Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 02 and June 09. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Win.Dropper.PonyVariant-6326202-1
Dropper
This dropper launches some malware possibly based on leaked Pony Loader source code. It attempts to avoid detection by injecting twice and deleting itself with cmd.exe process. It also contacts compromised WordPress websites to download additional files and attempts to also steal FTP login credentials - Doc.Macro.Valyria.6327969.0
VB Macro
This detects the initial stage of the Valyria trojan. Detecting the macro used and distributed in Microsoft Office Word documents will prevent the trojan's data stealing capabilities. - Win.Trojan.Loader-6328419-0
Trojan
This malware is of the trojan and downloader family and installs additional malware. It also looks to be able to perform spying operations. It's injecting itself, injecting a new explorer process as well. It's containing a lot of anti-debugging, VM detection and other protections. - Win.Trojan.Sivis-1
File infector
Sivis is a file infector that will replace any file in the file system by executable files containing copies of itself. - Win.Worm.Fadok-6328944-0
Worm
Win.Worm.Fadok drops several files. %AppData%\RAC\mls.exe or %AppData%\RAC\svcsc.exe are instances of the malware which are auto-started when Windows starts. Further, the worm drops and opens a Word document. It connects to the domain wxanalytics[.]ru. - Win.Trojan.Qakbot-6327689-0
Trojan
Qakbot is a sophisticated trojan primarily targetting personal information like banking credentials. Read more about it in our blog post. - Doc.Downloader.Generic-6327950-1
Doc downloader
As document based downloaders continue to remain popular as a preferred method of delivering malware, we continue to see their obfuscation methods change gears. Recently, we encountered a series of Doc downloaders that used two scripts to download the final binary. The first consists of an embedded macro that is used to remove a widely used obfuscation delimiter & write the resulting JS code to disk. The JS code is then executed via WScript.exe to download the binary, but static analysis remains deterred as most of the code gets processed by a string deobfuscation function relying on single character lookups from a master string. - Win.Trojan.Keybase-6328970-0
Trojan
KeyBase is a trojan that can be used to capture screenshots, keystrokes, and other pieces of system information - Win.Trojan.Siggen-6261194-0
Trojan
Siggen is a malware family with anti-debugging and anti-VM capibilities to hinder static and dynamic analysis. The samples drops a file in a temporary directory that is deleted once it is loaded and the second stage executed. - Image.Dropper.PhishingLure
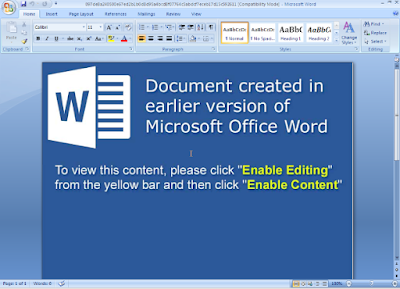
Social engineering document technique
These documents display an icon and text lure to encourage users to click and activate the icon. When triggering the icon the malicious code is activated.
Threats
Win.Dropper.PonyVariant-6326202-1
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- /images/wp/wp[.]php
- /wp-includes/images/wp/wp[.]php Files and or directories created
- N/A File Hashes
- 47c916890c345a0588e52cc29e6488b5c709217823b0049a46b9a9e5e07a6efb
- 50733aaab0b6ca4210df15017f51bb576c84fea2cbeb0912dd40a32056cd3c1b
- 4fe60f488f45f914edb650cc2e248d156ad8b257b610ad4848b1c245f38053e3
- 24558ad4b3a745c24a2dd42c73800ccfcd0c10dc17c67d83f3dcb3a4e479d46c
- 21b260fc6d38b2061263f66f3efd71116adbc75b95f57d424b079ecc1c4e5a02
- c35c5adf85410ad3a90804dfe053a0b6f53bef8c024898361a6c931c3598317e
- 416d71ce82336aa2dda064e6ba93a555ccf46c7ae2ad1faba379513965d9d485
- 81ee12d8f93c5b7574a1d797261f275e9b61f5ebd73ac836a68df3a18ef31c93
- b42d5092e2fa54a8312c4f534b9c1d10ff714241a8fc3e3a3f44c8870a1fdc4f
Coverage
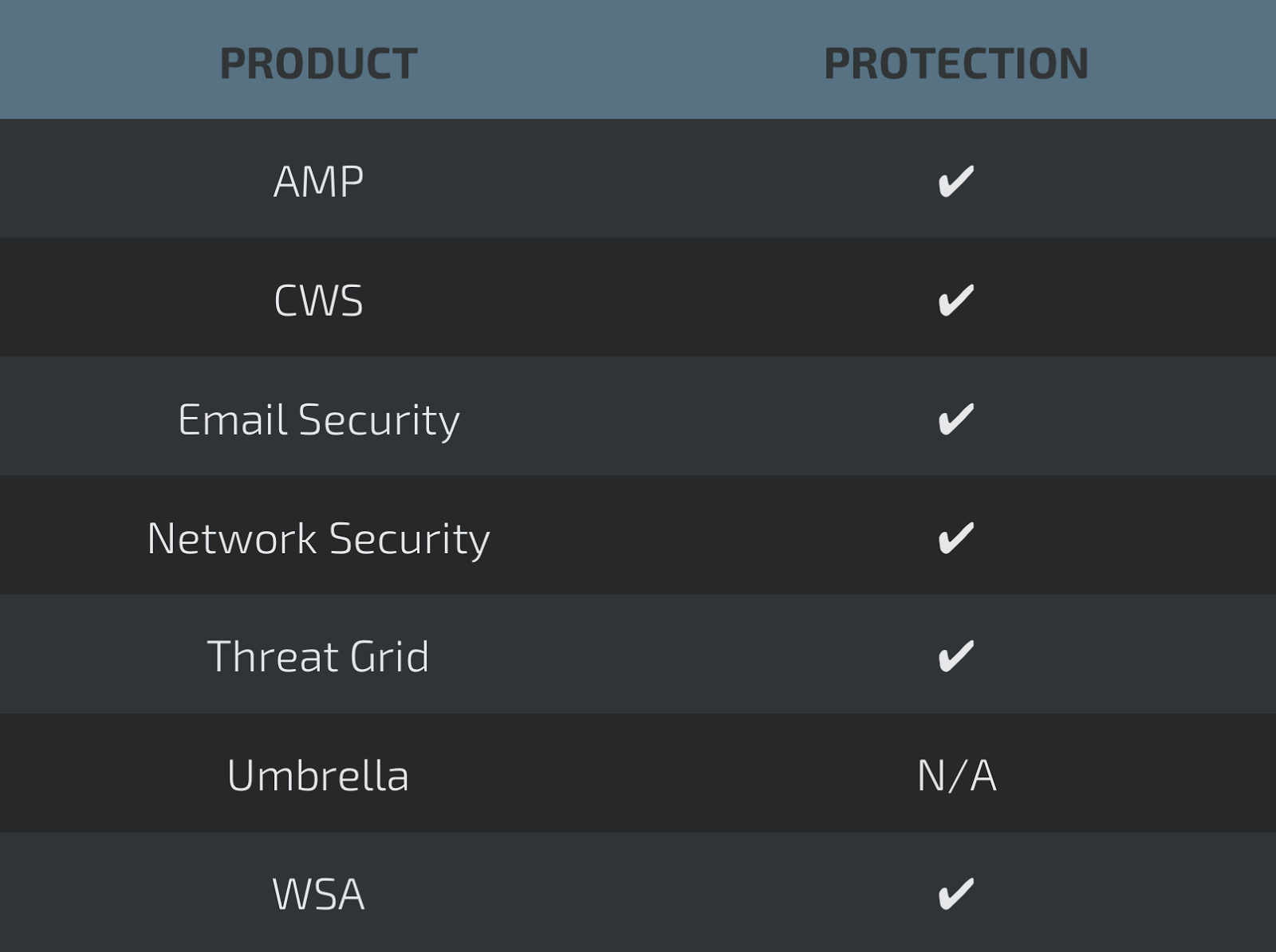
Screenshots of Detection AMP
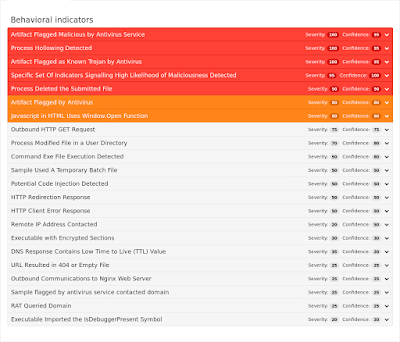
ThreatGrid
Doc.Macro.Valyria.6327969.0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 185[.]165[.]29[.]36
- 52[.]173[.]193[.]166 Domain Names
- N/A Files and or directories created
- %TEMP%\CVR9C14.tmp.cvr
- \Users\Administrator\Documents\20170605\PowerShell_transcript.PC.Wu4ufN69.20170605030528.txt File Hashes
- 097de8a240500e67ed2b1b0d8d95a4bcd8f07764c5abdcf7eceb17d15c592611
- 0cfe5dfa2b53c51076a5ea1aac89e7be91e83a70c6438b037dfd00ccd839ca6f
- 17b965a0cf6b0b316da2c659ec2c7bbe747819d09c1c1401d5a80272f47b813a
- 1fa78675658b45f99b1799c11681b3f5b7ec09881f3f600060576b4b0a74a65e
- 2378d2f333b50cc341e08f574d300ebcf12ee7140cb897620bc9c35f93929854
- 24384267829131c7158c50c109afea6026d327c65a66ef559a6540c2c8863094
- 2669d31701a90345db7492bc3de46db51af6a9137ce1bafdab2fd3122d2e040e
- 27a035174244dd347ee81cc932fccf414b1c32a0820fe6a55e242ee04e9c0686
- 2a3a0eea64d407c04bf65c3bd1b22c4243435d8b066e44011d1a9904f0f644e7
- 2de9f4f8df35ca71c1738d22bfb6a147670c25dcbe2014cfd0870a53e33f385a
- 38e71cd7dba75c6e6dbfa326843d10421d57ab3781c94c1174cfc260c86d4361
- 3d93b69809ad4d6cb2866583c7fc0144aa0db167fd4940ab17b3252c809bf1d1
- 3ea1c668e2b904c00f60d3bdd735a31261c49b29a39f2523c03271328a69c580
- 3f3adeed33a1a057f697c49f9d776c27c7fb9afb7cfa62eec2936ac24ae0d19d
- 4914a3125bf4d54a07ade2109325a324f813c500a5b6e8a2781b7c1876671455
- 556556a774b187d2068e8d6e4cc2d098fd06fe146e0b4578b68a602d9b9c47f7
- 56e76f857ba0006ce64a71404b3a5e0166659e069c7d31d488de248e3e8a7af4
- 5cc180f858ed3148aad169790640664280c4b908867256f7b1a0718575192c78
- 67e2d24be65f338f944eda6cffdda8013147088a8173e771795b399c3c182771
- 6b6221926ec36c928f0d0eef2d254766f30342714c3e791645d97c6c86cec31f
- 73b30d45b7f7a0893f8d8a1b3b55f10ff9d11e86619dccbb22a60d1f2462d5f6
- 7cc61b02a664bfdeb11daf0dbb6f7bcfa2b07291b4ba3d25e902850a76f91ded
- 7ec2376443a777c789d853489ba4192ff21923ab95f4810660faad4dd93e0813
- 7fcd49ea71363a666377a734b80c7608842a9acb868e1b35a3820a1eefd68975
- 900f2319a95ec33f4c42a4ceac088f0ab940aa0cde64c4da186b0322746d3e36
- 913b51d636924dc67655ac2bb69449858448f71363eafcd3cb7881da3fe12994
- 95fd8ea6a9b5778a75b76804ae8c1da2514239598edd1c324f25eb30a93fd715
- a3905f5dd2e106d19e260b36d9bdc7946cc8aae0f4343e8d6c7f671d0bdc7921
- a57fe946d0e6d5324080ad9625ed5f4cc2720c53cfa8dfc4185cecc9320c8e45
- ac1803de8dea5bca07b2eb654f0ce9b013285686014483e6c81ae7235b68e1aa
- b08b5eb8f5ab0a2fa8acebaf86bf48653f38b7efed83d88ba6076f0da4af9ace
- bb4e1f338f6d5c46d7890aa7eabe929de1467d8760a463c74379d651600638e8
- be53a9f3aeca760dfcea58b676db1f687f238e0c6996ec57e36fa6040f43e75e
- c3ffe88841a13a6222d667cb7aca8e0d77215b875403f4865ebf199ef64baf9f
- c571b06649be9a8d07ae380a7131dd8deba1bee2aa7067557857fee8cbd2c130
- ceb3fd6d517aaff2a122df2f9e8ab368cbf1efc8644344d4f228198e90c56399
- d6d05984c0d493eb75861c7d56c2cf649fcc912134e7df2894fc8bb3eec8980f
- d845e07f961afb0341e8d8da25fc08896bccd09ccc5136e74454308c9f95eff6
- e618d44cf1e7d121c9e934b1d530ebc4e830d1dd7d8228ac5b53a455def791a9
- e90846bb4883914000462df105e679bc4ad05d3d1b0900363dd18eba1aca5c33
- eaa3cb0af249967c7d9a66185db3cac7e93196da6281014206b6d0bc0fb7f34c
- ef6269b66111c365ef251e4128a286e16c972359ca406a02b6f81fa8b55b1cda
- efb1be187c1b7cb674f6912ceec3301da0cc5c993dc3d7d47f4fa7b9c5e80d1b
- f6650409983332866425e807dedc231b28a7cd3a468fe9e17be029fda17efe15
- fbdee3574019ef790ca4609c0414bf63da402c051351552e3a24f4e325e494e2
- ff9b033e0f4d48b6f77ae849cf3a94ea411583ea8c232b1da6fd1bc99d5e40d4
- fff62aadd6740b7c1a4b57758f95d5de0cc36e471e6d1ae40ca8141a5845a7eb
Coverage
Screenshots of Detection AMP
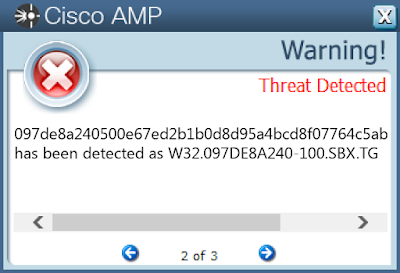
ThreatGrid
Umbrella
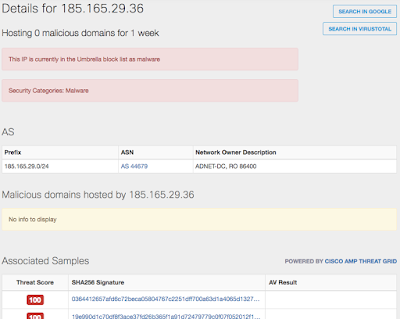
Screenshot
Win.Trojan.Loader-6328419-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: GITSecureService Mutexes
- LoaderMutex
- Local\WininetStartupMutex IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- N/A File Hashes
- 594e51c5d358d6a691ff2a80dffaddff77c9184ea072e415138c3d41b7c265ca
- 70df78ea8ee5f9f4561cbb595ca7c2acc982b3a0b7f84017a803e2a0d0494c5a
- 47bf1580e8407e9825d40348143ee14bb3f7458c32a367ae1a25f3a33a643a4f
- 503e751cc1c67c0688e92c28e4565de1448756443fdec4a638a019bd63816b33
- f228c82dcc233e42f098ef132796985e7e69ab0294e348182ed1fc79f9f49808
- 6fbf8a11f59e67a96bc1f6afd67fb4b5213f93ca15d75e14bc3b99ca5af37a5d
- c703896a92a7912a109336d28dec6dfbf568f8da63c635206d85c72fb2c4aea0
- 5b5de2fa244760de8a1a301347ab7a646160c257628f24f19d5072ba8d14d3fe
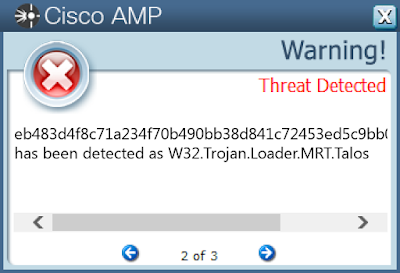
- eb483d4f8c71a234f70b490bb38d841c72453ed5c9bb0049d9affd2afe41cf23
- c8f06a449c4ba38e5f49b188fdddb2b49a5e7dc8716aa1f220c9ee40b06013a6
- 6ce02da8b29683da3c62719959522227598d38f3fc7eb056807c0fe83f051720
- f99385fa291e583b905bc5880a2d7a8789e9ac12d377beff7ab6afeba26f087c
- 859cbf1bcb8a1d4b9862e9da10b0e7b760c249ee83b01ae93c72176c021693f5
- 25a60570b487f02fc57962f8fbf1d859f5cff0f8b47f01e57c7ba2d9c9a3c990
- 23b62deaab5754b330be64cfb4e784cf2ac328356b767bace69a391219d577a5
- e9049130d4cee840324995b87d605672570c19e7d3621e1fd639b640876fa575
- 77b3f7eb328cb5f503bee90e65789a78be85a73977ecdaeb95c558d7bdb192bb
- 47a17129b7c2337735cad5c8f9694fc2ae5b344a0ca50647c8a5884b240a8587
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Trojan.Sivis-1
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- \Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\8HMRCBCR\menu_bleacher[1].png
- \Documents and Settings\Administrator\Local Settings\Application Data\Mozilla\Firefox\Profiles\z7t0o5cs.default\XUL.mfl
- \Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\8HMRCBCR\resultslist[1].js
- \Documents and Settings\Administrator\Local Settings\Temp\KB2533523_20160610_170929140-Microsoft .NET Framework 4 Extended-MSP0.txt
- %AppData%\Microsoft\Office\PowerP12.pip
- \Documents and Settings\Administrator\Favorites\Links\Suggested Sites.url
- %AppData%\Mozilla\Firefox\Profiles\z7t0o5cs.default\extensions.cache
- %AppData%\Microsoft\Access\System.mdw
- %AppData%\Mozilla\Firefox\Profiles\z7t0o5cs.default\mimeTypes.rdf
- \Documents and Settings\Administrator\Local Settings\Application Data\Microsoft\Feeds Cache\YB1OPN1Z\desktop.ini
- \Documents and Settings\Administrator\Cookies\LJOW70BN.txt
- %AppData%\Mozilla\Firefox\Profiles\z7t0o5cs.default\content-prefs.sqlite
- \AUTOEXEC.BAT
- \Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\8HMRCBCR\view[1].txt
- [...] File Hashes
- 38f441a14f81c370d0ac0934340d3d196bca832668ee6772ac88330614a91b2c
- ccbf43a2ab8074ca4a27952f0f3c052435ffe38cfa4644f63b609f96c978c014
- 0a08a78e10ffd4c2e176e089e092f3692b94da97457abcfc694082c525335fcf
- 0c1170f0bd12ecd8b4a507755dff78ea47d9057129d5ae09b2af82287b43664d
- 7366a0faef62af909a1ef1da05e2cbd1fc9534cbb26e20e90538e043f4517d5c
- 4e5297e0d0b8c702e6c97fbaeee1f329b2246a046790e0e8adb595f94accf47e
Coverage
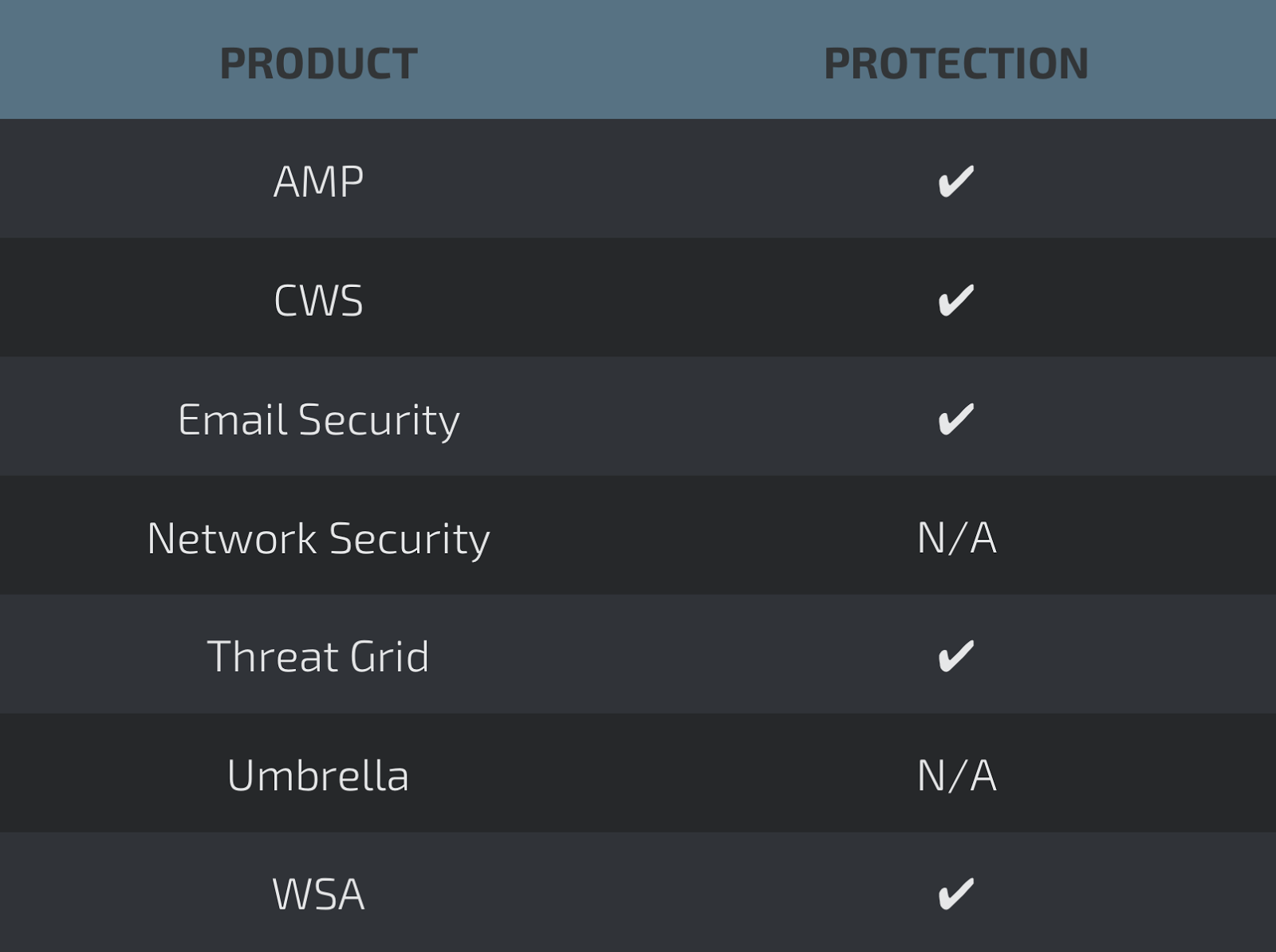
Screenshots of Detection AMP
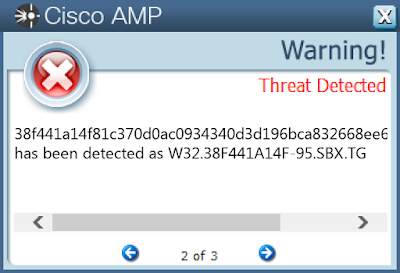
ThreatGrid
Win.Worm.Fadok-6328944-0
Indicators of Compromise
Registry Keys
- HKU\Software\Microsoft\Windows\CurrentVersion\Run Mutexes
- BFA31D7B-D1D1-40D5-A90C-A0909FFA0887 IP Addresses
- N/A Domain Names
- wxanalytics[.]ru Files and or directories created
- %AppData%\RAC\mls.exe
- %AppData%\RAC\svcsc.exe
- %AppData%\RAC\svcsc.exe.config File Hashes
- 03692f096e7fc9ab6bd470f7092ae80cc5dcfbf1dcb2a849dae2a2384e421315
- 04c679e80175039e07cbbd0b87a9877c297ef7e18d117f8dfa7c30ea42f78de1
- 056b0bc81124cf9ad6c094092e1f16f2aa96bf7efebcaeaf3830a8a228464a9b
- 06f89aa03b2e1f070b9fdfafd5356d0eaa1ea840f05ab7189d89f1cb1f70ff66
- 093808faa41383f1e3d33fd8a2e716fe4c5b9388bd42548f5423e6b5ff62a9d6
- 0ab690ef09a14798b9deb6cd0c116b8e0ed906b6bac16a05a5ae4bc38cabf467
- 0cac66a5a16efe52e2e878f5e8f6e34749e049c547ecf18f54955141e13e7058
- 0f93142998d1c0dddcf008b167f9611e0fc46539f50a35faf8266d71d31ad3e6
- 0fffda2d0105f10690d1989859deae3d50287474534649605a320f078616d658
- 148c4618e14a3c30f73dd6f910df6999ea4be2e32818f3747bdae03c175b7c48
Coverage
Screenshots of Detection AMP
ThreatGrid
Umbrella
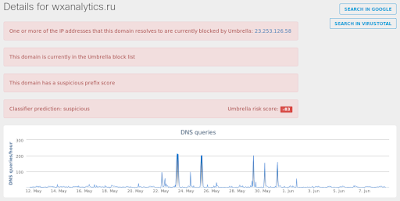
Screenshot
Win.Trojan.Qakbot-6327689-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: kddds
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\DBRNOCX
- Value: DisplayName Mutexes
- wawrtxtguelkunm
- \BaseNamedObjects\Global\uhtvtft
- eioigs
- \BaseNamedObjects\Global\ubrjqsxr
- knsoonoa IP Addresses
- 204[.]79[.]197[.]200
- 104[.]254[.]150[.]79
- 52[.]27[.]10[.]213
- 64[.]95[.]32[.]24
- 64[.]95[.]32[.]20
- 107[.]21[.]249[.]100
- 104[.]16[.]32[.]229
- 54[.]197[.]40[.]33
- 54[.]225[.]186[.]185
- 162[.]144[.]12[.]241 Domain Names
- jdlunsnxplknfahqhhcnydvjm[.]net
- bofznergcfar[.]biz
- yfptiliaesndlcvuemywsvcyh[.]info Files and or directories created
- %AppData%\Microsoft\Knsoono\knsoon.dll File Hashes
- 9a238c95de1ba5bc414aa0fd45297bf79f02b1de03d93a65ad74e91e37eb9ae9
- 0452810a21fc1207dc11a2a82127f30354fdc41aef95371b77a00b5592c11bb4
- 02ad78b356cb9723b18122a2fad033e0487be7e367864d7481371bde0b0b8acf
- 0200b37385ee4b54572e9ff8f9dca6b20ef6a41feefeb9f5eaf14fa35fe82b87
- 007f9ee2441329fe8c8ebf6f597c84eb1e4fea764dd228cfae9bed400c8af53b
- 006b191a135afecf86bd4df2fbf619f8f019ab316d2edb33d053209384c7d4cd
- 00141f6303dd960c61a4fdb06e686ccc972c0e0f092adaf823444e4b7e32ae09
- d52f95bb330930af7477604547dd33fdf3fe76e20301a67a7d490f6b1ebe5247
- 4712cf80102b7886a946ab6454fb0978f9d94feacd52c5df18850dbefa0158ec
- 5b7a5a58e4af312cd23e1f28597f2818953dd23abdeedb52adb882958e2766cb
Coverage

Screenshots of Detection AMP
ThreatGrid
Doc.Downloader.Generic-6327950-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INSTALLER\USERDATA\S-1-5-18\PRODUCTS\00002109F100C0400000000000F01FEC\USAGE
- Value: SpellingAndGrammarFiles_1036
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INSTALLER\USERDATA\S-1-5-18\PRODUCTS\00002109F100A0C00000000000F01FEC\USAGE
- Value: SpellingAndGrammarFiles_3082
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INSTALLER\USERDATA\S-1-5-18\PRODUCTS\00002109F10090400000000000F01FEC\USAGE
- Value: SpellingAndGrammarFiles_1033
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SOFTWARE\MICROSOFT\CRYPTOGRAPHY\RNG
- Value: Seed
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\Software\Microsoft\Shared Tools\Panose
- <HKLM>\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\RECENTDOCS\.docm Mutexes
- _!SHMSFTHISTORY!_
- Local\ZonesCounterMutex
- Local\c:!documents and settings!administrator!local settings!history!history.ie5!mshist012017052920170530!
- CTF.Compart.MutexDefaultS-1-5-21-1202660629-583907252-1801674531-500
- Local\MU_ACBPIDS09_S-1-5-5-0-35459
- Local\!IETld!Mutex
- Local\_!MSFTHISTORY!_
- CTF.LBES.MutexDefaultS-1-5-21-1202660629-583907252-1801674531-500
- Global\MTX_MSO_AdHoc1_S-1-5-21-1202660629-583907252-1801674531-500
- Local\WininetProxyRegistryMutex
- CTF.TimListCache.FMPDefaultS-1-5-21-1202660629-583907252-1801674531-500MUTEX.DefaultS-1-5-21-1202660629-583907252-1801674531-500
- Local\WininetConnectionMutex IP Addresses
- 74[.]208[.]222[.]23 Domain Names
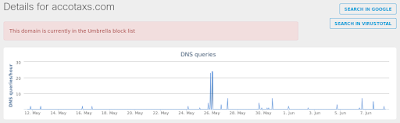
- accotaxs[.]com Files and or directories created
- \TEMP\~$e9214f2ae3380bf01724f704d58f3b9284dcc9522d9750ac770d49594901fb.docm
- %System32%\config\WindowsPowerShell.evt
- \Documents and Settings\Administrator\Local Settings\Temp\bbbababfcecbfa523.txt
- \TEMP\27e9214f2ae3380bf01724f704d58f3b9284dcc9522d9750ac770d49594901fb.docm
- \Documents and Settings\Administrator\Local Settings\Temp\bbffdeafaccece.txt
- \Documents and Settings\Administrator\Desktop\d37e.exe
- %SystemDrive%\~$runme.docx
- \Documents and Settings\Administrator\Local Settings\Temp\12tedsgsas124.txt
- \Documents and Settings\Administrator\Local Settings\Temp\tedsgsas124.txt
- \Documents and Settings\Administrator\Local Settings\Temp\eccbfaffbbb.txt
- \Documents and Settings\Administrator\Local Settings\Temp\bbbababfcecbfa.txt
- \Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\MRMBYDAX\gate[1].htm File Hashes
- 27e9214f2ae3380bf01724f704d58f3b9284dcc9522d9750ac770d49594901fb
- 078de2765221c2d5b5030bdd1d7adaa066dd4fc6a6575111df76ec7dd3785bfd
- 5239d220d79e36af270a89d0683f6744f2b823c18880aa7fe02bc004c52f78ec
- ab2ffad0977dda99a85c12d97fa40a8c09d5b81d08f7323e9e70e408ef017f3b
- c94d3f6f98fea91c7ff34920cbed45f800e6062706a7192ed6f354c96c669e4b
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
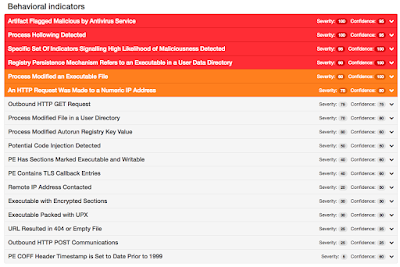
Win.Trojan.Keybase-6328970-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
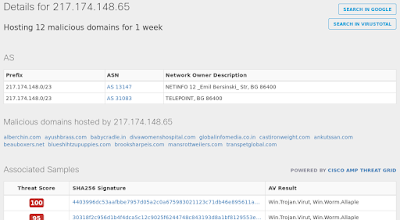
- 217[.]174[.]148[.]65 Domain Names
- N/A Files and or directories created
- %AppData%\Important.exe
- %AppData%\Browsers.txt
- %AppData%\Mails.txt File Hashes
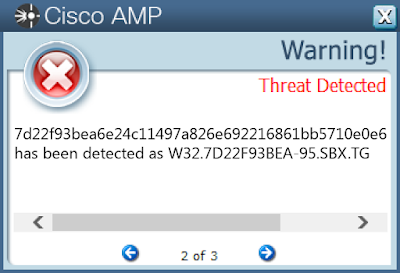
- 7d22f93bea6e24c11497a826e692216861bb5710e0e6a9842ed9c30463a11b24
- 8b1c64f993778c52906b8170cc6c16a07f4116e23661956a738323aca7b12c3a
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Trojan.Siggen-6261194-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection Mutexes
- Local\MSCTF.Asm.MutexDefault1 IP Addresses
- 52[.]173[.]193[.]166 Domain Names
- N/A Files and or directories created
- C:\DOCUME~1\ADMINI~1\LOCALS~1\Temp\nsrD.tmp File Hashes
- 76cac7eac498813164dcb94ed0812163bc4d261ef80232ec528aa941e0622479
- 2dd6b33d9e07c68b79b6674e0972f28ee316548c5e53b28331d88c739d1a5b8f
- 87701e501b48b94e9494bbda3f42a8b2a92a0e19d51d3e6023efae30b86f74a0
- 4a1b26fd16f985e1da3f1b5619b55f6170584ac51923bd6d6c4c455fc86d44da
- f20ef69203c8bd06da68071ccf38001fcd411de5c951bb38bb46a15e6d205458
- 74a306f136aa3b098fe99f6e35a1163d808c996e7ca6f8cd03fc69ec0a2573c0
- 8998b35cd76f170e62275661c0f0256883ec2b8e34b9e5ff9530c9da4d07fb74
- dd249e28e052a2e7747886a0596e7faf7e447fbef7260198509fc6e08c294bbb
- 745d8d433cba5315749dc61810d9bf4eb1864fb9737c4a2fc3718eda75917d6f
- 5527923be2a750415d9565fcfc38550bf292206cee0e415278e8e08d3f3cdbdc
Coverage

Screenshots of Detection AMP
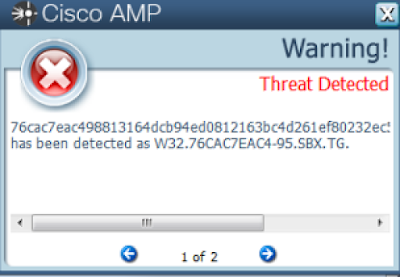
ThreatGrid
Image.Dropper.PhishingLure
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.MSO\E6B7EA3D.emf
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\654500.cvr
- %TEMP%\CVRFECE.tmp.cvr
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\31ADA98B.emf File Hashes
- 71c534db25e2c523ed71b7ec30289f8c91a15d8f61a7c132a8f0958086d9cf67
- b59051ead1c391fc3f5d4df44408606a6a0662456edf3a360760bc1df28e85b0
- 46e918a71e35421fd6384e4faa044758f636709aad1cdc28def585902560e75c
- 3fd12be1754315caaa508cb1dd3ed3c42d5ccfb9281a3c299b914da993919372
- 7d89276ddbb3e7d0a0c7628fbab04aace04e52f885b7b0619191b47eef4b3427
- 2190bab38a01b157023f4000b22958db934eb89fe2868593bcb3a28daca13cdb
- 884bdf459f5b218c56070cfba568a166e0f58df5e91373853b73a1eaf5c96896
- 55cae108a1f375d112831c24df0f9d0300028fb46e1ab4b7ff9c477da29888cf
- 069ea4075dfd279be50ee1a2904b6a5f024f7e924c91f5249e2047f93c971255
- c47359bd7ab8c463522a7e3356ed6de278cfa8ebe0afe9d5e8fcb359c356eb9f
- 8752350c7df238d3bc210f13edc74486c4c5e62ee935cc32fce6d84ba2fe3664
- c74a3428c963a4b8ecc86279e609b7e687d635068a7c607686c3b1228715affe
- 264bd038374d6dec2419788a189bc22253e944ae78e69082370700cfe163a5f6
- c9c4a76991fa7dabe4c5e242eceefb2276470ab16933576b8834a72db99bdb8a
- ba1e7358f4ac42e0e6d575e0f39c7a07939e31b03f82382486200b3d877fbe95
- 2aaeb1e014c6940fb9f1ed979622daec2bcb0afd27a431b60d575429513c4747
- 8fba7699a4f56f2ff0ef88137e7d9a045a8d58aeb2ee7764c70a57fd5e75c7b2
- 6c2e949f0e7ef6beb164e164636abfdb052386cc29318b4f80193ca1bb847e36
- 0fecda1f3e3c6bfc840119d3ec7788108b3bd2555cec500f9737499b57b20361
- e7b20cb956fb4bfbfbaaeae08265a3986114dd84fec72e6dbbda5ff8f0f9d602
- 63933469402c62a974f9e8c4d3563a1b8343cb5ae4962bbf8185cbcdf22f9855
- 5d146dc96acac7a6026b0a82d611c18c58852c328ea55d27737b2fbb0265fc3d
- 54071e124b61d87336c49408a420b98046828cceba18868e2fde9170a287843a
- e28775913fc2f714c665bc96babe101f509399754503dcfac1cff6614f0b5e04
- 2e76194f7889f84004a11d69af8df7a08c8602555a6f8629f146a593eb4bb732
- d15b79df9e9a6b9d09b984b1992f8433db9734e8fbe1036aecd05c941dfc6b12
- 0dc28f0d53d35417a7527ec8f248487ec270992bbfd0e1837a56fcda6fe9af1a
- fc66061242ba1d9cf3255437b6c8d0d8a0e6fdba3e63d9a611205b8654f11246
- 05264cd26e8d9c16ff1f5a71ee5641be5113ee247270072ac1e0173ee5688849
Coverage
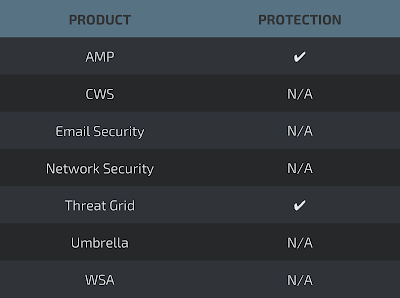
Screenshots of Detection Screenshot