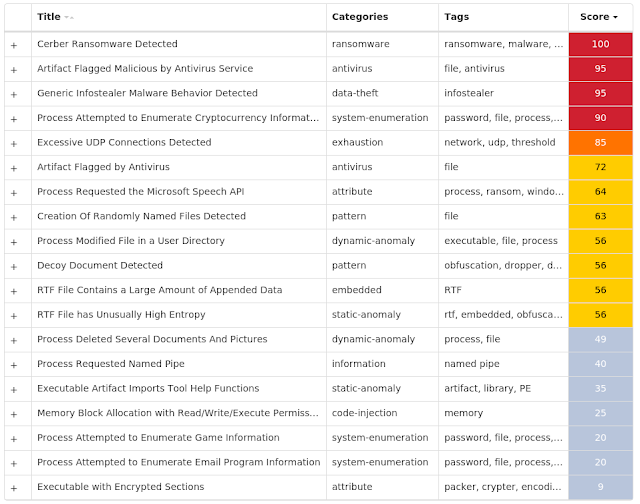
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between June 10 and June 17. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
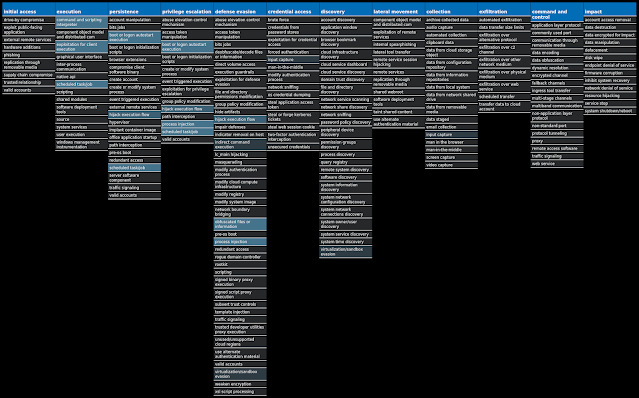
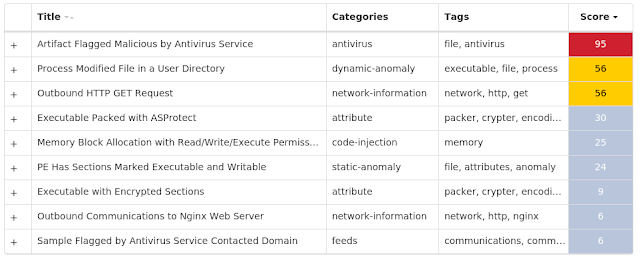
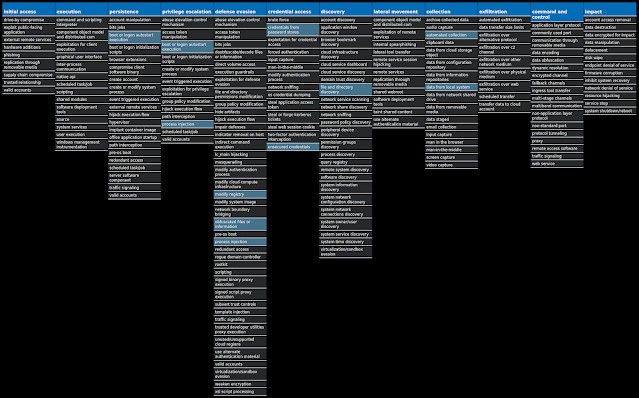
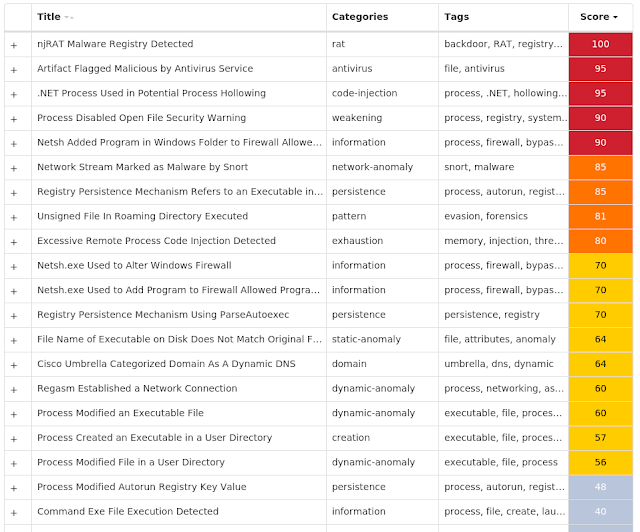
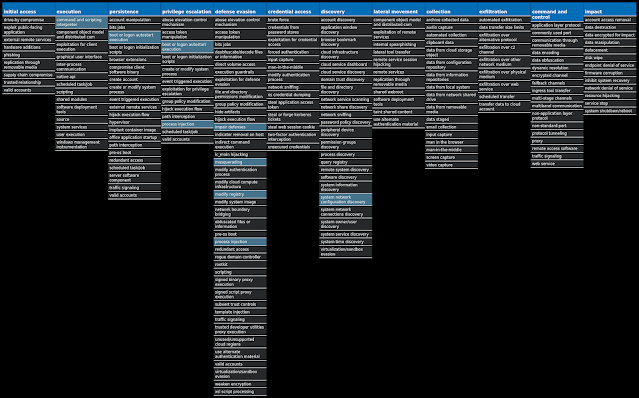
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name Type Description Win.Dropper.Kuluoz-9951554-0
Dropper
Kuluoz, sometimes known as "Asprox," is a modular remote access trojan that is also known to download and execute follow-on malware, such as fake antivirus software. Kuluoz is often delivered via spam emails pretending to be shipment delivery notifications or flight booking confirmations.
Win.Malware.Emotet-9951647-0
Malware
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Malware.Ursu-9951579-0
Malware
Ursu is a generic malware that has numerous functions. It contacts a C2 server and performs code injection in the address space of legitimate processes. It is able to achieve persistence and collect confidential data. It is spread via email.
Win.Malware.Zusy-9951717-0
Malware
Zusy, also known as TinyBanker or Tinba, is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe". When the user accesses a banking website, it displays a form to trick the user into submitting personal information.
Win.Packed.Johnnie-9951653-0
Packed
Johnnie, also known as Mikey, is a malware family that focuses on persistence and is known for its plugin architecture.
Win.Downloader.Upatre-9952018-0
Downloader
Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware.
Win.Trojan.Zbot-9951812-0
Trojan
Zbot, also known as Zeus, is a trojan that steals information, such as banking credentials, using methods such as key-logging and form-grabbing.
Win.Packed.njRAT-9951863-1
Packed
njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014.
Win.Packed.Cerber-9951870-0
Packed
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns other file extensions are used.
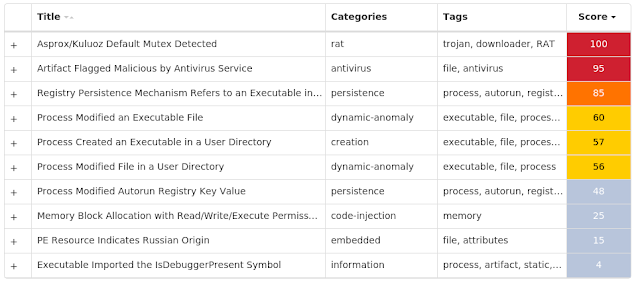
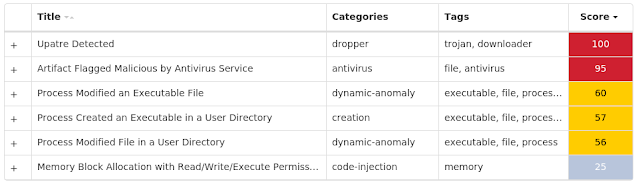
Threat Breakdown Win.Dropper.Kuluoz-9951554-0 Indicators of Compromise IOCs collected from dynamic analysis of 53 samples Registry Keys Occurrences <HKCU>\SOFTWARE\<random, matching '[a-zA-Z0-9]{5,9}'>
53
<HKCU>\SOFTWARE\KJJMJSES
Value Name: bdjqdfwj
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: uumhwxma
1
<HKCU>\SOFTWARE\JXUUKKDW
Value Name: locbrvhe
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: iqqhjsfw
1
<HKCU>\SOFTWARE\KPAETDOF
Value Name: krufhdbd
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: evjvokik
1
<HKCU>\SOFTWARE\BWUDIQJM
Value Name: jnwirdki
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: xufltbxk
1
<HKCU>\SOFTWARE\HIRHOATA
Value Name: eisnxhra
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: mdrufreo
1
<HKCU>\SOFTWARE\PRMHPLCR
Value Name: oshustei
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: aldpcbir
1
<HKCU>\SOFTWARE\IKNMTLOQ
Value Name: ldgxwqmo
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: gpqtqbjl
1
<HKCU>\SOFTWARE\NLGLIGOC
Value Name: ccdhafww
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ktfnusik
1
<HKCU>\SOFTWARE\EXICAHWH
Value Name: xbeqvghl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ghlwkjxg
1
<HKCU>\SOFTWARE\TDFEMELN
Value Name: rxkaagok
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: nwimalgk
1
<HKCU>\SOFTWARE\FVWAKPNV
Value Name: sisiqvga
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: pkpanwfn
1
<HKCU>\SOFTWARE\UFIJMRQA
Value Name: wuwxnmmb
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: hssjhkqt
1
Mutexes Occurrences aaAdministrator
53
abAdministrator
53
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 66[.]45[.]253[.]250
46
67[.]231[.]22[.]199
44
67[.]18[.]12[.]2
44
178[.]210[.]167[.]213
44
81[.]177[.]181[.]223
43
31[.]186[.]5[.]20
41
185[.]66[.]12[.]185
39
Files and or directories created Occurrences %LOCALAPPDATA%\<random, matching '[a-z]{8}'>.exe
53
File Hashes 03d16772164bf38fce12f8b20edf31e333dde72551d28946a6b0504572a7ee3c
0d11f50467268ec07cfcdcf7126ce47925e2734c9860193418f0bf7652b692b5
0ec35b0853067a546b01cdd703a3af294c2b9d13ead3f08431bf6409f4e3d768
117b43fa236e85316eae679843702e34611f783a8d32d987bfdf6d7c1e95cb05
15ccb21da4a19b67a8921f9f658c2e4a6a128377a53775f8a22e6d8a8c1aad19
165f2b77a3913502331e7479b9eb27daa502f95d345a21aa35e0bf25824419bd
181b3d14bc2ccebfe2eb9b807249c4389921328f15d8a1d9052101802cde8912
1a01fd2a79edf02208ac763bba4b85a573063695f739a14e71e8a52968203f92
1a02a929ec3913b35be686ed02c4e573d0269b89fef541698cd7367ce8305cac
1be0c8fa5a596a21af5a95eaefda391ae744de19f22d100868a741b1e3996185
2563cfb42ab2886f9421221b09fed67135e2a62ac81decac5f4fbc340260b9db
2ad88e50328965fae0bad32e09e034176f8e6ea79218e0ea45f3e9a32769c166
2cd8dfc9ba6f7f03897763376262263cafe0b066ca45414cb2fcd07dc3a74b6a
37f8435545d2899ec78f1310d526b8709b940fcc1fa7c209e769c51df7185478
3b14aa6be8f6b0e413d37c4e9db91f29d93b5cf5ea88a03af31a57dd95ad287c
3d4f44f5cfa2cfda03d736d07dcee9f5830d0306537651154cf0410082652b55
3f4fb2d9add4d85f1f1e951b05f11321086f5ae0954da0f1e763347dde6bf299
410669d18544b0046ce352513a5b2c20f895779e2310600abd0e5f73b4498e40
4896f409886858981d2470cb7be22021c0b0717c9ad347ee4fe79429b3db257d
4b1c65ac6dab390f0df1dc71aa4ced2a66e95a5f18cf3e22394471d7d06ecfb1
50873e470dd6ea1e75f5b2baefc2d7d0a828f178b773d69da4b958dc96678eb6
57a1bd5ba95ee4b0204130eef017f6ae00b567f68271e1d58c9a4916274e537c
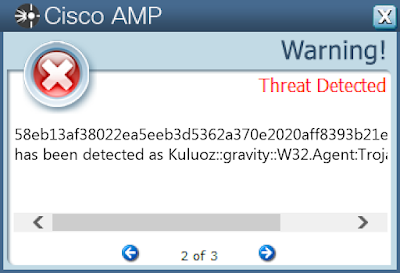
58eb13af38022ea5eeb3d5362a370e2020aff8393b21e26ec992bd910410ea86
590e2da8a84ead5f16888321431b54095748429ba8d995b20226c2632de7b01c
5f62d67d8bc2fe4893208bb9c839ee6944b75034e1613de5b4430534f0ef8da7*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
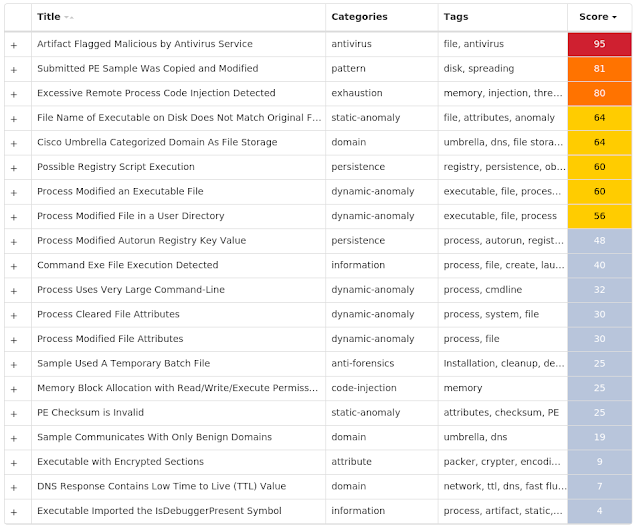
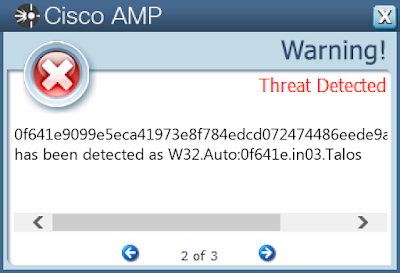
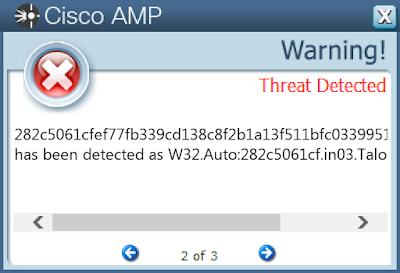
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Malware.Emotet-9951647-0 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{690D1BD7-EA98-1004-3AC9-E87553700E95}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{690D1BD7-EA98-1004-3AC9-E87553700E95}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63FC4996-AFD5-E391-06A7-EFB6E2702561}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63FC4996-AFD5-E391-06A7-EFB6E2702561}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10CDDA71-B745-777B-1AF7-51696DB9BB93}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10CDDA71-B745-777B-1AF7-51696DB9BB93}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{CFD6D5E6-02FB-7433-9261-E8E1B87CAC69}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{CFD6D5E6-02FB-7433-9261-E8E1B87CAC69}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{8BAB5812-9D02-8F14-74B1-BEDE393F8C1F}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{8BAB5812-9D02-8F14-74B1-BEDE393F8C1F}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10DF83AD-199B-9C18-3FEF-E4ECD6A42F66}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{10DF83AD-199B-9C18-3FEF-E4ECD6A42F66}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{1AD90FE5-CE2F-E8B8-CF09-E0B1912E9542}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{1AD90FE5-CE2F-E8B8-CF09-E0B1912E9542}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{05ED06D6-F422-71CC-26B3-C9964D56F645}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{05ED06D6-F422-71CC-26B3-C9964D56F645}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{98B09642-2764-54AE-3333-D8C6CA536428}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{98B09642-2764-54AE-3333-D8C6CA536428}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63D99860-AA40-CA79-F681-9DECBEF55447}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{63D99860-AA40-CA79-F681-9DECBEF55447}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{D4B277A3-C25E-BCDE-A054-D41AAC36394B}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{D4B277A3-C25E-BCDE-A054-D41AAC36394B}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{FE9DE6BC-A4CF-8285-E73C-DFE7A08197FE}
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{FE9DE6BC-A4CF-8285-E73C-DFE7A08197FE}\SHELLFOLDER
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\CLSID\{B11CF2E2-C0C2-7860-F12E-428101DCB963}
13
Mutexes Occurrences {24d07012-9955-711c-e323-1079ebcbe1f4}
13
{bf18992f-6351-a1bd-1f80-485116c997cd}
13
{ac5b642b-c225-7367-a847-11bdf3a5e67c}
13
{ed099f6b-73d9-00a3-4493-daef482dc5ca}
5
Files and or directories created Occurrences %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5
13
%System32%\Tasks\Ryddmbivo
13
%APPDATA%\1lFT
9
%APPDATA%\MJrHN
3
%APPDATA%\1lFT\icardagt.exe
2
%APPDATA%\1lFT\ie4uinit.exe
2
%APPDATA%\1lFT\xpsrchvw.exe
1
%System32%\5246
1
%System32%\5246\credwiz.exe
1
%APPDATA%\1lFT\iexpress.exe
1
%System32%\7496
1
%System32%\7496\icardagt.exe
1
%System32%\0786
1
%System32%\0786\AdapterTroubleshooter.exe
1
%System32%\7911
1
%System32%\7911\icardagt.exe
1
%APPDATA%\MJrHN\recdisc.exe
1
%APPDATA%\MJrHN\dpapimig.exe
1
%System32%\7124
1
%System32%\7124\SystemPropertiesAdvanced.exe
1
%System32%\0485
1
%System32%\0485\VSSVC.exe
1
%APPDATA%\1lFT\cmstp.exe
1
%System32%\1674
1
%System32%\1674\consent.exe
1
*See JSON for more IOCs
File Hashes 11937c5d0ecbfdad670f9ab669e0962da77eeb6adf08c321957a8967b4df85d6
130ad7d32592a45a7752eb5519d4eb1e8b3bc1d89c194dd3280c4092cb2df813
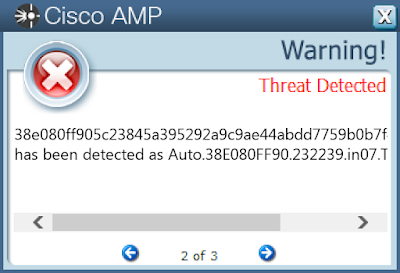
38e080ff905c23845a395292a9c9ae44abdd7759b0b7f43628c7be9f99de8ff1
49bcf6f627015d60bb285b80fcb825067d967591ea39af2b37aba982457fa277
77a213f839b6042cb81c0d62438edc6684c1bba47b15f99acb7dfc36a5200df2
7c43e2a210ec0bcc42f727d5a513ed5727f74b0e699f75944b68e4a64706bfe0
c13c882f05bb3955703461f3dd0d1c672f8c49c676f2a8ba23cd081861c00b4e
c26aa64c7dd9fd1c8ef6216502af95f047bdf5eca193a0a4163b6c33c254415d
d37e40966aba9b94dde2f19a84c4046ec6a08b4470597ebbbe9dc92e5f039b71
d4ab2f13939fab307477f91bca3466d208631fa5c2ea22ac6fde99aed0ac1111
d80cc713b58f429b602e56aa23fe4df4abb76f450f19306033b070f337b8fe4d
dba2b5323c3bb00c29e87031095ff2a5d559e840f7d998f255f555a310e977d7
f3c74369cfc6ddd9a046177bc525e076484257b6dd8f4f1ed9249c3e608939a6Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
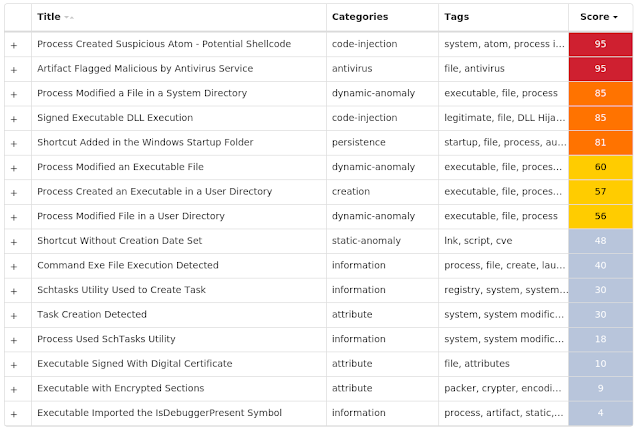
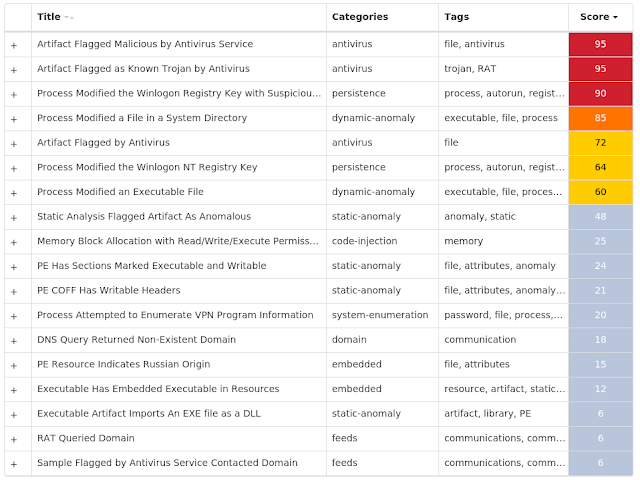
MITRE ATT&CK Win.Malware.Ursu-9951579-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Mutexes Occurrences {7AA4AA84-01C3-46CC-A00B-B0C840C728B7}
25
qm_mutex_key
3
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 27[.]254[.]66[.]8
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences pb[.]wungfon[.]com
25
Files and or directories created Occurrences %APPDATA%\Microsoft\sysAddr.dat
4
File Hashes 008eb76b3d5a9fe7f8981dc7cc03b8eee4b057cbbdacc37a8d76cc61ebec6281
014fc0be7d4ce5b735183db7e225e982c690db90616081d3f621ff29db0e5125
032085f5d5dbd471e6b4908869ead38a07dedda23e283342bde00ab32e6b7cb1
07980f20d13a72877f5f3e42845551f9706863c20174b3777fe72f1e4fd2b282
0b64e696150281ccb5ed39ca437d13b073b91fc5f8c409a97d08ce377d8fde4b
1483faa5958725204242ca17a8c91db73e7e1861d8871c8f8b9f82cd80684855
218518f37cda9a3a24d9e0e018cf71a7ca263ba497335445c3edec73573f42d3
22692cb2374431b564595e34a32d32147cb4047ac042869541d3638463a02f0c
24e995a669d984569832fe86f374f1bec506bd50bbc876426784463d311a7c30
2531acc711354ac26b715551b89c0aac6d441d2961b18846298f45ca7bba7850
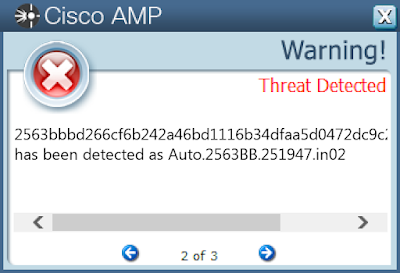
2563bbbd266cf6b242a46bd1116b34dfaa5d0472dc9c2116b678b3f8637588c5
296d5be886a08e4c6b1eac3438ff2f561b789dc3edfb29799323b46f3a5a918c
2ae17a2b382e80b44d1a97bcd05d7fdbf1b51ca0b2b67e46e072c351f827b862
2c3f6c2ea02439ba156b6f2c40edc2b9fc02d0abc8b7e4c3b0a68c077d17859f
3058d25bdbbb2ad4b639bf01f3481bd9d51365467cd9555ac2905d71fa1e22d3
311a390ed45b8f8a46d651faef37946af238fc48e0506fb88da643401a083244
392d0e0ad47c1c96b2208a4d2b971b984dadd5d180126933de056f9c3d50a7bb
3eaeadc84ca2617b9d371bb5b94659b7461e0d0b2d88558f26e95ca5d09357eb
470bd7590bc09312dc6af0487ef4a2d5f9f8b3337cd1c8876dc1531c8c678e8e
497930029fd34a5b626e8010a06d18672390c97e8f4ff4b68bfc61b9387abebb
52ce5f7e0e1223c82a4a88588a5658df64e6dddf262a2ca6af1ffcb5cc190054
5ca59c6611f4b91df2070408493b5b7ab89985848401c34e1a8ed0d012eecfed
5d2a540674e49178959767e8a1c335da233a8f8c3f509f1f4851ec0eed164557
6af6e5cfe7d10a2cbb7fd6b8a8041ab9fd263e51065d2806c8858539b558bc2c
6cb8e1da7b4042dda8f43dc21ccbff8ca317be65c80194744cea6bc4d1483bb7*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
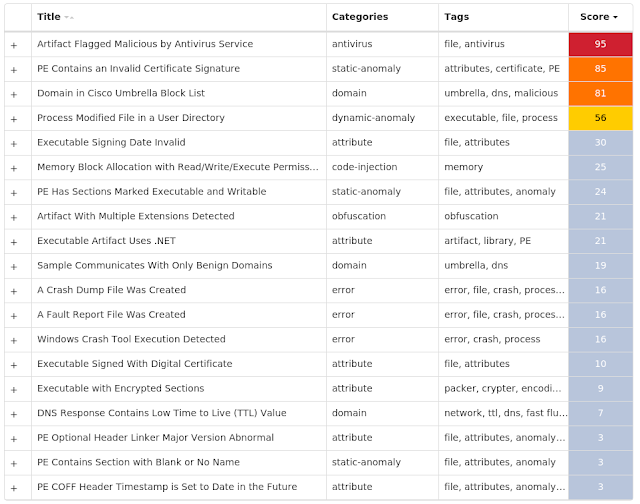
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Malware.Zusy-9951717-0 Indicators of Compromise IOCs collected from dynamic analysis of 26 samples Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VSS\DIAG\VSSAPIPUBLISHER
26
<HKCU>\SOFTWARE\MICROSOFT\SYSTEMCERTIFICATES\USERDS
26
<HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS
Value Name: 2d17e6
26
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: IntelPowerAgent13
26
Mutexes Occurrences 2d17e659d346
26
98b59d0b000000f8
6
98b59d04000000f8
6
98b59d0b000006a8
4
98b59d04000006a8
4
98b59d0b000006e0
3
98b59d04000006e0
3
98b59d0b000006b0
2
98b59d0b0000039c
2
98b59d0b0000034c
2
98b59d0b000004ec
2
98b59d04000006b0
2
98b59d04000004ec
2
98b59d040000039c
2
98b59d040000034c
2
98b59d0b000004f0
1
98b59d0b0000076c
1
98b59d0b000007bc
1
98b59d0b000005ac
1
98b59d040000076c
1
98b59d04000004d8
1
98b59d04000007bc
1
98b59d0b000004d8
1
98b59d04000005ac
1
98b59d04000004f0
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 31[.]13[.]65[.]36
26
31[.]13[.]65[.]174
26
162[.]125[.]248[.]18
26
12[.]153[.]224[.]22
26
17[.]253[.]144[.]10
26
138[.]197[.]63[.]241
26
104[.]21[.]41[.]17
17
140[.]82[.]113[.]3
10
172[.]67[.]141[.]102
9
209[.]197[.]3[.]8
8
20[.]84[.]181[.]62
7
104[.]244[.]42[.]1
6
20[.]81[.]111[.]85
6
20[.]53[.]203[.]50
6
140[.]82[.]113[.]4
5
140[.]82[.]112[.]3
5
20[.]103[.]85[.]33
5
13[.]107[.]4[.]50
4
140[.]82[.]112[.]4
3
140[.]82[.]114[.]3
2
65[.]58[.]11[.]254
2
20[.]112[.]52[.]29
2
23[.]52[.]1[.]232
2
140[.]82[.]114[.]4
1
8[.]253[.]157[.]120
1
*See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences github[.]com
26
microsoft[.]com
26
twitter[.]com
26
instagram[.]com
26
facebook[.]com
26
download[.]windowsupdate[.]com
26
dropbox[.]com
26
etrade[.]com
26
icloud[.]com
26
python[.]org
26
sendspace[.]com
26
Files and or directories created Occurrences %TEMP%\2d17e659d34601689591
26
%TEMP%\uddC7F7.tmp.bat
1
%ProgramData%\2b86j6hb4d.exe
1
%TEMP%\dvw2DC9.tmp.bat
1
%ProgramData%\2b264082jd.exe
1
%TEMP%\gtrE805.tmp.bat
1
%ProgramData%\b4fj2286f2.exe
1
%TEMP%\tme6D54.tmp.bat
1
%ProgramData%\b8f6f24db2.exe
1
%TEMP%\exh192E.tmp.bat
1
%ProgramData%\dhhh6bj28j.exe
1
%TEMP%\cbhB4D.tmp.bat
1
%ProgramData%\2bd62d6bhb.exe
1
%TEMP%\himB1DE.tmp.bat
1
%ProgramData%\djf2bj6446.exe
1
%TEMP%\nqy83A9.tmp.bat
1
%ProgramData%\bjbf008h8f.exe
1
%TEMP%\nqe2F62.tmp.bat
1
%ProgramData%\248jhb4f2b.exe
1
%TEMP%\rxcFAA7.tmp.bat
1
%ProgramData%\2bj8jbjbhb.exe
1
%TEMP%\nkuDECC.tmp.bat
1
%ProgramData%\b06022fff.exe
1
%TEMP%\phmFA5B.tmp.bat
1
%ProgramData%\bd2dhjh868.exe
1
*See JSON for more IOCs
File Hashes 01827881adc5584f7d2288e5e963160c98e1fda5d5f4f33e0a2d6b8b2d743237
03bcd9b34164998db2446d2d4fecc46231c007bb8eb8ee2548f43ad5a1403ebd
0c86296524c03d20adec3ac4804d86f7b96ab78e4832ab8f5a4550df4d198845
108cf8c9a06ce3e0119a733c472146e3f8a3a9d4bb7c36f26bab3ba594b71fde
171c661d966baf00f6ee7cda4f950a87bf1d8e716f26568656898beca218150f
1908a93f320d1628e7c25d19653f8ab6eb86c6479b2a75358141948aec47ec01
1b349b68841907ee055094feffecb0bb422b47c83fe695636ba78d3475be48d8
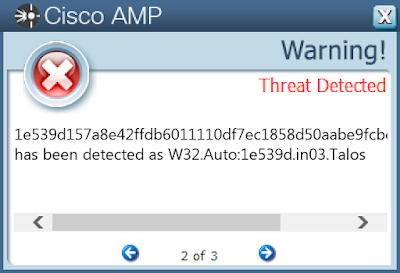
1e539d157a8e42ffdb6011110df7ec1858d50aabe9fcbc8e1720051427656d41
1fc8e90f1e5427bca5e5ffb95dceb11356a2054c79b15a7001a85041425eca27
28308a84b47b32733fff0c4b6e06e7c5ab167ba77e79b7f1d4ef0930353e709a
2b997e2ad4e646c1cf1c6114c78c5a8c676e8c3b35c8a1a3ae282af471011031
310b56553064533930fa99917c88453347bcef1a074e6e1386da883b2e40c0c6
31714578f7fd3a8a4cd34c6935f3e5dc61c3644cf4479fba16d535966705db9f
39097759e5da138e3e17518032476fd2c5335c739b4e37e6e77e9eaa7e3914d0
3967dd64c5424bfe3762ef22bfeb6bdf65b736606ee080a65627a6c73dc2ea76
461ab94e260e60d70917066ea58c68c376b394c244ab0256c711f17fc256f68f
46468e8076d924142490591d0a7044770c9b32e9ebdffd9acf97d737a2709aee
47a52917370e7ee1e252e1c2cbcaace8bcc8c6b454ff3c579314ac98dbcd695e
514ef4a4268745282585e5b13842fd4e1ecc6d2363197b9028d715df0f4b2ac1
552fd0ab41fad09a5314d8e1635904604743286fccd8a9eca09ad41e61474a12
575f6361702d5065d355954b5059de6aa68530ab23df995c530e74a2720d5c6a
68f1d25e6ffe8082f25bc250d64c27dc65dc65512083b222ada322dde3496e8a
6a7a01fff1a487039e692ce783ce802e7389b6386098195b860634ffecb26ba9
6fe2f061aafd8df62fffa2fda7dc86de685f0a512b95ca863463b8417ec21360
752781ac82e899ecbcf7ab1260859afa85d853ff5c89fe75a00abca010ed9c35*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Packed.Johnnie-9951653-0 Indicators of Compromise IOCs collected from dynamic analysis of 69 samples Registry Keys Occurrences <HKCR>\LOCAL SETTINGS\SOFTWARE\MICROSOFT\WINDOWS\SHELL\BAGS\159
69
Mutexes Occurrences Global\<random guid>
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 45[.]35[.]72[.]106
69
104[.]21[.]41[.]66
10
104[.]21[.]56[.]158
9
172[.]67[.]187[.]40
8
23[.]221[.]72[.]27
7
23[.]221[.]72[.]10
4
172[.]67[.]189[.]196
4
23[.]46[.]150[.]48
2
23[.]221[.]73[.]32
1
23[.]221[.]72[.]16
1
23[.]46[.]150[.]72
1
23[.]1[.]236[.]9
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ipwho[.]is
69
holdthismoney[.]site
64
apps[.]identrust[.]com
17
holdmy1337[.]ga
14
test[.]nominally[.]ru
7
Files and or directories created Occurrences \TEMP\System.Data.SQLite.dll
69
\TEMP\EntityFramework.SqlServer.dll
69
\TEMP\EntityFramework.dll
69
\TEMP\Ionic.Zip.dll
69
\TEMP\System.Data.SQLite.EF6.dll
69
\TEMP\System.Data.SQLite.Linq.dll
69
\TEMP\x64
69
\TEMP\x64\SQLite.Interop.dll
69
\TEMP\x86
69
\TEMP\x86\SQLite.Interop.dll
69
%LOCALAPPDATA%\g1nz0l1s7
44
%LOCALAPPDATA%\g1nz0l1s7\Browser Assets
44
%LOCALAPPDATA%\g1nz0l1s7\Browser Cookies
44
%LOCALAPPDATA%\g1nz0l1s7\Desktop Files
44
%LOCALAPPDATA%\g1nz0l1s7\Screenshot.png
44
%LOCALAPPDATA%\1337holdthismoney
25
%LOCALAPPDATA%\1337holdthismoney\Browser Assets
25
%LOCALAPPDATA%\1337holdthismoney\Browser Cookies
25
%LOCALAPPDATA%\1337holdthismoney\Screenshot.png
25
File Hashes 03b205636ddacee2791b3bea1bc540c52dbf764d263ff7e6b78e339976bbf1bd
03ed8536f865b257cb84d00578d68b30f7e4f5e2b8b11ea2c536f4a73fcc88bc
0651a3d54f5d93d46b458c172788bc789310228f66f52adeed3f5b14f3926020
071463e9857ac23eb26297a19681e96be05122bf1e42f79fa2804b2e7df4deab
0757ed3e6a6a99d98abae124a05ee33e191fd42481e9f9af456ea5d87cb0256f
07d45e42c071baed5f213a9cb454f423558dd8d227b5a385b5eea836166ed2a3
07d4eb068b92809328866c660e46882d3a056e86ea55aee5b564ea54a9cb16f1
07dd67ea6bec0584094609bee43a10b3a9f43cbb015e82987ebeb5c411af91d9
08994b0dd47da89a34c9bbbe8e15bb03150d1823a3daac94e86ce333964727ba
089988b533e82f9d61020b3b6979bc61aa693d163f398e0a9054fd6e64a29b4b
09a45da2f4cc0f91e3a6af29095f73607287871573828495d1cd8679f00ee197
0a52a1b56ac888497a88371c954325d312eae19cad14460b572aac8c5ac37d6d
0b2d71a663e60bb5cca8f76d2fd23468a8cc74b199bb382305c7412aceb3f63d
0c8ef4eda585236858772e3bd0f981a5aeec797a5af7888a6ca9c71a9de6c274
1008d9650c0b5b87e4791b18dad3458ee2cc0fe29a7262a86a4a83308c5fcfc3
10ad3015e2d6967c07d012358fcdae6f02f57e69616b0a91c0e6cdf6b683e9c3
121377d50799144f5d718ba9c1e805915fc3bd9d7594eb6115acd09e3d76f7d5
1300417d32610e74c37897b0e1f73efd9edeea5ded6052cf093e0555e685df2f
1394fe31d98ae7f742189f75e1ee7f0593540b79a46ffe07d61d4397de0f12c1
139e428d990500159cc153a5c1cd4558026542ed4c51dbd88e884e0c14f5f3a2
1432f96255366adb5119d016f627bf241da64b3d5aba0dc9e8e5bc941f138c02
154f79f3ca1f9eb8ec8fb728f038cfdf5ef83139cfa3f8b8f484bf7154817007
16f56872942abbf6b94ab2993cc94039d99ac7288af5f5368184c9e587bd0230
178a7baba15d9bfde158fb181b45b7e12dbccbc49c2d7f27c1b5f2728b9dec24
18d541517e2f22e05b92f1e29cba6a06a155892d61c8bd24a56ccf5ba2ea7070*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Downloader.Upatre-9952018-0 Indicators of Compromise IOCs collected from dynamic analysis of 24 samples IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 35[.]214[.]107[.]94
15
23[.]46[.]150[.]48
8
23[.]46[.]150[.]72
4
23[.]46[.]150[.]40
3
154[.]215[.]59[.]219
2
52[.]213[.]114[.]86
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences apps[.]identrust[.]com
15
rockeyracing[.]com
15
zombies7[.]in
6
sicherhosting[.]com
3
Files and or directories created Occurrences %TEMP%\hfdfjdk.exe
15
%TEMP%\ckjienn.exe
15
%TEMP%\zfbttcb.exe
6
%TEMP%\ttcbnaf.exe
3
File Hashes 032361585c4487032050c334cfb78e5b8edc2e1610f97830ba467356caa3f193
3976d442387200f662450deff6768a2299cc1cb7d94a7ddf70909ddfdf49ca45
44066b4808e35af43e2fcee023d20b7ba438ad2f13b6dba08b6d35ec70fe403e
46391535b45440cb62d8c18744bbdbe7a242df9d4a4c0005d6d3b257a4d2e3c7
4af32df9cfe6fe35d9f8e5d3e0fb46476fd4c21c3e68037f3d0b5379ff536110
4cf842c6025d44f8be0b85e0092a771c9bdec5f196c71dac88fa28280100b0d2
52295e1b2bde64f718c7985f9c6f79e23393b654d8e7b0161c9e372179c24e17
55b0245f06465a8e77cbab31dc2a600ac9898e86c70619a02c6cf65918960c77
666b205e8e91fa93a3a1c878ea239b93cd27e16aff0a88bd2b7bb2b82f5938c9
6e784398efa3b2695ed611f5b68a53ec31c90ecf2a17c9a6b89298918f7630d3
77f1680ed8ee17748450c70d477a58e6ff91184e2ac4aa2d2d91cd048150033a
7fcad26eb3223f272fcf8a31edebaf47e57f22f0f1f0a34bf9dda82f3c059291
93cfafab66104586e86e374c87058dda3fdb30144e36f15fe93926eefb4a954e
9594627b8e114f854ba424c21c4025a65491d86c43970431763f2538da464450
a68dc6367e9c209cb7a48106994e1f044383d0ba5fa58dd75db434e5a923cbb5
a6d0a7ee0c2ce3302af44fba3ae335e55b8b42e2cc0a80e8c7ae9637648fa721
acde6674eff9d4076cf9248bef4e1f8aff56bd7ce5be48330f6c46fa4af19e27
ad60f1a6f5155aba8c292565ac0556876f5d1bbea94fb6225ac51482469854ce
b365de55ba86c89f92a2180fd82d8568cbe61e25f3d5d02f1b6449dc7b889aff
bbeb8dc47bd3921abc9922f0a2a47765c83b17be1b5d0d14645adf27b7b1fc31
c7b4f5770fd0a8143aab1ce2e398569e1d8942f8ebd14ef78dd88445cbf80d35
ca35cb7e503469cee1f71b332029922b846d11449287f4a5fffe260ee2472af3
ebc5dd9d017cc04deacfd74c10c777315e69361dddb8ce041b9df341c01e00ea
f1e581da8776165ebcd36e1b33dbefa8951ea6b18da4ca035552a6bb64a4e444Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Trojan.Zbot-9951812-0 Indicators of Compromise IOCs collected from dynamic analysis of 25 samples Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\TRACING\RASCCP
Value Name: FileTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASCCP
Value Name: ConsoleTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASCCP
Value Name: MaxFileSize
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASCCP
Value Name: FileDirectory
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\SVCHOST_RASCHAP
Value Name: EnableFileTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\SVCHOST_RASCHAP
Value Name: EnableConsoleTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\SVCHOST_RASCHAP
Value Name: FileTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\SVCHOST_RASCHAP
Value Name: ConsoleTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\SVCHOST_RASCHAP
Value Name: MaxFileSize
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\SVCHOST_RASCHAP
Value Name: FileDirectory
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\VPNIKE
Value Name: EnableFileTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\VPNIKE
Value Name: EnableConsoleTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\VPNIKE
Value Name: FileTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\VPNIKE
Value Name: ConsoleTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\VPNIKE
Value Name: MaxFileSize
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\VPNIKE
Value Name: FileDirectory
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPHLP
Value Name: EnableFileTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPHLP
Value Name: EnableConsoleTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPHLP
Value Name: FileTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPHLP
Value Name: ConsoleTracingMask
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPHLP
Value Name: MaxFileSize
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPHLP
Value Name: FileDirectory
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPCP
Value Name: EnableFileTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPCP
Value Name: EnableConsoleTracing
25
<HKLM>\SOFTWARE\MICROSOFT\TRACING\RASIPCP
Value Name: FileTracingMask
25
Mutexes Occurrences MSPMutex
25
__SYSTEM__91C38905__
25
__SYSTEM__64AD0625__
25
Domain Names contacted by malware. Does not indicate maliciousness Occurrences de-openphone[.]org
25
Files and or directories created Occurrences %ProgramData%\Microsoft\Network\Connections\Pbk\rasphone.pbk
25
%SystemRoot%\SysWOW64\drivers\wsnpoem.sys
25
%SystemRoot%\SysWOW64\wsnpoema.exe
25
File Hashes 000e1cbc44ed0a94ca14ec39365c855a0a55fb5743ddcdc97d30020455248afd
012ca5ea88823d788ff795874809dae14c728e992b238cb2bf8ad38fa5bc16d4
0264a42001ae18cb0b93862aa1399be459f0ef43e6b4d51547e85f61947cfccf
037fdfe3bb7b55d2620f51e47023c7049afa10a6bb8bec989755fe60cad1b189
06262d80ef61a3e0e1b0a320834ac19b77f4e4dd250fb2b450e86d6c0e28f756
06364fd3a597c39708fced04f51657a71f105ffd8aac7235c248c5e1420904d7
07156d07e6fd2e1042d80069792284963951282aa103bde9111730c822c9f053
08ab8161c2f8b2cbef148fc41241c86f6e139442a9fd5f677fc3e7fe90dcf1d4
08fbf9cb9e84cf1fff69aabdb2d8d6ae9ff8d0728e80c539bb8468d6a09a28f8
0abe8c8e5f6100ce75900f8c12bbc37276e035522abc1d5c766c29c80df84d8b
0b547ec58c5e58cc22483c79822844b3d6e068a85bd879890a4555794ea3016b
0d97de762aad1f9bdc4719954adaf28c2f291eb761affb4474ad1ccf53d5176d
0e7480bf43861f281a20f05f44af294c48e1a9d4d119883e1820ad9128defcd6
0eae038f213da1fca9f5ce3cec70ead818130d36856f56206a8e88d1c3f5e7ce
0eb42d0f19b56aeecce6f0baca195cc0fccdd1c463528dc1de3e6444dd9de217
0f42370af3c7bf40b88f5cf2c77a8cf6da14a47e6d8db70a3cc51a2b00c364ee
0f641e9099e5eca41973e8f784edcd072474486eede9aac1f80d80f5e40e35e6
102a4e2988231a2448060457a75accc4016b9cf0e8d16d99789857981420fdf1
10b40225a1b941278979a70415ff2097820f911f7a722f036a914b80fdbae084
12c72898aa3b9ae1e9a372a151b67dc7c95a1409936180742acd5f4d1b20a684
142077ea439b03324f37a5010ccc3909daf1f1fb7ac9a478af7e851f490fd05d
1543751eef535b2b1b44bebe0051dc266414dd45b018139841784b0b556e282f
1594db35d07b4883d54ae197bf9e8386ec3631791c85fd155355923c827074ec
15b84c3a0140f74ede164b2de716df08ca71d8c1076abdaefb7b99f48dad5f84
169cee6a6c35d47fbe9cc192c32aeaa607f01e810936e0593bb0eae5cae8f1f5*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Packed.njRAT-9951863-1 Indicators of Compromise IOCs collected from dynamic analysis of 28 samples Registry Keys Occurrences <HKU>\S-1-5-21-2580483871-590521980-3826313501-500
Value Name: di
28
<HKCU>\ENVIRONMENT
Value Name: SEE_MASK_NOZONECHECKS
28
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: ParseAutoexec
28
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: ruuvcdjrlxftqnh
28
<HKCU>\SOFTWARE\98837D34F177F6CAE60B03C4B7735AB8
28
<HKCU>\SOFTWARE\98837D34F177F6CAE60B03C4B7735AB8
Value Name: hp
28
<HKCU>\SOFTWARE\98837D34F177F6CAE60B03C4B7735AB8
Value Name: i
28
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 98837d34f177f6cae60b03c4b7735ab8
28
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: 98837d34f177f6cae60b03c4b7735ab8
28
<HKCU>\SOFTWARE\98837D34F177F6CAE60B03C4B7735AB8
Value Name: kl
28
Mutexes Occurrences 98837d34f177f6cae60b03c4b7735ab8MTJBR09TVE8tUEM=
28
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 192[.]169[.]69[.]25
28
Domain Names contacted by malware. Does not indicate maliciousness Occurrences orlandorojast85[.]duckdns[.]org
28
Files and or directories created Occurrences %APPDATA%\ruuvcdjrlxftqnh
28
%APPDATA%\ruuvcdjrlxftqnh\ruuvcdjrlxftqnh.bat
28
%APPDATA%\ruuvcdjrlxftqnh\ruuvcdjrlxftqnh.exe
28
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\98837d34f177f6cae60b03c4b7735ab8.exe
28
File Hashes 02ced158fff33e644e10bd5c9faaacf5100aa45ec91b8b300408b3a21ea49d52
0a983b8a14ef1b253f058c3f17d1650109ce6ad5c8cf9c2fb9fa9bbbcb7778aa
128514af952bca2de0cea5b7cc6179a2f30ebaae2766ca1bc5dcf1dd333ebf03
16ee2defda09e350b8f3c6b206cb909a3ab25606943332390047c4366e807fe4
16ee3f8510c547b93f9d561b9ea803657557415ac333a8d38fc9b6fbe909a4f7
171e17c3bc3f1c503ae40f93fb74aebd5c60509fa91df6503824499762822ece
1b8654d6f1917924a744f42429a6341d1f61620b8499c26dc2ea9e9c3fc9445d
282c5061cfef77fb339cd138c8f2b1a13f511bfc0339951becde8f02e5da8e92
2967843b041f3441f8e7372545a8e2f7b8009499657b3a8ff77d5a71c6dcc31e
37335b068fdf004c732cc8f836d467e12891013856bacaf11618a8efb1d60539
376a1fc3bd286dfd0be98040b1c2bb4461d4a7ca532214bfe499f75c10e195b3
3c65fa09f187426ceba6b8522e41f2a6418e15dee31d2a66822e25ce6d2ae5ee
450dff9908f7866ef255f1c9f242ed604d42e82ea79ed9d02765ac40aca0461b
46f3651fd3412b2bb58e2ca699f1d56c35cb55221e3fe16fef7aaf784e297a61
4ad3fa204f00664652c8a9ba1b3bc9c6fc5f7c6ea0a6b7b3f17d15d1e783101d
526f22bf64336123dd9eadbbb88cd1329b67b465bead0d7f503a32cc7934c7f9
5ccbf25de465cd47cca9245cf5123c13858d0cc2bb24a6492816c6bca458b910
6c234e3722c1453d6d62e380b49e67625ab0293c45c2688dddf497f0e391eaf9
6cefd596e792526445b3923d3cf10f7e909cdc9de140ed2c5dd0c478bcf93ef6
7384160ecd4a3c883770c10ca3c9437cbe2bdffecea10016cbccf7601cae389e
7d3935c8afd9f897c760413a4d4e9ed9e2da918744061f8eebe43fe471eb49ff
7e15938bb7bf6f1bf2ac7a3b6b9b3edabf502c7ac4c23d3bc722e418b3d6cede
801880338338f355dc386717b6f13851858978d94751753e390f99e6ab7fe171
8648d3ae84b03c93792aeb5c33f4f172f0944cf3fd097ba70aab18074c4763d2
86af97977baa16148747a448bf7eca3231963368da48f1088a7ccbf2707f27f4*See JSON for more IOCs
Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
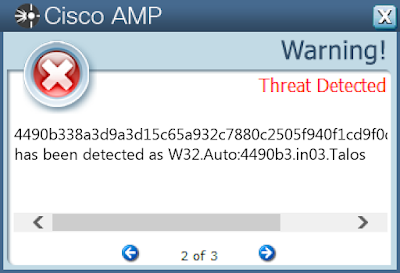
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK Win.Packed.Cerber-9951870-0 Indicators of Compromise IOCs collected from dynamic analysis of 13 samples Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}
13
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 194[.]165[.]16[.]0/22
13
17[.]1[.]32[.]0/27
13
78[.]15[.]15[.]0/27
13
Files and or directories created Occurrences %HOMEPATH%\Contacts\Administrator.contact
13
%TEMP%\d19ab989
13
%TEMP%\d19ab989\4710.tmp
13
%TEMP%\d19ab989\a35f.tmp
13
%LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat
13
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp
13
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp
13
%APPDATA%\microsoft\outlook\_README_B7BH9D_.hta
1
%HOMEPATH%\contacts\_README_PRGY_.hta
1
%HOMEPATH%\desktop\_README_D8HSYM_.hta
1
%HOMEPATH%\documents\_README_F3WMD_.hta
1
%HOMEPATH%\documents\onenote notebooks\notes\_README_UN1J_.hta
1
%HOMEPATH%\documents\onenote notebooks\personal\_README_W9D1Z_.hta
1
%HOMEPATH%\documents\outlook files\_README_EGQE_.hta
1
%LOCALAPPDATA%\microsoft\office\groove1\system\_README_OT63HA9_.hta
1
%LOCALAPPDATA%\microsoft\office\groove\system\_README_XAI61R3K_.hta
1
%APPDATA%\microsoft\outlook\_README_AUGGWE_.hta
1
%HOMEPATH%\contacts\_README_VCE2_.hta
1
%HOMEPATH%\desktop\_README_DGKOFZ_.hta
1
%HOMEPATH%\documents\_README_BB3H94_.hta
1
%HOMEPATH%\documents\onenote notebooks\notes\_README_7QM1M1_.hta
1
%HOMEPATH%\documents\onenote notebooks\personal\_README_Z1Y5_.hta
1
%HOMEPATH%\documents\outlook files\_README_WEYO0_.hta
1
%LOCALAPPDATA%\microsoft\office\groove1\system\_README_2WWE_.hta
1
%LOCALAPPDATA%\microsoft\office\groove\system\_README_FW0XKMN1_.hta
1
*See JSON for more IOCs
File Hashes 02f3f8d14acf7c5d5c026a449200bcbe0576ea66870d79e174e5f2349062bdca
198695e64c0d9f23120907d6c072506ae8f1387202cfc480137b922d6b29b975
21254357fd151284f0205b87e51512ab78098bb409017e8b41f4bc583acb046d
21719320102b6423c901aae016c18609f980baaf6d7f364ea7cc971b83c01478
4490b338a3d9a3d15c65a932c7880c2505f940f1cd9f0d99f5c7b240bd7e806f
7769b6f5d40c6de59400919f20c161cca9cbf3222ae70a46cf42e43367c64b4a
89cf0b7fc6f3d2a758985297d460b1ea242b4b0b6ea422fb1f049756b90f0c59
989c24c6641ace3db31890191b1eedab0490f480240eb9052cab8f483cd2706b
a864f5b878aa58fc2e381f4db133a52dfe9dd5a64b99c8f4b141e92dc6acf544
ab23c74b171bb64fd55cea933b7f9ccd4c1fecae6b6935df76123247f77f2ef3
c26259cfa6e203ea5f74a6823e7f463e2b148c37cc2a38391dc612efc84a6ba4
ddaac9de46f8fdfc04126f69f4940c6a4d2603bff3d92c41192335697d00bb2d
e45534dd14f2bb9a6a6cc3c5c1813b3e4b3fe4f74cbb8f9d8e38900f02f1d598Coverage Product Protection Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK