Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Sept. 6 and Sept. 13. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
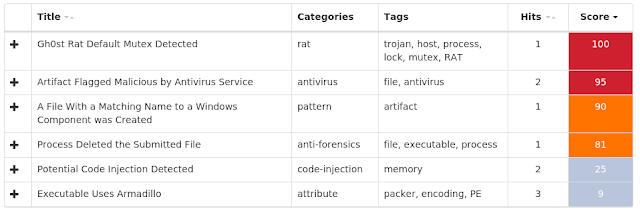
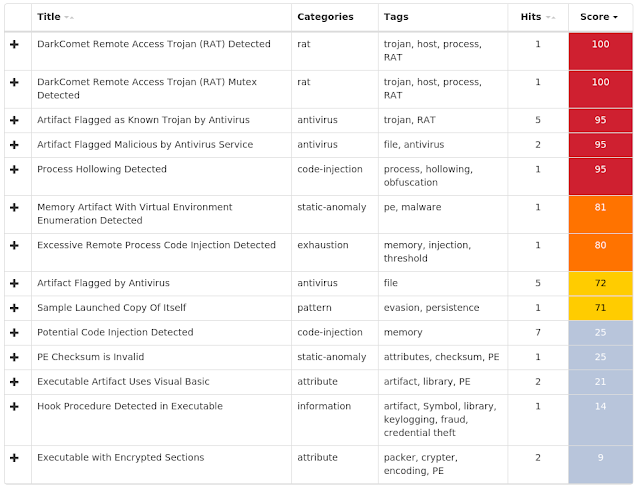
Threat Name Type Description Win.Dropper.Gh0stRAT-7155936-0
Dropper
Gh0stRAT is a well-known family of remote access trojans designed to provide an attacker with complete control over an infected system. Capabilities include monitoring keystrokes, collecting video footage from the webcam, and uploading/executing follow-on malware. The source code for Gh0stRAT has been publicly available on the Internet for years, significantly lowering the barrier for actors to modify and reuse the code in new attacks.
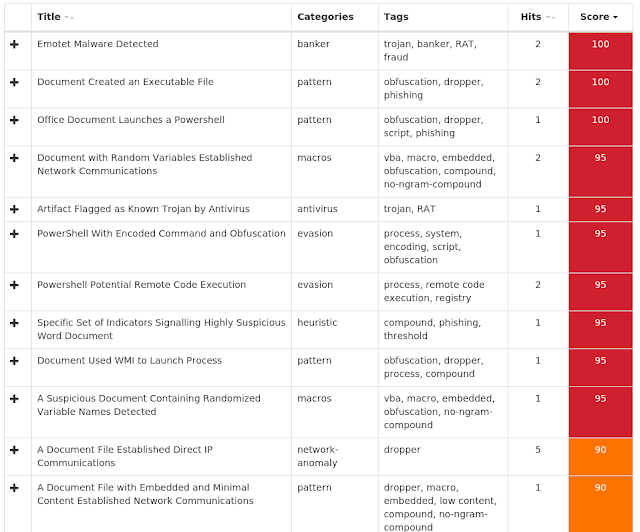
Doc.Downloader.Emotet-7155084-0
Downloader
Emotet is a banking trojan that remains relevant due to its ability to evolve and bypass antivirus products. It is commonly spread via malicious email attachments and links.
Win.Dropper.DarkComet-7154925-1
Dropper
DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
Win.Virus.Expiro-7153559-0
Virus
Expiro is a known file infector and information stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Ransomware.Shade-7158472-0
Ransomware
Shade, also known as Troldesh, is a ransomware family typically spread via malicious email attachments.
Win.Packed.Tofsee-7150793-1
Packed
Tofsee is multipurpose malware that features a number of modules used to carry out various activities, such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator’s control.
Threat Breakdown Win.Dropper.Gh0stRAT-7155936-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\BITS
Value Name: Version
24
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BITS
Value Name: Group
24
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Lostlove_K
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DEFGHI KLMNOPQR TUV
Value Name: Description
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DEFGHI KLMNOPQR TUV
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DEFGHI KLMNOPQR TUV
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DEFGHI KLMNOPQR TUV
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DEFGHI KLMNOPQR TUV
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\DEFGHI KLMNOPQR TUV
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: Description
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: ImagePath
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: DisplayName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: WOW64
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IJKLMN PQRSTUVW YAB
Value Name: ObjectName
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
Value Name: Description
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
Value Name: Type
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
Value Name: Start
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
Value Name: ErrorControl
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
Value Name: ImagePath
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ABCDEF H QRS
Value Name: DisplayName
1
Mutexes Occurrences 127.0.0.1
6
Global\f75b8341-d3d4-11e9-a007-00501e3ae7b5
4
k.ru9999.cc
3
45.114.11.137
2
www.ddostmd.com
2
www.3rbb.com
2
116.31.125.147
1
www.baidu.com
1
www.hkdcr.com
1
xiaoyuer3001.f3322.net
1
222.186.30.211
1
192.168.1.107
1
mm.zhangfanfan.com
1
shenxian2016.f3322.net
1
admin860129.f3322.net
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 45[.]114[.]11[.]137
2
154[.]210[.]146[.]138
2
116[.]31[.]125[.]147
1
61[.]147[.]103[.]67
1
222[.]186[.]30[.]211
1
23[.]238[.]148[.]74
1
221[.]217[.]66[.]122
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences k[.]ru9999[.]cc
3
www[.]3rbb[.]com
2
WWW[.]DDOSTMD[.]COM
2
WWW[.]HKDCR[.]COM
1
xiaoyuer3001[.]f3322[.]net
1
mm[.]zhangfanfan[.]com
1
shenxian2016[.]f3322[.]net
1
admin860129[.]f3322[.]net
1
Files and or directories created Occurrences %ProgramFiles%\svchost.exe
4
File Hashes 121441b204dbf7a02c8f4357452c99592ab9bdeb676089ccf1f24071f740251b
130abeb252c2a663ae691271f5d154722468d1b1b2ed23ef89d4fb9290fe081b
1326c0b36ad655c1653ce78e98204260ec8b9bddefa3cd8d2c620fab88b1a83c
25effefec15971bbe5714e37fd1f0e0e33298c691b61d04ed3af1b1359731a2b
287fcc0ae4a50e34215cfd084570d7b94ab4a3786b7260ad0b1167d1baa1a8b0
29a7a1457008f729066e21c378ea7c402fac80aa64619631565fb95a4d137652
2eb388113d650745686345acf88d32a44975e00764034875bd990aa5a80119ca
2f6d822e2ebeb0f94368b55c7c94a4f8a8b73b32214fe1f3fc5277da52411bf9
332a58814dc69a08873cc8bcbf3f8b8999dd2e7ea60ad47b635a7f735e3e85a5
47bac35158a06f748621847c0de60eab92db067f0cb95f798f0b342f508f1360
4805d4e36186da1bca0b0debf28a36ff772885f0b438d3924059ef3b9531b2ca
4de97329b8242136094b16a705fa15d3a4fe918d68b1f4f698b58ba1bcb16706
4ec20ea729ca18bed34a0dbcd2b65f049d0926ab9f94a5470bb24e600e771281
592ebcaa26bacc775420398933a0a9d63acdaa604f85805a3a3196d5a1a798ee
5f2336bb4321161e7115e63d08db836ef28be2df0cad4db9e6ce45ad3830c560
5f469e2248ae56e1077c2c87a1a15c2414352a94786845d3b65447d3ee23694d
626d4dc26ff7ec588635ad32e71fabeb8ad96887d24498ffa08a031e1e6a6bee
66db565cad627dde60e4f396ef1712f06d7b911670189ab21b870ecaada99531
681539e7da26b1130fdb65c581f5146067a51c3a42849874d6f7aa189209a754
682cf9935d0d19815becc05f3f1ed6931396f25ccf95b6deedf70a4ba94ba031
70d32abf71be74690a04ebfe9713e2287106964e46069612f37f4b0822dd8169
7b32dce1d5818551afd3efdbc3ba540c47b37942d12254fc26f16b5e3f50b96e
81f4af297381141ed4990b4837b0fb60385f29405b04df3a55d8953237aa1182
84df0240ad79f34c7172b8262ec0898e794d2448e43b1e0a577704c0b8ef40e5
8ec17725347ae019a5d5d00345ba283483797e8477bd23e98f59d8c6f3d37811*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Doc.Downloader.Emotet-7155084-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\AUTHROOT\CERTIFICATES\DAC9024F54D8F6DF94935FB1732638CA6AD77C13
Value Name: Blob
14
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]185[.]157[.]191
14
152[.]160[.]245[.]7
14
104[.]27[.]137[.]48
12
104[.]27[.]136[.]48
12
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]w[.]org
14
www[.]testrent[.]com
14
lackify[.]com
14
www[.]loris[.]al
14
financialdiscourse[.]com
14
fiberoptictestrentals[.]net
14
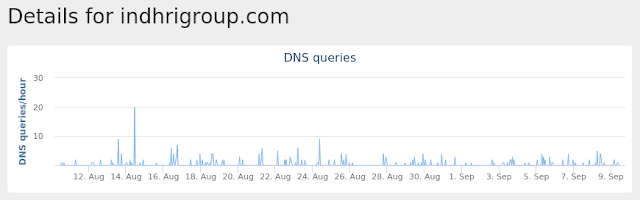
INDHRIGROUP[.]COM
14
loris[.]al
14
testrent[.]com
14
Files and or directories created Occurrences %LOCALAPPDATA%\Microsoft\Schemas\MS Word_restart.xml
14
%HOMEPATH%\490.exe
14
File Hashes 1157bbcfa2438b4142bc1dc163952714ef2e084cd27698f5c2f78193367f8033
3eaba85e842d0ed0489d430cb1bc37d1fca702845ba478a0e290115bebfd8827
64732ab1f700b865a24a0fe06e94a54a40724568af5381afd126096b59f18606
8ef79e33fc1ebf640f78cebe13485489f85caf08fbf4cee696aadb977f21d6e7
96ab8b7fc0b45cf2fc1277ad938ad4aabb1bcc157f0259e456b76f1684e4896e
c177de169b84382b1809efd361d8e5a6ee6eff262f479724856686d03c6bb6db
c707b20c85d03595b74a56768d69786c33076030059260a6684df7ac7b3a9562
cd75eda017abff329abfa5162be02c8042c86730dd948a6b423d3ebce5f5e3b8
e09474de88f323075c3ef4ba54c458e3275ee102b72a2bfc4894e79a9703c542
e192e2125ef244cff6787b3cba927d3e047fbd5d54dffd66d885a8c1789f2cde
e79e52b33e81b6d039817aa3cf87726db6de496fcb36477f29483a5730dd2874
f256396752c6a4164b4097d493b202de43fb8f8d7bba372dcd7ba45ba3edfd16
f54ad758e4ee395a12956b665b611ad69b622e672d9f4086e8754f4b301cfb04
f679763abeea019bdfdc22e23d9be3159ca1f325453f34e94954bee50176664cCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Win.Dropper.DarkComet-7154925-1 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC
5
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: UserInit
4
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MicroUpdate
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: Policies
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: Policies
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableTaskMgr
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
1
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: DisableRegistryTools
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{1Q4U2W04-714Q-L506-NR3K-B4MJ85W6X717}
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{1Q4U2W04-714Q-L506-NR3K-B4MJ85W6X717}
Value Name: StubPath
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{7F0I7VXB-063R-XLLO-731N-3EGO8NDEDVOR}
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{7F0I7VXB-063R-XLLO-731N-3EGO8NDEDVOR}
Value Name: StubPath
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{6C5V5081-L886-C7EB-2J6N-054ATGC34D64}
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{6C5V5081-L886-C7EB-2J6N-054ATGC34D64}
Value Name: StubPath
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: System
1
<HKCU>\SOFTWARE\TGB61
1
<HKCU>\SOFTWARE\TGB61
Value Name: FirstExecution
1
<HKCU>\SOFTWARE\TGB61
Value Name: NewIdentification
1
Mutexes Occurrences DC_MUTEX-F3XDA2D
5
_x_X_BLOCKMOUSE_X_x_
4
_x_X_PASSWORDLIST_X_x_
4
_x_X_UPDATE_X_x_
4
DCPERSFWBP
3
***MUTEX***
2
***MUTEX***_SAIR
2
054ATGC34D64
1
\BaseNamedObjects\054ATGC34D64_SAIR
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 193[.]161[.]193[.]99
2
92[.]44[.]166[.]32
1
81[.]214[.]120[.]214
1
88[.]229[.]213[.]118
1
176[.]219[.]165[.]9
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences hackroot00[.]ddns[.]net
1
berkeaksoy-45595[.]portmap[.]host
1
metin2ci[.]duckdns[.]org
1
toxicwithahmet[.]duckdns[.]org
1
denememusareis[.]duckdns[.]org
1
blackhamdsnh[.]duckdns[.]org
1
bluejeans067-51471[.]portmap[.]io
1
Files and or directories created Occurrences %APPDATA%\dclogs
5
%TEMP%\XX--XX--XX.txt
3
%TEMP%\UuU.uUu
3
%TEMP%\XxX.xXx
3
%APPDATA%\logs.dat
3
%HOMEPATH%\Documents\MSDCSC
2
%HOMEPATH%\Documents\MSDCSC\msdcsc.exe
2
%System32%\MSDCSC\msdcsc.exe
1
%SystemRoot%\SysWOW64\MSDCSC
1
%ProgramData%\Microsoft\Windows\Start Menu\MSDCSC
1
%ProgramData%\Microsoft\Windows\Start Menu\MSDCSC\msdcsc.exe
1
\dir
1
\dir\install
1
\dir\install\install
1
\dir\install\install\server.exe
1
%SystemRoot%\SysWOW64\install
1
%SystemRoot%\SysWOW64\install\server.exe
1
%SystemRoot%\SysWOW64\MSDCSC\msdcsc.exe
1
%HOMEPATH%
1
%HOMEPATH%\Desktop
1
%HOMEPATH%\Desktop\Yeni klasör
1
%HOMEPATH%\Desktop\Yeni klasör\install
1
%HOMEPATH%\Desktop\Yeni klasör\install\server.exe
1
%TEMP%\YOUS2.DCP
1
%TEMP%\SDQWEQ.EXE
1
*See JSON for more IOCs
File Hashes 08c0ff2a95d50cd94b1f5f58b3af99091d27490f949c0d3c68dbc81dec5f9171
190b08b1337d404696b0c91f0442d31149080c97b7a6fe13cf879b1a4ead4c94
3f74c0ebf0701b6726ddb4fdc6ddb15610d0075691b02e9615c50e095359b6c2
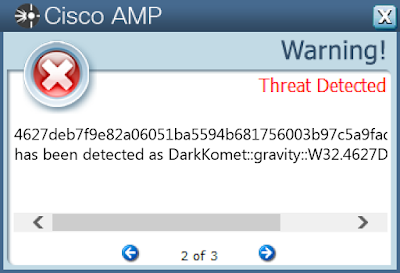
4627deb7f9e82a06051ba5594b681756003b97c5a9fadec91ec4af3d9ac9ed72
54ade3e9aa6cc71cb769eb69a65110f5fa5cdac93cbf20b82609b996bfaf76ca
611d5155f8e505c20f5d1e2bb70b37b84d7de3458577d89cc32dc12f0351ec95
988e7312821405d692b5b5846be7ede45f0d8bd23c914385a737efa0400f2bad
9cb46d011f79a6db1c6baef5b9cae3020166a515dff284fcd6ea2fb51da1cf1d
a5f9af2d94dd64d9c05e56d9560c386081823a69823d8609501f1506ab5d7a1a
a919a95c83a233542e5da375487e6fabb1b81157c8f5bb372e12bebad910b170
e586a39a113c6c49b096ff19519e822f736d06c805a01eaed6adee2ab5a5836c
f2ae8953fa9406d5f746ff92b94dfc1d0d09378f12372a71ef07c98f94167317Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Win.Virus.Expiro-7153559-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
18
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: HideSCAHealth
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IDSVC
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IDSVC
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IEETWCOLLECTORSERVICE
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VDS
Value Name: Type
18
Mutexes Occurrences gazavat-svc
18
kkq-vx_mtx52
18
kkq-vx_mtx53
18
kkq-vx_mtx54
18
kkq-vx_mtx55
18
kkq-vx_mtx56
18
kkq-vx_mtx57
18
kkq-vx_mtx58
18
kkq-vx_mtx59
18
kkq-vx_mtx60
18
kkq-vx_mtx61
18
kkq-vx_mtx62
18
kkq-vx_mtx63
18
kkq-vx_mtx64
18
kkq-vx_mtx65
18
kkq-vx_mtx66
18
kkq-vx_mtx67
18
kkq-vx_mtx68
18
kkq-vx_mtx69
18
kkq-vx_mtx70
18
kkq-vx_mtx71
18
kkq-vx_mtx72
18
kkq-vx_mtx73
18
kkq-vx_mtx74
18
kkq-vx_mtx75
18
*See JSON for more IOCs
Files and or directories created Occurrences \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\ckjgpiji.tmp
18
\MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\klncjook.tmp
18
\MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\bglnccaf.tmp
18
\MSOCache\All Users\{91140000-0011-0000-0000-0000000FF1CE}-C\mnclgkoo.tmp
18
%CommonProgramFiles%\Microsoft Shared\MSInfo\kcndgmlj.tmp
18
%CommonProgramFiles%\Microsoft Shared\OFFICE14\cgcganec.tmp
18
%CommonProgramFiles%\Microsoft Shared\VSTO\10.0\pnpndocj.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\bafefhom.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\dnmejccm.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\ejlkpjei.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\fijffced.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\ghpbhbif.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\gkbpadmi.tmp
18
%CommonProgramFiles%\Microsoft Shared\ink\pnhochhl.tmp
18
%ProgramFiles%\DVD Maker\jaemdheq.tmp
18
%ProgramFiles%\Internet Explorer\geakanpm.tmp
18
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe
18
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe
18
%System32%\alg.exe
18
%System32%\dllhost.exe
18
%System32%\ieetwcollector.exe
18
%System32%\msdtc.exe
18
%System32%\msiexec.exe
18
%System32%\snmptrap.exe
18
%System32%\sppsvc.exe
18
*See JSON for more IOCs
File Hashes 042fc31aadb0e0a33f91c9513ed9110d0c181de5b49f22614eb15ca759aabc58
07964288aebc5a85af04a534b2e795ded8c270466edfe2938cb5a7aae95fedee
2868317804d6a32158c492563f8cf121b0e714d116046f66323d49f7ea441f96
32084017ad00fe6e0ab45a804904363e3526f383cc78d35df55f66937b96f8fd
45414708db6a99c7fb927fcbc84861e55255a85e1583eaf661ef6226a880c525
53fd6b9b925d4cf2b143f057f11fa15659dd8d3e560aafa54148e87082e0aae7
69907401f98b32f51c11cd53b5149b29f8c4ecab38e08ca76188739f57e00431
6e3f1120e34aac4dea7bc87ce7a7185074841bc7077c2fa13a742f0ca53c81a3
6fa4177a1ee93669aa408db21de55d860d9792f6d544cf3510d4c121c95f5be0
749762f179e4c19d613a128150d3b82d1b0c138424ad3d436a77874a3392829e
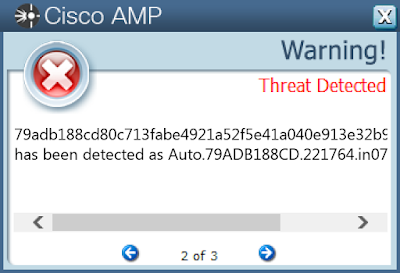
79adb188cd80c713fabe4921a52f5e41a040e913e32b995d98ea90a94cbb5006
91a4c230b121564208cbb629ddb79df79651738b2abd59c426b32e4dc4022f1d
a24c20594273edfc118ccce5b7e82081240e9f6a3323818f7ac17d990170471d
a52fdbfecc6455806e30f138c43f02186f91daf5fb032e62efd68e697322542f
b2aac39e286f2172baa62b16555191a60d6c1d25d63f73de51d80d60f263db32
c367dd19b06798008ed520730d0c7e05f28645d4565de62969a318275b9e6cff
de601aa4336e1ae644b7dcee10e0748cea30d70907b7e899ae39b364b56e181f
e62cf47c56c9858faf8a344e9b468293b48069c0f1d47034fea06409e9c26644Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
N/A
Screenshots of Detection AMP ThreatGrid Win.Ransomware.Shade-7158472-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xi
71
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Client Server Runtime Subsystem
71
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xVersion
71
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32
71
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
71
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: shst
50
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: sh1
50
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xstate
50
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xcnt
50
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xmode
50
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: xpk
50
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\WINDOWS ERROR REPORTING\DEBUG
Value Name: ExceptionRecord
41
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER
Value Name: CleanShutdown
32
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{509D0DCA-5840-11E6-A51E-806E6F6E6963}
Value Name: Generation
32
<HKLM>\SYSTEM\CONTROLSET001\ENUM\PCIIDE\IDECHANNEL\4&A27250A&0&2
Value Name: CustomPropertyHwIdKey
32
<HKLM>\SYSTEM\CONTROLSET001\ENUM\USB\VID_46F4&PID_0001\1-0000:00:1D.7-2
Value Name: CustomPropertyHwIdKey
32
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{509D0DCA-5840-11E6-A51E-806E6F6E6963}
Value Name: Data
32
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{6DD1DC5F-5840-11E6-B80E-00501E3AE7B5}
Value Name: Data
31
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{6DD1DC5F-5840-11E6-B80E-00501E3AE7B5}
Value Name: Generation
31
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{3F37BA63-EF5C-11E4-BB8D-806E6F6E6963}
Value Name: Data
31
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{3F37BA63-EF5C-11E4-BB8D-806E6F6E6963}
Value Name: Generation
31
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
Value Name: Data
31
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\MOUNTPOINTS2\CPC\VOLUME\{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
Value Name: Generation
31
<HKLM>\SYSTEM\CONTROLSET001\ENUM\PCI\VEN_1AF4&DEV_1001&SUBSYS_00021AF4&REV_00\3&2411E6FE&2&18
Value Name: CustomPropertyHwIdKey
31
<HKLM>\SOFTWARE\WOW6432NODE\SYSTEM32\CONFIGURATION
Value Name: shsnt
31
Mutexes Occurrences cversions.2.m
30
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 128[.]31[.]0[.]39
28
193[.]23[.]244[.]244
26
86[.]59[.]21[.]38
25
131[.]188[.]40[.]189
24
194[.]109[.]206[.]212
23
154[.]35[.]32[.]5
22
171[.]25[.]193[.]9
22
76[.]73[.]17[.]194
20
104[.]18[.]35[.]131
20
208[.]83[.]223[.]34
18
104[.]16[.]154[.]36
16
104[.]16[.]155[.]36
15
104[.]18[.]34[.]131
11
51[.]68[.]204[.]139
3
46[.]166[.]182[.]20
3
148[.]251[.]51[.]66
3
51[.]68[.]206[.]28
3
145[.]239[.]66[.]236
2
78[.]129[.]150[.]72
2
144[.]76[.]57[.]165
2
137[.]74[.]19[.]202
2
37[.]157[.]254[.]113
2
136[.]243[.]176[.]148
2
69[.]30[.]219[.]82
2
62[.]210[.]157[.]133
2
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences whatismyipaddress[.]com
31
opengraphprotocol[.]org
31
wsrs[.]net
31
whatsmyip[.]net
31
cmsgear[.]com
31
luminati[.]io
31
redirme[.]com
31
Files and or directories created Occurrences %ProgramData%\Windows\csrss.exe
71
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM01859862[[fn=Urban Pop]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM01859865[[fn=Kilter]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM01859866[[fn=Macro]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM01859868[[fn=Thermal]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM01972873[[fn=Summer]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM02455519[[fn=Winter]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM02455596[[fn=Spring]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Document Themes\1033\TM02455610[[fn=Autumn]].thmx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Word Document Building Blocks\1033\TM01793058[[fn=Median]].dotx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Word Document Building Blocks\1033\TM01793060[[fn=Origin]].dotx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Word Document Building Blocks\1033\TM01793064[[fn=Equity]].dotx
50
%APPDATA%\Microsoft\Templates\LiveContent\Managed\Word Document Building Blocks\1033\TM01840907[[fn=Equations]].dotx
50
%APPDATA%\Microsoft\Templates\Normal.dotm
50
%APPDATA%\Microsoft\UProof\CUSTOM.DIC
50
%APPDATA%\Mozilla\Firefox\profiles.ini
50
\README1.txt
50
\README10.txt
50
\README2.txt
50
\README3.txt
50
\README4.txt
50
\README5.txt
50
\README6.txt
50
\README7.txt
50
\README8.txt
50
*See JSON for more IOCs
File Hashes 00591b03aa2be7dc7e67fa04a5da57bb803a2b4bc008fd7df40feadb72d2f00d
00953fe490792ae76ab5a584513a0ab3c460bcaa4fbb08f88ea5f0a261c44eab
018f3383e5f17da7f673fcd53b624f3157bfce958d3defd546fc82baf26265c6
01b2c4dd09be08a0db5cd266c2b0f4ae01ab920c6647910de820eb9cf82d55d4
01dea6848c96188f53d6e90977326b3562a2fcc30bd84c3d0e67880d6d4b8c50
02146af20bcaec9dbf6f30071791e73c7fd4eac6657f3b9d3159a6f663764250
025207f8e1551eb8156dd759426d57b2cbb42ce7b65479f071b7ffe8d0d03479
02b34490a5a4688b754dbb9be6507330ae88dfbc911f5c09e9e9e7c7ef10f2c5
02bf9968e18495581c271d4110a7bbaaf3889043c93af10357cb10499c8950a7
0616e6bc594dea95fad720bc966573921d9f2ec92eddcf665975227776e07fd6
0644b301b6414d2fe97644ae926849252c7a33607f2288253e9e53c5afd5c476
067cc19af3565e37da3bc0189210ad87ad111faf2a4c845f01fca036e3da912b
068491e6b7b02d7fef9a4778862886565795765b28b3c8f72f0d7adebc0b0a47
06a02b8b9e4871d0e558818a259dc6b6fcd0789b3d6a0f1c35dfaf90a8fc33f6
072a786d43860a9b5c2d4b49c1228ba651fad80e812eccd3e698d0f7b1b3adae
0769d0046146bd19aa118706ac9a470575139f06479c2781b680b5d8b92cce05
093bc279dcf1d7ee9a194af8e1e323b9ebe94f8a59a6dbbed8e82ca552c4dcb2
09483603bc66291e19444d644a5627416fb09d097b2a5efac0755c957cf7aedd
0c244b7cf8841885f0fecb184610c80ff3b3f6015e86f50ce35023383396dbf2
0c703b45991e6b99d4d4155af6437c5e255d7e52af06a2c9a29a3391774e4ae7
0d35cc4470e1f4493c8a9919769a9069a7deae2ee6ced8bd8ef0040c934a57f9
0d7531dc6587e8d9f9e3eae58e803b4aafd6d35927e7d48cc0a730cdc98a89d0
0df9f6f2d26051ba29c79a61f46e482d0cd61bb20a699cc7937e2f52f4d20fca
0e1f57431d814b1383b0202f10cdc0e929bd17d7788dc04e5d99b5f60761484e
0e21c68614126c9afae8a7747af154fdd254def83795bdb4033cb5a50de80026*See JSON for more IOCs
Coverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
N/A
Wsa
Screenshots of Detection AMP ThreatGrid Win.Packed.Tofsee-7150793-1 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Type
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Start
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ErrorControl
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: DisplayName
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: WOW64
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ObjectName
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: Description
18
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
18
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
18
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\<random, matching '[A-Z0-9]{8}'>
Value Name: ImagePath
12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\cvjpowcr
4
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\haoutbhw
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\wpdjiqwl
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\mftzygmb
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\unbhgouj
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\ibpvucix
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\exlrqyet
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\tmagfnti
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\lesyxfla
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\slzfemsh
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\yrflksyn
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
18
69[.]55[.]5[.]250
18
172[.]217[.]3[.]100
18
46[.]4[.]52[.]109
18
176[.]111[.]49[.]43
18
85[.]25[.]119[.]25
18
144[.]76[.]199[.]2
18
144[.]76[.]199[.]43
18
43[.]231[.]4[.]7
18
192[.]0[.]47[.]59
18
95[.]181[.]178[.]17
18
173[.]194[.]207[.]27
16
216[.]146[.]35[.]35
15
213[.]205[.]33[.]63
14
172[.]217[.]197[.]26
14
208[.]76[.]51[.]51
13
208[.]76[.]50[.]50
13
148[.]163[.]156[.]1
12
64[.]233[.]186[.]26
12
208[.]71[.]35[.]137
11
172[.]217[.]5[.]228
11
67[.]231[.]154[.]162
11
209[.]85[.]203[.]27
11
199[.]5[.]26[.]46
10
199[.]5[.]157[.]131
10
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
18
250[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
18
250[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
18
250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
18
whois[.]iana[.]org
18
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
18
whois[.]arin[.]net
18
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
18
microsoft-com[.]mail[.]protection[.]outlook[.]com
18
honeypus[.]rusladies[.]cn
18
marina99[.]ruladies[.]cn
18
sexual-pattern3[.]com
18
coolsex-finders5[.]com
18
smtp[.]secureserver[.]net
15
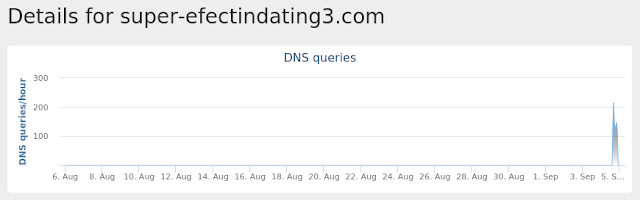
super-efectindating3[.]com
13
ipinfo[.]io
12
mx1[.]emailsrvr[.]com
12
mx0a-001b2d01[.]pphosted[.]com
12
mx-aol[.]mail[.]gm0[.]yahoodns[.]net
11
etb-1[.]mail[.]tiscali[.]it
10
mta5[.]am0[.]yahoodns[.]net
9
mx-eu[.]mail[.]am0[.]yahoodns[.]net
9
eur[.]olc[.]protection[.]outlook[.]com
9
aol[.]com
9
hotmail-com[.]olc[.]protection[.]outlook[.]com
9
*See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile
18
%SystemRoot%\SysWOW64\<random, matching '[a-z]{8}'>
18
%TEMP%\<random, matching '[a-z]{8}'>.exe
18
%System32%\<random, matching '[a-z]{8}\[a-z]{6,8}'>.exe (copy)
11
%SystemRoot%\SysWOW64\config\systemprofile:.repos
3
%TEMP%\supvobl.exe
1
File Hashes 1599aff065e6687acafc61a6f572652d1a0f7a0b17e3a71ca32fe848f2dc2732
1f8ca64991ba709a857f0dcd5bc5d6e9b0885ebc929989f03be3dfb58ecf9ce0
2360e7fb046aff05970dafbb74cdf5544e4699143605d8334772554f50ead3ac
4368a7bb048f1ba83bbd8430b2f49cb566cd69642ed3e9de3675f69533125b29
471c51b4340ed0091aeaf0402f762230689951e448f703033ed4bd1f2fb7a7d6
5195a9a5a3094c3735668216461d2be638152ae0738dab4d8a9295b697bc567c
675f23d881b4685a171767073e01f889ddeb879af7036fde7bcf341f33699da5
8092a1a1db9009435d1177afdef7fb7334e090b8d1b2f5c3e4d121ac0c110cbb
8120184d0a6340d01c5226d28747a2da5c81ef323e126df5a92ff9ada41b5c42
86cf3a207714ea953fb6834643b68064b912c077d44c31b9ed287feab0bc0e4a
8baff9107ff5c48ed53d633fe18f039d3cdd30eedcf05e55b4c467f9f9aed831
9c8275a2d03edd430e8263980a2c31106ab7116e40b93bead7108c6ed97e29fc
a3e921ece8ec6a501dbb88c78fea54e2bd15e46b22cb61abced99973c70cf6f8
c2606f0413239f1c60cccd260374e6b88694718af0389be6d173a5c466e7d819
c2a86711660f12b21a7f3fe3fde6b7f07faeb486111d71e34abc27f90f31b415
c94a846dc45a26b4d3869ac32de34aa780720d4cd21743847bb87a2da4a14a8b
d7d152e0dc028976050dbace9078c99feddce0f805c1892b4f1ac92feaf5fe15
dae992cf09f4681239e858e69eebfff7e35786069d7719482ccbb15615ec7a7eCoverage Product Protection Amp
Cloudlock
N/A
Cws
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Threat Grid
Umbrella
Wsa
Screenshots of Detection AMP ThreatGrid Umbrella Exploit Prevention Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. CVE-2019-0708 detected - (7002)
An attempt to exploit CVE-2019-0708 has been detected. The vulnerability, dubbed BlueKeep, is a heap memory corruption which can be triggered by sending a specially crafted Remote Desktop Protocol (RDP request). Since this vulnerability can be triggered without authentication and allows remote code execution, it can be used by worms to spread automatically without human interaction.
Madshi injection detected - (2740)
Madshi is a code injection framework that uses process injection to start a new thread if other methods to start a thread within a process fail. This framework is used by a number of security solutions. It is also possible for malware to use this technique.
Kovter injection detected - (1860)
A process was injected into, most likely by an existing Kovter infection. Kovter is a click fraud Trojan that can also act as an information stealer. Kovter is also file-less malware meaning the malicious DLL is stored inside Windows registry and injected directly into memory using PowerShell. It can detect and report the usage of monitoring software such as wireshark and sandboxes to its C2. It spreads through malicious advertising and spam campaigns.
Process hollowing detected - (1503)
Process hollowing is a technique used by some programs to avoid static analysis. In typical usage, a process is started and its obfuscated or encrypted contents are unpacked into memory. The parent then manually sets up the first stages of launching a child process, but before launching it, the memory is cleared and filled in with the memory from the parent instead.
Trickbot malware detected - (1131)
Trickbot is a banking Trojan which appeared in late 2016. Due to the similarities between Trickbot and Dyre, it is suspected some of the individuals responsible for Dyre are now responsible for Trickbot. Trickbot has been rapidly evolving over the months since it has appeared. However, Trickbot is still missing some of the capabilities Dyre possessed. Its current modules include DLL injection, system information gathering, and email searching.
Gamarue malware detected - (205)
Gamarue is a family of malware that can download files and steal information from an infected system. Worm variants of the Gamarue family may spread by infecting USB drives or portable hard disks that have been plugged into a compromised system.
Installcore adware detected - (128)
Install core is an installer which bundles legitimate applications with offers for additional third-party applications that may be unwanted. The unwanted applications are often adware that display advertising in the form of popups or by injecting into browsers and adding or altering advertisements on webpages. Adware is known to sometimes download and install malware.
Excessively long PowerShell command detected - (95)
A PowerShell command with a very long command line argument that may indicate an obfuscated script has been detected. PowerShell is an extensible Windows scripting language present on all versions of Windows. Malware authors use PowerShell in an attempt to evade security software or other monitoring that is not tuned to detect PowerShell based threats.
PowerShell file-less infection detected - (89)
A PowerShell command was stored in an environment variable and run. The environment variable is commonly set by a previously run script and is used as a means of evasion. This behavior is a known tactic of the Kovter and Poweliks malware families.
Fusion adware detected - (41)
Fusion (or FusionPlayer) is an adware family that displays unwanted advertising in the form of popups or by injecting into browsers and altering advertisements on webpages. Adware is known to sometimes download and install malware.