Over the past week, information regarding a serious zero-day vulnerability (CVE-2017-0199) in Microsoft Office was publically disclosed. Since learning of this flaw, Talos has been actively investigating the issue. Preliminary reports indicated that this vulnerability was actively being exploited in the wild and used to compromise hosts with Dridex, a well-known banking trojan.
On Tuesday, April 11, Microsoft released a patch for CVE-2017-0199. CVE-2017-0199 is an arbitrary code execution vulnerability in Microsoft Office which manifests due to improper handling of Rich Text Format (RTF) files. Exploitation of this flaw has been observed in email-based attacks where adversaries bait users to open a specifically crafted document attached to the message. Given that this vulnerability continues to be actively being exploited, Talos strongly recommends all customers patch as soon as possible.
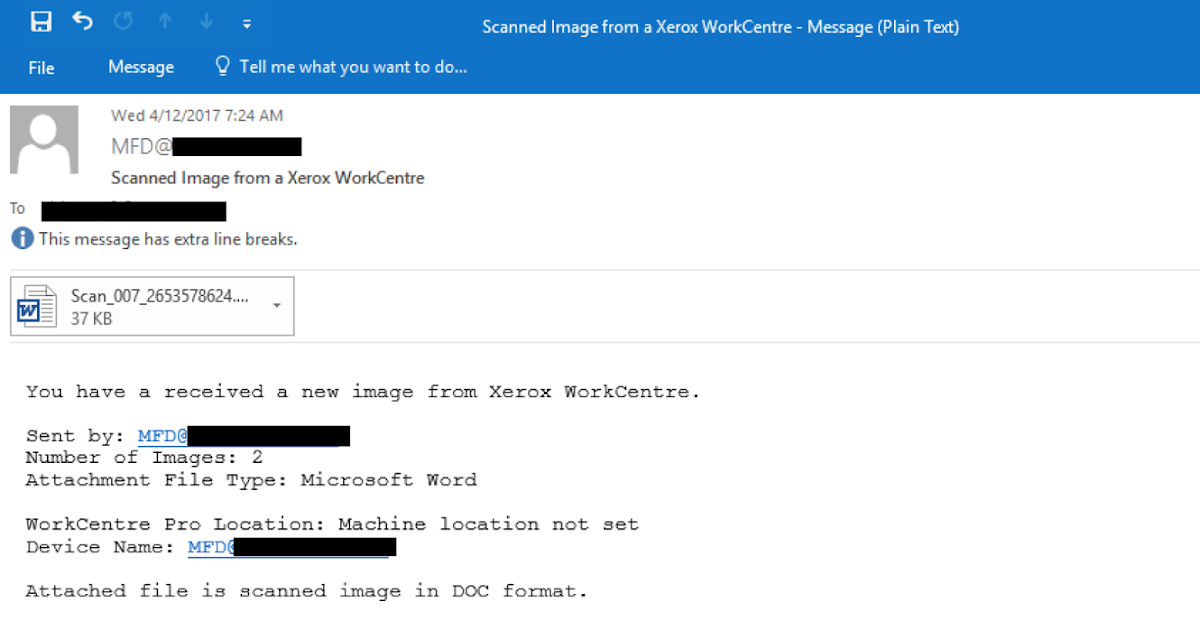
Talos has observed several spam campaigns that have attempted to compromise users by exploiting CVE-2017-0199. In one particular instance, Talos detected and blocked a campaign where adversaries were sending phishing messages designed to appear as a "scanned image" coming from a Xerox Workcentre device.
The attached documents were named similar to one another with randomly generated numbers being used in the file name, such as Scan_005_4102974675.doc. Note that while the document filename ends with a .doc suffix, the contents of the attachment are actually RTF-formatted. Talos has observed that adversaries are using different suffixes for files that Microsoft Word can natively handle to evade temporary countermeasures of disassociating .RTF files from Microsoft Word.
Upon opening the attached document, the user will encounter a prompt from Microsoft Word asking whether they would like Word to update any links to files that are referred to in the document.
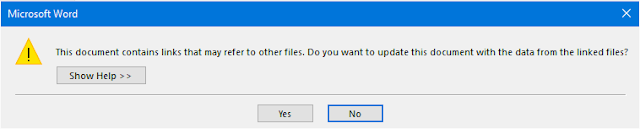
Unfortunately, due to how the exploit works, click "No" effectively does nothing as the the exploit will have already been run. Most of the samples Talos has observed download and execute another file upon successfully exploiting the vulnerability.
Talos strongly encourages that users should exercise caution when receiving unexpected emails containing attachments. Adversaries will be looking to exploit users via methods such as this, or via other social engineering avenues.
Observed Samples
- 13d0d0b67c8e881e858ae8cbece32ee464775b33a9ffcec6bff4dd3085dbb575
- 14d58c0844d12c5def85b8595992e73e7214e6c6b749ed8d015d5eaec90249d7
- 14e4d9269304d5e92f300adfcc5cc4f65ead9b3898a3efbeac7e321ef3ca3b40
- 17dfd3747821deb1c89a829c88593764a3a2097fcdb23824c21ef48f66e961ef
- 1b622bd463172f4fddfb0250d647de796f25487d9fe23e0343bfda64720283a6
- 1b9723563c662ac577145361e6efc85097ddd7ab69796ced5fdbc8a1d9c6cf71
- 1c340bbfb9f95ab3f2e0e53ab381877afaa35e276da8e82a7ce779e9663a2c9e
- 2264b3e47dbacd7c8027570d6d651df50c577003e110d0b996da81d6c7693234
- 23306c4ab3e725e4b552f5362c47a842e0faf90ca729e7c5746e3e8528e1d9c2
- 3063b95f558ed3c64d28e1f487b51c0377c20f19400beff1f38d963ad2113382
- 3c0a93d05b3d0a9564df63ed6178d54d467263ad6e3a76a9083a43a7e4a9cca5
- 3c9cbe523ce25c33c4da7e19ce91cc9f170ce03d1fa53f27aeb0f67100214f6a
- 425f4d87857d5813776ba154d3646100b6923c2803d5640c7cb4c21fb0cfb7b1
- 4453739d7b524d17e4542c8ecfce65d1104b442b1be734ae665ad6d2215662fd
- 4db72f22b4297158057ec9093154c04861d02cc24f75f4ef7f12c612c6f6dcfc
- 5a4e7f22d2d3fa7f48db5ea4ef34072fd16465657af2ba8a4f14c04602b6a0d2
- 5c5c6f8e20e0bdedd2d218d0718b8bf1d909598d2cc760a006838346be85c5aa
- 5e7f1764ddea586646fee7ba90f469c8ca060a2d80eaa2aea7e204c9aa0a616e
- 6059d031f6bb2f2442b6f3f56f18637a79ba65000eea14ee357af1471c5d1bbb
- 64ca94397197d5ac8189770bff60a95bb4ec7441a64b0cb30b6eef35d8d8d193
- 6da2e59c9569bf07c8ab658032b5b3075a2f4898679ad899233b8ef9571d401f
- 745d05b59cfa9579a0cb14597748434648ca7536870f242e8c5ac10aa45ec546
- 78432a4b9a3217edb2a5e2e790f1cabf6e96bfcf2a19dc8b721a293e2dc59d12
- 792470a756978cbcf27ecce5792918cc6b88ada8c34de1b80cbfc19e69528c7f
- 7a048f25e3d1a5746a190af7201fc82623685280af127b49ca80ef3ac1718d9d
- 7a6d430195da8e9f1db38e476c41985bf421ef8215d09290c8472260e4142653
- 7f2a499891a72b9f3b0923be0f9db490463639166b41a15fe3bf5387df660f1c
- 85c64c744d30b19fccae6398dfcf43bddd2b3c3796f8c50fc5855a868216b79c
- 86f632c4ef666afaa753b3e5008443b0be79f3e0d809e140a961592cb75813bb
- 8e7322080604ac3c2094c8cf1bd044e163e3f3ca5100e237a03ef7f7c8aa6c9b
- 9aa5aa06f94066b28da8a0a146aa8d4933e1df8b006f69fa16925156d54257b1
- 9b084feac125dd1c4c8dba4621ec9c607250f9889cb1b7448238f9fe9192d2ab
- 9d9c6b651d50afb853cb7e5c9819ae89d871c4311cb5982f852775ba82f9f24a
- 9dc7deb92b68dc7eb6c50226b1d8281ad517cc06ddf5d0732f6fab343aa70738
- a00bb4c41272dc67f92ec0a6c5cec7b606d44382b7637523be8dc5ca2e320fda
- a7fa6e64286134448b369e4241798907eb9afd01d4024d51bc3a2790c453dd15
- ac968aa2e3a034daa4f066f3755da82fb0bd5bb5c59b26bf1b111ee20c34e501
- ae48d23e39bf4619881b5c4dd2712b8fabd4f8bd6beb0ae167647995ba68100e
- b128f58594b5c6371bf4245d7fb6fd2b1fd61fdc1f4cf0811356194d6903495e
- b1590276f37e5fc2aacaaa4d0f6e16b74421623353bdaf14b296e6778d3cc655
- b3b3cac20d93f097b20731511a3adec923f5e806e1987c5713d840e335e55b66
- b42ba25763ae0166c23353200e4e84480924cd0bee60b9ae87314d9c1be6288d
- b807b93fbe9f39477d875c269bab1325e97672f467ce16cd6e10d2f1f6d4f071
- b9147ca1380a5e4adcb835c256a9b05dfe44a3ff3d5950bc1822ce8961a191a1
- b9b92307d9fffff9f63c76541c9f2b7447731a289d34b58d762d4e28cb571fbd
- bd9e3c2def719de0a5e41ea84a64d20cf1140d34731788c3d1f91940dfafad16
- c98f34e4e87f041c3f19749bbb995bfcd2e3de20c2ba619ea4a0ed616ac1b629
- cd31709d3e5f0ad0a1cd16d4d2fd01947dcccaacf98e38cb7afb72c94fe29413
- ce926763c053e6f9a637cfd86c2312de012d1618eb1cc86b421e5dc5a117c125
- d134a40a2e4c04e822983b6ac9f0b85506b3f2402234de696bdf3be662bb651a
- d1ca07a3bbe7ce33821ac8b73eefc2d87f72293a6c9c95ac427c41593ef92d9f
- d3148d2189b148d8d8cb63976509fd6abc186340cbcf29f68f5370d536fbe5c9
- d3c3b2e6681ec812a9df035954aa3aa82e463dfe226afddfa6f534e2a07a057c
- d3cba5dcdd6eca4ab2507c2fc1f1f524205d15fd06230163beac3154785c4055
- d70851f30c94f5a3abb7a4e7557777733cf507bc9f98632867e3c55ce8e2b7b2
- d9dcff78d334c3bc459f0e58209d77693384ede7db761ce1928daa50a4f14273
- e20368cdb4c96c95066073a07b9941d010822fde033e51529a8d26900413f371
- e7f3eb567583bc85a1a002e5d289d526bf4c16b7ed356d9973ff458b7635e072
- e9339747b31f576e6d4049696a4f4bd7053bcd29dafb0a7f2e55b8aab1539b67
- e9da2fa0496c4fe5d749767cbda82b8838a94384b2ddf6389a946e2ee7e36edb
- ee71a6191a1c9cc89c91ead19e1291e7e743d40740aeb4e3278cdd673f879b81
- ef43da73da325b2b68feaf7d709fb30e4eb3f74e4750a6507bebd925fa1c41a9
- f4a0f65e9161a266b557e3850e3d17f08b2843ee560f8a89ecf7059eba104e66
- f59b1ca8ad354b66b95d36712b331dc4b9d152ee564c504c8f4f33add6da360c
- f8f7cbd257329af8d7ab6c3736ddfcaed1af658197a8e94a2422c823b55c43c9
- fc1bca6aa87ee0e075cc11cdcdfb9dc3dd22e42a45c71a4caa03362b9d477782
Malicious IP Addresses
- 63.141.250[.]167
- 64.79.205[.]100
- 95.46.99[.]199
- 179.108.87[.]11
- 185.44.105[.]92
Malicious Domains
- btt5sxcx90[.]com
- rottastics36w[.]net
- hyoeyeep[.]ws
Coverage
Coverage for CVE-2017-0199 is available through Cisco's security products, services, and open source technologies. Talos will continue to monitor the situation and as a result, new coverage may be developed and existing coverage adapted or modified. For the most current information, please refer to your Firepower Management Center or Snort.org.
Snort Rules
- 42189-42190
- 42229-42231
ClamAV Signatures
- Rtf.Exploit.CVE_2017_0199-6231737-0
- Rtf.Exploit.CVE_2017_0199-6268975-0
- Rtf.Exploit.CVE_2017_0199-6268975-1
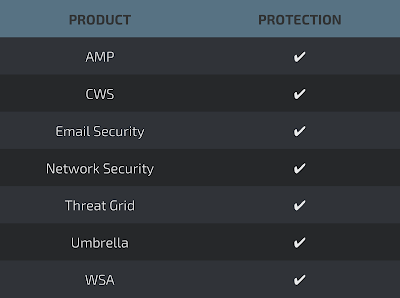
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of malware that is downloaded by documents exploiting this vulnerability.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
The Network Security protection of IPS and NGFW have up-to-date signatures to detect malicious network activity by threat actors.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network