This post was written by Jaeson Schultz.
Introduction Over the past five years the Necurs botnet has established itself as the largest purveyor of spam worldwide. Necurs is responsible for emailing massive amounts of banking malware, ransomware, dating spam, pump-n-dump stock scams, work from home schemes, and even cryptocurrency wallet credential phishing. Necurs sends so much spam that at times Necurs' spam campaigns can make up more than 90% of the spam seen by Cisco Talos in one day.
To conduct a deeper analysis of Necurs, Talos extracted 32 distinct spam campaigns sent by Necurs between August 2017 and November 2017. The result was a collection of over 2.1 million spam messages, sent from almost 1.2 million distinct sending IP addresses in over 200 countries and territories.
Necurs Recipients From an email marketing and delivery perspective, Necurs doesn't appear to be too sophisticated. Necurs' recipient database includes email addresses that have been harvested online, commonly deployed role-based accounts, as well as email addresses that appear to have been auto-generated. These are among the worst, most unreliable sources for obtaining email addresses, and any legitimate email marketer wouldn't last a day mailing to addresses such as these. Of course, an illegitimate botnet such as Necurs has no such concerns. For many months the email addresses in Necurs database seemed to be largely static; Necurs hasn't actively added any new addresses for at least the past year, possibly two years or more. In November of 2017, Necurs stopped mailing to many of the autogenerated accounts.
At one of my personal domains, Necurs has been seen mailing to addresses such as 'equifax@' --an email address that was originally stolen from Equifax years before the 2017 breach. Necurs also often mails to 'thisisatestmessageatall@', another email address I generated and put into the wild, long ago. There are also variations on other legitimate addresses, for example 'aeson@', '20jaeson@', and 'eson@' which are all variations on my address 'jaeson@'. The number 20 was present at the beginning of many of Necurs recipients. Hex 20 corresponds with the space character and is used in percent-encoding, etc. This provides further indication of the harvested nature of these addresses.
Other addresses in Necurs' mailing list appear to have been auto-generated. For example 'EFgUYsxebG@', 'ZhyWaTmu@', and 'MTAyOvoYkx@' have never been aliases at my domain that I've ever used, and the only mail these accounts ever receive comes from Necurs.
|
| Necurs email received at an auto-generated email address |
From our set of Necurs' spam messages, Talos extracted only the user alias portion of the To: address. There are numerous email aliases, such as role-based addresses, that appear to be in Necurs' recipient DB across many different recipient domains. Strangely, the list also included some odd email aliases deployed at multiple domains such as 'unity_unity[0-9]@', 'petgord32truew@', 'iamjustsendingthisleter@', 'docs[0-9]@', and others.
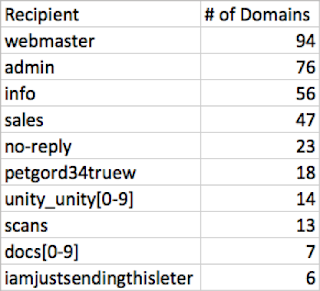
|
| Email alias and the number of domains in our data in which that alias was found |
Interestingly, some of these same strange aliases can be found on Project Honeypot's list of the Top Dictionary Attacker Usernames, though it is unclear whether Necurs obtained their aliases from this list, or whether these aliases made Project Honeypot's list as a result of Necurs' spamming activity.
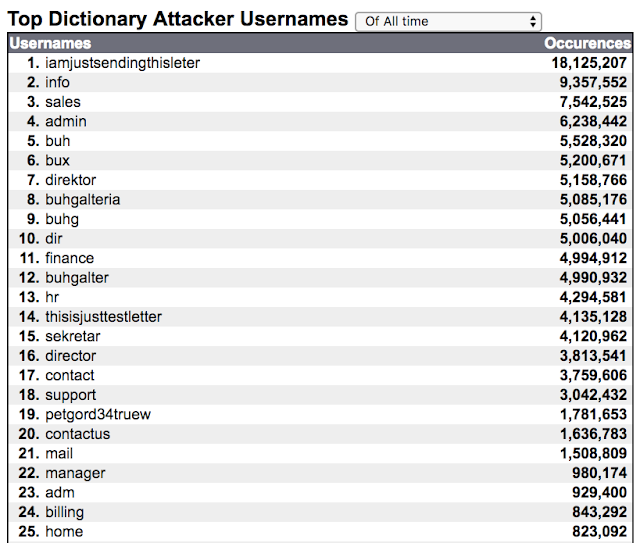
|
| Project Honeypot's Top Dictionary Attacker Usernames |
Necurs Sending IPs Next, Talos extracted the sending IP addresses responsible for transmitting Necurs' spam emails, and we grouped the data according to geographical location. Rather than being uniformly distributed worldwide, a majority of Necurs' nodes were concentrated among just a few countries --India (25.7% of total spam), Vietnam (20.3% of total spam), and Iran (7.3% of total spam). More than half (51.3%) of the sending IP addresses in our data came from just these three countries. In contrast, other large industrialized nations were only responsible for tiny fraction of the spam. For example, the United States, was home to 6,314 (less than 1%) of Necurs sending IPs. The country of Russia was only attributed to 38 sending IP addresses out of a nearly 1.2 million total sender IPs!
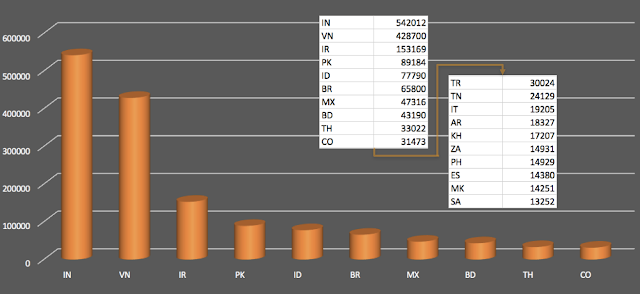
|
| Number of spam messages sent per country |
Talos also analyzed the individual spam campaigns in order to determine how often the sending IP addresses were reused from campaign to campaign. We found very little infrastructure reuse. In fact, none of the sending IP addresses in our data were seen across all thirty-two of the campaigns we extracted. Only three sending IP addresses could be found across thirty of Necurs' spam campaigns. The vast, vast majority of sending IP addresses, 937,761 (78.6% of the total), were only ever seen in a single Necurs spam campaign! This means that Necurs botnet is large enough to conduct attacks over several months without substantial reuse of most sending nodes --an impressive feat.
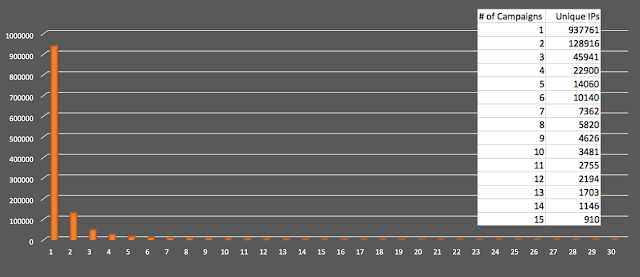
|
| Number of unique IP addresses vs. how many campaigns in which they appeared |
Necurs Spam Campaigns Typically email campaigns from Necurs fall into one of two categories: high-volume weekday campaigns, or low volume continuous campaigns. Necurs has occasionally been seen sending high volume campaigns on weekends, but the vast majority of the time high volume campaigns are limited to the business week only. The mailing list database Necurs is using seems to be segmented, such that the high volume campaigns use one subset of email addresses from the DB, and the low volume campaigns use a different set of email addresses.
Pump-N-Dump Stock Spam Below is an example of a pump-n-dump stock spam sent on April 12th, 2017 by Necurs touting the stock symbol QSMG, Quest Management Incorporated. On the following day the price of QSMG peaked at $2.33, probably netting the criminals a tidy gain on their initial investment. QSMG is currently worth less than $0.02.
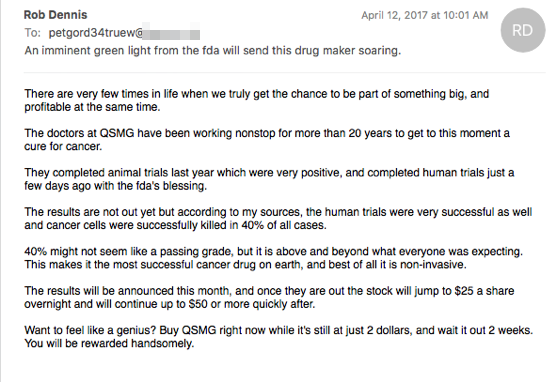
|
| A message touting the penny stock, QSMG |
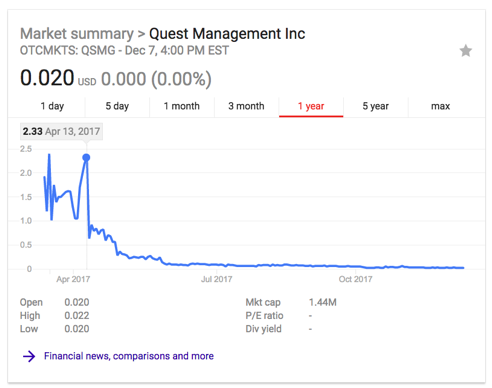
|
| QSMG was at $2.33 on April 13. Currently it is worth less than $0.02 |
Dating Spam Necurs also sends dating spam. Recent dating spam have arrived without any URLs in the body, except a mailto: link to an email address. Current dating campaigns have involved the free email provider rambler.ru, but other previous dating campaigns have taken advantage of similar free email services such as gmx.com. Necurs' dating campaigns have also been known to include HTML links to fast-fluxed domains, or sometimes compromised websites (Wordpress, etc.).
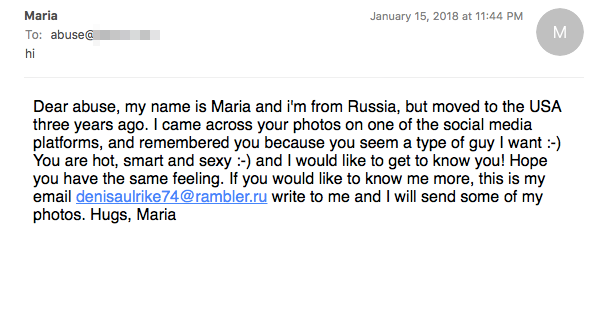
|
| Necurs dating spam featuring an email address at rambler.ru |
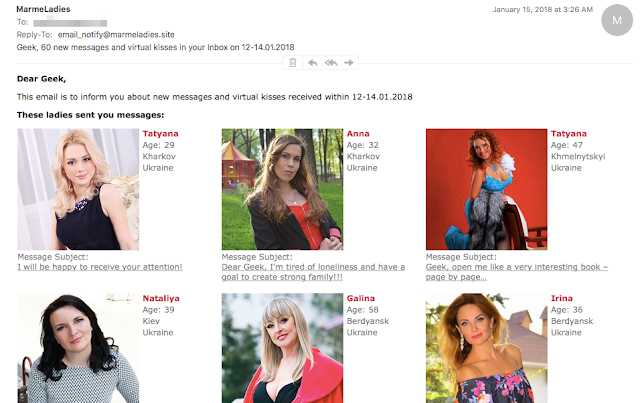
If you respond to one of these dating messages, you may be enrolled in a Russian dating website such as marmeladies.site. In this case, the criminals are making money by referring new users to these dating sites. Most likely they are being paid on an affiliate model.
|
| Marmeladies is one of the dating sites to which victims who reply are directed |
Ransomware Of course one of Necurs' most well-known payloads is ransomware. Necurs has been one of the biggest distributors of the Locky ransomware. Locky also works on an affiliate model. Inside of each locky sample, in the metadata, is an affiliate ID, which is always the same (3) for Necurs mailings. Most of the time, very little investment is made in the design of the messages themselves, as in the following example.
|
| A typical ransomware campaign from Necurs |
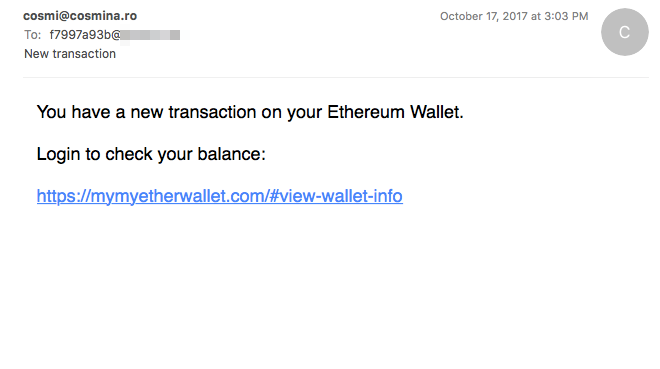
Cryptocurrency Credential Phishing The rise (and fall) in the value of digital currencies such as Bitcoin and Etherium has not escaped the attention of the Necurs criminals. They have been seen conducting attack campaigns using domains designed to look similar to legitimate wallet management websites. In the email below, note the extra word 'my' in the domain 'mymyetherwallet.com'.
|
| This domain is registered to appear similar to the real Etherium wallet management site, myetherwallet.com |
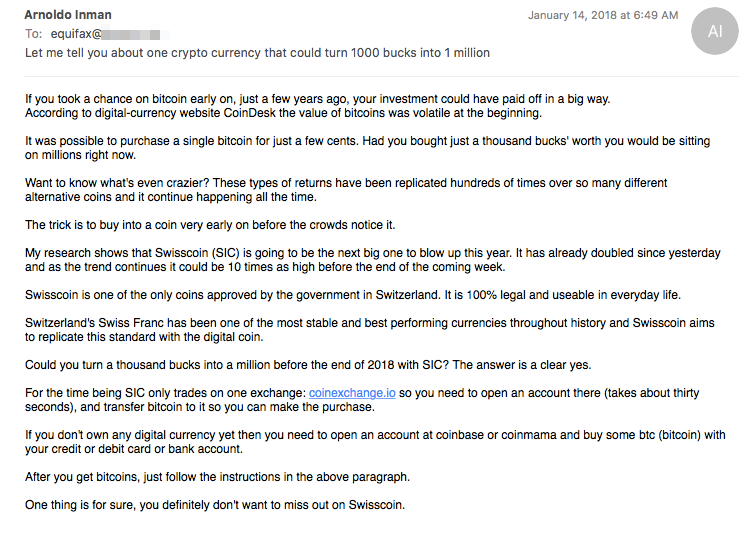
Recently, the Necurs attackers have drawn from previous stock pump-n-dump scams to come up with a relatively new tactic related to cryptocurrency. They had a spam campaign pumping Swisscoin (SIC).
|
| A Necurs spam email encouraging recipients to buy Swisscoin (SIC) |
Job Spam Necurs was recently sending a low volume job spam campaign which includes links to freshly registered domains. For example, in the email below, sent October 30th 2017, we can see they are using a link to the domain, 'supercoins.top'. (The affiliate id in the URL is always the same)
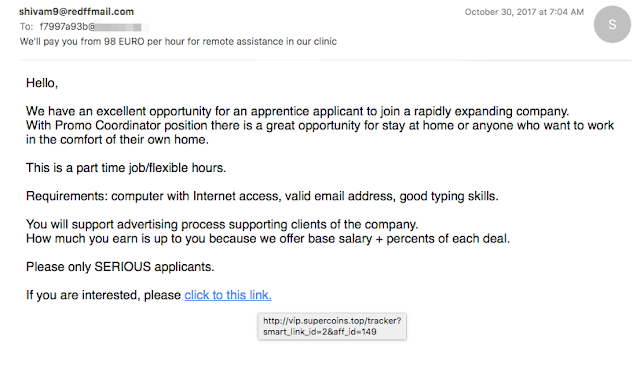
|
| An example of a low volume, job-related spam campaign from Necurs |
Attribution
whois-agent@gmx.com Checking the whois record for this domains we see the following registration details. Note the registrant email 'whois-agent@gmx.com'. This is an attempt by the threat actors to convince the casual observer that the domain is somehow registered through a third party whois privacy protection service. Email accounts @gmx.com are free to the public, and in this instance the attackers have simply generated the alias 'whois-agent' for their use in registering domains.
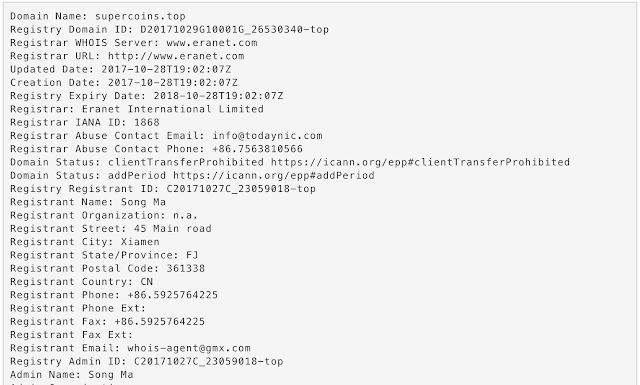
A review of the domains registered to 'whois-agent@gmx.com' yields 399 domains (from DT as of January 17, 2018). The list of domains registered to 'whois-agent@gmx.com' reads like a who's-who of criminal activity.
Among some of the more notable domains we can see obvious phishing domains:
amex-notification.com
amexcardmail.com
amexmailnotification.com
natwestonlinebanking.info
hsbc-sec.site
dropbox-ch.co
dropbox-fileshare.com
dropboxmailgate.com
paypa1.info
sage-uk.com
sagepay.infoTypo-squattish domains targeting cryptocoin-related sites:
myetlherwa11et.com
myetlherwalllet.com
rnyetherwa11et.com
blockchaifn.info
blockchaign.info
blockchainel.info
blockchaingr.info
blockchait.info
blockchalgn.info
blockchalne.info
blockchalner.info
blockchalng.info
blockchanel.info
blockchart.info
blockchatn.info
blockcheing.info
blockcheit.info
blockclmain.info
blockclnajn.info
bloclnchain.info
bloknchain.infoFake Flash Player Update domains:
flash-ide-update.top
flash-ime-update.top
flash-one-eupdate.top
flash-one-update.info
flash-player-update.info
flash-update-player.infoEven domains intended to masquerade as government resources:
asic-gov-au.co
australia-gov-au.com
canadapost-office.info
govonfraud.infoA review of some of the domains in passive DNS gives us some other important clues. While most domains are only registered for the minimum of one year, the attackers have chosen to maintain the registration for a longer time on other domains such as 'pp24.ws'. That domain is home to an online marketplace for buying and selling stolen credit card numbers, stolen ssh account credentials and more.
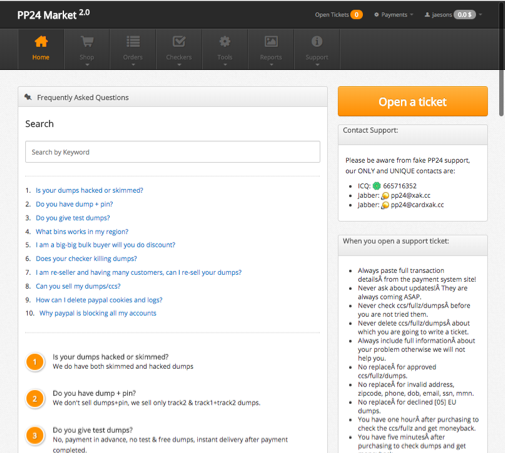
|
| 'pp24.ws' is a website dedicated to buying and selling stolen credit card numbers |
Passive DNS also reveals instances where the attackers have hosted domains belonging to different registrants on the same IP address. For example, when Talos analyzed the passive DNS records for one of the attacker's domains: 'setinfoconf.com' we found that this domain was hosted on a single IP address for a couple months in late 2016 before being parked. When we reviewed the other domains living on that same IP address we saw a bit of a pattern, and most importantly, some of these domains were NOT in the list of domains owned by 'whois-agent@gmx.com'.
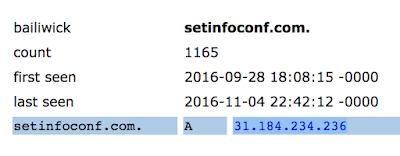

whois-protect@hotmail.com When we check the registration information for one of the above domains 'setinofis.pw', we find that there is a different registrant. This time the email address used to register the domain was 'whois-protect@hotmail.com'. Just as with the 'whois-agent@gmx.com' address, this is an attempt to appear to a casual observer that the domain is protected by whois privacy protection when in reality this email account appears to be under the direct control of the attackers themselves.
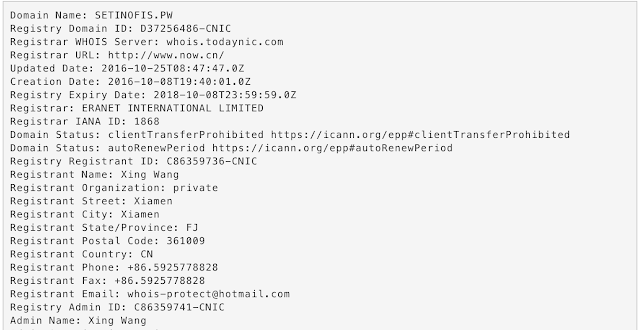
Reviewing the list of 1103 domains (Domain Tools as of January 17, 2018) associated with the 'whois-protect@hotmail.com' email address we see much of the same illicit activity we saw before.
More phishing domains:
amex-psk.org
amexsafetykey.org
applerecoveryprogram.com
applerecoveryprogram.top
barcalys-offers-online.com
bt-europe.com
btconnect.biz
btconnect.info
bttconnect.com
dhl4.com
docusign-australia.com
docusign-net.com
docusigner.org
dropbox-eu.com
dropboxa.com
dropboxes.org
dropboxsharing.com
dropboxsmarter.com
e-intuit.com
efaxplus.com
global-intuit.com
hsbcbank.top
inc-r.com
ing-update.info
kbc-bank.info
paupal.info
paypa.info
poypa1.info
quickbooks-intuit-uk.com
quickbooks-support.biz
quickbooksonlineaccounting.com
sage-uk.org
sageim.com
sages.biz
sagetop.com
security-hsbc.site
servicebying.com
telestrasystems.com
vodafonestore.net
wellsfargocertificate-637-9270.comMore domains targeting cryptocoin-related resources:
blockchfain.info
blokochain.info
myethelrwallet.com
myetherwallet.top
myetherwlallet.com
myethlerwallet.com
rnyetherwlallet.comSimilar themed, fake Flash Player updates:
flash-foe-update.win
flash-ire-update.win
flash-new-update.info
flash-old-update.top
flash-ome-update.win
flash-one-eupdatee.top
flash-one-eupdatte.top
flash-one-update.top
flash-one-update.win
flash-onenew-update.info
flash-ooe-update.win
flash-ore-update.win
flash-oue-update.top
flash-owe-update.win
flash-oxe-update.win
flash-oye-update.win
flash-playernewupdate.info
flash-toe-update.win
flash-woe-update.win
flash-yoe-update.win
flashnew-update.info
flashplayernew-update.infoWe even see targeting of government resources, just as we did with the other registrant account:
afp-gov-au.com
asic-au-gov.com
asic-gov-au.com
asic-government-au.com
asic-mail-gov-au.com
asic-message-gov-au.com
asic-notification-gov.com
ato-gov-au.net
augovn.com
austgov.com
australiangovernement.com
australiangovernments.com
federalgovernmentaustralia.com
gov-invoices.info
goviau.cotzyywz@qq.com Checking the registration on some of the domains associated with 'whois-privacy@hotmail.com', we can find some domains in which there are other registrants and the whois-privacy@ address is simply an Administrative and Technical Contact. This reveals an additional registrant email address employed by the attackers, 'tzyywz@qq.com'.
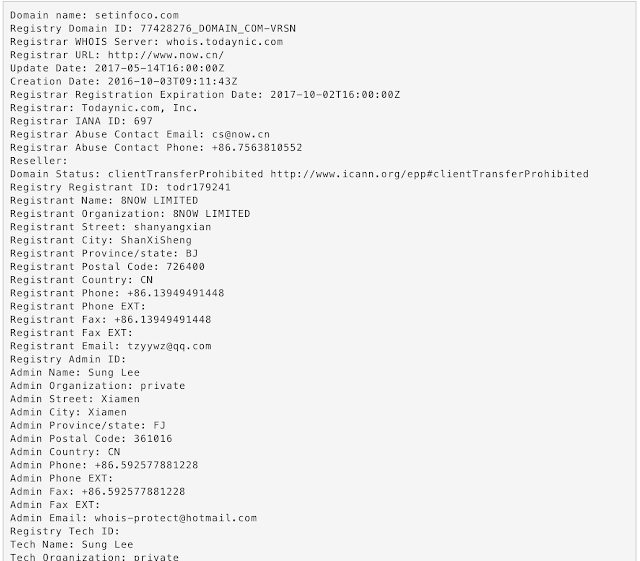
According to Domain Tools (as of January 17, 2017), that qq.com email address is associated with over 2500 domains. Most of the domains belonging to this registrant email appeared to be domainer-style domains located at TLDs such as .bid and .top, but we also see a heavy dose of illegitimate looking domains in the set as well.
Some typical 'Domainer'-ish domains:
aapk.bid
aapo.bid
aapq.bid
aapu.bid
aapv.bid
aapw.bid
aapx.bid
jbanj.top
jcqth.top
jhtaq.top
jhugs.top
jian0.top
jian1.top
jian2.top
jian3.top
Illegitimate Domains:
amex-notification.com
amexaccountvalidate.com
amexcardcustomerservice.com
amexcardmail.com
amexcardpersonalsafetykey.com
amexcardpsk.com
amexcardsafetykey.com
amexcardservice.com
amexcardservicevalidate.com
amexcardsupport.com
amexcardsupportservice.com
amexcardsupportteam.com
amexcardverification.com
amexcardverified.com
amexcardverifier.com
amexcloudcervice.com
amexcustomersupport.com
amexmailnotification.com
amexotpcardcustomerservice.com
amexotpcardsupport.com
amexotpgenerate.com
amexotpgeneratesetup.com
amexotpsetup.com
amexotpsetupcustomerservice.com
amexotpsetupservice.com
amexpersonalsafekey.com
amexpersonalsafetykey.com
amexpersonalsafetykeyregistration.com
amexpersonalsafetykeysupport.com
amexpskcustomerservice.com
amexpskkey.com
amexpsksupport.com
amexsafetykeycustomerservice.com
amexverifier.com
amexverifierservice.com
docusign-australia.com
docusign-net.com
dropboxbusinessaccount.com
mail-asic-government-au.com
postbank-kundennummer43.com
postbank-kundennummerfinnaz.com
salesforceproaccount.com
verifybyamericanexpress.com
verifybyamexcards.com
yandex-login.com
yandex-user578185.com
yandex-user912.com
yandex-user952.comMore Domain Registrant Accounts Revealed We can associate even more registrant email accounts with these same threat actors using similar techniques. While researching passive DNS for one of the domains we found previously, 'blokochain.info', we ran across something very interesting. That particular domain was hosted October 21, 2017 on the IP address 47.254.18.28 which belongs to Alibaba as part of their cloud hosting product. When we analyze all the other domains which have been hosted on that same IP we see many domains that belong to the registrant email addresses we already knew about, 'whois-agent@gmx.com' and 'whois-privacy@hotmail.com'. However we also see several domains associated with different registrants.
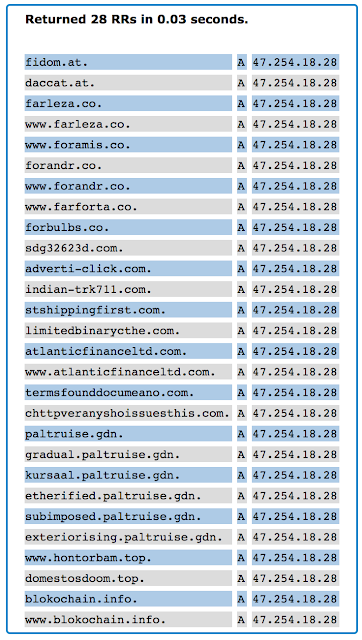
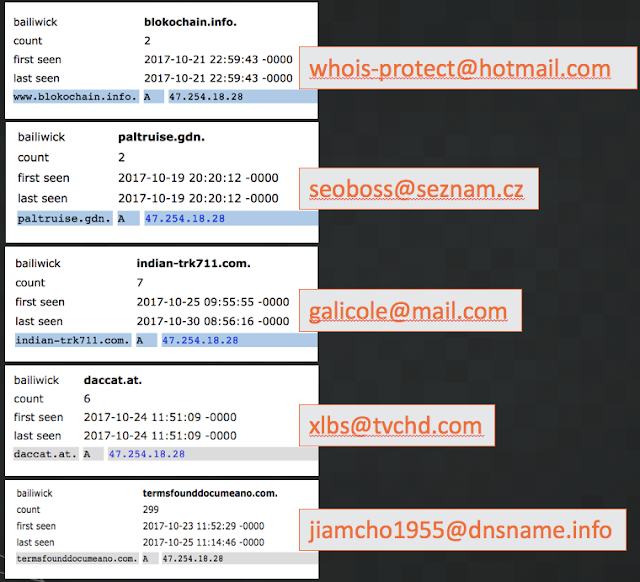
seoboss@seznam.cz Looking at the list of domains found on this same Alibaba IP we find the domain 'paltruise.gdn'. This domain is registered to the registrant email address, 'seoboss@seznam.cz'. This registrant has registered 125 domains (Domain Tools as of January 17, 2018), many of which have been linked to malicious activities. According tothese links, domains associated with this registrant email have been used as part of the Rig Exploit Kit infrastructure. The domain, 'paltruise.gdn', was hosted on the 47.90.202.68 Alibaba IP address on October 19, 2017 --only two days before the IP was used to host domains belonging to 'whois-protect@hotmail.com'.
galicole@mail.com The domain 'indian-trk711.com' belongs to the registrant email address 'galicole@mail.com'. The 'indian-trk711.com' domain was hosted on the 47.254.18.28 IP on October 25th through October 30th, 2017 --also very close to the timeframe in which we saw the IP hosting the other malicious domains.
As of January 16, 2017, DomainTools attributes 918 domains to the registrant email address 'galicole@mail.com'. Among some of the domains associated with this address we find gems such as:
1royalbankrbcdirect.top
amex-onlinesecurity.top
buydumps.top
buydumpsonline.top
carder-cvv-shop.top
carder-cvv.name
carding-cvv-shop.top
carding-shop-cvv.top
carding-shop-track2.top
cardingcvv.top
cardingshoponline.top
cvv-carder.name
cvv-online-market.com
cvv-shop-carder.name
cvv-valid.info
cvv2-online-store.top
cvvcarder.name
cvvdumppluspin.top
cvvshopcarder.top
dumps-shop-valid.top
dumps-valid-shop.top
dumpsonlinestore.top
dumpsshopvalid.top
netflic-validatesystem.info
netflix-information.info
netflix-supportvalidate.info
netflix-verifysupport.info
netflix-veriificationbilling.info
netflixveriify.info
shop-dumps-valid.top
shop-online-cvv2.info
shop-online-dump.top
shopcardingonline.top
shopcardingtrack2.top
shopcvv2online.biz
shopcvvcarding.top
shopdumpsvalid.top
shoptrack2carding.top
store-cvv-online.biz
storecarderverified.biz
storecvv2.name
track2-shop-verified.biz
track2cardingshop.top
track2verifiedshop.top
valid-dumps.top
valid-market-cvv.top
valid-shop-cvv.top
valid-shop-dumps.top
validdumpsshop.top
verified-carder-store.com
verifiedcarderstore.biz
verifieddumpsshop.top
verifiedstorecarder.biz
verifiedtrack2shop.info