detection AMP
ThreatGrid
Win.Trojan.Generic-6454615-0
Indicators of Compromise
Registry Keys
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\eapqec.dll,-102
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\eapqec.dll,-103
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\eapqec.dll,-100
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\eapqec.dll,-101
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\dhcpqec.dll,-102
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\dhcpqec.dll,-103
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\dhcpqec.dll,-100
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\dhcpqec.dll,-101
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\napipsec.dll,-1
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\napipsec.dll,-3
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\napipsec.dll,-2
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\napipsec.dll,-4
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\tsgqec.dll,-101
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\tsgqec.dll,-102
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\tsgqec.dll,-103
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: @%SystemRoot%\system32\tsgqec.dll,-100
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: 35f4cf4b9d22a75d4f44d45247335d79
- <HKCU>\SOFTWARE\35F4CF4B9D22A75D4F44D45247335D79
- Value: [kl]
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: 35f4cf4b9d22a75d4f44d45247335d79
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500
- Value: di
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKCU>\ENVIRONMENT
- Value: SEE_MASK_NOZONECHECKS
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- Value: ParseAutoexec
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
- <HKLM>\Software\Microsoft\Fusion\GACChangeNotification\Default
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
- <HKU>\Software\35f4cf4b9d22a75d4f44d45247335d79
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Tracing\Microsoft\NAP\Netsh
- <HKU>\Environment
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Tracing\Microsoft\NAP\Netsh\Napmontr
- <HKU>\Software\Microsoft\Windows\ShellNoRoam\MUICache
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Tracing\Microsoft\qagent
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Tracing\Microsoft\qagent\traceIdentifier
- <HKLM>\System\CurrentControlSet\Services\Tcpip\Parameters
- <HKU>S-1-5-21-1258710499-2222286471-4214075941-500
- <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
- <HKCU>\Software\35f4cf4b9d22a75d4f44d45247335d79
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
- <HKLM>\SOFTWARE\Microsoft\Tracing\FWCFG
- <HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
- <HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig Mutexes
- 35f4cf4b9d22a75d4f44d45247335d79
- Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7
- \BaseNamedObjects\35f4cf4b9d22a75d4f44d45247335d79
- RasPbFile IP Addresses
- 52[.]15[.]72[.]79
- 52[.]15[.]194[.]28 Domain Names
- abdullahxd[.]ddns[.]net
- achreeff[.]ddns[.]net
- fatehtawba[.]hopto[.]org
- youdkme6[.]ddns[.]net
- boubou14789[.]myddns[.]me
- hixx[.]ddns[.]net
- hoangvanloi[.]ddns[.]net
- hackingisis[.]ddns[.]net
- aymandz[.]hopto[.]org
- deface666[.]duckdns[.]org
- ramzy778[.]ddns[.]net
- adsvcksl0[.]hopto[.]org
- hostalukkzattack[.]ddns[.]net
- 4mmujnm11[.]ddns[.]net
- love-5aled[.]ddns[.]net
- njrat511[.]hopto[.]org
- rootbot2[.]ddns[.]net
- force-ss[.]ddns[.]net
- aadlallame00[.]ddns[.]net
- ksa-99[.]ddns[.]net
- updateservice[.]ddns[.]net
- forever12qut[.]hopto[.]org
- wydad2002[.]ddns[.]net
- feedback007[.]ddns[.]net
- sniper1994[.]hopto[.]org
- falcon777[.]ddns[.]net
- pikhateamspeak[.]duckdns[.]org
- krkr-7rb[.]ddns[.]net
- sagadegemios[.]ddns[.]net
- sniper04[.]ddns[.]net
- omerbahram00[.]ddns[.]net
- koshtmna[.]ddns[.]net
- colorado[.]ddns[.]net
- minhahostvitimas[.]ddns[.]net
- zkiller[.]ddns[.]net
- 1[.]tcp[.]ngrok[.]io
- hussein1984[.]ddns[.]net
- sniperusa[.]ddns[.]net
- sodotest[.]ddns[.]net
- notfoundd[.]ddns[.]net
- portaclore[.]ddns[.]net
- al38lal56er[.]ddns[.]net
- paubrasil123ei[.]ddns[.]net
- samuli[.]ddns[.]net
- droid[.]ddnsking[.]com
- naoe1noip[.]hopto[.]org
- njrat98[.]ddns[.]net
- windowssystem2017[.]hopto[.]org
- dndon[.]ddns[.]net
- plon[.]ddns[.]net
- kskhtk[.]ddns[.]net
- belegugamaniawr[.]hopto[.]org
- boubou14789[.]hopto[.]org
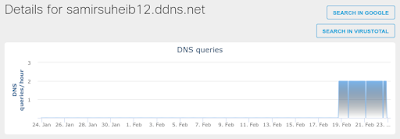
- samirsuheib12[.]ddns[.]net
- machouche17[.]ddns[.]net
- menescraftson[.]ddns[.]net
- tronn[.]ddns[.]net
- zombi16[.]ddns[.]net
- hamaditigwan[.]ddns[.]net
- r4y3n[.]ddns[.]net Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Start Menu\Programs\Startup\35f4cf4b9d22a75d4f44d45247335d79.exe
- \TEMP\R8v6FbJV.exe
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\35f4cf4b9d22a75d4f44d45247335d79.exe
- %AppData%\server.exe File Hashes
- e537ffeb2bc202f2a8289e9c96115c5c03280cdbda5a82a81d83b97570ccfcce
- eada793b386002f297ad511a2ae780cd011b189f1dccbd6ca62d89345095d6e6
- 49fbf92ef158694f0ed792403f7a066d88831ba71e5f4018f707010f2627210d
- 4c54271a9c1fc98d0561c6f8ab45be77121bb382453e07d49f2b56d89bd263ab
- b6712bdb9c15e7e3cbeb71a32cd2103c1286509a85e7db870baed53d71b0dcc2
- 15fa9fff9515ae191c98aabd7a870699d3683ad9ae0b9fbdb4fb875e35c43183
- 8def70bf3014498d6c05556fd1b5b72982205423bb5bfa9d25ab4288ecbb506f
- 658e4b5c23b609d535abc535901b848569dd294f26952fb07a25dc3537116bf8
- a4b0b9b8b4240370b6c9f030eaac7b852f10da8069b36d3387fd1b96e472d73a
- 2f2e7e92f633924afa45b5da925e217643ed08e605ced40949f0ca78adb36d6f
- a1d8135b1ff1c5d8c28016b4ff09bb47606f04f815a4f268c6d82d25398f7bec
- 46a5a182b94569e4db66ae877064a18a1ca470aa0302d400eaed02545d83c1eb
- 9bce170ab8da2c93a54bac556b0666f93ab09bfa9965b03bdbc7861ee413448e
- 90e7a37c2183bd83b02d3a6ac8af8a3afd19e0a1561bf16f2338476802dcfefa
- e1673a3ed97150082c0e89712386c71f6feb8fd1d7428fe633cfae0d1ca9baba
- ba1d8858e7863db19f04cf44cfa92906887833a84099f2bc810ed5c6863b46b1
- 59a56a0d81bac39e5a7a9299ae700b5734b1b038fa800c006463c5592620107d
- de3357a9ab3d0f03cb4025862a0f0a38f1eb2e0d2909f9537597c4e341cc14be
- bc9c84da6bac2680ae866d540768af8f744c321d2cedcccd97fb17299d5904c6
- 2e7b6747e309c3d8fb98ebe25eeeb9f4644162084b304a68ef00a5690be27b46
- 8d3b285e6b1a0c1f21e9a950ab580800f184b0d6456dd117c74edc37020c31f3
- b371a4708ba510da541267981d4b05bb6dafbe4b07b387952c582db4ea691e26
- dde1cc674ef61703752be1d3354f0f766724678aa0fdeb6376e7448a901d7f78
- ff2269482bf29fef74fdb1d15cfae2417955f1aaa80cd8e3c296d21bec23bf98
- ce533f8f084a79294aa1254db01fd630dab95ccff22124d9fb4c51fe16a2948a
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Trojan.GenInjector-6443827-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASMANCS
- Value: FileTracingMask
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASAPI32
- Value: FileTracingMask
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASAPI32
- Value: MaxFileSize
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASAPI32
- Value: ConsoleTracingMask
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASMANCS
- Value: MaxFileSize
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASAPI32
- Value: FileDirectory
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASMANCS
- Value: FileDirectory
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASAPI32
- Value: EnableConsoleTracing
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: FSjrvbtr\s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0s\\0
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASMANCS
- Value: ConsoleTracingMask
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASMANCS
- Value: EnableFileTracing
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASAPI32
- Value: EnableFileTracing
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\REGASM_RASMANCS
- Value: EnableConsoleTracing
- <HKLM>\Software\Wow6432Node\Microsoft\WBEM\CIMOM
- <HKLM>\Software\Wow6432Node\Microsoft\Tracing\regasm_RASMANCS
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\Software\Microsoft\Fusion\GACChangeNotification\Default
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\SOFTWARE\CLASSES
- <HKLM>\Software\Wow6432Node\Microsoft\Tracing\regasm_RASAPI32
- <HKLM>\System\CurrentControlSet\Services\Tcpip\Parameters
- <HKLM>\SOFTWARE\Microsoft\ESENT\Process\regasm\DEBUG
- <HKLM>\Software\Wow6432Node\Microsoft\Tracing Mutexes
- \BaseNamedObjects\7261cb8c-207c-4c90-b816-c6717f9f50fe
- 7261cb8c-207c-4c90-b816-c6717f9f50fe
- RasPbFile IP Addresses
- 208[.]91[.]199[.]224
- 37[.]187[.]116[.]23
- 208[.]91[.]199[.]223
- 192[.]168[.]1[.]255
- 208[.]91[.]199[.]225
- 66[.]171[.]248[.]178
- 208[.]91[.]198[.]143 Domain Names
- glop[.]me
- us2[.]smtp[.]mailhostbox[.]com
- smtp[.]tridentsaefoods[.]com
- bot[.]whatismyipaddress[.]com Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\tmp3.tmp
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\tmp2.tmp
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\tmp5.tmp
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\8a30b2df-789d-2a28-7167-76c811ca3a9f
- \TEMP\IMG-PRO-FORMA INVO.2017.1.11.exe
- %AppData%\FSjrvbtr\AVetZPQw.exe
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\tmp4.tmp
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\tmp7.tmp
- %System32%\wbem\Logs\wbemprox.log
- %TEMP%\a998c159-9477-9c4d-f909-8a857896ecad
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\tmp1.tmp File Hashes
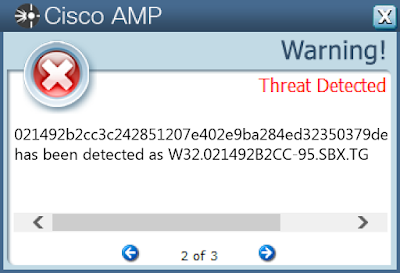
- 021492b2cc3c242851207e402e9ba284ed32350379deac649f38426130b2c01f
- 048800615c3449d53e8b3c28489fabb4e8f4d758ace9f585f8f2ea585d3c7fad
- 18d5300979ddaa3b65ff7579aa3725921b44e945e40ed54e55a0396add9d3323
- 2cd6fc2a4572f4b1a39371a8df8c664eabe119608908d441257e72eb203737f4
- 6346200d4e21bcd391e3557b72791f033c51fc72ebfeb359498b63c1c8d832ca
- 7ad83d75a4223be0dec837d26fa78e4d7a69e4379c01c3ae31f3aa82483fbd2d
- 90cd726b06dffb129795b132f92d39750492d168206ef22b0ee422a6a55663cb
- b111124ced4570df72cefd1b5d0d1afc1f1dae7db1319c4e720f52c23b76c0ad
- b9a43f89e0b974b2f2b2af15e80353b10175ed3e9d4e015d85f96d7d38e65c6c
- be9f065d0330585bc300e3a56c7ade7da01a48af2d1c7634e20c2896c45a2024
- d90dc3f22cc7bd92f22bafa9d77b0e373849386eae57606b42239f915357084a
- e128f7ad54a882d2d269733a956f49e5b1bf2b182781f24f98f058f2d8f48787
- e4b1ee306ab7080c48b05746da8130fdeede8730214e00778c8231f6d8d6e7c0
- fb237b7fc75cec8180f4d853c44911dc0dbdb705be39c3e6f1f2a523b79ff9d5
- 7a7afe3c990a21f1076dd57769d2e199e081ef04f5fb250da5c6d4d109034dc0
- a9657835057ff11177054c128e834217fd6ba5e55279caab16391f12147c0757
Coverage

Screenshots of Detection AMP
ThreatGrid
Win.Trojan.Regrun-6454954-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\INSTALLER
- Value: DisableMSI
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: System Monitoring
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
- Value: NoFolderOptions
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SYSTEM
- Value: DisableCMD
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: DisableRegistryTools
- <HKCU>\CONTROL PANEL\DESKTOP
- Value: ScreenSaveTimeOut
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CABINETSTATE
- Value: FullPathAddress
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: xk
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
- Value: DisableConfig
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\SAFEBOOT
- Value: AlternateShell
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\AEDEBUG
- Value: Debugger
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\INSTALLER
- Value: LimitSystemRestoreCheckpointing
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- Value: Userinit
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: DisableRegistryTools
- <HKCU>\CONTROL PANEL\DESKTOP
- Value: SCRNSAVE.EXE
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\AEDEBUG
- Value: Auto
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
- Value: DisableSR
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value: HideFileExt
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value: ShowSuperHidden
- <HKCU>\CONTROL PANEL\DESKTOP
- Value: ScreenSaverIsSecure
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: MSMSGS
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: LogonAdministrator
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value: Hidden
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- Value: Shell
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
- Value: NoFolderOptions
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: ServiceAdministrator
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\System\
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer\
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\
- <HKLM>\SOFTWARE\CLASSES\lnkfile\shell\open\command
- <HKCU>\Control Panel\Desktop\
- <HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows NT\SystemRestore
- <HKLM>\SOFTWARE\CLASSES\batfile\shell\open\command
- <HKCU>\Software\Policies\Microsoft\Windows\System\
- <HKLM>\SOFTWARE\CLASSES\piffile\shell\open\command
- <HKLM>\SYSTEM\CurrentControlSet\Control\SafeBoot\
- <HKLM>\SOFTWARE\CLASSES\LNKFILE\SHELL\open
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\CabinetState
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\AeDebug
- <HKLM>\SOFTWARE\CLASSES\lnkfile
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Run\
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\
- <HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\Installer
- <HKLM>\SOFTWARE\CLASSES\exefile
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Winlogon
- <HKLM>\SOFTWARE\CLASSES\exefile\shell\open\command
- <HKLM>\SOFTWARE\CLASSES\LNKFILE\shell
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Policies\System\
- <HKLM>\SOFTWARE\CLASSES\comfile\shell\open\command Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %WinDir%\Tasks\SCHEDLGU.TXT File Hashes
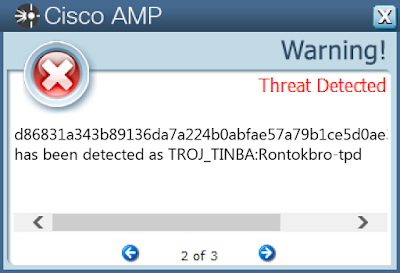
- d86831a343b89136da7a224b0abfae57a79b1ce5d0ae3447bef628d262fb0f12
- c137279e9650a0112f3a3460172a41f307e32aba43016c6d85b1d33859079bba
- 060bf8faec0beb953af3c72b54ea334abc1057f5bc96a65a140810ac55d2e6ce
- b6a80a6ed3bc851a1685ef19dc3a89424813b93a10b25a0684631a532dea71ca
- 13cf35842c9ef3f362bb7d3c6c8c50957f5b156e865b45b57e2e420416a3f656
- e6f2a103d62c0dd55cdbd3776578fd8ff3ea28532404a811c0dcd9ed7df473c0
- ddc14512ed0a1c00988ef4ea0ea59b832d4e17a25500e7a2f7d5caaa6aae0245
- 4a66e0bfcdd2addfccd8ba68c50d2b803beb2b8120a6cf4f8fecf4a0b0cf1678
- 9dda2f8f7543c8074f4c284c00e5310a599b364def138a99d7425ec1b205b7e0
- b2d99e9bb7d597d69b139b07c3ac03aeb37f959094ab0f50bc2a8269d340b8b6
- 59695cfe42cc0d5418a4568d946949af5fd9de14bdc160d1a5d12d5916a9b411
- 2c4d182d15533ea845e2d8741a3012998f339a3a6411735a07e4a5722ed0738c
- 80fd45667ccd54a83e5a54339fa4f5260929bc59f1a57be49251e3ebdcd5abce
- f0c6a8ed12cb35d5986a1ad51f035f684f0b2953c8b4738e5243777920d23169
- 04b54cac517f204d2f4159a819b63825a8be41a0470d9666ea2110607888c857
- 3c7e07a560d5cd46a054d44663440f7ef38b48157ae16c39e7a8c8859d517d80
- 6262f5c8735e38bc8ab646dc1edb6f989478c3d50abadd7b9b58a5e63d558dc1
- 5d5175472fbb0a943818f84a6b2423c410c212390310daca531e6f0f880c336d
- 57b930abca5b4f3cdd3c7c50b77224ea732dc5d44d2e8443c9199b7701a8307d
Coverage

Screenshots of Detection AMP
ThreatGrid
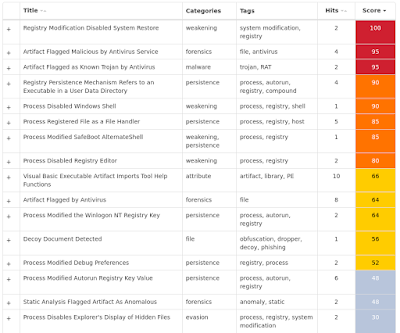
Win.Trojan.Startpage-6455053-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{69910372-D455-48F9-811C-B1191062C1B7}
- Value: URL
- <HKU>\Software\Microsoft\Internet Explorer\TabbedBrowsing
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E7E6F031-17CE-4C07-BC86-EABFE594F69C}\iexplore
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value: LanguageList
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{69910372-D455-48F9-811C-B1191062C1B7}
- Value: SuggestionsURL
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{789FE86F-6FC4-46A1-9849-EDE0DB0C95CA}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{72853161-30C5-4D22-B7F9-0BBC1D38A37E}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{69910372-D455-48F9-811C-B1191062C1B7}
- Value: DisplayName
- <HKU>\Software\Microsoft\Internet Explorer\User Preferences
- <HKU>\Software\Microsoft\Internet Explorer\Main
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{B4F3A835-0E21-4959-BA22-42B3008E02FF}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\MenuOrder\Favorites\Links
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{DBC80044-A445-435B-BC74-9C25C1C588A9}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{E2E2DD38-D088-4134-82B7-F2BA38496583}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore
- <HKU>\Software\Microsoft\Internet Explorer\LinksBar\ItemCache\0
- <HKLM>\SOFTWARE\Classes\TypeLib\{1EA4DBF0-3C3B-11CF-810C-00AA00389B71}\1.1\0\win32
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{FB5F1910-F110-11D2-BB9E-00C04F795683}\iexplore
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Uninstall\{28e56cfb-e30e-4f66-85d8-339885b726b8}
- <HKU>\Software\Microsoft\Internet Explorer\SearchScopes\{F7067876-A17A-4A11-A92B-185B2E8D39B6}
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\trust
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKCU>\Software\Microsoft\SystemCertificates\TrustedPeople
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SEARCHSCOPES\{69910372-D455-48F9-811C-B1191062C1B7}
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\trust
- <HKCU>\Software\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CTLs Mutexes
- {5312EE61-79E3-4A24-BFE1-132B85B23C3A} IP Addresses
- 1[.]1[.]1[.]1 Domain Names
- N/A Files and or directories created
- N/A File Hashes
- 6daffa157bd0a686cec232c2d1ffc764b7b85d7a94a6c2b13b46e3903fcd78b8
- 60dbf376cedaecb73bc2bd558024a2af9a95a3044d7343850a7ca03d098943f1
- 9eea8a80c3d01e16ab4ed53e9743d1dee0351b9ce6dd632dad938b71d78f8cce
- e74e9dd028c909ebd85012866f2e9ac33bc1db243499230d0e0c225eee9adb1b
- 18afad450f4b7816ddf1451e48684cefce677671ae5d6747fe90be2c3d8bd82e
- ab15bfd82688bd582807715e61aaa40f018f80fa0e99bbd018bc47a6c1aa80f4
- 399c3b0534f83e5778e2e1f65633d12e92b7b395d38315d964a640df646d32d8
- dbc1311001ddb6e3069e7b6d5dce0ce3618d736e1603f0271ffc52abbb8e2f0c
- 32bcd39615ac8e11e42b24925b24e74f4a4540acc763c5255c7bde0a00e1f253
- f31f9f266b453ddde95d2bab56548a32269b12d8c54c6efc7a91628b2a72273e
- a0014494734eb608b9f7af9f3c71057babf7f486e19745286bc574f766b4760c
- 228a8c340397acc65c36004acac69a29204840167527deb1f6ed02b75c8cbf1a
- f9552c1892cb3bd49289fb7eb541353027e6d431194d326c24b231b529adc0ba
- 62d5c29939f8c70c80797165dcff9b9170a77a82354bc0d2a5625c115a7dbc6f
- cc8a88dc216648a8ea78174b04c0c874cecbec2a2e6b93a742eaa530264cb563
- ab8cc1d317663161a27eba9a23d54f3c6d71bfb774dda248eadc052062e76cb1
- 13b51f0088c3c341d59467f89601703b20f160585d6008707572b12862ae894d
- 91fd6e5bf7737e284fc80757fbdf0e141564d37c0e50e447e1b7dc2ce1cb7a2e
- abc0a5ea42a72483a16308ea888d1a56f27c8e8c02b6a93d816339e7acab9c49
- 33033fc8af66d92c077aeeb997043c90a64d4aba8840779dedb4f446be7b94f4
- d463ae2543a2a81dc89d84b6ca9f195c430d65cf25fb753a9e4ab5fad1b4df2e
- 0b11ccc6fc403eeebd9edd0e9087406beeaf5aea9b38cfd7d4a57139e777619f
- 6b148642e7d64be68a97a13d776b03a76406bd2553ef0314b5afcb5906ad43d1
- 278cda56d3b11ab3712751f7c3848465a728aa13cf07980722509b04d992626c
- e32a73c2356c41a50e83cd9e7bac747249aed1fe68f17ee71d0a90887c3c1401
Coverage

Screenshots of Detection AMP
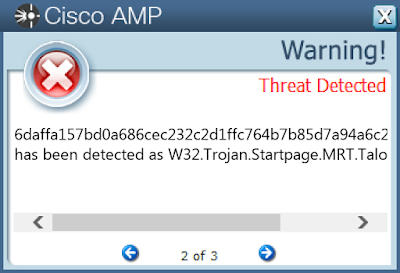
ThreatGrid
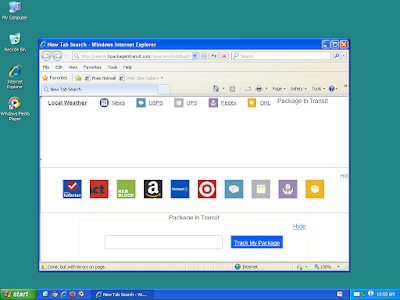
Screenshot
Xls.Dropper.Powershell-6454576-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 192[.]168[.]1[.]114
- 192[.]168[.]1[.]255
- 192[.]168[.]1[.]1 Domain Names
- bitcloud[.]gq Files and or directories created
- %TEMP%\CVRA534.tmp.cvr File Hashes
- 1955b36980486ceb95b0194fe10ed7aa9b317b7c3d6f79f152ff4f0aebba50eb
- 471c4a3ac3ee5f32cad237e320bbacc99c0b1cc52cadd351a9cd35eebc36ea97
- 1e0c9247ec3bb3d9f0e7a9e422aea3263ec32db17ffed0b4ae6a6e4b791fa195
- 9adfcba2c8a8e25433eb3cb88593d22314d59e0d420f1735df2908df7e7b8881
- 2241ad38594e08c9a72417e1f232ae1256c551f3b466d53a3ecf0fe4b3ac976f
Coverage

Screenshots of Detection AMP
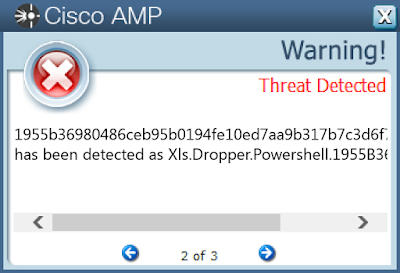
ThreatGrid
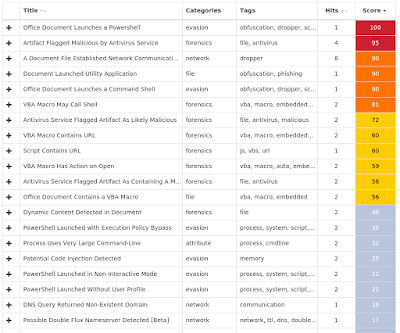
Umbrella
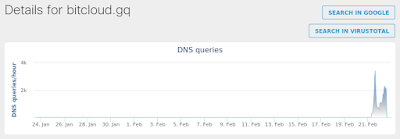
Screenshot