Today, Talos is publishing a glimpse into the most prevalent threats we've observed between July 14 and July 21. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavior characteristics, indicators of compromise, and how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of date of publication. Detection and coverage for the following threats is subject to updates pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
This week's most prevalent threats are:
- Doc.Downloader.Agent-6333860-0
Document Macro obfuscation
These document downloaders are Excel worksheets which use obfuscated macros to trigge Shell functions and leverage cmd calling powershell. The execution chain typically is Excel -> CMD -> PowerShell download and execute. - Doc.Dropper.Agent-6333859-0
Office Macro Downloader
This is an obfuscated Office Macro downloader that attempts to download a malicious payload executable. - Doc.Macro.Obfuscation-6332451-0
Office Macro
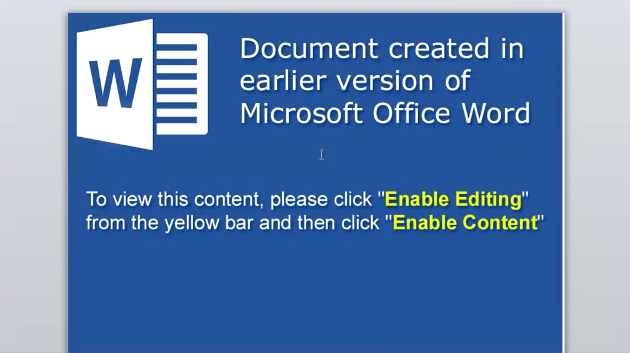
Malware authors leverage Office documents to compromise a target system. To bypass anti-virus products they will employ obfuscation techniques. This cluster uses Arrays to indirectly access data and reform it into the required data to evaluate. - Js.Dropper.sPowerShell-6333821-0
Dropper
sPowerShell is a JavaScript dropper for both ransomware & information stealers that are written as PowerShell scripts. The script itself is encoded with Base64; the original JS script is responsible for decoding it. Once decoded, the PowerShell ransomware gets to work on encrypting files based on an inclusion list for file extensions. It will not change the file extension for affected files, & it's up to the user to discover these modified files or the ransom note that is left for them. There is no automatic prompt for the dropped ransom note. - Win.Trojan.Agent-1388716
Trojan
This polymorphic sample is a dropper that will create copies of itself on the hard drive under different random names to ensure persistence. It can carry different malicious payloads, so it can be used as a delivery mechanism for different types of threats. - Win.Trojan.AutoIT-6333854-0
Trojan
This is an AutoIT malware which is packed in a self-executing RAR archive. The malware is using process hollowing to hide itself from a debugger, is communicating with a remote web server, steals passwords from Firefox' password store and adds an autorun registry key to achieve persistence. - Win.Trojan.DelphiSpamDown-6333856-0
Downloader
This sample is a Delphi downloader. It is spread in the wild and it is related to a massive spam campaign. The binary is written in Delphi and contains anti-debug and anti-vm tricks and tries to contact a remote server to download additional resources. - Win.Virus.Virlock-6332874-0
Virus
VirLock and its variants are polymorphic ransomware that not only encrypts the files on the system, but also infects them by inserting a modified version of its own code at the beginning of each file. It will replace each file by an executable disguised as the original file, with the same icon and its "exe" extension hidden. Once executed, it will infect the system and show the contents of the original file. Additionally, it locks the screen and asks the user to pay a ransom. It will try to connect to google.com to check if it gets redirected to some localized google page such as google.co.uk or google.au. It will also try to spread to network shares or cloud storage platforms, in an attempt to increase the damage and potentially infect other users that may inadvertently open shared infected files.
Threats
Doc.Downloader.Agent-6333860-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 52[.]14[.]80[.]76
- 52[.]173[.]193[.]166 Domain Names
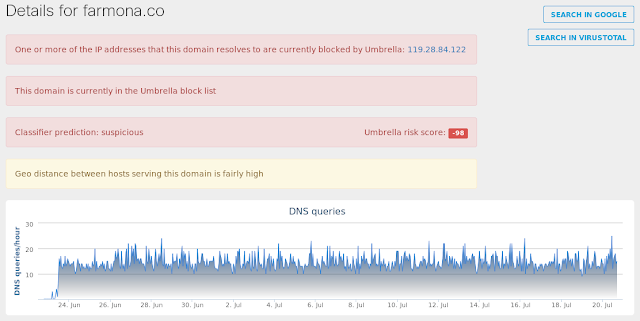
- farmona[.]co Files and or directories created
- %TEMP%\CVR668.tmp.cvr
- %AppData%.exe File Hashes
- 01c4f96c8117df219cf9f50723454ace242edcf2d22b09e8e72c5d0c92aad540
- 01ed6302a7ea8d4c54d439b7016b99b6dca275f85d22611811bac8c135309d41
- 0634216b34baf0fdc293002632932312293fc4854701b143c6f4735e8cd98b45
- 070e56e7170fc63c1c42c3b0b37df5a25f5c7e2e0a5fd454e8e8e63de2b71bdf
- 07aa3365d733098e11e91ece1628130217414488d3fce0e2e261bfb29ab6fed9
- 0be6e5bb277cbe815beced059aa5fb5160954dc8fd3fef918746caf276cc82a3
- 0fc8af1a3deb4d2895b9bb202278299369a16950239288577472bc06fbf07e4b
- 13fd575d1474ae579f55615733f75fa50231447b8653e6eb58678103ee82e99e
- 1b01632e1a44445124165ed61592527fe649a32ed889ee75fdb73d07bf396812
- 2248f89b848781c0405cc0cead60172ec75e035aca12e8c147818192fde2266d
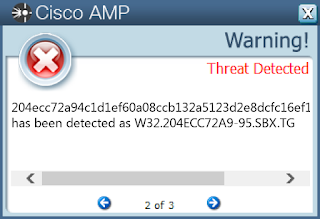
- 204ecc72a94c1d1ef60a08ccb132a5123d2e8dcfc16ef1cacebb20887049ec2d
Coverage

Screenshots of Detection AMP
ThreatGrid

Umbrella
Screenshot

Doc.Dropper.Agent-6333859-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- atlon-mebel[.]ru
- ayurvoyage[.]com
- enzyma[.]es
- inormann[.]it
- kms2017[.]com
- pta-babel[.]net
- studio80[.]biz
- sxmht[.]com
- test[.]atlon-mebel[.]ru
- tidytrend[.]com
- westsussexcentre[.]org[.]uk
- wizbam[.]com Files and or directories created
- %TEMP%\proshuto8.exe
- %TEMP%\~DFFD1107AB284DD884.TMP
- %TEMP%\serenade8.TEMP File Hashes
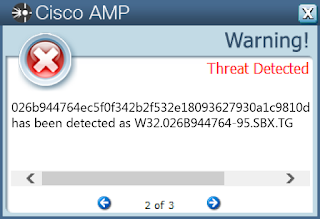
- 026b944764ec5f0f342b2f532e18093627930a1c9810d235a4893ecbbbe4eaee
- 04f5160bf3126ad52a819a86cf4807dc83c89a4e5a2643b49b3fe60bf01c8419
- 09a43a41f182b0677d28b7e9cc685d1217f5c1fca63af4418f0a9ef776f6dd0a
- 0a0bf44d664575b194063536138d0b5ea9d3583e956e675462b55decf4ad73a9
- 0ea9107334209b304b650ff86854862d4eed68e616aec015618853b1d6a3c001
- 1c32493b72d3c3da9b7d4b9022edfdec445a7feaa261e621799c1e45241b5b2f
- 1dd941235ba3aae55c0f876131d6381ef47c4c37f6be0116b61a5ff0ddf4da6a
- 201a567836576380edc8d7a1b7f2e70c4127faa7ea541da4d7e0457401b2b492
- 2debe28ebdeea8789a136170782018789d7ba6e8d07b8289231c8b6aa509a839
- 351376c7a04ab7bf3f4a22b124165c4817d7fefe35dd2d0834cd3fcf3c580043
- 36ac209d2115d4b64b3b2b41b8731235168ac71d744740dbbc73f6c13cc85bab
- 3ceb74963648d8adf4b47303d74d344628257dc36cf87a4330099fc264fe6ae5
- 46bdd38ab49faaed1aa40c17d17e2a45ba87236dee0802c6e9e1385bfc1fe261
- 4aca7a72441a2100f4d40348e813ce0bcdb87e7d311e4e2e3b1dc53eecd9f149
- 4b62feae568e3aaf8510897ab6c674283a7d133d4e72b4aaa4864a465bd88807
- 4d4906439c50c3c8e80b40e0f1135f3c6df31b1fa596f668d4f8c48ead902dc3
- 5e7442c9c6b95f9a7af5ce9a08b1d61852e1da901ddf96e1604374be36d823c1
- 6274606653a2bb4470d3acdd72f11af37827253f5a728d539da9be0a6fb12db3
- 631e4b651c157a1179bd28fc71cc072a933ec7a9be962fa4e758963c4f450673
- 6994c078ad88915221a6679dcab25f942a6799c998bfffd36004f500faf1d2aa
- 69fee7f159df45b2f3fe177b0e4f8377b2f281d907c15ce69b3f5fd43592d297
- 6a7fcf70672bec03c73443dc26ad8cd5dbed6227de7073d7d37d2c920d3ca5b7
- 77deb4917f19577c06643e0268b96b12050d6814c07e961f84bd143189ba23b8
- 7b28472b8552e2f9f63126a66ef1bec226acf49919e821c8204e0142864af7c2
- 7c31ebd234e9ea4e8e5176cca74f95cf6d0f8ebdad6f5bae0aa07229cff3557a
- 8046e1b4a24d714812f4fcfa7f7debfa2057a83c8631b7e2112d37653c83aa04
- 8902a87a99470edc2210af7f660ae3f1d032a4e764ae5415f00b3de4e873715b
- 9217691c969ca90bba7e68648c5d52c1fec4183f2837adb407b55e6957cc62c8
- 95dfa7cb08275d55c2daa3dab39cd3502ed8e9221501ccd43096c4dcb69574df
- 9a7972ec543717861bf0030e35069c5d672ed0447a1f7690f8e3992329b4e08f
- a5067cd834500ad631443d66f52a8454adedcc316bdd9a9f340587efe3d71862
- a912eebe77cd06413744e8bca95c7bc4d7200a82097178cbfd478778d89afc16
- af598ffbba3c59ce109d2ddd9ef58425bd3a8a70bbbea48b14460dcef21704d7
- b1828e83a4d01b45adb238165e17520f5853a2a8d1ac083d2f6130be8813e5fb
- ba9ae0515d7d720634114de6f669bcb9c9bc8bebb9b30df98585b8c2751cb419
- d34e29aeae628324e27067f1b0ed9895b335a99eed2bad836b2cb08cc311276e
- d3a1dc1018514102ce83b054374a0422328ba812f78a9fee7d17b224a7b7fb9b
- e3a122deee0913710df8e2d8137f089123e455195a6d71dac072343fc8e48c2e
- ec67964a20940b42a58a3149327e519c97505ae0227566d31a72e94a31add0b4
- ed8779e9e0231c4882152bae2be367a9cac0d2b270a5fba8d9dd56ccd6ddcb34
- ee5b16b15dd712ff7e0ada9e6b93da04fcfe9043e53a605d0ace1fe365f0bd54
- f0892554e22c923645f20e9de0920199a791f744dee18f9c8df7f0b0ffa954e0
- f921d1fd16fe5735f1abab55e836fd6817e9d6e340d0d056af25b7214559cf7b
- ff29411724d4cac3a6553ab621180f8a2c05cf01573c97873061b9df9ba57246
Coverage

Screenshots of Detection AMP
ThreatGrid

Umbrella
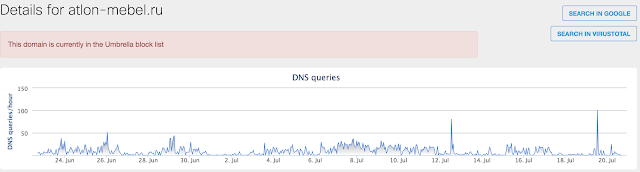
Screenshot
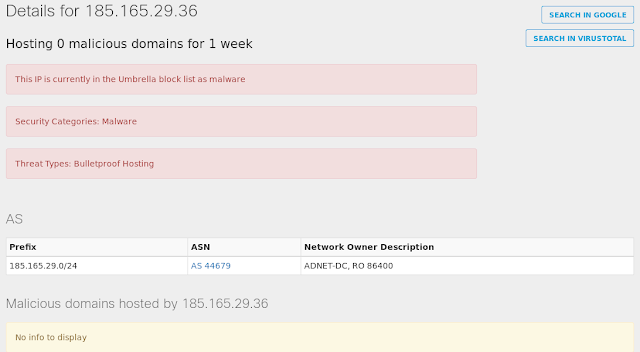
Doc.Macro.Obfuscation-6332451-0
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- 185[.]165[.]29[.]36
- 52[.]173[.]193[.]166 Domain Names
- N/A Files and or directories created
- %TEMP%\CVR65CC.tmp.cvr File Hashes
- 41b9c93fed52bffe68d03abbcbe42086a9baf743d56f9262abd5b4c7fcbff951
- 4c5f92378c3fe002163abb763ab30de3b167512255af8f90c0ab7ca85e15fe7f
- 8c0559c86e7879ecf25442bc0a8105193d44e9641ac939077d43f6c4dcfc4e9c
- 727d8957c910dd733b4960f22535e61375e417cc521b820ae8a917597af86295
- a84e3659977948b8f14cb2bfacef19d997463e779fed8750fa2d44b4342584b4
- a4e076bdea2bdc1028d232079b0bcf42a9b4997fb43e78fbda745f6bb047612c
- 404de9c0ea3f8061c69e0dac80c6706e9ad263059ed845f1d69fc77b367a51aa
- 7ac2d7693119e8e07ee9ab0979a219f99763deb2b4134e8a6c18cec7aba1a76a
- 29015d08a221749ca7cd1b9526ae4c434457199ac3226236f9e57fdb01b21213
- 1259e834561574787f5e8c6f0fd7e3af62ce566317275ad6e0484b2d2d02904e
- 341b86bd427dfca140ef6b3f47c7f269fe3ada974692237cc038f5910326d806
- 5d91e7426fb87e5f2c9a5aa575d8bc0e98b7e1a09947dcb4e4943c5c047933d9
- f11534d903c19da7f9b951419fb31fc8027c27f7ed7e3fdb89a923004a838ca1
- 513a70f9692100bab9aee761125a446c7a7fb2ddd8395810f64c73cedd664f8e
- f2fee82c08af4579275a7bfd7859bd9031c43a4c871ab6bb1d3fe1d699c020ca
- a0b29989213e1c2e08bcb136d77164251fcff105c640a9ba75f9ed87c6a0407b
- f04ce92cb9f190f8c06d444ac5431f637b6ea8ba864201a549903e3115968403
- 3743bc035609dc41608e2580bd9ee1555bbd8e9311dcf879e12821ce40727db5
- ab004137cd4eeff2528c749bc80fa8c05be279fbadf54fd48eb433a63ba9ebaf
- 2611831b22f6b0df892e363d429a666b5a4bb9303a97b30c527fb4f43379a462
- 0dd337e3bef51dd39867317b47870076c8bda3efede772fc571b48d59ff79bcf
- ec0aba7dec0510afc007260370f08f166f6aeadbf0e38206aef3b2df96c6fddb
- 58bcd393831d35adf5343ddeaedc3de4f9b4c11565cbcb21e220ef20d34061d6
- 7531238a3e7a788700bef153d999c6527975c108176e435a0ca200e15fa08d5a
- 5702fa93b08399d8f8d7d1ef1eb2902e7f37a9bbaaf5d9aa6b85a2844224662e
Coverage

Screenshots of Detection AMP
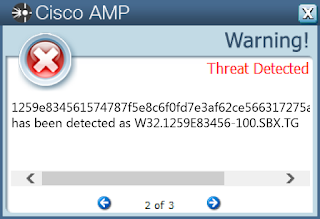
ThreatGrid
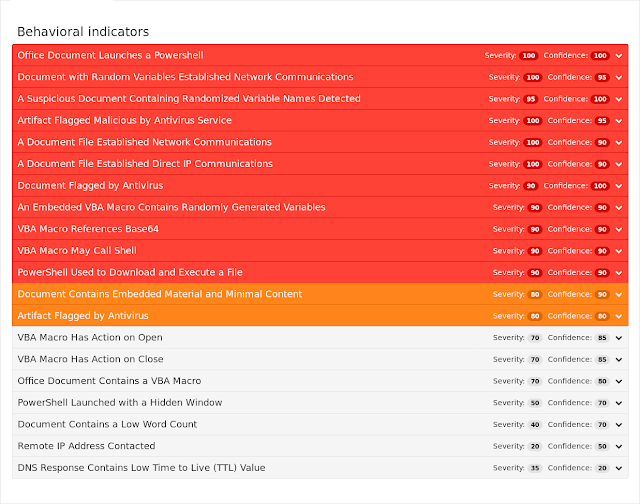
Umbrella
Screenshot
Js.Dropper.sPowerShell-6333821-0
Indicators of Compromise Registry Keys
- HKLM\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection Mutexes
- Sessions\1\BaseNamedObjects\_SHuassist.mtx
- Sessions\1\BaseNamedObjects\DBWinMutex IP Addresses
- N/A Domain Names
- joelosteel[.]gdn
- ipcaservices[.]xyz Files and or directories created
- %USERPROFILE%\Desktop\_README-Encrypted-Files.html
- %USERPROFILE%\Documents\_README-Encrypted-Files.html File Hashes
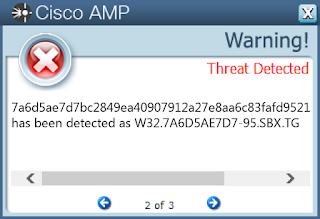
- 7a6d5ae7d7bc2849ea40907912a27e8aa6c83fafd952168f9e2d43f76881300c
- cce0da7814b5966ffacfecacec0e87aec83989889b56e4dc37eed7873b51617f
Coverage
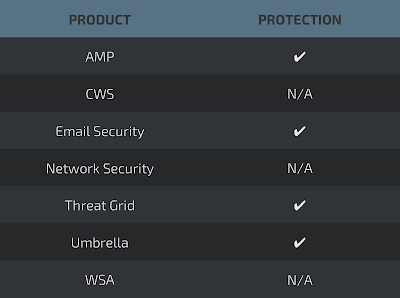
Screenshots of Detection AMP
ThreatGrid

Umbrella
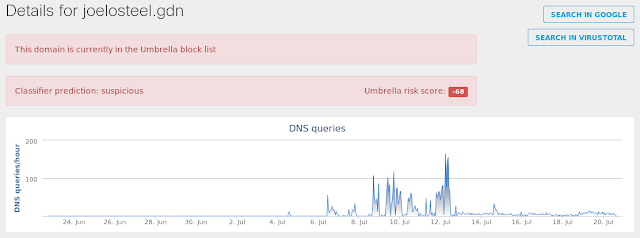
Screenshot

Win.Trojan.Agent-1388716
Indicators of Compromise Registry Keys
- N/A Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %SystemDrive%\e86nw5.exe
- %SystemDrive%\4kh4ht.exe
- %SystemDrive%\ucrr38u.exe
- %SystemDrive%\fllx91x.exe
- %SystemDrive%\9f2c5u7.exe
- %SystemDrive%\022240c.exe File Hashes
- 6ffc7684a7ce4e263d0018310e03f4c81df776cd2ad1fdb26e0cb46ee5a9d899
- 588d681952c3d07a6f2dd740e6253a6160a37ec3d80d376f742b2f1c9e9fa3a5
- 0c27abc4b32cd84d8ed11907d8b47e0caa41af884efbe599e287978ad56cc6d4
- 56fc60eff1ce21bc0662abce0ce74834e530b4baf297f055bdfdc5bb77c22ec6
Coverage
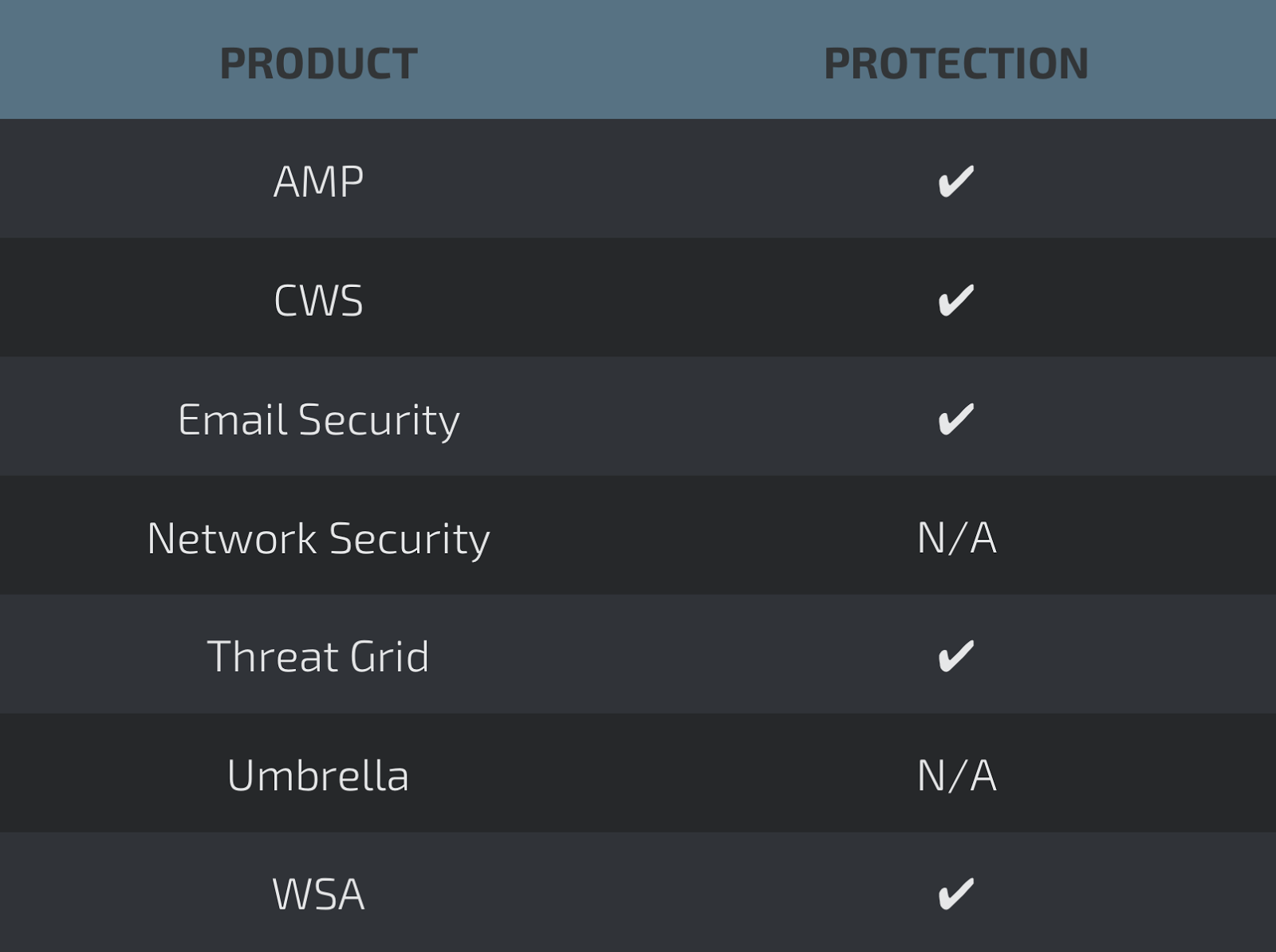
Screenshots of Detection AMP
ThreatGrid
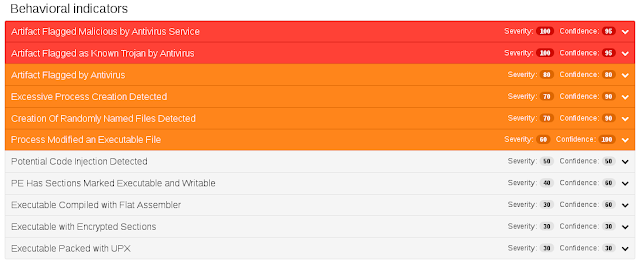
Win.Trojan.AutoIT-6333854-0
Indicators of CompromiseRegistry Keys
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Mutexes
- N/A IP Addresses
- N/A Domain Names
- cn67975[.]tmweb[.]ru Files and or directories created
- %TEMP%\fjs\[a-z]{3}.(ppt|xl|icm|pdf|txt|bat|docx|mp4|bmp|ico|jog|dat)
- %TEMP%\667796.bat
- %TEMP%\fjs\svu-mkc File Hashes
- 927bd28d825adc6569d1e307bd3709f73350b3ca2b0f98bbbdd2370526ae19b6
- bb51a0200e84137fb1c07e39fbd7f0ded1eda78d3c95cfa1e16887f0762ab665
- 2cd44a3204106c4fa3e11c310f21a3d0a89795ae90cad00117c779386ea619fd
- 83a482b1771474915838db7251d00cf12ae5171c04966621bba82c5829e57b4a
- a831d5503c549917d333d45c72532f0407ed306ca5c95478dad11cb34342ca60
- f8305d63f8d4ebc4b4c4bea7c3dd75b3d3c3f53aa2f28cc789a2573d55b83613
- ea047fca20938acaeaf82d7753a86bdf9c6ed1bcb6573634d8f515d15b6ddd13
- 62f72450c470bd01096766ac25e8b6ca4edb79683c2ee5b2cc89ec2234983c44
- 38dfdc80844d6f6b0d1a73843f1a4704d7bb12cf2ca61d98a54d1cdb5722ac66
- f81a37d816c639fd977d7781f7fe54cc51e2e34aa3bb8bc877c74ae140025003
Coverage
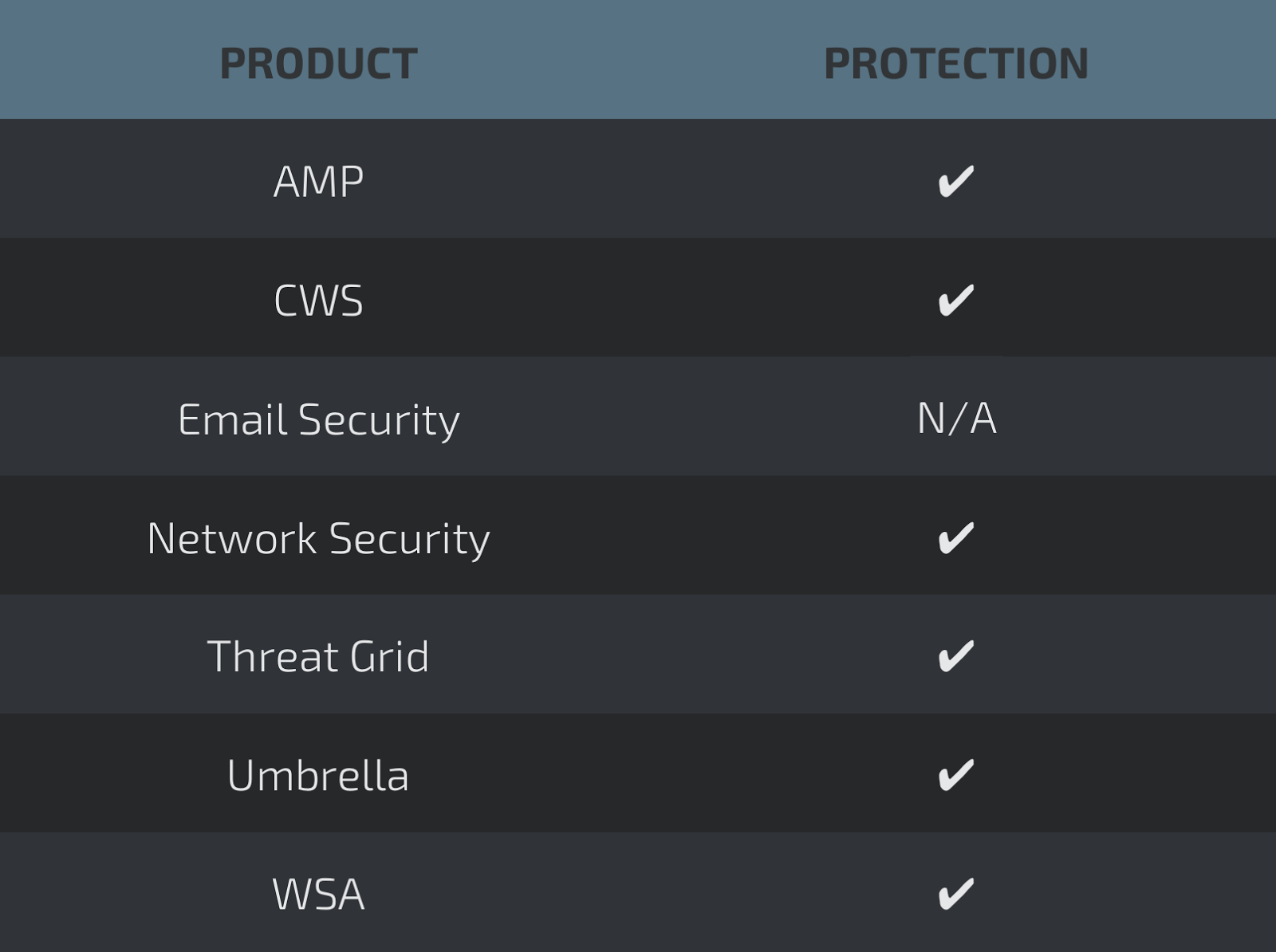
Screenshots of Detection AMP
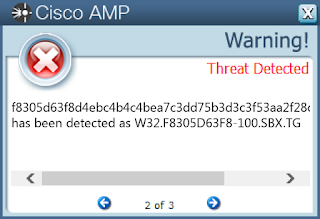
ThreatGrid
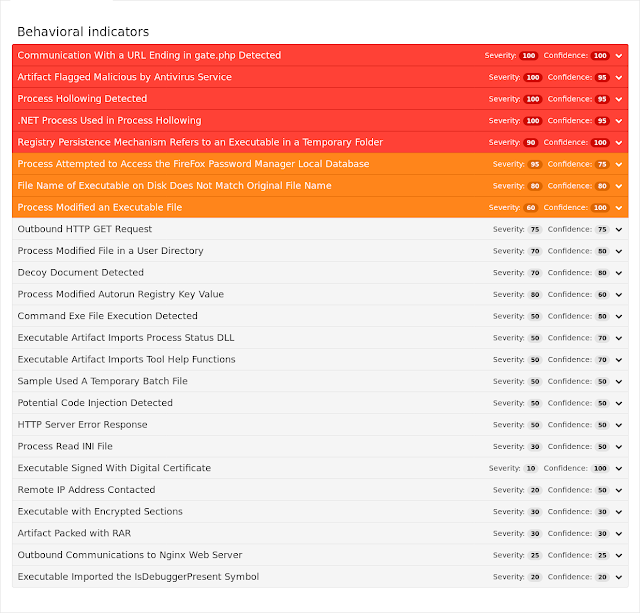
Umbrella
Win.Trojan.DelphiSpamDown-6333856-0
Indicators of Compromise Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection
- HKU\Software\Microsoft\Windows\ShellNoRoam\MUICache
- HKU\Software\WinRAR Mutexes
- DBWinMutex IP Addresses
- 92[.]53[.]96[.]122 Domain Names
- cg51478[.]tmweb[.]ru Files and or directories created
- \samr
- %System32%\wdi\{ffc42108-4920-4acf-a4fc-8abdcc68ada4}\{debd4f12-5573-4e21-a11a-2adccd61a055}\snapshot.etl
- %System32%\wdi\{533a67eb-9fb5-473d-b884-958cf4b9c4a3}\{bc3d8877-b46d-4746-b041-b538af5e2cf0}\snapshot.etl
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\713906.bat
- \TEMP\scan sample.exe File Hashes
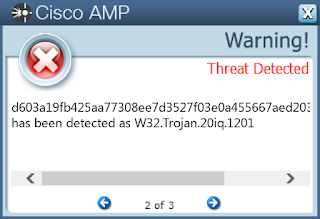
- d603a19fb425aa77308ee7d3527f03e0a455667aed2030b4fc2c46388a230dad
- f23220f487d021aed897deee04e7aaada2521d096406517cd3adcacf4754beac
- 72464898f83126f1a89d76cf76b2867b58655b3b316c2000dd185f2c31a4d786
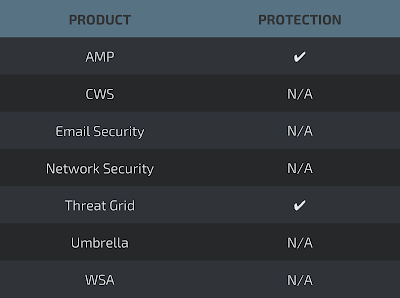
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
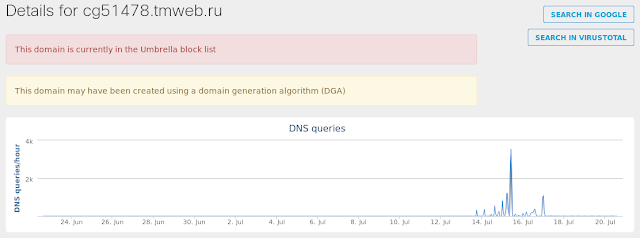
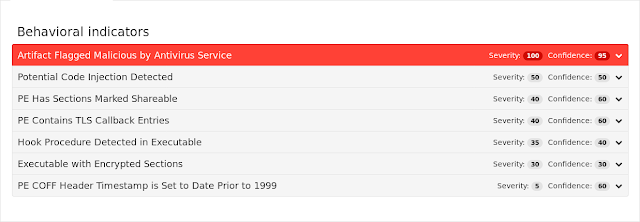
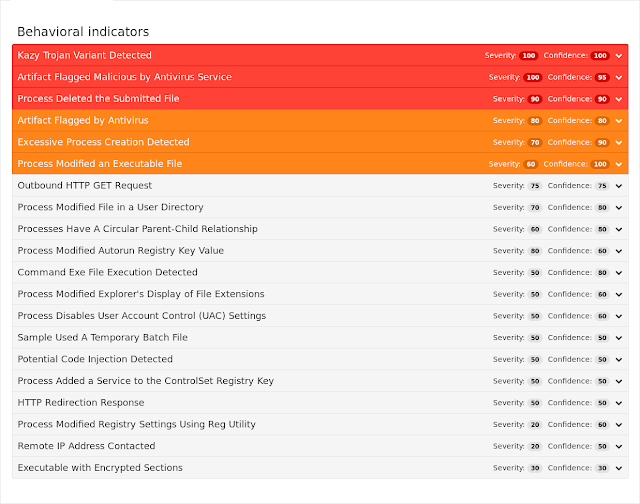
Win.Virus.Virlock-6332874-0
Indicators of Compromise Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VOSIYOAG
- Value: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VOSIYOAG
- Value: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VOSIYOAG
- Value: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VOSIYOAG
- Value: Start
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: rgwIEcIs.exe
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VOSIYOAG
- Value: ImagePath
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: IMMwgswc.exe
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value: HideFileExt
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value: Hidden
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VOSIYOAG
- Value: WOW64
- HKU\Software\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\VosIYoaG
- <HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Mutexes
- \BaseNamedObjects\OeoQEIQU
- \BaseNamedObjects\JMcsAgIg
- \BaseNamedObjects\eKQoMYQM
- \BaseNamedObjects\rgQAYgUk
- \BaseNamedObjects\juAkwAUg
- \BaseNamedObjects\WUUMAwEY
- \BaseNamedObjects\LIAAoosI IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %SystemDrive%\Documents and Settings\Administrator\mYAMwMEo\aYEsEocI.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\eAsoAsoc.bat
- %SystemDrive%\Documents and Settings\All Users\xEQswAgE\hEEskAMI.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\file.vbs
- %SystemDrive%\Documents and Settings\All Users\keAQYows\Ngwockko.exe
- %SystemDrive%\Documents and Settings\All Users\eCQoYwsY\cOIkcIIs.exe
- \MSOCache\All Users\{90140000-0115-0409-0000-0000000FF1CE}-C\DW20.EXE
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\f1d2_appcompat.txt
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\HAIgcwYY.bat
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\JikQIUos.bat
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\1aba_appcompat.txt
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\BywQYkYY.bat
- %System32%\wdi\{533a67eb-9fb5-473d-b884-958cf4b9c4a3}\{a69f0170-8245-4aed-a99e-3b0aad202ce2}\snapshot.etl
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\vgMUkcEw.bat
- %SystemDrive%\Documents and Settings\Administrator\HQcwsEQk\iUEAMAQY.exe
- %SystemDrive%\Documents and Settings\All Users\wkkIwsUo\FcIoIUwU.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\oiwwooMU.bat
- %SystemDrive%\Documents and Settings\All Users\UUkwYskE\tIAMksoQ.exe
- %SystemDrive%\Documents and Settings\All Users\TiggsEgM\iigYwggc.exe
- %SystemDrive%\Documents and Settings\Administrator\josYsEwI\IEkIQAgg.exe
- \TEMP\f903440f2b8e05fde78b17ad34bdae047604a33af999aaee8954dc1f689d3298.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\B291D.dmp
- %SystemDrive%\Documents and Settings\All Users\OUkAAEIY\qaMAkEQc.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\NuYsMUAc.bat
- %SystemDrive%\Documents and Settings\All Users\ymYgUYAo\PqUEkQUs.exe
- %SystemDrive%\Documents and Settings\Administrator\SKsYAMwU\OugokkEo.exe File Hashes
- 81bec8df30db0bd694ecf01d3950fbe91823854ab017c0cb176d32c9ada3f202
- d49a98d35bcb6ff16206c6d1e1495d4ddf9f1911f785bccda24c2b1e0bfe3d03
- 6cff1fdde90a5708301b2d3c48729ebf3be7bb4a8f0e6992406affe034ad0a0f
- 94549c01f4ca88d7169141b7a8aaa0a79a28e2770811ef84febd639af70c7a74
- 824eed3471a9f86836ac4bced8a5ce7f57df95048a995dc0219feab771404f28
- db2415f2259b7ec9aaa6ab004a659753ad51dafccbc8696f0a5e906750304efc
- faaa74146e151d525e94e536ee2605a76c8a0d1699024979181712a03b249f25
- 7cd99c34887ea6213f18347720d7b1d257969f821bc78f6ad128f55ff137096c
- 61012a5ae49bcfc6c31110b0117c9ed3d3f810cb8053857ef3017b403aeb4ad0
- 6161ca5b2cd218ae1c277e6fcc509f571cc409ae4b2aba007d0e1ef28057fd7d
- cacc1b16c233ad74c95b051edb5542a2824441314aba3f12e0397b857222c0a9
Coverage
Screenshots of Detection AMP
ThreatGrid
Screenshot