Welcome to Cisco Talos' weekly Threat Roundup, where we go over some of the most prevalent malware and vulnerabilities we've seen over the past week. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this round up are:
- Win.Dropper.Snojan-6553195-0
Dropper
Snojan is a downloader that is used to drop and execute additional malware. - Win.Dropper.Fareit-6544485-0
Dropper
Fareit is malware designed to steal sensitive information like stored login information. You can read more about it on our blog https://blog.talosintelligence.com/2015/09/down-rabbit-hole-botnet-analysis-for.html. - Win.Dropper.Icloader-6553203-0
Dropper
Icloader is a dropper that can install malicious or potentially unwanted applications. - Win.Dropper.Zbot-6553346-0
Dropper
Zbot (AKA Zeus bot) is info stealing malware targeting users banking credentials. You can read more on our blog https://talosintelligence.com/zeus_trojan.
THREATS
Win.Dropper.Snojan-6553195-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKCU>\SOFTWARE\DOWNLOADER
- Value: quarantine
- <HKLM>\SOFTWARE\MICROSOFT\RADAR\HEAPLEAKDETECTION\DIAGNOSEDAPPLICATIONS\CF30E3D3DF78F487C056A09D220EA29EE17F1478304146F1395DCD4273DB6DEB.EXE
- Value: LastDetectionTime
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\Software\Downloader
- <HKLM>\Software\Microsoft\RADAR\HeapLeakDetection\Settings\LeakDiagnosisAttempted
- <HKLM>\SOFTWARE\CLASSES
- <HKLM>\SOFTWARE\MICROSOFT\RADAR\HEAPLEAKDETECTION\DIAGNOSEDAPPLICATIONS\cf30e3d3df78f487c056a09d220ea29ee17f1478304146f1395dcd4273db6deb.exe
- <HKU>\Software\Downloader
Mutexes
- N/A
IP Addresses
- 104[.]28[.]21[.]191
- 104[.]28[.]20[.]191
Domain Names
- reason0monster-meadow[.]tk
Files and or directories created
- %LocalAppData%\Temp\Downloader
- %LocalAppData%\Temp\Downloader\tempicon.ico
File Hashes
- cf30e3d3df78f487c056a09d220ea29ee17f1478304146f1395dcd4273db6deb
- ad71f36a2cfdd5cd113a12009ef4e56e21fe028ac449841ab2effa87292292ec
- 8c28892b44b95c2f04ceedb0be68e8fdaa6eb444b2f1fd9f1db5eed9be8a4147
- 5761e20e73dadf7be05f7fafcb40d9b816885c8331fc69448eab3965ac8ae940
- c6739a0e1151cb69ab43089901da6c5f1b932dc41048d02e4bd242b0e38e91fc
- 422851acbc75b521896e06a5158e32d94a0a652212843fd87a00d88bc47dc52a
- 3e7df4da29ac871c46a77e4bbc4dc1c080f73370a7db820cd6fc87884db7bf89
- 80382158e2bb303c7e046d5144fa0f49d3c525f84fde81f4bb9fbb8e162927f5
- 5a6a4807e91e3a706999d60a44cadd362f89ec94ff19088b24aad9239c676f78
- cec042b98f1ca6d223a4a3ce911098493ef656c7f628e0404325b5f143fd26b8
- 5c712a999755291a8cd0204a2e18cf876117e10074d89c8ba1f4fbafaf4fcaf0
- e4b12046b82cdf5a6d30f08b11134e3e1caf321fabd2424f2c3873041eb1c1b0
- 5a74303325990d5beb7f46f91429a6178fb1fbb0daf64e82d72906608b8a1e90
COVERAGE
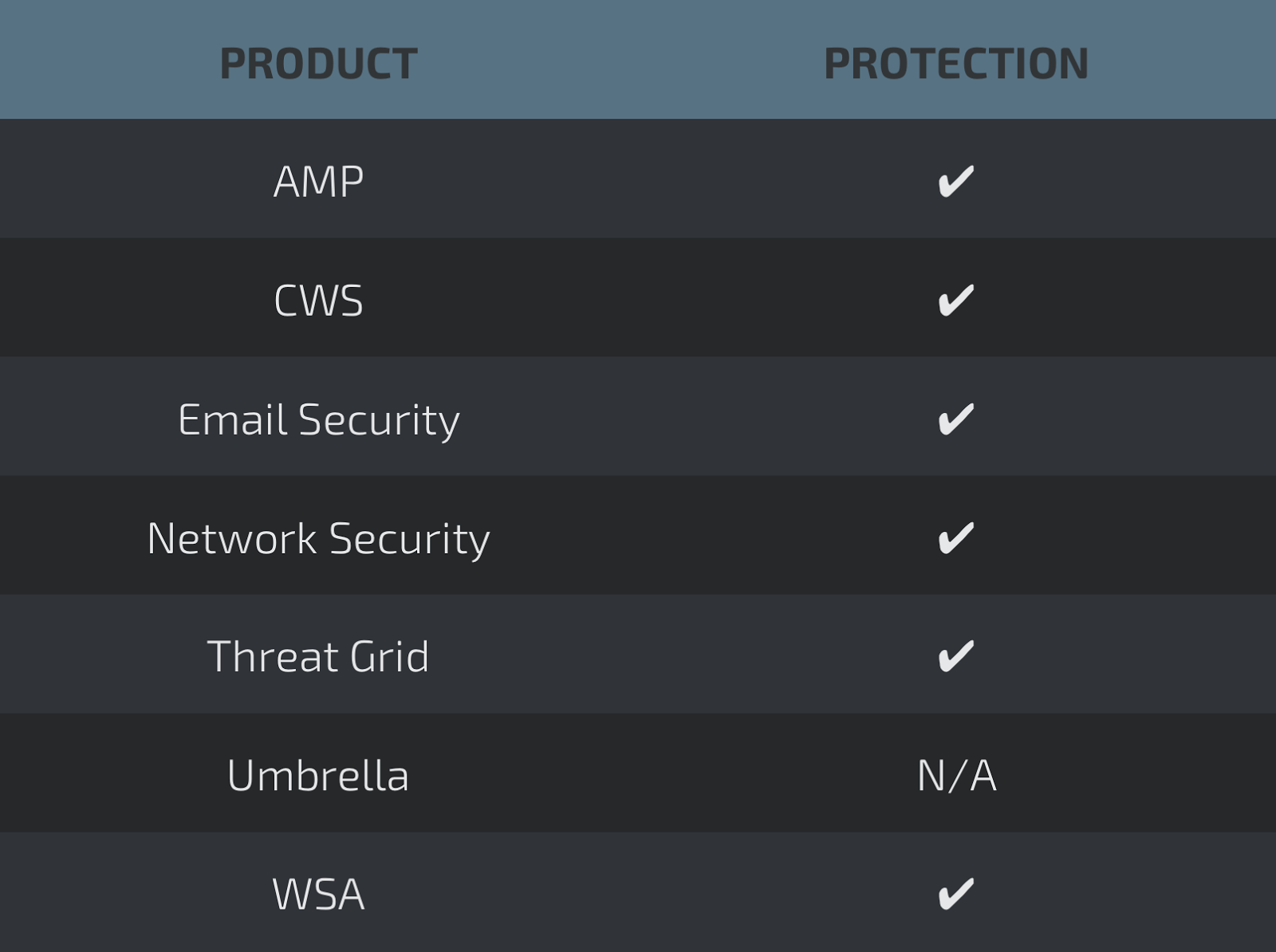
SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Win.Dropper.Fareit-6544485-0
INDICATORS OF COMPROMISE
Registry Keys
- N/A
Mutexes
- N/A
IP Addresses
- N/A
Domain Names
- N/A
Files and or directories created
- N/A
File Hashes
- 2e7d24541da31ab5a130cf7df030e1c3d2ee31241713cd2a55733ac2557888fb
- c98038f1367e8fced0f902e73ea97dfe07d6b2863ce5fad439e87f3a75eee2d2
- 90c33b025fea52ec12cab793625eccf08fc55e544976d8aeed82c883c78ea8d6
- db88e8ce7f0015c132e1a5924c0d51888b3c7edad698d7dd99a62408dded21d4
- 77f546ee92e7466eb3950374e5afad7af73daed911af1c17482b6ab0abb44500
- 38fa0b6386e446ee7e1678f3a883bdc93681d5038da66486cfea4a2d9d9c4fc0
- 1b6d23ded662ec5bfb5d34904fda6f337be2069557dddc139e69d48672bf5c96
- 1f3f15ea6539c98148ef586de273b29d698986317354f2312e2dba6c4c5c5cbb
- 87cd1118be63b7fc999c715f5a54877b72db273cff33d95427518a489959a755
- c7f53968de7b8c7c0f8311c9df55717844afe6f63a8e4ab7f0fddc6b31c5aa7e
- a9ae093f49608d3220681a69f8873156369f86a4b5dbb135a5ed295dfb01a6df
- 3c2c7e48c16c4f9ba5238d397243f0aac758a37feea57f08ae0df78a957324da
- b666016a21c083b8e528f8175ae2d6417ba2ec3e5dc2a6336e29e52efe960a89
- aed6353688be80e822dd4d9c214d939632fe0db9930a3149b7bc865c9daa5b01
- b5eee79eb0cddb48fedce82ed4ae4ba364b995a97c536d528c739b01d7503eb4
- bb8213867ea8ba9a16071d4e4f817fdf66f70e2a18a7fea1791efa885701ba87
- 27d159cc11b0eab97c37e8cde3c13cd2d7e9720e7ffa41a7e8451d08c8e9da0a
- 47f7b3ccdc0a8a91da054181d31a15f756762608e577750bd4c90c892fd47768
COVERAGE
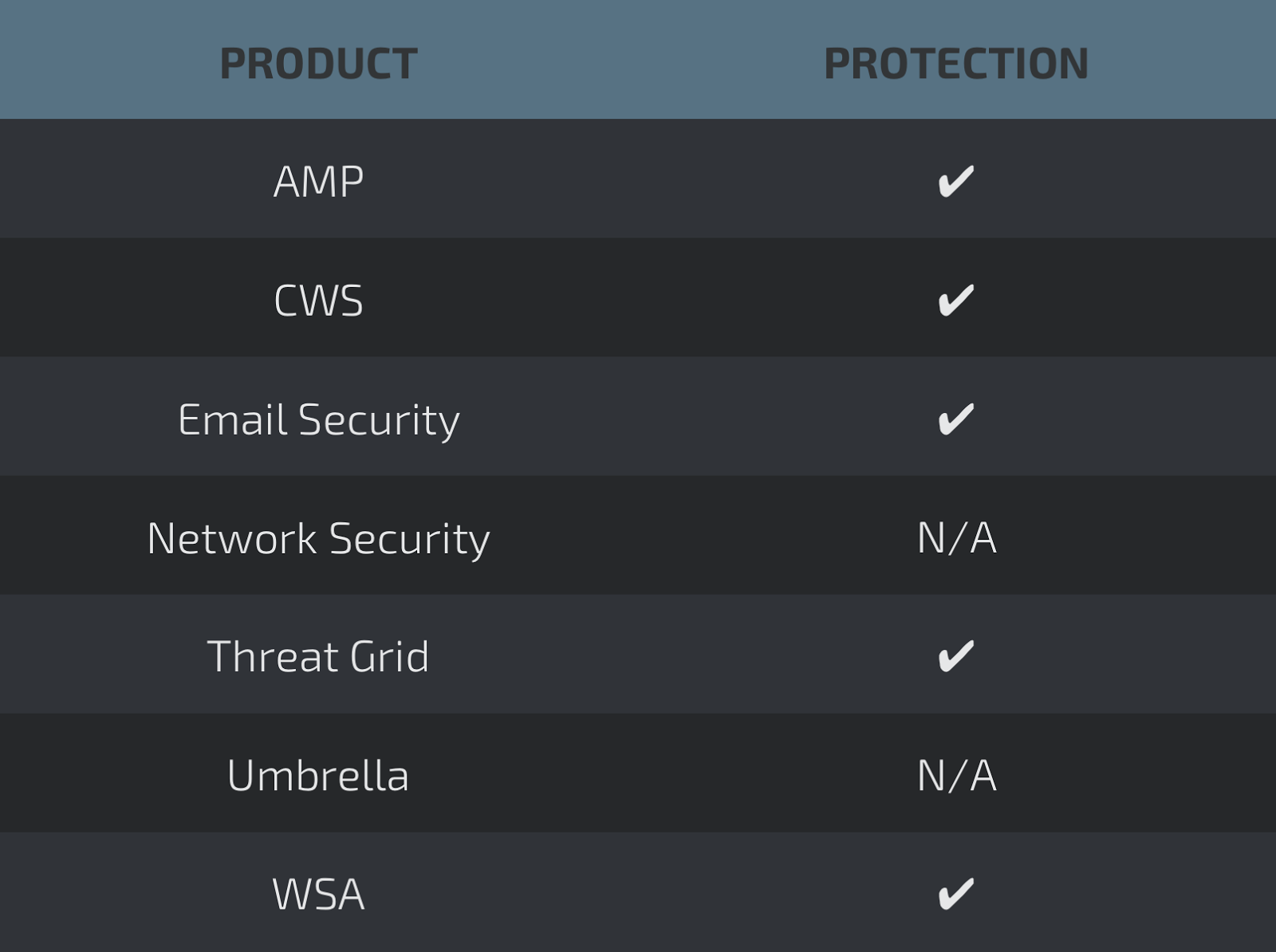
SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Win.Dropper.Icloader-6553203-0
INDICATORS OF COMPROMISE
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: SavedLegacySettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- Value: DefaultConnectionSettings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpDomain
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS
- Value: DhcpNameServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDefaultGateway
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpDomain
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServer
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpSubnetMaskOpt
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpInterfaceOptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNetbiosOptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- Value: DhcpNameServerList
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS
- Value: DhcpScopeID
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- Value: CachePrefix
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- Value: Collection
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- Value: CachePrefix
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value: AutoConfigURL
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value: IntranetName
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value: PnpInstanceID
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKLM>\SOFTWARE\CLASSES
Mutexes
- N/A
IP Addresses
- 188[.]42[.]242[.]245
- 35[.]158[.]168[.]189
- 1[.]1[.]1[.]1
Domain Names
- ec2-35-158-168-189[.]eu-central-1[.]compute[.]amazonaws[.]com
Files and or directories created
- N/A
File Hashes
- 0a5fe807dec1750e12787b96aa1fb5f8ddfc46f48d36af32049a2f1750ae9bff
- 81102d69100b4ee91bd1247a22ed5959f2da57c2bcc064bdd531264284a8763e
- 1e7bfdd44e0e8331ce3f03cb37b6ae8f30667a4ab0fc5fa7b417cc9feeb4a7f8
- f573a18c7b57275b2737e62c5c0468acf688a9c2fad9a3c5b83d5209bc96cceb
- c08e6b6708db6621a434275fa085516873cdd6ff39e818b741891b2377dfca2d
- ef50d5e5dcc2a1ea6f546304b266b5c8960b0ee9c87305fc63c3cca26019d7d6
- 800a0533147b774a1fd6940e948772ec20114ad4d2856ae1160dd09708695b38
- a4f236efc26615e3ade5ff9c961d698b0aafc40b1b257a441dccd8ca060dfa90
- 2f6f1cf599cef00e89b826b408f62d0949dc3dd8a1f6ef7b64a4d3368f7f0e6b
- 554098adf01c6e799494a0415fff359bce2cf1543c23d7b46c464c9ec49982d6
- ac1164f631b5ca03ee6e2dd39a492ca0b49c9d14a2ae4b2714e135ed48669dbf
- 8054fdaa9d6c198ee592d03b236c3e78272f699e3149b288f8a1a4109a5aadd9
- d721a98df1592e152d2a096ca936bbe776d76e013478ceebac99114b07330e89
- 743375f8d3d42ed1fb2b02193e4366d718edd0b8b6b70ad0c69d937392bb82c9
- 524c3716396d539e0ab0b4801fe784e81a32395a9ce0222cd4ab8348831c2a70
- 44eeef3be66e7530c1201ade7a5e9e8ea15066bc91916173aa104d4576ce4b18
- 94afc3856a03eab297025cfc6f5f3ed81cb81a925b745103b619d409baeb4b13
- 9148c9000dfd4a1fe9a1fb64301c84eba312b578bc2c605ca1644169f8ab8916
- 572fd355a7ee18c8c3b3f14f4864597038eb76beca81527128e4eeba0d630706
- 54765436d9bfea2116fbff7a9069e4ca643f55eb5e722237cdd5d3a350e4b0ac
- 7b4abf2b425c28e2130cb43022fb18ca52c545f28cd74fff09db9a6ff4082b56
- 0698f016609e0c86abe57e6e5ebb547802d3ac77ac63714cfdbe0eb3c8eece03
- e35d8a62870f2d1ab0fb56fe6e35fb50f980aa2dc83c01e8509b4fed170ee1b4
- 7b7bce1098190011792b81b744fb21870fc99f3060882112a305b153d7140d4a
- 2b0fb049cb28726bef4586260e67d28e627ddc5421691d0fd32cce9a487d35ce
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid

Win.Dropper.Zbot-6553346-0
INDICATORS OF COMPROMISE
Registry Keys
- N/A
Mutexes
- N/A
IP Addresses
- N/A
Domain Names
- N/A
Files and or directories created
- N/A
File Hashes
- 723a41aee74c1dbda6649f6b4d97836d1eca0d5c82b36b3215abb0ee6559bf6a
- 27a498db8bf71b58aa53acbe01e96d9c5823badf808dfe201a566ab2f510af10
- fecd0ee9dde36132141660d0d6bdf70ae9c8de12f982a3eba3d187934553892a
- b7fb44c2c32afad596829db9aee32e6e97710435b5e48b78a4dab12b22a723f1
- e40b578a8122101de0df16884f1dfd08d1a1b49a47bf5c39ede5ece9573a03c9
- 8e35333bc6db1fed6d63b0da78a84dbc422a5b403975ed5513b8eab4670dbbab
- 340bd1ed4f96ca6f3877a57493fa647ff155045d28026d998e75a1225bdc5e62
- b6b9c98e7b2f61ecb6710d8415d02db230732f6b7b972fcb41ebcebcde256b41
- 47acb7051c8a0bc9c30f5691fae38750a25714d4fec10bcbcb2092559784fc30
- fad370e039e311cb76ca9d100f77409f3145a000e1b951b54bfd08fa4df07828
- ad0c94d8bb7fa915a87895ef17fb96446c045b4a4c78c0b67171752615ae48e6
- 070308a72056f5eb6ed95cf22fe97a582bacf825e31c0f0a7826ece1b604186e
- 17abdd1ae8ca74e061c6b3f2ef93c70a0278cf6fd272f186de43f6c3a605c61b
- 5a6c010c9f54051c031aab95f1c9237553569d5d29638f163ef75b62ecf97e36
- 75bec7ec1132adefb053663c654569d65874cf829ac4180748d7df2b7cb8bdb4
- 18d8a4dd9fe6949724546b197809f9c0f9542f1dbc6aded5462b7e0aee35c7f8
- 36a22ec97078427aff2fc35483a637e24188c371b8cfba6dac01377b06d634a7
COVERAGE

SCREENSHOTS OF DETECTION
AMP

ThreatGrid
