This Post Authored by Nick Biasini
For a couple of weeks in June the threat landscape was changed. Several high profile threats fell off the scene, causing a shake-up that hadn't been seen before. For a period of three weeks the internet was safer, if only for a short time. Still to date the Angler exploit kit has not returned and the threat outlook appears to be forever changed. This post will discuss a series of connections tying back to a banking trojan called lurk and a registrant account with ties that were far reaching across crimeware.
Details Crimeware is a class of malware that is concerned only with monetary gain. This class of malware is commonly associated with some of the largest, globally distributed threats in the world including Exploit Kits and their most common payload ransomware. One of the key aspects of crimeware is that it largely infects users indiscriminately, it is occasionally targeted at specific individuals or organizations, but most commonly is designed to compromise those that interact with the threat via email, web, or other methods. As ransomware has exploded over the last 12-18 months so has the money available to those that create and utilize crimeware. This has led to an increase in the types and amounts of crimeware Talos observes daily. The unknown is what connections exist between the various types of crimeware and the organizations that create and run them. Recent news, coupled with some major shifts in the threat landscape, specifically associated with crimeware implies that one of the largest threat groups we have ever seen may have been taken down, or at the very least on an extended vacation.
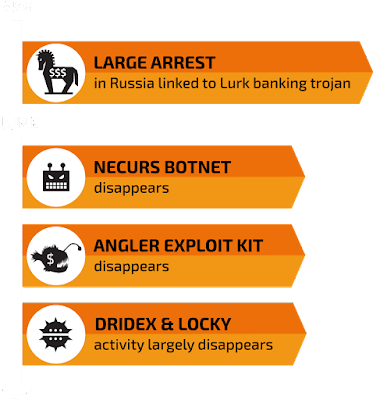
Arrest Announced Earlier this month a group of individuals were arrested in Russia. The arrest was linked to a Russian-specific piece of malware named Lurk, a banking trojan that was specifically targeting Russian banks. Due to the malware being restricted to Russia there wasn't a lot of public information regarding the threat itself. Talos found some references to it along with C2 domains while researching the Bedep/Angler actors that were discussed at Kaspersky SAS in February this year and published here. Based on the data that was released associated with the arrests, the individuals stand accused of stealing ~$45 million USD from Russian banks.
Lurk Since the arrests there has been ample coverage related to Lurk, so the technical aspects will be omitted from this particular post. Instead the focus will be on the C2 infrastructure that has been identified. From various sources we have compiled a list of more than 125 C2 domains.
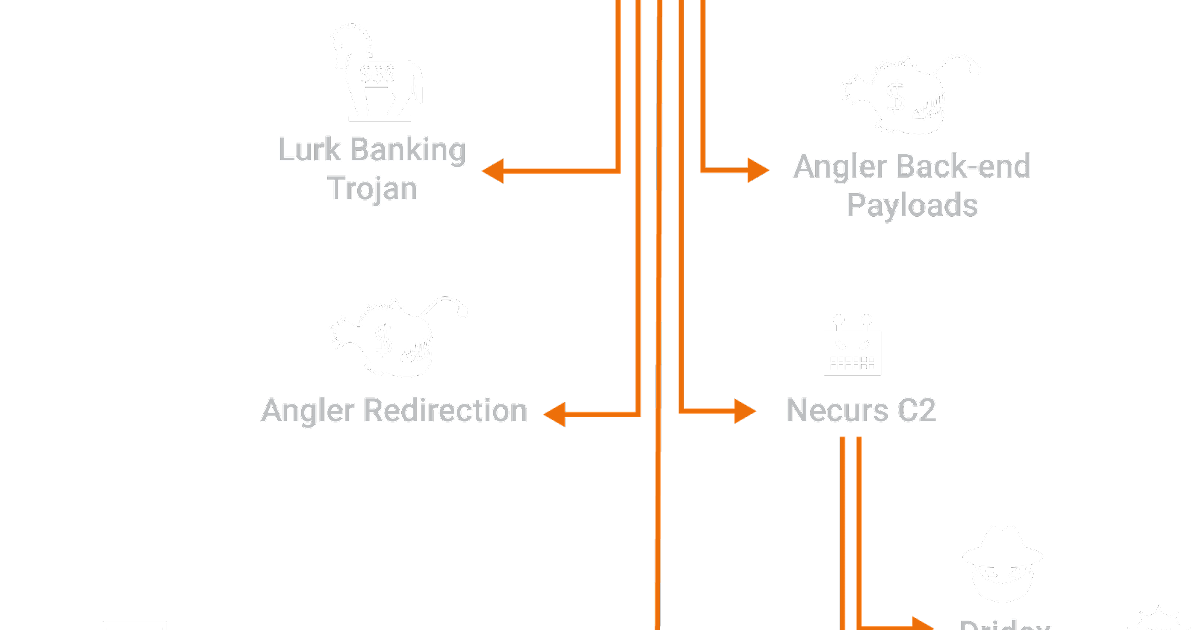
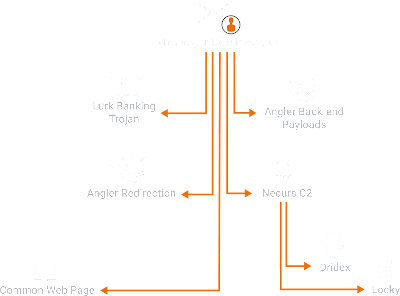
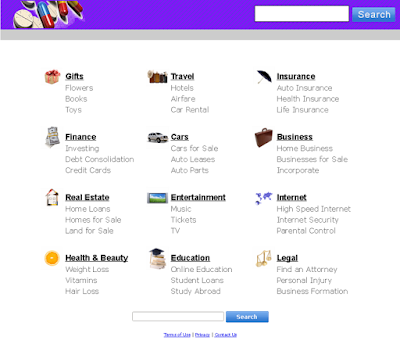
Based on this information we began looking into the Whois records for the domains and found some commonalities. Approximately 85% of the command and control (C2) domains that were identified were registered to a single registrant account john[.]bruggink@yahoo[.]co[.]uk. That email address should be familiar to those that read our research into Bedep as that was one of the three emails associated with registrant accounts that were tied to it as well as Angler. This particular registrant account was of interest because of its role in the back-end communication of Angler. We found a domain registered to this account, wittalparuserigh[.]com, was serving the payloads that were being delivered by one of the Angler exploit servers. In addition it was also found to own domains that were associated with redirecting users to Angler instances and finally was found to be hosting the same "default" webpage on some of the C2 infrastructure as the Bedep C2, a sample of which is shown below.
Angler Impact At this point there were clear links between Lurk and Angler, not the least of which was that Lurk was being delivered largely through Angler to victims inside of Russia. The question is, would there be any noticeable changes to the exploit kit and if so how big would they be? What happened was bigger than we expected. Within a week of the arrests taking place Angler has disappeared from the threat landscape. Let's pause for a second and talk about how significant of a change this is. Angler was, by a large margin, the most prolific, successful, and sophisticated compromise platform related to crimeware. Based on our previous research its users were making approximately $60M dollars annually from ransomware infections alone.
This is not the first time Angler has disappeared, most recently for several weeks at the beginning of the year. However, there are other indications that this is not as temporary as the disappearance at the beginning of the year. The biggest indicator has to do with gates. Gates are a key part of researching exploit kit activity since they are the mechanism responsible for getting users to interact with the exploit kit itself. In the several weeks we have started to see a mass migration away from Angler to other exploit kits. The transition to Neutrino from EITest has been well covered, additionally I have seen the gate I talked about at Hack In The Box, shadow gate, migrate away from Angler to Rig and Neutrino. Keep in mind that I found evidence of that gate being used to host Angler from over a year ago and they suddenly shifted.
At this point most of the large scale gates have moved to either Rig or Neutrino, something that was not seen when Angler disappeared at the beginning of this year. It has also been reported by Kafeine that the kits themselves have increased their costs to prospective users, another sign that a major player has left the market. One noticeable omission from the list of exploit kits being migrated to is Nuclear. Nuclear has also disappeared shortly after two different research projects were published by Talos and Checkpoint. Angler is the first major global threat that disappeared around the same time as Lurk, but it would not be the last.
Necurs A single region-specific banking trojan and the largest, most sophisticated exploit kit going away would be a huge story, but the research lead to more. During the research back in February, we uncovered a couple of C2 domains associated with Necurs that were owned by this same John Bruggink registrant account. Around the same time Lurk went away and Angler disappeared so did the Necurs botnet. This is widely considered the largest botnet in the world and with it several other high profile crimeware threats took a major hit. When Necurs went dark there were significant impacts to both Dridex and Locky distribution with Talos seeing significant decreases for Dridex and Locky respectively. Locky had decreased to such a small level that it looked to have been removed from the landscape all together, it appeared that a major portion of their distribution was reliant on the Necurs botnet in some fashion.
Necurs Resurgence Recently we have seen several of these threats returning to prominence. The Necurs botnet is back online and delivering both Locky & Dridex. It was down for approximately three weeks, but it's resurgence shows that again these threats are making far too much money to not be resilient. In time it's likely all of the major threats that we've seen be hindered or disappear will return.
Landscape Shake-up There is no way to say for certain that all of these threats are connected, but there is one single registrant account that owned domains attached to all of them. If this one group was running all of these activities this will likely go down as one of the most significant arrests in the history of cybercrime with a criminal organization that was easily earning hundreds of millions of dollars.
However, the celebration will be short lived as we've seen in the past, when a group this size is taken down a vacuum is created. All of these threats will come back, in some form or another, and will have learned from the mistakes of their predecessors.
The best evidence of this was the author of Blackhole exploit kit being arrested, for a time there was an arms race between exploit kits to see who would take the top spot. That eventually gave rise to Angler, which took the sophistication of exploit kits and drive by downloads to a level not seen with Blackhole. We expect the same thing to occur now as Angler and possibly Nuclear leave the threat landscape. Other lesser known kits will likely try to fill the void, which we have already seen with Rig and Neutrino, as well as the new kits that are likely already under development.
One thing this does show is that despite all the variety and different actors making use of these technologies there potentially was a much smaller group responsible for a far larger chunk of the crimeware space than previously estimated. Regardless, the threat landscape associated with crimeware has drastically changed over the last several weeks, and it will be interesting to watch it respond and evolve in the coming months.