Vulnerability Discovered by Cory Duplantis of Cisco Talos
Overview Talos is disclosing TALOS-2016-0227 / CVE-2016-8714 which is a buffer overflow vulnerability in the LoadEncoding functionality of the R programming language version 3.3.0. The R programming language is commonly used in statistical computing and is supported by the R Foundation for Statistical Computing. R is praised for having a large variety of statistical and graphical features. The vulnerability is specifically related to the creation of a PDF document.
Details This vulnerability specifically affects the PDF creation capabilities of R. During the creation of a PDF document, the file containing the encoding array can be specified by the user. The following command can specify the encoding file for a PDF.
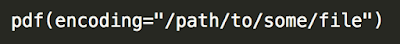
While loading this file, each of the specific elements in the file is copied into the 'cname' element for each item in the 'encnames' array. The 'encnames' array is part of a EncodingInfo structure. The 'encnames' array is of a structure type 'CNAME' with a 'cname' attribute that has a set buffer length of 40. If an element in the encoding file with a length greater than 40 is provided the buffer is overflown. This overflow could be leveraged to potentially gain remote code execution later in the program. Full details of the vulnerability can be found in the advisory on our website.
Coverage The following Snort Rules will detect exploitation attempts. Note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. For the most current rule information, please refer to your FireSIGHT Management Center or Snort.org.
Snort Rule: 40894, 40895