Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 31 and April 7. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Js.Downloader.Nemucod-6198135-0
Script-based malware downloader
Nemucod is a popular script-based downloader, often resulting in drops for Locky & Cerber. This latest variant consists of ~30-50 lines of minimized scripting code, relying on obfuscation & requests to several domains (most of which are in plaintext). - Doc.Trojan.CommentObfuscation
Macro Obfuscation Technique - Heuristic chaff
This obfuscation technique utilizes macro comments to inject data, characters, words, etc. into malicious office documents for the purposes of obscuring heuristic, static scanning. As an obfuscation technique, these droppers are being discovered delivering payloads of all sorts and sizes. - Win.Adware.Gator
Adware
Gator is common adware that is frequently bundled with ad-supported software. Gator can add toolbars to browsers, add links to the user's folders, and create popup advertisements. - Win.Worm.Allaple-6171102-0
Worm
The worm scans network subnets for connected machines. It will try to log on to machines with frequently-used credentials and copy itself to the C$ network share. The worm is polymorphic and changes its code when copying itself. - Win.Worm.Mamianune-6230992
Worm
Mamianune is an email spreading worm and file infector. It copies itself to the infected system at the %system% directory, and changes the registry to ensure persistence. It will try to spread itself through email to addresses found in files present in the system. It may also create files in the system with .htm extension. - Win.Trojan.VBEmailGen
Generic Trojan/Information stealer
This generic trojan is heavily polymorphic and it is written in Visual Basic. The main goal of this malware is to steal credentials. These credentials range from FTP logins to passwords stored in the browser. These samples perform injection and try to complicate the analysis with anti-vm and anti-debug tricks. - Doc.Dropper.Agent-6206825-0
Office VBA/PowerShell downloader/dropper
This sample is a Microsoft Word document that uses a macro to launch a PowerShell script to download and execute a secondary payload. - Doc.Macro.AliasFunc-6203108-0
Office Macro Obfuscation Heuristic
Office macro code is used to further compromise a target system. Macros can leverage external Win32 APIs to download files, write or modify files, connect to servers, etc. This signature looks for imported function that are aliased for malicious intents. - Doc.Macro.wScriptObfuscated-6203135-0
Office Macro
Office macros can provide functionality to download files, however, to accomplish this certain functionality it used. To prevent basic detection techniques macro developers obfuscate the way they create and access API required to perform certain actions. - Doc.Dropper.Agent-5932811-0
Marco
This sample is a Microsoft Word document that uses a macro to launch a PowerShell script to download and execute another executable payload. Unfortunately, this secondary payload was unavailable at the time of this execution report.
Js.Downloader.Nemucod-6198135-0
Indicators of Compromise Registry Keys
- HKEY_USERS\Software\Microsoft\Windows\ShellNoRoam\MUICache
- HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager
- HKEY_USERS\<USER>\shell\open\command
- HKEY_USERS\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\OSUpgrade Mutexes
- \BaseNamedObjects\Global\C278B16ED3FB49FB
- \BaseNamedObjects\FDDC561D84D621F8
- \BaseNamedObjects\shell.{18D0266F-2D74-3F5C-79BE-40E45584D13C}
- \BaseNamedObjects\18469BB796AF13B3 IP Addresses
- 62.113.208.114
- 37.140.192.161
- 195.29.89.23
- 195.141.45.95
- 86.109.170.121
- 78.40.108.228
- 109.234.161.38 Domain Names
- vip-charter[.]eu
- gipnart[.]ru
- zivogosce[.]com
- evro[.]ch
- fp[.]amusal[.]es
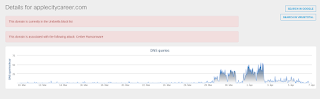
- applecitycareer[.]com
- horizons-meylan[.]com Files and or directories created
- %APPDATA%\d2f225f\045b126.356b036e
- %APPDATA%\d2f225f\8dcb019.bat
- %TEMP%\exe1.exe
- %SystemRoot%\system32\config\WindowsPowerShell.evt File Hashes
- a7d5a8786bef4bcdd5786e347277f84ff8c1da90ddea0a3c85ccb367aa22b630
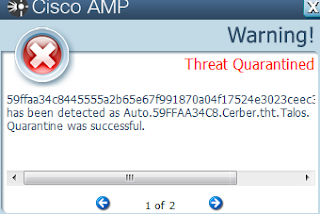
- 59ffaa34c8445555a2b65e67f991870a04f17524e3023ceec338dcda7f33c99c
- 5ca09f901b1a0996e0aa8d027928503eb8ef107ae69eb7771b466706f7f3a27d
- c6a97bc59e99bd19ce5134df7469b770ca734a39e6e83ddfe8282be33928aeac
- dae57172401bb726a28c4317cefc475ebf662c62a04e60bb6da462a31f921fb7
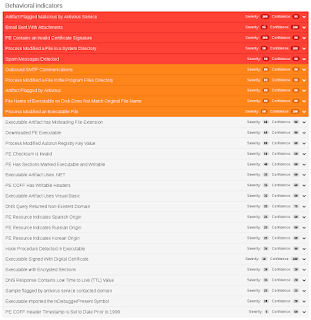
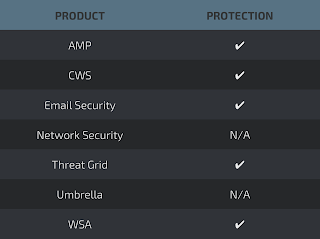
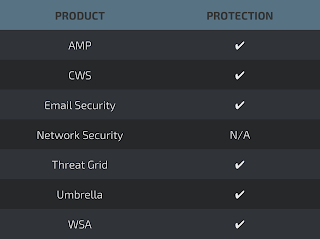
Coverage
Screenshots of Detection AMP
ThreatGrid
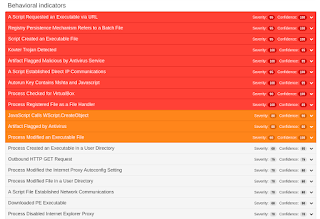

Umbrella
Doc.Trojan.CommentObfuscation
Indicators of Compromise File Hashes
- 14f79bd9dd171ebe7ad96d0fb799bf7afd492a51f32a2bcb5594a84b2beb7ddf
- 3d14e2ae06a16db70e9d7d7495be830703d8f3da1aeebfadf2831782b479e726
- 5fd368dac325e282cc8fb2f70f0f003425881bc9615adc7ae23420996dbd4ece
- 94d92f9a7a0de39363089d243ac6249d66a8a803532821d8d260ccd9c86a2017
- 9a4957219e6f48262e54bc660c37d40d79ef98abfae95f8942e734fdb92ce6f9
- ae892ee8cfc3685d78182dfd6b31a6f7691e9892c727bf2016e4764f6ec3eb84
- cbf86eef9d0b22d28a46ba309172dca58f7c0d98986cba1ebd3fa47e4aaa0783
- Cf17ab33a117d24bf64a83f7604ed6e125e3a3c7c9e4a6af274058ee4d2bada3
Coverage
Screenshots of Detection AMP
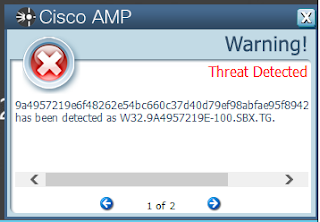
ThreatGrid
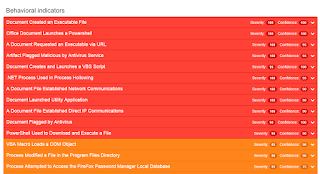
Win.Adware.Gator
Indicators of Compromise Registry Keys
- HKLM\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN\Trickler
- HKLM\SOFTWARE\QWERTYUIO\TRICKLER\AppPath
- HKLM\SOFTWARE\QWERTYUIO\TRICKLER\OldTrickler
- HKLM\SOFTWARE\CLASSES\CLSID\{21FFB6C0-0DA1-11D5-A9D5-00500413153C} Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- C:\TEMP\<original_filename>.exe
- C:\TEMP\<original_filename>_3202[a-z].exe File Hashes
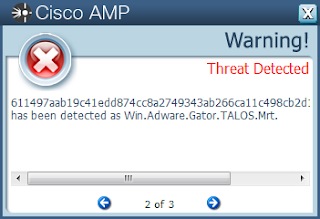
- 611497aab19c41edd874cc8a2749343ab266ca11c498cb2d149101f7ae4efa4c
- 52cd00a58dde64c67971d7c88fdb486a6bdfdecd158d3be3aac0cd7fe26a75be
- 531ad4d1eedb21e43a97223475d84e161e635ead793c67ec649d6b848699bd54
- f4785012bea82b1c843383f2a579644cbb2dd2929740f3f3e31890a016db4e07
- 6453bd44b7d459b9c3920f55f35dfe673d22b337332b8a6c60427c668d635723
- 34e667fc845cdfed918cf3e04a998ec4453a1162931e341a83a0fcb3cbb26cfe
- b672f6b44cd0a1482d63c20f5d1ed2bbbdb0764b5cfaff2526e062be4868973c
- b0667ceb4931e8174b08b01005082f725eae6853041b80d4dc4bb30f64200fc3
- 4b44d48de8f6f53a7a49fc83e210cdb82a6f2f6112c557e114eda00876e56198
- 35cf22dcf978e5e712962680153b6f6e824ee15de845f1e94abd2cc9ef9575d4
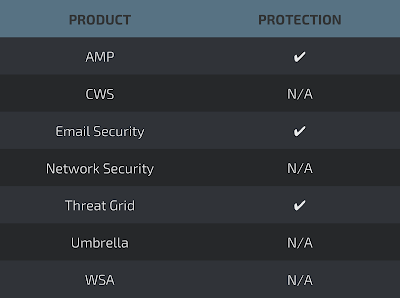
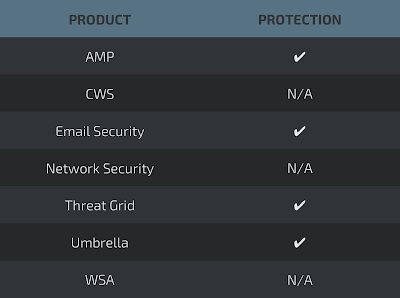
Coverage
Screenshots of Detection AMP
ThreatGrid
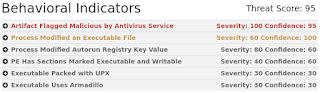
Win.Worm.Allaple-6171102-0
Indicators of Compromise
Registry Keys
Creates class IDs which point to the malware binary. The CLSID varies, and points to the dropped worm binary
- HKLM\Software\Classes\CLSID\{A18CE63E-6C47-00A5-8688-927B7EB5E2B5}
- HKLM\Software\Classes\CLSID\{A18CE63E-6C47-00A5-8688-927B7EB5E2B5}\LocalServer32 Mutexes
- \BaseNamedObjects\jhdheruhfrthkgjhtjkghjk5trh
- \BaseNamedObjects\jhdheddfffffhjk5trh IP Addresses
- N/A Domain Names
- N/AFiles and or directories created
- C:\I386\COMPDATA\[a-z]{8}.exe
- C:\Program Files\Adobe\Reader 8.0\Reader\HowTo\ENU\[a-z]{8}.exe
- C:\Program Files\Adobe\Reader 8.0\Reader\adobe_epic\eula\en_US\install.html
- C:\Program Files\Adobe\Reader 8.0\Reader\HowTo\ENU\WS[0-9A-F]{8}-[0-9A-F]{4}-[0-9a-f]{4}-[0-9A-F]{4}-[0-9A-F]{12}.html File Hashes
The worm is polymorphic and creates a new binary each time it copies itself to a new machine. The given hashes are just examples of worm binaries.
- 044020f369542e3ef8e6e3d1697904cdf9484c9382bae0e9a5e637056bada5b3
- 06d7258355f841ceb8ef0f444785eff6886fb16b5f60303c4321dfdd57b5debd
- 08bd26a0b0a1c4ae70fa72cf1efe6e0a1b908bc34e05f1b861c6aa3a3e1fec2c
- 3ea6d5f924fc9bd3dd55a97c62a8be2ef52142003a5ef298552a494ba7c837ea
- 4ca685cf021aa8c1fbd93f6bca7264a733f577cf86a0f1d132db179c4a45fa76
- 7a6facb36eab78bab5378f800ef44fa4fc955ed41de0eeafd8769dc968d96e9c
- 7fece8b506810686e2fe5ae34efa773b1abda48e3b175e3c4d5d957e6e8c4b55
- 8e5c4063c4b384b5e2e07035f69e66c16e93fe78cd4d2162dd092f118f83e6c4
- 926edb2df49ac87e7f57dc7283f57a2f2c0296817dc5332b7ba88142ae732127
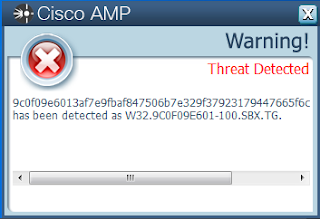
- 9c0f09e6013af7e9fbaf847506b7e329f37923179447665f6c94340b2d269e79
- a4dd532c71f0f802c313f12e971349c8f06b273cfcf85458fe1d0f45a3a78a75
- b64e6c26a213a5bb955155e009c4fd31b697761e992fd040da98459611a0afef
- ba92b52950a1f41a4b00022bb119ff8f8680d67bd73c4971a83fc71cc045b1f7
- cba4e590a5dec97562c19c99337c31891558621d9e462ccf176831bc67e73601
- d87de7d2adc271d20dad6ccf8b606a3bba1a3dbbc1d32726bb2482d856e8bac4
- de0c9b69b5d20fa75813dfca45e6c9dc619c794e26785dca8e6cb810896ec20e
- e8617de08bd8da781992099073c7f7a5f8e682f63ed0ad7575fbc1903170887a
- eea5674aa53774cde05f098415a07761ad45d20fc5f1d143c04c1010f6239462
- f673c0be7d8a164cc49601746616aa784e3420202e94f1a56fc1a9c94cdea8da
- ff63a199a865ab203218523b1bbb90bac9f282bf1abbf9b3887411b6934dc2d9
Coverage
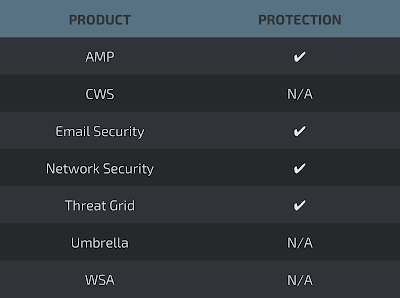
Screenshots of Detection AMP
ThreatGrid
Win.Worm.Mamianune-6230992
Indicators of Compromise Registry Keys
- HKEY_USER\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
- HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Mutexes
- [a-z0-9]+ E.g.: jhdheruhfrthkgjhtjkghjk5trh Files and or directories created
- Will infect modify any executable found on the system.
- May create files on the system: [a-zA-Z0-9].htm File Hashes
- 08858fd01702c814b5524988ab8c0802c8c66990559bbb68081c592251b9a133
Coverage
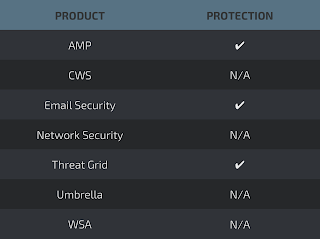
Screenshots of Detection AMP
ThreatGrid
Win.Trojan.VBEmailGen
Indicators of Compromise
Registry Keys
- HKEY_USERS\Software\WinRAR\HWID
- HKEY_USERS\Software\WinRAR\Client Hash Mutexes
- N/A IP Addresses
- 192.3.140.114
- 192.3.140.121
- 62.108.34.122
- Numerous other IP addresses can be associated depending on the sample Domain Names
- slynny[.]usa[.]cc
- expresslimco[.]usa[.]cc
- limvat[.]usa[.]cc
- *[.]usa[.]cc Files and or directories created
- \samr File Hashes
- 024df78f71a7974a33611a17ce6e552c5c33c8bf9c63a2a3286260cb7024ecc2
- 0b949c2da04adb63a0b2b2ab879d55bd18e870a867b703e2c6d2099e44a4a1d6
- 126195829847422118cf942572388a6d57d29a1d4c4bdb61ddac6f9c41b829bd
- 1540943aa8da93cf72deb4d0b032696cf62fefd43d9e57266291583e99b4d62e
- 159f524d461df27925e0f6730a0f275d5751f2216932de120b3ddb4a0dc6a3e6
- 26a4396750bfe364c9843dcada3cccdd148667115b5b9606803e68b17bd7182c
- 27c393ba6411561f57342dc22ae4392b21292d4ed56e54f4aa2c486a1cfaf416
- 3e245c3e12d86e74a1a679ea41354a9c130de66f7cba27c68314f4ed1c9833c1
- 417438c96804eaa6748d90ddacea232600733c0fca293e2f8b18934425159c2d
- 43d87148fad6c0a9cc94019626670622889a95e6e12f4bec22a63ee2549f077c
- 54583a611eb881e755caf34379db0ab49030aa50c17a3eb4e09519a36740d61e
- 5a37dbecf825521597ec511ae03e854c8000c9b6220db8f10bf18415fa856a90
- 5e25b891306342a02c2d744381bb5429823430a8ad7297dd53a0b61feaf64e38
- 8153c480b72455c5e03f3e5322f603962f9d23532a849318c8a30a6f63a61d3c
- 83df6d5fdb6371d45c4ab2dd333fc7ab4b1c1a729926720006cc250355198fbc
- 86f5d1ff6049450eb53c9ba28cdf2ad26087def29e4f34f56f835390aca0058e
- b4ba641367f66c48859229c6039b6ebab89b21cd86ff4c169c4cfdc411663654
- c3f622584222c8a97614ab1b210bdbe3c67d21de6d51c1c583bd29e3ad0c30f9
- d2e07f91f7edb89707c1d314b69678b56aaf0edb4ab8d30047fad4d2b782332a
- df742a83513a3537b451d7cb8598398a6be849e0cb3ee886e7be59c69d12c780
- f6ba14b376c96abda2444fb555951674e4cb589b3943652e01c4fd44b1a2e71b
Coverage
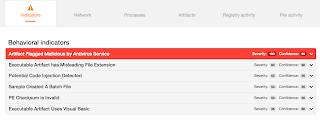
Screenshots of Detection
AMP
Umbrella
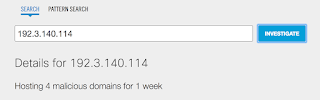
ThreatGrid
Doc.Dropper.Agent-6206825-0
Indicators of Compromise
URLs
- /file/cet.ert?showforum=12.0 IP Addresses
- 62.109.7.232
- 185.163.45.27 Domain Names
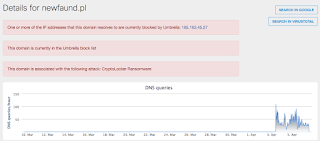
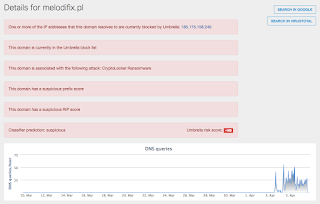
- melodifix[.]pl
- newfaund[.]pl Files and or directories created
- %TEMP%\programming.dll
- %TEMP%\YarnMavin File Hashes
- Acb997996c74749f073a83ebb852e7396d546cd692f2590c78e5dbe40c86c725
- BB4D13340B82060A7F300A8408CA4533A51017318A5FBCBC40FA49E156367108
- B51701FCF002CFFCC361A7E111AFF2A19FD98E591DF61D1EC93C641CE5FA1CB1
- 003cc8bae434d0bf7dc3fae1d5b7dc35e66251540c0fbcc025ed6e9471b9756a
- 025976cfbf9192f813bb19b182aa7df5a578e6c55edb44be1b59d4529900cce0
- 02946a61761581336f31fdc8e933e577324395da77a104ab26badc50649efb23
- 039ba8310975624d55f1e85ed931fdbe44068af5101fc21a783acd97277179ab
- 04070452057f5262513b2d5cf0f5fdae34410d2531a966e8fd416a5edfff0e0f
- 09155ce0b9b9a6c49143c7aac3ec2c693b50a3b12e14b46a7c37f6d004165013
- 0c9af6f03f35d4d04a568c50f1c7813abbe862865c203934982a0f173304b4c4
- 0cb68591ab238da5e203a7cb1e0bbb9ebddfb3906e43194819ecb0d7039f54c0
- 0d6d5a2c9b06f986ea468e3df1602c307bb2478155c3566bd9421901ffc0c289
- 0e47674ac2dc230f8905be6446c077627fa5672dcf309d844580e14b87a3e42d
- 0fc621e81a188a89e269b4440b8c62ae5812ce7b658224fd45628a0c3a983b88
- 10508d5e47b50be2f15a8419a214c91e6516c604dceaba66a2d06a2334bf777a
- 14b45db836ff1c0d7e283d0ff824013d7a48c59d3805c20cf9a4c61106256fe4
- 155d7611a75392ead0d69df77ce4be4e72235dfd3c5e10b9bb850da5a57cbfc6
- 18224d2e924945aea1b73f89fe10e3c8e64dab1f50233e56fdb279fd172b010e
- 1b375ba7912e96821e9b5706a25f3a0411898f2cc3f9690b3e12fca84fac1e15
- 1bb1a1b58db0b6c9e0946b3ced3d576fd057c0365141968a43dec6c72d1d511a
- 1e303941e1b520d962080164ad54a75c0cf25aa53f80effb2891708869495bbd
- 1f8558ae8a8f11afa0e6bcb4b9a8bdc20e9b98efdc63f44e088802befebb570e
- 20a46289b115d2258dd9d0217729e8828664358a3c81653458fb17271a99f171
Coverage
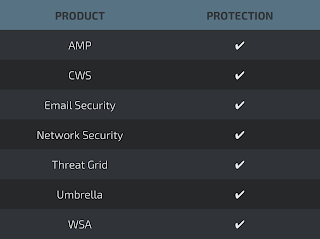
Screenshots of Detection AMP
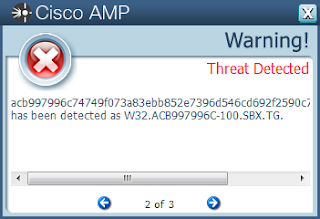
ThreatGrid
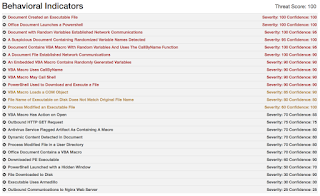
Umbrella
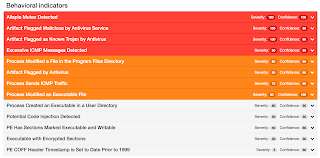
Malware Screenshot
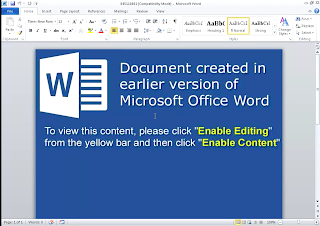
Doc.Macro.AliasFunc-6203108-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- N/A File Hashes
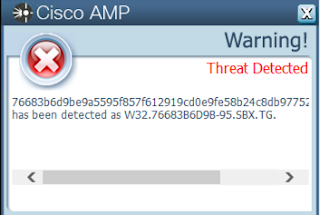
- 76683b6d9be9a5595f857f612919cd0e9fe58b24c8db977522c21eee4e7c612b
- 84ab92e565c0eadee1e2da2dd8c55d82b356330786acbd088d5eced779eaecf4
- eac422d2a54bab4305cc313fa8682f33715ecd5b3c03a7a82883dd19282100e7
- 5553e39dcd0d8b91e1b2a2829201e3b994457c7ffbcc6d2d8f87c860f2462877
- 485aaa99469550cdbb5542cd43cc0f5318017ada250c2fe7c8ba6e2d5d2693b0
- d26c4d26b044cd2f19fbf8b039c7c57328aa3e4ce12bc5c604ad9ff59512fc69
- 8f09461b86e819c67d138c44d2cc94287af56b691e96c5515853f0273a2daa08
- B4fc5bdb79eac839cb285ac7b3bbccd679e8e4776bde3947beb86d0c6ce07bf5
- 28eafbd69faed61103d8334d78a6f18512cf8fa5e61a08bb554fbd3bff6d5222
- fd0c2c8213e97cebf0b627627634db07cdc610f3f79bc9b0b239fa9b4a540b39
Coverage
Screenshots of Detection AMP
ThreatGrid
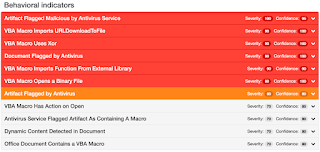
Malware Screenshot
Doc.Macro.wScriptObfuscated-6203135-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- oceanshipforafrica[.]gdn Files and or directories created
- N/A File Hashes
- 2b0aca97ac42bca58ed6abdf81bab340825da442291bc15d1c5a22ee7e8b009f
- 7ddfffd8b5827d09f93e4ba9da2f3cfe965fe7e5fb8ec680856c12dc024b7827
- 7a72bad05f9d4bd653c131fcf800cd0ad21eb179597d398f2e49963ff86a0c4f
- 7ca81591a87ed9ac1d9b2a02a7a1a64394f52f138108b190db83a49b6db35d36
- 190496d6b2db946d2342ece0bd0d1addf20bb15234d07934c6ec55a52e7dcb0e
- 37a57d36516a29996282f1999bbd0d0184ebc82ed7975155345a93d7c0d26fb9
- a237af78f7b3e81d060d3d1ae6edf22706c8815c88cc1b93a1b0ee759897a54a
- 2feecb7d931b2d16af9a7ced7bbf7c08f91ea404dd6034c13040d814462ffc5d
- c60fad4b7ff90f58d3e1be3a9f3a3a75de82727520553e23c264208e0f51f248
- D1563a9faa9590dafc097936cef24b406359da72e2dd3accca7bf697732cdae8
Coverage
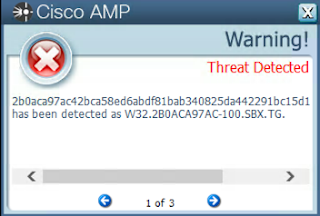
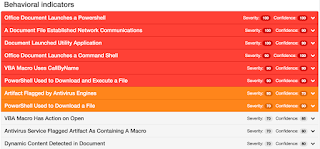
Screenshots of DetectionAMP
ThreatGrid
Umbrella
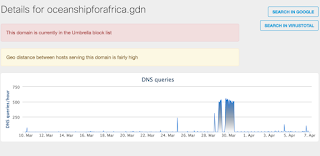
Doc.Dropper.Agent-5932811-0
Indicators of Compromise IP Addresses
- 5.154.191.172 Domain Names
- iuhd873[.]omniheart[.]pl File Hashes
- 02af015f85bca96b018e8ff7e9c0a2a7e32fc71ccc9620eb31063e8488fe6acf
Coverage
Screenshots of Detection AMP
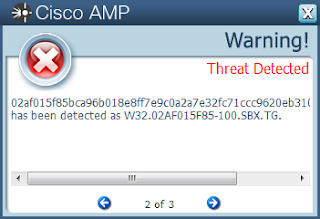
ThreatGrid
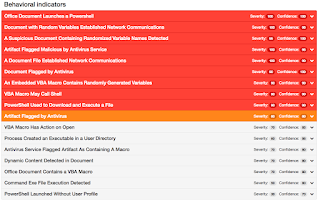
Umbrella
Malware Screenshot