Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 21 and April 28. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your FireSIGHT Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Doc.Macro.MaliciousHeuristic-6298845-0
Office Macro
Office macro code is used to further compromise a target system. Macros can leverage external system binaries to execute other binaries to further compromise the system. This signature looks for code associated with hiding the core functionality by including junk code. - Win.Dropper.DarkComet-6301230-0
Trojan/RAT dropper
This is a malware dropper. It currently drops the DarkComet RAT. The file is a slightly modified version of wextract.exe, a legitimate Windows tool to unpack archives. The malware payload is stored in the resource section of the binary. The dropper binary is actually a multi-format file, and can be interpreted both as a PE executable as well as a cab archive. The modified Windows binary will extract the payload binary from itself and run the extracted file. - Win.Trojan.ServStart
Trojan
ServStart is a trojan that installs a persistent service on the victim’s machine. The service exfiltrates information about the infected computer including machine name, username, keyboard language, and computer performance specifications. The malware server can respond with commands to download and execute files, or execute shell commands. ServStart has been observed using multiple dynamic DNS providers for its command and control infrastructure. - Win.Trojan.Agent-6298180-0
Trojan (credential stealer)
This sample attempts to collect stored credentials from a number of installed applications and then attempts to transmit those credentials back to a PHP application on a possibly compromised server. - Win.Trojan.PWS-6299789-0
Password stealer, injector
PWS (also known as Fareit or Chisburg) is a credential & sensitive information harvester. Select information such as banking credentials or web browser password databases are queried for on the infected host. Any discovered data is propagated to a C2. These recent samples are protected with the Armadillo packer & rely on both code injections & dropped VBScript code. - Win.Dropper.Emotet-6301061-0
Dropper
This dropper is delivered through different mechanism, most of the time the victims is redirected to a website to get it through malicious pdf, http iframe injected. Once running on the computer the binary is gathering details on volume disk drive and other details, injecting process, dropping itself and contacting internet to execute more. Websites observed delivering ransomware and trojan banker.
Threats
Doc.Macro.MaliciousHeuristic-6298845-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- storefronts[.]pl File Hashes
- 23b90b1c55fdbbd371655da0ccf359e891deb51ed5bbc0ac772c5d572f4b3a42
- 2471636a92daa0a54095aa66b55ad2fea5fd5d6372b0be9d65d1d1e2cef31bd5
- 2b24221aabc8cd18e756a579b29a005fc9c33213f5ec963b9b6ccf4e6187b23b
- 4b781b8370f973b9204b44c8ce3615692fc66c1613967a44924984d35fba7bc4
- 4ee6b9bb8e903bed9a82c7dad6d62163e3a4f759ade5f5f8fcf899945bfd9264
- 564c37dcd8322bd6e8cabc788f982a35f7d3e335c3d736ce544fc17a6b090183
- 59b54e7c4e052adbc1d64dc61623af6f55db1a8692b373cb6ca871ba087feaac
- 6930d456c506c94b9e19a08659181b7d376254dca652d0e56c305764867578d2
- 6a0eae0addd6ce84966ac1bd006e9582036eaaa1011a38190f700871cc37de24
- 7045d8f339cab73cf0ec7f31a7b3a31a84057f0b275f789f4bfed9dffee35564
- 7638745d08de218fa16e9c0828ed0a1139223d3ebddf4bb528bc3ae185cea90e
- 81cdded9aa21513ad9c6ae04455a7fce68129135f3358b9c5e28a80139e78f21
- 93472e054b4b4fcc54a71a32b6275f8b35c8ef84490248d21c094f19a537c773
- a0bfeb90468ddf50a3c85d5074e002b1d89995d6377eceeb0781ba5292facbcc
- b3dfdfcfea160ed34eb69da55909294f78d2b5a6320cbf5151a3da01c6449631
- c185559d0a38e782167beacff78a7a72544d82890b5e5723e6a25a70e6e16d59
- d2c1b89129e3e26544bfbef3fac4567c3629817a98ded9ce5c7dee485d0364a9
- f2e4fe273c4a8cc1cd7799d5558c58b8a08dfe160235dfa2eb2a8bad9bba40aa
- 02481825e922c38ba797ebc18d5a8273ede8c5a4d52eecd2f58eb569533d780b
- 06736e5f3127a54bbe6bb25f4a82ca95371e5cc8654a893c02d3d4e677e0b916
- 21b039f3171f26911290dad3e1ce0da6d6d3545e11f9a119408922ac2ae06db6
- 2643f9f8dce45983eac80feeebd16adbd498e3a644ef8b05bc40448be9342ddf
- 2ac6b5487c69427476b48bcbbddd7646842e02363a0d4ebe1b1998da6d1f55a8
- 2dad87b69ee91bfa71d911b791e5468efb6ce689ccc4cde3e91626cbfcfc14ab
- 2f4853b54c36adf9ca9fbb163dacedee78b6b027fac3c24c72120e9d8cc6f01e
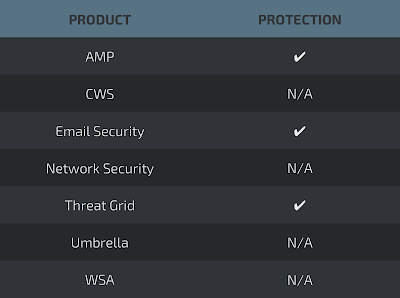
Coverage
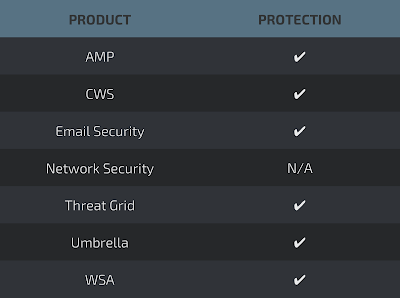
Detection Screenshots AMP
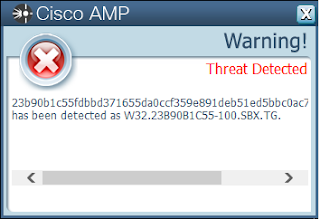
ThreatGrid
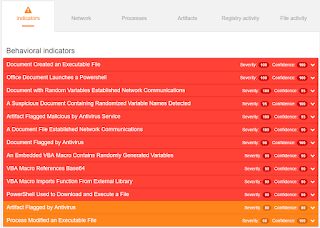
Umbrella
Malware
Win.Dropper.DarkComet-6301230-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A File Hashes
- 05C8DE4B97737440913F5C714082AD647281FA50F1904B1BF11EDB8560294FAC
- 07D9D6DA8C6CD162DD9FC78AC48EAF82BC49D4239908AF354E44C4822FE06D62
- 099ADD24586D77C5F2B8EFB9C33A8A11B5A0C11001A8534D9635A674ADC260AD
- 0A155F4F20367E4D23B6D238208FA5F943A1341E47BDBB2DBC520CCB27AD120B
- 150420EDB4BF00DADCF71601781DBE3BD6E34CBA767153B9F82307EDDF391395
- 15F2BB3B4A12A6F5B0965FDE62AE21B2796D7659BBA8011FC22AF40D465984BE
- 318B2A4F06345E95C63E4623F52E0E7C57257548C74E0C7A272FCB64D3F49692
- 4B0BB06E09ED0B2EDB085641E125490E9B1A6CC5652C05C77C78E47CF9448D35
- 507874BA705282183F928D3AE11ED5497A0F1EAC3368DE75C392D17749CB8EE9
- 55FDFC65C0C10A958239E0447E5696989FE66557437EB725849BB578D882D74E
- 5D31C073C4B7322A7DE871D533D520DE2444466D0C944CB06F6244D2CE57D49D
- 6597E2DD82FC203BA2C609B358B2E0CAE37A4309808626DA27BD58614077D646
- 6A23031FDD70C6D57D8FE9C8D3EFE6A423C38BF2D46B9B24959E5CA7D0714FCA
- 6C652B0E4998456F150515EBF50CA569CF373BA709442F6909DD7D4330C83D2E
- 6EB12C46F0605D8F915C8E895FC70D189D9E8825775EBDB464A9A24834887E60
- 776B2679819B1E0385E1630EEEC50190DAAAEC0EEF9F659EE728C47991FABFBB
- 77FA104262E3FF983B3418540FF744E0EAAE5E66388333ED785EF6F5AA2801F9
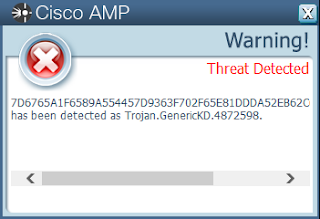
- 7D6765A1F6589A554457D9363F702F65E81DDDA52EB62C600250E0F94C473A16
- 8590486CD299DAA9BF42497EF28028364E4E18B6C60B725736A7D2DDC73BBC2F
- 92EABA06563800BA670249E90D91C32F9D315889439BCAA73F24D2C08E285B84
Coverage
Detection Screenshots
AMP
ThreatGrid
Win.Trojan.ServStart
Indicators of Compromise Registry Keys
- HKLM\SYSTEM\CONTROLSET001\SERVICES\NATIONALLWC\Description
"Providesufl a domain server for NI security." Mutexes - Nationallwc IP Addresses
- N/A Domain Names
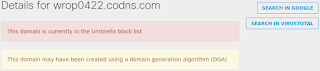
- syhaw1516.codns[.]com
- wrop0422.codns[.]com
- ansbase.9966[.]org File Hashes
- fbbc6852ff1947fcd820b90e60ab71af93ffad079bd13a0d2b514955bb1c9d62
- 40eddfac964b69ee2e26742faaacfe50960fa0232a1b9a11c382e61cecd700ff
- 6106eda3ae39449fec42db2caf4f1b5f994d72b5a759dddfd77a8a29ebb3f497
- c106435a2aced27d03ee5531eda025b14cec106106a1c7ca750127090f6d2039
- 8d4366eff17da1c18ab3fed1692628756a8f41f3145877f895b7ef950055262f
- 3be7ab79f032cf24b09fc05b08544fd61ec7e3fd355f8ab7b4580eb43d8c3e55
- ff6b7320d6b75a638c0f2d024f43853dd78993276a8f6b5f7463d6317858dd9c
- c9a193d273f606860bee0dd4a878a6421233b05ac4c6faf357d9324f0d6a575a
- 932d8d5829570237e9ab7688dd2d3c03812a05157f72af124cabf530be583789
- ba07a79a2f4d51eaac585b0f50e3b1e61d8fc555592aadb1e5d3916fb26b0e27
Coverage
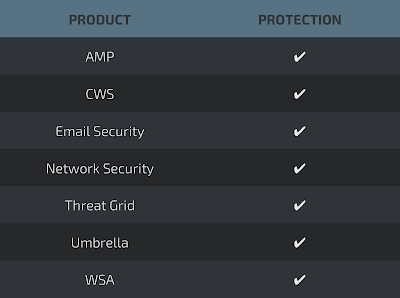
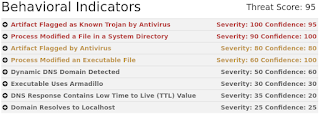
Detection Screenshots AMP
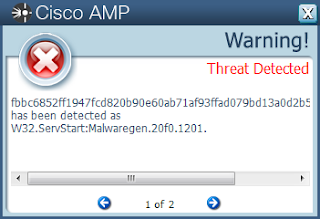
ThreatGrid
Umbrella
Win.Trojan.Agent-6298180-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/AIP Addresses
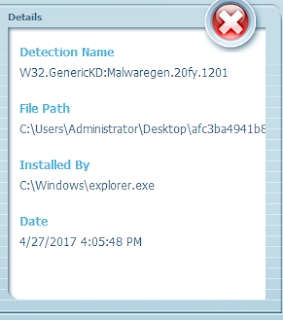
- 212.129.14[.]211 Domain Names
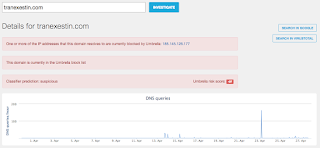
- tranexestin[.]com File Hashes
- afc3ba4941b89a4467e2f1a4ab0df2c88ef5e39264182a4b3a2dbbfa5b022e3f
Coverage

Detection Screenshots AMP
ThreatGrid

Umbrella
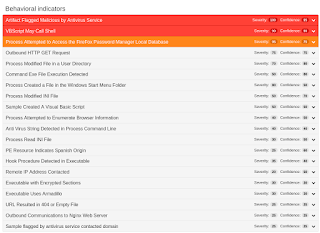
Win.Trojan.PWS-6299789-0
Indicators of Compromise Registry Keys
- USER\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- \MACHINE\Software\Wow6432Node\Microsoft\Tracing
- \MACHINE\Software\Wow6432Node\Microsoft\Tracing\tmpVtFw4a_RASMANCS
- USER\S-1-5-21-2580483871-590521980-3826313501-500\Software\Microsoft\windows\CurrentVersion\Internet Settings\Connections
- USER\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\Microsoft
- USER\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Network\Location Awareness
- USER\S-1-5-21-2580483871-590521980-3826313501-500\Software\Microsoft\Visual Basic\6.0
- \MACHINE\Software\Wow6432Node\Microsoft\Tracing\tmpVtFw4a_RASAPI32
- USER\S-1-5-21-2580483871-590521980-3826313501-500\Software
- USER\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\P3P\History
- MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters
- USER\S-1-5-21-2580483871-590521980-3826313501-500\SOFTWARE\MICROSOFT\Visual Basic
- USER\S-1-5-21-2580483871-590521980-3826313501-500\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2 Mutexes
- N/A IP Addresses
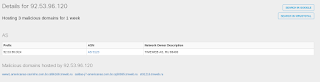
- 92.53.96[.]120 Domain Names
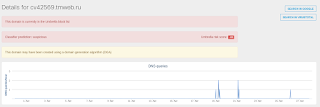
- cv42569.tmweb[.]ru File Hashes
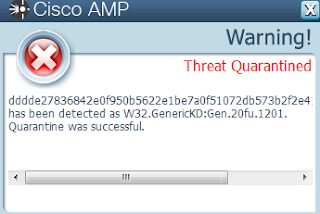
- dddde27836842e0f950b5622e1be7a0f51072db573b2f2e41d20d4b4c45028d8
- dc086f745c35b2abe58675e546b475ed64f15ea6e9d4492a0502476f784ea85c
- 97cd05c529002b85ae756a9e7b7da7a538026583f0886a235cf48b72c378551a
- 2992c6ce7ccda6fef751a912eafb8a31e3426bde8964ccf31b0512390bd61615
Coverage

Detection Screenshots AMP
ThreatGrid
Umbrella
Win.Dropper.Emotet-6301061-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 188.165.220[.]214 Domain Names
- N/A File Hashes
- f566fdc382f6988599cb16894d8a9a92e291d83574834de705d6367b520b6b50
- dda1fffa38e3f9d30833d201b542422aed15a41253b2a72797ad38dfba8fe535
- 6d4fa878e2930cb3bedc2078855f6d7db7b6b136464f6dff256d8c62657b505f
- 8ad1c1655d6d3b2a4931ae2dd9eb4e3b7be488a7f39b9c396fe1eeda2eda05a7
- c0e8a92ba6ce12d803ecfccd01432f855e6fd9ad19825602a74a081459e25389
- 5598fdcc6c0c2e7bdb095193a5f986e6cf22fdcca26c2e8451c46d787ef18435
Coverage

Detection Screenshots AMP
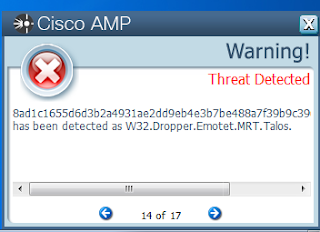
ThreatGrid
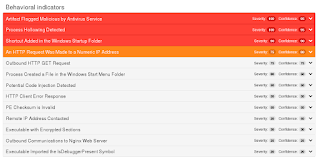
Umbrella
