Tax time in the US is quickly approaching. Everyone should be on the lookout for scams that are designed to trick you out of your money and personal information. The IRS is warning users about an increase in the number of email scams being used this year. However, these attacks are no longer limited to just the United States. Earlier this year we notice tax phishing campaigns targeting Ireland. Therefore, we decided to take a look back over the last year and see how widespread tax scams have become. We quickly realized that tax scams have gone international and now impact numerous countries across the world.
To give you an idea of the scope of the problem that we uncovered, our post will look at tax phishing campaigns from the following perspectives:
- Tax Related Domains
- Countries Impacted
- Attack Techniques
- Timing of Attacks
- Interesting Twists
Tax Related Domains
One technique that threat actors use to trick users is to create domains that are very convincing. With taxes, obviously creating a domain with the word “tax” will likely make the domain seem more legitimate. Therefore, we decided to use Domain Tools to look for domains that have been registered since January of this year that begin with “tax”. Our search returned 122 domains that had a risk score of over 50 on a scale from 1-100. The domains included names such as
- taxreliefideas.com
- tax-due.info
- taxrelieffacts.com
Obviously, this is not even close to a comprehensive search of domains that appear to be related to taxes. But even with the domains from our quick check, it is clear that these domains are registered across the world and not limited to any geographic region.
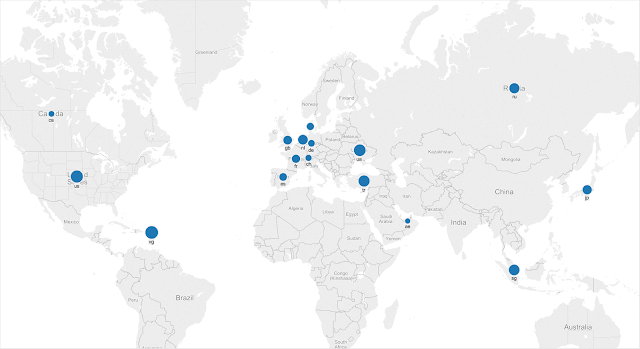
Countries Impacted
Just as our initial domain search revealed domains spread out across the world, our examination of actual phishing messages also revealed a similar global impact. We started by doing searching for subject containing the phrase “tax refund” in the following languages:
- English (tax refund)
- Swedish (skatteåterbäring)
- Italian (rimborso fiscale)
- Danish (tilbagebetaling af ska)
Researching our data for 2015, we observed campaigns targeted against the following countries: - United States
- United Kingdom
- Canada
- Ireland
- Denmark
- Australia
- Italy
- South Africa
- Sweden
Most of the phishing attempts are in English except for the emails targeting Denmark, Italy and Sweden.
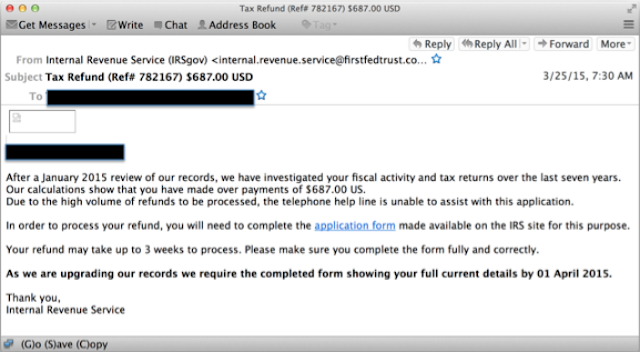
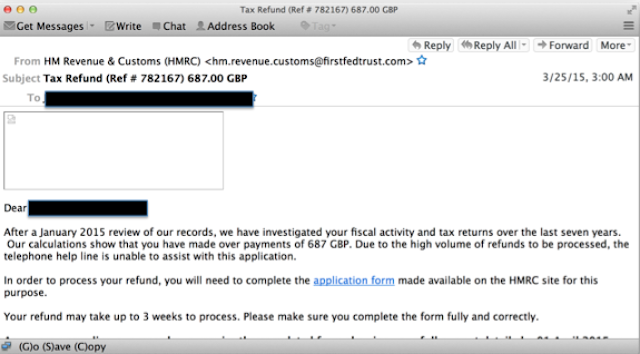
In our research, we examined numerous phishing campaigns. Most of the campaigns did not have any clear similarities indicating that they were initiated by the same threat actors. One campaign from March of 2015, however, was interesting in that a very similar message was being sent to multiple countries. This campaign targeted the United Kingdom, Canada and the United States at the same time. Based on the similarity of the messages, It appears that the same threat actor was behind all of these messages. Each of these messages mentioned an audit of the last seven years and the target receiving a refund. The text of each email is essentially identical except for country customizations, such as the different currencies for each country (GBP for UK, CAD for Canada, and US for United States) and different tax agencies.
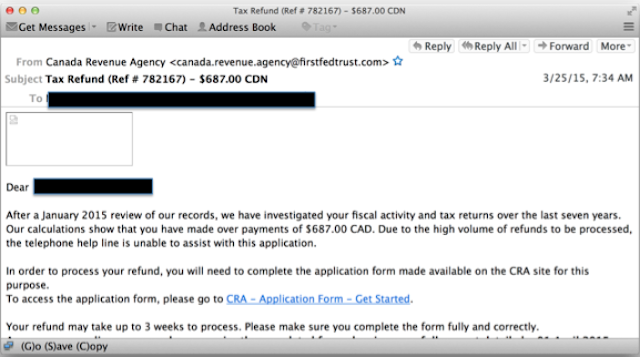
Attack Techniques
All of our research was focused on using email as the initial infection vector. To trick the users, the threat actors utilized both messages with attachments, as well as messages containing links to sites housing malicious content.
Attachments
The attachments that we examined fell into two different categories. The first group involve sending the user an attachment that contains malicious content. These attachments varied. Sometimes the email would have a executable file hidden inside of a zip file. Another common approach was to embed malicious macros into a Word document. The common factor in each of the attachments was that it included some type of malicious content designed to take effect when the user opened the attachment.
In other situations, the threat actors attempted to get the user to leak sensitive information by utilizing an HTML attachment that looks like a legitimate form, and depending on the mail client may even render as part of the email message in the mail client. In these situations, the threat actors attempted to make the form appear to be as legitimate as possible, frequently utilizing images from the site that they were impersonating. When the user clicks submit (after entering sensitive information), that information is sent to some compromised website, adding to the attackers collection of compromised accounts.
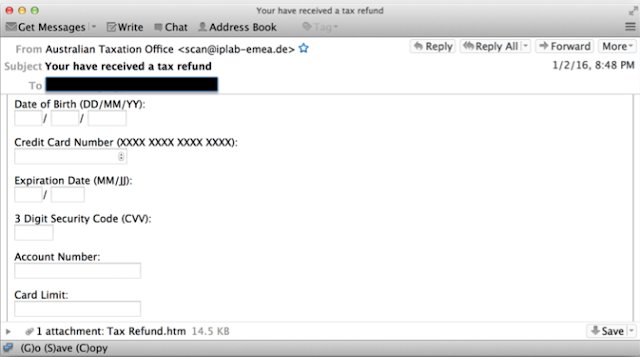
Malicious Links
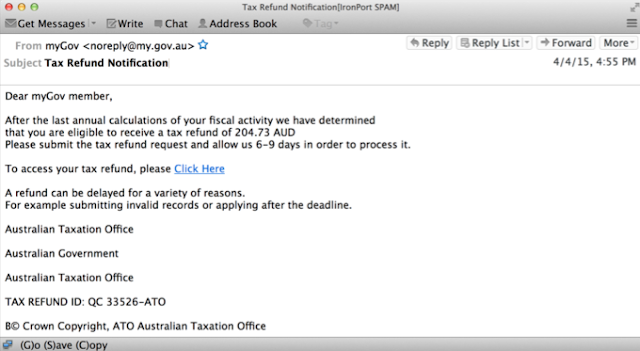
Everyone knows that scanning an email message for viruses has become a standard security procedure to enhance email security. To avoid this scanning, many threat actors are now using malicious links to lead the users to their malicious content, instead of including an attachment that may draw unnecessary attention. Other times, the link simply redirects the user to an HTML form to capture sensitive user information (instead of including the HTML file as an attachment to the email).
Timing of Attacks
You would expect to see these attacks shortly before the tax deadline for a specific country. During our research, however, we noticed these phishes continue throughout the year. Seeing these campaigns a couple of months before a tax deadline is obvious, but threat actors initiating campaigns months after the tax deadline as well. We saw a phish that was sent a couple months past the tax deadline indicating that the user is entitled to a refund because he overpaid his taxes.
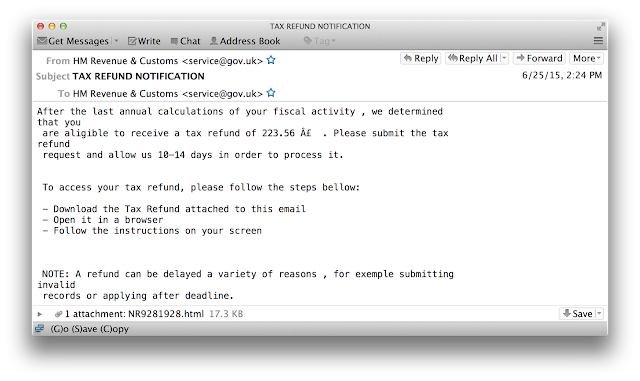
Attached to the email is an html attachment that requests the following information from the victim:
- Gender
- Full Name
- Date of Birth
- Identification (Passport or Driver’s License)
- Identification Number
- Address
- Phone Number
- Credit Card Number
- Security Code
- Sort Code
- Bank Name
- Account Number
If the user fills out the form and clicks submit, then his data is sent to
hxxp://americasfootcenter.com/kindox.php
Interesting Twists
Besides just impersonating the official tax agencies in various countries, the tax scammers have also attempted other tricks to deceive users. An interesting phish we observed was the IRS supposedly forgiving the tax debt as shown in the following email.
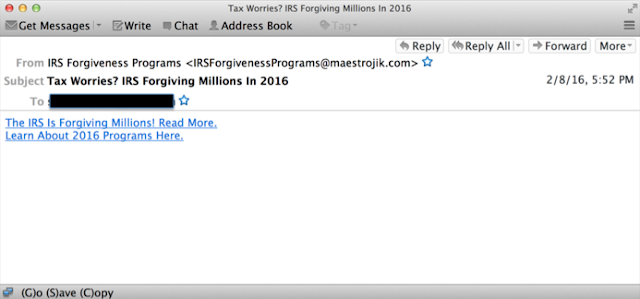
Another twist was emails claiming to provide seminars on updates to the tax law. Some of the titles for these emails include
- Handling Federal and State Tax Levies With Ease. Register Now!
- IRS: Tax and Payroll Updates for 2016
- Reminder: Annual Tax Update Here is a sample of an email from South Africa that claims to provide seminars on tax law updates.
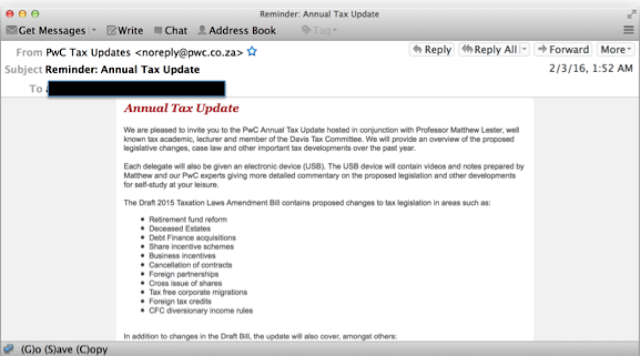
But instead of link to real seminars, the users are redirected to malicious links such as
hxxp://is.diez.penamail.com/sendlink.asp?HitID=1454485845341&StID=37628&SID=14&NID=791054&EmID=35029178&Link=aHR0cHM6Ly9pbnZpdGUucHdjLmNvLnphL2ludml0ZS9hbm51YWwtdGF4LXVwZGF0ZS5waHA/aWQ9NzM1&token=17118fb09e25a6d01e8c8a550fe50d9f6f59f398
We even saw attempts to impersonate tax preparation software.
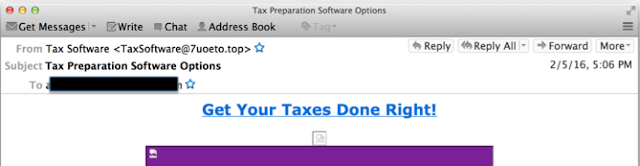
This phish attempted to get the user to click on a link which would redirect them to a link such as hxxp://www.7uoeto.top/l/lt1O920BW86YE/86M578KK580U40WW477112XN3411156693 Other attempts even claimed that you account was locked or that you tax software needs to be updated as in the following subjects:
- Important - Your TurboTax Account is Locked
- Your TurboTax Update
- A Very Important Information From TurboTax A final interesting twist was emails that pretended to be from the IRS and claiming that the user was the victim of identity theft and needed to act quickly to safeguard their information.
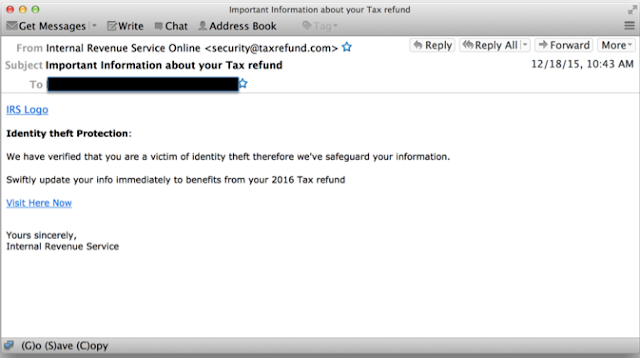
IOCs intregup.com www.7uoeto.top
timbresat.com
quggyiz.nogaarikha.com
www.bollyauk.ru
www.agro-lux.com
ato.gov.au.26p214b583k7a0z01473.cgovtt.info
avantgardetekstil.com
accounts-hmrc.gov.uk.sms4.xyz
sirjupiter.com Claim your tax refund
You are eligible to receive a tax refund
Tax Refund Notification Australian Taxation Office tax refund confirmation!
Tax Refund New Message Alert!
Tax Refund (Ref # 782167) - $687.00 CDN
Tax Refund (Ref # 782167) 687.00 GBP
Tax Refund (Ref# 782167) $687.00 USD
Tilbagebetaling af skat - DKK 7122,00
Skatteåterbäring: 6120.20 SEK
Rimborso fiscale per 2014-2015
Conclusion
Scammers are constantly trying to steal your money and identity. As we approach the tax deadline in the United States it is important to remain vigilant and to think before your click on that link or open that attachment. But as we have seen in this post, these phishing attempts are not limited to any specific country but impact users across the world. Having a strong layered approach to security is more important now than it has ever been.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
The Network Security protection of IPS and NGFW have up-to-date signatures to detect malicious network activity by threat actors.
ESA can block malicious emails sent by threat actors as part of their campaign.