Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 29 and April 05. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
- Win.Malware.Vobfus-6919817-0
Malware
Vobfus is a worm that copies itself to external drives and attempts to gain automatic code execution via autorun.inf files. It also modifies the registry so that it will launch when the system is booted. Once installed, it attempts to download follow-on malware from its command and control (C2) servers. - Win.Malware.Barys-6919339-0
Malware
This is a trojan and downloader that allows malicious actors to upload files to a victim's computer. - Win.Malware.Zbot-6919277-0
Malware
Zbot, also known as Zeus, is trojan that steals information such as banking credentials using a variety of methods, including key-logging and form-grabbing. - Win.Malware.Autoit-6919193-0
Malware
Autoit is a malware family leveraging the well-known AutoIT automation tool, widely used by system administrators. AutoIT exposes a rich scripting language that allows to write fully functional malicious software. This family will install itself on the system and contact a C2 server to receive additional instructions. - Win.Virus.Expiro-6918982-0
Virus
Expiro is a known file infector and information stealer that hinders analysis with anti-debugging and anti-analysis tricks. - Win.Trojan.Winwebsec-6918829-0
Trojan
A that masquerades as legitimate antivirus software, alerting users to nonexistent threats. It disables Windows Defender and Windows System Restore. It also may block users from accessing websites or programs until they buy the "antivirus" software. - Win.Trojan.Emotet-6918815-0
Trojan
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
Threats
Win.Malware.Vobfus-6919817-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Local\MSCTF.Asm.MutexDefault1
- \BaseNamedObjects\A
- A IP Addresses contacted by malware. Does not indicate maliciousness
- 208[.]91[.]197[.]66 Domain Names contacted by malware. Does not indicate maliciousness
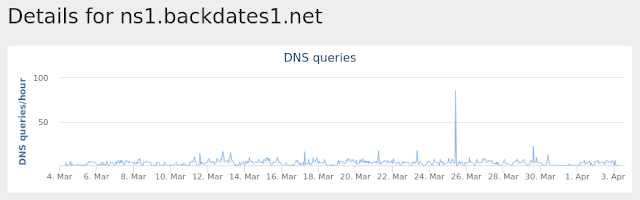
- ns1[.]backdates1[.]net
- ns1[.]backdates2[.]com
- ns1[.]backdates4[.]com
- ns1[.]backdates2[.]net
- ns1[.]backdates11[.]com
- ns1[.]backdates17[.]com
- ns1[.]backdates8[.]com
- ns1[.]backdates15[.]com
- ns1[.]backdates3[.]net
- ns1[.]backdates1[.]com
- ns1[.]backdates3[.]com
- ns1[.]backdates5[.]com
- ns1[.]backdates1[.]org
- ns1[.]backdates9[.]com
- ns1[.]backdates10[.]com
- ns1[.]backdates16[.]com
- ns1[.]backdates1[.]net[.]example[.]org
- ns1[.]backdates15[.]com[.]example[.]org
- ns1[.]backdates4[.]com[.]example[.]org
- ns1[.]backdates9[.]com[.]example[.]org
- ns1[.]backdates8[.]com[.]example[.]org
- ns1[.]backdates11[.]com[.]example[.]org
- ns1[.]backdates17[.]com[.]example[.]org
- ns1[.]backdates2[.]net[.]example[.]org
- ns1[.]backdates16[.]com[.]example[.]org
- ns1[.]backdates3[.]com[.]example[.]org
- ns1[.]backdates10[.]com[.]example[.]org
- ns1[.]backdates3[.]net[.]example[.]org
- ns1[.]backdates1[.]com[.]example[.]org Files and or directories created
- \??\E:\autorun.inf
- %System32%\winevt\Logs\System.evtx
- \autorun.inf
- \??\E:\System Volume Information.exe
- \$RECYCLE.BIN.exe
- \??\E:\$RECYCLE.BIN.exe
- \Secret.exe
- \??\E:\Passwords.exe
- \??\E:\Porn.exe
- \??\E:\Secret.exe
- \??\E:\Sexy.exe
- \??\E:\x.mpeg
- \Passwords.exe
- \Porn.exe
- \Sexy.exe
- %HOMEPATH%\Passwords.exe
- %HOMEPATH%\Porn.exe
- %HOMEPATH%\Sexy.exe
- %HOMEPATH%\c\Passwords.exe
- %HOMEPATH%\c\Porn.exe
- %HOMEPATH%\c\Secret.exe
- %HOMEPATH%\c\Sexy.exe
- %HOMEPATH%\Secret.exe
- %HOMEPATH%\c\autorun.inf
- %HOMEPATH%\seofuaj.exe
- %HOMEPATH%\RCX9D65.tmp
- %HOMEPATH%\RCX9DC4.tmp
- %HOMEPATH%\RCX9E23.tmp
- %HOMEPATH%\RCX9E91.tmp
- %HOMEPATH%\RCX9EEF.tmp
- %HOMEPATH%\RCX9F5E.tmp
- %HOMEPATH%\c\RCXAE6C.tmp
- %HOMEPATH%\c\RCXAEDA.tmp
- %HOMEPATH%\c\RCXAF39.tmp
- %HOMEPATH%\c\RCXAFA7.tmp
- %HOMEPATH%\c\RCXB015.tmp
- %HOMEPATH%\c\RCXB083.tmp
- \??\E:\seofuaj.exe
- \seofuaj.exe File Hashes
- 046c299741954c07ca5feab9039d7a7208c9e5dad3fca354041acdecab550cf9
- 057d66787c6ee44bd9d8015f563c3b6e2eab4a83bfe2eee53e1b7d0006e0df84
- 05f0f24b4fc446cf95fe3be015fe0f61908d1b5cbb1706a14c2e393886454f38
- 0b5716a756064ebe398f0e164f8d7e0dd747ca50795e3624b5574fd78e92059d
- 119bb2c3b038c70448cbb9a4a8f8eeed1071d2174f5d1907a01d348f1740927e
- 1506a6d7439fab0a6b3c775fdde0627bacafa4760900c0f111edce4d55a03a50
- 1bd8db7ee7413001573a689ae4ebcb29da7652717f35ecbd735a87f3d621586b
- 272c48ac067319a1c8d51717c5f34b34ac4db4f970f9fccc5915d7bf77123ecb
- 2bd2f27610560eea9d652b3b8c44225a4b66ef349350e53fff8b42406f74ad3d
- 2dd8cc3597a6e411b7f258c2ecb78aacd54d9cadb3807997b2b00c1a4e07e178
- 368d741aef2ab6e41a4696f5d28dee169580dfff4cc69a5946faaec3d14925bb
- 3b6a66df8369ac8bf26e8402989d29534b7d7e1c7e460d970f50416e2afe5ffe
- 40466788e57d5200867dcfd7a3f2c18004b8317c19a0528af585c537edfc1201
- 4a67a46ce70cd36aab995cd0a04621a4050cac0488bab6c433efb1324c6b4513
- 4b77f7be93f7a27a30a87f5d3fd611d54ead6b62a18a12dcfca3bd65f3081e86
- 4cbbeba77a0e8af025aeb17352a36b6c75687a00827ecac1f9dfac206603ab52
- 4ce11c03c2fd40bd58f7044d9bf17fce4118e31cc058113a8cb6d68b0fe2cbc7
- 5312c2573551bf4ea733031528f4e79b8b1c675c2a05e4059c06cf9c2706b9e1
- 5ebbf7f1ffdb7f5a5483ad26971c20bf7ffdea7fd1566260d6e4875ff9a477c1
- 61707b56cec807908e713dd8acbcc2ee8b7359c9c3e8eb826e53fca3fa0de866
- 62312807fa51f896940f2480b29a133365a146eccb5c5775faf886f3238b2f9a
- 66c85f135b970fd774f2582202458bd083ecf71bc1f80cd195706d7b354bb601
- 689860f079fe900589e3c70af6932587b44135439b48cde5462537008a9537f4
- 6c863b2f65224fbc6d85702cf9cf48b120a851ec4c2f7e76b21c9c56b5427d82
- 6fc3ab28e7177cf2ca67f6d3a945979b6bdce37eea446d21cef54181a673a35c
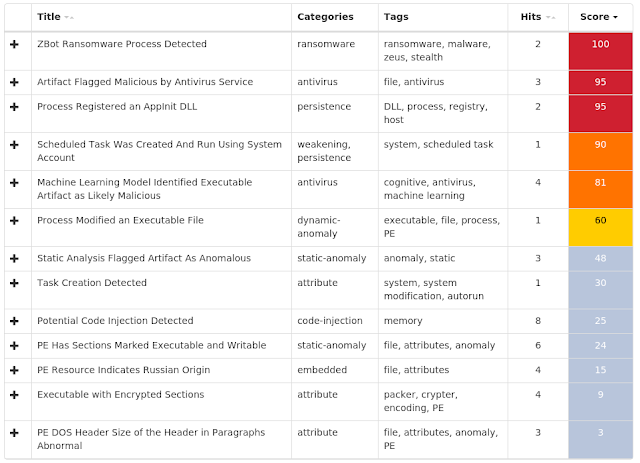
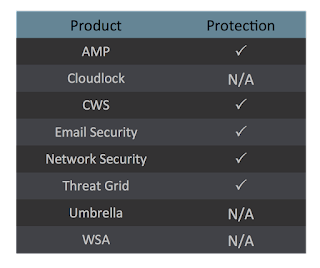
Coverage

Screenshots of DetectionAMP
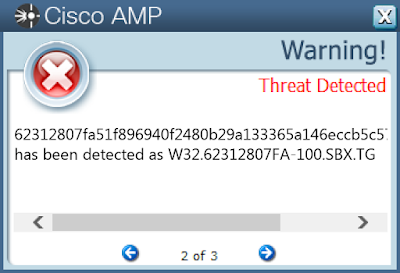
ThreatGrid
Umbrella
Win.Malware.Barys-6919339-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\AYBBMTE
- Value Name: Index
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{FF46FC7D-1E0D-46F8-87EC-94D0FDA83668}
- Value Name: Path
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\AYBBMTE
- Value Name: Id Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 216[.]218[.]206[.]69 Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %System32%\config\SYSTEM
- %System32%\config\SOFTWARE.LOG1
- %ProgramData%\Mozilla\thfirxd.exe
- %ProgramData%\Mozilla\thfirxd.exe
- %System32%\Tasks\aybbmte
- %ProgramData%\Mozilla\lygbwac.dll
- %ProgramData%\Mozilla\lygbwac.dll
- %HOMEPATH%\APPLIC~1\Mozilla\kvlcuie.dll
- %HOMEPATH%\APPLIC~1\Mozilla\tfbkpde.exe
- %SystemRoot%\Tasks\kylaxsk.job File Hashes
- 0869ac4f786a1f544abdab137e4470e008b50ae49e740f4137d2457805e4ded4
- 0db104c871e5214fc4365b34cfdc74c4e0330668da0399653865f43d96b58160
- 106af8294406803fa0773813b3d827acdacc00e2faabb99d215afd091226b7b2
- 1ea3c3bd8673dec3901d7f82b77f8e8bfad3bd51bd80d7796b2a9b7e07a98339
- 223b3d2d4ada9ab9423efa187c1d230503ebd37fecca1209f3afcb9c15d961db
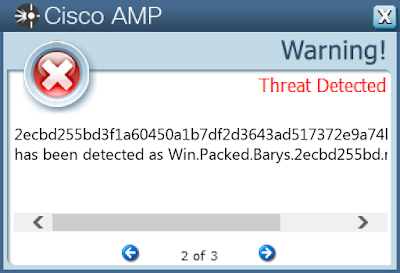
- 2ecbd255bd3f1a60450a1b7df2d3643ad517372e9a74b41fb2981d31ceeb017a
- 4034f9ff4d3fb10e1afe93e12e97183f8859b5c745cde8e9a52cbe0c93a7524c
- 4b89e180490dd4da410bedbccb5c98cb78901b752eedeea3588c25a833117b8b
- 50136cda2cb504a1c9dc6344b24d1b46c5c24c87b97fb33da23ab52346217f95
- 5316ea912b78ff5f98cffbd4104bc5f57abc07946e53a0e7b4ed4100e9a511e0
- 58007a4c73c96932b44d67ec7c6db050ed18577f2cc5eec427be6a2b6a962dd6
- 5a5c3aa34c245fb90404cba3d98ab53445683ed8dc470bad316707915ad1fbe7
- 5e0b77a4db61b89aa98faa07433c12366cef0b747b677005df139c18a48e8643
- 60a0121cfcffdd898bb452aa464bc9dd0cf658b11285b4ba917c480046503370
- 6b4864ef87cbc0b4884075a60f5bfbdb39e84405fd6f7f01b019c81013ef9b68
- 7e777487165f72a5d42608e2bc4c3fb8ccf0c2aa0c059c53f4c05d6318803be6
- 809c104c5546b025e8680f612573ed4e1123a19cab555deb9984407d69c18abd
- 84d35bea78f59fcb33cc45d7ea6eca8d9cb1b9b1a1a5c493e88e020386c1eb43
- 868b8e6f1301f54178839130eaefc5bbf2e6aa1c78e6054389a1f2d0b02a1bcd
- a0aa2c03d0f4e9caed5f0a1e52e59423944864ad2d9ccdcd54b271d7133bbf2f
- a6e84c3b4c46fbb17f9ae770c2244579ab3e7b82621290d977ff93b539b9bf37
- afecfc0b7e4c6218fcfb546ce088cbd6b5087358a5e44bab9595df720e1a7490
- bb04cca5245d8ddda41a24339ab63e8519bffd83a2bbcf80e74c2945bd1420c5
- bf211d2a71ff102c2c4fc3d41afb7f9a4f46e37aea06b64d86cddca372438d44
- da42054f51ba5744d7b2be271b96bc220002a1c5dee7580c540746a6f8436dc5
Coverage

Screenshots of DetectionAMP
ThreatGrid
Win.Malware.Zbot-6919277-0
Indicators of Compromise
Registry Keys
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\COMPATIBILITYADAPTER\SIGNATURES
- Value Name: aybbmte.job
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{FF46FC7D-1E0D-46F8-87EC-94D0FDA83668}
- Value Name: Path
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\AYBBMTE
- Value Name: Id Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 216[.]218[.]206[.]69
- 116[.]255[.]235[.]9 Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %ProgramData%\Mozilla\thfirxd.exe
- %ProgramData%\Mozilla\lygbwac.dll
- %ProgramData%\Mozilla\lygbwac.dll
- %HOMEPATH%\APPLIC~1\Mozilla\kvlcuie.dll
- %HOMEPATH%\APPLIC~1\Mozilla\tfbkpde.exe File Hashes
- 19300406a8fedba8513085fa93004d3330024e3a97d685c34bf4404e15e9beea
- 1d8005f6fecbb238db1b40e6cb7afc2baf323c0059883f0bb7b11c01c1067026
- 276dab07147db188ff45e12e53ec462af42e1973a4687a2b2e3e9301c15db929
- 2a0588520f7752424195cc36e6843d09ec850b6c7a41e966af58f3ebee8353c0
- 33626a9cd5105d595872d76146629d1b440bb625383ac30f71c7f9ff369982f3
- 35b7a37a7bd1ad371add7f0d3a3d9e3f9d8dc22894d0949c775f9eec5fd60104
- 3832485cab5a4ea92c616b24bf79374a4999eb76119e2e14e40c7f693a71ea1c
- 408f335dc58fa9fe44e16c4f76813c3cb6bca1821134cd3eaacc162787d74ee7
- 424171b94775b10d108095adb1a29f3ee6b8918e2bc3e6b96d62ea8a9c2ff01a
- 42c89f9e463771c6de93ecbd94210a7242234ca512ba2d68e4133e7835ce9f46
- 466731dc06288c6288b2b306ecd2d457d23624b32dc8a6ba950f2344a4ec0228
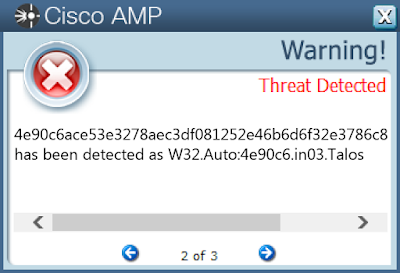
- 4e90c6ace53e3278aec3df081252e46b6d6f32e3786c862895fc724595bdfd09
- 54f29401d5a69da03b8e1ed390e76a94b0967ae4859d885db5abd5a8632a8ce1
- 58b1da3642367b1f8f80a018befaaeaa91ddbc0187d56f52c62eebeb06ac4291
- 5c41aca107b6f288e5436c5722150e62845d594a89dd31de98865f87a1618880
- 6ce10269595ec82e081472bddbdfd235086f6205dd836464e68c11b29b56a96c
- 701fd08f2dcd10f75e462feaeedbc04c5d640d57e7203bfecf490c79b8da50ab
- 795fb4569df188d5ce7ec1448d5088ffa7dc79bf60ea02e0fde15a2e8b4d0868
- 79af5e9ff5b60e9ac555bf82c43d01b20d7a2d4faa85fff2651883cff52be4e8
- 7dcde4f60dd8f1caf3c37047cbde35c00ff4c70d2bb6e33ac6811c0f2d0a7742
- 84ab81138637667e9a304c70f6332d6e07a7fe01cada75b87501e1119654fe62
- 88fd82e899034dfaeaf5fb3fa40ee31849e35dc781718119207c049a506d47b8
- 8be6442f102a1a607ba44cb708e1b78c847a17d583e8caf673885613ac58eb35
- 8d6f9213c8611b2d23dbe7ad43749c20332f35926c72eb71d4b8bc125b80730f
- 8fe26438c3bd8257c7c09e13bcb06f049a65cdeef64fdf6260048b97c839c72c
Coverage
Screenshots of Detection AMP
ThreatGrid
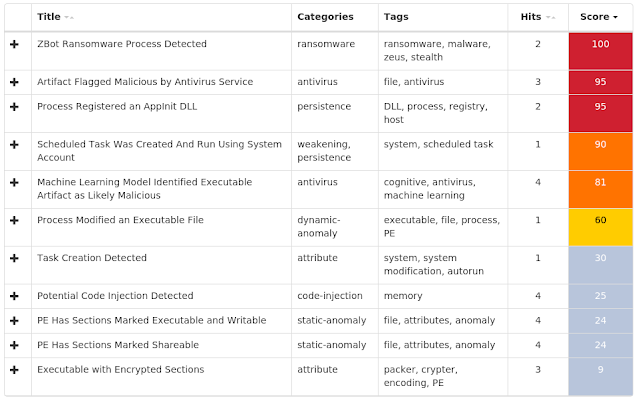
Win.Malware.Autoit-6919193-0
Indicators of Compromise
Registry Keys
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value Name: LanguageList
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\WinTrust\Trust Providers\Software Publishing
- <HKCU>\Software\Microsoft\SystemCertificates\My
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: ProxyBypass
- <HKCU>\Software\Microsoft\RAS AutoDial
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\CA\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Disallowed
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\Certificates
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\DISALLOWED\CRLs
- <HKLM>\Software\Wow6432Node\Microsoft\SystemCertificates\Root
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\ROOT\CTLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CRLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUSTEDPEOPLE\CTLs
- <HKLM>\Software\Wow6432Node\Policies\Microsoft\SystemCertificates\TrustedPeople
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\TrustedPeople
- <HKCU>\Software\Policies\Microsoft\SystemCertificates\trust
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\Certificates
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CRLs
- <HKCU>\SOFTWARE\POLICIES\MICROSOFT\SYSTEMCERTIFICATES\TRUST\CTLs
- <HKLM>\Software\Wow6432Node\Microsoft\EnterpriseCertificates\trust
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CRLs
- <HKLM>\SOFTWARE\MICROSOFT\ENTERPRISECERTIFICATES\TRUST\CTLs
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
- <HKCU>\SOFTWARE\MICROSOFT\RAS AUTODIAL\Default
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\OK3KMXI9HE
- Value Name: inst Mutexes
- 3749282D282E1E80C56CAE5A
- Local\ZonesCacheCounterMutex
- Local\ZonesLockedCacheCounterMutex
- eed3bd3a-a1ad-4e99-987b-d7cb3fcfa7f0 - S-1-5-21-2580483871-590521980-3826313501-500
- dxdiag
- \BaseNamedObjects\dxdiag IP Addresses contacted by malware. Does not indicate maliciousness
- 62[.]173[.]139[.]203
- 85[.]143[.]175[.]2
- 107[.]173[.]219[.]120 Domain Names contacted by malware. Does not indicate maliciousness
- jfnutts[.]com
- jamesxx[.]dynu[.]net Files and or directories created
- %APPDATA%\D282E1\1E80C5.lck
- \PC*\MAILSLOT\NET\NETLOGON
- \lsass
- %APPDATA%\D282E1
- %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5
- \samr
- %APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\Preferred
- %APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\7bfba4ab-37fb-49ad-95de-c46116256232
- %ProgramFiles%\Microsoft DN1
- %ProgramData%\images.exe
- %LOCALAPPDATA%\Microsoft Vision
- %HOMEPATH%\Documents\20190401
- %TEMP%\~DF3968B9D4F94E63DD.TMP
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\.url
- %TEMP%\4vlsgi4i.nxw.ps1
- %TEMP%\gs2vkrhw.jd3.psm1
- %TEMP%\1xjo2rvg.l3o.psm1
- %HOMEPATH%\.exe
- %HOMEPATH%\.vbs
- %HOMEPATH%\Start Menu\Programs\Startup\.url File Hashes
- 00e6268b7676fe162515c9b4191ae17186d708961a5545cf2b0e76e0d702a035
- 02f9a5389aea7c071f277a51bbd449d845b7e5acb5a94c5e795bd283415569be
- 055f89ea1016a672124bf38461d7a04632c9caf270714a783b34fa014e038c57
- 06e27b85a1994a896d81cf423bbf9bbff1bbc5d89d26d4aa8b0fbbfa6b824d13
- 0837fda8e72d32584a4c53dcc8f7ca75f38eae979d178f6db434e9521fbe82e8
- 11a4e3e12cec6041bdf9508c56a7d75a00992f59c929172eabd8725a89904970
- 15159b94f3fbf990f53b9df0a5f08b66fb1548e84d48c99a7537be84bece2062
- 1f450f566e7896c60524017d006bb01902e854371313abb8d8f62038de2ecc7b
- 21705746b4eb464753d99cc7999db91a55ca4a8a08ab53b8031c969adc47d899
- 31cdf98e7e648986edabcbf58a70030ff882d2ec08106440b2b97b7d17d890f5
- 468bd5cd0779eec9d11b325e5dd7aa7721e7189a04b7d92a236279d1cbab4439
- 4e46d7ddef280bb91c73f15975b610d3bc4be014d29f05dade4860932cd63913
- 556b0f36507a9da9bc8236d6328ac25b7d42e7d62d859ccb6163d117d9d39ccc
- 64c2d4517abd6081f6401ee4237132f087177b8891d9840ae9e69fdd128dc9b0
- 7254eb9ebb64ad0916d7678e8d01fca31a18d73f970a64394f9fc88069590929
- 8594f3e2f19d3512830312737a9706fb8a3a92ab8d4afad9f2005c8d6c644db7
- 8616e952c063ad624242745f595803a39931e134bd319b57cc36251e73aad3cb
- 8acab560aa72f1d6a39b1bcdc48334e51cb9654fb21185da22413434bb01d22c
- 9104f6034c2e99c2fd8d3158be68b20a93ba51f0d25b6e4908094f75cc3234ad
- 977eb4729a3f3f20fdda9cc7cb4ba5e5e6066f3e9f0d05874b9978bcd6471532
- a428bb2458b74579874a41d9ebb463835dc938777b7a21f52454af4e52856603
- b1aa39eef0e0f815f9c91993cc24e786cf050f17e818f103416e7dd95727b911
- c0406b0fedfb94e25ddd6b04947830c82460f5080999ad08fd5abc23fcf004dd
- d9e637657dacc3e665fa5abbaa30443f474a299c0fa61b801409233a62e8440d
- dad963b9062233185343b7564500514c8e51ed1056f717615e7885524a5ba8a6
Coverage

Screenshots of Detection AMP
ThreatGrid
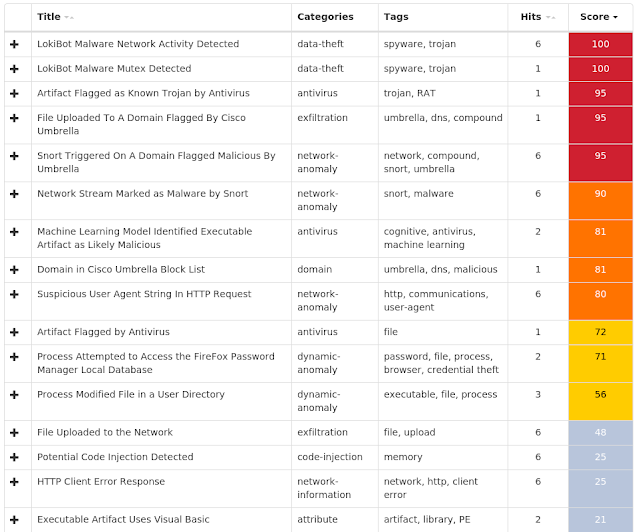
Umbrella
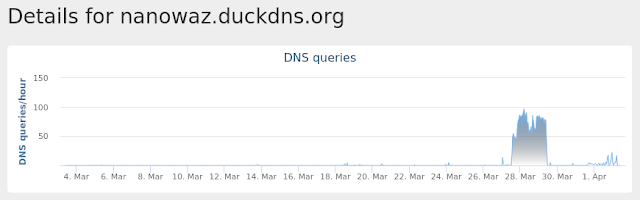
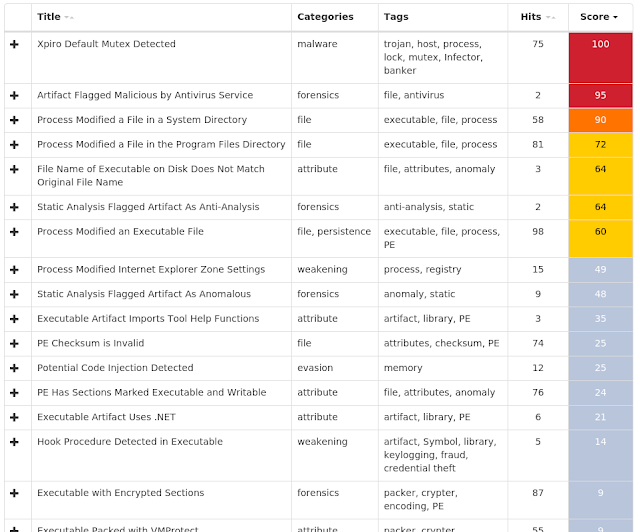
Win.Virus.Expiro-6918982-0
Indicators of Compromise
Registry Keys
- <HKLM>\Software\Microsoft\WBEM\CIMOM
- <HKCU>\Software\Microsoft\SystemCertificates\MY
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
- Value Name: Start
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\4
- Value Name: 1406
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\75
- Value Name: AeFileID
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VDS
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VSS
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WMIAPSRV
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WMIAPSRV
- Value Name: Start
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\.NetFramework\v2.0.50727\NGENService\State
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\.NetFramework\v2.0.50727\NGENService\ListenedState
- <HKLM>\SOFTWARE\Microsoft\.NetFramework\v2.0.50727\NGENService\State
- <HKLM>\SOFTWARE\MICROSOFT\SECURITY CENTER\SVC\S-1-5-21-2580483871-590521980-3826313501-500
- Value Name: EnableNotifications
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\0
- Value Name: 2103
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\1
- Value Name: 2103
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\2
- Value Name: 2103
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\3
- Value Name: 2103
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
- Value Name: CheckSetting
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
- Value Name: CheckSetting Mutexes
- Global\LOADPERF_MUTEX
- ASP.NET_Perf_Library_Lock_PID_640
- BITS_Perf_Library_Lock_PID_640
- ESENT_Perf_Library_Lock_PID_640
- Lsa_Perf_Library_Lock_PID_640
- MSDTC Bridge 3.0.0.0_Perf_Library_Lock_PID_640
- MSDTC Bridge 4.0.0.0_Perf_Library_Lock_PID_640
- MSDTC_Perf_Library_Lock_PID_640
- Outlook_Perf_Library_Lock_PID_640
- PerfDisk_Perf_Library_Lock_PID_640
- PerfNet_Perf_Library_Lock_PID_640
- PerfOS_Perf_Library_Lock_PID_640
- PerfProc_Perf_Library_Lock_PID_640
- RemoteAccess_Perf_Library_Lock_PID_640
- SMSvcHost 3.0.0.0_Perf_Library_Lock_PID_640
- SMSvcHost 4.0.0.0_Perf_Library_Lock_PID_640
- ServiceModelEndpoint 3.0.0.0_Perf_Library_Lock_PID_640
- ServiceModelOperation 3.0.0.0_Perf_Library_Lock_PID_640
- ServiceModelService 3.0.0.0_Perf_Library_Lock_PID_640
- Spooler_Perf_Library_Lock_PID_640
- TapiSrv_Perf_Library_Lock_PID_640
- Tcpip_Perf_Library_Lock_PID_640
- TermService_Perf_Library_Lock_PID_640
- Windows Workflow Foundation 3.0.0.0_Perf_Library_Lock_PID_640
- Windows Workflow Foundation 4.0.0.0_Perf_Library_Lock_PID_640
- WmiApRpl_Perf_Library_Lock_PID_640
- aspnet_state_Perf_Library_Lock_PID_640
- rdyboost_Perf_Library_Lock_PID_640
- usbhub_Perf_Library_Lock_PID_640
- kkq-vx_mtx1
- gazavat-svc
- kkq-vx_mtx89
- kkq-vx_mtx91
- kkq-vx_mtx92
- kkq-vx_mtx93
- kkq-vx_mtx94
- kkq-vx_mtx95
- kkq-vx_mtx96
- kkq-vx_mtx97
- kkq-vx_mtx98
- kkq-vx_mtx99
- kkq-vx_mtx31
- kkq-vx_mtx32
- kkq-vx_mtx33
- kkq-vx_mtx29
- gazavat-svc_29 IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- \srvsvc
- %APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\Preferred
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.EXE
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.exe
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.exe
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.exe
- %CommonProgramFiles%\Microsoft Shared\OFFICE14\MSOXMLED.EXE
- %CommonProgramFiles%\Microsoft Shared\VSTO\10.0\VSTOInstaller.exe
- %ProgramFiles%\Java\jre6\bin\javaw.exe
- %ProgramFiles%\Java\jre6\bin\javaws.exe
- %ProgramFiles%\Java\jre6\bin\unpack200.exe
- %ProgramFiles%\Java\jre7\bin\jabswitch.exe
- %ProgramFiles%\Java\jre7\bin\java.exe
- %ProgramFiles%\Java\jre7\bin\javacpl.exe
- %ProgramFiles%\Java\jre7\bin\javaw.exe
- %ProgramFiles%\Java\jre7\bin\javaws.exe
- %ProgramFiles%\Java\jre7\bin\jp2launcher.exe
- %ProgramFiles%\Java\jre7\bin\ssvagent.exe
- %ProgramFiles%\Java\jre7\bin\unpack200.exe
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.exe
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.exe
- %CommonProgramFiles%\Microsoft Shared\ink\ConvertInkStore.exe
- %CommonProgramFiles%\Microsoft Shared\ink\InputPersonalization.exe
- %CommonProgramFiles%\Microsoft Shared\ink\ShapeCollector.exe
- %CommonProgramFiles%\Microsoft Shared\ink\TabTip.exe
- %ProgramFiles%\DVD Maker\DVDMaker.exe
- %ProgramFiles%\Internet Explorer\ieinstal.exe
- %CommonProgramFiles(x86)%\microsoft shared\source engine\ose.exe
- %ProgramFiles(x86)%\microsoft office\office14\groove.exe
- %ProgramFiles(x86)%\mozilla maintenance service\maintenanceservice.exe
- %CommonProgramFiles%\microsoft shared\officesoftwareprotectionplatform\osppsvc.exe
- %SystemRoot%\ehome\ehsched.exe
- %SystemRoot%\microsoft.net\framework64\v2.0.50727\mscorsvw.exe
- %SystemRoot%\microsoft.net\framework64\v4.0.30319\mscorsvw.exe
- %SystemRoot%\microsoft.net\framework\v2.0.50727\mscorsvw.exe
- %SystemRoot%\microsoft.net\framework\v4.0.30319\mscorsvw.exe
- %System32%\alg.exe
- %System32%\dllhost.exe
- %System32%\fxssvc.exe
- %System32%\ieetwcollector.exe
- %System32%\msdtc.exe
- %System32%\msiexec.exe
- %System32%\snmptrap.exe
- %System32%\sppsvc.exe
- %System32%\ui0detect.exe
- %System32%\vds.exe
- %System32%\vssvc.exe
- %System32%\wbem\wmiApsrv.exe
- %System32%\wbengine.exe
- %CommonProgramFiles%\Microsoft Shared\ink\mip.exe
- %System32%\FXSSVC.exe
- %System32%\UI0Detect.exe
- %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngen_service.lock
- %SystemRoot%\Microsoft.NET\Framework\v2.0.50727\ngenservicelock.dat
- %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenrootstorelock.dat
- %SystemRoot%\Microsoft.NET\Framework\v4.0.30319\ngenservicelock.dat
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.exe
- %ProgramFiles%\Internet Explorer\ielowutil.exe
- %SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{33EC2C09-9668-4DE7-BCC0-EFC69D7355D7}.crmlog
- %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\ngenservicelock.dat
- %ProgramFiles%\Internet Explorer\iexplore.exe
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.vir
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.vir
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.vir
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.vir
- %CommonProgramFiles%\Microsoft Shared\OFFICE14\MSOXMLED.vir
- %CommonProgramFiles%\Microsoft Shared\VSTO\10.0\VSTOInstaller.vir
- %CommonProgramFiles%\Microsoft Shared\ink\ConvertInkStore.vir
- %CommonProgramFiles%\Microsoft Shared\ink\ShapeCollector.vir
- %ProgramFiles%\DVD Maker\DVDMaker.vir
- %ProgramFiles%\Internet Explorer\ieinstal.vir
- %ProgramFiles%\Internet Explorer\ielowutil.vir
- %ProgramFiles%\Internet Explorer\iexplore.vir
- %ProgramFiles%\Java\jre6\bin\java.vir
- %ProgramFiles%\Java\jre6\bin\javaw.vir
- %ProgramFiles%\Java\jre6\bin\javaws.vir
- %ProgramFiles%\Java\jre6\bin\unpack200.vir
- %ProgramFiles%\Java\jre7\bin\jabswitch.vir
- %ProgramFiles%\Java\jre7\bin\java.vir
- %ProgramFiles%\Java\jre7\bin\javacpl.vir
- %ProgramFiles%\Java\jre7\bin\javaw.vir
- %ProgramFiles%\Java\jre7\bin\javaws.vir
- %ProgramFiles%\Java\jre7\bin\jp2launcher.vir
- %ProgramFiles%\Java\jre7\bin\ssvagent.vir
- %ProgramFiles%\Java\jre7\bin\unpack200.vir
- %CommonProgramFiles(x86)%\microsoft shared\source engine\ose.vir
- %ProgramFiles(x86)%\microsoft office\office14\groove.vir
- %ProgramFiles(x86)%\mozilla maintenance service\maintenanceservice.vir
- %SystemRoot%\ehome\ehsched.vir
- %SystemRoot%\microsoft.net\framework64\v2.0.50727\mscorsvw.vir
- %SystemRoot%\microsoft.net\framework\v2.0.50727\mscorsvw.vir
- %SystemRoot%\microsoft.net\framework\v4.0.30319\mscorsvw.vir
- %System32%\alg.vir
- %System32%\dllhost.vir
- %System32%\fxssvc.vir
- %System32%\ieetwcollector.vir
- %System32%\msiexec.vir
- %System32%\snmptrap.vir
- %System32%\ui0detect.vir
- %System32%\vds.vir
- %System32%\vssvc.vir
- %System32%\wbem\wmiApsrv.vir
- %System32%\wbengine.vir
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.vir
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\dwtrig20.vir
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\ose.vir
- \MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\setup.vir
- %CommonProgramFiles%\Microsoft Shared\OfficeSoftwareProtectionPlatform\osppsvc.vir
- %CommonProgramFiles%\Microsoft Shared\ink\TabTip.vir
- %CommonProgramFiles%\Microsoft Shared\ink\mip.vir
- %SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.vir
- %System32%\msdtc.vir
- %System32%\msiexec.vir
- %System32%\sppsvc.vir
- %SystemRoot%\Registration\{02D4B3F1-FD88-11D1-960D-00805FC79235}.{C0F5CDA5-94A5-411C-9D50-E0AEC7EA25A6}.crmlog
- %APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\29a1f50d-6e60-4de9-b56c-1a6439e5baa1 File Hashes
- 57d65c0c068da7ec72e8c9ba0c6f9a354917bae5127f55de1635a6d5d471d60b
- 6e16f59631c0382f8902123e8f021656235724d3b76ec33913dcd813f567df4e
- a9a42f7c8d67d59137bcdb813ff2c92277fcf778599e349062be332960b91c62
- ad6d8581a541cc8622b132e171627324d8e02c4ba2a3804e0f6763d336207a01
- ad73a287c879b1ac9605f5889064373e95f3db526e98c3349a48d63c549c23c2
- b0aa80111d23dd578815c935aa529f30a5f10b38e6ef799a402f7819bb077d89
- b21649f76ec9cce8d3937f512c8d9a841979d1b90cb3f24ca2eb1a0d97c615f0
- b9e9f61ba07393c6da51ea20c3764b0088f0fc9cfc6be99d355fe1f5aec82f8f
- ba649d6fbcade5b73b2a761f4d40702c2a21195fed22285213959abebd818833
- c11d1f5a9c5056c439ddfef99150dd0a817c728c73dbcee9d80956389164b9d0
- c56268667843181e7aad8cb849496a530be0a7916cfda65e34942bb8e0b909bd
- c7f0f4fde7c85f456e95bfdbe2a5ab25f07a8e749c11e62b8be2e56587d9ebaf
- c9785ee70ca68ac41cb78fd83e37fc33837c10d3d82ad2188b2554ef14c2a345
- cc7f00cab330786e2de92e1fb3b36baed5868da2f66744d9d058072e9b5587b9
- d7d5248e70e3ebfd772783ef78f22d7843596fda42231659373827504ce9ca2b
- dc78031890299fa4a8ee415a90ed95a79dc060a2a55342d7d60da8c468bf5288
- dd198d756ce002a3eab75e4faedb6e48cfd27032ad4e9f4643f454b613b616dc
- ee3c63c6c9d0c5887b22a820d1b97b44ec97ee212f819d9ad478a6846e6a5f87
- faab282b345611411cbe53e35c94f2c56c9314bb4211a20ebfb6b17d85366cf4
- fac8e1f9ef6b06eff6e7ec4a5c088644f21f82882daf674e27e699fa9563357b
- ffb30a4ba399b607cb0b72fc67353a75609c28f66c73d41cc5f13fecc8f400c1
Coverage

Screenshots of Detection AMP
ThreatGrid
Win.Trojan.Winwebsec-6918829-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value Name: LanguageList
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value Name: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value Name: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value Name: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value Name: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: AutoDetect
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
- <HKCU>\Software
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: AntiVirusOverride
- <HKLM>\SOFTWARE\WOW6432NODE\Microsoft
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- <HKLM>\SYSTEM\CONTROLSET001\ENUM\WPDBUSENUMROOT\UMB\2&37C186B&0&STORAGE#VOLUME#_??_USBSTOR#DISK&VEN_GENERIC&PROD_HARDDISK&REV_2.5+#1-0000:00:1D.7-2&0#
- Value Name: CustomPropertyHwIdKey
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\svc
- <HKLM>\System\CurrentControlSet\Services\luafv
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\UNINSTALL\Live Security Platinum
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SYSTEMRESTORE
- Value Name: RPSessionInterval
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\LUAFV
- Value Name: Start
- <HKU>\Software\Microsoft\Windows\CurrentVersion\RunOnce Mutexes
- Local\ZonesCacheCounterMutex
- Local\ZonesLockedCacheCounterMutex
- Local\MSCTF.Asm.MutexDefault1
- DBWinMutex
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_1024.db!dfMaintainer
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_256.db!dfMaintainer
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_32.db!dfMaintainer
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_96.db!dfMaintainer
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!ThumbnailCacheInit
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!rwReaderRefs
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_idx.db!rwWriterMutex
- Global\C::Users:Administrator:AppData:Local:Microsoft:Windows:Explorer:thumbcache_sr.db!dfMaintainer
- 539D542E222D2DDE0101049AB5EC2432
- ..MTX
- 529C532D212C2CDD00000399B4EB2331
- 56A05731253030E10404079DB8EF2735
- 57A15832263131E20505089EB9F02836
- 5AA45B35293434E508080BA1BCF32B39
- \BaseNamedObjects\5B4FD7CC222D2DDE0101F14FD252FD4F
- \BaseNamedObjects\5A4ED6CB212C2CDD0000F04ED151FC4E IP Addresses contacted by malware. Does not indicate maliciousness
- 116[.]255[.]235[.]9 Domain Names contacted by malware. Does not indicate maliciousness
- www[.]w3[.]org Files and or directories created
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Live Security Platinum
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Live Security Platinum\Live Security Platinum.lnk
- %HOMEPATH%\Desktop\Live Security Platinum.lnk
- %ProgramData%\529C532D212C2CDD00000399B4EB2331
- %ProgramData%\529C532D212C2CDD00000399B4EB2331\529C532D212C2CDD00000399B4EB2331.exe
- %ProgramData%\529C532D212C2CDD00000399B4EB2331\529C532D212C2CDD00000399B4EB2331
- %ProgramData%\5A4ED6CB212C2CDD0000F04ED151FC4E\5A4ED6CB212C2CDD0000F04ED151FC4E
- %ProgramData%\5A4ED6CB212C2CDD0000F04ED151FC4E\5A4ED6CB212C2CDD0000F04ED151FC4E.exe File Hashes
- 04311b0a06d95014390434149f1dae9f1c8e399e678fe80903d515501b4ac04a
- 0ee9b85dd0d097210d138ac73b5687d8de17e4880131360a258295b0ece85006
- 35512788e3ec6bf939840d6ac94191b7976b4309bb26bf91eb00b461beb29ad3
- 420a929f0ce0a6194d82a41b1674f2e2fbc78278c0723c37a2bcd038aa997301
- 4ce41686ffaea1f9c80d2bbe00bbbe0a1da864a038a0a48066f209bbc98cb969
- 520eefe6fde2fe435b885080259ae7357c291de05c7d3df8ae69095e48a1ca1d
- 73208a63a25abaec555e1621f991b167ccd40eac8b06d330fd2642d157d028d1
- 7340137319da76ae915a176658a9f577847aac97908d2ab1edaa289c092f8954
- b34930cdd050eb0968301ec594091dd714f516547bc41f37390031655f282577
- b7192f768a639280169016309758dd5e4d5be76a96850b7eab52c25198ecdafa
- e639df0b0afa8a5fafd40064339d75b7098de98068ed9b9d1e20da9e3649d25e
Coverage

Screenshots of Detection AMP
ThreatGrid
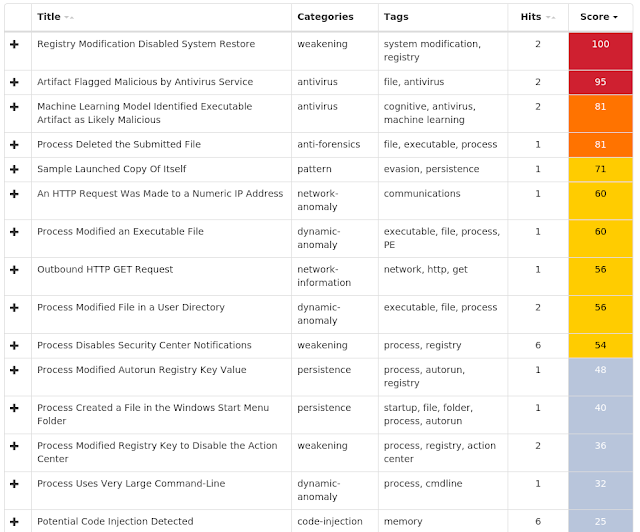
Win.Trojan.Emotet-6918815-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value Name: Collection
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS
- Value Name: DhcpScopeID
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value Name: LanguageList
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value Name: PnpInstanceID
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE\IndexTable
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE
- Value Name: _CurrentObjectId_
- <A>\{32DE27EC-AB30-11E8-A007-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST
- Value Name: CurrentLru
- <HKU>\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
- Value Name: Type
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\5A-54-99-D2-86-6F
- Value Name: WpadDecisionReason
- <HKLM>\SOFTWARE\Microsoft\ESENT\Process\guiddefribbon\DEBUG Mutexes
- Global\I98B68E3C
- Global\M98B68E3C
- \BaseNamedObjects\Global\M3C28B0E4
- \BaseNamedObjects\Global\I3C28B0E4 IP Addresses contacted by malware. Does not indicate maliciousness
- 212[.]227[.]15[.]158
- 72[.]167[.]238[.]29
- 216[.]40[.]42[.]5
- 74[.]208[.]5[.]5
- 74[.]208[.]5[.]15
- 196[.]25[.]211[.]150
- 97[.]74[.]135[.]10
- 173[.]201[.]192[.]158
- 67[.]195[.]228[.]95
- 192[.]211[.]51[.]147
- 74[.]6[.]141[.]43
- 74[.]202[.]142[.]72
- 184[.]106[.]54[.]10
- 173[.]201[.]193[.]101
- 196[.]11[.]146[.]149
- 193[.]252[.]22[.]84
- 64[.]98[.]36[.]5
- 74[.]6[.]137[.]75
- 173[.]194[.]204[.]108
- 64[.]90[.]62[.]162
- 107[.]6[.]16[.]19
- 208[.]84[.]244[.]49
- 69[.]168[.]106[.]36
- 74[.]208[.]5[.]13
- 107[.]14[.]166[.]78
- 173[.]201[.]192[.]101
- 212[.]227[.]15[.]138
- 40[.]97[.]124[.]18
- 107[.]14[.]166[.]72
- 65[.]254[.]228[.]100
- 74[.]202[.]142[.]71
- 190[.]95[.]221[.]182
- 200[.]58[.]118[.]149
- 190[.]226[.]40[.]3
- 200[.]24[.]13[.]80
- 18[.]211[.]9[.]206
- 64[.]250[.]117[.]68
- 200[.]45[.]191[.]16
- 69[.]156[.]240[.]33
- 64[.]59[.]136[.]142
- 89[.]19[.]2[.]235
- 192[.]185[.]4[.]138
- 64[.]85[.]73[.]16
- 200[.]50[.]175[.]25
- 200[.]40[.]31[.]18
- 209[.]249[.]170[.]98
- 65[.]182[.]102[.]90
- 200[.]58[.]113[.]90
- 173[.]203[.]187[.]187
- 52[.]96[.]38[.]82
- 31[.]172[.]86[.]183
- 186[.]64[.]119[.]135
- 192[.]185[.]16[.]118
- 50[.]87[.]144[.]197
- 190[.]96[.]118[.]53
- 67[.]241[.]81[.]253
- 154[.]0[.]163[.]40
- 174[.]136[.]30[.]150
- 190[.]15[.]222[.]14
- 200[.]58[.]110[.]122
- 205[.]204[.]67[.]142
- 158[.]69[.]99[.]42
- 162[.]144[.]71[.]101
- 74[.]205[.]78[.]113
- 121[.]78[.]246[.]33
- 200[.]58[.]123[.]107
- 201[.]220[.]211[.]7
- 173[.]0[.]129[.]16
- 190[.]224[.]160[.]116
- 200[.]107[.]202[.]6
- 188[.]165[.]208[.]226
- 66[.]96[.]134[.]1
- 103[.]15[.]48[.]91
- 50[.]23[.]248[.]182
- 179[.]60[.]208[.]2
- 192[.]185[.]107[.]140
- 192[.]185[.]90[.]238
- 108[.]179[.]234[.]88
- 162[.]241[.]2[.]35
- 192[.]185[.]185[.]176
- 108[.]167[.]189[.]42
- 108[.]167[.]160[.]249
- 59[.]124[.]1[.]19
- 192[.]185[.]184[.]94
- 192[.]185[.]26[.]156
- 108[.]167[.]181[.]188
- 192[.]185[.]2[.]182
- 98[.]136[.]96[.]84
- 207[.]249[.]74[.]109
- 83[.]170[.]124[.]82
- 159[.]203[.]163[.]219
- 184[.]150[.]200[.]201
- 50[.]87[.]150[.]177
- 190[.]107[.]22[.]116
- 66[.]195[.]202[.]115
- 69[.]16[.]228[.]14
- 66[.]96[.]147[.]110
- 190[.]124[.]215[.]2
- 50[.]87[.]59[.]65
- 187[.]157[.]85[.]132
- 200[.]119[.]246[.]201
- 96[.]116[.]224[.]179
- 69[.]175[.]31[.]212
- 188[.]121[.]52[.]82
- 200[.]58[.]110[.]40
- 69[.]61[.]0[.]198
- 50[.]62[.]176[.]244
- 104[.]236[.]244[.]101
- 67[.]222[.]2[.]148
- 14[.]49[.]39[.]215
- 192[.]185[.]37[.]19
- 162[.]217[.]70[.]59
- 192[.]185[.]190[.]90
- 192[.]185[.]136[.]209
- 192[.]185[.]76[.]191
- 192[.]185[.]129[.]8
- 192[.]254[.]185[.]112
- 192[.]185[.]4[.]23
- 66[.]96[.]147[.]103
- 108[.]163[.]221[.]2
- 190[.]11[.]243[.]146
- 66[.]71[.]241[.]102
- 212[.]83[.]168[.]160
- 62[.]210[.]127[.]136
- 50[.]62[.]176[.]42
- 64[.]26[.]60[.]221
- 67[.]225[.]221[.]173
- 67[.]241[.]81[.]253
- 190[.]96[.]118[.]53 Domain Names contacted by malware. Does not indicate maliciousness
- imap[.]1and1[.]co[.]uk
- mail[.]gmail[.]com
- imap[.]gmail[.]com
- smtp[.]secureserver[.]net
- pop[.]1and1[.]com
- smtp[.]1and1[.]es
- MAIL[.]GMAIL[.]COM
- mail[.]1and1[.]co[.]uk
- smtp[.]live[.]com
- smtp[.]mail[.]com
- pop[.]secureserver[.]net
- mail[.]secureserver[.]net
- pop3[.]telkomsa[.]net
- imap[.]secureserver[.]net
- secure[.]emailsrvr[.]com
- mail[.]multisistemas[.]com[.]mx
- pop[.]infinitummail[.]com
- smtp[.]mail[.]yahoo[.]com
- smtp[.]telkomsa[.]net
- outlook[.]office365[.]com
- smtpout[.]secureserver[.]net
- imap[.]comcast[.]net
- smtp[.]vodamail[.]co[.]za
- smtp[.]orange[.]fr
- imap[.]mail[.]com
- mail[.]biz[.]rr[.]com
- pop[.]biz[.]rr[.]com
- correoweb[.]iess[.]gob[.]ec
- smtp[.]roadrunner[.]com
- mail[.]basculasmagnino[.]com[.]ar
- smtp[.]infinitummail[.]com
- smtp[.]windstream[.]net
- smtp[.]shaw[.]ca
- correo[.]movistarcloud[.]com[.]ve
- smtp[.]arnet[.]com[.]ar
- pop[.]broadband[.]rogers[.]com
- pop[.]hostcentric[.]com
- smtp[.]arnetbiz[.]com[.]ar
- smtp[.]broadband[.]rogers[.]com
- gator4126[.]hostgator[.]com
- mail[.]dotster[.]com
- adinet[.]com[.]uy
- mail[.]mi[.]com[.]co
- imap[.]bell[.]net
- pop[.]everyone[.]net
- mail[.]chikool[.]cl
- smtp[.]mailplug[.]co[.]kr
- royalmabati[.]com
- mail[.]infovia[.]com[.]ar
- mail[.]pomonatowing[.]co[.]za
- mail[.]tmmchealthcare[.]com
- mail[.]interdns[.]co[.]uk
- mail[.]hazari[.]com[.]pk
- smtp[.]tesapparel[.]com
- mail[.]empresasjayir[.]cl
- mail[.]serbanc[.]cl
- mail[.]shineaccesorios[.]com[.]ar
- mail[.]teambuildingempresarial[.]com
- smtp[.]berabevudigital[.]com[.]ar
- mail[.]conduto[.]com
- gator4216[.]hostgator[.]com
- smtp[.]terra[.]com[.]mx
- webmail[.]carbonesdesantander[.]com
- smtp[.]mail[.]yahoo[.]com[.]ar
- correo2[.]redynet[.]com[.]ar
- mail[.]freightlineroftoledo[.]com
- mail[.]ebmworld[.]cu
- smtp[.]dreamhost[.]com
- p3plcpnl0728[.]prod[.]phx3[.]secureserver[.]net
- mail[.]oxigenoshoes[.]com[.]ar
- newmaq[.]com[.]bo
- sintcom[.]com[.]mx
- mail[.]inttegrain[.]com[.]mx
- email8[.]luxsci[.]com
- pop[.]itcsa[.]net
- mail[.]grupodemejoracontinua[.]com[.]mx
- mail[.]dtpressnorte[.]com[.]ar
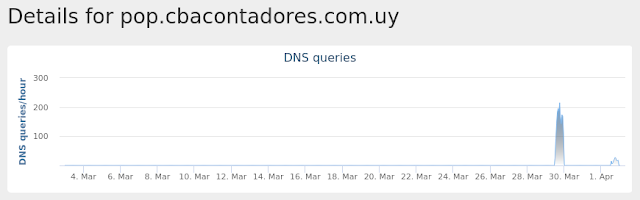
- pop[.]cbacontadores[.]com[.]uy
- gator4012[.]hostgator[.]com
- mail[.]ahesan[.]com[.]mx
- mail2[.]isysa[.]com[.]mx
- mail[.]peltier[.]net
- pop[.]moorwaymanagement[.]com
- mail[.]ykkip[.]com
- mail[.]refridcol[.]com
- mail[.]digosaautopartes[.]com[.]mx
- mail[.]merzey[.]com
- pop[.]icon1[.]ca
- mail[.]cablenettv[.]com[.]ar
- mail[.]petrovalle[.]com[.]ar
- md-ht-2[.]webhostbox[.]net
- iceschool[.]com[.]pe
- imap[.]europe[.]secureserver[.]net
- mail[.]hblseguros[.]com[.]co
- mail[.]bell[.]net
- mail[.]listo[.]com[.]co
- pop[.]mcargo[.]net
- mail[.]heyas[.]com[.]ar
- mail[.]sedicomsa[.]com
- filter1[.]nsbasicmail[.]com
- mail[.]iphsa[.]com[.]mx
- mail[.]seproacr[.]com
- pop[.]startlogic[.]com
- cowealth[.]com[.]tw
- mailbox[.]carrossierprocolor[.]com
- mail[.]enviro5[.]com
- grupomycasa[.]com
- mail[.]cssialtda[.]com
- mail[.]diligroup[.]com
- mail[.]salon53[.]mx
- imap[.]tiendasenforma[.]com
- pop3[.]sld[.]cu
- smtp[.]ipv4networks[.]net
- mail[.]navarac[.]com
- gator3161[.]hostgator[.]com
- mail[.]ramasa[.]com[.]mx
- mail[.]tradequimsa[.]com
- pop[.]premium-soft[.]com
- mail[.]comodoro[.]coop
- mail[.]distribuidoralamaro[.]com
- mail[.]gaiasrl[.]com[.]ar
- server1[.]cosefa[.]com[.]ar
- lamallorquina[.]com[.]uy
- mail[.]dycindustrial[.]cl
- mail[.]ibs[.]mx
- MAIL[.]BELL[.]NET
- mail[.]kinderland[.]com[.]ar
- mail[.]metropolitainerefrigeration[.]com
- frbb[.]utn[.]edu[.]ar
- mail[.]manchesterdental[.]co[.]uk
- p3plcpnl0515[.]prod[.]phx3[.]secureserver[.]net
- mail[.]lodis[.]cl
- mail[.]lionquick[.]com
- eclipse[.]websitewelcome[.]com Files and or directories created
- %SystemRoot%\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
- %SystemRoot%\SysWOW64\kyGqvfpU.exe File Hashes
- 02a0a4800d92ba59432af6e47480ede2769bd53d7af7840ce9a8ee7097ae0003
- 079dd41f7437110d28bbd3c0f6bacb2f0cd1b23cb899772e8c380124be044fac
- 09ad52e3866b1cd1629f5206c38d968ed82977026dfa79f3f9313625fce9298c
- 16969a648499623f5b6d61785673c445035bcfa90d4303b88b922d76e6d95728
- 1ab5e8be2711179c75581141bdaacf4b1fbc1806806d73e53b94e2286e150569
- 2ca9efb4e856be7af3bbaa2c22108ab30a0aa30203b5accdd2787f4d4bda0315
- 337af19fb5a1403b332b77a5c6958387ba9150d225d32c6474d5807fb5e9c21c
- 43e226bd92a81a17a2f73a0e9f2f0ea7dee5c7756a4a6d476483cdf456024fdf
- 49116b29290b3878908d64fc78d1fc92c21f9add774c8a3b2e55e8763f8a8267
- 503c9111d0fc0efb4a3290c977dd8f0f6cf4925de69bf644fbbdf03857ca1776
- 521c964fe97018ae915a3762dbf31a2397f7c283a494f19671354d5a179dcf3a
- 524622e92156fb4e155e18f820b2897f60b49b2e0533ed449ab99642b16ef887
- 52f83952d33df5dea2440d6a0211c004a41b6543f64edc6b9428c2b55897d45b
- 53523d8333a3e913bb53523269c22af0e38d26bae9f637f2617acef7dabab06e
- 5353758894e7cfaee0376ac38e76a1c366b1d0ea19911affdd23f2cbdc12d020
- 53c708d13bb6526de05446fdef04d9d9f183f825596c89cc92d8e7aced3acbd0
- 53d075b5be564101c888a82187527845404a2df42e7ae774937f9630da98fc3a
- 559028389697aa6b223920c69441d68dddf5c1d46d7be8b3fb0d23af183d477c
- 5844365b389ab2865c1c032561da07954e1b8312a61fe612672d7c11aca908c9
- 5971aaaa42335a059f017e6586776f5b5de40590b4e68dfca8124811e372300e
- 64cffcac96694cf3ffce2b7ff2962176f0fea267093ea4970d2aac3d53038fea
- 67f41f532423939b59a2f0b890028ec7b9de5ec71b7e8bd0a8aee7906101174b
- 689685a2edd6b0cabc8ca0fcbcf39e53e4da57d65dfe0e2658964dfb8cca39dd
- 6cfc0383c421992c8d4e0f8a9a13e705e67b1735ad71520eacc1351c9e8cdc14
- 78a0a5844a1ca119d94bcaea5ac5b8e256f2711b76eaccdffd0089c18f079e2d
Coverage

Screenshots of Detection AMP
ThreatGrid
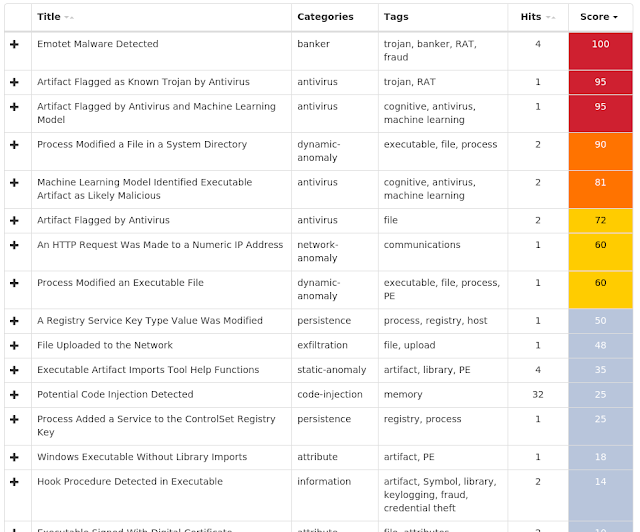
Umbrella