On Friday, April 14, the actor group identifying itself as the Shadow Brokers released new information containing exploits for vulnerabilities that affect various versions of Microsoft Windows as well as applications such as Lotus Domino. Additionally, the release included previously unknown tools, including an exploitation framework identified as "FUZZBUNCH." Preliminary analysis of the information suggested several of the released exploits were targeting zero-day vulnerabilities. Microsoft has released a statement regarding the newly released exploits targeting Windows and notes that most of them have been previously patched. Talos is aware of this new information disclosure and has responded to ensure our customers are protected from these threats.
Coverage for the exploits and tools disclosed by the Shadow Brokers is available through Cisco's security products, services, and open source technologies. In some cases, coverage for specific tools or vulnerabilities was already available prior to today's information release. In the cases of the exploits dubbed ETERNALCHAMPION and ETERNALBLUE, Talos had pre-existing coverage that detects attempts to exploit these vulnerabilities.
Talos will continue to monitor and analyze this situation for new developments and respond accordingly. As a result, new coverage may be developed or existing coverage adapted and/or modified at a later date. For the most current information, please refer to your Firepower Management Center or Snort.org.
Snort Rules
- 14782
- 14783
- 14896
- 15015
- 15930
- 26643
- 41978 (for ETERNALCHAMPION and ETERNALBLUE)
- 42110
- 42255 (for ESTEEMAUDIT)
- 42256 (for ETERNALROMANCE and ETERNALSYNERGY)
AMP Detection Names
- W32.Variant:Gen.20fn.1201
- W32.GenericKD:Malwaregen.20fo.1201
- Win.Trojan.Agent.MRT.Talos
- W32.Variant:Gen.20fo.1201
- W32.Auto:07b8a1.in03.Talos
- W32.Auto:0b3e8a.in03.Talos
- W32.Auto:0c9e49.in03.Talos
- W32.Generic:EqShellC.20cn.1201
- W32.GenericKD:Equdrug.20cp.1201
- W32.Malwaregen:Equdrug.20cn.1201
- W32.GenericKD:Malwaregen.20cp.1201
- W32.Variant.20fn.1201
- W32.Auto:1a3acf.in03.Talos
- W32.Variant:Malwaregen.20fo.1201
- W32.Trojan:Equdrug.20fn.1201
- W32.GenericKD:Gen.20cn.1201
- W32.Auto:24e0b1.in03.Talos
- W32.Malwaregen:Equdrug.20cp.1201
- W32.Variant:Equdrug.20cp.1201
- W32.Variant:EqCrypA.20df.1201
- W32.Generic:Equdrug.20cp.1201
- W32.Variant:EqDrugA.20fo.1201
- W32.GenericKD:Malwaregen.20fn.1201
- W32.Variant:Malwaregen.20fn.1201
- W32.Generic:Malwaregen.20cp.1201
- W32.Generic:Gen.20cn.1201
- W32.Auto:346117.in03.Talos
- W32.Variant:Equdrug.20fn.1201
- W32.Auto:352ef2.in03.Talos
- Auto.3E181CA31F.in10.tht.Talos
- W32.Variant:Gen.20cn.1201
- W32.GenericKD:Malwaregen.20cs.1201
- W32.Auto:4ac6f5.in03.Talos
- W32.Auto:4cc308.in03.Talos
- W32.4E1DF72362-100.SBX.VIOC
- W32.Heur:Malwaregen.20cq.1201
- W32.Auto:56254f.in03.Talos
- W32.Auto:593415.in03.Talos
- W32.5F06EC411F-95.SBX.TG
- W32.Auto:6001e8.in03.Talos
- W32.Auto:60ea11.in03.Talos
- W32.Auto:64ed2c.in03.Talos
- W32.Variant:Malwaregen.20cn.1201
- W32.Auto:6cd023.in03.Talos
- W32.Auto:738348.in03.Talos
- W32.Auto:76e02a.in03.Talos
- W32.Auto:7901bb.in03.Talos
- W32.7B4986AEE8-95.SBX.TG
- W32.Auto:7b9bcf.in03.Talos
- Auto.7C4F3817C7.in10.tht.Talos
- W32.Auto:805848.in03.Talos
- W32.Auto:8d28e4.in03.Talos
- W32.Auto:907168.in03.Talos
- W32.Variant:Generic.20cn.1201
- W32.Auto:970df0.in03.Talos
- W32.Auto:99339a.in03.Talos
- W32.Variant:Equdrug.20fo.1201
- W32.Auto:9aa34b.in03.Talos
- W32.Auto:9bebd2.in03.Talos
- W32.Auto:9ee687.in03.Talos
- W32.73252:Equdrug.20fn.1201
- W32.Auto:aa4a52.in03.Talos
- W32.Auto:aed16a.in03.Talos
- W32.Auto:aed477.in03.Talos
- W32.Auto:aee118.in03.Talos
- W32.B2DAF9058F-95.SBX.TG
- W32.Auto:b57181.in03.Talos
- W32.Auto:b6f17e.in03.Talos
- W32.B7902809A1-95.SBX.TG
- W32.Auto:b9d95e.in03.Talos
- Auto.C5E119FF7B.in10.tht.Talos
- W32.Generic:Malwaregen.20fo.1201
- W32.Auto:cca60c.in03.Talos
- W32.D382E59854-95.SBX.TG
- W32.Auto:d38ce3.in03.Talos
- W32.D52CFA731D-100.SBX.VIOC
- W32.Auto:d8722d.in03.Talos
- W32.Auto:d9f792.in03.Talos
- W32.Trojan.20fn.1201
- W32.Auto:dc4adc.in03.Talos
- W32.Auto:de578a.in03.Talos
- W32.Generic:Gen.20fo.1201
- W32.E1DFF24AF5-95.SBX.TG
- W32.Auto:e9a236.in03.Talos
- W32.Auto:ea3b8c.in03.Talos
- W32.EF906B8A8A-95.SBX.TG
- W32.Auto:f720d9.in03.Talos
- W32.F7A886EE10-95.SBX.TG
- W32.Malware:Gen.20fn.1201
- W32.F8CD0D655F-100.SBX.VIOC
- W32.Trojan:Gen.20fn.1201
- W32.Generic:Malwaregen.20cn.1201
- W32.Auto:fd2efb.in03.Talos
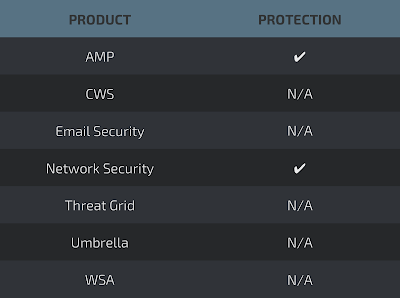
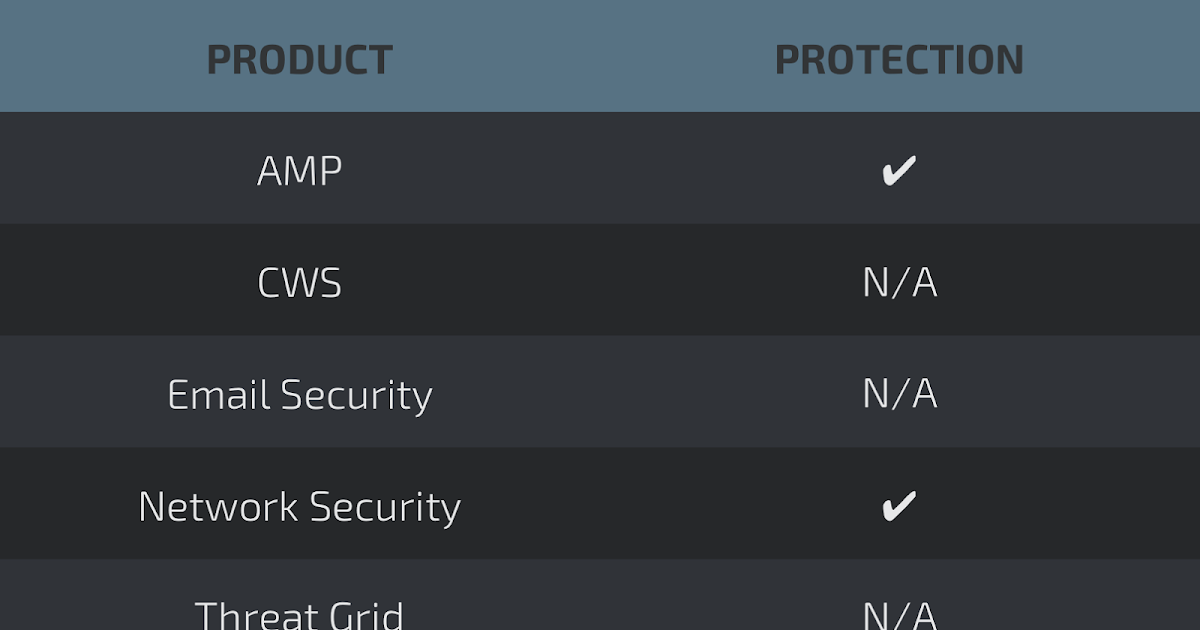
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of malware utilized by threats actors.
The Network Security protection of IPS and NGFW have up-to-date signatures to detect malicious network activity by threat actors.