Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 16 and June 23. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
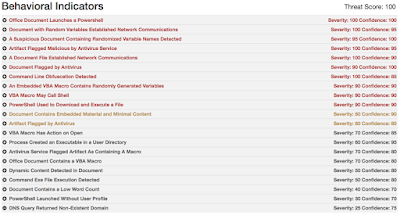
- Doc.Macro.StrObfuscation-6329879-0
VB Macro
Microsoft Office macros can be obfuscated in various ways. A recent resurgence of malicious Word documents include the use of a string obfuscation to mask the intended functionality - Win.Dropper.skypee-6329923-0
Dropper
This malware is a trojan dropper that is used to steal banking information and user credentials. It leverages Visual Basic code to install itself and establish persistence. Characteristics this malware exhibits include connecting to different domains to POST data using URI patterns like /http/image.php or /admin/image.php. - Win.Worm.Untukmu-5949608-0
Worm
Untukmu, also known as Brontok, is a worm spread through email or infected USB drives. It stores several copies of itself on different places on the hard disk, including system directories. It gains persistence by modifying registry keys and creating an entry in the Startup directory. IT also modifies several system configuration parameters to disable the registry editor and the shell, as well as modify the safeboot shell to prevent the user from cleaning the machine. - Win.Trojan.Shifu-6330434-1
Trojan
This well-known malware family contains counter measures to protect itself from analysis. It gathers details about its victims by stealing user's login credentials for online banking business. - Win.Trojan.Blackshades-6327385-1
Trojan
Blackshades is a prevalent trojan with many capabilities including logging keystrokes, recording video from webcams, and downloading and executing additional malware. - Win.Ransomware.BTCWare-6329927-0
Ransomware
BTCWare is active Windows ransomware that was first discovered a few months ago. Since then, it has undergone various changes, including changes to the encrypted file extension & the cipher used to encrypt such files. Earlier variants relied on weaker cryptography options that included RC4, allowing brute force recovery of the private key in some cases. There was also a noted variant that had its private RSA key leaked online. This recent variant relies on AES-256 with improvements to the handling of the private key generation. - Doc.Dropper.Agent-6330744-0
Office Macro Downloader
This is an obfuscated Office Macro downloader that leverages Powershell to download a malicious payload executable. The host that these samples attempt to download the next stage from currently does not resolve. - Win.Trojan.Yakes-6330794-0
Trojan
Yakes is a trojan which installs itself on a machine via a .vbs script in the Startup folder, and then allows its packager to connect to the infected machine. IPs and domain names of the CnC server as well as mutex names vary depending on the packager. - Win.Ransomware.Locky-6330799-0
Ransomware
Throughout the majority of 2016, Locky was the dominant ransomware in the threat landscape. It was an early pioneer when it came to using scripting formats Windows hosts would natively handle, like .js, .wsf, and .hta. These scripting formats acted as a vehicle to deliver the payload via email campaigns. Recent in-depth look: /necurs-locky-campaign - Win.Trojan.DownloaderJava-6330457-0
Downloader
This sample is a .NET downloader. It downloads additional Java files from an hardcoded URL and they are executed. This binary is actively sent as attachment in an ongoing spam campaign.
Threats
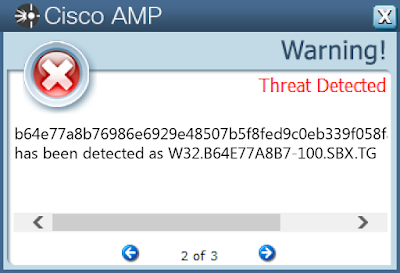
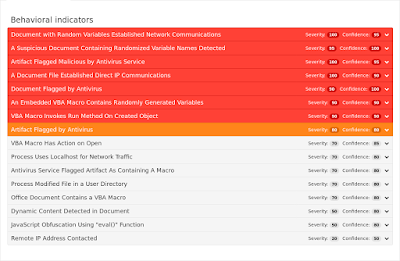
Doc.Macro.StrObfuscation-6329879-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
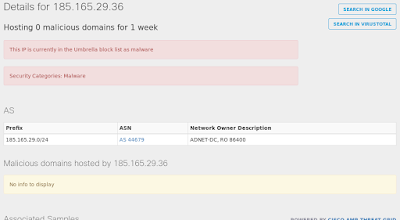
- 185[.]165[.]29[.]36
- 52[.]173[.]193[.]166 Domain Names
- N/A Files and or directories created
- %TEMP%\<random_string>.txt
- %TEMP%\<random_string>.txt
- %TEMP%\<random_string>.js
- %TEMP%\<random_string>.txt
- %TEMP%\<random_string>.txt File Hashes
- b64e77a8b76986e6929e48507b5f8fed9c0eb339f058fa5a31d38920e25c3a8c
- 9bcbbba6636b99da1ab567813af8226fb22ab47509326c6501d22e40efa1464c
- 79a89d266bcf1b8c829b823203fce8e69159246469c14ac355f615c2dd783e01
- b96f975a2c7cfb03e53e35f365e3f16e51c2370b15970693c7dd2201f08ddb1c
- 3e4c9f8828897c19e264a2a066d9c181edf08885b6fafdec833aa683259aced9
- 79a89d266bcf1b8c829b823203fce8e69159246469c14ac355f615c2dd783e01
- 48487be062791d86b66d10cbdd54ce1b1dfbfe99a86bfd8c3b2ba6be7df28f6e
- 3e4c9f8828897c19e264a2a066d9c181edf08885b6fafdec833aa683259aced9
- b64e77a8b76986e6929e48507b5f8fed9c0eb339f058fa5a31d38920e25c3a8c
- e0e134db8de265d9ecd2f174cd143da54a4a922d64abfff704488ded3c7b3bdf
- 9bcbbba6636b99da1ab567813af8226fb22ab47509326c6501d22e40efa1464c
- 02840c7ca57b46ba7d6b40f93e0054dd180a290b30c2a8397fcd646ef30cfdf6
- 6f39761c2c1fcd6975505a47828f9dec483c8ec730ba68eb05e09ef60a91c879
- b96f975a2c7cfb03e53e35f365e3f16e51c2370b15970693c7dd2201f08ddb1c
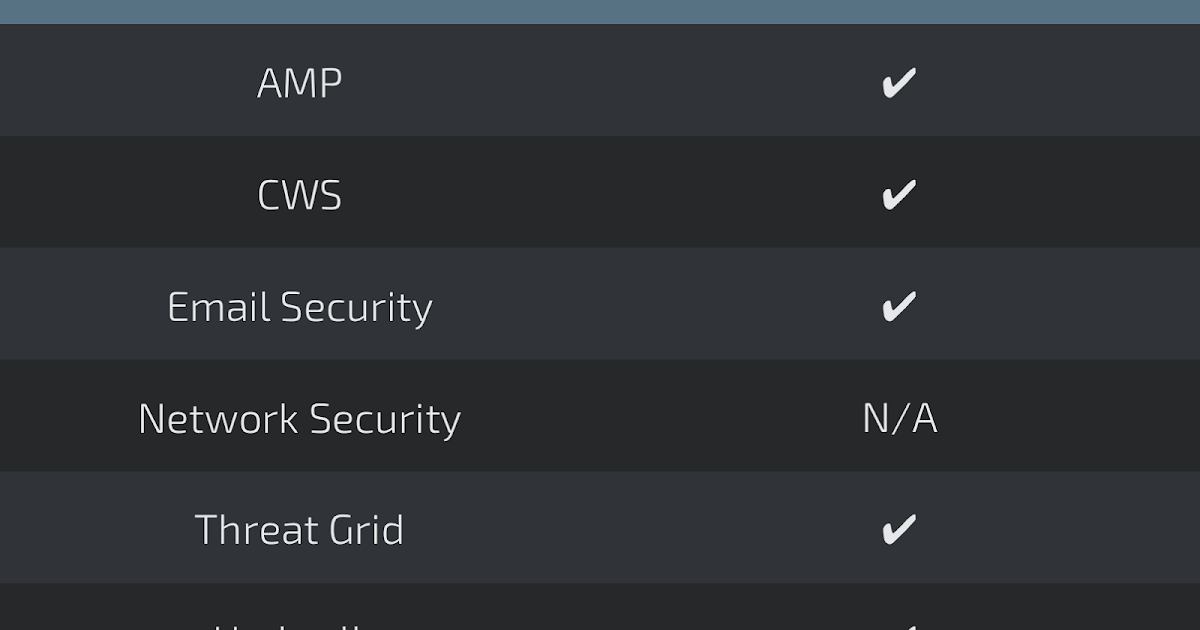
Coverage
Screenshots of Detection AMP
ThreatGrid
Umbrella
Screenshot
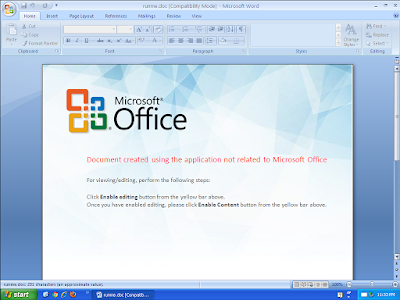
Win.Dropper.skypee-6329923-0
Indicators of Compromise Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: skypee Mutexes
- 1505527138 IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- N/A File Hashes
- 35b8bf77573eef9acef8b19521e43ce3d440a5e02ccf6deda05ae58eeac3cfe8
- 09aa51458f73755e4e58a7d59853f07d685d7e7dc48971117b1e9392a1aa416f
- 99e7ecbe795d7d6a03c4965b2ac7d79544a6772a97ccaca909f66bfe174fa023
- 26ef58faf48e58dc0680c6b595436dbba01ea3c8fca809858fcfc47d66b56914
- 0d983d4ee06e08b4e1df021c17792a8352c8ff4b2d3e6ee4f7fe53ce30122d66
- 0b5800e19bdb4c43ab1469ce88af3d807eaa7620697a4b88368ab6beef098240
- 3a5c13ed645ab7571c2a6ba27fd689e748e7d42de35bc076d18ad76070a13d14
- a6f34f3a70ea64adccfbd983abfebe9dc46741064da0520582b09ce6d6a966ee
- 5ac152e574c091986561d8055d0b0a97fab1267c6dfba69d169ac9c41a5bc390
- f33a3141ee599c94ff60b40be0c0d18c66732640a809b4319a0140eb7827bafb
- 7f7fe90b586671e59c6769e4202871fb10573983de7fbe7ca7ad3a97af7395af
- dd8826ffbe107318163ed2716231ccf588453308bbcd3c798720e7586c059f99
- 2b3d33238a64134c347db9a3f5b9f0fbecfe62199f081c3c44fb5f1b0948e7cc
- e336b8976fb83889c3027ed084a02f9de97f90787304bfa87c58be8dd8035e20
- 7f990624c65a28f0803e19c5a37d34567a921d17531899a384f2077c1c6f5dff
- c62ef9ef0c92b95740f8a67c9879d3c2f951655cccc20c310140668265d8135f
- bb5f19265e7b5094cdf55c401bae987cf895bf885cf485c3c627c1fe267e9bfd
- f5d55f9539e753fe3a4e0de50bb3c6347ee9928c0f6db33e5f6b6e4af179da0f
- 2948da52a96f06cfc4bfb7d4d079201aaa3ef89de1cc144462973107c4962435
- 77ca8909ec71c9086e569cb2acbf4c766dd60f758a5ccc938402d3f176636ae3
- c80fbdbba34721670043965c3b02832df7f8cb1c5b5c57b04dbb5ee6346d5994
- 8c2579168922d065854582cc486a0bb43f8accb60ccc01ad1035894012ac2e83
- de8f2233c54d10ae9b51325cefb5dfad644acc225d4ddacb5c77ed89b6b1a645
- f5f11cc63feec411864cdc27f1d0d186b5173cf443876450e445d47d29b8ada6
- 1ca9f0b54357839435e64dd26d74fb365622b54395f56bf25985db0e7470a355
- 68ed0c9628c7764c5b3826309fe5db06a5380e7f1c8ebfb8f62c68d12d135b49
Coverage

Screenshots of Detection AMP
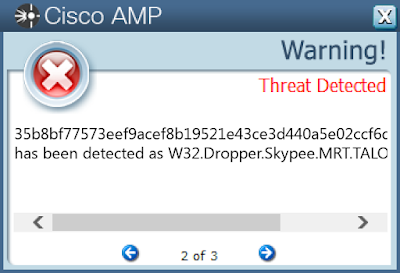
ThreatGrid
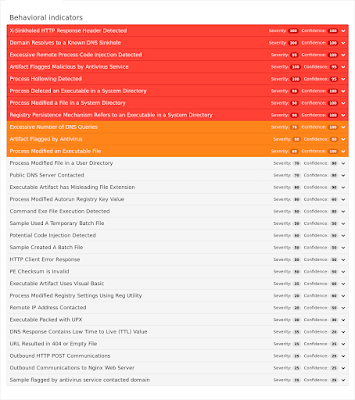
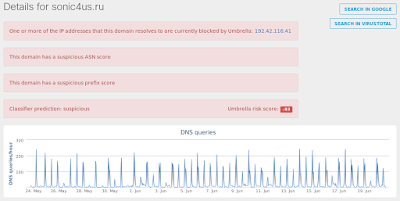
Umbrella
Win.Worm.Untukmu-5949608-0
Indicators of Compromise Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\OFFICE\12.0\OUTLOOK\RESILIENCY\STARTUPITEMS
- Value: w+%
- <HKCU>\SOFTWARE\MICROSOFT\OFFICE\12.0\OUTLOOK\RESILIENCY\STARTUPITEMS
- Value: l:(
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: LogonAdministrator
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\INSTALLER
- Value: DisableMSI
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
- Value: DisableSR
- <HKCU>\CONTROL PANEL\DESKTOP
- Value: SCRNSAVE.EXE
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
- Value: NoFolderOptions
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CABINETSTATE
- Value: FullPathAddress
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: DisableRegistryTools
- <HKCU>\CONTROL PANEL\DESKTOP
- Value: ScreenSaveTimeOut
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\SYSTEM
- Value: DisableCMD
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: xk
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
- Value: DisableConfig
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\AEDEBUG
- Value: Debugger
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- Value: Shell
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MENUORDER\START MENU
- Value: Order
- <HKCU>\Software\Microsoft\Office\12.0\Outlook\Resiliency\StartupItems
- <HKLM>\SOFTWARE\CLASSES\lnkfile\shell\open\command
- <HKLM>\SOFTWARE\CLASSES\LNKFILE\SHELL\open
- <HKLM>\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Policies\System\ Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- \Documents and Settings\Administrator\Local Settings\Application Data\WINDOWS\CSRSS.EXE
- \Documents and Settings\Administrator\Local Settings\Application Data\winlogon.exe
- \Documents and Settings\Administrator\Local Settings\Application Data\smss.exe
- \Documents and Settings\Administrator\Local Settings\Application Data\WINDOWS\SERVICES.EXE
- \Documents and Settings\Administrator\Local Settings\Application Data\WINDOWS\SMSS.EXE
- %System32%\shell.exe
- \Documents and Settings\All Users\Start Menu\Programs\Startup\Empty.pif
- \Documents and Settings\Administrator\Local Settings\Application Data\lsass.exe
- \XK\Folder.htt
- \Documents and Settings\Administrator\Local Settings\Application Data\csrss.exe
- %WinDir%\xk.exe
- \Data Administrator.exe
- \Documents and Settings\Administrator\Local Settings\Application Data\services.exe
- %System32%\IExplorer.exe
- \Documents and Settings\Administrator\Local Settings\Application Data\WINDOWS\LSASS.EXE
- %System32%\Mig2.scr
- \Documents and Settings\Administrator\Local Settings\Application Data\WINDOWS\WINLOGON.EXE
- \xk.exe
- \XK\New Folder.exe File Hashes
- 26fbb2aa5a28de5e149e0178dacb964333c852bbca2a1416d860e5edc84cbe04
- b5e7b1b06efe80a081a2cbdff0fab4539be0797b2351ab4e1b247303586d1340
- 36890fa6756c252bc89abb88ec9da140cd87937eb5223af05e4e8ef36ec019c9
- 34c9c0d2fbb403f7e8068ce49071da6dbeadc4ad995101388c9ad092e38f90de
Coverage

Screenshots of Detection AMP
ThreatGrid
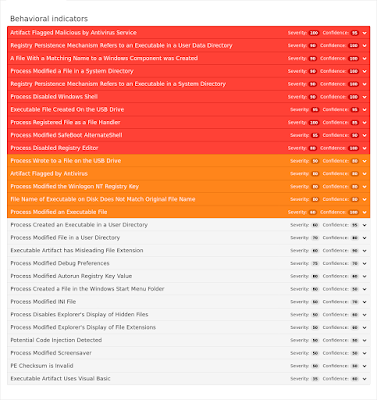
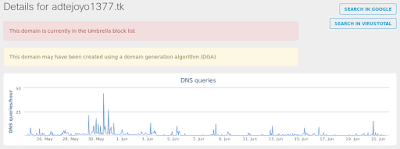
Win.Trojan.Shifu-6330434-1
Indicators of Compromise Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: IntelPowerAgent[0-9] Mutexes
- N/A IP Addresses
- N/A Domain Names
- DGA Domains
- adtejoyo1377[.]tk Files and or directories created
- %PROGRAMDATA%\[a-z0-9]{8}.exe
- %APPDATA%\[a-z0-9]{8}.exe File Hashes
- 280a3734efd7e54a32c8719c0efe0365df6b14e8ac54e301736c8ff9829da424
- 5283c7d5db5b5629b5b58534bcf6cd7607f0d015d740ca91ee85ade420b7460f
- 2271a2e9d72580e98331792d94fca75e5a0c1dfee958d79652adf9eaab3ee266
- fc9a9633b8ab0b78a820c74bda57ab608316c81d6ed6b469e7487ce3712bf62b
- 3ad0138c2d8842f3aef8b045e05e28e441b81ea8444dce0b6799f4ec65c70540
- 23045a27de525a0d8c85390414ac4458a32bdbd6f9dc8f0e39b32dad3f89fa55
- 55768ac9504b8e612b380fc0984277f0576dd8d129a5363e73d4d2a9baff5c7e
- 06144d28c5d1db06fa8f78fdcb651145d6500483a9b1fe26c62a510dbe1763b7
- bace9b3e3220c6e9f6281f4d4a1eabb9223e6093ccc9876c600a31671b790ed2
- fbaab6ab727898b1ff27fdffec49bbe00976474b93741b1fca5eeb38f1f25099
- 0c4a32e9eaeb38e1b30ad44f52c4f8ea3f2e3f522d9b2281ecd3701383b20cfa
- 252db718eb383331a34cbe53c0b9889c80452e19bc06007e740eaa23e2ef2a8f
- ca9c3f80a3faaaf001f3fdb37e1cf9abb14a1628be2a9f6ba4e0cc51ed708cb9
- 27922f495e54bf51cb7329a75c533ca4a1ab8323f1f781dfd027571a37c7485f
- f1dcb8e18a764d300267f2bc0873bf8ec15385cec7ab1d2871e43f238f86a6f1
- a9639bd0930f2db17de0321f99ce70355f1dba17b4aa6f5444a4c2490738e255
- c0522065fbce82a74d13361c88be210f62a8633c9a59203cea0ce6722619092b
- f7e904b2eb8c5280d008cdf93e10fab87df6bb2423bdf1e8f7bb203f63c15ede
- 280a3734efd7e54a32c8719c0efe0365df6b14e8ac54e301736c8ff9829da424
- e2404f8fb7f080cb0b344c1f006cde4a00143641633bb454069773d616a9106e
- b232dccdb27873c64616d2cefcf2dd81f7958ec8778e31da7f1688a68fda4249
Coverage

Screenshots of Detection AMP
ThreatGrid

Umbrella
Win.Trojan.Blackshades-6327385-1
Indicators of Compromise Registry Keys
- HKU\Software\Microsoft\Windows\CurrentVersion\Run
- HKU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\run
- <HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Mutexes
- LVLWU6KG22 IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- \Documents and Settings\Administrator\Local Settings\Temp\jd7018sy8tv.exe.jpg
- %AppData%\D6GM5WGET8
- %AppData%\JD7018SY8TV.exe.tmp
- %AppData%\JD7018SY8TV.exe File Hashes
- 017a3ea76063f364f9d7a70ecde761e22005b74fce020e798e6151d3806dd251
- 0620a1061f4c14acbaa3b5b70bab4894aae33bc9f30bc8623ea9f63ddc953088
- 0743dd7863c03515d74a1832592c1409bdff0d30aac4f45ba73dc99ef3c1e5e3
- 086be8b2789ccb88f60c71773de7c22cf1d97aa72d2b21a3cde9248cc7321606
- 0a3e9d5ec49cc97f1c9fc2a59e53462d0d2fe6fa1f448e69e401e63769dafe0a
- 0ba95e35fcde6b1b3f49d1267e3dea8f2a8b4acb5633bc3acb3aefe9bf3e7680
- 0d58482c771ef85649f1375f6ab61c48c380c7694b3ad7552af1bdc1ec724890
- 1014e1c1246a6c7cbb519ed711a2168955ee4b4222baae5be911f981088604db
- 15a64cded5bcf3dc911bfeb3a5701a376dea51f9f8530dc0949ba6e6f4339cc4
- 18039335deeaf295164f5e24c5afbcc50fa27f2eaf5733be2cf51bcf01f664c3
Coverage
Screenshots of Detection AMP
ThreatGrid
Win.Ransomware.BTCWare-6329927-0
Indicators of CompromiseRegistry Keys
- N/A Mutexes
- ONYONLOCK IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %WinDir%\SoftwareDistribution\DataStore\DataStore.edb
- %WinDir%\SoftwareDistribution\DataStore\Logs\edb.chk
- %System32%\config\SysEvent.Evt
- %System32%\config\WindowsPowerShell.evt
- %UserProfile%\Desktop\!#_RESTORE_FILES_#!File Hashes
- 0951b80a41f06f8062c85c80be0276c6a1328edb2a501ed69ed25083303724d2
- 0b5b4111df2b4b2f78ec053db14ea5c74965ec13f1902570b06697d71a77dcd7
- 1cde4818229f719153565dd84b01d3927928e7a2b6a61684ee932520f55250a9
- 3f9b9062ca3497614ac021146b229b07786774934f98a261547b24df5cc5b263
- 6617035053954a5131d401061c58831e181ddfde221f402029d5ed4bd39561dd
- 6b4363a419208d6fe093f5a95b55653560d236e1a302f98d22fdfc36488ebcb1
- 72653d3a882901867143579131a6e9dff2f72a647afe21035c1deda0c4c943b0
- 741950e9be430267efff601fca1a7c21b65b904658fa46f9e618ea50787faaac
- 79afde5a759bcd71165b547f7a310fa06674c565a2e81af0304bc1a4527bfa1b
- 7bd14a6ceacc14e67e84add894d432c6383676ea89265b36515014cd136851e3
- 7c19bc3a4ad7cddcd78eee053b408779c25a56c9666e9cc9d76ea617aaa0934d
- 7f86548bdcd97e3faa3e8df0bd6b6aac7c05ed9d445a2bb7973a4d6efd39bd6a
- 880d25776e08769a75c43bf9a69f9f7cafcc46546690270fa36785195f327d97
- 8bbaa450526bc2933d462ae24439148273434ff342e0a0774d5e37af4bb16864
- 97b88ae6bee56ae6193c7908eaabac9be579861868cc575cc345c1d1bca1e302
- cef0439b7b483900323614d6cf2eb341019d747aaa0feb81710ef836d330ca9c
- d0ab335e86e665edbab58240ae6aa691fa4802ae831c0204e71f90a34ae66983
- db5fefc3b8349efa907ed2812c869b10d8de109ff005fe8aac15eaa4c8efdcb8
- eb843f4f80ae2e58b569f916239c6208601eece08efb334ae12b8658e3436987
- ed3118f96c7e87ea768a40acc574b2ff3cae3a3cdf2419ccb30c750a876d5f30
- f7850a2efe397098859d8c3d0ed0b4fa93f87148382e250f094d12f021bc8460
- f9d27f4f3231cd80b19b30de4426aecada466e18ee785e82d5afa59e986b4d16
Coverage

Screenshots of DetectionAMP
ThreatGrid
Doc.Dropper.Agent-6330744-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
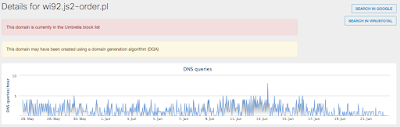
- wi92[.]js2-order[.]pl Files and or directories created
- %AppData%.exe File Hashes
- 0033b70080a9ee615a371a5c18c373bc9a703a9b5dbcac39a2584a328a49bb87
- 3a8abf2f7fade51114fde4251ff98b23093e07a7545be3568f3da7ba730bb995
- 3a93346632f58a112708b761154a170be06de1b6a0583f58053cfb1fce09c780
- 6465c7ce45a1430e55cf10e43732892a1f86fa90646adf5628dd6d72dd849e8f
- 6ab9d03a0fc72b377712f262601db2f14561e6f285d9742e956416409bba3e64
- 8daded1c8acd270c0371e6c24310dacb4d841c801b707594823f371ce601f29b
- 9b23fd1d89331bddc13063391bea1c03fbaf813a584554cd43b1d6bb6574992a
- d19a574a36079ca7885ae142c0f24578743eb98cca7f57df3c2258c8dbb874bc
- d31705a64e38340872f6b9e8287e0297d4fd13cb8373295ce0d9ffdf6947e43f
- e545a49f26d1482225dd25bf0b2790a1f6d5f96bda9afd90ec8cd38b7b20ec07
- f048103ee6f0902b3025729301ce9bbbfee35272bc594be2a6cbd7da72f6f4c4
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Screenshot
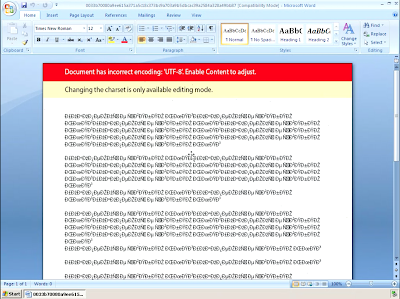
Win.Trojan.Yakes-6330794-0
Indicators of Compromise Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: 35bbded46273bc9f6fa3fc5557dba9af
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: 35bbded46273bc9f6fa3fc5557dba9af
- <HKCU>\Software\35bbded46273bc9f6fa3fc5557dba9af
- <HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce Mutexes
- qazwsxedc
- 35bbded46273bc9f6fa3fc5557dba9af IP Addresses
- 105[.]154[.]213[.]56
- 52[.]173[.]193[.]166 Domain Names
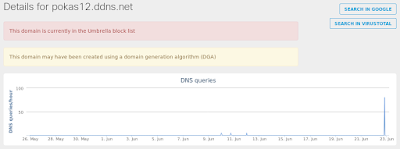
- pokas12[.]ddns[.]net Files and or directories created
- %TEMP%\IXP000.TMP\1.xyz
- %SystemDrive%\Documents and Settings\Administrator\Start Menu\Programs\Startup\x.vbs
- %TEMP%\server.exe
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\x.vbs File Hashes
- be73fc08bed6bba6c25688c150da18e26314c5d670d741d52c457e01f0a1ad0e
- f1055f9d223106263dd0d8879be304da2cbe83428c2277a8b42c96c762121a1b
- a5024be1b974fc16ca190a26a01bef35e02aceaa4c8fe8a3938084e22d623ce2
- eb319d0c53ec709a0482cf58a65b615fcba38a2b44b41e832b4804c6aba68280
- 75d9b6086aa9bd51596733a163bd568cc648978ac68e7ebdd817654b4c7e6fed
- d323180a15cf584a184aa63a0044ec7701cb9d75769386bec21992ffd585d9dc
- eeb4c5448c1a4a8723f860c7ce30889c2c5d018abe17df43fae2f6d23a713568
- 4657c3f05d44048fdfc41190e652413ba2508565aa9185fa1a0670a2536a95cc
- c585135463d4fce5053f47c255747524585b98c1c3f8dc305beefa17d2fcfa9e
- c99d37d2cfc2861254d1bb82cc6b41617e659e8f0430e63cd20f44778a3bfaac
Coverage
Screenshots of Detection AMP
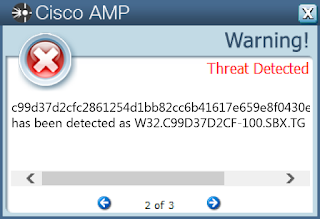
ThreatGrid
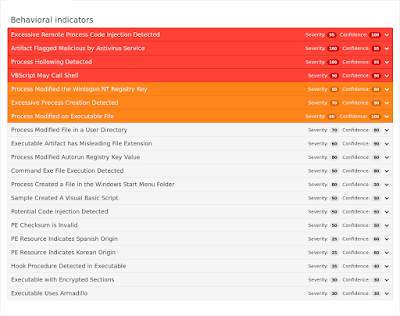
Umbrella
Win.Ransomware.Locky-6330799-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- .*\loptr-5e5a.htm
- <GUID>.loptr File Hashes
- 091141f6b67540ba8848f1b081ad40d5f6d8172c878d40046f82ab0234acf3db
- 7f4777245025c96d936d14b3b4a718be35ced59558f090e1197adfca5d9573b2
- 26074772fa68db08f463c66deeabe064bcd9d48032430bbbdf27ffdf8967e8c5
- 85fa592bf685966d8da1cf72f2c6c092b40664de9c17d9cc4894f8f08e06f567
- 49184047c840287909cf0e6a5e00273c6d60da1750655ad66e219426b3cf9cd8
- e7b8d8e3c19b6b3cc4a6eafced463f08176330fe243d8a9fcd20aedc5af17806
Coverage
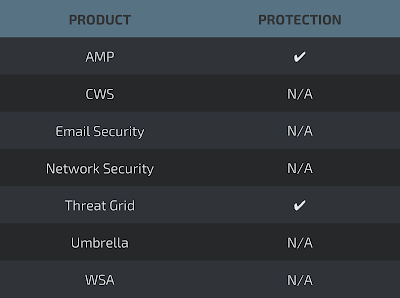
Screenshots of Detection AMP

ThreatGrid

Screenshot

Win.Trojan.DownloaderJava-6330457-0
Indicators of Compromise Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: miZPeWpyLHr
- <HKCU>\Software\Microsoft\SystemCertificates\My
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\TrustedPublisher
- <HKCU>\Software\Microsoft\Windows Script Host\Settings
- <HKLM>\SOFTWARE\WOW6432NODE\Microsoft
- <HKCU>\Software\Microsoft\SystemCertificates\TrustedPublisher
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\TrustedPublisher
- <HKLM>\System\CurrentControlSet\Services\Tcpip\Parameters
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Root
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPUBLISHER\CTLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SystemCertificates
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TrustedPeople
- <HKCU>\Software\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CTLs
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKCU>\Software\Microsoft\SystemCertificates\Disallowed
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Disallowed
- <HKCU>\Software\Policies\Microsoft\SystemCertificates\CA
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPUBLISHER\Certificates
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TrustedPublisher
- <A>\{C108F07B-312C-11E7-8D90-00501E3AE7B5}\DEFAULTOBJECTSTORE\LruList
- <HKLM>\SYSTEM\CONTROLSET001\Control\DeviceClasses
- <HKLM>\SYSTEM\CONTROLSET001\Control\CoDeviceInstallers
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\Root
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPUBLISHER\CTLs
- <HKLM>\Software\Microsoft\SystemCertificates\TrustedPeople
- <A>\{C108F07B-312C-11E7-8D90-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\A93\Indexes
- <HKLM>\SOFTWARE\WOW6432NODE\Policies
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\PRINT\PRINTERS\Fax\PrinterDriverData
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs Mutexes
- N11463_-4521624950585898-1497978066453
- Local\__DDrawExclMode__
- Local\__DDrawCheckExclMode__
- RasPbFile IP Addresses
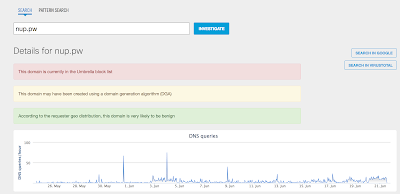
- 149[.]210[.]145[.]237 Domain Names
- nup[.]pw Files and or directories created
- %AppData%\.qjava\Java\lib\jfr.jar
- %AppData%\.qjava\Java\lib\rt.jar
- %AppData%\.qjava\Java\lib\jfr\default.jfc
- %AppData%\1497978066454.jar
- %AppData%\.qjava\Java\lib\javafx.properties
- %AppData%\.q7z.exe
- %TEMP%\_0.15066600419658372851713423405977803.class
- %WinDir%\Temp\FXSTIFFDebugLogFile.txt
- \Users\Administrator\UlBrZNAMJSJ\iMCImxZnYcm.KwyVDG
- %TEMP%\tmpA3A6.8e4d0709-e282-42fd-a717-9d512ecd2cb0.7z
- %TEMP%\_0.32579030377917368405753216876059627.class
- \TEMP\c9bd2f466d2c1500af5414f03f7d5c908cafdd602c23a8136cf82054233f7791.exe
- %TEMP%\Windows7851854962857713622.dll
- \Users\Administrator\fUTkALeaTxM\ID.txt
- %AppData%\Oracle\lib\fontconfig.properties.src
- %AppData%\.qjava\Java\lib\ext\cldrdata.jar
- %TEMP%\tmpA3A6.tmp
- \Users\Administrator\UlBrZNAMJSJ\ID.txt
- %AppData%\Oracle\lib\jfr\profile.jfc
- %TEMP%\tmpA395.tmp File Hashes
- c9bd2f466d2c1500af5414f03f7d5c908cafdd602c23a8136cf82054233f7791
- a49fb3f2f4a8e5d996b49d51eae11ec11dca3a1aa2db319ed004d898c4484bf2
- b0f8ca0c55a07bc4a9a12ee6dade6843aa9ca875ebd082759b2a85727fe64f83
- 26c487810b80460a69711463dc3ffaa8d0ca6cc21dbf2856660fc1ceed23af53
- 555bdc43352d19ed64b7580206208462bfd3be9038bcb92c0898d2861f995c4b
- 3977f37224326f7508ed5f086fc4161d2f8d2aacff62f7c05d29243a8f401fa8
- a84eef3d331514764cb72146a376f61e3cf2189fa7d2f81d1a7e99b41fafaedf
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella