Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 27 and May 4. As with previous roundups, this post isn't meant to be an in-depth analysis. We'll summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats is non-exhaustive and current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org or ClamAV.net.
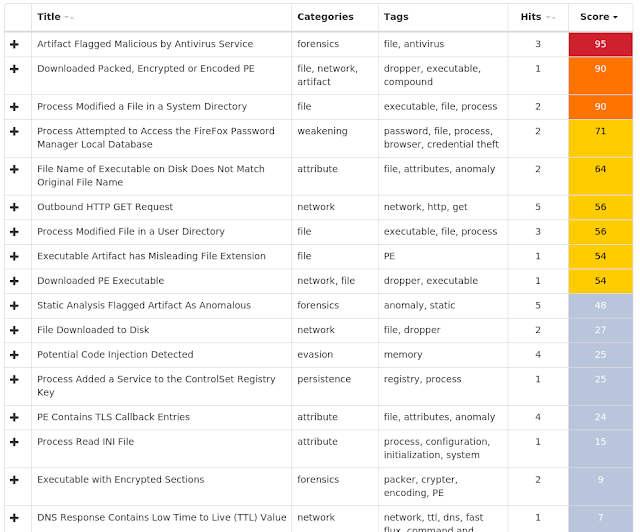
The most prevalent threats highlighted in this roundup are:
- Win.Dropper.Yakes-6527307-0
Dropper
This malware family sets up persistence on target systems by adding a registry entry to HKLM\Software\Microsoft\CurrentUser\Run. It also uses netsh.exe to modify Windows Firewall rules to allow a DLL to communicate externally. - Win.Ransomware.GandCrab-6526409-1
Ransomware
Gandcrab is a piece of ransomware that encrypts documents, photos, databases and other important files, and adds the file extension ".GDCB" or ".CRAB". - Win.Dropper.Tiggre-6526413-0
Dropper
This malware is a trojan spyware. It will exfiltrates information from the victim's PC and sends it to a command and control (C2) server controller by the threat actor.
Threats
Win.Dropper.Yakes-6527307-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: internat.exe
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value: stplck
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
- <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
- <HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
- <HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig Mutexes
- N/A IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- N/A File Hashes
- 212459961e8c3c574cefadaf422e3226c169f01593d480cdf303dceae56e200d
- c4a606577fe097b9f3eb9ad1bf3e3d95f917383c765ba929b428fdb8bd17f44c
- ac7b2901d2dffff27e27c4e2889f729496b94c4ffef3802391f7aefd837f6109
- 50d4bc39a6a426f9980a64bc464703dabe3ea4fa183265c66cb3d1c8adf82ddf
- e5bf1ff23ec9b7977e28643ba1102adb96576166de6e749c15f0fd54e8379a45
- 1d0a138b233dd25cfba925034778bc05e911407633385de30ebe15be61984bae
- bf131b8194cdc3073adc2913e3133d049361cc0d8ffd09161e71c537abbc9b46
- 4b581e236cd18568b32a67356c31a86799393edaad60af2b8dbba8babe3ebeb1
- 0d6f846d3a96d84279a28b990201473882ffa08d733300b0da19e7897580d0e1
- d77b972781dcf37a1c6a8f3d17077db8ef83f01f0e6449595836dafde9dabd13
- 76dc4a0faea60ed479dca96a57faa6eb4249665d32f23530ae57ebe63a1911b3
- f8d14cf852d1a450866d4749733dca06ce08f0b48534874b46218d671526eef5
- d377c493b98ffbf9dcc3b9938441f628de5bef99078b1351b6c0088f3ca87483
- ff06a02731588c4dd5b78584f5342739f4b65c37cfb34d73380d8e98a66fa18e
- d76273353bf949dafe1afb1ee27c19efd1221e8cc3bc9eb7cba1d18089b7ff4f
- c2ff1b2e48e269a22f10d7a89d2483af007fad5ac21d417e213802aaa0403870
- cc52ae1383c424b2481b3e975aa0b6c93061e63c28b7f93935222e474b75fae6
- 39cd2440d772085b1f2b84e524363a6e260eef6f2031300b9b6e02e433010419
- 3a5cff60f6dce5a0f264921838486ce9a7f48c2d897eb57886211bc99130d132
- 14b2f4fb032f20cedbdd692dcc1a8cefcd445a94198f58adc474fee8dc7d57af
- cd5ac2fd508dc3db95995fc643090f73581d937ac7620e058b7bef011e5c7eed
- 3015144e74631e7990953621367f33a673dea745154e904147532239ae5fedc6
- 26498d8b242924cad96dea24b39d5df88850c24c5e567db646c8d20891e87ab2
- 35f0da1890f512f1185cf1502306c641cc9a6a28060b387e33d638bda22a5e96
- ed57490c6876bf5d420841bdf5bf79002c323ea29b1e4b74093eb40290abb821
Coverage
Screenshots of Detection
AMP
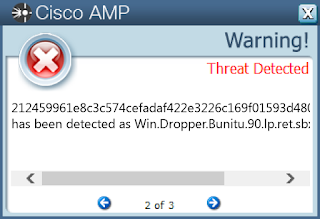
ThreatGrid
Win.Ransomware.GandCrab-6526409-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value: azpprnrnrcq
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce Mutexes
- N/A IP Addresses
- 66[.]171[.]248[.]178 Domain Names
- NS2[.]VIRMACH[.]RU
- politiaromana[.]bit
- ns1[.]virmach[.]ru
- ns2[.]virmach[.]ru
- ipv4bot[.]whatismyipaddress[.]com
- malwarehunterteam[.]bit
- NS1[.]VIRMACH[.]RU
- gdcb[.]bit Files and or directories created
- %AppData%\Microsoft\auzyuj.exe
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\7TZAD419.htm File Hashes
- 7b9b8f829674aa2eb6a64413c242597e3a2f6f4b1aa4c9f6309be3877180209f
- 6c1521794b8232598e0fee70656da09528e8acac1e3ccb443e8cc9efb4a43d83
- eb27a047448f0d5901cda8d4e47854a26acd602bc3d89eebdc0768ad053b0c2f
- d880eed2076d1e0ce0d019e029b503dae291aa620f5624ba7c40f21a0f425e77
- 311746c6767acda1e4cb18471642a1fea312a5e00aa69098c8f84de0846da311
- 7a89a0ac5ef495b7198dbdf91d06f21b976a70ad693c1236116a5eb0dac087a7
- 8b59359e89fbddfd85ac6af0641ebec1881aa7c28a6479205b876abdc47fc8bb
- 740528b18d963721e598cbf35e42df5929cd0c3ee90c41853063174c05d5d689
- d1901ded57b17e405c68f235db33d7be48cef6b0a9a45eb58de7b771b7582004
- dd387d1748454444a8990cae3d0a46b9c11d5addc9830bac55013a2db15dbd16
- 022995fa1ce1451aac2d87c8b85cdddd68f5bea4563c3af98987c4d3dca2f824
- 6b3a7117a457273d4016243892b86456ae9d1acd35eb770702363ce55b938e1a
- d71337186b871ad011ae9b1f568290997ec445f468702273a68a7f5366bfb2d9
- dd57a216c5482daa9ffe0764e144bda881fd5e47d27c5b716d2d71ae471bc624
- 7c99916b0478a4cbc8c94aeea5aa6b90f8056461c4881fdb645dabe98a1ee190
- 2f73091f77c899d4ad8df765088d7602081e0a570cb1d26da030c64781ab0172
- 4b64922b694e26c5abcd2bf8ba9954520009e4c1088e4ce9417fb2d06a2c79db
- f7961fecbaf223b8318e50cbea4822c3a7da106ecb2a8411d03af5aee6328812
- a62bd1ff7efca64002d5831c3ea43cb713f8501e2c83bd30ab60d91047d45a72
- 9b162db4b38c2b650d2521e1de8c56cb0fc5b56aebcedf27c9d35f51e12a717a
- 0678aafb4eb91d68de4c9354e4a254ece02422cbb43157ae06b5b925a1165992
- eea453fe669f09bc36259544063528ceac9153caf597e5ca27801cfb7e8db3be
- 4b53ebc0f9a4678c012151171718731e98d45f806b170ca04c7b2510b0e7c116
- af2705303549459628dfa11354c4fa16ecf13c45453d16c819a8cd6c26d5cee1
- 280d97ae7c5e478c185f5ea86e5fd214b0023539f7623be7c9500489309f85a1
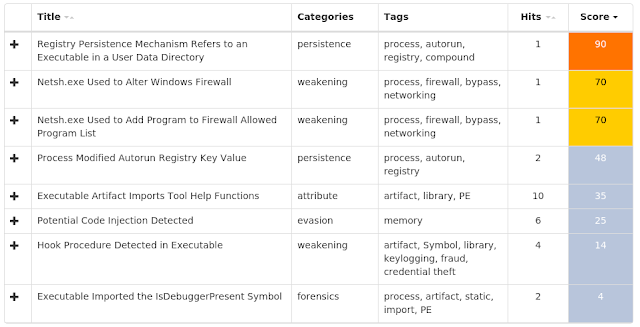
Coverage
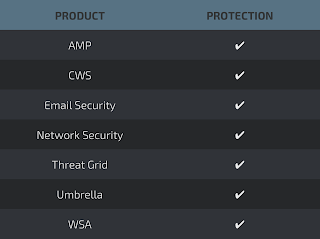
Screenshots of Detection
AMP
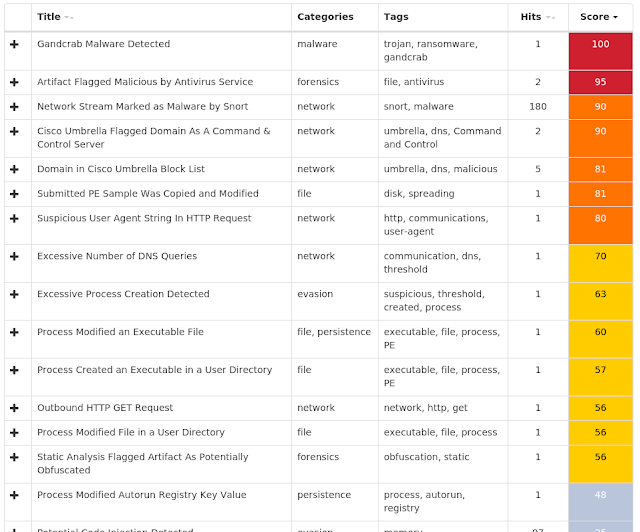
ThreatGrid
Win.Dropper.Tiggre-6526413-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpDomain
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpNameServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDefaultGateway
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDomain
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpSubnetMaskOpt
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpInterfaceOptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNetbiosOptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServerList
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS
- Value: DhcpScopeID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\Software\Wow6432Node\Microsoft\DownloadManager Mutexes
- N/A IP Addresses
- 104[.]238[.]156[.]230
- 45[.]76[.]241[.]231 Domain Names
- down[.]kaidandll[.]com
- api[.]new-api[.]com Files and or directories created
- %LocalAppData%\AdService File Hashes
- d51890673d1a7cd7de5eecd76a54211b3cebb15058ec22dce44bfabb3ef86ec0
- 939d208be5589007d24178a92620411e2c6d84387c790699e57cb52e063a5348
- 03d61dc3fc8d70e0075081d3e02f520861f342f7ec1c4b1cbaf895f995d38b4f
- 77d36423c105319a4797d0c70acd6858416cf87111ff843eef23e2b30ad0b473
- c87547487236791ff3dc1d6daef854825fb49f0ad5c96b69037dba7b08185841
- 9cbb5dbb783671ffbfa65ce3b5053259536de48f0d64312e5c46e6cf49d9c901
- ae6f4e3c68704c99db60617c09405ffcd914141f6147f7234bc5639105fb702b
- 876b2e195cbc70915501f15a41b6f4e5b447985683427ba36d392bb0907ad021
- 575d3e31f44e5af6fb84ad47d6b5556338b3f092847e49366358a0523b34cda0
- b5ace9a48d9b304066b4d355921495cf32d3a8b303b2f82800ef11556b310474
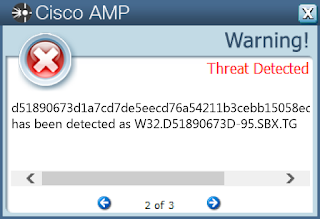
Coverage

Screenshots of Detection
AMP
ThreatGrid