Today, Talos is publishing a glimpse into the most prevalent threats we've observed between January 05 and January 12. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
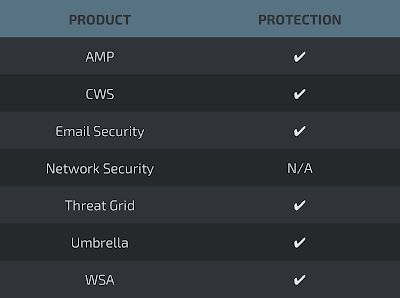
The most prevalent threats highlighted in this round up are:
- Win.Adware.Coupons-6417934-0
Adware
The Coupons malware family, frequently seen as adware too, is known to injects vertical and horizontal advertisement banners into websites. The malware has the capability to install additional malicious binaries. - Win.Downloader.Downloadguide-6418258-0
Downloader
Downloadguide is commonly bundled with other software. It may install unwanted browser extensions that can negatively affect the users browsing experience or by injecting ads, or share private browsing information. - Win.Trojan.Agent-6418378-0
Credential Harvesting Trojan
This obfuscated .NET trojan self deletes and migrates around in memory. It collects system data including Outlook and Firefox stored information and a machine screenshot. - Win.Trojan.Bancteian
Trojan
This cluster contains samples belonging to the infamous Bancteian family. This trojan has many features and it is persistent. It modifies systems files and disables UAC as well as hidden files listing. Moreover it performs code injection and it should be able to download and execute files downloaded from remote servers. - Win.Trojan.Emotet-6418193-0
Trojan
This dropper is delivered through different mechanism, most of the time the victims is redirected to a website to get it through malicious pdf, http iframe injected. Once running on the computer the binary is gathering details on volume disk drive and other details, injecting process, dropping itself and contacting internet to execute more. Websites observed delivering ransomware and trojan banker. - Win.Trojan.Generic-6417450-0
Trojan
This cluster focuses on .Net Trojans that make use of process injection techniques to mask malicious actions. - Win.Trojan.Generic-6417989-3
Trojan
Win.Trojan.Generic-6417989-3 is a trojan that will contact a CnC server and try to steal information from the infected host. - Win.Trojan.Rincux-6417593-0
Trojan
Rincux is a Windows trojan distributed to act as a downloader or contribute to DDoS attacks. This variant relies on the Armadillo packer for added protection against analysis attempts. It will also fork off into several child processes based on binary drops to the Windows root directory. - Win.Trojan.SocStealer-6418271-1
Trojan
This malware is a trojan spy. It will extract information from the victim's PC and send them to the malicious actor behind the threat. - Win.Trojan.Zusy-6417556-0
Banking Trojan
This trojan uses Man-in-the-Middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe". When the user access a banking website, it displays a form to trick the user into revealing personal information.
Threats
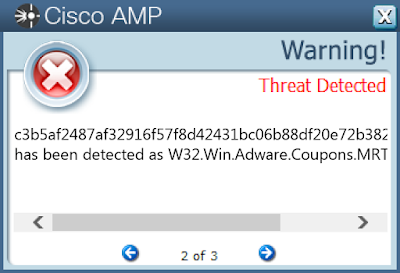
Win.Adware.Coupons-6417934-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- N/A File Hashes
- c3b5af2487af32916f57f8d42431bc06b88df20e72b38221b5f5f6464b82f01d
- db8d472d6437ef578ea0af7222af606288b247e847ff6ea08f830f9a3c919698
- 1b776ccc9d8ce5f83cf8d99e40c3b60f208bb3eb09a723fb844d4377b8af0e4a
- a6da7c7869f82a146a27bf06b2076d9e3929a6c20e413c7a9734641058b89e40
- edfc4ae651f3b9c858902791db52608036bdfcd2c23dbb4417c33b0852265f1a
- 83e58852442ed18b48c40e5c2f49fca174ae4007df7b6738ecd66663c9ccd88c
- 7100cb4b1cb6fa8e6a1897a9e3675ad0bae2ee82b63264ade40ce00bd7056606
- 2e9fa9b027d355a1fc50ca77bd7b7850a3a1d56122de5894bda5dc1579708fad
- eaa3e4886140186455fd515ecbe44e98c37f19e5353a3f2362cdc94b4e3178c4
- d7cc319288f079faa2f078d68ad3058890893e0952aae677652dbadc8ef7ada3
- d60409eb6b57d6f3b863da3a5ea8e0cb3dcec11f51324f6f110259dcbabb2b54
- 7086cae185896225b4924cc5e46e8e6edf2abfc78de1f4f695541b124d7bd795
- 19e971270674fd66f23747bec75bceac78431ea120a0338aa71182d36c3c4fa0
- c6444613969c7ad0b4fea1bfec260200ab8378a496bd77f2f04ea87dfec110ab
- 6c370706286c012d9e9f7f17ef6bd27f17a5d6f54232e94efcf507e45148abf3
- 0311c1383a2112b46ad9821c49a6aa5424776a37f207db4fd88f689ae061715a
- 97d422a62763ac81fa5007768c98b45adbf8107bcfe46cfde873fdf7395f3947
- 0347385888c90f292574903ebb72cd3d1e6b900796100cd130ff46d27de5cf09
- 328c1c54df14ccd6ca36d14ad981b9139807020979bd371eaf916c28027776c4
- 62ec31504f1dcb2a64891dcd2f5926bf6ad147b4c36358951f0b67fd0b77e689
- 85e3d4996b42c5d0c558195e5699ec62e24a94d4f4b5431cd440c9a4c2e4180b
- 48c15084f2a9f83831b9dc2811156e81ad18890b0d059c2ca7c3cc40eb243deb
- 61e8eff89c7b7c26454deb86170d3c6a38be3dd077f59d0f827fbddc6d60404a
- 8966c6c67b61def5d4e72129507f5ba9a16a27593357ddcec5e51b1cafe92207
- 40d2277549bb5b079c154dae83dd462d89f1036947a211112fba988e0f51e046
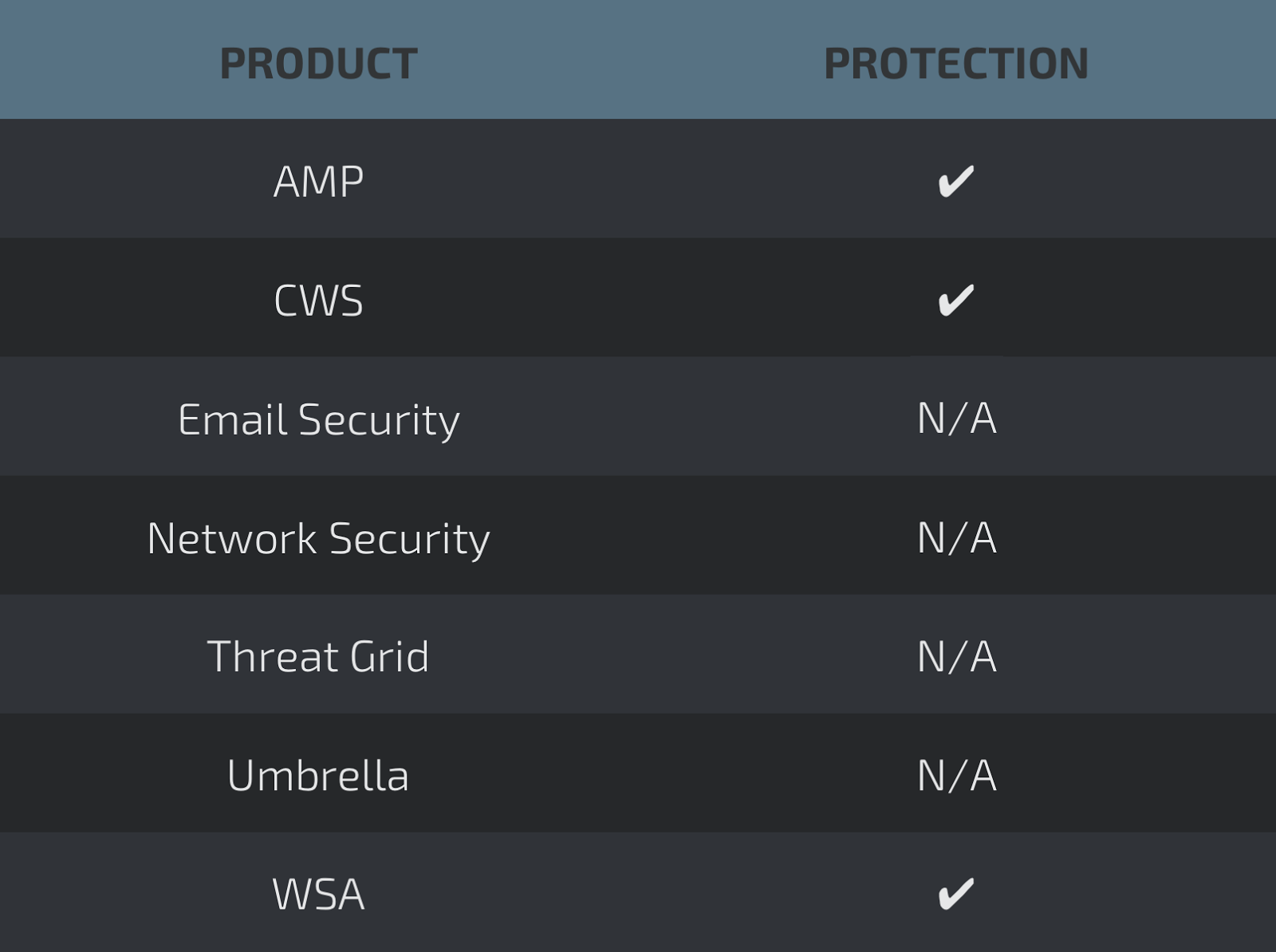
Coverage
Screenshots of Detection AMP
ThreatGrid
Win.Downloader.Downloadguide-6418258-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Internet Explorer\Main\WindowsSearch Mutexes
- DlgCpp IP Addresses
- 23[.]102[.]60[.]206
- 104[.]40[.]156[.]71 Domain Names
- dlg-messages[.]buzzrin[.]de
- dlg-configs[.]buzzrin[.]de Files and or directories created
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\DLG\ui\offers\fd286b8d7f971e3468eba12c41b59383\uifile.zip.part
- \TEMP\download-downloadspeedtest.exe
- %TEMP%\DLG4547.tmp File Hashes
- f0d58b5f95df0334943a6ddfe69002d76d014402050001bd0e49dcda87e235a4
- 23b495217cfeffa3c5ec8a842e109c281e3e56ceda74c3aefa772ed35028269c
- cd2cf4cf6f86568ae34da56e46245a2569b06cc8098055292576e1516d682239
- e1a193f844881ac3215a237323e3cfef179e907cd175bf5f644e4991b849bee4
- cc9581cbcd550ffc661f505b39fa0dee831014101fec1bdd0773647754337e60
- 4f5ccef0a56e46ed4c4cee2d255e3805c45924bba2e915fc076fe9009b84ea59
- 948e8e7cdcdc56ac33c9d3609f43b601aa01b56651f6bbc120fb2aabc50fae0a
- 220f1b3998fdf561501bfd979dd123f4c5881bd30ae040d215fd108c2f191b99
- 5a50f0badf17522ee97f07add6533362b0c203b894d3d8aee9415c6889cbdf8a
- 31297810592b4b0363d5b5789bad3b5da3dfd3c633ad8b9e5d1e8c7f9acb7ef2
- ea95d29ba35dd2d85d1a51e6bd3512e426962f2ce44d8f1e666d5a48f341ae59
- 4dfcf69e32b2e896a50fa784e8a4868384254ab5f53da7e7c1ab1d5db0081f01
- c8729c7f479bcadeb3677aba3308154a45c731c74278943e1d22a439f8fa8aff
- 1049e9f4052a0b7c9ddc141f0b6ae6a65588d948e9303458d377c0169bcb2654
- db4b0afd6e8fffe1de96f59f6e54c98b47b207f9e3606347bfea74ac1125fc0f
- bdf2bb0d4008cac0d2aceb8c3653342aaa5c7543209819f55708d0a2c66d8cc0
- 36d797122a02e757a4f18bfcdbd95fc2648fc6f1a99472722b8cab48d300c969
- f0b71d1a0e281dd5927fb2c5a82cf90938feffe7587dece0a3e7885c8a2a681a
- 4128737ed9fd6ec454b6284b3fdb9d9152606b7e1f12d83138fba669425574b9
- b1971317dd3567c839e6aa0a0082b18af101c9cbd7aa52177a55e2c00154a542
Coverage
Screenshots of Detection AMP
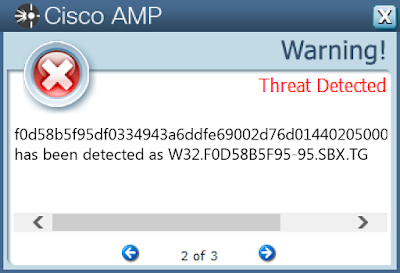
Win.Trojan.Agent-6418378-0
Indicators of Compromise
Registry Keys
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _ObjectLru_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _FileId_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _ObjectId_
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
- Value: L4XTIT8X0X1
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST
- Value: CurrentLru
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _UsnJournalId_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- Value: 10000000090A2
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\10000000090A2
- Value: AB5
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _Usn_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: AeFileID
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- Value: ObjectId
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- Value: ObjectLru
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE
- Value: _CurrentObjectId_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: AeProgramID
- <HKCU>\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook\
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Thunderbird\
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\4c8f4917d8ab2943a2b2d4227b0585bf
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ecd15244c3e90a4fbd0588a41ab27c55
- <HKCU>\SOFTWARE\Microsoft\Office\15.0\Outlook\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\8503020000000000c000000000000046
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9e71065376ee7f459f30ea2534981b83
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\f86ed2903a4a11cfb57e524153480001
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\{D9734F19-8CFB-411D-BC59-833E334FCB5E}\Calendar Summary
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\33fd244257221b4aa4a1d9e6cacf8474
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Firefox\20.0.1 (en-US)\Main
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\a88f7dcf2e30234e8288283d75a65efb
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\10000000090A2
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\Indexes
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9207f3e0a3b11019908b08002b2a56c2
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000001
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000003
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Policies\Explorer
- <HKCU>\SOFTWARE\Microsoft\Internet Explorer\IntelliForms\Storage2
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\3517490d76624c419a828607e2a54604
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\82fa2a40d311b5469a626349c16ce09b
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\c02ebc5353d9cd11975200aa004ae40e
- <HKLM>\SOFTWARE\Wow6432Node\Mozilla\Mozilla Firefox\
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\5309edc19dc6c14cbad5ba06bdbdabd9
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
- <HKCU>\SOFTWARE\Microsoft\Office\16.0\Outlook\Profiles\Outlook_2016\
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ddb0922fc50b8d42be5a821ede840761
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\0a0d020000000000c000000000000046
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\df18513432d1694f96e6423201804111
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\13dbb0c8aa05101a9bb000aa002fc45a
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\d33fc3b19a738142b2fc0c56bd56ad8c
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000002
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\{D9734F19-8CFB-411D-BC59-833E334FCB5E} Mutexes
- 8-3503835SZBFHHZ
- <3 character prefix>RTU088V35CE4z IP Addresses
- 208[.]91[.]197[.]39
- 198[.]251[.]84[.]92
- 198[.]251[.]81[.]30
- 173[.]44[.]37[.]208
- 45[.]58[.]190[.]82
- 103[.]47[.]81[.]80
- 104[.]149[.]163[.]27
- 46[.]23[.]69[.]44
- 64[.]32[.]22[.]101
- 70[.]39[.]125[.]243
- 188[.]164[.]131[.]200
- 104[.]27[.]176[.]2
- 209[.]141[.]38[.]71
- 104[.]27[.]177[.]2
- 192[.]161[.]187[.]200
- 68[.]65[.]121[.]51
- 104[.]221[.]251[.]226
- 198[.]52[.]124[.]90
- 192[.]0[.]78[.]24
- 192[.]0[.]78[.]25
- 107[.]161[.]23[.]204
- 66[.]96[.]147[.]117
- 204[.]188[.]203[.]154
- 95[.]183[.]53[.]20 Domain Names
- www[.]atopgixn[.]info
- www[.]szsyxsy[.]com
- www[.]9u82eum[.]info
- www[.]doors[.]property
- www[.]pilates-sunbury[.]com
- www[.]jmtravelconsultants[.]com
- www[.]dangkytaikhoan[.]net
- www[.]whoever[.]group
- WWW[.]YHCF88[.]COM
- www[.]dontdodebt[.]com
- www[.]jieleshxijie[.]com
- p2017090801-dns01[.]junyudns[.]com
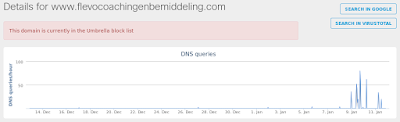
- www[.]flevocoachingenbemiddeling[.]com
- www[.]armortechnologylimited[.]com
- www[.]yhcf88[.]com
- www[.]020jiezhuang[.]com Files and or directories created
- %AppData%\<3 character prefix><5 characters>\<3 character prefix>logim.jpeg
- %AppData%\<3 character prefix><5 characters>\<3 character prefix>logrv.ini
- %AppData%\<3 character prefix><5 characters>\<3 character prefix>log.ini
- %AppData%\<3 character prefix><5 characters>\<3 character prefix>logri.ini
- %AppData%\<3 character prefix><5 characters>\<3 character prefix>logrc.ini File Hashes
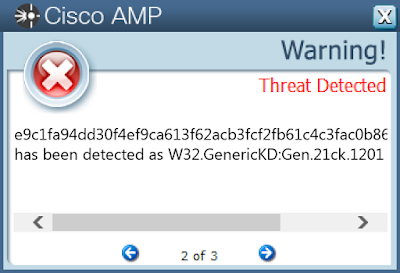
- e9c1fa94dd30f4ef9ca613f62acb3fcf2fb61c4c3fac0b866ae484cd5dc578d7
- 55ebfbbffe1cb77efa39b0c7b5348b0aef03a251349c88cb8bcf4358bbe73558
- 5b6e111a37e7c0fdaefd543ea45ff37f162bfeda2b58ce60783091ad6129f11a
- 3ad3991209de094faf8bbfac835ec38ac57318fa78c3ef11eee5d4acd0118460
- ea9eb1d7b61d711807c4609bf55f62af5bd6049585e086b75385963868ca31d6
- 38318b262a6d85673fdf8fdcf4ddd5666f438f18dbeed8569a4d769f42ae05c2
- 59571268f235c8094036ab44f5f5c2be3819fd72888cbbfda2150e336549b2a8
Coverage
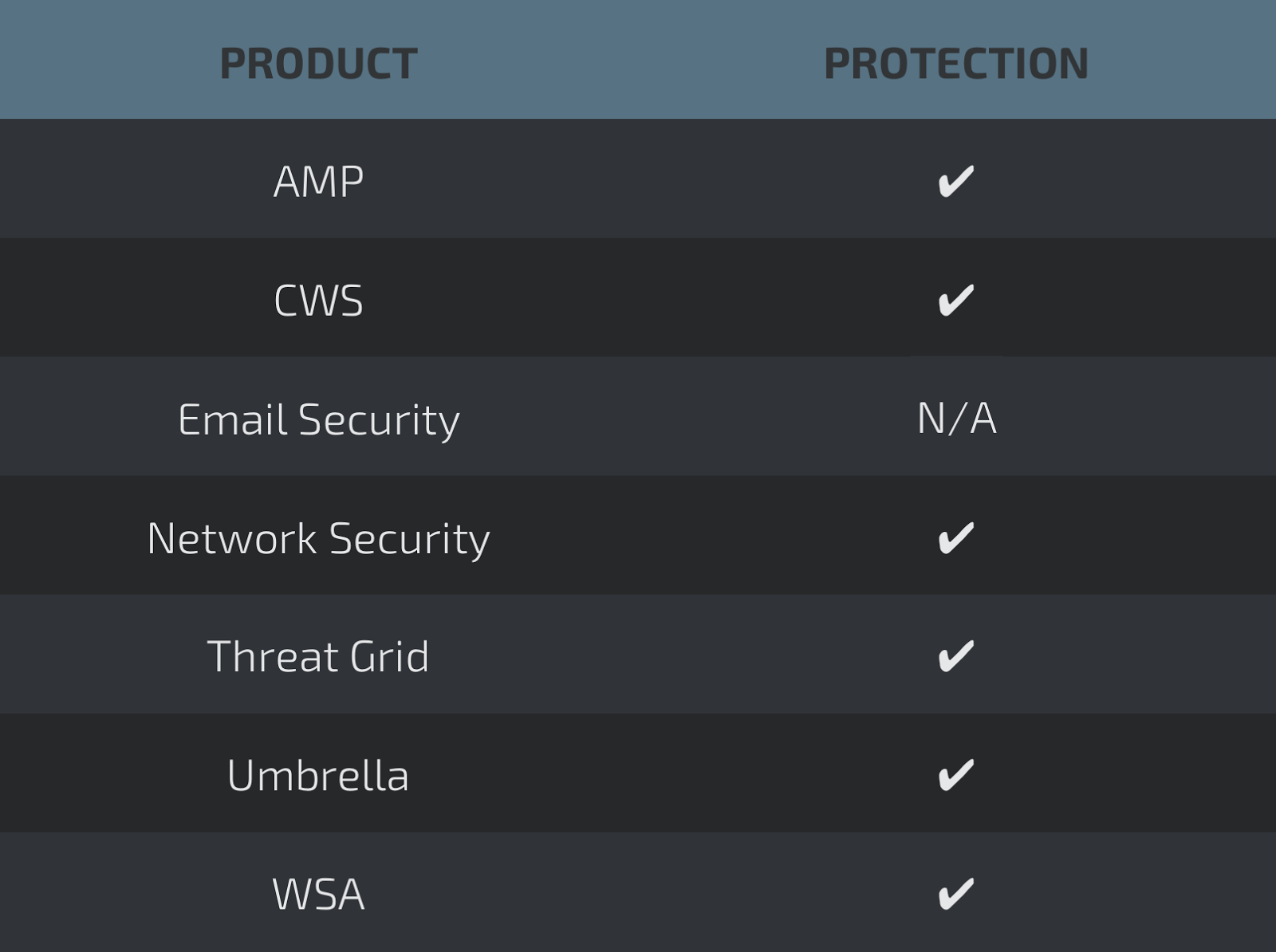
Screenshots of Detection AMP
ThreatGrid
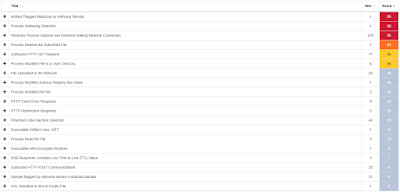
Umbrella
Win.Trojan.Bancteian
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: PromptOnSecureDesktop
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- Value: Shell
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- Value: Userinit
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER
- Value: GlobalAssocChangedCounter
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: Microsoft Windows
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: ConsentPromptBehaviorAdmin
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: WinDefend
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value: ShowSuperHidden
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value: EnableLUA
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: Host Process for Windows Services
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
- <HKLM>\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Explorer
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Mutexes
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!rwReaderRefs IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %AppData%\RCX3.tmp
- %WinDir%\wininit.exe
- %WinDir%\wininit.exe (copy)
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Application Data\svchost.exe
- %AppData%\spoolsv.exe (copy)
- %TEMP%\icsys.ico
- \TEMP\03479bf7ca41f9cb7a1243103b8cc49b4963489b4fce9d80237d93ce1439fcc2.exe
- \Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01.chk
- %WinDir%\RCX1.tmp
- %SystemDrive%\documents and settings\administrator\local settings\application data\svchost.exe (copy)
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\icsys.ico
- \Users\Administrator\AppData\Local\svchost.exe
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Application Data\RCX2.tmp
- \Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V0100010.log
- %AppData%\spoolsv.exe File Hashes
- 03479bf7ca41f9cb7a1243103b8cc49b4963489b4fce9d80237d93ce1439fcc2
- 086928aa133cd03aa950e0172ea060f51794f74dceb0974fe335d68d8762cc31
- 1fc56d9b169a79fa34565f7dc1ffe85501da06abfead4beb4add8f0d77dfa61a
- 2893f28740ab0a01fdc40dcdee227649b8d930af288e5a43fd989195441b6029
- 29c488b4cdbf1023b9aebe15c5e3b56280e3424ee02d9f38d82ac47221688853
- 4b32a37e27c5d21cda8349829484736ad79c5f5559d81e709a9fabb064793eff
- 53907dc338e0d219b3b0a38ff28958b1a2c862a4ef0b8bf2ebaad9ba9c032399
- 6b11929c8b220ab7557d999c74aa27773bf6ecf975a5b4309fc39fff95b76ed9
- a585c8eb9366029b147b5e027b136420aa214183d3ff200e6899324faa02bbe8
- ac0cf677808ee093e27a20511b8346e127931310d65af1b61c65dfcfb5f543e6
Coverage

Screenshots of Detection AMP
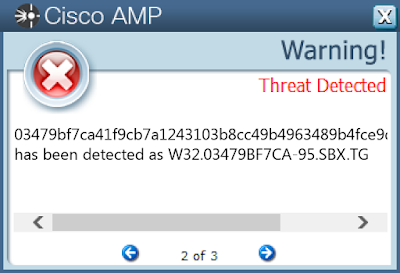
ThreatGrid
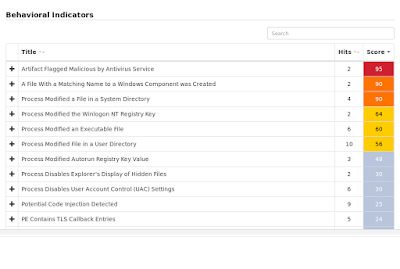
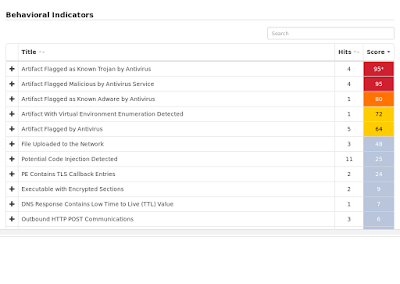
Win.Trojan.Emotet-6418193-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\LOWREGISTRY
- Value: AddToFavoritesInitialSelection
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\LOWREGISTRY
- Value: AddToFeedsInitialSelection
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride Mutexes
- Global\AmInst__Runing_1
- Local\ZonesCacheCounterMutex
- Local\MSCTF.Asm.MutexDefault1
- \BaseNamedObjects\Global\AmInst__Runing_1
- Local\ZonesLockedCacheCounterMutex IP Addresses
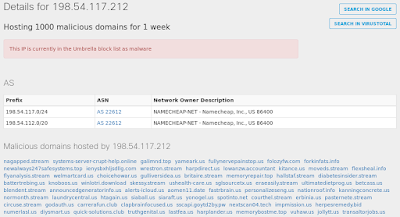
- 198[.]54[.]117[.]212 Domain Names
- www[.]selfdislikedfarfet[.]site
- www[.]quaintspokenracketiest[.]site
- www[.]millesimalnonremuneration[.]site
- www[.]secularistsarakolet[.]site Files and or directories created
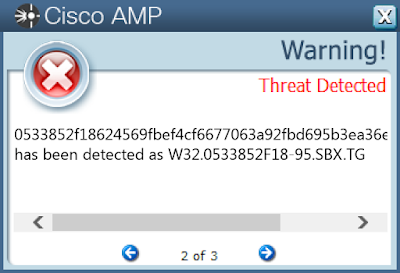
- \TEMP\0533852f18624569fbef4cf6677063a92fbd695b3ea36e003da95999d6c8d9cb.exe File Hashes
- 0533852f18624569fbef4cf6677063a92fbd695b3ea36e003da95999d6c8d9cb
- 0a3c71a1b1e82e87de944e0c2672f97db0e78a076124b00692233414a8054cb8
- 0b49337bc87bdcef167fa6b7313c23a836e9a5a45f827ba0eca7262901b9770c
- 2299fb45a9a7f48d618c33d665bb0c88ea5545c86ba4ea05fbdb73dc38de96a5
- 24bd0b9517591458af75b8f1ad1b59e57fc6fe9eeaa41086d31c55a4c259e12d
- 27ef5e8a51c44b6351ea13af6454ce7c34d506c604d9eb6366c7b98ce70a37b4
- 293580f6560d8d9b4d3a413dedd347f2cad79bf7e9f22519d9b60cfdb0f52fc6
- 2d2582eba24d58be4ca332a30daf4fd42d95e25986446b464f465c8dbcc08572
- 30f73c131ca8864f57d5c3501ad7e75be30eb8bafb79f9ce0c9becca4813c7fc
- 33dc66ca6d18acaff3ee13baa7a2f925f5b0bd4dc8ea9436e4e5aecc57775fe0
- 3726d3185b6aa67c425b7e1866ac424284737df53df1c83e9a040428837c4a8c
- 37d65942c6ae66de3fbcbbbab3e184f4c566cbb4cc0c6bc3060dab27df15da5d
- 563a41f03cd9f6e1917b486ec1de9ef941f7449f3bf2635f7fa6186455db01c5
- 69137a62cfc2e60c5d2915d919fe987fa94c1510bdd180bc3079330f1897bb64
- 725f01277f2b4f35a17ea0d3e61a910b8c118ec5f70405fa359a1a0ee0e4e525
- 72c6f63cd23d2de81ca96f7246efc9e11a1c8ae9e8f41755aea03ef067ae484b
- 831cc8a05f15820256cc41705cd3fe96f38bf3dbb61372b48d229b81922b15dd
- 90d6515b29f9f59d551f8f170b731f9831ab63a2a8f6d70358cee6d5df519efa
- 9ddb4d20633a371d2ab3858f4c74ce2c2d55804c40aedde9b46afcc98db8f709
- a5716b4266066ed231e6c207cf2850627c3c8fa84d2e96e8ebf65f8f918538d6
- b9121f992ba17130ce6429aba0c47138b059b0c8aec2cb36ab446361c95eb238
- bc2451362e8658b64bdf2421c4c73e9c35cfbdcf370944e9482fa496b6a91d5a
- e9757f25588b668b1708788639ba3dcc0c5a0010f425d19ca667e5d70e0e5939
- ee2b22547da7ebcef73af0dcd8dccb1b25bb2a13f09b2b563015b34c24562ebc
- f13483a7ec5d329e5da2901fa9f3fcea6eff6e4cb1724200df114d214a8cd0bf
Coverage
Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Trojan.Generic-6417450-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
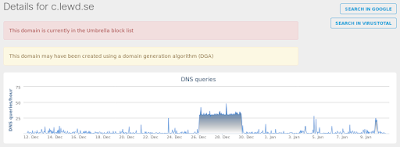
- 104[.]27[.]162[.]68 Domain Names
- c[.]lewd[.]se Files and or directories created
- N/A File Hashes
- 26164675ee05afb06a76f8d9a8b27b11562b3576aee5bffcc4d83e9e7c3a7a16
- cd60a72e6afe723faf2a470d4c664f91c15691f149cb03db96e9e0e6806e3897
- 4a07fa4e68366bebf3873736b28354500000814d63154538e66f65e6aa70a853
- a148d91ebbc97e53b4febc23960ee0d1f3170bb4625c94deeb0ad32e7ac28ee3
- a86662848047586347e4fe38341e67c43eef8c83738e22376a7bd992d11f26b6
- a555f788fabda605dd622c7a3320ae31840fb302b82a7d05a981e37cee0d11b2
- 243359e04224afa42981cfb9a24c269ddb8adc0c1d49839aa7ad8a929c22e3c7
- 007be09ba9b3ad3beb5e6ba63a1cec3ea9985b6bb261c7152de3f8e9f558ce2d
- 7bf374cf242a630ca540616e870b575fb63e674c90d24626c656c148b2156ee6
- 3ef315249309fd118662b78bb1923afd71d7f7876fbed516d573ccf6e70182c1
- 0d8031a8b9e1f5aa16fc7c82115565d1d468a8f4f3a828339eceb901f76b5577
- 9a5cde6f48c1fb2b1fcdce11e8b9e72a0f23910c05b6420c78e3c027033e09c0
- 59b04b8760f88213171dd6b45b5d4d85dc7b9b5f86a976a3eff2e9c27f135929
- ce533f8f084a79294aa1254db01fd630dab95ccff22124d9fb4c51fe16a2948a
- fe04dde6a78fdb8029ead6f87d072ec7b2b9f530e6d4913e296903b34ea64176
- 49fbf92ef158694f0ed792403f7a066d88831ba71e5f4018f707010f2627210d
- 698b7960c7aa2703b7468a6867adfc13a68c31390ae47132de34efb2dab7ae39
- 4dd1f3fd4c4548bd757bf4f88d8d0a3d6e4359a5c41f8b4dbf0a44028a2d73ae
- 56a0ecc8d86810358cdacd8ea41f6dfce683c5121226d906a418b5a15060b9f9
- 58c6f5ef2df1e08a36a51ed36a3ae15ee2ab05b3046ccca1a09526640316e079
- d1e6d2ba273fed39c272d2d944dd244bd6566f38b5dad94637af147c44355e80
- c4b6809128e9a17a0b5032ea34b373095940f488544bd0350293a175e0079b2b
- fb39b3f2ade2fa2754493d3d1208facf01c2ece961aa7c6e1e1f10607c9d4962
- 018fad91a80cd1ff5328bf6ee3fe613b563eea547d23d22cd708d76cedbc578b
- e1673a3ed97150082c0e89712386c71f6feb8fd1d7428fe633cfae0d1ca9baba
Coverage

Screenshots of DetectionAMP
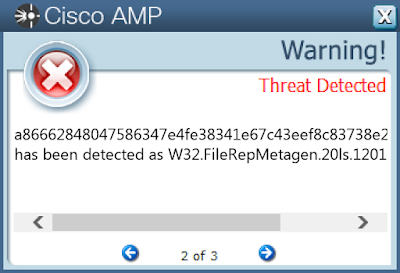
ThreatGrid

Umbrella
Win.Trojan.Generic-6417989-3
Indicators of Compromise
Registry Keys
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Run Mutexes
- DBWinMutex IP Addresses
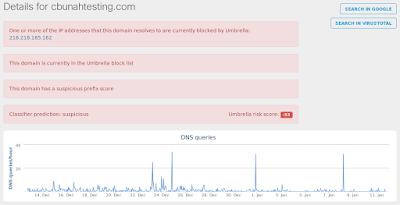
- 216[.]218[.]185[.]162 Domain Names
- cbunahtesting[.]com Files and or directories created
- %AppData%\5145C9BD\bin.exe File Hashes
- 05beeee9353e581e5e0fad00ef8b88f90f911a45411dd52b620fc2cc73ba1e85
- 7ca99c0c24283ff2b6f8e0f81ba7edcb17948e4fee7bc8c3cc22d5026c455f4a
- c247197bf71c4fadbc4e267888f6c416f4775c07a1fc8aa8d0d1144b5ba1db36
- 100c808616f05668a9c73101e9dce21702e8bf241f82374eb5aa5f0646cca3e4
- 744a6e99676a89e8cfd2b0ff2c540f2500f1afc5dc541e3611b0dc04973244ef
- d8781d7dd2e9cc4b029a9147cf5691c8622b15b1bdbd438f8cd1443e9c268a31
- 7f7b2e315d47d3b8874517443888e229aa738f211e3ebcaa67d6859539e439bb
- 3ab29f60bf807759931c817cb40a42140296364fa8a5e0b032e8a6851accce5c
- 4bbf688503c81af93e8c598242c0a087b57aaa4c95fedb3193e4a021e535fde0
- 2e965a7d0769b37a6e4af06db67592b3b0778b6929936bf8b4af8ef370af7eca
Coverage

Screenshots of Detection AMP
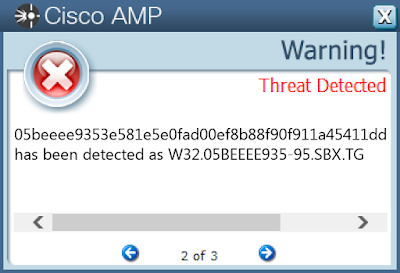
ThreatGrid
Umbrella
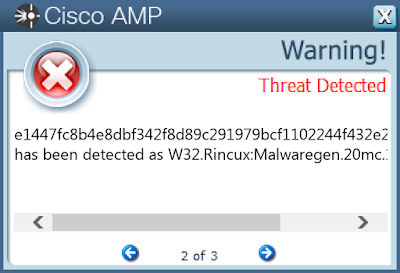
Win.Trojan.Rincux-6417593-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %WinDir%\{BCE28CAE-5ABE-4a95-871F-99EC11C0AA0A}.exe
- %WinDir%\{21581114-3E37-4566-BDFF-D20147EC1489}.exe
- %WinDir%\{CB20A050-980B-4166-80A0-C40DD09170BD}.exe
- %WinDir%\{A2201725-11C8-4a99-97BF-FF6A9C385D0B}.exe File Hashes
- e1447fc8b4e8dbf342f8d89c291979bcf1102244f432e25c704d2d504458276a
- 5cf36cb510ce50c61e02f273439987e413f8de1d71a85788e9fcc0639bab0947
- 4e6d866520ad1ac811b2ccfe95376194d39c5b4fbd110f0d8135d2af69aeb3ce
- c863e0b35242e38e72d82cb5e1aae245816405583e800dedbb3705e42ca66290
- eaa28566211fb0784bfdb173b4685dfb57d644a82559c5e6402f024e04cb1f86
- 7e21525165a5c2314e80458cee08d1bfcbbbf27ebb4b4dfb838f0a957b2053fb
- c688f5d47654368b1497692d2a50ba1b1e57624452f7f359f85db65ce1fbd2ca
- f97592b069b8bc6a26af88d312e3af83da88d483ad76aeb5a6a782a5e5dc8a54
- f480682591f7bb7a5c66f32c0ae20bf47c6f8fb4dfefac1e27e0ab7fe1d9fe69
- 69fb4279770e54269e5e60f47e8d015f01e79da5e4ea80a9e896ceb2176505dd
- f48445efb3d70f7578ff1cb60508d3dc57e5a5240ab3196694a25e5a99355cdf
- c99f8764e6e4c11773b2d229a3dc335aca8783630c5a4620c5671d6b8cde3dfd
- f463eeeccc175d90def65b4e65e504fe50c9fb413aa9f8178d8fa777062216e0
- c4d2b74d66362f926e99ab1a89f46e311d789e28eafabffb9668278422403c01
- f816a1a589c791c36a2724551a5cd76590415dc449f27b1dff724af73f216382
- 45198fe505ee4983fd007576cefeb56502f04d1787fde7d446d2263334fad33a
- 4dc57fce4bfd27dc132183e62d5f52aff7dfebca2e5787075eaa6193ad5a4215
- 28c348a5c96ca0464bc972e574b31cf4ee57a4955e99d8966b6bdee8b16652ac
- eef8802720faea54224cdd4147c7b19db4af84a4dac310322ade1d374436436c
- 90559e71cf6d6a27a9ff490a31d2b10c914708f2288fee837e2b7fabdbeb350d
- a244aea82e33f99002238bf84ed4e17bbcf45857393056c96f1294bda1b5fdcc
- 99b1a18b219ff4f709586e736b9dc93d8fa0f31e0ab8ac97db2553411fab5329
- 598cb724819f5dd1ddb7921c9f1ebc3a5b37380f3ab812dd22d89c085c489b8c
- 85cbd0c99f4e8293c2a0edfc759baade5a536e983c24cd5e0a9cb869725e4cf3
- 26a8d667aee3819c597636a1643413f3146262343ef6442cbdef681f0f6c75e1
Coverage
Screenshots of Detection AMP
ThreatGrid

Screenshot
Win.Trojan.SocStealer-6418271-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE\PARAMETERS
- Value: ServiceDll
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: Start
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: ObjectName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: Description
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: WOW64
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SVCHOST
- Value: HNServiceGroup
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _ObjectId_
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: Type
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: ErrorControl
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: _FileId_
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- Value: AeProgramID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNSERVICE
- Value: ImagePath
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500_CLASSES\LOCAL SETTINGS\MUICACHE\3A\52C64B7E
- Value: LanguageList
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- Value: 10000000095A9
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- Value: ObjectId
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CTLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\SmartCardRoot
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\System\CurrentControlSet\Services\Tcpip\Parameters
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\SmartCardRoot
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\CA
- <HKU>\.DEFAULT\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\TrustedPeople
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Disallowed
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\SYSTEM\CurrentControlSet\Services\HNService\Parameters
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\SYSTEM\CurrentControlSet\Services\HNService
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\Root
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CRLs
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\Disallowed
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\trust
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\Root
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\My
- <HKU>\.DEFAULT\Software\Microsoft\SystemCertificates\TrustedPeople
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\trust
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKLM>\Software\Microsoft\RAS AutoDial
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\Certificates
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Root
- <HKU>\.DEFAULT\Software\Policies\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\TrustedPeople
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\AuthRoot
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\Certificates
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Svchost
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\HNService
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\Certificates
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CRLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\CTLs
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CTLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\Disallowed
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\DownloadManager
- <A>\{33CA8D6D-A479-11E7-BE8F-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\ROOT\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\trust
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\DISALLOWED\CRLs
- <HKU>\.DEFAULT\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\CA
- <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\SMARTCARDROOT\CRLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\Root
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\Certificates
- <HKLM>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\CA\CRLs
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUSTEDPEOPLE\CTLs Mutexes
- Installer20171023 IP Addresses
- 104[.]238[.]156[.]230
- 45[.]76[.]142[.]144
- 52[.]85[.]146[.]50
- 157[.]240[.]18[.]35
- 45[.]76[.]241[.]231 Domain Names
- api[.]new-api[.]com
- m[.]facebook[.]com
- d3vzyycpfbk7qm[.]cloudfront[.]net
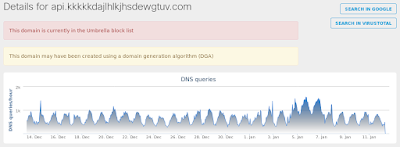
- api[.]kkkkkdajlhlkjhsdewgtuv[.]com
- down[.]kaidandll[.]com
- rep[.]pe-wok[.]biz Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\report[1].txt
- %AppData%\Mozilla\Firefox\Profiles\1lcuq8ab.default\new_cookies.sqlite
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\X1IF8CSM\dll_x86[1].bin
- \Users\Administrator\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\dll_service[1].bin
- \net\NtControlPipe10
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\report[1].txt
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\TQM3V6S2\dll_service[1].bin
- \winlogonrpc
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Application Data\Google\Chrome\Application\winhttp.dll
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Application Data\AdService\AdService.dll
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\ip[1]
- %SystemDrive%\Documents and Settings\Administrator\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\track_dre[1].php
- \Users\Administrator\AppData\Local\AdService\AdService.dll File Hashes
- 73ed012536499f859ac55c2fb0017e65255f2462f13b663ed1d85e552c13740b
- b6b43b0e6488b384a3ad695ceb1d6b576910ce721079346cfd1d12dd9eea5108
- 043d07796535fa5f9ee2bd33139d442c824b5e251471f8d4b54c8f15bc2d0165
- 4d094bb5a93660f8e897ce8f191089cd9f76af8b6dd806fc2681acf2a3d70f38
- 0bb012ff4961c880d3df768e1374ae4bafeabf453dd3d7ae2d4065bc58f52bcf
- d083fbd8b7f1ad561aaaceabfcc601616ed3fdbf076ff845bef53fd178ca6a34
- 3389df5d81737fec0e3eeb43c94e2210a14b4227b88c94d7fcff32474d38a19f
- 34e4890aaf63d57d686cbb8c9722f5bdef9a41fb127b56d895c5bd87b7ce92ba
- ebba38b2a422277646ea55484f41cd919d0bd2d619e8d45bfd9585aac8986369
- 51243602a1bb3c7784373c17b430ff2491d1679ae6e169175c45907f0313b76b
- 078baebe5ee2cadda00cd0142280a7bd1034494e79819f16d22a4fe961b3dc84
- e134c3dd3e4e39e6c6a373416f5969ec56dfb90c53b6ba847dcfc4f7626de995
- b5d5a2cc7f8a796009674981f60c76fb99eb6cceb6a19f276e13c0ce9b22ef4c
- 45b6a109d001e4dc2e66d4570c19384d7aa44332e906feef739649b9ebc77bb0
- 89e5effdd6426658db77526775b5ddb6f51487dbd80f7f55e79c2fce32a8abea
- 026764bc699841080691463758db461d64138343a310b918bac027cf67ffaf34
- aecf6184c2b620a198f0415a16d6ae824f09df25bbc310b24edfbf5ee0b7c3a5
- 04fafb357ccdd1f9aac6db2c62ae274f58f6fb5b569b10f15e3b3a94fc1ae899
- 115767f49767127544b6365e2551f5b3977af593b222619d8ebe1603b550a4e1
- b5da35a9a483d86c19d4d450006698d2bd6c41b9eaa9783d563e1522c6ef11a4
Coverage

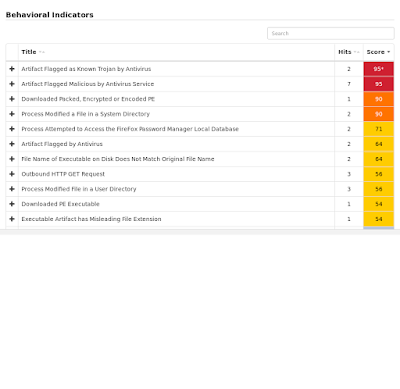
Screenshots of DetectionAMP
ThreatGrid
Umbrella
Win.Trojan.Zusy-6417556-0
Indicators of Compromise
Registry Keys
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: DFF7E57F
- <HKU>\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %AppData%\Roaming\DFF7E57F\bin.exe
- %WinDir%\setupact.log File Hashes
- 02d99600a3bc049905479aaf281baa9611e3116ac1055cf90f5af317f2abee7d
- 0546853f1fa7e7715f1f80e8d544f19055b9c118672d8fe07843b3bcc9b5a212
- 0571a872f9ae83ad0c1a618cd702e4804bef66dc75771d12d0d343086b692edb
- 05d0bd7260555bed0b868b76e03bfc2e7b667fb50f6b2926a57e06eca75bd948
- 0820695810d62160ede23b19ae1a9a28955136b79122c6fea4e316508241ee8a
- 08764af08c10eadace45a49d3a9d77ddcd815a9bb5f6a00b25d09f161b9ce799
- 08e5be88de6cd4a641747552eee45a7f4a77e30afc514447c2e3b95ebf2f348e
- 0a089121a2c7e5fcfb86a1ed4ed7f60e0e7d0a795294d0de3c96869ec94f0d46
- 0b025f4e1d6521bc0ab29c4ea6ac2e32dc26585dbb367389e550229c0db783a8
- 0c19771b538e6bcc23afc97d52763f0cdc95aeb5329acb03697f235dbc93611b
- 0c7e05eccf846610557f9a5ca087ff4842cb7973850e6f6da4fa28e5973a365a
- 0d9a1563b9f7aa42224cc8148741e54f040fbf566fdab0f7c121a8b015e24ee3
- 0eba1ccd4bd977ad336204abf2dd6757828ff13d7bc3ebaca3ed9a9eab275951
- 0efdd84b7916529809d3facfe81897f2f03b239cef6899ae501386acbc8a8e04
- 0f04e601a9cf2a9f6cb422a257c3616f0a8b9884de52dd3f6a0ac944ded2a435
- 0f0560851aa49ff627a08246af165ba0af6b1be58058b8f9c675bd758f606b68
- 12f52ad98e75c8d57a457b6b4e02767da04ce051ef7abc59ac975c45358d2cc6
- 17006395b5609f935fea89d8186649ba59a1b1ae2ff19437c85420d5ca5315c5
- 197fa42138b01d074fdac0c5eee8a3aa67baaa26fe243a293e5e7eb57f37d384
- 1b609587a5a8896a37087737e481d79d4a097e3a1a75d46c5f0bf408c8561280
- 1c74cbf79258ca7906b431f4f6efeefc085d66b5032bcad4ec7a9b3960ae9b8f
- 1e470e2602e1bcc9c2470c4a375008b3493c181a3e659df5bdf22fc62382d851
- 1e5b4e6b02aea1d466b2851583a2c7102083a9c0288f580e9fd8606136003a17
- 1ebddb51a2cbce90cdaab17cad42dd3178109bdeaaf342bcb02d82e48992c8f8
- 2391a31b7dc07f209a6039044a1d0f11bfcb3b628716b6f842e959f7e90042e8
Coverage
Screenshots of Detection AMP
ThreatGrid