About two months ago, we found a vulnerability in the Winamp 5.55 MAKI script parsing module. We reported our findings to AOL. AOL then released Winamp version 5.552 with the fix. Here are the details:
Winamp MAKI Parsing Integer Overflow Vulnerability
Vendor:
AOL/Nullsoft
Severity:
High
Systems Affected:
Winamp 5.55 and prior versions that support Modern Skins.
Overview:
A vulnerability exists in Winamp. The vulnerability is due to an incorrect type cast while parsing a .maki file (a compiled script file), causing a buffer overflow. An attacker could provide a user with a modern skin (via a webpage download for example) that uses the maki script to execute arbitrary code within the context of the current user.
Technical Details:
Winamp’s modern skins scripting engine reads strings from the .maki file. The format of these strings is composed as follows (multi-byte values are in little endian byte order):
Offset Size Description--------- ------ --------------------------------------0x0000 4 Unknown (it seems to be a type code)0x0004 2 Length (Y)0x0006 Y Function name
When gen_ff.dll parses a .maki file, it reads two bytes and does a sign extension, which results in a stack buffer overflow.
The following shows the local buffer size (0x10008):
.text:12094DAB var_10144= byte ptr -10144h.text:12094DAB MultiByteStr= byte ptr -13ch
If a string size is greater than or equal to 0x8000, edi will be 0xFFFFhhhh (where, 0xhhhh is the two byte input)
.text:12094F62 loc_12094F62:.text:12094F62 mov ax, [ebx].text:12094F65 movsx edi, ax ; sign extension.text:12094F68 inc ebx.text:12094F69 push edi ; Size.text:12094F6A inc ebx.text:12094F6B lea eax, [ebp+MultiByteStr].text:12094F71 push ebx ; Src.text:12094F72 push eax ; Dst, buffer is located in the stack.text:12094F73 call memmove.text:120951E5 loc_120951E5:.text:120951E5 mov edi, [ebx].text:120951E7 add ebx, 4.text:120951EA mov ax, [ebx].text:120951ED movsx esi, ax ; sign extension.text:120951F0 inc ebx.text:120951F1 push esi ; Size.text:120951F2 inc ebx.text:120951F3 lea eax, [ebp+var_10144].text:120951F9 push ebx ; Src.text:120951FA push eax ; Dst, buffer is located in the stack.text:120951FB call memmove
Reproduction:
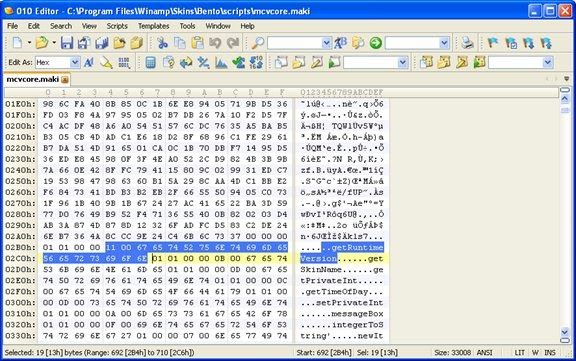
I used the Bento skin’s maki file. The highlighted text in the following figure shows the two byte size (value is 0x0011) and the following 17 characters. I changed the size to 0xFFFF and inserted a lot of 0x41 (obviously more than 0xFFFF). Then BANG! EIP was overwitten with 0x41414141.
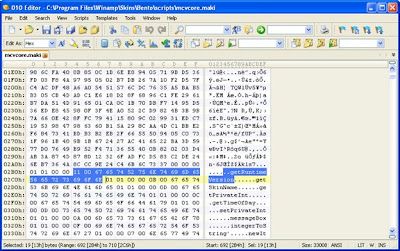
Resolution:
Sourcefire released detection for this issue (gid:3 sid:15433) on 2009-03-31
Vendor released Winamp 5.552 on 2009-04-11
Update:
This issue now has a Bugtraq entry, available here: http://www.securityfocus.com/bid/35052