As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
You can find an additional JSON file here that includes the IOCs in this post, as well as all hashes associated with the cluster. That list is limited to 25 hashes in this blog post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
- Xls.Downloader.Sload-6774021-0
Downloader
The Sload downloader launches PowerShell and gathers information about the infected system. The PowerShell may download the final payload or another downloader. - Doc.Downloader.Emotet-6765662-0
Downloader
Emotet is a banking trojan that has remained relevant due to its continual evolution to better avoid detection. It is commonly spread via malicious emails and saw a resurgence recently during Black Friday. - Win.Ransomware.Imps-6765847-0
Ransomware
This is a trojan horse virus that may steal information from the affected machine and download potentially malicious files that spread via removable drives. - Win.Virus.Sality-6765491-0
Virus
Sality is a file infector that establishes a peer-to-peer botnet. Although it's been prevalent for more than a decade, we continue to see new samples that require marginal attention in order to remain consistent with detection. Once a Sality client bypasses perimeter security, its goal is to execute a downloader component capable of executing additional malware. - Win.Packed.Passwordstealera-6765350-0
Packed
This malware has the ability to harvest stored credentials, keystrokes, screenshots, network activity, and more from computers where the software is installed. - Doc.Downloader.Sagent-6766662-0
Downloader
Sagent launches PowerShell through macros in Microsoft Office documents. The PowerShell then downloads unwanted software from remote websites.
Threats
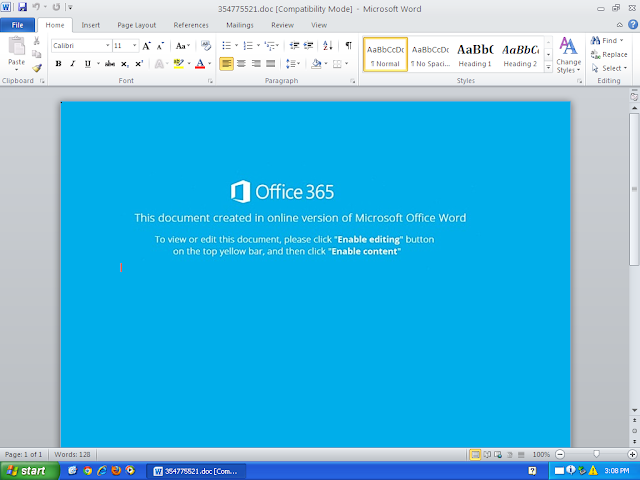
Xls.Downloader.Sload-6774021-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- KYTransactionServer.MutexObject.Administrator IP Addresses contacted by malware. Does not indicate maliciousness
- 216[.]239[.]34[.]21
- 64[.]210[.]137[.]102 Domain Names contacted by malware. Does not indicate maliciousness
- ipinfo[.]io
- images2[.]imgbox[.]com Files and or directories created
- %LocalAppData%\Temp\psefaeec.nvt.psm1
- %LocalAppData%\Temp\yb31jdzi.jxl.ps1
- %UserProfile%\Documents\20181205\PowerShell_transcript.PC.ZR0bVMzf.20181205131554.txt
- %LocalAppData%\Temp\CVR1B6D.tmp File Hashes
- 06f128b08f332142a5e0cb8d6c26a780316623ff62673684ccb9f37f98e3f87e
- 07b4dc36a3389ef60f3444bde94f6b9440e6cd2d658671096d01e4909a0044e3
- 0fa2d0e86ffca3b299776ef219a1ca248f8bc89eb866c39894780c97859c7540
- 132a3cf5d1534553294af816d2796d21c2a7a379eb3fbe6f67e8fda895a68a77
- 15c3daf032053b55a6bc280ddbdadfa668172a43609da78a421856b5f84f1381
- 24ccc8f6607e2577e1fa9e3f3cb474e6a309f420765bff7d64a38ba1c6a2d508
- 393326257ec1f08c2379a375308e0b5a6879ffdb8d68362f46a6a56f2fa9c0b1
- 3bfb9adbd0af64301780ae06f4db63fcceb21dad38a8df0f6023c60d51fc71ac
- 42728401a73b538b441d0643b302122f03960a26d8f2513af5a780e24bfe9817
- 511b09caf3e19d96a2e8606c35ef9e39e18903e7895ae225dd7807cd46d50c21
- 55e145df9b9668105f52c6f61e5ca6d421edf7fa1856af1162452a7dce6b6e3c
- 5dfe4ad7cc7866e81248aa06e2c8204f6007e9694a5d1a4d6739d9a313ed249f
- 5f8fd3edd5feaf3bf12702d0bec48df5710bac2770b59aedeec46c563f2f4df9
- 6a7e95ffccb39bce1203731899b14adba3afd79d7bda7f783256011c510ffd0a
- 74a2bd67f90c0d6d906286d4aea6de32bd9bfb05ac631de15b8429758573d22f
- 7559d01473ed8f6a5d101e39ca32f5d2a975a018a017100967417c5ca8f5f578
- 983b13f4ae9b8b9dbb6fd5e4fa024e862628bd748d2ece92cf4b4c2048d88ad7
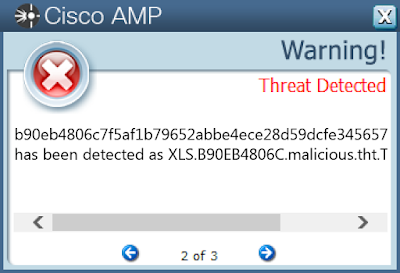
- b90eb4806c7f5af1b79652abbe4ece28d59dcfe345657cc6e5a04f52e07ded0a
- d23817b23214e53ee9400e9a307b522add72c875d3c98ba397525ac11c963379
- f06ebe75d30a2855c3dd1c6e7b3430765213c52db423f818f770b74329f451a1
Coverage

Screenshots of Detection AMP
ThreatGrid
Malware
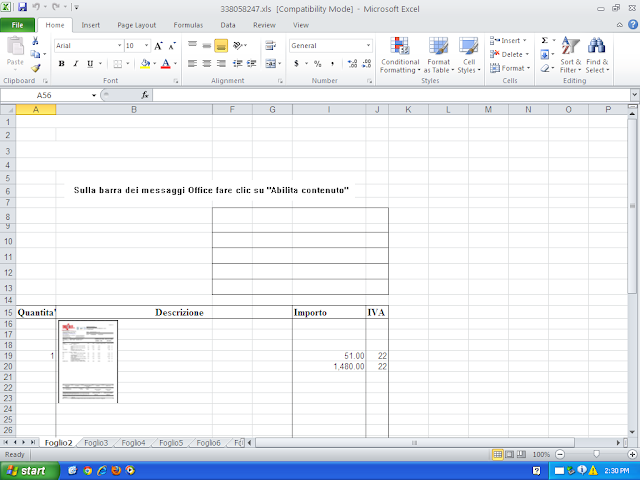
Doc.Downloader.Emotet-6765662-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\mwarepwd Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 144[.]217[.]184[.]168
- 198[.]0[.]36[.]237
- 162[.]220[.]11[.]30
- 216[.]198[.]175[.]99
- 71[.]179[.]135[.]10
- 184[.]168[.]177[.]1
- 72[.]167[.]191[.]65
- 77[.]221[.]130[.]34
- 179[.]188[.]11[.]22
- 74[.]79[.]252[.]106 Domain Names contacted by malware. Does not indicate maliciousness
- p3nlhclust404[.]shr[.]prod[.]phx3[.]secureserver[.]net
- ejercitodemaquinas[.]com
- jsplivenews[.]com
- dealnexus[.]intralinks[.]com
- gvmadvogados[.]com[.]br
- infobox[.]ru
- chstarkeco[.]com
- www[.]infobox[.]ru
- www[.]legal500[.]com
- g-steel[.]ru
- www[.]gvmadvogados[.]com[.]br Files and or directories created
- %LocalAppData%\Temp\GmP.exe
- %TEMP%\GmP.exe
- %LocalAppData%\Temp\hu3xyaa3.0rw.ps1
- %LocalAppData%\Temp\mz5ranh3.2bk.psm1
- %LocalAppData%\Temp\CVR2D3B.tmp
- %LocalAppData%\Temp\~DFA8496BB3134EB884.TMP
- %WinDir%\SysWOW64\YC4GWpe1p4Ot.exe
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@gvmadvogados.com[1].txt
- %SystemDrive%\~$4550683.doc File Hashes
- 0da3104bfc37f64817dbbb0f5fd699c19db913b2a2f5c6f883b0813f1669638a
- 1ca11cdd2bafbcd28491f6e46e1a2dfd9c435effb2ac941c7d164114d82d2aec
- 21694e71a6d384e5080e422ca98dd16a52c39e430bfdec1732b3706c480914e9
- 25fafc8f6d6819add0f2f907d1cf8a760ea0e4256b5a9997ebae705a7f40691e
- 434a1520a7608017e839ecd8804d04ef5d53d0b1dfaae1e8865383510cb314ca
- 46c708f3468052469785a18c61440521d05eeeb48625122b2f0879924fcf19a2
- 4e03038cd03633b18f289487b717e6f9b75315c382794c73943092f6a90d170b
- 6007e6c3de3dade995044f661cd8d53a9245ed12c1c56d427bdd3aa267398921
- 6311b3f0767a57f8c7ee0c6e317fad84bc9d39a12e48f28505ecddc842a66095
- 8286c59c07e75f97219bf649077d3ea44f497e715376fa867fec38fc34917ae8
- 9248345ccc78b67a968c1f2082916ee58d0ce5642698a7a6e2f830f65937bc8d
- 95696fdc9073bbb5feb71da630fa3c1f2255c3f7025bce4bc2ce7a0bda261bdf
- c060f2d8dc9a46d2805e514584fcdf02e39e2e56110c2ef0f0464e2ae40d3842
Coverage

Screenshots of Detection AMP
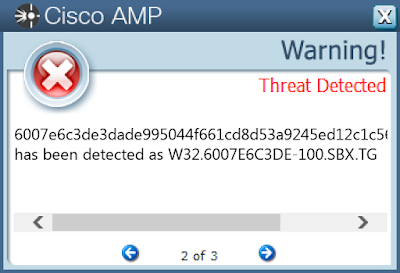
ThreatGrid
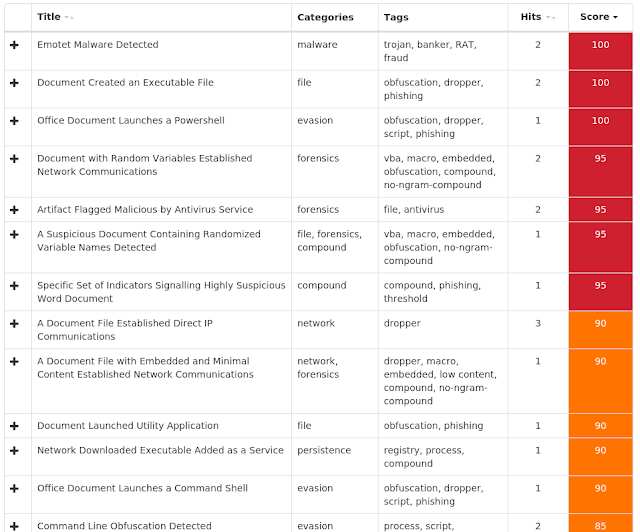
Umbrella
Malware
Win.Ransomware.Imps-6765847-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Global\LOADPERF_MUTEX
- DSKQUOTA_SIDCACHE_MUTEX IP Addresses contacted by malware. Does not indicate maliciousness
- 185[.]9[.]147[.]4 Domain Names contacted by malware. Does not indicate maliciousness
- s142814[.]smrtp[.]ru Files and or directories created
- %LocalAppData%\Temp\98B68E3C.zip
- %AppData%\Microsoft\Network\srcc.exe
- %AppData%\Microsoft\Windows\audiohq.exe
- %System32%\Tasks\ApplicationUpdateCallback
- %System32%\Tasks\System\Security\upjf
- %System32%\Tasks\System\smartscreen File Hashes
- 504c6e964c591cd6b4aac5193600058863a5c3c3b9ae7e5756315114fb032a11
- 52691c9c33c0b2707d74cca5738a15313ccd5264279a20933886a1f4d60aaea1
- 6acf9095e1f5725380bdac7fd7d1d9f07fdb44daa4682c2c8ef001094252d699
- 8c84a6d109b529446bb89ae69175f848579699bfc0bcb6dd23a2cdfd31b48f43
- 8d19e0e2b8ca2d659ab37a67e094d09b3e208453a2db48fea93840a203f3e7db
- 982024167a8bc0e5f6fce2b476655b91c821d09f324f95e77f0d38358d1a881b
- 9c2d5ab12e6f67faae5444007b9135834af71cc5e23c53801fa39877b9068101
- 9c4780fa358ee65ac1f2361e1e2757f475674145977bfb8a43870538dd6f85ca
- a3786fbfefcdec86bfb9ea1f4d14faa1285dab5bc846ba556b6b9ba3c974c420
- ca7073947e41d18d30565366df2522f12bbeb0d4a856e1572d654a3d569bd3ce
- d2482568a93e5755ff97a8a481e92db8d3f2e4995ee310645f9a1951a9075250
Coverage

Screenshots of DetectionAMP
ThreatGrid
Umbrella
Win.Virus.Sality-6765491-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\WOW6432NODE\Creative Tech
- <HKLM>\SOFTWARE\WOW6432NODE\CREATIVE TECH\Installation
- <HKLM>\SOFTWARE\Creative Tech Mutexes
- csrss.exeM_328_
- lsass.exeM_428_
- smss.exeM_204_
- svchost.exeM_840_
- wininit.exeM_320_
- winlogon.exeM_356_ IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %System16%.ini
- %SystemDrive%\autorun.inf
- %System32%\CmdRtr64.DLL
- %WinDir%\Temp\CRF000\APOMgr64.dll
- %WinDir%\Temp\CRF000\APOMngr.dll
- %WinDir%\Temp\CRF000\CmdRtr.dll
- %WinDir%\Temp\CRF000\CmdRtr64.dll
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\bkhxl.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\pelbwv.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\scih.exe
- %WinDir%\Temp\CRF000\creaf_ms.cab
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\tlinwq.exe
- %WinDir%\Temp\CRF000\mint.ini
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winbdaue.exe
- %WinDir%\Temp\CRF000\mint32.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winbhys.exe
- %WinDir%\Temp\CRF000\mint64.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winbqckk.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wincsbehn.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winfudq.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winimau.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winjcsnxu.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winkggnjk.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winkmdt.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wintyttku.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winvcpbm.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winxraoo.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\xatik.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\xovxjg.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\ydgy.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\ysrnph.exe
- %System32%\drivers\oiihn.sys File Hashes
- 055dd786fbb1c16e793f806368aa0f05ab7ef45db767fe5a7a829f11da37da0a
- 14f659a71058babb085af0f228c34339da3f124fdd66f63976357d64e69c661f
- 1daef9e1a3fe804680acf7e0a64724d4c106fea7aba46d437738b7ab72cff59d
- 3b6a5842eeab177d8d869f8eac9aea7342cb1117ac063e4cc2e3c4298107b028
- 5d83a8691b914f3971c6b91e8c82803b479ae70756cfbeb987ddb842eb399d8a
- 88f585ed82535a991dee6b054caf7efd9f4bb54acdde8fdf7d05eba8997d1058
- 973dbe64453445eb82a2e619842f46c8ed3e6ca74533db582b472e79bc01601c
- a28cd979f9395cc482d9de5d7fd676a379e97920a37784763bfb72f348556cdb
- d746b850bf25ef3872d33c3b0067910b8d075a0bed0af89c3c14ecd2efee3fab
- f2864685d01a793c2e76191d3be5278b6e1d59a9fb5b20e7a229e3d634108c8c
- f6c27d2fdfed0a6b67e5aee197388797ef77a4cece21c849ac096d075dbd93c9
Coverage

Screenshots of Detection AMP
ThreatGrid
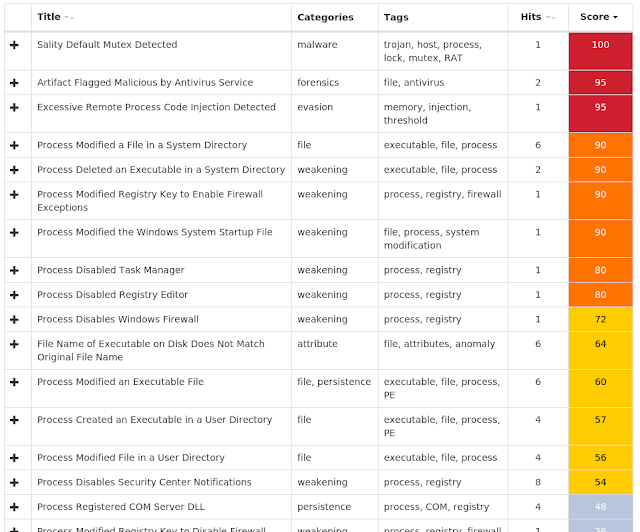
Umbrella
Win.Packed.Passwordstealera-6765350-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 173[.]194[.]175[.]108
- 104[.]16[.]17[.]96 Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- \??\E:\Sys.exe
- \??\E:\autorun.inf
- %LocalAppData%\Temp\holderwb.txt
- %LocalAppData%\Temp\holdermail.txt
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\dw.log
- %LocalAppData%\Temp\bhvBB7A.tmp File Hashes
- 02e17144bd22b469828d3a6663ce5ec0c87e24e729322cb97cacbcb4b2949033
- 02fc82a18398f81deaee007c20d90e0e3c9722b30d2698f90e796023fc5e1740
- 04757c1d814ad34c90bdee0993b86a0b33301abffaee9818310341a950cb9815
- 0496858beb4cfd6709dff2122d85e33245ff41ec53831b8fcce61fc5702bef74
- 04f66de839722231e20ae25ced41dca0f5e62d1e50b0accca5b65b192d6e4c58
- 0526201aa5028da43a2e3d8192c2d62c6953e4f940a631a6365099a22c934200
- 055b60ff72bbfc431a15134e7dac00b64a3ba6f53f8041b62d3676e2c0e517fc
- 05a3db5d7b308fde9e5763fc960d88463eb1c517a1a645e9cd38229269bf1627
- 05e18862ebc7be845735b589227ee2ae63ee66bc7ffb3755c52a8f84495d80db
- 06b95f87826fe1272911920412ad972b931c31b1c785fa27ec05c177382da0b6
- 06c4d3945b94f611019fc283b93fd63fb3f8405796db59cb5f8222782d0c7ea4
- 0826278ce6120f1730ff87aa84ded08db3f6941cc910f46d9f57957ecf699049
- 092c6895af99df4b4c094f62e3a92d6d8bf0088844b4b6bbf691bb4f625850d3
- 0a46824e179fb9eb61835adb9c9a02919bf41a756f9dbf120cbaed51acf17166
- 0a82eb0c8e3d7c2334c4eff82dc394f65654bf72b8ceb6e9d940d90ed3a6ba0a
- 0af37d3cb266570cc11f48a4eff5fc4cc4636b7b180801e4cd677bd2d29ce22a
- 0b5552c57c06a47fe86276ff15b2695ac2e9dcc6cad5f98f2ba5c43e14932b89
- 0cbb8c5cac42acaaf4136770140177fe6261271ec1d035cd433a8b9a97e602d7
- 0cff7e9d13a3216254aba643143dd218ca25ec2a503be1516f97a10fed1a151c
- 0d07f7c0463a4db0108f63464284c6f278b5ebce3252c8c5172f51e123208d7f
- 0e187bb3f6a4c196a92d1ccdcdc0db28861a0be845f0930a9eb308d27489755f
- 0e428856132a0fc043f63994abd9cf9fe06975a21f16187d1758af8b73785b1e
- 0e4a73fe7c720fa7b00134247ba8aae22ff6cf3cb4edfd994fb599c102462b4b
- 0f4682294cea6ff676cc6aa4fbec8fb899bd3bda0b8f73c51e116304a85d5358
- 0f5a78e562be95f13a1fd161b81f11f142e560758b48f12b631b83a38645817e
Coverage

Screenshots of DetectionAMP
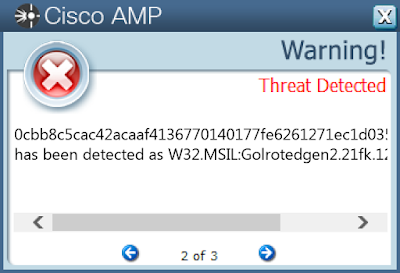
ThreatGrid
Doc.Downloader.Sagent-6766662-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 144[.]217[.]96[.]196
- 68[.]66[.]224[.]4
- 188[.]40[.]14[.]253
- 185[.]45[.]66[.]219
- 192[.]185[.]122[.]50 Domain Names contacted by malware. Does not indicate maliciousness
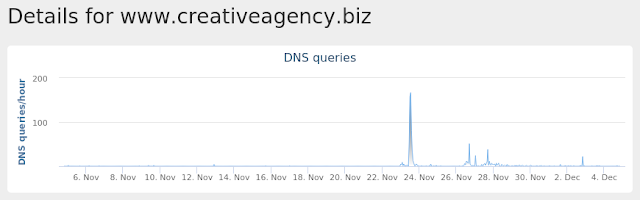
- www[.]creativeagency[.]biz
- mandujano[.]net
- biogas-bulgaria[.]efarmbg[.]com
- mahimamedia[.]com
- www[.]brgsabz[.]com
- creativeagency[.]biz Files and or directories created
- %LocalAppData%\Temp\zUw.exe
- %LocalAppData%\Temp\dxaf1lgn.ghy.ps1
- %LocalAppData%\Temp\mj5uf2iy.ilx.psm1
- %LocalAppData%\Temp\CVRE3A0.tmp
- %LocalAppData%\Temp\~DF21FCDFAA58A2E1E9.TMP
- \TEMP\~$c0d21bd6c8e28fdebd78dd6505135b6cca400773990a89056de054ed7cbe29.doc File Hashes
- 0093dcbd8f4bbe4b06e73de6de547ad5993077a113a44c4323a976433246b86b
- 0842492265ff119471f0caa69725591341898fde26bf968bbd5471470154cd3b
- 201227dd0b8a0fa4b3d9b9cddf1f209c6de1addda9bff6adce66a626838f7e66
- 25884a9b024598d9acedc91f15fd6297cba4dc3f704d6a19f626c86e69667e17
- 29932262d4afc2f1c90346e826a4df4d56f18bce251fb70993d6d601ffbe51ec
- 2e3431ff0a71cbf27d91acbce1e1dc80e4ca59873f451dca029aa0548a732bd3
- 30a2e836865ade4af8e8e35726d7187658804ae243ec4a6ef1085d27c2ea18ed
- 3204ba3905b38598a69f46de696b2305f5d1052bf0c42d62facd220fdd6f59e1
- 3d50876ea89c344ce580f8105d16077c6345a23cf8738668fb0985abf6dcd03b
- 3f631a8710b38c08cc4ec7098949908017023ead46db09357c0cfa00e0f88b81
- 42a55cc69003e563f10fc82e660da83815e969d1b40018a4687ff024f2745e56
- 48c247e5dc712829c5af6a481e0466eb4c92d6ba88bd21bf396a72bd1b2ef22d
- 50e0322b2884afb29a5d3d00b59a46ec1328accd770e877b03024eaa81d487b4
- 5d4af8e033d5aadba853c0c16d63b672c521a93d5c595c8efde012e3a3a24424
- 7d25d591fe5291003a2c43e8d479dfd06ad40c2720a9fc3ffe4b304b97678602
- 8bf2b7e3d0b5d4928ba715c5a7060aea26a7c0fe487853135a03bf6d02af581b
- 8ca568c68a48c2af33147af88da854129364ae3217832cdae95842101ca031b9
- 8d782fc91c991a792498e33dc2db3a2c05f3a3630d6ee0ea5a616e95a67071ca
- 8ddc6466bafab540c2efbb2b24492addb9e8987c0fd54676f68d15e23cbe3480
- 9a43186e72bde764614b092b55d4dfba00f528c5f0d45e6ccb56dcee8763a845
- 9aee7617f88dfffed06e6998a6cfaf8dc1f92dc2ab0164b495a4980fcb9799e1
- a0ad77058d9f583cc7d4127cbeb367e4d714968336157b8ef03e6945c260dc1e
- aeb657063c6507df8da52bc48126c8cfd5d0bd89113d00e4ea1e698f8fb6425f
- b1c0d21bd6c8e28fdebd78dd6505135b6cca400773990a89056de054ed7cbe29
- b66d3770ec1baa5f15c4665d3ca734c4613c0d6bb0e9c167de0a70b1a44f5a41
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Malware