Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 20 and 27. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this roundup are:
- PUA.Win.Adware.Multiplug-6518212-0
Adware
Multiplug delivers a large number of files used to display advertisements. - PUA.Win.Adware.Linkury-6518171-0
Adware
Linkury is another browser-hijacking adware, which comes bundled with other software. - Win.Dropper.Temonde-6517997-0
Dropper
This is a trojan compiled in .Net. It performs code injection on another process to avoid detection and extend its control. - Win.Dropper.Chapak-6517991-0
Dropper
Chapak is a trojan, which makes itself persistent on the host system and contacts a server to fetch commands and potentially download other malware. - PUA.Win.Adware.Itorrent-6517988-0
Adware
This is a bundler, which installs adware and other potentially unwanted applications. - Win.Dropper.Vabushky-6518142-0
Dropper
This is a dropper, which unloads Vabushky, a ransomware, onto the local system. Vabushky encrypts local files. - PUA.Win.Downloader.Downloadguide-6517985-0
Downloader
Yet another malware that installs potentially unwanted programs and browser hijackers. - PUA.Win.Adware.Browsefox-6518209-0
Adware
Browsefox modifies the browser to display ads and change the search behavior. This adware is typically bundled with other products. - Win.Dropper.Gandcrab-6518210-0
Dropper
Gandcrab is a ransomware that was particularly prevalent this week. Samples were delivered via Word documents. While the documents were different, the executable fetched by them was the same for each campaign.
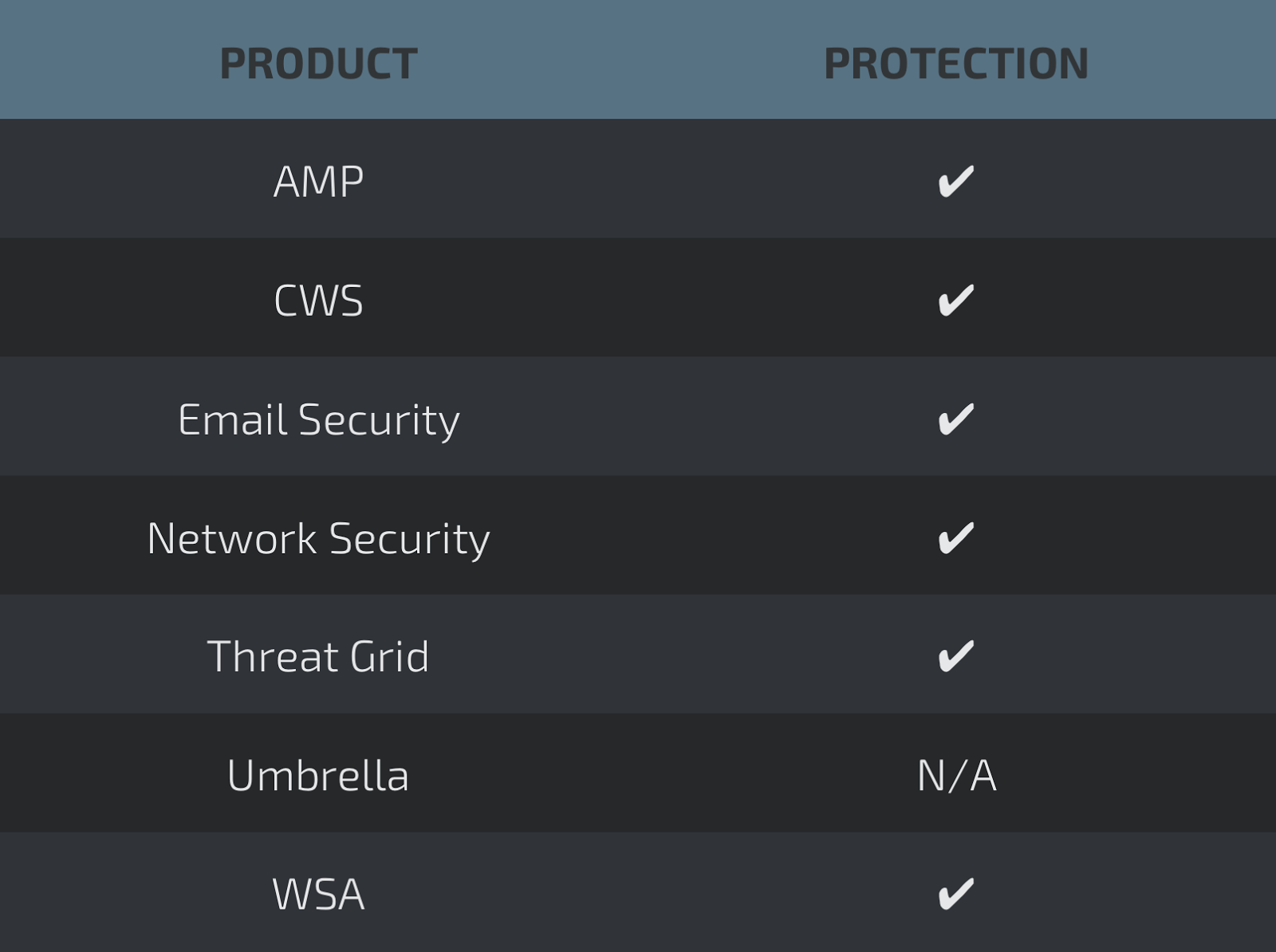
THREATS
PUA.Win.Adware.Multiplug-6518212-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\LOCALSERVER32
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\LOCALSERVER32
- Value: ServerExecutable
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\TYPELIB
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKLM>\SOFTWARE\CLASSES\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\PROXYSTUBCLSID32
- <HKLM>\SOFTWARE\CLASSES\TYPELIB\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\HELPDIR
- <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\VERSION
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}
- <HKLM>\SOFTWARE\CLASSES\TYPELIB\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\FLAGS
- <HKLM>\SOFTWARE\CLASSES\TYPELIB\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\0\WIN32
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\TYPELIB
- <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\TYPELIB
- Value: Version
- <HKLM>\SOFTWARE\CLASSES\WOW6432NODE\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\PROXYSTUBCLSID32
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SOFTWARE\CLASSES\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}
- <HKLM>\SOFTWARE\CLASSES\TYPELIB\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKCU>\SOFTWARE\WEBAPP\STYLES
- Value: MaxScriptStatements
- <HKLM>\SOFTWARE\CLASSES\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\TYPELIB
- <HKLM>\SOFTWARE\CLASSES\INTERFACE\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\TYPELIB
- Value: Version
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SOFTWARE\CLASSES\TypeLib\{157B1AA6-3E5C-404A-9118-C1D91F537040}
- <HKLM>\SOFTWARE\CLASSES\Wow6432Node\Interface\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}
- <HKLM>\SOFTWARE\CLASSES\TypeLib\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\0\win32
- <HKCU>\Software\Microsoft\Internet Explorer\Main
- <HKLM>\SOFTWARE\CLASSES\Interface\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\ProxyStubClsid32
- <HKLM>\SOFTWARE\CLASSES\TypeLib\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\FLAGS
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\LocalServer32
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\TypeLib
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\Version
- <HKCU>\Software\WebApp\Styles
- <HKLM>\SOFTWARE\CLASSES\TypeLib\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\HELPDIR
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}
- <HKLM>\SOFTWARE\CLASSES\TypeLib\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0
- <HKLM>\SOFTWARE\CLASSES\Wow6432Node\Interface\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\TypeLib
- <HKLM>\SOFTWARE\CLASSES\Wow6432Node\Interface\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\ProxyStubClsid32
- <HKLM>\SOFTWARE\CLASSES\Interface\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}\TypeLib
- <HKLM>\SOFTWARE\Wow6432Node\Microsoft\NET Framework Setup\NDP
- <HKLM>\SOFTWARE\CLASSES\Interface\{3B3F3AAD-FB97-49FF-BFEE-D22869AC4326}
- <HKCU>\Software\WebApp
- <HKLM>\SOFTWARE\CLASSES\TypeLib\{157B1AA6-3E5C-404A-9118-C1D91F537040}\1.0\0
- <HKCR>\WOW6432NODE\CLSID\{F28C2F70-47DE-4EA5-8F6D-7D1476CD1EF5}\Programmable
Mutexes
- N/A
IP Addresses
- 45[.]77[.]226[.]209
Domain Names
- R2[.]JOBURNT[.]NET
- R1[.]JOBURNT[.]NET
- r2[.]joburnt[.]net
- r1[.]joburnt[.]net
- c2[.]allocal[.]info
- c1[.]allocal[.]info
Files and or directories created
- images\progressbar.gif
- %LocalAppData%\Temp\2eB3B1f\steps\1.ini
- %LocalAppData%\Temp\2eB3B1f\steps\3.ini
- %LocalAppData%\Temp\2eB3B1f\images
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\SCREEN0[1]
- %LocalAppData%\Temp\2eB3B1f\steps
- %LocalAppData%\Temp\2eB3B1f
- images\loader.gif
File Hashes
- 93289f85a27f71089eddea6f139d7c41344d318f411850126d75ea51aff6733c
- 3c2c480d23acacf31423e2b78520f88bd3bb0b481d2f43840aed1d16d0987f93
- 598c1ca12fb83aaeade0b19ad6d18ed680c011ee085c0798eda44b97aa38644b
- fbfe94ed1d3d11dff22ebccf7a80028f3052e863aae2b095bd700773a4d5d123
- a9eb76def683a0ffba1ab2704c40715d133fb6884121849096fcbaf8b3e65541
- ee92af9885b7b962d550b5c559001b71d3a5186c63edc2b84c6ee0a3d11f6038
- 1c6c368211a29b5f69ff64da32147ba4241f62fc77d02e66e98873b024bb2046
- d0424200836fda85e802c7c0e16aa1bcff1f9dacbc7524586244bf0c55b4c83b
- f5d97121664e2df180bb286d808c899ff085bf67ff42e8cf4573f5a14be52b72
- 14aee87a92ec1fc11211f5b52f6fe0c8f94c724a5a14b6ea0957ca25dedb0892
- b8688655f68b5d395cb4914e711e1995b4123688412d7fe06372cc3c0c8267a7
- 74ef0193265e7ca2e353a75f51fc81324669352775db867030b77687e65316f3
- 5de9d6ebd6d3c90d5819259d4c2f8bd646a861c36d090cc955c2408d7924ee9d
- 35a21ae4f4cdcf2681697cab80dae2a19cdd27f978e2e4875199967b100bb69c
- 0cf84cd5e553946d61bba2ec1e0c6b988c63dda6fdfe55bb70d0e742781bdb15
- e1a04d38648a472cfd5a87fdfaa480d2e38bcc88bda3b3e5181bbc1a2bcbba9d
- b193e85ec1b01e95d0a4575093868f92b0179ace355b78d7f6c87541fe68b370
- ac605db020addf7d28c6f919aca656cc97df7771801748b78d68a34fc2c07721
- 5afa83ca67022bc19477b014e20b4613e93b3a595dfa5f317ec9d602135aa21d
- 68fb06e263e78d0993d69c574c8508ee9fab8289310ec22542c4a686c2fbbc11
- 632e9c757e6a7ff18b8d382161af1fd6491eb8650fc12079cbcb617d624423ae
- cc80abc53d7720b98517f8a2321f457cd7b7a250f7ae8cd45846bab1c2558a50
- 16878f5289a2acda314ede318c644f4a3c271f1495e6d4bea1493aa2e3a88a36
- 1caeb8b04af0bffe857f6f7617f01d82f20177fb1a6913d46b974f62aa20ce2a
- f8abce29ef422582ed920d36d26be5357041ceca2297442c931f70a7e4f9c8e0
COVERAGE
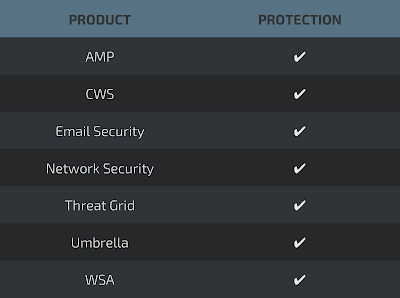
SCREENSHOTS OF DETECTION
AMP

ThreatGrid
Umbrella

PUA.Win.Adware.Linkury-6518171-0
INDICATORS OF COMPROMISE
Registry Keys
- N/A
Mutexes
- N/A
IP Addresses
- N/A
Domain Names
- N/A
Files and or directories created
- N/A
File Hashes
- 91e4d7e3fe06af8180d03d35a88b13ad18c91784840b29ebbabd0897f03c85b9
- bc3e7e29b6fe2012781ef03cf08967ee577e4ddc4f643a753eea6057474dcbdc
- 969e8b516f4a717475e03661429ac2fa6a446ba26f8bef680e7881ebd66960c4
- 1fe2e86e58738c48c37274e273adef72e287ce86e3f42fb65b11ae6ebb553ba2
- 2b0d96ac5f744b63f2ccac770d7ebed16c27f42080a2e3e28d67dda778e4047e
- 610a95d15b5b189f04d12da43450d0ab8ba84e108943c2bb3a43162e980e82cf
- 6e5ced523eeec1ca10df59bd446f92ad5c1ed029152250457f27d2a09f6bc6c3
- 4bf6b5977c3921c9c64a9f96082b1476a8d9c96b31e2af7435471ec1bbae21a6
- 130ec795353581ee133a6a41ab7a546fd116d2b0144117346ef740fa15be4b98
- a5cb5b7f01b765fcc51ff84061c609b72aae5cef1bcd795f3e5efa67c8629064
- 1a8215183cb4bc71f6e30c3c2e72f786cf70d0ad25af0865b49d1d667d52091c
- bb2f71514dd42d3dfa81df0cf2e5d0f7bd51b40d13925410bd02a29e9dde404f
- d6c7b30f4cb108f802fc592e7e0aef0140b09514600b5500ad32caa83653db5f
- 132f430515486d593e247fedff3b503d2fe96013e20660c9afe2251d34c39967
- e45f125305d1dc217dca73fb75e89fc3243cd839ed22c46483a752b46e142d8c
- 8037c529362ffc95eaeda800830b56892addd747a416d4ea130ae3ea27fd3b2e
- e871b106da94ac12cb606e303279fed865c7c93b64ddbba6c758770841ef07a5
- b07357cedc32609686210cab144e5534289a9917d6731c5d94cb3c39aa6bd375
- 3aa333d83f3b6b631ed2576ed8fe745a5c90fbf33f3591e0e3ee1c602d7818bd
- 79b9e3719b1825c2506c39e876fc4007d63d72d2ece87bf952d55feb652057f3
- 0639d833c0a7d3d6fb8f9b7f92dc94cd562ac9c47060483436fe9d94c16e5135
- 6a65245e7ed18ede739f10a4d40be6c94f6e5c98b3ed11d0eea248d5cc9ff11b
- 6c3fd7ca8f725a51fbfbd1f9db7ee4032177c5324bc4ef5706372099d973f009
- ff10ff4a8ab0c3fee8d071c83d46f5c6c5a9057719a373874617283c544f1b10
- 5121d56efc3809129297ee364599222b75e77626a0650777f7c4c49345d17e5a
COVERAGE
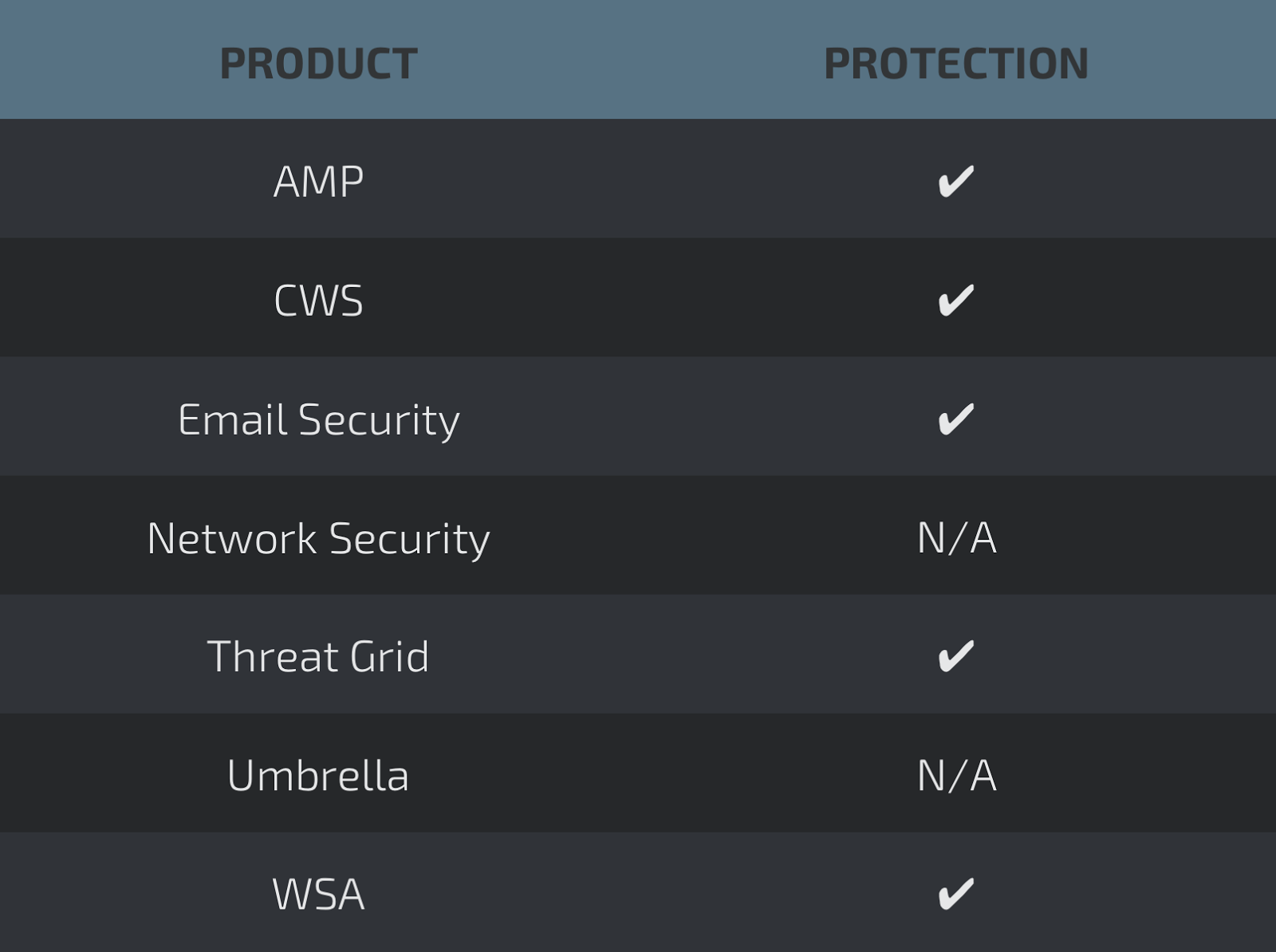
SCREENSHOTS OF DETECTION
AMP

ThreatGrid
Win.Dropper.Temonde-6517997-0
INDICATORS OF COMPROMISE
Registry Keys
- N/A
Mutexes
- Global\CLR_CASOFF_MUTEX
IP Addresses
- N/A
Domain Names
- N/A
Files and or directories created
- N/A
File Hashes
- b0662b7e4ca76b633d7fa52a06b4720cc853528d4400c309ed42b9f861c4d0ac
- 47376c59afd142cadb3e254a7e63b24e1e77de31e181187c7d342104253c7574
- ccbe3c1a79cf6b7d07e6a2fb24ef3ebc1152354b4994cd0d9b5ca94c2df46da6
- 3a14fd4223810486654135562a655c0681fdd2974ece9176052ee5e36a0e9ea7
- ce41b0bc6b918b0866cc195784d2ba08d33c2f599c5b7ff383390517593239be
- ad2f25d3c2840f42c9b0d496b4125b428c5d339cff3314b55ae54e8b79ee3ed4
- 0c37f6474d2d93a51da230b381a01da8b053248c5dfc4dbb6779d57b190f26a3
- 870778c3c6d04c83f05805b3b0a9d56356224f7f76d42ad29ecfe882e3c20d20
- 4620f7f7a2340f01f98b4d78f2b61aeb40a8354c91151280a3c54477a49c757d
- 5f157c0ba35bfe6d325cdef614c9aa677d749f1651b0a1228a00089269cbdb2d
- 93692c5ff1a68074c64d0669eeb133bf74d8946300bbf2ee03230e00e4b3a8ba
- 94d3a893baefe31231d40934db7eb6a9fd1243b56386dfa022dc6c30cfdf16ee
- ef05bc231e06777d5fdc77b3ca76bd167c39e31b3a728b88628a183ec9115a0c
- e7c4eff70017f79df91242135de536cc57e808d9cfddcfcef143ac76fb6459cf
- 1231830b27d1e59968e92f0cd5c4d4d2202eff9721ccb24dd87eba864da466ac
- 160c33212fbfeeb2afd8a9413d00a506b7f7c795375ee3bdcf8b10d50564bf0e
- bedc93271e1e0765ccec9f6560361413356948c7363494994048660477cfae45
- 8c26f89d4073d3cf99da3197f556a13aaee0af9fa71887d837236109ee0dda11
- c8fe4346e53515c87a35e6b401efd28659e0cdc3c21094949d0c270e2a10b5a9
- d1c779a3f3540e7100aac4774d21a9cc0f79944f649b34991eec85e025b74240
- 8677ab94aea9a1ce5dbec3b5701a27c86dbfd5eb6ef30ff99c57ec21b942b1f1
- 1fd97e491e3ebc4ab1fc9fe1dac1eb700924cd4920839007ae257579780580be
- c4d7447ee91e066529282c2b6caccb285e4d264765c6483ba4ff802209b6afe6
- eb6399c420bd574436d1a508ec3f22e1540be110606d7a5679fc92ad217e26ce
- ea68665c2dadd9bbff4d81ed2c3037530dfb2b388eb212a4f666743e44877ad4
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Win.Dropper.Chapak-6517991-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value: pfypvwhssoy
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Mutexes
- \BaseNamedObjects\Global\pc_group=WORKGROUP&ransom_id=359814f23c28b0e4
IP Addresses
- 66[.]171[.]248[.]178
Domain Names
- NS2[.]VIRMACH[.]RU
- 1[.]0[.]168[.]192[.]in-addr[.]arpa
- politiaromana[.]bit
- ns1[.]virmach[.]ru
- ns2[.]virmach[.]ru
- ipv4bot[.]whatismyipaddress[.]com
- malwarehunterteam[.]bit
- NS1[.]VIRMACH[.]RU
- gdcb[.]bit
Files and or directories created
- %AppData%\Microsoft\rojovu.exe
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\7TZAD419.htm
- %WinDir%\Dorawonu kenevuli
File Hashes
- 38e70f6ab21df8f358a0339efacf813c398d2c81ac84eb170692b7f4a9d85a11
- c5284d7f81af2640b87e389739c393377f9cf44f66c734544dd7c5d36e5ebce8
- 511d460a7a89f8e04ae63c095a6bd609ea3430070c2219abf52b54b6a68cf65d
- 771be31a99b3a142530974876c7b19631e41909014aa830d8901db4ea0dcdf75
- 6116763086a3f5cca15f35eaf1c4e5b622486e180f57b97fedf03b9d489ee944
- fdc1af5f15cc306e1a31af6fa92b5c78a02839cf1623c44ed6dedf3c96e3e66c
- 4a9d4dcc8bd9a5648254db92047fd1b34d5b62ae9a73ad472ebc8831e5f7cf14
- aeeff1ad563cc9fd9e7199209c489fbe4ca86bda6d650b6d0437341a65949adc
- 5c902360da48c8aa3764fd81471f58ca9a741af24955101a9ff8927bd1e284d0
- f4e6ba27da9e31d52ae6a0483cccf0806aeb23590cff70af85f2af89f55b9dc5
- e8027abfcbe9f3d3fbda1e635318a9f9ff7dbadec2697a630f21ecdf72d43a6e
- 6500b0fc6b279282716162300a4ebfe059ef254479313392514bf9af7b0b5f54
- 1a0a083d3905c1b37f010130b19e73db0cd4385090c35c951dd6807da14db397
- 39027deb5b01892736313fc5b1acef81ee0d6e581ee3514768416371b9482c3b
- be15a74b15c3607d6d6d9995e1752bac8b78d4316098971669c9f6c10a7d9c0c
- b88dffcb8f1ecf6629100041f13c5b406c72ca5620067d49c6cdcbf46b8458a9
- 91435815f46bc5ad768c77636c23ee71ec6a82b88819e545f499b0c498d477c0
- 691f1968e302150ca31abb2e25ba117882418a4de9227a6201b8a6e759740bbd
- 49abf7cf6af3fda93f22c08316706d8596f29b45d2513f9682ff2d209b8f4d43
- 757825ffc0c5e38b61b3d56d57f7372223401bf47b891f1b6e333021b4804a20
- 516b2b6db75a4155fde2e0497da0ac000404e9872acf701ff1898df0ba4a51cb
- f2a55bf2bb857bf74eaabccf704ba5424de2c14fb88306327164abb8ad678536
- 85e84238a760302bbfd913d9dbf6d57d4a4c5939e27c930eaca6145f24f58b95
- ea4c4220c9d997032a3269b002a86752725c83115a1f1f9b12371721836945bf
- e1fa4987144085f9924993039e07d6f4e3d90b4b7b63864655bab7209fe9d97f
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Umbrella

PUA.Win.Adware.Itorrent-6517988-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\Software\Microsoft\GDIPlus
Mutexes
- N/A
IP Addresses
- 52[.]29[.]64[.]41
- 52[.]29[.]39[.]104
Domain Names
- info[.]atmili[.]ru
- s[.]itorrent[.]bz
Files and or directories created
- %LocalAppData%\Temp\98CBEC1.tmp
- %LocalAppData%\Temp\98CBEC2.tmp
File Hashes
- 5d4374d3efad7aa1fb713f39228ca03ba2d635d95dcc868448c64ced8462669b
- 4d19aaf8351aa917ae7e0451e5e3d555266230492b92df14924207898fe0556e
- ff7cbe2b22c305e60d97df17900c6dbd1f3ee04f893aa2f0064e8baca4b095e3
- 3650b0eb28ec8aa62803b5225f1d802c8c86030183d13568ca5b7ca83433c6b3
- 14189877093a87f0c1134cec073ca1b2feae37b98db1dc9ac11b28d22eacad41
- 0674b063dd2337e1ef589c6140513bd03775f98a8e7cdcd48ad516f2206196ea
- 4aafbe0e0fadbf24d9b7606ec02ed67472bfa2dfd80e911b80783ceac9ef707a
- 62fc29d2df8aa13dff0aeeaefc5226745fe49d7e0e676475924e365764fb93aa
- bfd7f93e3a51fe337dd83ae8b10db73db759d8950e41ffa5f10f3a9dd4637c16
- 8dfcd382927817426e77d43b6eb0a1b549a90dd623e3322bb87c8bc5b3af9a80
- 0ac7f7714b66003494e817c495a7cff7d00ed9c776f3852d6ae97a4f87fa76b1
- 8305265d4dc7323eca0bdc4b8dd05f7aefa8bedeaaca32de0158503624a901da
- 64f60f5274a7c672c9ab2616209c622aebc384a05d23f118f423a8ad7c89537d
- 4081b52e671a7ad760d8247d8946d1ee7909e727330efa8029afeac4926837e5
- 606f74b199f3ebffa19c8b97c80afdf81cbfc320d4cc27530166ac32d77184bc
- 7c5460496f4ce2ff5384ea07fa07a8022557a6f07e796a06269bba39c92b825a
- 8bf4e8f31580ad26afd918b8d895c1e222d5d60290c63a98ac22f046a5d63c9b
- f487f94cdb442263a9536771a081e04f8890e0884ff85d49992357066c5a6447
- c557ea0836e365f9c3b490cc7e03c180b4924a562c0d13d0720d902efb9bcca9
- 163c50c2c5fd71fc90d32c5b201eae19ef0f07ed17006058c210a6856021f892
- 71d8a2b00a79567120449b5be30ccbbb30b3df3619bd22bb72666a548f13eeea
- ad7e4d6ef119c9a1bd24cad2d540ca97b6d8f872f1a7cc56f284fe1fbbcfeeb2
- efa15c4ecc4a72a498103e9ee3fe46c8fb10f356996c51b55be1d838441f5905
- 2bb8cd9afc4b1dcbbea1aef78e7dd1fd4519dbcd84e318ae8d95ab6b2d3291b5
- cc44c2e0af8ecb0c3f6d06e12171b0a7b579a535d98d9cf16708a37f9c01d53f
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Umbrella

Screenshot

Win.Dropper.Vabushky-6518142-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDefaultGateway
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDomain
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpSubnetMaskOpt
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpInterfaceOptions
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\D0-EC-4E-4C-68-09
- Value: WpadDetectedUrl
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\D0-EC-4E-4C-68-09
- Value: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\D0-EC-4E-4C-68-09
- Value: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\D0-EC-4E-4C-68-09
- Value: WpadDecisionReason
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNetbiosOptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServerList
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value: WpadDetectedUrl
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value: WpadDecisionTime
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value: WpadDecision
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value: WpadNetworkName
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- Value: WpadDecisionReason
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpDomain
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpNameServer
- <HKLM>\SOFTWARE\VBSZKYHV
- Value: h
- <HKLM>\SOFTWARE\VBSZKYHV
- Value: w
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS
- Value: DhcpScopeID
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}\d0-ec-4e-4c-68-09
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKU>\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{CFFE6C1B-C698-4A68-B86B-DD768F696445}
- <HKLM>\software\vBszKyhV
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\d0-ec-4e-4c-68-09
Mutexes
- N/A
IP Addresses
- 93[.]115[.]93[.]16
Domain Names
- N/A
Files and or directories created
- %System32%\vBszKyhVp.dll
- %System32%\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
File Hashes
- e5d37e741c64965d38d30ce53e8b80996a26b806ce4400789bb89deec6522632
- 62321486dbed50c38e356e48863522c8c34e1300fe00276839ccf8d5afb9c841
- 6d7dda4b9afd2609b3a9994304d611e532162d29b812f96a03aa0f9e156c4577
- fa168315e0e19fe319c9b48bea50b7e51519b16c828d74acc3f9d23ae8ee85f8
- b6c714f8167add365e23d2479c1dd401740cad0bc8b63dc214de63a56df54669
- 1eef403ddd8dd010b7ab5bcf6b6712a44b61cff62c2db804c4e8caf0a3df5257
- dcd3dc2fee778172e4adce4ea100e2cba0e590028c9b7ecef7e6736b8a50b289
- 8cd0afe406d49d69c16574f75256e3df1421296894062c619f0da2173f771e64
- e69d973504e34512b713f9e827113933fcb0317e0a96f0d0f34cd0ad86f99121
- b43b77f254c0f554634b7cbf524c1466c9cd9cf8d1eb59aa47c508cb47b3ca83
- 9ef72f076e0cd74e58e93654a8fe556144102221b63daba988448c6851bc12bb
- fd182a516290da90accab1ed6111b2833b56b10adaafd09105c31abab9b6158a
- 3399af9c82bc394bd730d9f7dd947947431a8033979d6d5ae64a53d4715541da
- e9801efc84681d52ecb905a22f154f41e848077319b67a31afb85c3ff7212c6d
- 463aa2d0b27a92d0d1b872d70bc13abe90a8b4622649a0e8d5b8135cd20cd901
- bdf235c92c2d880df003221ba993639971f3ea5aba29597a561c48a684949743
- 2b6d7d1c3d31bd042d6dbc31386b8641863d58e6b791c0b3c7b88cea6ae88950
- a3213eed4e1ffaf58f680c2d76f4be16783f1c40ba25d7480d7d1b2bedeb4c23
- 25b9b7e68b36e941c41376fec5c929dde6e3ffe05223cae34becf22c5c4f4e3d
- 3145293a52c8730bddfe326e00f9a6afcea42fa22ae12eb70cb64c47d06b2ed2
- be8b254407529caf893760aaa1db43303eb0f4b00bb51c7e0d4a1d05bd702014
- 2344027fc2269e49976251e652faf815d943ba12cafa340b4f3064161207ddd7
- d982d7d4bb9a9bbfa5d0a0e5cddfe4ab5a6455761d2f30a27ded543b9bcd42fe
- a6aeb422cb95bd79dadb200ee9db1479723bdbd4ea090bcf6f5e5cf9dd2457d9
- 4c2e70f4ec71f29a4ff7fb069c0c0a0b71050a99667fe9afd83c46ee3af58fa6
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Screenshot

PUA.Win.Downloader.Downloadguide-6517985-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\WINDOWSSEARCH
- Value: Version
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012018042620180427
- Value: CacheOptions
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012018042620180427
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012018042620180427
- Value: CachePath
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012018042620180427
- Value: CacheRepair
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHIST012018042620180427
- Value: CacheLimit
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\Software\Microsoft\Windows Script\Settings
- <HKCU>\Software\Microsoft\Internet Explorer\Main
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\Software\Microsoft\Internet Explorer\Main\WindowsSearch
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\EXTENSIBLE CACHE\MSHist012018042620180427
Mutexes
- \BaseNamedObjects\DlgCpp
IP Addresses
- 104[.]40[.]188[.]185
- 104[.]45[.]146[.]238
- 104[.]41[.]149[.]192
- 104[.]40[.]156[.]71
- 72[.]21[.]81[.]200
Domain Names
- cs9[.]wpc[.]v0cdn[.]net
- dlg-messages[.]buzzrin[.]de
- dlg-configs[.]buzzrin[.]de
- dlg-configs-weu[.]cloudapp[.]net
- dlg-messages-eus[.]cloudapp[.]net
- az687722[.]vo[.]msecnd[.]net
Files and or directories created
- %LocalAppData%\Temp\DLG\loadingImage\loadingImage.bmp
- %LocalAppData%\Temp\DLG\ui\common\last\js\jquery-1.10.2.min.js
- %LocalAppData%\Temp\DLG\ui\common\last\css
- %LocalAppData%\Temp\DLG\ui\common\progress\img\icon.png
- %LocalAppData%\Temp\DLG\ui\common\progress\img\progress.png
- %LocalAppData%\Temp\DLG\initWindow\css\style.css
- %LocalAppData%\Microsoft\Windows\History\History.IE5\MSHist012018042620180427
- %LocalAppData%\Temp\DLG\ui\offers\d033278d2583e0fe2b7585ceb4483ad9\img
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825\css
- %LocalAppData%\Temp\DLG\ui\offers\d033278d2583e0fe2b7585ceb4483ad9\css
- %LocalAppData%\Temp\DLG628A.tmp
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825\img
- %LocalAppData%\Temp\DLG\ui
- %LocalAppData%\Temp\DLG\ui\offers\d033278d2583e0fe2b7585ceb4483ad9\img\img1.png
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825\img\img1.png
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825
- %LocalAppData%\Temp\DLG\ui\common\progress\progress.zip.part
- %LocalAppData%\Temp\DLG\initWindow
- %LocalAppData%\Temp\DLG\ui\offers\d1218f43853f973f710cba676ef66845\css\style.css
- %LocalAppData%\Temp\DLG\ui\common\base
- %LocalAppData%\Temp\DLG\ui\common\base\js\jquery-1.10.2.min.js
- %LocalAppData%\Temp\DLG\ui\common\progress\img\br-rb.png
- %LocalAppData%\Temp\DLG\ui\offers\d1218f43853f973f710cba676ef66845\index.html
- %LocalAppData%\Temp\DLG\ui\common\progress\img\bar-lb.png
- %LocalAppData%\Temp\DLG\ui\common\last\img
- %LocalAppData%\Temp\DLG
- %LocalAppData%\Temp\DLG\ui\common\last\img\img1.png
- %LocalAppData%\Temp\DLG\dlgres\DLG-Product-Logo.png
- %LocalAppData%\Temp\DLG\ui\common\last\index.html
- %LocalAppData%\Temp\DLG\requirements
- %LocalAppData%\Temp\DLG\ui\common\progress\img\br-b.png
- %LocalAppData%\Temp\DLG\ui\offers\d1218f43853f973f710cba676ef66845\img
- %LocalAppData%\Temp\DLG\ui\common\progress\img\img1.png
- %LocalAppData%\Temp\DLG\ui\common\last\js
- %LocalAppData%\Temp\DLG\ui\common\progress\img\progress-bar.png
- %LocalAppData%\Temp\DLG\ui\common\progress\index.html
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825\img\progress-bar.png
- %LocalAppData%\Temp\DLG\initWindow\css
- %LocalAppData%\Temp\DLG\ui\common\base\css
- %LocalAppData%\Temp\DLG\ui\offers\d1218f43853f973f710cba676ef66845\js\jquery-1.10.2.min.js
- %LocalAppData%
- %LocalAppData%\Temp\DLG\ui\offers\d1218f43853f973f710cba676ef66845\uifile.zip.part
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825\index.html
- %LocalAppData%\Temp\DLG\loadingImage
- %LocalAppData%\Temp\DLG\ui\common\progress\css\style.css
- %LocalAppData%\Temp\DLG\ui\common\base\index.html
- %LocalAppData%\Temp\DLG\ui\common\last\last.zip.part
- %LocalAppData%\Temp\DLG\ui\common\progress\img\151.gif
- %LocalAppData%\Temp\DLG\ui\common\progress\js\jquery-1.10.2.min.js
- %LocalAppData%\Microsoft\Windows\History\History.IE5\MSHist012018042620180427\container.dat
- %LocalAppData%\Temp\DLG\ui\common\progress
- %LocalAppData%\Temp\DLG\ui\offers\1522ef138ba104249c3934a80811f825\uifile.zip.part
- %LocalAppData%\Temp\DLG\ui\offers\d1218f43853f973f710cba676ef66845\css
- %LocalAppData%\Temp\DLG\ui\common\progress\js
File Hashes
- 9e80a9629faaf49911b2d55e47d662e93a9f0c3a44cdb8f6e073248ac6dc351c
- 6f96cb6e06e72dca25f5a86bafbbf54ff41444408370b5948078ac54eae173dd
- 7f0a548256c1ae127d63567454b3423f1f1bb0894e1c4052419ac3b559451d97
- 36b4be4057e110d4cc2f6bd51c64a378c33e51ccf1704490218f71b7680ae34c
- 48e9a887ad404d4cd86c1a2a5cd554a53bb726626d21d0816275c3ddfd557d9d
- 4219002c5441b449b4467be6adc3bffc20acc99de0bdc83110874ef9207430ee
- 93faa77350b1950cd65f55d5be5f7ff5912c8668b3b62c718aed1fe8a38f86f5
- 6c3c69f854fadcda9c13b80f1723579ccfe71aca91aed8b5c4fd7b0628d51c4b
- f825588ce048eaa7c398be354bea3ffe0f7c6512f345962243bcb59cdb30a4f3
- bfbb38e548a52a0f382ed522eb4af650dcaae568f2cdc50f12e47af8d58fdf5a
- 2a63b30132cf5e87858e1c4e17c803980e40d2c88d78a5217dd96cc1cb7159a5
- bd7b9ab1834ac41e95174f00240d37eda802c3d42cbafc8dbc3ad30dcc007369
- d861c6696a5e6c3b2022df85ffc7640f33b0e54428ae497bb330b2aba259b7e9
- 2bc14d1d7c7d5d0ab5062568888ffbb2e9d1260b2e1285c9b40c45821bd2bf72
- aba71484082260bb50ca65395a81ab9fbd35b6e166186b06464b3308157c83ff
- 99490c14e2a4f0f483556dbcad7b2d54f69ce512656224ef16f71e0090a25f57
- b31ff12203cb9ffb5d9727c2a67a19da79d87d8120b6e9d11d4b95e7a9e8e91c
- 58a8d3881e95c490f07f45d993938fc4d6456445f34de3231769d6780f338ab5
- cc8d8e263a8e0b6bd427cf5acf4fc4dc221cda4b457db08c1784dbb93e99e3ed
- c370fa71ae2f4fcefa06bc564102f4f29bb4dcac1fcbcd32d9dd2bfae7e711a0
- 25c86d135b52ea0178efee2d61381b217f0d9eccf47bdd67f556524dd0aefe3c
- f7308eede1d35ad4ff82d5772fc1942675ac68d326966d74477cc5e7062cf457
- 65ccc33e020e5f954be9caa62e3f4ead076fd7670eca20aeb0169661100f40c9
- 9798ccc97125290bbbac1bce664e2d7db30a8177477af78aa4e820931272ebfd
- 7dd11a1e78d6b3aae7743733767a9062ff73455e631c16d1cc007207d35cd555
COVERAGE
SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Screenshot

PUA.Win.Adware.Browsefox-6518209-0
INDICATORS OF COMPROMISE
Registry Keys
- N/A
Mutexes
- N/A
IP Addresses
- N/A
Domain Names
- N/A
Files and or directories created
- N/A
File Hashes
- c8e854f4dae4072154f324023486d4e80f13e33617ecb4835bfc1e1cd39b3917
- e6aaa4ee84ce59b1fb8840f60e10d6b44af458641670479577e40bf87a12213f
- f9c662335648b5a9b41fc5fd924b3dc003399840c50e545edae35035827ca158
- 36519727bef36b4a878c5f74d7822ef79d916e9b2dd945430ad062be37e15dac
- c8de2537db16100c8e993a95210eaa922aaab758693253015ea7e6b1ae97efc1
- 802ecca3de31fc5c856cd45eab1bd312ba376e43cc53e4c72aa76c2eb1d107e0
- 1148c11c538fc4b62926ae3c817e7ee6f6066710e90da8da250c67a65cd39824
- df2c8d329cec7769b3f80e4e233fa872f1ad829ac1d0fef2707762edb5be7b5f
- bd3e42ffe6573c0678169da09f4a4c9edfbf4743547258450199b88b9ddea1cf
- 2b5478b13a17c2b07aa4e5e6d60a20880ad96d2ff6a4f5538a5eb76a581d2707
- 2d43ea47c4718358ba2338204f39484adf74746720140f82eb4d1ef5de2aaf92
- 0a59af6f94c49f2cc979c1797aaf1116601c6bd224c4cb71d7c68994e27adf82
- 9a7ba66c452046a923c365bf422a2cc47bda02ec99b0572a9afc3232a3aa778b
- 748ca5b71088c520cdace941ac85655883622ecf64c18e3dbb55f6ff48ba4ca6
- 7407c38ab706c460fc3c78b7cb1d63f87cc823d43e46031bf5744868a3b0d9ef
- 6b9657efde984d01479364ca72edaa8da05e3286f46eca5fefe22de79dec83ca
- 52202a3bfd2e6cf27eca88aec33c3c10b878ac7ef45a837f946e9a7147ab317b
- 5b6eabf0b67e59ffdc19d7de742d97a0a01e5e142824723d8b213af8a01b534a
- 888bf7e0cae92f6218e98ebe17de3884f06b99d343df55d3c563039de449d88b
- c7609ad5e50d5b908a5474fb8648c824f335fc03e28a976743089952e1f7abed
- b20ea863ccb7ccd780af4c0e9075d97d2c64c3c795de438ba4be7e371e8dce13
- 3cb57462b962fd65d746743506651952a8f516246502b1598aa1a971ee1e7ec7
- 0daa164a8b453ada5fff14f3e29ddb4395d47d4c4102b1eebde5228be80e51f8
- 0408eed39aee7c02e3eac8c967f786bebab5b2716332dddc63529ada7cbe94d2
- 3c080b429de9c04801079c31c1496a61df7226a356f718dbe44161d33d9207a0
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Screenshot
Win.Dropper.Gandcrab-6518210-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value: skhclrzohqf
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
Mutexes
- \BaseNamedObjects\Global\pc_group=WORKGROUP&ransom_id=359814f23c28b0e4
IP Addresses
- 66[.]171[.]248[.]178
Domain Names
- zonealarm[.]bit
- 1[.]0[.]168[.]192[.]in-addr[.]arpa
- ipv4bot[.]whatismyipaddress[.]com
- ns2[.]cloud-name[.]ru
- ns1[.]cloud-name[.]ru
- ransomware[.]bit
Files and or directories created
- %AppData%\Microsoft\czhatp.exe
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\R0L7W0PH.htm
File Hashes
- 9f3fff0d33f24a6c33cbe2eb73279f9a84bab0e9ebbeecc0812d840bb1a7a9cd
- ee76c548867fe400ffba20191ff3cda4b0c17e757a34a5e033beb27609ce00d2
- 6a724649c1ff4713811d2cd20040a4b297b609baac3d7365f86bc0a46181f0bc
- 3167af650dbf40ce92c280ede3a98827bfa91393e9eb82c7d2706dbdb7314055
- 1249d39166972fecea8a6d9883fcb787aa5d3a76fc069bff30d8169f6f6cac39
- 55717667e82abb6640728e3f54f417c0e43e4074263ed8609cb3a53a8a71cea4
- f377f6456d01efb32b2f0d872309d846a0067a778e2759ef8eca366ab392d9f3
- eab4bd04e2cc37b0515c6afd8859aeccacf48f004211ff78d1c86697c7db1bca
- 1a3f9284c72f1b50669f16b4b883e20f7ae179fa90837d223a19814059c42789
- b28c5559bc1ac8b8ac03db87b99c5ff0860c4eae72776d8a658a373cd238df71
- c8798863e8741484557a2bc60963fa6b8f454a644673645fa2e5610305e1cf66
- 72389784141f9e694c4c547f234eca74a9ae563cbd7f13132cc9be113ba45600
- 0f110c3e3830554f19c906d03bc54631dd552897b974461e6a6bf469524c2449
- 8d9f1ffb082214e56252b51ce071c892d4a80b7a8ba5f664953848407c4ee536
- 7b1bdb0119f6bbac4ef62ce9a0fe03cf1a7d8f9a9243a4d9921dbc78311df503
- 20edf76d80a009863089ea1a2a13204fca58a9e15393b40dd1f9e325fb2cc676
- 78707d5e62547d52e7f0d76b7b43a4a8b0902a6463592b48beaad7b074ad5724
- 60c38375999628c4e0dda146f71d54dccebae44e6fe9caa232a8599653a3392b
- 23084b55e2f962ac0d809563e2fd8a6a91973d88e8ae0788316ff9398394aa30
- f8f59273834de7c36422384cc8533b3f46c54c4198d5e3b99c8c3e585a3bd057
- f6e56a84834c8dfcc405e8376706e56a064921a97275733c1d5518719718583a
- 1d6f2497e4cf0d6ed08a8678db2382c1a6a914455afa91ba72d9790782f5671b
- f83d3b17f1472f1b4aae34d5e9d344a9c2ba2dad0c51c41a29a18213ddc9c237
- 46f3e720df4661afe0075c6f9ca0a8158a758c267c249994070a455be97a6297
- 2135a6aa534cc195a340d1853fb7927fac025b08b8a151fd2a2b0b86aa2c298e
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid
