Today, Talos is publishing a glimpse into the most prevalent threats we've observed between August 25 and September 1. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Doc.Downloader.TrickBot-6336123-0
Downloader
Campaigns continue to distribute new TrickBot samples through malspam & document based downloaders. This recent variant of downloader mimics account correspondence from a large financial institution, but the macro used for fetching a TrickBot sample has been stripped down to a simple deobfuscation & shell invocation. - Doc.Dropper.Agent-6336106-0
Office Macro Downloader
This is an obfuscated Office Macro downloader that attempts to download a malicious payload executable. - Doc.Macro.Obfuscation-6336014-0
Office Macro
This cluster of Office Macro documents use the same obfuscation technique to prevent quick analysis. Manual analysis of the obfuscation technique shows many variables and instructions that are not used or evaulated to junk code. - Doc.Trojan.Agent-6336128-0
Office Macro based downloader
This set of downloaders uses string obfuscation in VBA to build a download command for the shell and execute it with the VBA Shell function. It was recently observed delivering TrickBot among other paylods. - Vbs.Trojan.VBSTrojan-6336102-0
Trojan
This Visual Basic script downloader fetches a binary from the internet and install it into the system. - Win.Malware.Dinwod-6336124-0
Dropper
Dinwod is a polymorphic dropper. It copies modified versions of itself to the root directory then deletes the original file. The copies drop the payload DLL in the Windows directory, then force legitimate processes to run the payload via DLL injection. - Win.Trojan.AlmanCloud-6336008
Trojan
This is a Trojan. It contains many anti-debugging and anti-vm tricks to hinder the dynamic analysis and detect instrumented envrionments. The binary can try also to register itself as a Windows service and it modifies the host file. Moreover, it has functionalities to infect USB drives plugged to the victim's computer and it may work also as keylogger. Finally, it has code to contact remote servers and upload the collected information. - Win.Trojan.Cuegoe-6336130-0
Trojan
This is a trojan downloader. The payload varies and is unpacked inside a lengthy linear decryption routine.
Threats
Doc.Downloader.TrickBot-6336123-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Global\PowerShell_CommandAnalysis_Lock_S-1-5-21-2580483871-590521980-3826313501-500
- Outlook_Perf_Library_Lock_PID_90c IP Addresses
- 210[.]16[.]102[.]251
- 216[.]239[.]32[.]21
- 93[.]114[.]64[.]118
- 5[.]152[.]210[.]179
- 146[.]255[.]36[.]1 Domain Names
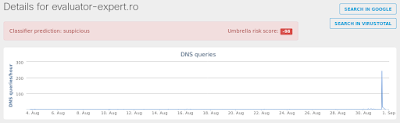
- evaluator-expert[.]ro Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\bicprcv.exe
- %AppData%\winapp\Modules\systeminfo64
- \srvsvc
- %TEMP%\cdqfm.bat
- %AppData%\winapp\group_tag
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\cdqfm.bat
- %TEMP%\bicprcv.exe
- %AppData%\winapp\Modules\injectDll64_configs\dpost
- %AppData%\winapp\Modules\injectDll64_configs\dinj
- %AppData%\winapp\aganpat.exe
- %AppData%\winapp\Modules\injectDll64
- %AppData%\winapp\client_id
- %AppData%\winapp\ahboqbu.exe
- %AppData%\winapp\Modules\injectDll64_configs\sinj File Hashes
- 14ab690a2f5d4fd74f280804a1b59f5c5442c1280e79ee861e68a421cac80ce3
- 2419210bdd20b352b357573e72eb82bafa801b078f25517546bd348e2e93a505
Coverage

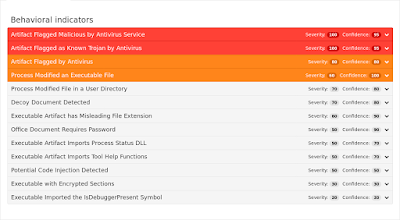
Screenshots of Detection AMP
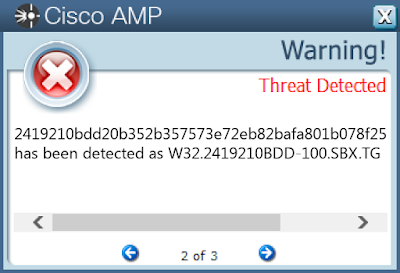
ThreatGrid
Umbrella
Screenshot
Doc.Dropper.Agent-6336106-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 185[.]165[.]29[.]27
- 185[.]165[.]29[.]129 Domain Names
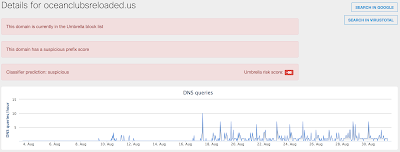
- oceanclubsreloaded[.]us
- oceanfreightclubs[.]ir Files and or directories created
- \TEMP\New Purchase Order.xls
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\40DVD2HR\OT[1].exe
- %AppData%\Microsoft\Office\Recent\New Purchase Order.LNK
- %AppData%\Microsoft\Office\Recent\272622119.xls.LNK
- %TEMP%\wbfg.exe File Hashes
- 56ef4bb6608968653af98649fddf204933134038b6b27b118ebedcdc5ec5af0e
- 946def9e50a762ef29de5b56086d976f26446f0bcb5f2590c0354eae1318e0fb
- 220128b685d4e96e793756636e32257b8fd22e038890d8f194d1681343bea923
- a4ad5629d490b466e4e62bf9048968ff45466c73849609b64d6617bf32e5cc5f
- d6ece69e9f8035de573411d57ea11e0bb22d243e0d47b620b9cb99793218b121
- aecf2b9c77b76f08c6a240cd5b0782f3abba0a872caea783f5105b3b3f42851a
Coverage
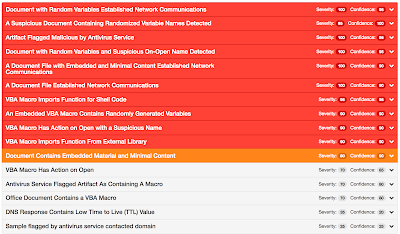
Screenshots of DetectionAMP
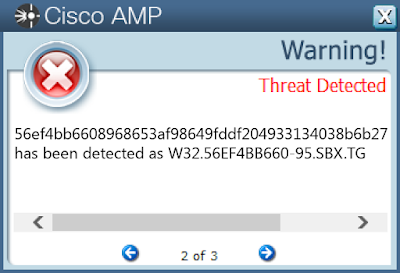
ThreatGrid
Umbrella
Doc.Macro.Obfuscation-6336014-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CERTIFICATES
- Value: 3488D8938CAA8400F802C2439F4B8FCDCE406396
- <HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CERTIFICATES\3488D8938CAA8400F802C2439F4B8FCDCE406396 Mutexes
- socket.1
- socket.0
- tty_list::mutex.0
- socket.2
- Global\刐ƶ IP Addresses
- 82[.]195[.]75[.]101
- 91[.]219[.]237[.]229
- 109[.]163[.]234[.]8
- 38[.]229[.]72[.]16
- 23[.]21[.]138[.]252
- 31[.]185[.]104[.]20
- 78[.]47[.]38[.]226
- 104[.]20[.]73[.]28
- 184[.]73[.]220[.]206
- 46[.]28[.]110[.]244
- 81[.]7[.]16[.]182
- 198[.]199[.]64[.]217
- 174[.]129[.]241[.]106
- 50[.]19[.]238[.]1
- 154[.]35[.]132[.]70
- 62[.]210[.]92[.]11
- 72[.]21[.]81[.]200
- 151[.]80[.]42[.]103
- 5[.]39[.]92[.]199
- 86[.]59[.]21[.]38
- 192[.]30[.]255[.]120
- 192[.]30[.]255[.]121
- 185[.]100[.]86[.]128
- 144[.]76[.]163[.]93
- 178[.]62[.]22[.]36
- 104[.]20[.]74[.]28
- 51[.]254[.]101[.]242
- 46[.]252[.]26[.]2
- 89[.]45[.]235[.]21
- 192[.]168[.]1[.]1
- 178[.]62[.]86[.]96
- 178[.]62[.]197[.]82
- 52[.]173[.]193[.]166
- 192[.]168[.]1[.]255
- 120[.]29[.]217[.]46
- 138[.]201[.]14[.]197
- 86[.]59[.]119[.]88
- 192[.]30[.]255[.]113
- 192[.]30[.]255[.]112
- 85[.]25[.]116[.]81
- 107[.]22[.]255[.]198
- 23[.]23[.]170[.]235
- 192[.]168[.]1[.]127 Domain Names
- fv-st-konrad[.]de
- www[.]fv-st-konrad[.]de
- api[.]ipify[.]org
- api[.]nuget[.]org
- chocolatey[.]org
- dist[.]torproject[.]org Files and or directories created
- %AppData%\Mozilla\Firefox\Profiles\1lcuq8ab.default\cert8.db
- %TEMP%\ts\lib\net40\fr\Microsoft.Win32.TaskScheduler.resources.dll
- %TEMP%\ts\lib\net452\it\Microsoft.Win32.TaskScheduler.resources.dll
- %AppData%\MS\s\SECURITY
- %AppData%\MS\s\EXAMPLES
- %AppData%\MS\s\socat.exe
- %TEMP%\ts\lib\net40\zh-CN\Microsoft.Win32.TaskScheduler.resources.dll
- %System32%\config\TxR\{016888cc-6c6f-11de-8d1d-001e0bcde3ec}.TxR.blf
- %AppData%\MS\Tor\tor.exe
- %AppData%\tor\cached-microdescs.new
- %AppData%\tor\lock
- %TEMP%\ts\lib\net20\zh-CN\Microsoft.Win32.TaskScheduler.resources.dll
- %TEMP%\ts\_rels\.rels
- %AppData%\MS\Tor\libgcc_s_sjlj-1.dll
- \TEMP\~$L Information.doc
- %TEMP%\ts\lib\net35\es\Microsoft.Win32.TaskScheduler.resources.dll
- %System32%\Tasks\MRT
- %System32%\Tasks\SC
- %TEMP%\ts\lib\net40\JetBrains.Annotations.xml
- %AppData%\MS\Tor\libevent_core-2-0-5.dll
- %TEMP%\ts\lib\net40\JetBrains.Annotations.dll
- %AppData%\MS\s\cygreadline7.dll
- %TEMP%\ts\lib\net20\JetBrains.Annotations.xml
- %AppData%\MS\Data\Tor\geoip6
- %AppData%\Mozilla\Firefox\Profiles\1lcuq8ab.default\prefs.js
- %TEMP%\ts\lib\net20\Microsoft.Win32.TaskScheduler.XML
- %TEMP%\ts\lib\net35\zh-CN\Microsoft.Win32.TaskScheduler.resources.dll
- %TEMP%\ts\lib\net20\JetBrains.Annotations.dll
- %WinDir%\AppCompat\Programs\RecentFileCache.bcf
- %AppData%\MS\Tor\zlib1.dll
- \Users\Administrator\Documents\20170822\PowerShell_transcript.PC.SLCVvGfn.20170822125043.txt
- %AppData%\tor\cached-microdesc-consensus
- %TEMP%\ts\lib\net40\Microsoft.Win32.TaskScheduler.XML
- %TEMP%\ts\lib\net35\it\Microsoft.Win32.TaskScheduler.resources.dll
- %TEMP%\ts\lib\net20\Microsoft.Win32.TaskScheduler.dll
- %AppData%\MS\Tor\libevent-2-0-5.dll
- %AppData%\MS\Tor\tor-gencert.exe
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{16FC3937-61E8-4A38-8962-5CC96E748100}.tmp
- %AppData%\MS\s\cygssl-1.0.0.dll
- %TEMP%\ts\lib\net40\es\Microsoft.Win32.TaskScheduler.resources.dll
- \Users\Administrator\AppData\Local\Microsoft\Windows\WER\ReportQueue\AppCrash_mshta.exe_b620274e31657385a0786969c6cab647bc5a5eb0_48824423\Report.wer
- %TEMP%\ts\lib\net40\it\Microsoft.Win32.TaskScheduler.resources.dll
- %AppData%\MS\s\cygwrap-0.dll
- %TEMP%\ts\lib\net452\Microsoft.Win32.TaskScheduler.dll
- %AppData%\MS\s\cygncursesw-10.dll
- %AppData%\MS\s\VERSION
- %AppData%\MS\Data\Tor\geoip
- %AppData%\MS\s\README
- %TEMP%\ts\lib\net35\JetBrains.Annotations.dll
- %TEMP%\ts\lib\net452\es\Microsoft.Win32.TaskScheduler.resources.dll
- %TEMP%\ts\lib\net35\JetBrains.Annotations.xml
- %TEMP%\ts\[Content_Types].xml
- \Users\Administrator\Documents\20170822\PowerShell_transcript.PC.tnwsG1BN.20170822125100.txt
- %TEMP%\ts\lib\net40\Microsoft.Win32.TaskScheduler.dll
- %AppData%\MS\s\cygcrypto-1.0.0.dll
- %AppData%\MS\Tor\libssp-0.dll
- %TEMP%\ts\lib\net35\fr\Microsoft.Win32.TaskScheduler.resources.dll
- \TEMP\DHL Information.doc
- %TEMP%\ts\lib\net20\it\Microsoft.Win32.TaskScheduler.resources.dll
- %AppData%\MS\Tor\libevent_extra-2-0-5.dll
- %TEMP%\ts\lib\net452\Microsoft.Win32.TaskScheduler.XML
- %AppData%\tor\cached-certs
- \Users\Administrator\Documents\20170822\PowerShell_transcript.PC.PBM+k85t.20170822125056.txt
- %TEMP%\ts\lib\net35\de\Microsoft.Win32.TaskScheduler.resources.dll
- %System32%\config\TxR\{016888cc-6c6f-11de-8d1d-001e0bcde3ec}.TxR.0.regtrans-ms
- %AppData%\MS\s\BUGREPORTS
- %TEMP%\ts\package\services\metadata\core-properties\b413d53c92364baa9958fdda02cd8e9a.psmdcp
- %TEMP%\ts\lib\net20\es\Microsoft.Win32.TaskScheduler.resources.dll
- %AppData%\MS\Tor\libeay32.dll
- %TEMP%\ts\lib\net20\de\Microsoft.Win32.TaskScheduler.resources.dll
- %AppData%\MS\Tor\ssleay32.dll
- %TEMP%\ts\lib\net452\JetBrains.Annotations.dll
- %TEMP%\ts\lib\net40\de\Microsoft.Win32.TaskScheduler.resources.dll
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\40DVD2HR\api_ipify_org[1].txt
- %TEMP%\ts\lib\net35\Microsoft.Win32.TaskScheduler.dll
- %TEMP%\ts\lib\net452\JetBrains.Annotations.xml
- %AppData%\MS\s\FAQ
- %TEMP%\ts\lib\net20\fr\Microsoft.Win32.TaskScheduler.resources.dll
- \Users\Administrator\Documents\20170822\PowerShell_transcript.PC.MiXmZ0jf.20170822125034.txt
- %System32%\Tasks\SUT
- %AppData%\tor\state
- %TEMP%\ts\lib\net452\zh-CN\Microsoft.Win32.TaskScheduler.resources.dll
- %TEMP%\7238.exe
- %TEMP%\CVRD4FC.tmp.cvr
- %AppData%\MS\s\CHANGES
- %TEMP%\ts\TaskScheduler.nuspec
- %TEMP%\ts\lib\net35\Microsoft.Win32.TaskScheduler.XML
- %AppData%\MS\s\README.md
- %AppData%\Microsoft\Office\Recent\DHL Information.LNK File Hashes
- bce01bde972b5d97e6bc163cd632fa7c2a1e9f1913abe69f8eb25d22a06063c8
- 029923c7508a27907e2c88baf9cc2effa2f78e81f4728eae2c185935f2a51fbd
- 07b63a132b60b293532787b50c7765c6af9cebcc0449592ad31dec1198fc8b5a
- 12c9ae29a83bf6ecf5766d9f51a2927d586bed20c3d37e4e150ffecadf8cd010
- 2d1cbae9da80482fffdbbcc4f761e5b12ffbfeb2446026862d381ac80fa0f335
- 4c5c70e7c517e35f93fd65aa493a9bbad63561ad7dc8b5235e23ca843c9c274e
- 5d683f41aa10da94c4737aa8901fc92b93d4f5484f4728bcbd802b9336275d59
- 8b3c33104719d76829977a595901992bb7183ded8f5d1ef379281c7c158ef803
- 900df27eff06c022c5fc9f6ebdb6f5f1a1e9d65c2de1d5f6300c899937bb95e7
- 9ef470811ceaab0d47bb4b8e0abdf7d783902c208fedda35f8292b60af7f6870
- d3bc718d0cb24a9ffb25ae75d413f29fdb173e9174fd07d06ee8bb49ebec2330
- e433044ade8b09c97cd4b2008bccb9f12d45e32f84a94efbc800754c58ed3eb2
- efe8092be61ec8c11d6152fbf569517299f3a17322a14d5e1c13350ceaeac223
- ff428dd61e1f50b36e6fc6707054840c0912455bea073edc5806467ca8cb7046
- 0009657099e7e3f555a68ae39827099905339f5dafe648585175de089a75ba6b
- 3724ecf98a0a71f54c227e00417bf0ea603ca480ac6db2a2708cc275f6227104
- 44cd48611f0044d98082ba3dd816b61fe80ee91812fc05ee1f3f37690f51bacc
- 488f6347913c580600ca24527ab8a0f3d2129c597a6398cc857eec4f1b0348c1
- 4b9f88762b2eb226b86c5bb4ce04b4ffcd07d0e332bbc92ed6dd2d7d451c8269
- 57c8d5b413e5ddc4bbf416ef8ac9b902eb1058e18b79e76ef5340c835c9cfa73
- 6fe1e272df58349481d71357488f08fda7bf4709cd72be00ce5e42c244783649
- 6fef1c02e5d06c9cd2b29fee73e796791b7b84a1875ff19296140d49823621ae
- 6ff2121b359d8a2776c25293aa96b823759b0796e559e70bc6d2e8adaf208fd7
- 8b0d3d287580a5095e92aaf357bb39e1ab754dd3eaa4ca9c2f7ee4727f5649dd
- 8e03b31baaa847ffef1df04336d7629bd8c8ca169406768479114b91b96c9092
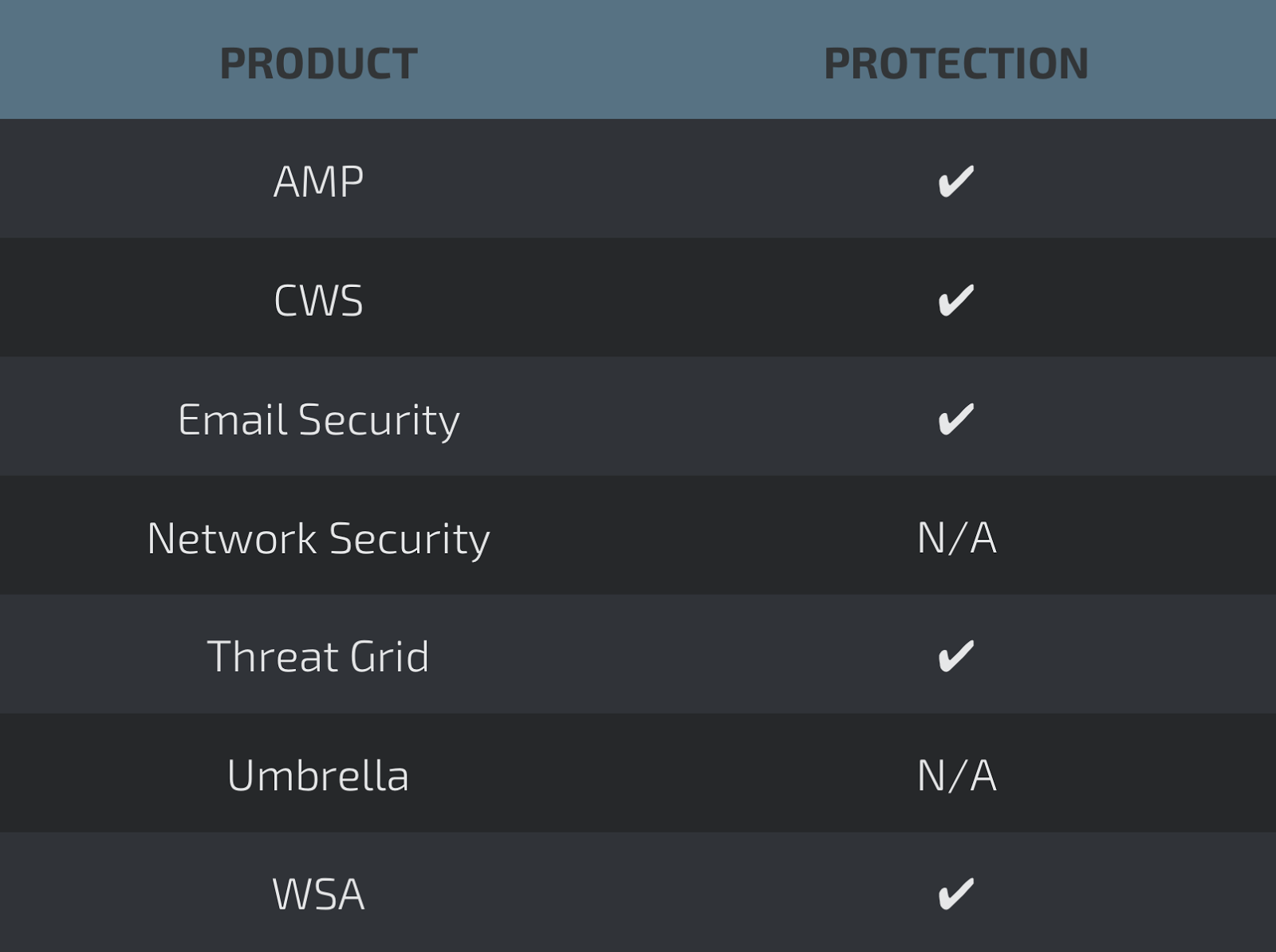
Coverage
Screenshots of Detection AMP
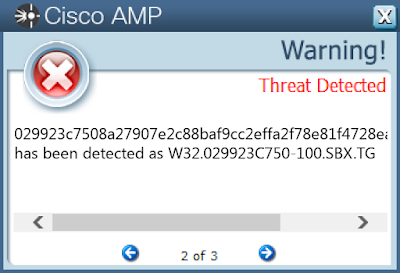
ThreatGrid
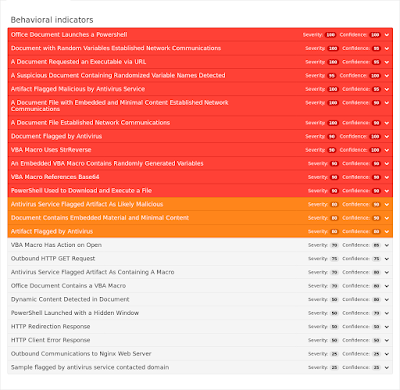
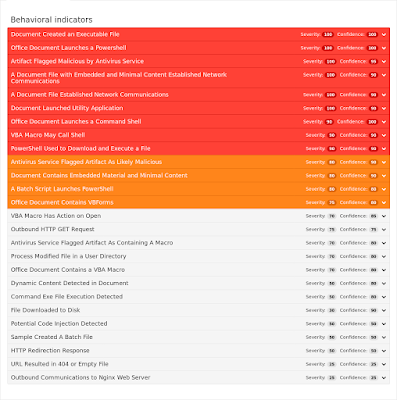
Doc.Trojan.Agent-6336128-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 216[.]138[.]226[.]110
- 64[.]182[.]208[.]181
- 5[.]152[.]210[.]176 Domain Names
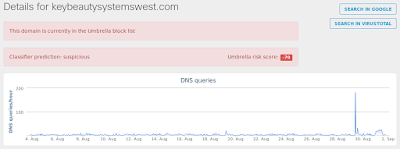
- keybeautysystemswest[.]com
- icanhazip[.]com Files and or directories created
- %AppData%\winapp\Nkahvx.exe
- %AppData%\winapp\client_id
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\Olaiwy.exe
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temp\lubuj.bat
- %AppData%\winapp\group_tag
- %WinDir%\Tasks\services update.job File Hashes
- 9557c5337e1ebcc8dfe36e284be35c32ce22d2a4fbac56602d326598594899a8
- b20fac264fb5724f17caafc34df08fc57879c0b30d360352a8e2b1ae3f9c2022
- e77b85c8d93c7d1093eeea80621ad45ab3f091d537837a425b4e8829a2041aa4
- fef300c8fad4477c75fd83aaa5a0033ee79c46e948148b4a7ed372943c306f5d
Coverage

Screenshots of Detection AMP
Umbrella
Umbrella
Screenshot

Vbs.Trojan.VBSTrojan-6336102-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Network\Location Awareness Mutexes
- N/A IP Addresses
- 138[.]128[.]191[.]146 Domain Names
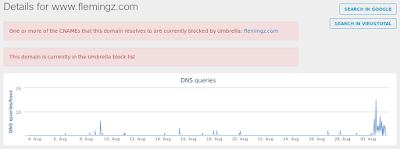
- www[.]flemingz[.]com
- flemingz[.]comFiles and or directories created
- %TEMP%\ReAIquyDcG.exe
- %TEMP%\ReAIquyDcG.exeA File Hashes
- 940723f511b9ecaf14478330baa01d4384f168de4b9c25a42e2865fde11067e4
- 5bf717cf8794bc159f95b59fb73e46d8e46fcca03d5dca9b47d0b398fb9db17a
- a9832474a614d15382a50954c3adf5ab7774698dcf57417c80f2abc640399639
Coverage
Screenshots of Detection AMP
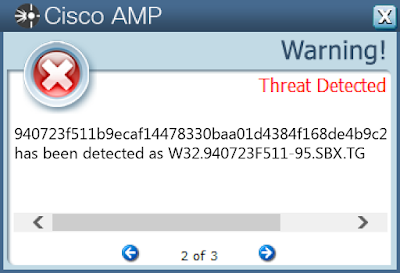
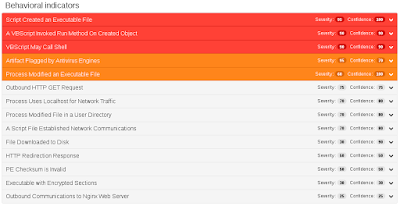
ThreatGrid
Umbrella
Win.Malware.Dinwod-6336124-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %SystemDrive%\jr8g6w6.exe
- %SystemDrive%\3t9bd.exe
- %SystemDrive%\dvdvv.exe
- %SystemDrive%\69w460.exe
- C:\Windows\friendl.dll File Hashes
- 002eb4fddf6e8f9165e28694da6f368626282bd7e99c11f1eaeb365339c2331a
- 01b538e451a390f7cfcdc263355dca070ea1a578d083fa94762912cff36b226b
- 026a7284b6420e06f20e683054e0ed01a0afa14321fe4094c14bdb63a46ee17f
- 04d8c0fd0f85b534c8a225be38e7bda9dc7edc248b1f6419fb64a99fde5b4b11
- 050e9daae7c0778e00b17a71d70f34a9ec60c7ac1d309d53ffd23e7a74f81b2e
- 06ebf78a7f2f3cbc7a8961051f3bfe9211b8dc8fd255be6f9df7b96f261a46ad
- 07509506034c49b52314ee53984af6556396da7070c9d0069324f555f722db6d
- 076e08eb3eae357b4ee75f9bc1e9fe8a9ea3b3e3ddafe244e0583e320a0bfd26
- 07ab8a56baed7f7014781b275e8324e8bb7974360ac05d017c65d40ed05e1869
- 07b5361cde1a670a587bd7d58160c97282415a025b4b9d1efa806a121e577027
Coverage
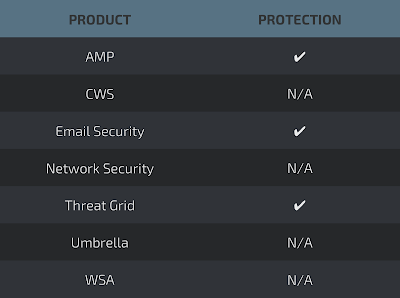
Screenshots of Detection AMP
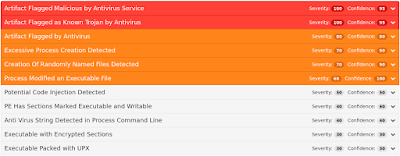
ThreatGrid
Win.Trojan.AlmanCloud-6336008
Indicators of Compromise
Registry Keys
- <HKU>\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
- <HKU>\SessionInformation
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKLM>\SYSTEM\ControlSet001\Services\Eventlog\Application
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- <HKU>\SessionInformation
- <HKLM>\SYSTEM\ControlSet001\Enum\Root\LEGACY_RASMAN\0000\Control
- <HKLM>\SYSTEM\ControlSet001\Services\Eventlog\Application\Microsoft H.323 Telephony Service Provider
- <HKLM>\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
- <HKLM>\SYSTEM\ControlSet001\Enum\Root\LEGACY_TAPISRV\0000\Control Mutexes
- \BaseNamedObjects\Global\RAS_MO_01
- Local\MSCTF.Asm.MutexDefault1
- \BaseNamedObjects\RAS_MO_02 IP Addresses
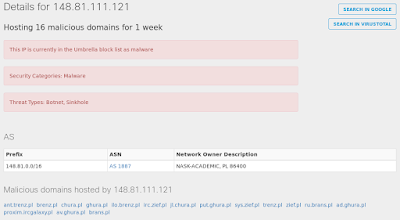
- 148[.]81[.]111[.]121 Domain Names
- klcwba[.]com
- ajiyoh[.]com
- dpwrjl[.]com
- uatcte[.]com
- imtxxh[.]com
- lobsyb[.]com
- xcckyn[.]com
- uvebwz[.]com
- iazfmh[.]com
- zisbon[.]com
- wyspqd[.]com
- oeuuvh[.]com
- udvjli[.]com
- abvjlx[.]com
- aoogeq[.]com
- ilo[.]brenz[.]pl
- lxoalw[.]com
- wvnyqa[.]com
- gnapgq[.]com
- cxniir[.]com
- gzoiji[.]com
- rrbuas[.]com
- tdsuye[.]com
- kfgsia[.]com
- vdbqhy[.]com
- ygmyqt[.]com
- upeuoz[.]com
- eqyaud[.]com
- wouaoc[.]com
- omkbel[.]com
- ioiufb[.]com
- eyakmj[.]com
- ukjqcx[.]com
- twngee[.]com
- bkegyi[.]com
- dgyolj[.]com
- ycztdl[.]com
- dtptuw[.]com
- aqqvuo[.]com
- ioafts[.]com
- caqiny[.]com
- zqkqzt[.]com
- dezims[.]com
- ukngdn[.]com
- ousvfo[.]com
- bdgxqr[.]com
- axqeuo[.]com
- bidnxy[.]com
- heuaot[.]com
- gqugaq[.]com
- aikuul[.]com
- eiijba[.]com
- qsjite[.]com
- btaeqx[.]com
- teioez[.]com
- obwijg[.]com Files and or directories created
- %System32%\wbem\Logs\wbemess.log
- \Users\Administrator\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF
- \Users\Administrator\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{684B4A19-F6D3-453D-B879-0BEB15FECE08}.FSD
- %System32%\drivers\etc\hosts
- \Users\Administrator\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF
- \ntsvcs
- %WinDir%\Prefetch\273142363.EXE-3748BAA7.pf
- \lsass File Hashes
- a0fc82de8afd8ac9d2a9df4c5f94ea0d44abdad70af70624f168c3c34036d35b
- 5e0fcf513867bb834af4ebb405a328d66838e528e32e420a89eab7b8619f1830
- 64091a671d00602e4f81f987207ac2b16f5c3e86f98add903bf369b528db2d38
- 9727223d176381c88f6f5f17a2e7f99981eaba31282a41c1ceb3158bccbe08f4
- f095ae655db18fb27667ece1c168b97d42b1b164991cda154022d6f8e270cd49
Coverage

Screenshots of Detection AMP
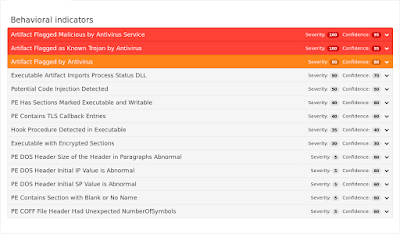
ThreatGrid
Umbrella
Win.Trojan.Cuegoe-6336130-0
Indicators of Compromise
Registry Keys
- HKU\Software\Microsoft\Office\12.0\Word
- HKU\Software\Microsoft\Office\12.0\Word\Resiliency\StartupItems Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\D.tmp
- %SystemDrive%\~$runme.docx
- %SystemDrive%\runme.exe
- %AppData%\Microsoft\Templates\~$Normal.dotm
- %SystemDrive%\runme.docx (copy) File Hashes
- 73c4f4e0dbe8bb08fa68c7aa73e44651a322d5a04e462e546d6cf0c9e4897235
- 6d20ac8668c1876117cfb7686d1dd71a82a88bc69595a9d698591a5ea41878b6
- c8810c54be65f65747458e905afaaf534202d2c6bd5dc681309a1872042946b3
- f3b527e625e6f198b5d44150bd4b5408935e57b7f7b395deba33f1662e2a2737
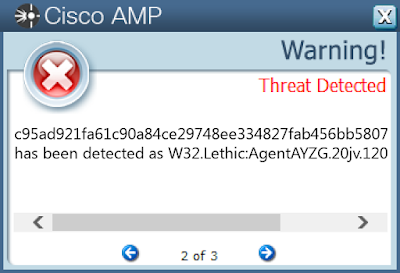
- c95ad921fa61c90a84ce29748ee334827fab456bb5807ad2f3e5c688bc539903
- 5f312c0ec89ad31cb819663059c97505cc72032f429cff33c61995ca651d52c0
- afc27b6c6deace69313e1e164257ca0b5e5ce003c34c79ca1dc43dd67129f081
- 55a8224f9b571776935e0340c9093b35b90b9138ef87e8484429b27c9ea61681
- 9edbd6e5cf7cfa8f6c5ca9a80a487e420996cae0982fbcbfe72206c0b85845db
- e0d385356bc5dc0a7619553d391259b8acd0f226dafb719b505bec4cba58fb46
Coverage

Screenshots of Detection AMP
ThreatGrid