Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 14 and April 21. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Win.Tool.MeterPreter-6294292-0
Hacking tool
Meterpreter is a component of the Metasploit, an exploit framework for pen-testing. Meterpreter is injected through a code injection vulnerability and resides only in memory. The component can be extended at run-time via in-memory DLL injection. - Win.Trojan.VBAttachGeneric
Trojan
Various samples that Talos have observed are polymorphic trojans written in Visual Basic and deliviered via spam campaigns. These samples have been observed creating autostart registry keys to establish persistence as well as injecting code in other processes. These samples also beacon back to remote servers with infection information and to await commands. They also contains anti-vm and anti-debugging techniques to hinder manual and dynamic analysis. - Win.Dropper.Skyneos-6192156-1
Dropper
This malware, written in .NET, is installs "Skyneos V1.0" keylogger on the victim machine. It will also send an email with a subject "TripleXannonymous" to a dedicated mailbox indicating infection occurred, where the email is containing username and computername. It also modifies registry keys accordingly to run. - Win.Trojan.Cybergate-5744895-0
Remote Access Trojan
Cybergate is a Remote Access Trojan that allows attackers to fully control the target system. Functionality includes command shell interaction, screenshot capturing, audio/video capturing, keylogging, as well as uploading/downloading files from the target system. - Win.Ransomware.GX40-6290314-0
Ransomware
GX40 is a Windows ransomware family written in Visual Basic .NET. Samples have been distributed via spam as a fake Windows update tool. Files targeted by extension are encrypted using AES-256 ECB with .encrypted as the new extension. Infected hosts are not locked down, but a ransom prompt is still given upon execution. Some samples request contact by e-mail before providing a Bitcoin address for a payment of 0.02 BTC. - Win.Dropper.Gepys
Dropper
Gepys installs a malicious payload on the victim’s machine, and sets the payload to execute each time the computer is restarted. This dropper can be used to install a variety of malware on the victim’s machine. - Doc.Macro.MaliciousHeuristic-6290326-0
Office Macro
Office macro code is used to further compromise a target system. Macros can leverage external system binaries to execute other binaries to further compromise the system. This signature looks for functionality associated with obfuscating strings to execute a Windows command to download and run another sample. - Win.Trojan.Fareit-6296798-0
Trojan (credential stealer)
This sample attempts to collect stored credentials from a number of installed applications and then attempts to transmit those credentials back to a PHP application on a possibly compromised server. - Doc.Downloader.Powload-6296855-0
Office Macro Obfuscation Heuristic
Office macro code is used to further compromise a target system. This heuristic focuses on macro techniques to obfuscate shell commands by leveraging WinExec from the kernel32 library. This week it has been used to deliver various ransomware families.
Threats
Win.Tool.MeterPreter-6294292-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A File Hashes
- b93a5e2c8068b84aca852899b119577fe3da77f4edd01d41ebc1c92abfbb8203
- e21ea550d8307956232df048f2623df436d0903666b257eda95962173100a54d
- 96c3e2c6e428ac63faa88de3970f50f95ff0a224698bd7e299bf7860b387d2f3
- 6dc3c45ba6aa3b8551843ef5e38c44b3b6c7d1bde0278948270157c676e82d37
- 59876794db1a73c00735d7c25fb206e4f5b722788f04d5143883f84d825546b7
- 29e5a7efb03ec69c3bc19756228e232d539f1b3bdb75b6bb00729fc446cdbf1b
- 148b6f924f612720619b009ef1cc35c060b0e8553cc403b475f7922220b19e99
- c8b27b261222a1d20c5e4d7d569e3a6b95ec763c4973e49d077816cfddf826ff
- ae52cd09f3fe264ffe9b1c3c4bdfba1dea47ba4c7306792c139d375373de82dc
- 9de9e23df4712ec2e496155fb4fb851df8976030eaff5c7e955fb4409604395b
- 02da7a71eb34ba11778c14599915f400a0f5dbd5f02a4175e0892ed752fef28d
- 0835abebef4c7c0a0808ab2168f1b58c0f6345160b7ccc689a5df2d95e61fa90
- 08555875425df997fa72dad869f8a7e389809f25cf90c1e2b4e659e7a0128496
- 1fbaf79cccadca652db1af811d52ea918dbde09518615510f64a7421f32abeee
- cc205ab2f88aea3a021dfd9472d6411d0d52a8a3043f992b225169585128a792
- de7939ed67925ca1c824d6b0400aa1f2bf6d955db4ce8becb2ae56403e729164
- c92a69d11c1ac5f7d209b8b42fd338ea4123e1dc16dc97f7fc06b31ea7ebb7b8
- c38ff8ecd12cdd6be79f76cd59c0c7a279fa51bf806a8cad8159366651b58103
- 43fa6fe9c0374e7ef960994e519868c22bc4115ae05ddb1ef17a972c4bdd6716
- f552b77831e3b5577ff40158e417fee5599931d7e3b4c17075eec47520c2b688
Coverage
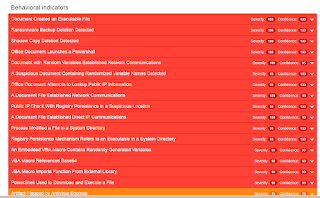
Detection Screenshots AMP
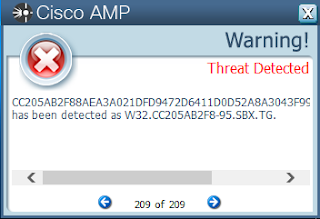
ThreatGrid
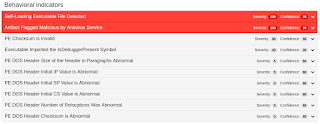
Win.Trojan.VBAttachGeneric
Indicators of Compromise Registry Keys
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run - Persistence/Autorun (NAS Manager\[a-z]{6}exe) Mutexes
- N/A IP Addresses
- 89.35.228[.]198
- 191.101.243[.]120 Domain Names
- css.alminvestmentbnk[.]com Created Files
- C:\Program Files\NAS Manager\[a-z]{6}.exe
- C:\Documents and Settings\Administrator\Local Settings\Temp\[a-zA-Z0-9]{8-10}.exe File Hashes
- 5514b9f92aecd3b063b3d922dee493ceca4ccfbd0d94b23e506f94c3acdad37c
- 2d1244bb024cd109e349968a79d0a4d2b9a0490f92f186f4b184326895b33b0b
- d375091524f770ee3b648770d9b250f697c5ab6ea64b8768aee9cc0feb7e7632
- 4bd4bf948e9a0911d21acef4f035145cfeeb76454809edf5675ebb5b41522e2e
- 754e2d75a93827a5be8194f12e2c28be91b06978c7e95cb862b68e67537c6e2d
- b95d95c662abdf6ebdd27c649e6d7d82801f1346f24cee5e9eaf8aefb63a7017
- d2ca3c2b3092fc0464c9553f4271aefeb869d1dfcd1c003b80866f0c0f5993c4
- 3ded24e864722c12ee193bf1481e7f52f901deb9f2babe915668480e02b66f38
Coverage

Detection Screenshots AMP

ThreatGrid

Umbrella
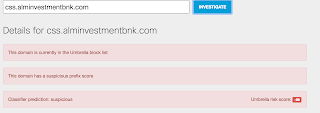
Win.Dropper.Skyneos-6192156-1
Indicators of Compromise Registry Keys
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run %APPDATA%\GxBArVz\WJrYnjU.exe Mutexes
- "wJFKrvS" IP Addresses
- N/A Domain Names
- N/A File Hashes
- 397b758eb5d29c3fa73fdb554431b91782e9bacec264c7a9fe23ec636b02c8ad
- 999040d9e578672b56d3af96b0794bf4943d706f148f551e31f4342ff8d74cde
- 61fdda35c17936282f1ec22781743d7c81838f9283a219826ca3c4be7c556272
- c295a62c605d59335f0dd2f5724a3fbf07c5b71173389be19328f4480ffa63f0
- 579f2dc6bb11b2b748b29b90262bf4e89d2c7c34ea5176904e43d67cecc9b678
- a6e74ddaf03536438b9a2eaf72d06a8e2e6f68d0a9c3656efb64883afafd1709
- 1ec5eb9ef00ac05b36ff81e4b176254f6028b9b6c1d7cbeb4f67548bcbbf5e1b
- 2e0fb62b32393f13120c8e3db4bef27794db2c96c8e1fffdd9bdd11eb182a9a8
- 3cc72f3decf89086593d0e862d2537f81e9f82f862725a1018de32be4c60df6c
- 19a286089d830dfb9cbfaf24f162249d25ec90f13ca180f5eb106fdb6bb3b36a
- 839a74407ba04a305cbe37aff2e755d46d5cd44b111e6028aa96f3f51b9a09ff
- 3ee15dfaa1175b574a8b49dfc13995e2990e97746e318cd132903b18a394eeaf
- 1bf7821d9cedfd63011f9e9db40bad4153ead19891592ef94d5f997059f1c41a
- 59dcdff902ba56fb6fd3ba7720333e4b95c1fe11199152fb1af70f71da248904
- e5559bee38107824f965c228496b74e1e18fd34a79a405f51ea7062bd923449e
- f7549cc0889a19fe0619f0cb9545a7c15e3e4c0b57148fd9919be96c032203f9
- 032bcc041d877bbf957df93d22390a841700789e46aa2d077cd1db4f2e01e76f
- 9127163c4c6b96ed1dd2eea39f8fe55d4b3be1cb2590a53d1b454ee93124c4b6
- dd8b85b8717fbc0d0579bf5a3a0e526648bf9bedca2bc50d2192b9fd2efa5c4f
- 0a8151ae2fe8c73935df6986243a8f04c6d7de17ddb0f789c753a64ce5d759c1
- 20f554732e030e8487efa57725ed1bbff5ff44249da04b41ccf42f099d1ab908
- c798f885e301a61ede7b2a479c3b75bede7783d3ab602d65ec352e052c2a24d7
- 4550b5aa76408a448a11f78a2820135a1f705c21ed47a26daafe9453c3a93e38
- 9cf9084351c33b1b68131bcb89cbc19b819b8b2b9dcc3e4b889ebac1bf0858af
- aab799820d4235808a6508f67fd226bb0fd4e87d744469cd1c582f45dd213c88
- 384a2a36e466f93a66322d727823f5dba1a477469978116e6a84f9874de00dfe
Coverage

Detection Screenshots AMP

ThreatGrid
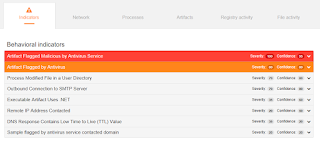
Win.Trojan.Cybergate-5744895-0
Indicators of Compromise Registry Keys Created
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Name: HKLM - HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run
Name: HKCU - HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
Name: Policies Mutexes - ***MUTEX***
- ***MUTEX***_SAIR
- _x_X_UPDATE_X_x_
- _x_X_PASSWORDLIST_X_x_
- _x_X_BLOCKMOUSE_X_x_
- ***MUTEX***_PERSIST IP Addresses
- 187.32.137[.]66 Domain Names
- theprojectxgm.ddns[.]net Files created/modified
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\XX--XX--XX.txt
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\UuU.uUu
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\XxX.xXx
- C:\WINDOWS\system32\install\server.exe File Hashes
- 684a4dc6bbd6b006e1976107a67bf6e7d7644a3258484c99402ea619f7f2a616
Coverage

Detection Screenshots AMP
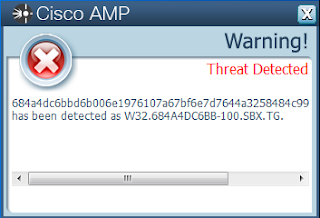
ThreatGrid
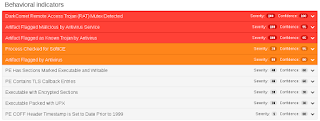
Win.Ransomware.GX40-6290314-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A (domains resolve to virtual IP's in use by web hosting providers) Domain Names
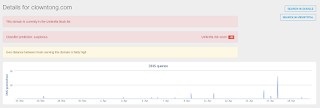
- clowntong[.]com
- Ganedata.co[.]uk File Hashes
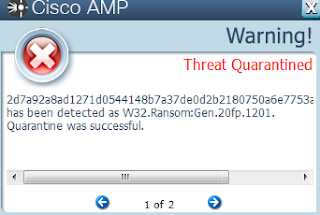
- 2d7a92a8ad1271d0544148b7a37de0d2b2180750a6e7753a26f97b801c369fb4
- B6cbd7f5f6d9946b27be877ab5bd8205f64a4155ef202694dc2ce9fb2981c18d
Coverage
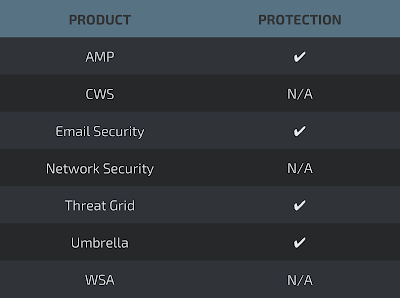
Detection Screenshots AMP
ThreatGrid
Umbrella
Malware screenshot

Win.Dropper.Gepys
Indicators of Compromise Registry Keys
- HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS\AppInit_DLLs
Value: C:\DOCUME~1\ALLUSE~1\APPLIC~1\Mozilla\[a-z]{7}.dll - HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS\LoadAppInit_DLLs
Value: 1
Mutexes - N/A IP Addresses
- N/A Domain Names
- N/A File Hashes
- 50e9012ae2bf0889f21914acf507a91164df7f7afa3faf87e056ec399262198c
- 2e3462102717bede243945fcb442d5fedabec308ee358a4d47782362ca4aa06e
- 6428003415cc2338ed842909d930bf16648737f9b82af7802aaf0f6c25df66b1
- a8294b03c2de716d7c186229d80fb6f5739911e365ecbd13bfc9156e79c2c3e4
- 8689ac26e1df50fa5769327042031172820ab34d74caed21b9156923f57e1bbf
- 91b1a40f59db3af84c4a2bcaca1a2f55a4622e8b42f1ec0675b7634d6b4a932e
- 554f21359d5e804135cf4f325d6ead010235622a81f310e690538065ec2726bc
- 31da4ca9abf91af1b5eb5e3b8ff7e046a24bbb56fa3128c48742f47873272f65
- f53e78c57cdae3d01337626d38c1ec9d2566114f3f8d3af3da54caa28738edeb
Coverage

Detection Screenshots AMP

ThreatGrid
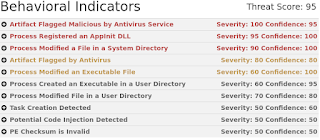
Doc.Macro.MaliciousHeuristic-6290326-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A File Hashes
- ea8fbf51c26a4bf0c2c09c4eda7dddd84c19a14fd86028e2491a012548aced61
- 82f052437c190821e209508f80b1c22f982bfb16bd5f8dd9bec9371ac0d1f9c0
- 4d41f39368c70cb30329b46bddc61d8994590e12ed7c4181f82f5d3f90442efb
- 8ccc7718cc590a00857a7ff73a6c8acda01ac7b8460c179e514eff3fbc658d29
- 415e1d148165148bd9f9d4312e95a685ceb16640e2f3e99171af19d7d06a58eb
- 88a37526f9769ee9ef2cdd4a98974f17284ff293f29131ec7cdd3b3ec34ab076
- 3ebe2e91598125856058fc251594864936f28a4dc0c173f163f77532090e751d
- d4d73c48982729d1b8baa017c250d25302bb8d57eaf84f802e612d2f4d0533ff
- 1ce183c58bf4440d6928b299b4c6ba20325949dee7c2d103a1f81e716045db4a
- 43ab5ad6cb9d059ce1f745d80f45749b8d3b583bf2e8ef4e5a737cfb8cd920ef
- 9dd198863c3e54750fab21ac6521affc9a1dac3124fbbee6eab8d58aecee26bd
- 20b8c96f5ebdf2fa2ec337552a8b990bb04706b47872a6e6f57141885c6627e6
- 7767aad9c2b271c58eaa9bc69a4d02788c8f179690bc62eb50c0ce1e01a28093
- 07b70b5ee017779746bb9d429684cb9f6cc892b43364db00813a0dd8c78c94c4
- ac13f9fe491790e443557df4b43b0dee394a556493940de8544dccf21d9f4468
- ce4374e2bc2852dfb9a947d3d5a450c9882f78c7a2cce9bd9bc38c52519c0f5a
- dfae08da81b55aad202cd4a58a03793dade7670c489466215fda8889e78c9257
- 5e16067776a303af01c7b07edb1a9ed1c704a836b52a86be9b4331d2f1337727
- 0e78873a05f6b38784d3046fa474e4e2ef5cd8ffba224d481aeeb861445140d2
- e3554e7023a05caed3f5cecdd14bde1f8bff36ddf5fa6655f05394f5874cdee3
- 84f6eaa6667202884b1f44e188f2d32da28d7e94aea45c1eed2c167fdf0adff9
- b09f8f8cd3310f52f0be8fbbc06fa4dfe320e01809ef029cf0bf834c9ec30e46
- 5464f9a1167e2262f229b43e96cf4398a68762419cb5b130b62af7bc5c81ee9f
- 95fe51428511126edc0405420fd8dd130668558f678ef2b15acee4123daf77ec
- 3a8a64289bf5486bf4ad9cc7e2dac095e924dd9c91f28b53b4733af62063a586
- ef50419714e8bbc98855570dea4841fe92b87af93eaa2dcbed9443195dbed565
- 9046275b47f332504800cd9427f32a729babac0fc47e987b99947e2c36720271
- b2d970b4acbc75627355562e21de446c9c77c1e9664f0cdcbefd65947a98286e
- 85b0a49b0b04bb75e1fc7fe0600170195982e88312a51f61b87c795380d0cb27
- 5be9d79d1a933264a704cfbfe547fabfd00f5729a69056a5eae3af4907a19c05
- 32d3690ff19448cba8472963eda694168933946ae667f175ec0e36418af2b656
- 533c687050b73cb187b6cf2fa5638d4bc775f7815c5c49070f93f60714f615a8
- cf2f1603fd0f0160cee318cec9dda36c9dd016b0aa68bca33010a7b8114327db
- 238668f1f9b65de23d738c101f49e3daaf38af67bc3a799e8449844c008d6e0b
- bae085920e1f9e860d81a8b05ef4339e51c4e7dbe1a4877daf323f783fd66693
- de875b6a133e995fa40b82e6ed0e82a618b46596114ab818cfbc3074d675c9f3
- 1ba3ac6d485f56467096ff921fc3291c9f29e544f26db29b41db7557f234fbdc
- cb145d2bcb45fdfadde9835a625a35d4211bc9fe7a2570e6a895516ae92839eb
- e9677396d0f743adde90fb25e83ba96f3d080004d3974dc88440c7a023a050a3
- 36d4d582d371baff6b8ca10c22bac318012665045283fe5c76da1caa6249945a
- 56b9ea97db50ea45ceb0a60b28a4964e93f5eff91e1d8048a6fb3d1182a18824
- 6c23937fb1280d15a7fa631f30a7af9daa667973ed40ed8952f0b9cdf9711bba
- 8d8fb5aa93d435834cc6660a795ab79f00f2c5b12a5ddb7fe043576cd65c4903
- 8080348ccd9330a532af3f3aca0bdae15379984b7063db5d9427114b045fcc32
- d75b43df6ded6c683665c7ac5cb21607cd898b2614988bb0eff9565cd33b56ef
- 5e1117f72ad7da6e62a73a7038e5c619631fc97612632943da70e3b1f08a8614
- 18932143798d8cffbe4fd93e2593f6ff7a92e30fcbc85b181b08eeb1dd227c50
- 9559c2b404c9006ee4fd6d68caab17e0191d98468031ff67c0a2ae29dfb8ddea
- 5c8c09baf59378e5868bc3b69039aa2ef30d5bce59907f0af53a6dff5ede012e
- 1ddbba660d6bd0db2411cecf7ea02989f18653f3f8fd6007a2ec6a49ef7e044e
- c566ab01110368bfc7123389a5fc77bbcbe0760f57e0981621bc0eef13bce5a8
- 0ac1c753602492a9eb9390daf7c6ab644155f29e32b32fd5b5792c17c251d86e
- 797e7d7b1b113665481cac3562d685591a44df06b2323b4371f3ac14415308b6
- 8ec6a7b8a22a1c786d9dcdc89b16ccd70e1a91ac8a2a11cd8b4d413a116879a0
Coverage
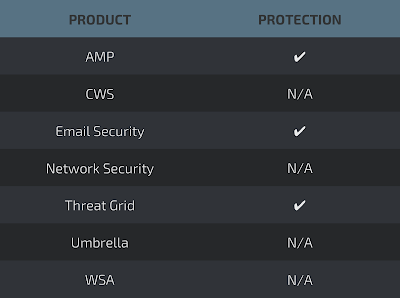
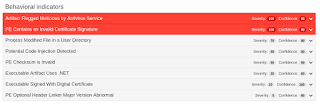
Detection ScreenshotsThreatGrid

Malware Screenshot
Win.Trojan.Fareit-6296798-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 5.153.47[.]230 Domain Names
- dondada.acurdem.com[.]ng File Hashes
- ce405ebd2475244959da62f23f45dce072a7d2c13bf08c09ea34d6a8d60ac49e
Coverage

Detection Screenshots AMP

ThreatGrid

Umbrella
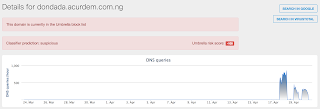
Doc.Downloader.Powload-6296855-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/AIP Addresses
- N/A Domain Names
- N/A File Hashes
- 0039b96405d8827aca9232f7bb94a5c71a75dd5c965cd229b22458ebb97911ca
- 02abe3625a2acb2e670cfc36f7a4f1d82fbe61ff1fea9ad5ec5096f37ccbfb70
- 030ff53ce613c122f12fd7569eab3ce8364080c62fbe508ccc974ef9342642fb
- 0491be85530667942df61a503c92146ac9b46f7b0313c920fa22de66a603fcf9
- 051afb7fcf6222f23d4752a84dc5940ed0d0aaa42f6ad13c18891196792c6456
- 06d4f59d6613c8710f920ee40d24a7259818def35905c624097b5ec65535feaf
- 077fbc7279205df5108eb9f86a3dc89acbc175bb7927218081de340162049d23
- 079cdfa884bea9771ee7c4f28ac70a658ac9782ddd62ab441ac7bfc3489cd873
- 07b045365e3608f3e3086bf7efbf826eceda05f8c5d30e36737ade5f7cf6c3ea
- 0936af07881f8656370603ffcfd0b057d308036e3444c38fa3f653990545a0d9
- 094acc57fb5fea958dc5be48d809546bfd38cd69e3bac0f3b5cbc6c04b0ab854
- 0960b6a40b7a4af9b0cd3636b7ace16b61909beb4fbb69b04e20f0daf4f612ea
- 09f795f22dd14bd06f7f4bac5ea3c58342410fc737797e6f57c020051df18274
- 0b8ac08140a7e02dc07a16210f373291072bbf6117e5331c799cf403b13c431d
- 0d27447dd3fc4f06a213a1076699b83df36723888190a521f863e966214c7c08
- 0dc7b93f915809d75194bee4a9674cdd328bc0c39a554c06c6062b7c6e6ebf22
- 0e8713ef446741ccf60d854d604dc5de66a73699745a6bb818de9fa624b001c0
- 106bee1d44995470a414cbbfff03fd71f8d1293d737f85ddc417df80cb3fbf19
- 110f982d95a3f7691d312852b34505407fcd84b0f92d931e699fbf0cde7459c5
- 127e2da8450815f2568dd0e3d0e6fb567b2b2bf661bae9ab1630976c4850704b
- 1349c9c178f7d3e92e577661917c376a8bf98b4d1ebcd66f2a211366ed29c23c
- 159f013169e83d8a1f1dde7536766ac398ea29b5394ec592da27ab974d528658
- 170af256b8d1ffb867075ecefbd03e9f4b55539ab4359d3bfde03a9edd575257
- 18da3338acc46e910909b45b524d20bbbd1e5e158943c6fe303373e7bcf53588
- 1aa3369ab9d458e5b8a45b0b9ce30946aafaac7d409ccf9767c7c02d94f099fb
- 1b8511f04d8b6ad0b4bbc70f4d641f6200edde4cd6db5b6011026372538fe361
- 1ca749c7aeedc86e2884f64041ed67bed5e618cc79733ca932e31a893d2763f2
- 227379a1e5dd52d2767e1b39f2bcde391fcacdcb102edff5e8850d01a06de175
- 23af47d6ca64082566f6674e7330ae26b891afb6ee8491da991241ee4bcc2610
- 252b68dda98ca46e5ee2987870f69dd300ee055699597fc692389fb19fe1d36b
- 26c5dafca0d786d46d84a2e1d45425c4db58d6f714b28bf5874e205c5c0d7f59
- 277c524f46c02c613219971445127f83b5df38a5256ff02ed9dd77540244ef7c
- 2b3540b9f5b6a4565af3a46041d5349157ddb231be7549ed3bc0aa45a0c3d027
- 2cbc366467f9fbd1b15f89d0310f079ee1c2dfb4a6b8a8ecc1ca305af4cd48f2
- 2cf059d33afc0e4ec2fef33143cb35f71ca5dc1198944b70c7483ed9bbfd3f24
- 2cf081278bbc033b39d7db71be4f73918047f795d09ac5b080dac81817b63c9d
- 2d339b0cafc46e90d44f654d4ddd6a4cb63f49e948c88a14aa8170988b93e299
- 2f1c3767da55c730e7953e3211b9e55633d9e5cd4acd20bf0321ad38a6f1406b
- 31be9f322e520a47744e19bd3dd994581111aaa02532543c5df712d864448626
- 330d4427ea82ef90565c815f7f84263d4a73ae9b3418e371f4d3903e0300f8eb
- 33310bba1c3b525385e422221dc3d4ea94dc0d034f436a72b6cf9256f8db4913
- 33ad98d01e9a607be3ccc82bd3c2b57bc5fc0882783719d00effeff64d55c722
- 3482fd6b720f33fac957070682c423a3fe1562e18bf2d65ce85eb8635e3cfd57
- 37fc4a1534288a0afc74f9143b6afa94cd566cc04129fffceb2cb29d8fb60ad9
- 397ad1783d16f3c53cc97882b3ac79149f4f752b8e63aaf1f8bcc200b24919d6
Coverage

Detection Screenshots AMP

ThreatGrid