'Magic Hound' is the code name used to reference a seemingly limited series of malware distribution campaigns that were observed targeting organizations in Saudi Arabia as well as organizations with business interests in Saudi Arabia. Similar to other malware distribution campaigns that Talos has observed and documented, this series of campaigns made use of phishing emails containing links to malicious Word documents hosted on attacker controlled servers. When opened, the malicious documents display a message instructing the user to enable macros in an attempt to entice recipients to execute the attacker's scripts and download additional malware, thus infecting their systems. Unlike some of the more sophisticated campaigns seen in the wild, in the case of 'Magic Hound' the attackers made use of commodity malware and tools. This included tools such as IRC bots and Metasploit Meterpreter payloads as well as an open source Remote Administration Tool (RAT).
Talos is aware of this targeted campaign and we have responded to ensure that customers remain protected from 'Magic Hound' as well as other similar campaigns as they are identified and change over time.
Coverage Coverage for 'Magic Hound' is available through Cisco security products, services, and open source technologies. Note that as this threat evolves, new coverage may be developed and existing coverage adapted or modified. As a result, this post should not be considered authoritative. For the most current information, please refer to your FireSIGHT Management Center or Snort.org.
Snort Rules
- 41655-41659
AMP Detection
- W32.C21074F340.magichound.hunt.talos
- W32.EA139A73F8.magichound.hunt.talos
- W32.DA2ABDC951.magichound.hunt.talos
- W32.0D3AE68286.magichound.hunt.talos
- W32.F0ECC4388F.magichound.hunt.talos
- W32.860F4CD443.magichound.hunt.talos
- W32.B42B118621.magichound.hunt.talos
- W32.4BEEE6E7AA.magichound.hunt.talos
- W32.5E0E09C986.magichound.hunt.talos
- W32.3161F9087D.magichound.hunt.talos
- W32.B6C159CAD5.magichound.hunt.talos
- W32.6A7537F2CE.magichound.hunt.talos
- W32.16D87FBD86.magichound.hunt.talos
- W32.92BC7D0444.magichound.hunt.talos
- W32.86D3409C90.magichound.hunt.talos
- W32.C3A8F51763.magichound.hunt.talos
- W32.A390365DDF.magichound.hunt.talos
- W32.D2FFC757A1.magichound.hunt.talos
- W32.79C9894B50.magichound.hunt.talos
- W32.2F7F358250.magichound.hunt.talos
- W32.8C2E4AA8D7.magichound.hunt.talos
- W32.ABE8E86B78.magichound.hunt.talos
- W32.9E4D2E983F.magichound.hunt.talos
- W32.E57F77CC3D.magichound.hunt.talos
- W32.CA6E823DED.magichound.hunt.talos
- W32.EAAECABB43.magichound.hunt.talos
- W32.1C3E527E49.magichound.hunt.talos
- W32.29A659FB0E.magichound.hunt.talos
- W32.218FAC3D06.magichound.hunt.talos
- W32.E5B643CB6E.magichound.hunt.talos
- W32.71E584E7E1.magichound.hunt.talos
- W32.388B26E22F.magichound.hunt.talos
- W32.33EE8A57E1.magichound.hunt.talos
- W32.5469FACC26.magichound.hunt.talos
- W32.528714AAAA.magichound.hunt.talos
- W32.66D24A5293.magichound.hunt.talos
- W32.CFCE482710.magichound.hunt.talos
- W32.68DB2B363A.magichound.hunt.talos
- W32.E837F6B814.magichound.hunt.talos
- W32.F912D40DE9.magichound.hunt.talos
- W32.AF0AE0FA87.magichound.hunt.talos
- W32.6D1A50CA3E.magichound.hunt.talos
- W32.6C195EA18C.magichound.hunt.talos
- W32.97943739CC.magichound.hunt.talos
- W32.7E57E35F8F.magichound.hunt.talos
- W32.DB453B8DE1.magichound.hunt.talos
- W32.82779504D3.magichound.hunt.talos
- W32.1C550DC73B.magichound.hunt.talos
- W32.7CDBF5C035.magichound.hunt.talos
- W32.B2EA3FCD2B.magichound.hunt.talos
- W32.3F23972A0E.magichound.hunt.talos
- W32.133959BE83.magichound.hunt.talos
- W32.BA3560D3C7.magichound.hunt.talos
- W32.D8731A94D1.magichound.hunt.talos
- W32.D08D737FA5.magichound.hunt.talos
Domain/IP Address Detection
- analytics-google[.]org
- microsoftexplorerservices[.]cloud
- msservice[.]site
- service.chrome-up[.]date
- service1.chrome-up[.]date
- servicesystem.serveirc[.]com
- syn.timezone[.]live
- timezone[.]live
- www.microsoftsubsystem.com-adm[.]in
- www1.chrome-up[.]date
- www3.chrome-up[.]date
- www5.chrome-up[.]date
- www7.chrome-up[.]date
- 104.218.120[.]128
- 104.238.184[.]252
- 139.59.46[.]154
- 45.56.123[.]129
- 45.58.37[.]142
- 45.76.128[.]165
- 69.87.223[.]26
- 89.107.60[.]11
- 89.107.62[.]39
Other Mitigation Strategies 'Magic Hound' is an attackers continuing to make use of phishing emails and social engineering in an attempt to gain a foothold into organizations' networks. It also highlights the need for a comprehensive strategy to combat spam and phishing emails as well as a security awareness program. Links contained within emails from unknown or unverified sources should never be accessed.
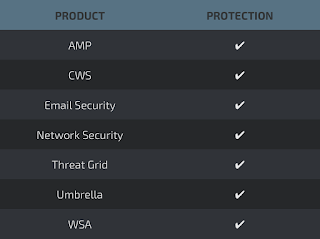
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
The Network Security protection of IPSand NGFW have up-to-date signatures to detect malicious network activity by threat actors.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella prevents DNS resolution of the domains associated with malicious activity.