Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 28 and August 04. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Doc.Dropper.Agent-6334774-0
Office Macro Downloader
This is an obfuscated Office Macro downloader that attempts to download a malicious payload executable. - Doc.Macro.Obfuscation-6334622-0
Office Macro
Short, heavily obfuscated VB Macros make use of calling functions indirectly to prevent automatic detection. - Vbs.Downloader.Trickbot-6333852-0
Downloader
Trickbot is a banking trojan. The prevalence of this malware has recently spiked and is being distributed through several malicious spam campaigns. Many of these campaigns rely on downloaders for distribution, such as the VBS scripts. This particular downloader relies on heavy obfuscation, string splitting, and what appears to be widespread use of a name for a legitimate database tool in an effort to evade detection. - Win.Downloader.Psys-6334750-0
Downloader
This malware presents itself as an Adobe update to the user while downloading files using an embedded Tor client. Infected clients are often compromised with bitcoin miners and other malware. - Win.Downloader.Upatre-6333840-1
Downloader
Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables such as banking malware. - Win.Packer.VbPack-0-6334882-0
Visual Basic Packed Executable
VbPack executables obfuscate control flow by using call statements where the stored return address points to strings. Series of these calls collect string artifacts like library names and export functions to leverage the WIN32 API to prepare for the execution of a malicious payload. - Win.Trojan.DownloadGuide-6335034-0
Downloader
This malware is a trojan downloader written in C++ that presents itself as an application installer. This malware family leverages techniques to hinder dynamic analysis as well as sets up a proxy. Additional components are download and executed. - Win.Trojan.Madangel-1
Trojan
Win.Trojan.Madangel-1 is a trojan that will replicate itself through network shares and eventually connect to a C2 server to retrieve other executables to install into the system. - Win.Trojan.Nitol-6335025-0
Trojan
This malware family performs DDoS attacks. It copies itself into the \Windows directory and installs a registry key for persistence. Further, it deletes the original executable to hide itself.
Threats
Doc.Dropper.Agent-6334774-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 95[.]110[.]231[.]145
- 186[.]103[.]161[.]204 Domain Names
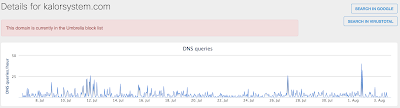
- kalorsystem[.]com Files and or directories created
- %SystemDrive%\~$7661883.doc
- \TEMP\Attach_ID547.doc
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\743234.cvr
- %AppData%\Microsoft\Office\Recent\Local Disk (C).LNK
- %AppData%\Microsoft\Office\Recent\Attach_ID547.LNK
- \TEMP\~WRL0053.tmp
- %System32%\config\TxR\{016888cc-6c6f-11de-8d1d-001e0bcde3ec}.TxR.blf
- %AppData%\jottingstributarysthesauri.exe
- %System32%\Tasks\services update
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{71906E9D-AD49-4D65-BCF8-C606DEC3CF07}.tmp
- \TEMP\~$tach_ID547.doc
- %AppData%\Microsoft\Office\Recent\267661883.doc.LNK
- %AppData%\Microsoft\Office\Recent\sanctumscutlassesinstrumented.LNK
- %AppData%\winapp\insshmfrsqhatsaqxrsgdratqh.exe
- %TEMP%\CVRB190.tmp.cvr File Hashes
- 619948e1aa1ce2a8dd9c4e97884ed929f5bb3bdf9626d3cb97b2d99cf56d51da
- 11b39f6d68386a652afdca623783ec7141961db0a6d321a279b1603fc462cd0d
- 687bc84ce1f1b6dc0a99fc01b0fec5fa00d58b4ab1083bea7867b1bfc7d84ec3
- e4c29ce79af3e1d5a6b4d41a6239bbb369cca0ca4742fbb28fdb58cf3a1d6c67
- 6604d8dcd1ed5a53c5d03c2509f2d5d9a421e3a12b6087dfadb83e69805439ca
- 4abfd7fd9443a61c98be138d55c84c317c9959893e2c8a297ee9d13ef18d387d
- 09a9bf51b2f18df57c796993b037b91b7a1f2400716132339d35cd6f8497da1a
- f3387add07c0c321189823bfe08296fa6eaa983693421dfd40d9208b8e68543b
- 324b4a83ee73bb3b3d5a9b4099fc7c3ffc6c0497eec01b62513c6f91731763da
- 551008d7fe2e292728188a14231d37d741becaa4c64290af671c3dc440ab8743
- bc661ec240c941eb0ae04b11cedcfbfed2b81e5487346823c10cbf0e88df59e1
- 5cbc42190c97da6f9737bca56c30e24f2679467a04030c732b320ce278114ea4
- 08887558f6388dcac9afb8b0c311558d4e8a34974dc01168f74e5f711ac59535
- 17504f7f93bb6be7230ff1588623556ee62299082aa3f2dc539d5a48f714593a
- e191cbadbe4a2c24427bba011a3abf56ccaea8ba8e991b4b60c07d406412c11d
- aa100e2c541e4a1c4fa3a75c077a9b5b94fc99b0d19bd2e194d9baba5bd9f346
- 75c74b872ecb14b99579321930b72f3749b416a1e1242f906c6d9e8515b7e4d3
- af29409564b009d3d71621483b7d62adafe77eb1ada41abd0239ae07c30c2abc
- a385c7d8d006d80f6bfdb583aba085c0c4a18afddd05ab07ade49522dc584dbd
- 83ff2ddc3b76f9c1cba2e7a806f84a50dca2913d55a33e619f650a6b6a6b272c
- 7dee06e698a8baa78df73f058f9be2b269a5344d2dc449bcdbe87e44000b8310
- 4255b90bb30c02b4fe1a42ccc55742f641d75810038aa8fdae6057a9a41afb1e
- 519363cc5308578e3565d9d73e1ace3145156d3e14c17ec1ef7a189bf6bf9381
- 89983f03a9a2b9b5e9aeb7c8f637fec5ecbeec1378b676de5c326f74e31918a4
- 06b0105e71ca2e1f9bd63cd417dcf6437a325eea393b57f4c622eb413f922265
- 47833122bc78d99040f29bb2f5c01b5c0b9f4b5b81b09b6a6951e7fa67509f8a
- 427d8860cbb12f680692c1a54da26e189b4498b2314984932112400d138eaae3
- ff6ff8c4af0499c0ff4379378cbb9d3eddbd48b197fe07277371c20e2dae70d8
- 1bf710707642000bcf37c0774c12b004127235b710dd7116f08d86bfb04a28c8
- c3e10665750030082cf2e37c8e882b8572a8be65d6ee51bfc253853a70d1db90
Coverage

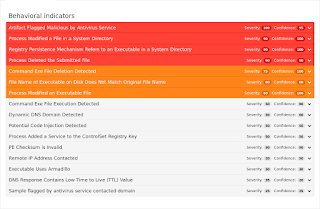
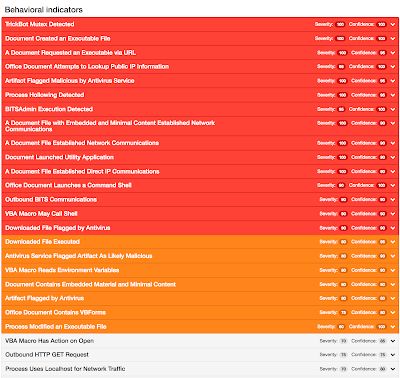
Screenshots of Detection AMP
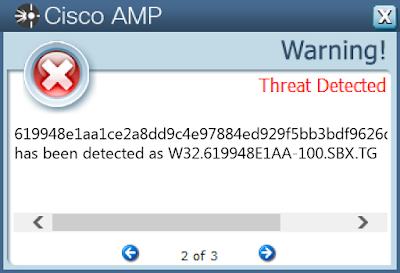
ThreatGrid
Umbrella
Doc.Macro.Obfuscation-6334622-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 178[.]175[.]138[.]162
- 176[.]123[.]0[.]55 Domain Names
- halohh[.]tk Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\driv.exe File Hashes
- 4cd9c04390f2b7171e50e1c0b1afde499160aac0da9aed28ee5677863a389c5e
- 0bb9ba9d3ba8fe8f8fd4c464f27674e07a3d231642a21571e03e0f08bac6909e
- 617ac6d026a110629694b28c977bf5e8d445eb25ccd83f14b925ca032f779cec
- 98233482a8e37abaaf5cf6a36fdee60c3a9a0a4d075a6e8807798fe5e443106a
- 268571fc240204b17d9989379d184efb984458ce5b6a593ed3178e8a4b62cc17
- 8814e9aad599c98bb01ea9690c1afbb8d891bf1e6f50f0bc1d23fd8887e7411b
- 4cd9c04390f2b7171e50e1c0b1afde499160aac0da9aed28ee5677863a389c5e
- 753113c77192320f1844f132143f106e5dc73b271e44c2a3b214205eea8e42df
- 17224da53b266c1a7e487d95b57ad47c21dec82ca42056a785dd816555d46967
- db4703a6cea9b700cc17b527e7d0a4e228bdd41659bece18c65f0877724c87a4
Coverage

Screenshots of Detection AMP
ThreatGrid
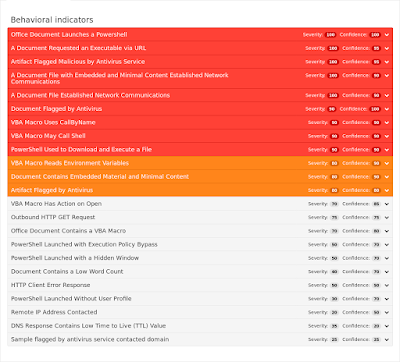
Umbrella
Vbs.Downloader.Trickbot-6333852-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Local\c:!users!administrator!appdata!local!microsoft!windows!history!history.ie5!
- Local\WininetConnectionMutex
- Local\_!MSFTHISTORY!_ IP Addresses
- 37[.]220[.]90[.]208 Domain Names
- annmcclean[.]co[.]uk Files and or directories created
- %TEMP%\cNyXqxuTxfU.exeA
- %TEMP%\cNyXqxuTxfU.exe File Hashes
- 42747cdefebee5af8ae2899825fa6d0bbd1d52a853ec1262f1395310a42d4726
- 43be972338fd27a180a5b6540b212513377491f3a16cc750b67c8150e8e0d3f1
- 9033a377113f80beedde5575de1fe832bb0e49b9bc6e33851b26e8c8a47fd6d8
- cd0e8181c7276b138793366c3fbb3a58275225fed8c434185db56dfcda421f7b
- e10be1a5388458c128fc832afca671d3fdaa30195737b0935fd8ef80314afc68
Coverage

Screenshots of Detection AMP
ThreatGrid

Umbrella
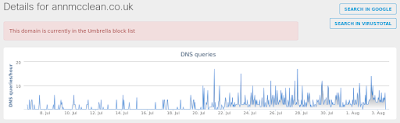
Win.Downloader.Psys-6334750-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- thephotoblog[.]xyz Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Start Menu\Programs\Startup\[0-9]{9}.exe
- %SystemDrive%\psys2\psys.rar
- %SystemDrive%\psys2\<extracted rar achive files> File Hashes
- 1beb16a8467a8957d1a752c396e1a50fceab554498ce9ea65396c37d07e8a28d
- 498a9cf24d40c098ec793e13e96f7a5001984b3f6436271fdde5ff88c23b88f5
- 6d7ed964e02fc1a370777d3f2baf1a279ff6bd85f5240d49735f62f909978542
- 9e21521a7264a76e4ba6b6f3f2f518fb8f95b4b3cfa2a45028fa43be46916095
- e1d407c2b954c9c705431fe9c7d7a9f8995441015414a20381bdc502534c50eb
- f4313a33210b75ba928e5bf91df91f2d1fe7b75d2971b2c9e11c0f4d76dedb35
- fb536d40d118322f31746a577c400488e1020ea8073cf36cfe37712f91e27cb3
Coverage

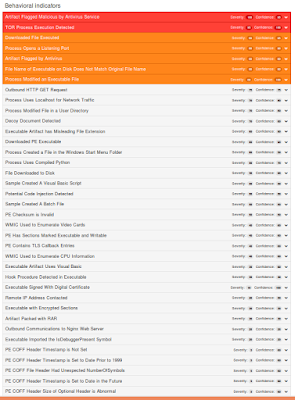
Screenshots of Detection AMP
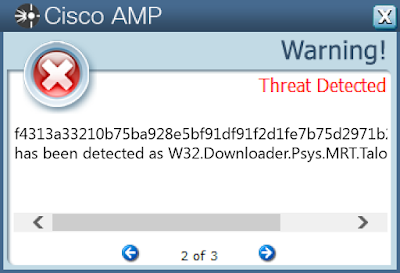
ThreatGrid
Umbrella
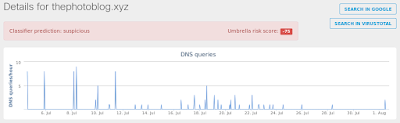
Screenshot
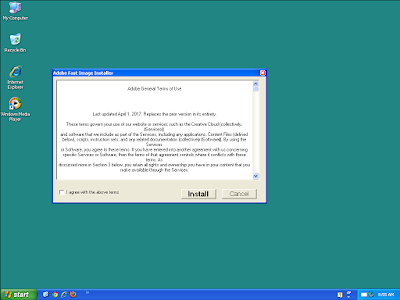
Win.Downloader.Upatre-6333840-1
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- technopoleci[.]com
- pearlstours[.]com Files and or directories created
- %Temp%\lisca.exe File Hashes
- 0f6325d3fd6177cee19770b12d97efa8da46cb23a7173e227efc2291e59034d3
- 19a4c65bc812eb74df5b41c058f345c5a4fbc838de59e4127e4cf784770a63df
- 23da35463015938e649624b1e606507fc1c36998a3cdb730f02309055609bd2f
- 249698d153aec8b19f511529aae5efc852cacbbc4f45020e4b9a3bdea933a6fa
- 570323e1150fe8e0802b03eb7848452c89ea1247512365bdb8621ecac4d15507
- 5f2c8ac317bf4d58610c803c01c95d358cb25600f632644e01d5c31a74fd2554
- 5f3a9efa98d7acfb0793292b2475eba2d547632c63f3b4ca5d1958731d264506
- 6c44efb2baabb7b66849e69567c8b3394919efdb2491a1392ff237090c380f1f
- 75309ff6942162fa19e4c7d430456a699cbee26106afeffc71f02325c9ab37c4
- 8978bcef1799a5ea3324ce88b9a848e85987958b8ea7dcc0ba511120e6602aa0
- 9d4effa16fa83e12179a674966af8a49bb592fa58de53ee2866f5ceda8206733
- a67638a9940841bc5222a160b0d28930c5244be769e6091122cfc7aaefa71335
- ad54d0d8d9b80aff216cc9097849efc52b2990a6b8f9d6a24f9a22709be35267
- c707645487cd7d7c8001fa40cfa2475c23705f65048c3831eefb5580e39b3845
- c75bc2341ed612c8e5154cb88e7110544e3ff59fed30af28e441c0d31d088da8
- c9975f106e8e0e7ceee70bd285159226e7687076a0e3b84c525a953657f6b1ff
- eb0601efd61b34a2fac8468b613913983c2b1968b77aec8848c2dddf4443e952
- ec439a41172d7683ee803e336e4b175b8baebc8d4ceed40c6b63b5649d7855ff
- f6ae56489c1063a48079b1cf5c1252a8f1f3af70918c58fed90ce453bd6cec9e
- fc0f51ffddad995a4588fbc28d10d0037cc36708e4875a057629bd5a2d975a43
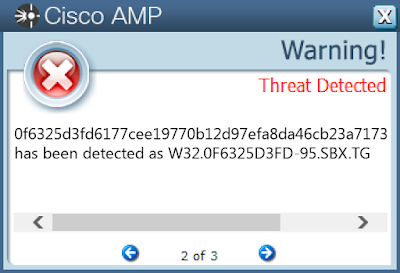
Coverage
Screenshots of Detection AMP
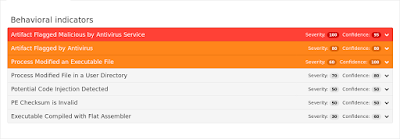
ThreatGrid
Win.Packer.VbPack-0-6334882-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- \BaseNamedObjects\4EAB18A7EBDA2A0128649942 IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %AppData%\7EBDA2\2A0128.hdb
- %AppData%\win32.exe
- \samr
- %SystemDrive%\Documents and Settings\Administrator\Start Menu\Programs\Startup\win32.vbe File Hashes
- 2095d70fb739a0fe1af7a0c17d28934fff79fdabe5412c90d01aa103ba409452
- 29a438f87f3cba8d92f0892d551d9a1392fa4f00790aa006cdf098f377c3e419
- 2f6ba28b1e011f466c697853af8033986a2d2d629ad4e7c833f8e34762d357a9
- 342a928efa083ab47f29d83c3886799fc9c344e1d4122f628299c0acf85b12d8
- 507af0c158e03bd967d856d6310c842acd8aa3118612840fa395c201185ace9d
- 5a20fefb3bdb7b6357f7e00bf66bb7fca4d3a6be566856370793088e94118a1d
- 69aca79fc824166616de124a89c7a78cd25c097a6df951ba9943ea6867afbb6d
- 714264ce71ef28fa86a37abcdb8eaa726ce80e52a87e4b1fb20c1522e72088f9
- 799b05b59250e3316a1f1b583e1a5e82f66f0f3756dc8616b7f572e723a208cf
- 7cb3eca68f707bfeb7fda5cf549b9c1cebe9ed4cb06dd3a17cd5c1d07364462e
- 80d0e916ee763752670f8425bbb3df60db22d96566f3e8bc273fb9cf1ca57dee
- 8a0de6f0099dd38a0a34d7eb3319d6eb89b4ef3bc9835ea9dcb33dcb1dd0a47e
- b5b5a289ff062eec0d5db7a081fe69e85c16500194dc45be18e038aa6f7cd109
- d2cb512fa85e3d77072a10e9a107d44e79e2017b7c182db29008b5edabc53e00
- dfa7f428e0cee8bf254d8a33b685082e90723cd318bce9df59450dfa7a3fb6d0
Coverage
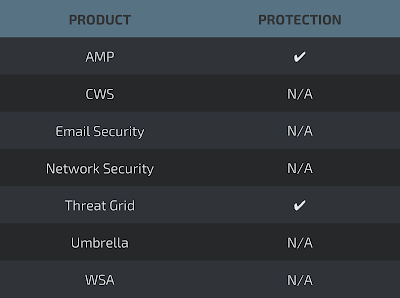
Screenshots of DetectionAMP

ThreatGrid

Win.Trojan.DownloadGuide-6335034-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Internet Explorer\Main\WindowsSearch
- HKU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Extensible Cache\MSHist012017080320170804
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Network\Location Awareness
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\Software\Wow6432Node\Microsoft\Tracing Mutexes
- DlgCpp
- MSIMGSIZECacheMutex
- _!SHMSFTHISTORY!_
- Local\WininetConnectionMutex
- Local\_!MSFTHISTORY!_
- \BaseNamedObjects\DlgCpp
- RasPbFile
- Local\ZonesCacheCounterMutex
- Local\WininetStartupMutex
- Local\IESQMMUTEX_0_274 IP Addresses
- 104[.]40[.]188[.]185
- 72[.]21[.]81[.]200
- 104[.]40[.]156[.]71 Domain Names
- cs9[.]wpc[.]v0cdn[.]net
- dlg-messages[.]buzzrin[.]de
- dlg-configs[.]buzzrin[.]de
- dlg-configs-weu[.]cloudapp[.]net
- az687722[.]vo[.]msecnd[.]net
- dlg-messages-weu[.]cloudapp[.]net Files and or directories created
- %TEMP%\DLG\ui\offers\3cc9566f4a803e726fe2ff36e63a6bc3\uifile.zip
- \Users\Administrator\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012017080320170804\index.dat
- %TEMP%\DLG\ui\offers\2f682d34f7ca97e9988360367f18412e\uifile.zip
- %TEMP%\DLGCBB2.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\3cc9566f4a803e726fe2ff36e63a6bc3\uifile.zip (copy)
- %TEMP%\DLG\ui\offers\4eee8661eff0ab9af2f73a9c050f7d06\uifile.zip
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\2f682d34f7ca97e9988360367f18412e\uifile.zip (copy)
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\2f682d34f7ca97e9988360367f18412e\uifile.zip.part
- %TEMP%\DLG\ui\common\progress\progress.zip
- \TEMP\8b55500ba6953f1a232fb2fffa7c55a29a4fbec6a353f3ad6da670fc911aac33.exe
- %System32%\wdi\{ffc42108-4920-4acf-a4fc-8abdcc68ada4}\{bc3d8877-b46d-4746-b041-b538af5e2cf0}\snapshot.etl
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\common\progress\progress.zip (copy)
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLGD.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\18b3f294321c1361e5232935c8e4ab35\uifile.zip (copy)
- %System32%\wdi\LogFiles\WdiContextLog.etl.001
- %TEMP%\DLG\ui\offers\18b3f294321c1361e5232935c8e4ab35\uifile.zip
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\b027951991b0ce592b2d579b8888057c\uifile.zip (copy)
- %TEMP%\DLG\ui\common\base\base.zip
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\b027951991b0ce592b2d579b8888057c\uifile.zip.part
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\common\progress\progress.zip.part
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\18b3f294321c1361e5232935c8e4ab35\uifile.zip.part
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\common\base\base.zip.part
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\common\base\base.zip (copy)
- %System32%\wdi\{533a67eb-9fb5-473d-b884-958cf4b9c4a3}\{a69f0170-8245-4aed-a99e-3b0aad202ce2}\snapshot.etl File Hashes
- 8b55500ba6953f1a232fb2fffa7c55a29a4fbec6a353f3ad6da670fc911aac33
- 756901560838b9d1ec9fe20300c772d336629d1d3e8a798626bc2009d433620d
- 17d58fb6ca87a08d515681c3f11ebc72667aae66fd59cc5f400cf893189b5ce1
- 3cc8c8b086f33d5ed62a5d9088d53693f31237473cbcf5268919c7cea016193e
- b5b6de4fd07c9929f1a066dd3d27fc3f0ccc72a6f0f3f9336b60f9445150e336
- 37da3a745745ad81a3b20bcbbc43a0bca6e88991a7812f833751b8be642e3bc0
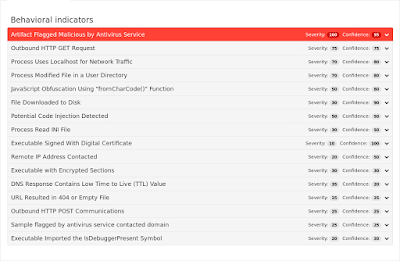
Coverage

Screenshots of Detection AMP
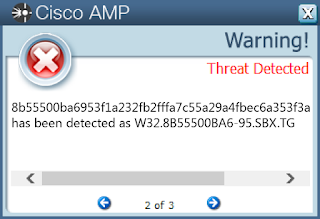
ThreatGrid
Umbrella
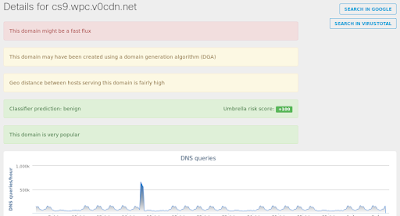
Win.Trojan.Madangel-1
Indicators of Compromise
Registry Keys
- HKU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\LANMANSERVER\PARAMETERS
- Value: AutoShareWks
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\LANMANSERVER\PARAMETERS
- Value: AutoShareServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: Serverx
- <HKLM>\SYSTEM\ControlSet001\Services\Eventlog\Application\Microsoft H.323 Telephony Service Provider
- <HKLM>\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List Mutexes
- Angry Angel v3.0
- shqq
- \BaseNamedObjects\Angry Angel v3.0 IP Addresses
- N/A Domain Names
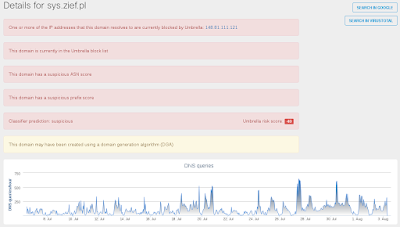
- sys[.]zief[.]pl Files and or directories created
- %WinDir%\Prefetch\WMIPRVSE.EXE-28F301A9.pf
- %WinDir%\SysWOW64\Serverx.exe
- %System32%\drivers\etc\hosts File Hashes
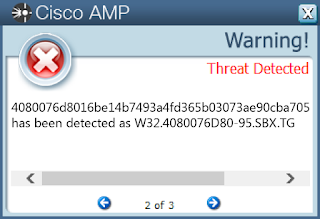
- 4080076d8016be14b7493a4fd365b03073ae90cba70590b25039ef76b2d36aea
- 7ad3924efe8802153b9dadc5bc055b329ec8c2850b91dc5f5a1bba42533a8758
- 3ad3d18277238e0a6e0a84a6e901395ad647466a0e68275a7426203216b05025
- fbf9d40bc0abe116c19404298d324fcb5a2ddd19d2d97dc31418446be3637a22
- a010da80c2d35d420958b858fc1e5e700fab866799aa786e1feab4fba5ee6dbb
Coverage
Screenshots of Detection AMP
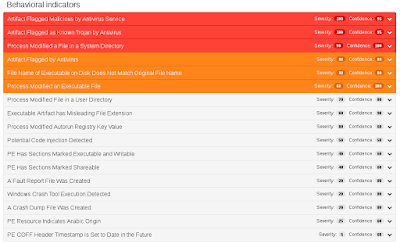
ThreatGrid
Umbrella
Win.Trojan.Nitol-6335025-0
Indicators of Compromise
Registry Keys
- <HKLM>\System\ControlSet001\Services\Sertiey\ImagePath Mutexes
- N/A IP Addresses
- 103[.]235[.]46[.]39
- 119[.]29[.]112[.]122 Domain Names
- www[.]a[.]shifen[.]com
- www[.]baidu[.]com
- ubcRCeHZx[.]nnnn[.]eu[.]org Files and or directories created
- %WinDir%\Debug\eiahost.exe File Hashes
- 917b400da5befe32d00e0503a05cb2f1d635ace6029e30e2ba034da93d4927af
- 2136e6be115617349992b506aced588dced1f5496e97443dfcc31344873f624d
- 2b21ea686281211c8ba3a548128c310b7b239697ca8cd590c26353f5fd14cccf
- 830c3bf61e613137ce7fc5eb3a4205519bb021ef9ea179382559c398caf24dc2
- a82a94d3d964f48d344459f39be5f7b76c09c91f8374517a0315d3e7d069b73c
- e018f2cb152ab5c9bedef63a760b223eb91e965703a691877550ca390e46ea84
- b359d8aa7b59c52aa7e6ce32f1a8bfbf8ff95e2a50c3b44f434fda77cfbcf82d
- c06616aff5c46d7788c48b873b11a6aa9518ab8f1c075e164ef6c968207f845f
- 3a60cd3ab3cd6e71d0836f24231da876a6996a9d556d4e290d0af70b53b0b659
- ed90bd5202eb621c7e44b25e83b1222efbd98094efbfc84d10ed4e12a89cc284
Coverage

Screenshots of Detection AMP
ThreatGrid