Executive Summary The holidays are upon us and the shopping season is kicking into high gear. This year, an estimated 270 million consumers will shop online and, for the first time, more than half of them will use mobile devices to check off their holiday shopping lists.
With consumers searching for holiday discounts through display ads, social media and email, Cisco Talos Security Intelligence and Research Group predict that both malvertising and email spam will be significant vectors for cyber crime this season — especially for mobile shoppers. This is worrisome for the simple reason that most mobile devices do not posses the ability to block many of these threats, leading to increased vulnerabilities as attackers seek profit gain during the busiest time for online commerce.
Through their research, Talos found that Android users are particularly vulnerable. Of the all Apple and Android OS blocks observed on the Cisco's Cloud Web Security (CWS) platform, the Talos team found that nearly 95% were Android-related. At the heart of the problem, many users are running significantly older versions of the Android OS, which lack the security updates for today’s most persistent threats. This holiday season, we advise that our mobile shoppers exercise additional caution.
Keep reading for more on our findings and recommendations.
The Holiday Shopping Landscape Adobe recently published their “2015 Holiday Shopping Predictions” report, and a few of their predictions have direct implications for online security while Internet shopping this year.
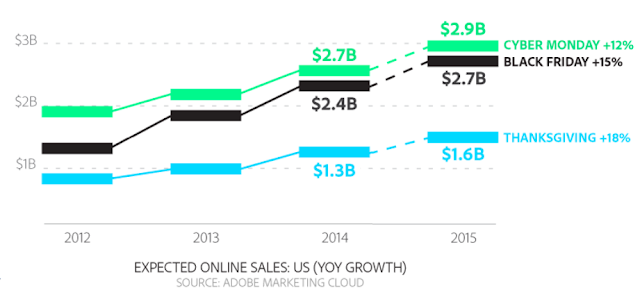
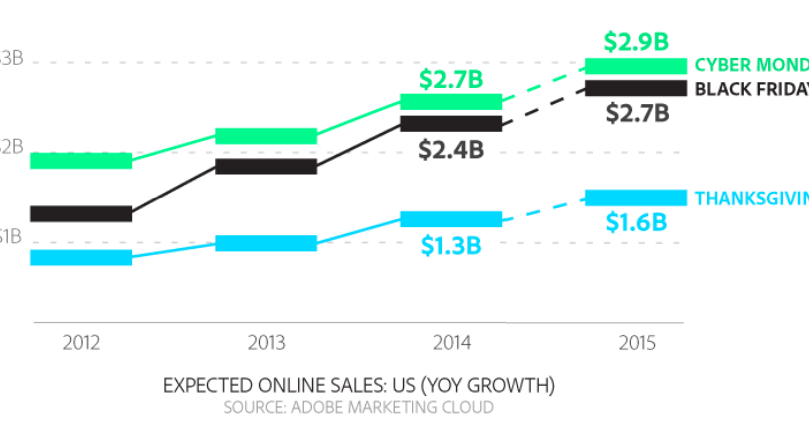
During the holiday season, Adobe expects the total scope of online shopping in the United States to be $83 billion dollars (up 11% from last year). The report also indicates an average spend per Internet user of $305. Doing the math, this means we could see more than 270 million online shoppers --an enormous target for attackers. As shoppers we must do what we can to minimize the risk of becoming the next victim.
Shopping While Mobile One key prediction from Adobe’s holiday shopping report is that for the first time mobile devices will drive a majority (51%) of online shopping traffic. On the surface this is worrisome because many mobile devices are not configured to block advertisements, including malvertising. Further complicating the mobile ad-blocking scene is the fact that some popular ad-blocking apps require customers to proxy all of their web traffic through a third-party host so ads can be removed. This presents obvious data privacy complications for users of these apps regardless of their desire to eliminate advertising or protect themselves. There are some non-proxy-based alternatives, such as the new iOS 9 Safari Content Blocker extensions. All users of both mobile and non-mobile devices are encouraged to use some sort of ad-blocking software or plugin to protect themselves from the threat of malvertising.
With so much shopping traffic expected to come from mobile devices, it’s important to gauge what sorts of devices will be used. According to the market intelligence firm IDC, when it comes to smartphone OS’s, the worldwide market share for Android OS is a whopping 82.8%, followed by Apple’s iOS with a 13.9% market share. Other smartphone OS’s such as Windows, Blackberry, etcetera, are all in the single digits or less, so we won’t focus on those for the purpose of this analysis.
The fact that so much of the mobile market uses Android is somewhat troubling. Many Android mobile devices lack the capability to patch vulnerabilities in the operating system without an update from the OEM/carrier, which means they will likely still possess significant unpatched vulnerabilities as they traverse the Internet and make online purchases. Further, most Android users are running old versions of the operating system, as illustrated by this data from droid-life.com.
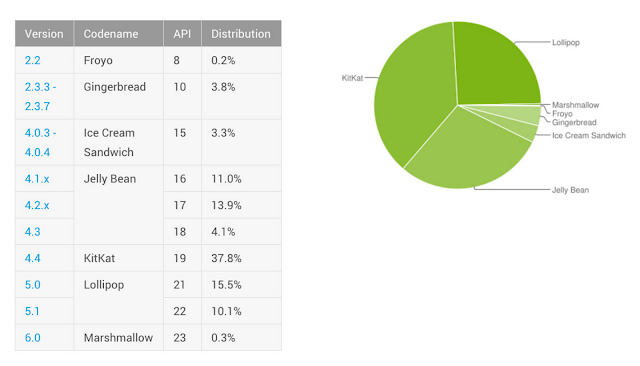
|
| November 2015 statistics on the distribution of Android OS versions from droid-life.com |
After reviewing Cisco’s own Cloud Web Security (CWS) data for the last six months, we find that 12.2% of all blocked HTTP transactions are attributed to either an Android, iPad, or iPhone device. Among those Android/iPad/iPhone mobile-related CWS blocks, an overwhelming majority (94.8%) were Android-related.
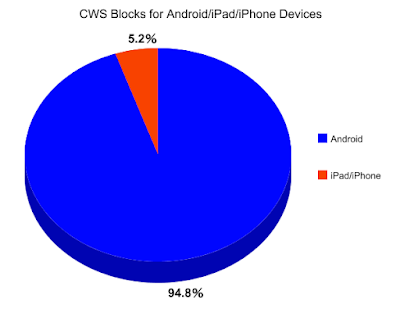
Additionally, corroborating the data from droid-life.com, the Android devices found in the blocked HTTP transactions were running significantly older versions of Android OS; we found most devices that encountered CWS blocks were running Android OS versions 4.2.2, 4.4.2, and 4.1.2. (The most recent version of Android is 6.0). Lamentably, the only way for many Android users to upgrade their OS software is by purchasing new hardware, which is the sort of planned obsolescence that seems to suit everyone, except the end-users.
Additionally, when Talos checked the CWS blocks for Android OS devices specifically, we noted a significant increase over just the past few months --right in time for the holiday shopping season. It is important to note that this increase in attack activity is not likely related to shopping itself; The point is that no one wants to be doing their shopping, entering personally identifiable information (PII), and credit card information, using a device that has been compromised.
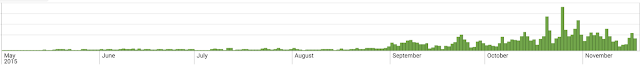
Clearly, based on the available data, when shopping this holiday season our friends running Android based-devices should exercise additional caution.
Vectors for Badness™ The Adobe report claims that holiday shoppers will be finding their steep holiday discounts primarily through display ads (23%), followed next by social media (14%), and then email (11%). Because so many threats propagate through spam, social media, and malvertising, the safest way to shop this season is directly purchasing goods from the merchant’s website.
Mobile shoppers will want to exercise extra caution when finding holiday deals on social media. When we checked the last six months of iOS-related blocks having a Referer HTTP header, 29.7% of the time users were referred to the blocked content by m.facebook.com --Facebook’s mobile site. Android users didn’t fare much better with blocked content coming from m.facebook.com in 22.5% of the HTTP Referers.
Conclusion Nobody wants to be the victim of cyber crime. To protect ourselves, we should deploy an array of different security layers.
Talos recommends use of secure web proxies like Cloud Web Security (CWS) or Web Security Appliance (WSA). OpenDNS can provide security at the DNS layer. Secure email gateways like the Email Security Appliance (ESA) can protect against illegitimate holiday deals propagated through spam. Advanced Malware Protection (AMP) at the network or endpoint can convict malicious binaries that might somehow make it past the other layers. Local browser client protection from "ad blockers" such as Ghostery, Adblock Plus, NoScript, Request Policy, and others is also highly recommended.
Finally, beyond all the technical layers that can be deployed, we need to be smart. Especially when performing activities such as shopping, it’s far safer to navigate directly to merchant websites than risk being lead to malvertising in the form of online display ads, fake email offers, or malware disguised as social media promotions.