Today, Talos is publishing a glimpse into the most prevalent threats we've observed over the past week. As with our previous threat round-up, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
Win.Virus.Virut-5898123-1
Virus
Virut is a polymorphic file infector. It has worm behavior and infects external devices plugged to the computer. It contacts C&C servers and it has backdoor functionalities.
Indicators of Compromise
Registry keys created
- HKEY_LOCAL_MACHINE\Software\Microsoft\Tracing\winlogon_RASAPI32
- Value Name: MaxFileSize
- Value Data: 1048576.0
- HKEY_LOCAL_MACHINE\Software\Microsoft\Tracing\winlogon_RASMANCS
- Value Name: MaxFileSize
- Value Data: 1048576.0
Registry keys modified - HKEY_CURRENT_USER\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value name: ProxyEnable
- Old Value:
- New Value: 0
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\TRACING\WINLOGON_RASAPI32
- Value name: ConsoleTracingMask
- Old Value:
- New Value: 4.29490176E9
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\TRACING\WINLOGON_RASMANCS
- Value name: EnableConsoleTracing
- Old Value:
- New Value: 0
- HKEY_CURRENT_USER\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value name: SavedLegacySettings
- Old Value:
- New Value: Base64 content (verbose)
- HKEY_CURRENT_USER\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value name: ProxyServer
- Old Value:
- New Value:
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\TRACING\WINLOGON_RASAPI32
- Value name: FileDirectory
- Old Value:
- New Value: %windir%\tracing
- HKEY_LOCAL_MACHINE\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
- Value name: C:\Windows\system32\winlogon.exe
- Old Value:
- New Value: C:\Windows\system32\winlogon.exe:*:enabled:@shell32.dll,-1
- HKEY_CURRENT_USER\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value name: ProxyOverride
- Old Value:
- New Value:
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\TRACING\WINLOGON_RASMANCS
- Value name: EnableFileTracing
- Old Value:
- New Value: 0
- HKEY_CURRENT_USER\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value name: AutoConfigURL
- Old Value:
- New Value:
Mutex Created - Shqq Files Created
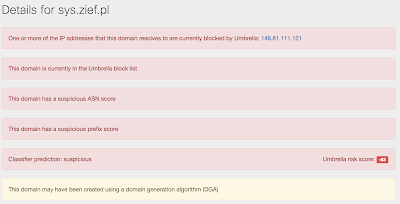
- %SYSTEMROOT%\system32\drivers\etc\hosts IP Addresses
- 148.81.111.121 Domain Names
- Sys.zief.pl File Hashes
- Bc11480f1900f19229113e575f4b46c4036b9b273154ee99e0e39811f4cc1a67
- 95435becfd04b78d802007b89c05430961e7a73f9b042c2dbd0f3eac1e964323
- A81039813c7d6b4ea098e9cbeee6063b240cd2475622b8ebe0a3c3ce906924c5
- 87e0d38d7cd7863ec43cfcc81a439b9edeb45cd7e9080b045a16bfc648383d39
- 6ff496d70284e2308caf6024da5faff8322f04cb81b317d747244fe5e24a3b6c
- c6c04fe371acec11c87b16a5e299fc72fb2c8f4636f566540df27960c996f01f
- F2c8a75a1d7b7e3dca477897741619b19f946258c42364271cf19a7b0233da90
- Ad7bd34ca44579e10c9aaaa8660d0f14d9861cabdbecd9847908aa2d68a16581
- 58a11dddfc23f9bf54580f79bfde40c930d0028c25be3d1033d178d6ccd5fa7e
Coverage
Detection Engines
ThreatGrid
Umbrella
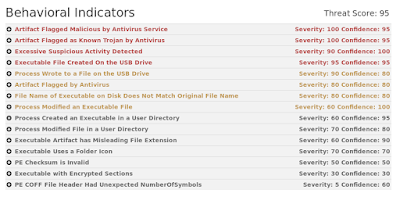
Win.Ransomware.Virlock/PolyRansom Ransomware
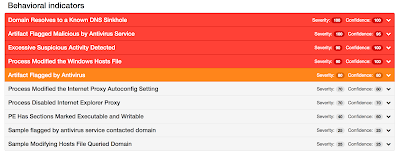
VirLock is a polymorphic ransomware that not only encrypts the files available in the system, but it also infects them by inserting a modified version of its own code at the beginning of each file. More specifically, it will replace each file by an executable disguised as the original file, with the same icon and its "exe" extension hidden. Once executed, it will infect the system and show the contents of the original file. Additionally, it locks the screen and asks the user to pay a ransom. It will try to connect to google.com to check if it gets redirected to some localized google page such as google.co.uk or google.au. It will also try to spread to network shares or cloud storage platforms, in an attempt to increase the damage and potentially infect other users that may inadvertently open shared infected files.
Indicators of Compromise
Registry keys created
- HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run
- Value Name: [A-Za-z]{8}.exe
- Value Data: C:\Documents and Settings\All Users\[A-Za-z]{8}\[A-Za-z]{8}.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Value Name: [A-Za-z]{8}.exe
- Value Data: %SYSTEMDRIVE%\Documents and Settings\%USER%\[A-Za-z]{8}\[A-Za-z]{8}.exe
Registry keys modified - HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- Value Name: HideFileExt
- Old Value Data: -
- New Value Data: 1
- HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- Value Name: Hidden
- Old Value Data: -
- New Value Data: 2
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- Value Name: EnableLUA
- Old Value Data: -
- New Value Data: 0
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- Value Name: Userinit
- Old Value Data: %SYSTEMROOT%\system32\userinit.exe
- New Value Data: %SYSTEMROOT%\system32\userinit.exe%SYSTEMDRIVE%\Documents and Settings\All Users\[A-Za-z]{8}\[A-Za-z]{8}.exe,
Mutex Created - \BaseNamedObjects\[A-Za-z]{8}
- \BaseNamedObjects\[A-Za-z]{8} Files Created
- C:\Documents and Settings\All Users\[A-Za-z]{8}\[A-Za-z]{8}.exe
- %SYSTEMDRIVE%\Documents and Settings\%USER%\[A-Za-z]{8}\[A-Za-z]{8}.exe
- %TEMP%\[A-Za-z]{8}.bat IP Addresses
- N/A Domain Names
- N/A File Hashes
- 9a55023dc479233a728dac2fd788b3e8b5a86091fcbcb575bbf3549189fb173f
- c2eb5753f3c1d70adb4d8e11c7180944005b1be32093b52dc1072a7c5e95f108
- fdc83ee924f41ee0ac707ec41b0712fa881894d24151a1a451410e8cff297af2
- 30761603de368bc7c94a9ec35ff7e8aeedb8ae13eb366936a3b50885fd9e39df
- 29174fab1e53c84fd99e0fb3f9e3c4c231dd94ae33db2cacf6dc82fdb9b21c60
- 1f68643772f3bb8ce75bbc746bc0b9b3f096a094f2141062ec75b1bfd15101fc
- 834c8e26451949144917b41f35dc870b1f8a07d195492f116fb7d4a1fc4d464e
- 0ad9fc8f59b3734213d1149b01256bdb54200f4ecfb0923275d2c7030d8c96d5
- 3373e7d31d28847f80bebf3c07a1e6502950403129f2491f933e6574a8f92a40
- 3fb92233eedaf5e35a9ef5d28e4c28209b656733e2690ec92449628651b959d6
- 2e26c2a3f9bf0637b3738adaa615632e7e68130190609dafd0db37e7ab9a37af
- 1326226d66db6702a8fdd2a4271ad5bc1213575b39a7529dce6e8a71c0a9ac77
Coverage

Detection Engines
AMP
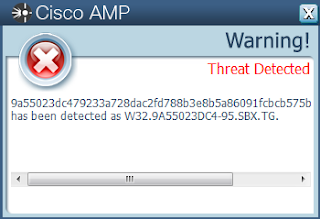
ThreatGrid

Malware screenshot
Win.Worm.Regrun-6012730 Worm
Regrun is a worm family replicating itself on disk drives and USB keys. It disables access to the registry editor and changes the shell program when the system is booted into safe mode. Regrun maintain its persistence by modifying registry keys. It also perform files associations to be launch with.
Indicators of Compromise
Registry keys created
- HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: MSMSGS
- Value Data: %USERPROFILE%\Local Settings\Application Data\WINDOWS\WINLOGON.EXE
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN\SYSTEM MONITORING
- Value Name: System Monitoring
- Value Data: %USERPROFILE%\Local Settings\Application Data\WINDOWS\LSASS.EXE
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN\SYSTEM MONITORING
- Value Name: LogonAdministrator
- Value Data: %USERPROFILE%\Local Settings\Application Data\WINDOWS\CSRSS.EXE
- HKEY_CURRENT_USER\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SYSTEM
- Value Name: DisableCMD
- Value Data: 1
- HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: ServiceAdministrator
- Value Data: %USERPROFILE%\Local Settings\Application Data\WINDOWS\SERVICES.EXE
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: xk
- Value Data: %SystemRoot%\xk.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\BATFILE\SHELL\OPEN\COMMAND
- Value Name:
- Value Data: "%SystemRoot%\system32\shell.exe" "%1" %*
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\EXEFILE\SHELL\OPEN\COMMAND
- Value Name:
- Value Data: "%SystemRoot%\system32\shell.exe" "%1" %*
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\PIFFILE\SHELL\OPEN\COMMAND
- Value Name:
- Value Data: "%SystemRoot%\system32\shell.exe" "%1" %*
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\LNKFILE\SHELL\OPEN\COMMAND
- Value Name:
- Value Data: "%SystemRoot%\system32\shell.exe" "%1" %*
- HKEY_LOCAL_MACHINE\SOFTWARE\CLASSES\COMFILE\SHELL\OPEN\COMMAND
- Value Name:
- Value Data: "%SystemRoot%\system32\shell.exe" "%1" %*
- HKEY_LOCAL_MACHINE\SYSTEM\CONTROLSET001\CONTROL\SAFEBOOT
- Value Name:
- Value Data: %SYSTEMROOT%\xk.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value Name: DisableRegistryTools
- Value Data: 1
- HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value Name: DisableRegistryTools
- Value Data: 1
Registry keys modified - None Mutex Created
- None Files Created
- %SystemRoot%\xk.exe
- %SystemRoot%\system32\IExplorer.exe
- %SystemRoot%\system32\shell.exe
- %SystemRoot%\system32\Mig2.scr
- %HOMEDRIVE%\XK
- usbdrive\Data Administrator.exe
- usbdrive\XK
- usbdrive\XK\Folder.htt
- usbdrive\XK\New Folder.exe
- usbdrive\desktop.ini
- %USERPROFILE%\Local Settings\Application Data\WINDOWS
- %USERPROFILE%\Local Settings\Application Data\WINDOWS\CSRSS.EXE
- %USERPROFILE%\Local Settings\Application Data\WINDOWS\LSASS.EXE
- %USERPROFILE%\Local Settings\Application Data\WINDOWS\SERVICES.EXE
- %USERPROFILE%\Local Settings\Application Data\WINDOWS\SMSS.EXE
- %USERPROFILE%\Local Settings\Application Data\WINDOWS\WINLOGON.EXE
- %USERPROFILE%\Local Settings\Application Data\csrss.exe
- %USERPROFILE%\Local Settings\Application Data\lsass.exe
- %USERPROFILE%\Local Settings\Application Data\services.exe
- %USERPROFILE%\Local Settings\Application Data\smss.exe
- %USERPROFILE%\Local Settings\Application Data\winlogon.exe
- %ALLUSERSPROFILE%\Start Menu\Programs\Startup\Empty.pif
- %USERPROFILE%\Local Settings\Application Data\Microsoft\Outlook\~Outlook.pst.tmp IP Addresses
- N/A Domain Names
- N/A File Hashes
- 2cf6386760d97a1d305bb823134d46750a368a248fc872a6242fb41e693fc4ce
- 933af1cae4769bd98e2be1802b423f99ee3d7244b22629c2e607e100fef37036
- b029eb236c2ed1aad84f8e9f6c235fe9c9a6ce758b53dce4fc42425fb4c7e5f0
- 3c588fc0fe07a29c98e2e76bd691b65702dfc1e3db2b9bd164defae8a2f0d8a2
- c3662ca86e76218624e77cd152c10e03c0239765c02ca9bf444a380104f6ea0a
- c05bd9347fed6be886d4e761c847835e25ef4522e9f6d694da4e3644b7877f7f
- 000718e0ca70ca451494c4a1be1a44d4dd9b48b64c55e362825488fea78f25c4
- aea4767879bd12c9605804b4696a2dce1908159182aef78727fee76b5dcd2a21
- 20faecc0f9c6a625992617339ea1f4b700846c867a43ce91060cdb815fff9e79
- bbd9482b09b0eb4377f5f540ef9b4893fcf003b08cab47261916cd31c1b823c6
- 79dd228fd0f5e09bb6842ba127dae26b85a850d20d472641d2af7af5ada96420
- ecaea889b7b4f7a7b4901d947395c16cfcf16a80528ea23ad91769d974cef235
- 460857e975092b0cca4813833cc2e201a5a6b14e0efad96d393c1e9c13f7a0af
- 891aac1d82e6a840cad78239fbe51eda6b6aab6fab967654b388491614a4fc1c
- 5492f7b994994239abd0225afcd62de3666cf109fa0979a4eced0048d4f2592e
- f1aefb4699b89cad56f3f50d26d8d8b39fb200dfcc6e48543e6c8f67165dc629
- f9210ad388fc4aeb0efe91a4701efa2a23fbdffb968c83fb925f96f8d058028f
- 30977d2a2697c802bfe142ab6fcc36a47692320006a5d86b064a178ee49a2817
- 0959547e4a484018a4e8807c8fd92cfb07c3971d328d538a3db745ee6b380ccb
- ac869bfe412125fc96a184d3cabbeba746f2b087d2252242be8c454c36b4817e
- fcbb7562cfbe902f31e7fabca6502ca070b9bcb725d220a08620c7bada7dc7ea
- bcb6d08440e00895f09137783545b57dc53ab2d152d91e1b51ee414b60784bd9
- 9230467d1d5cfaa832aaaf2f463d5ed7c7bc5eeeacf64d6966656e2cd272a2bc
- 2cf6386760d97a1d305bb823134d46750a368a248fc872a6242fb41e693fc4ce
- 376a74efe8a5fc81e8f2d8b45bf8b0eeb0ec2bdf5c0782727fa9b553e13c4875
- 4d0468bb43f4de7459b58c4588573b51a083daec631de97d5dec8a85334c3286
- 312b17a38b57aa5f39ab2e402631dc7e45008b08d5becab228b98764638373b5
Coverage
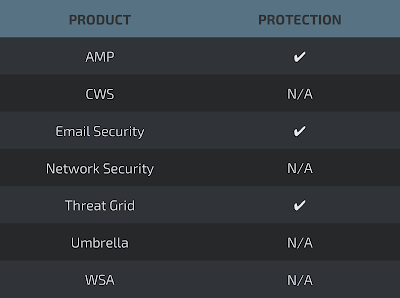
Detection Engines
AMP
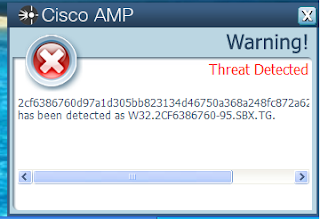
ThreatGrid
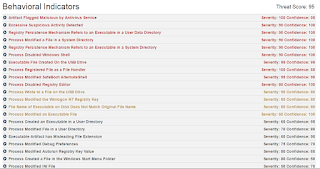
Win.Trojan.Vbswap Trojan
Visual Basic credential harvester. After mouse activity is detected, Vbswap searches for stored credentials and server information from browsers, FTP clients, and email clients. Collected information is sent to the embedded server and the Vbswap then self deletes with a Windows Batch file.
Indicators of Compromise
IP Addresses
- 103.11.190.170
- 107.191.35.77
- 131.153.38.169
- 162.219.28.187
- 169.255.57.4
- 185.145.131.104
- 188.40.248.80
- 192.3.140.121
- 207.182.141.194
- 239.255.255.250
- 62.108.34.136
- 62.108.34.162
- 89.111.177.28
- 92.53.96.179 Domain Names
- aumsooria.ddns.net
- Bigzee.usa.cc
- Cb74020.tmweb.ru
- Central.pk
- Chuddie.darkbastardz.durban
- Dms-mos.c14110.shared.hc.ru
- Fingers-ciao.com
- Fingers-ciao.net
- Newgi.usa.cc
- Newsmart.usa.cc
- Obis.darkbastardz.durban
- Perfect-technology.org
- Silverliningbd.com
- Stpowered.com.sg
- Sybanindia.com
- www.stpowered.com.sg
- www.sybanindia.com
- Xavica.usa.cc File Hashes
- 113484A1416FB4645355A88DC806BA8EC56BB383EFCF932661402A5887E11F2B
- 179719F9828C1BAB0FAC18DCB29FA62AC6B50BEE9846021F66D6235E2ADB4FD3
- 1A871F1FF905ACA5BD9D170E26B50D2B8BCF13622EB8B5BC21D8B5967D6EE010
- 1F77DF59064BDAD8517845253B6705869DBB3386C523D500003D5FE3A79DDCD9
- 2518CBDDA8B91112239A3A59FAEE20FA5F52E6BF34E93D133638CFCD83EE3B03
- 34BA105FF24384F18F193B5ADE74AF41B46A21A547F3DA7213BBF062413D0B24
- 370DD0361D3910A58BCDF78A0BC6DC71D6663FFCBC7EBC63EE514059734688DD
- 3E9AE7180C0ABB04E4DBB2B7478A827DB627A840E6607AC9F8237EDF41DDE7B2
- 44FD5631EC4A4A0C9A106ECF5C12189CF654366357392A279AE0F0D021F4EDE4
- 463D9330C11F729A59C32C01FBCF3FF0A3411E38EEC7080A2AE97BEF9C12A97A
- 47FDB875CB83D86888B7F9EF71CC72E00D99424FC4A7CAF0673F08D3AF204DE7
- 5DE80C52914EACF217CB4A70B7BA32AE40EE69C00C8D5AA3864129C1B2A26F3F
- 681DC2995702C6601BD64CC3A3B917934B1A767A8A9927175C9F87A13A71F2F7
- 6A7967D4F20A85A6A48F6EDAA46C29E86D8E0C0670C76237025B9472E6BA0AA7
- 6B246BB47322560A6C687FACC7C13813FAE14D1855A5F424717BBA54417CD6FD
- 6DD24419EA9EA9651D4F106F39780CD1E24FDAD6211AC7D37DB1C1CB10CDB530
- 72B7699891014CFFDF7A125298632035539809D9F89556612C4A0FD33AAD94D8
- 7447794094631DDAC56B970FB958A42AA6247DED89A2E921BFED294A419CD053
- 86D94403B1D7605E20429972595E938E9F9C3A757148D12A1E9489F02709EBD0
- 8774DF1F9A77486FDC20558BF75C2FE6D03EEE645ADDF0CB92B418DA7F2971B0
- 87A989596824AFCA6A5FA77343942B6C0E718C415EF40683343023D447113EF9
- 8CCE7794F09480FACBD607E12D4DBEC889D86247E620ABD90E32D0C7B9353076
- 9C3EA1B0761A834C6F386EED2EB69D7B64CA533F6D1C76BFFB2EC5BAD3D633A7
- A0A6658C48D56DD29F545735D3320B769874D85B7C703852F539295386F07E8B
- A22FFF831DBF91368997EF0B288A97034C2B88CCC29565A231096522B65FA495
- A27760DA48D0F40C209D104496DD4D80F6EF4E8251CFE7A3B92A9CEE59E7AA64
- A89C6E66052EA3F0E29CE32BE67792A301C4A5B271EA89DF520998C5560E0FDA
- AC2328F2D9117E3C83B0CECE9713EF4F990C43E5E827BA36A25BF2E9C9A9DF4B
- B224B3435F9477FA3B8CC91E10A82426B2BDA4152832A46633EC2F0A32B70522
- B93C7C417393BB701C02227C7B3059356C38A19404B22AD5616F436F785D4B1D
- BA5ECBDBD446CA0FE1CB80C905F6701970B82A857AA669DC776AF7F510649DAB
- D21844A443A88BF09C601980AFCBB479D161DC1970D7AB9559071CD7FAD48FEA
- D63A1B15508BA70B68713429E298006312C3D4975042D3358D61A2ACAAC4D3FC
- D8B2DDA1022BFA34FF47F4850EC040583A535772B8F49A11C4C319C61308F8CA
- F0F1B2E4CEC14CA957D3B79492B6A1E85A6AA811D141B48D3DC7D5B585D5002B
- F24A194934446676F88D6025918928DACAD7EB4AAAAF57BA1A0B5897D2FB9758
- F46CFFA96B66AAB89EDAB21C47B120BF349DF8261379BCE21312914EB8DD42F2
- FED1A307CED537647A117F5A04C2B36DCE5C14F884BA1756240A185045E64C02
Coverage
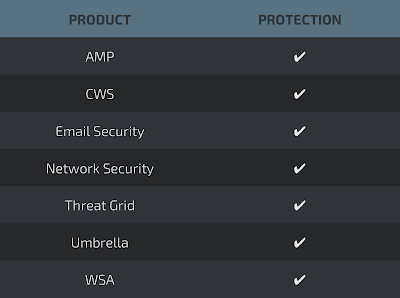
Detection Engines
AMP
ThreatGrid

Umbrella
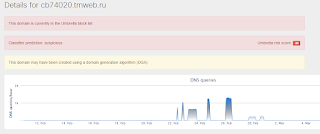
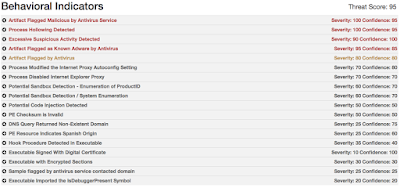
Win.Adware.MultiPlug-1 Adware
File downloader utilizing a domain generation algorithm for downloading and installing adware on the compromised computer.
Indicators of Compromise
Registry activity
- N/A Mutex Created
- N/A Files Created
- %TEMP%/D.tmp IP Addresses
- N/A Domain Names
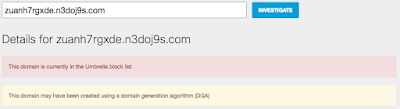
Domains below are part of a Domain Generation Algorithm: - 0ydttndat.4wvdi5t7k4.com
- 1ipahq.d8ntvqxqk.com
- 1zh7dpalr.ji1dwuuw.com
- 2vdylhs.o7di8uy4.com
- 7qacdryb.k60pbj4t.com
- 7zhyhhzmvutl.ji1dwuuw.com
- 8phpdwe.o7di8uy4.com
- 9slaax9.o7di8uy4.com
- aehih8lizm.d8ntvqxqk.com
- b9t4dp.tf4svxp2.com
- bedepexlb.ji1dwuuw.com
- bmt0tgxu.1eitpwrz.com
- csddh8fntx.ji1dwuuw.com
- e5dwdqdso.f5usp00wmh.com
- eatttvvli.nd29ok7.com
- fhpjp8.ji1dwuuw.com
- fjadlx0r.nd29ok7.com
- fllfd7th.hhx153fw.com
- g3trlj5vyt.o7di8uy4.com
- g4hdtcjcmpa.ji1dwuuw.com
- glaoab.o7di8uy4.com
- gppuan.8dmhrkg8.com
- h1lctl.o7di8uy4.com
- hdlsa1r1ed.nd29ok7.com
- k8hwtr.d8ntvqxqk.com
- kjtwl5v4sa61.4wvdi5t7k4.com
- krtopiera.0b72kiq.com
- lat3t9a3ib4h.o7di8uy4.com
- mgaitrt.o7di8uy4.com
- mtallp3.d8ntvqxqk.com
- nbhrdgrstq.o7di8uy4.com
- nwlrdwm5eas.0b72kiq.com
- o3l8dagf.d8ntvqxqk.com
- owlhdjmngqf3.o7di8uy4.com
- pphtam4dz.ji1dwuuw.com
- puduhy37k.3xokbqi51.com
- qhhmhsbsq4bh.n3doj9s.com
- qmavty1ua9ta.shf7xnj59y.com
- r0pkaq.o7di8uy4.com
- r1tzpr.d8ntvqxqk.com
- rypppxdkrktu.o7di8uy4.com
- s3d7acgqgq.i9bkgi2347.com
- sntmhkdgp.1eitpwrz.com
- ubdpa9l0.o7di8uy4.com
- vgh4lpwdtkw.ji1dwuuw.com
- wsa5di.i9bkgi2347.com
- xed4p9r49yhs.o7di8uy4.com
- ydtaaszmc.d8ntvqxqk.com
- z3a1h0.rg2rwk60f.com
- zragtld.d8ntvqxqk.com
- zuanh7rgxde.n3doj9s.com File Hashes
- 58d7e6427b63c5461ee6813957c198010737c555c0509dee6f65a5686ac4e417
- a7ad35d460afaa831200fdcb947eb8b4bbbf90f676ac69898dfe8a8d3572f05b
- af4936e904b7aef3351793812d9044c50203d7e8387c30e27f16512b5797fdd4
- 862fbaa377c858d06d313bb544c358871cd6bc49befd19fba45c55757e5db016
- 8cf90f6c399bdddf6e2dfffcd3b82b04272ecd1ac5d3eb03b673974e9c3b5a12
- 12874f0c63dc87869f2dadb4a2315aba778e3047cdef8612eb4e7aff11815312
- 149fcc0051cad27b0c9da7d5c5b63cfe1e196f3513d0794211a76da8a67370fa
- 104824a7d07101ef39568843655339859edc47629c1b2ac055b9bdded5362ca2
- e6d02709db0d8dab8c3eeb96f4b6b4556a0365284d3e941a6f3fcf95149dfdf5
- 763c344dafd645b47a7c53c710bb197e81a924fc21e21817f8bbe6c4cfde1df2
- 6ef90c4b1610903f4670933e3f68a0c4cf74b7fd87012cdac61d39b1dbc9ebaf
- 7b27b82f77bccb4624c9f70f17b22be8840aba6b62799394dde3b88e6965663c
- 4ab48e404cb035060560d36eed50508066080e76337de10a4225af45ec2288b5
- e79746062211d88f2d052950f8c78709823804897389c7b5b7da41699544c7af
- 07c5d056f285582db4fd673d24bf993b5f4ba41bc9931b4e89aaecdd5b254f3f
- 382fdcec78aaa6a63ef98bd567b2d326c106ba42a684070f56f9a483de108408
- f4f9723df12b88e4b8b7638e9d31c8cc4754b92b717ed123f50b5c8deeaac826
- fd41588284383c3436a60b5cce7901400218587df810b0bc3c056a5cec11dbf3
- d8e9f29a78ae1d061fadd2beb2a6dc35077c9db75fb7265223aff0eef883af3b
- 583cae2ec3c520eb83127902c05179d7a39386c8fee918189d002a77ff96d1e4
- 56d547e3782abdbc3ab7919a46236a06aa325b16efcccf4e47c2975214dca8d8
- f9b5c37565b822321fc39b93aaec1250cb81d90117d03dc2bc7b37d7af54f719
- e9b99263c1a5fd1c737adccca327ec83887ba04a3bb702d6de0901c6e84ecbe0
- adf5d59ebd7aa6ea3228ae1e9599a9acb1e4b26af186d41358278355ec4477c3
- a74a48ecdff3e6bfc48b3824b1aaac692533ea13bb65fa89efcd655c342f1884
- 328d8a37398c0153c76c998c813ae66a2997ca756d95e3f8906ed979e23ee09f
- b06c1b419768c522fa47e6759db6f23c3440f6720937734115dcc5025fd9ebb7
- 942251f24be282f2af99169c39cd059988cea53ec8d78d0afef39b72e88d62f4
- a287b41ae7eccfb67a3f462456956d4f0fbee61a65fd29f971b9937febe5b2b3
- 9f801cf83a0cd88498cff14d1427cb696486acd2be2dbe95adb8ca5a13476c8e
- 32883572e8c9e7de8c0d73e463fee2cc1538af56cd054588600062ca35f31c17
- 345b0b81a6450394d3e300e15e6bbb3c8c1dc82e3f62e8092dea84178b3a42a8
- 45d2a340dcfe13f12606d6aac7d12abaca5a9b5234311fac444d7d858199e179
- f9ea8979f46a38eab4bfb8b32115ba42bcccd95911cca18995f1d7b24f52f2a9
- f9aefaeaf2f4127709ddb7f72e10140c6842f163b4978d0a3d4bcb5459036564
- fd35ce694f24f5a5f81f697094cbcbd6211cbe3af27220fcff0d3f4b2783e8c3
- 9dee7d5ddf7a4a82263cf92093ffe3ffc7098707ca4941474cf44720e016006e
- 7c54f288699c0a7cd08d7c45e5119a19b9fe7d19ab4ca0c28e27a7a0710a0436
- 251c474da489fb64493cc8b0b19565f674b83bcd643aa0e5f08255ca31a2aa39
- 5f36cbd862d6dc3d824e3931b2e31e64dbfe707f38b7e460ac6c15fca4b45909
- cc9b98adccb100f9b3602381a457c1101993aaa1638a925de60e52e57ebbd145
- 68b1198aa4569fe181b2f11ff602c6203ecb95971e1d4ace65850c9dbf3d9214
- eedeb3bde71c2a1ae5a44cf6858428f0a7eb2924033c8a858a06d4864592d590
- c73a65c56f3fa00fb9cfa13f1175ef73e6f2acaf2ce223c9ac19aa0edd297d43
- 2131d57653f8fe6942348f300836146f8874ddf38a3b26b6be7fa56497f43e07
- 351547796c46eb7d2968c67c97da7449b44dceae50225683b281936039008099
- 36f7ccdce7c2d99f8ed1546ef13e021c6f119e1886786b2c4587d64944432642
- 3052c8b4543fd0453157deaddc1fe39e0b8b231cd6e06cdfd57b3105526470b6
- 62616e1241e3e6ac8bbada082a089cc640c364e3956a11e26d37ee5f9b7c69fd
- 1548fa6d5d5729cd2804c80860c4e3ab45ef86bea9768a6fe2a2bc298a1af8fe
- 4085e30a45421f3faed8b12f2b17c0c384e7efe8a70d97de209878a9b2a82025
Coverage
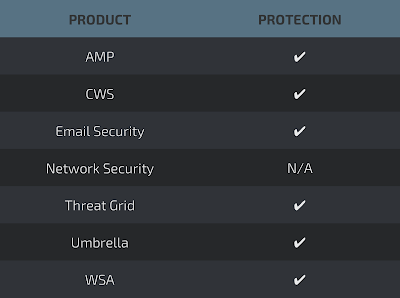
Detection Engines
AMP
ThreatGrid
Umbrella
Win.Worm.Mira Worm
Mira is a polymorphic worm that spreads by copying itself to several folders on the infected system. It can spread via removable drive, or by mapped network drives. Mira mimics existing files and folders (e.g. C:\WINDOWS) by creating an executable with the same name, then marking the original folder as Hidden. The mimic executables use a folder icon, and open the associated folder when executed. These mimics are easily spotted if Windows is configured not to "Hide extensions for known file types". Mira constantly attempts to add files to all removable drives, which can the operating system to prompt the user to insert a disc into empty CD-ROM drives.
Indicators of Compromise
Registry keys created
- None Registry keys modified
- None Mutex Created
- N/A Files Created
- %APPDATA%\Saaaalamm\Mira.h
- %APPDATA%\[a-z]{5,6}.exe
- %SYSTEMDRIVE%\TEMP.exe
- %SYSTEMDRIVE%\Program Files .exe
- <USBDRIVE>\System Volume Information .exe IP Addresses
- N/A
Domain Names - N/A
File Hashes - 0607f1b1550d5a0a83c486ebf086e773b4b8888a232c5908b904568fe48df73d
- 0714d79b9454cdd30ec105c86b4874e80cefb9b5e2a498d37a4d703e47293741
- 0adafcc57fc8abd80f5aef181cc26c00f38eaaa43ca155610a4075e245a31dc2
- 0b8d7697e15f2b569dc732234e71b2559955ada2f0b1773333ccc4a2505e81fb
- 17e213c496bc1c5886431b2d23202dd5f624c9deb9a931b74dee217348771f91
- 1ab7ec5423bcc0f4ae465c4a9bd777ba918508f39ff0ae4a0337974bc61eaa86
- 1d32e8d719a952f8cf0268a557e0b68133ba37b0af1227b7b13659c242a0ab1c
- 1db3d4d5325d41bf0d27071d9f5bb2155cad292c86524e0525848428b7f90a0a
- 1f5173db3b8f16c694d2c3107114464c683d97130854dc192e0de55b7680b0e3
- 226b1e4f69a14482406fbc2efedb9b214e35040948db532a77222dd467fc679b
- 2346e83c2f5dec1853ce1e2fa51ee899d48855159cb8fd33082bbc094edaa906
- 2447c502c06db3dbd681da38a1b41052466d73ce9a8a4ea2c2a13154a45da276
- 2becc2cfb65f07a29e3bb215fc132421fedc3d98670fb521d22e8497a11f5e65
- 2e35e03ad729e4cf90cfac130666d15913008ead179ac4dcd236e76e56ccbb7c
- 32794a8821773c068b1fbc378572c91fa8b96853ea93a5ba21f8a142b3a1d422
- 33308891d1612d1aa682a6b92a7bb05d0d75c9de4af493727920f1ec02fb2a64
- 333989555071d197a162f96b62f53499a05ee15e3b6a049941368a84ad1d2b14
- 34807d88e19560985575f0c2567d0652f96e8b736752a1332a715fa72cb60dfd
- 37d5751de744ea923584e3e4622e1add179c6d22c29f83105b983cab5f010c01
- 396f5001edc0c013ea746319ab45611b87486b8195ec24a986e4e2d6c16d7ae1
- 3a6543bb86cda6c167f2abaeea0c16f9de864ad7a3f7f55742cf076c7303303f
- 3cb38a00aea4d81935d45601b16ee361634b57b9076abaeb65a09e83cbfc92f7
- 3d7b25e97e08d09260416ecef6fd83cf5f3a70f44711892d9d1311a0666ae849
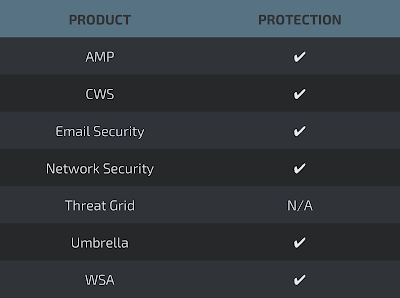
Coverage

Detection Engines
AMP
ThreatGrid
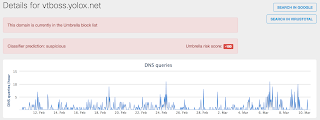
Win.Trojan.Vtflooder-5969619 Trojan
The malware is first contacting a domain to get additional data using its MD5 as a parameter. Once it get back answers it attempts to continuously upload a copy of itself to VirusTotal. This family is well known for collecting information and sending them to a remote server.
Indicators of Compromise
Registry keys created
- None Registry keys modified
- None Mutex Created
- N/A Files Created
- N/A IP Addresses
- None Domain Names
- vtboss.yolox.net File Hashes
- 00cdea7d7a2d92a332fc2910478e65115d926f749d8d348bb04757aff5e1c3f4
- 003fe1a731fd2fe5af17b8e7c54762a47130f0f3f70a767e2523b560d4098fba
- 0b43897829c6dcab5f3dc05e024733ec6b7bacc064c6a15272f2312c4d170698
- 3713f73a8c8aaab9cb3c02f0757283522f5046bbe263815358bda95bfb51c6ed
- 3a3730877e932b5d347e622dc0179c0eb5e561ab468b431d95b9d9d9a69ba827
- 41641fb06700d2fe01af837a4a5df9ad5938e46996471f0f95484ccfd3ca4c73
- 48e1dc63f2ec7633cd32dd728402d89be4056b8c70f35fe0b619b0d6ac8478f7
- 4b01733631a7f522d94d81b7e365114f5a9189de19399b21f7943d2ba7cb0dfa
- 4d2a2b3f62a99929f38239ce6265ac25fb36b0adc42a116dce8069d89948d28f
- 4dcde1782ea114aead7d200fd5565e96582441470b4e78612b69efe23f8d8746
- 4f835acf498699ab852fde2686af201985e02e081667b1ce3061c4fe77826942
- 5144d2f1b2edc796a74384240cba0958c6dfce05a3d33ceb3cf2f7a979b3211a
- 5b00458894e67137e0c3b711055cc0223988cda67060122ca57ad4a91600c4ca
- 61bf6b2cc57215c755000abb19117c6b7978d625ba54e6865c98066fa784ea7f
- 62b6001c8241155bc169863447444489b75d9ac0b9f1555e565581f5a06770f0
- 771569f8f32e2cf90a9574f02da30e9c103a40797f90330982333b11ef26500f
- 802f50a54c435d59e69e80ca5420316e1c86f86ae0d356c0569e0d4d8db176be
- 80f067f309d99d3388ee2ee0631d270fd891be0cf43e117b541ce04d0adcb8ce
- 9b0604d4f05fb0112edfd51d255a847af36ea2ebc43d2c5612d86b605b62f8f2
- 9f4a05b09c6cd960754e97d16c0aeddf057aac287ab7aed908eeeffb9ef11ffd
- a00dc97cdaa57dc9baf07d29d9659a1d9939484333dbdfe3665342e2db344cba
- ba259ed6c12120a60f14dee8393b2fdf105db514fdeecfe973f3c285e72fa917
- bb3679f23884bbe8598e1d1b7f78ae4decab004ac9abde0ab0623040e5cd6242
- cf14b28c6e8c4ac5ce3c95a27ba6ccf06ab0a19e5f8500486e8cb6b65e8130e8
- e21742cef8ec4034b619cbd181f2586da2fe526cc84ba969316e69fb76a9b574
- Ffd250866635598d34540049c570eaa51811ff798a8d6fffb613741339574c0c
Coverage
Detection Engines
AMP
Umbrella