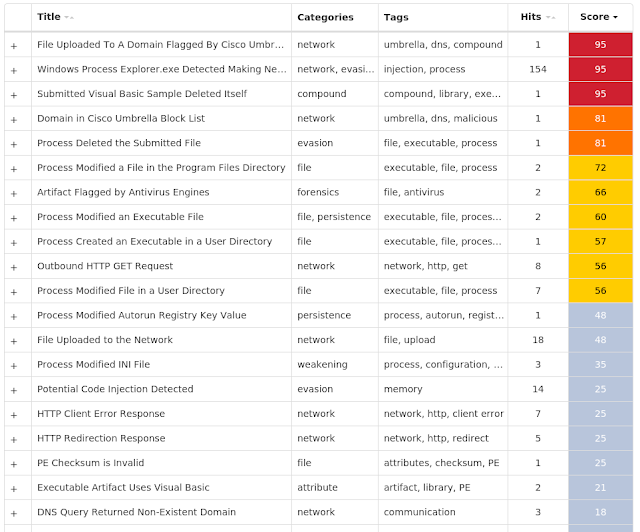
As usual, we are bringing you the weekly Threat Roundup to highlight the most prevalent threats we've seen between June 15 and 22. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and is current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
The most prevalent threats highlighted in this round up are:
- Win.Dropper.Generic-6584427-0
Dropper
This dropper attempts to allocate a memory region with the flag PAGE_EXECUTE_READWRITE to later inject malicious code and then execute it. These samples also contain TLS callback entries, which allow malware authors to execute malicious code before the debugger has a chance to pause at the traditional entry point. - Win.Dropper.Fareit-6584428-0
Dropper
Fareit dropper injects code into legitimate system processes, usually through an evasion technique called process hollowing. Some samples may use VB scripts to execute some of its malicious activities and modifies autorun registry keys to maintain persistence on the host. - Win.Dropper.Zbot-6584477-0
Dropper
Zbot (AKA Zeus bot) is info stealing malware targeting users banking credentials. You can read more on our blog https://talosintelligence.com/zeus_trojan. - Win.Trojan.Generic-6584512-1
Trojan
This trojan is sometimes related to the Emotet malware family. It creates a copy of itself in system directories such as C:\Windows\SysWOW64\. It is also capable of uploading files with information about the infected system to remote servers and adds a file as a Service in the System Registry Current Control Set. - Win.Malware.Installcore-6584374-1
Malware
This adware creates a copy of itself in %APPDATA% with the "tmp" extension. Some samples contain a library reference to the SetWindowsHookEx function that could be use to monitor keyboard or other user input, which could indicate keylogger capabilities. - Win.Trojan.Jaik-6584366-1
Trojan
Jaik contains a library reference to the VisualBasic runtime DLL, which allows the process to run Visual Basic scripts directly or internally. It also attempts to allocate a memory region with the flag PAGE_EXECUTE_READWRITE to later inject malicious code and then execute it.
Threats
Win.Dropper.Generic-6584427-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LruList
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FileIdIndex-{3f37ba64-ef5c-11e4-bb8d-806e6f6e6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\0a0d020000000000c000000000000046
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\13dbb0c8aa05101a9bb000aa002fc45a
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\33fd244257221b4aa4a1d9e6cacf8474
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\3517490d76624c419a828607e2a54604
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\4c8f4917d8ab2943a2b2d4227b0585bf
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\5309edc19dc6c14cbad5ba06bdbdabd9
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\82fa2a40d311b5469a626349c16ce09b
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\8503020000000000c000000000000046
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9207f3e0a3b11019908b08002b2a56c2
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000001
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000002
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000003
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9e71065376ee7f459f30ea2534981b83
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\a88f7dcf2e30234e8288283d75a65efb
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\c02ebc5353d9cd11975200aa004ae40e
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\d33fc3b19a738142b2fc0c56bd56ad8c
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ddb0922fc50b8d42be5a821ede840761
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\df18513432d1694f96e6423201804111
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ecd15244c3e90a4fbd0588a41ab27c55
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\f86ed2903a4a11cfb57e524153480001
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\{D9734F19-8CFB-411D-BC59-833E334FCB5E}
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\{D9734F19-8CFB-411D-BC59-833E334FCB5E}\Calendar Summary
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\10000000090A2
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN Mutexes
- 8-3503835SZBFHHZ
- O957R401SY5ZZzJz IP Addresses
- 198.54.117.218
- 104.27.180.157
- 184.168.221.104
- 52.72.89.116
- 64.98.145.30
- 107.173.153.58
- 162.213.249.103
- 180.76.141.40
- 217.76.128.34
- 104.237.136.127 Domain Names
- www.dingjian1688.com
- www.tradewindsonlinemall.com
- www.mewqaccmertgroup.com
- www.holymedgap.com
- www.tealeurope.com
- www.clinicaslipedema.com
- www.christynhomes.com
- www.oliver-group.com
- www.eloloans.com
- www.yourdready.com
- www.cinderellagames.com Files and or directories created
- %AllUsersProfile%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
- %LocalAppData%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
- \PC*\MAILSLOT\NET\NETLOGON
- %AllUsersProfile%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
- %WinDir%\AppCompat\Programs\RecentFileCache.bcf
- %ProgramFiles% (x86)\Bzv1lxh98
- %ProgramFiles% (x86)\Bzv1lxh98\igfxnpttjhuh.exe
- %LocalAppData%\Temp\Bzv1lxh98
- %LocalAppData%\Temp\Bzv1lxh98\igfxnpttjhuh.exe
- %ProgramFiles% (x86)\Bzv1lxh98\igfxnpttjhuh.exe
- %AppData%\O957R401
- %AppData%\O957R401\O95log.ini
- %AppData%\O957R401\O95logim.jpeg
- %AppData%\O957R401\O95logrc.ini
- %AppData%\O957R401\O95logim.jpeg
- %AppData%\O957R401\O95logrc.ini
- \TEMP\tmpQDq_1r.exe File Hashes
- 20c27455b4a86eda29e494e4241f95599175133f8d852759be88641654374ef6
- 286a7c32ede0a4650e399ee1fefc347d9265befc3381eacefdc63937e19cd6d4
- 349a7f3b6c5cdb14d58b7eb8d2256a593f3097bf22960504d6d094472fbd1366
- 3522d25848b5fe656d1fb100ae5d546f376569f8441f5c0e7745f4ac234a5c55
- 7165fc0f622effb44f6893555e898f3cafea60858923409863e0e2528536999d
- 7dd9adc72effd65e28191edfd0e282eb4375c3206983fdfae255d12d2f407e91
- a6e515869be77e1f332df975ca719a54544a0fa56698607788294215369b2ff6
- bf9274591ed4a439d9b5d8fd6e4c620804e7c33130c8cdc8258df3de7f330fd6
- e1f0bfaa87925d5f89b9ccc3196246b26296a1ea305ab3bab6e681a78d130bf4
- e3f0529b2f75ca2930b2bc3dc22d2ada08491abf7a3f384e8ef81ae91ef2b25d
- fcf94877a6daa05e2e22d70f2d2deb469a655d77a8318a7d2b038a331364e780
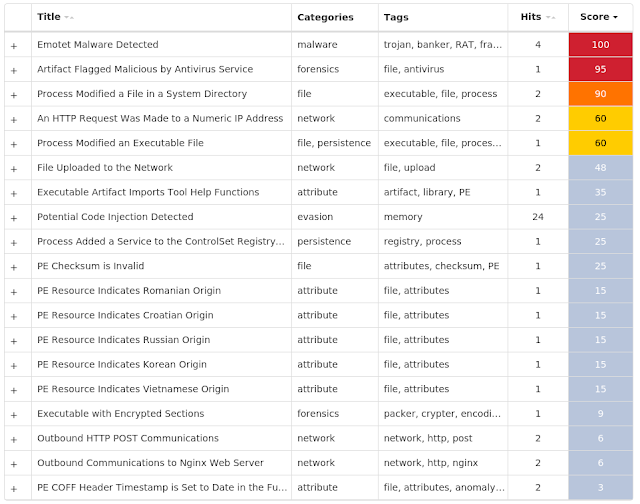
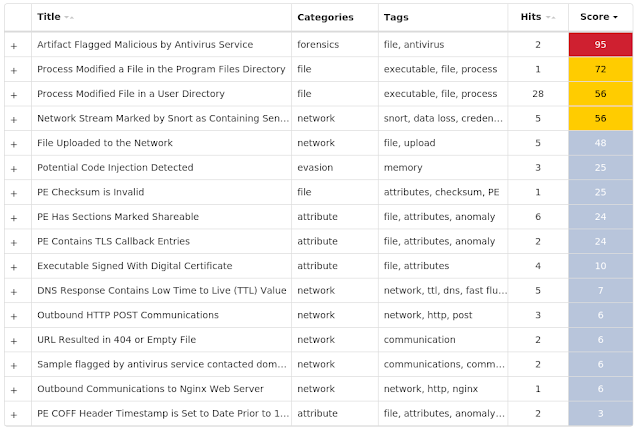
Coverage
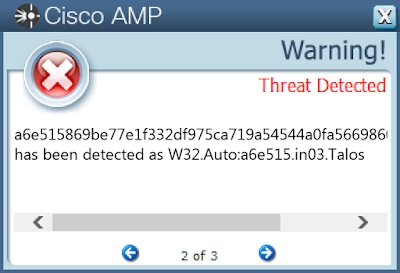
Screenshots of Detection
AMP
ThreatGrid
Win.Dropper.Fareit-6584428-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- <HKLM>\Software\Microsoft\Fusion\GACChangeNotification\Default
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Mutexes
- N/A IP Addresses
- 216.146.43.71 Domain Names
- checkip.dyndns.org Files and or directories created
- %AppData%\MDU Resources Group Inc\MDU Resources Group Inc.exe
- %AppData%\MDU Resources Group Inc\MDU Resources Group Inc.exe
- %AppData%\MDU Resources Group Inc File Hashes
- 09aee7d45b4d4990fbfe44fbc41d908d363c3c6b3a68a633b6d0d88819dd8203
- 0ab5ea239c3b4a2eae0c9a8d7fe6fbfceb877e542a823bf971e712efaac84a00
- 0ad759f72f4c8fcfb84067b4b53776763c2e5b663ee1617f15135918a056bc4f
- 21793b775320c182c4db6ffd742445ddddc9dd4925ef1ca979ed6a35c617fd45
- 27a501fb263df4360b53753c91a66bda55541d7e0b43e5698665978f537a2eb8
- 2ff4ee2c05c59076e923c0ee07a27a2f8434fcfe047d341538b1ea8cdfa6729d
- 3ac4b5cd646a722924118e761366480c83ab278dbb5416a5e58e0eddf3a1b903
- 406d5dc4de69215015543a52be7d3bafdeb7191adc98084563d55b5996659ce4
- 437068cc219c152d4bef83c2dd6916e0c0a090eb607c68018c28c6ac82c84b2f
- 4c65d4cf2a7773a7358323b826665b0dcc8eefaa6cc543fb493f3aff3329804a
- 7ff6c48e69875b5d824d1a6b005e179002076f4ce90fce5c9a22f044ac65291c
- 94a44a077ea320d2bbf338b72fa4c263d8cf70eb398c5ffb07d5dc7e0adf840d
- a92ad1f6f77b663420940708572de26cbaaeb70d4e22114f7c1c8f62d7f4d500
- b381f69867fff9a3e07c84f7186a1ed86dbf98c7b9f09df3978b6649e13fb1c3
- b5e589fd4e4522ab6320a76a1c2e69e6e1e557628e87cc16e0572ef0f31453d8
- c0b1a8acf40906c0c0ee2041ee1e3f1c04ec0b73602b0ed8e8e97104075c70a7
- c11d18e057fd911901e9473689b04156110cf5eea97e4b33f363b00ad0d161e0
- c4df3b3743c9696c5f20b9763644bff65500440019bbc83f85930ddb287a936b
- e18f8ac7f8275e648ef44c882e032389770e0ce4fda43142b69ab23ab4e9f45d
- e9c8209739ed62082a8f9cb4067ab2c8ff2588db6c0a165726b55cb5bef62695
- f32c8bd9e3c0bedcbe6c33d08723513d3da438219902c25012c10d648a11d824
- f51967541563d54bd8e7219a127d5f2189cf01eb33236729b3dbb540b171d17d
- fd29ce672f03d7970cbedcd45a75e512a1df62e758f5776b90e1af6f1a2c2f2c
Coverage

Screenshots of Detection
AMP
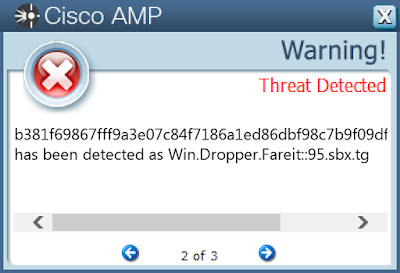
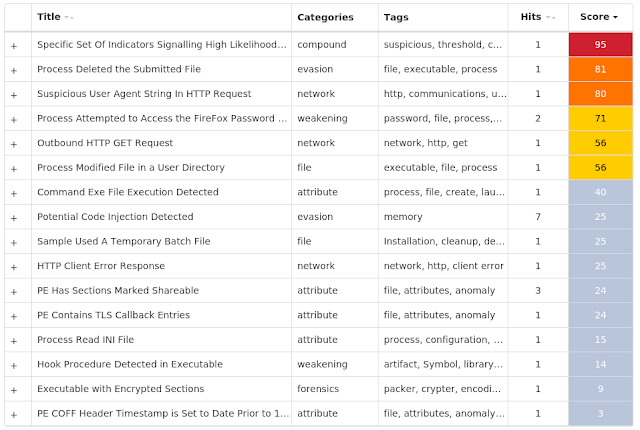
ThreatGrid
Win.Dropper.Zbot-6584477-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\NETBT\PARAMETERS\INTERFACES\TCPIP_{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TCPIP\PARAMETERS\INTERFACES\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}
- <HKCU>\SOFTWARE\MICROSOFT\Ycbi
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- <HKCU>\SOFTWARE\Microsoft\Ycbi
- <HKCU>\Software\Microsoft\Windows\Currentversion\Run
- <HKCU>\SOFTWARE\MICROSOFT\YCBI
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.101
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.103
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.100
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.102
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\ACTION CENTER\CHECKS\{E8433B72-5842-4D43-8645-BC2C35960837}.CHECK.104
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS Mutexes
- N/A IP Addresses
- N/A Domain Names
- roster.su
- etot.su Files and or directories created
- %LocalAppData%\Temp\tmpb550dbcc.bat
- %AppData%\Ikywz
- %AppData%\Ikywz\opmaf.exe
- %AppData%\Meen
- %AppData%\Meen\moibq.aqy
- %AppData%\Zulie
- %AppData%\Zulie\ylhib.ecf
- %AppData%\Ikywz\opmaf.exe
- %LocalAppData%\Microsoft\Windows\WebCache\WebCacheV01.dat
- \TEMP\tmpWfEKb5.exe
- %LocalAppData%\Temp\tmpb550dbcc.bat
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\Preferred
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\faf08ed1-edb0-448c-809a-73cb275c3833 File Hashes
- 153f450b211047e543b1ccce8ef6afe41a476aeccfd961cd0159d24e1096f77f
- 20d24c1936867db7511ec35003079dfd0bd6fa91f4bc0b34485c7f3a5adf31b4
- 71361e9c9a716ad6b6e0cc13e35b1f3ac0e39aa1eb33d445b87add909fb6e665
- b9163c8a5974b8b9397fc2af2fa692cbf6a9e332bf2fc5cc7cfe4ef256ec3bc6
- bb463702eb24d0d43d4510366ef05dc0cc5d6c001db2d80b7da59ce27d0f096c
- bfe8551016d5e77bc71774f3a1bb7b194ed0817ae11155347c8b3ec8f8f9578d
- d2c7a02492ab09e846a8dac12ab7bb7d742f0052071ab194cb6f838c68b14381
- df65bd267142c58835136c519d40eb4b529b735e4d0ee7baa7aee00e62d17f00
- e1de7ded32c7deabba387fd5ccf09d62c8fbd13b18a6bf1c8fa17d6746688c84
- f675c120ed096112a120ec9b4a72dd589f5fed33d280b851c71d1c9657397a5f
- f9dd63a23f4cf30db953e13d2a9f66fa6db69ac59b432f3a7abe9b6d9a955631
- fb48a9b9da0d772521f925d3f578930cbd078e438d8c0a796a1112f1f96db659
Coverage

Screenshots of Detection
AMP
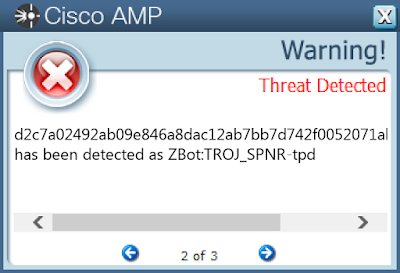
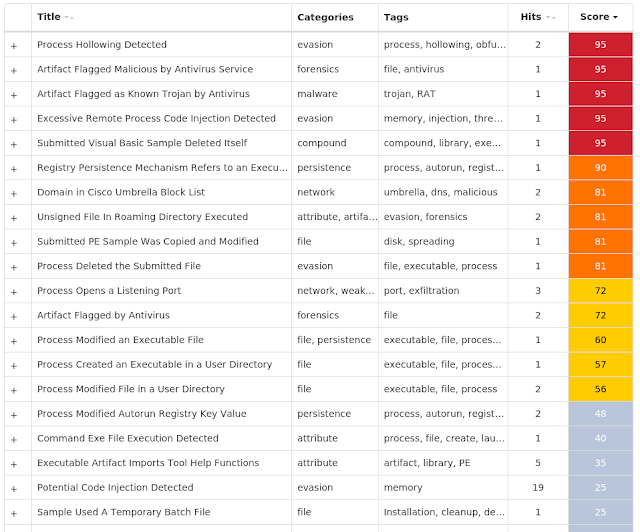
ThreatGrid
Win.Trojan.Generic-6584512-1
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC\PARAMETERS\PORTKEYWORDS\DHCP
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\IndexTable
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FileIdIndex-{3f37ba64-ef5c-11e4-bb8d-806e6f6e6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D6
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D3
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D6
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D6
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\8000000005683
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\A00000000572A
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\GENRALNLA
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS Mutexes
- PEM1A4
- PEM938
- PEMB6C
- PEM570
- PEM6D0
- PEM53C
- PEMB18 IP Addresses
- 192.168.1.1
- 255.255.255.255
- 192.168.1.255
- 70.182.77.184
- 69.17.170.58
- 209.85.144.108
- 68.1.17.8
- 209.85.144.16
- 62.254.26.220
- 82.57.200.135
- 193.252.22.86
- 194.60.217.89
- 74.124.44.100
- 195.200.78.68
- 64.8.71.14
- 108.167.146.22
- 193.252.22.84
- 208.91.199.223
- 64.210.232.50
- 192.185.4.48
- 217.79.186.14
- 66.147.240.163
- 64.98.36.162
- 69.168.97.48
- 62.254.26.231
- 62.24.139.43
- 216.40.42.154
- 40.97.188.226
- 184.154.202.50
- 143.95.253.117
- 198.89.124.197
- 158.69.57.254
- 192.185.4.148
- 69.163.253.7
- 74.208.196.99
- 212.1.215.225
- 195.229.241.221
- 69.89.31.229
- 54.169.79.115
- 93.17.128.164
- 50.87.144.90
- 64.136.52.50
- 144.217.66.117
- 69.168.97.78
- 62.24.202.43
- 52.71.59.20
- 64.4.202.62 Domain Names
- smtp.orange.fr
- smtp.googlemail.com
- smtp.crosbyisd.org
- smtp.robeson.k12.nc.us
- smtp.fuse.net
- smtp.tim.it
- smtp.cox.net
- smtp.blueyonder.co.uk
- mail.vd.educanet2.ch
- smtp.gmail.com
- mail.wanadoo.fr
- gator4037.hostgator.com
- bbm-exchange.bbm-germany.de
- mail.cmidwest.com
- mail.banit.club
- mail.sfr.fr
- smtp.netzero.com
- mail.telebeep.com
- smtp.tiscali.co.uk
- mail.virgin.net
- s4.fcomet.com
- smtp.gtscarrier.com
- smtp.charter-business.net
- mail.cecompute.com
- smtp.hughes.net
- smtp.rcn.com
- mail.dbmcbride.com
- smtp.talktalk.net
- smtp.whitecars.com
- gator4136.hostgator.com
- mail.niuelec.com.pg
- mail.rjcables.com
- gator3071.hostgator.com
- mail.fuse.net
- smtp.wanadoo.fr
- smtp.exchange.1and1.com
- smtp.orthopaedicsopenjournal.com
- mail.tropitelvalley.com
- smtp.exchange.emailservice.io
- box429.bluehost.com
- mail.cmail.club
- mail.xplornet.ca
- mail.labolab.com.ec
- smtp.nhspeedometer.com
- smtp.emirates.net.ae Files and or directories created
- \srvsvc
- %WinDir%\AppCompat\Programs\RecentFileCache.bcf
- %System32%\config\SYSTEM
- %System32%\config\SYSTEM.LOG1
- %WinDir%\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
- %WinDir%\SysWOW64\wrGwEEi.exe
- %WinDir%\SysWOW64\wrGwEEi.exe File Hashes
- 07fd0e423c2272c76323d8b816f83ff4e4715fa97d22ef331131bd4ac5b084b4
- 114d916fdfc70a518790f184311ff5ef3488b4181366e782b37c0d68fdfd2f1e
- 482be1caf6a2a0b959a4a40460c007f88615ab787b8771474f9c6fc5cf5acf66
- 4ac3cc415b1b3847b69ec0e7fb4287dce886fe17631a4f5a9f0f400118aa972a
- 5ad9c2866e77495fe2d41c5067879bb938716fe00e4a8dbcfaa7b90a8b53655e
- 5f12c45ebd24669b0e69e63c549c6812d742220c5221bb147c6312f1a68ac5dc
- 6a3d06d6bbe7b98f604cc9167b7a96c94b8fb7f749f893038926f552b56c8931
- 7335842c08c2f8caecf1754ca5d5ee75d9a4cdaae05d70792dd4be56127de424
- 7f198deac8ecf78fc1658728669c1523176a65d71e95605b28991b09a40a6259
- 8387856244d53a3025f8eafbe1cd2bbfcf0c40c6a04f70de1d0e22d29261de96
- 86d9d667ba5d0880ada452dbac0b6dec35c30248398d14f984143ce7738e61fa
- 969e2c1803df2eda353feb8381687922d28d58bc2910feabc894842d4d9a388f
- 9c5e793117db00555164da86a4c4f075b24abef08b313bc192bb80a9f55f4e69
- 9fbbcd37da800026d3dcd10d2e3cd622447ff0d91c65c6ddf4a232dee2b6f054
- cc0208db49b171a19a6309301e78a0619bf3122887da1d28ea29ee0e84717026
- dad9965c05194ec329b240eec4e975269c2f4bc2a3fdda057872991c541ef7f8
- e7f818214208a01677a70b60b598703ab4c4408b1a495172e25934a7ae11c84b
Coverage

Screenshots of Detection
AMP
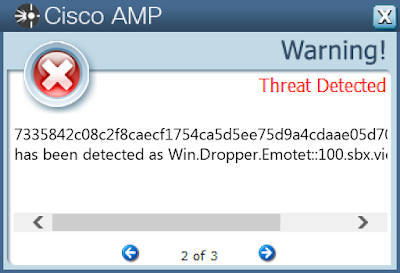
ThreatGrid
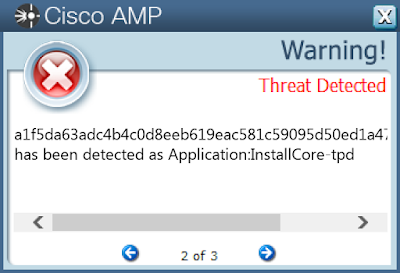
Win.Malware.Installcore-6584374-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- <HKCU>\Software\Microsoft\Internet Explorer\Main Mutexes
- !IECompat!Mutex IP Addresses
- 35.163.153.35
- 52.206.6.222
- 52.42.47.197
- 34.218.108.244 Domain Names
- rp.totikik1.com
- os.totikik1.com
- os2.totikik1.com Files and or directories created
- %LocalAppData%\Temp\in699DB22B\
- %LocalAppData%\Temp\in699DB22B\2A4213C8.tmp
- %LocalAppData%\Temp\INH265~1\css\
- %LocalAppData%\Temp\INH265~1\css\ie6_main.css
- %LocalAppData%\Temp\INH265~1\css\main.css
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\browse.css
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\button.css
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\checkbox.css
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\images\
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\images\button-bg.png
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\images\progress-bg-corner.png
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\images\progress-bg.png
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\images\progress-bg2.png
- %LocalAppData%\Temp\INH265~1\css\sdk-ui\progress-bar.css
- %LocalAppData%\Temp\INH265~1\csshover3.htc
- %LocalAppData%\Temp\INH265~1\form.bmp.Mask
- %LocalAppData%\Temp\INH265~1\images\
- %LocalAppData%\Temp\INH265~1\images\BG.png
- %LocalAppData%\Temp\INH265~1\images\Close.png
- %LocalAppData%\Temp\INH265~1\images\Close_Hover.png
- %LocalAppData%\Temp\INH265~1\images\Color_Button.png
- %LocalAppData%\Temp\INH265~1\images\Grey_Button.png
- %LocalAppData%\Temp\INH265~1\images\Grey_Button_Hover.png
- %LocalAppData%\Temp\INH265~1\images\Loader.gif
- %LocalAppData%\Temp\INH265~1\images\Progress.png
- %LocalAppData%\Temp\INH265~1\images\ProgressBar.png
- %LocalAppData%\Temp\INH265~1\images\sponsored.png
- %LocalAppData%\Temp\INH265~1\locale\
- %LocalAppData%\Temp\INH265~1\locale\EN.locale
- %LocalAppData%\Temp\INH265~1\images\Color_Button_Hover.png
- %LocalAppData%\Temp\9E6FFDFF.log
- %LocalAppData%\Temp\9E7000AD.log
- %LocalAppData%\Temp\9E7000BD.log
- %LocalAppData%\Temp\inH265813966324383\
- %LocalAppData%\Temp\inH265813966324383\bootstrap_5001.html
- %ProgramFiles% (x86)\9E7009E1.log File Hashes
- 00f5fb9fcc5740a8538141cd5faba3ff4c326558c62e5e95da316129785673c5
- 012a09533536cc77bf0eaed8ab3acefae793bdd35223ce5391710c70ddffe393
- 0135775f4298ddb7b44b2bb40c869c8ad78ba874203e151634eb2c71506c7332
- 0546adad07a2169c980d9965bc94ed94b9fce9b2f310ae1be8c6df3ba8c0a177
- 09d060282484fb0eed75a2f7e5970699b002c42ebddd5b0017911b01706f4646
- 09d603e99ccec947facb2b2da48bd5c7da44c622da2c97344fa89ed39dd65812
- 0a1c695bef83997a684e845b9179c9e229e4ca479e92e81b2e006dac6f559fe9
- 0a52f81e4d9c244880353df9b641c88f4649ced7df1a820c1bcc5a9722189a0b
- 0c07cb171aa5978cd5eeeecd22ed32b83e253926f82a439f2be076248894b1d9
- 0c97012e37ef8f55af1b9926c065c9c08bc32224718f2bbd6f3a3e971f6075d7
- 0e4ee2f6bddd019745bfca57bd47260ba52e0c8bc42013036b05d89fc643592a
- 0ec5f5d88faf0ed99235adf55c0f97870512a10144d97d8b32658bf718d4bca8
- 0fb590428e8b12d48d74e7744bb00aaa88c9079deadc8f5e61aec1145e67e0c1
- 1357c5fa8e01e446f4ec0065e7400b5810ee53115735f09e97a3af413b6d8de9
- 14018597d0f8231df086e21e0d8660b4ad94aeda5fefd3749604039731d50f55
- 14416c9bf4c7b938377b528cddd359509ce3c09a57b12a756451432f96e3e8a9
- 15d4ce867af59a0f95c4acd35c4abd4e0d8fe199a7a32fae5480c68669aa2469
- 17bde73dc4ee1fd1999d6efe7519a25bbfc61fe53c705665a2451b26367826b4
- 1806d1dc9deebea348c03f731696c0191f7ddf74b7c3af512df96e9c86dade47
- 185b0a621bd278df79a77eddecfe9908e8032b9e19d5db930ef5cfa56b766a45
- 1b6f5acaa8737285ab91f7ca5d80dff908aee706254c1aad1eabb8f310f78649
- 1cd10e184752c9eb4bc7c1d3301bc80f5d56b25c294d66945e4ae86653aa87a8
- 1e6bb4ed50b658e0bdd74fdfbb7897f847d83be01292b19fc29d4ebcc52557b6
- 200de4855c7523956ccbd08585b6102cec28ddc0710a6a1e11885b7b73b1d541
- 20ba5231bc9b84ce5640aca571ca65f76b0d1e2e5ff07250057c2757b3d58262
Coverage
Screenshots of Detection
AMP
ThreatGrid
Win.Trojan.Jaik-6584366-1
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\CONTENT
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\COOKIES
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\5.0\CACHE\HISTORY
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\INDEXTABLE\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}\1000000008F79
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\LRULIST\00000000000029D6
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\Indexes
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\INDEXES\FileIdIndex-{3f37ba64-ef5c-11e4-bb8d-806e6f6e6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB5\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- <A>\{F698CDEA-372F-11E8-8419-00501E3AE7B5}\DEFAULTOBJECTSTORE\OBJECTTABLE\AB6\INDEXES\FILEIDINDEX-{3F37BA64-EF5C-11E4-BB8D-806E6F6E6963}
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\0a0d020000000000c000000000000046
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\13dbb0c8aa05101a9bb000aa002fc45a
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\33fd244257221b4aa4a1d9e6cacf8474
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\3517490d76624c419a828607e2a54604
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\4c8f4917d8ab2943a2b2d4227b0585bf
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\5309edc19dc6c14cbad5ba06bdbdabd9
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\82fa2a40d311b5469a626349c16ce09b
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\8503020000000000c000000000000046
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9207f3e0a3b11019908b08002b2a56c2
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000001
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000002
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9375CFF0413111d3B88A00104B2A6676\00000003
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\9e71065376ee7f459f30ea2534981b83
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\a88f7dcf2e30234e8288283d75a65efb
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\c02ebc5353d9cd11975200aa004ae40e
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\d33fc3b19a738142b2fc0c56bd56ad8c
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ecd15244c3e90a4fbd0588a41ab27c55
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\f86ed2903a4a11cfb57e524153480001
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\{D9734F19-8CFB-411D-BC59-833E334FCB5E}
- <HKCU>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\{D9734F19-8CFB-411D-BC59-833E334FCB5E}\Calendar Summary
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Mutexes
- 8-3503835SZBFHHZ
- O247ST8-UYZ6KDCz IP Addresses
- 34.202.122.77
- 199.34.228.159
- 188.93.150.105
- 199.193.6.130
- 79.98.129.62
- 198.185.159.145
- 156.67.212.57
- 94.73.146.154 Domain Names
- www.acilklimaservisi.net
- www.mediquipmedicalsolutions.net
- www.thisforthatquidproquo.com
- www.verim.site
- www.nextdealworld.com
- www.pelatihanukm.com
- www.maydiamondbeautyandstyle.com
- www.mirrorxr.com
- www.nuuee.com
- www.walktofinancialfreedom.com
- www.epsycoachez.com Files and or directories created
- \PC*\MAILSLOT\NET\NETLOGON
- %AllUsersProfile%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
- %LocalAppData%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
- %AppData%\O247ST8-
- %AppData%\O247ST8-\O24log.ini
- %AppData%\O247ST8-\O24logim.jpeg
- %AppData%\O247ST8-\O24logrv.ini
- %ProgramFiles% (x86)\L0xbx
- %ProgramFiles% (x86)\L0xbx\winztqlgh18.exe
- %LocalAppData%\Temp\L0xbx
- %LocalAppData%\Temp\L0xbx\winztqlgh18.exe
- \TEMP\tmptxf6QC.exe File Hashes
- 4145362d249b81cd7f7caca054693ef5621a1f820101b4bff27009c896157e75
- 5270a58badc5af1c4eb47e8100958699dcb4ef137670da52e24d23f1d687caac
- 5dda41fb0abc6528d80995aedb47c0b59fc6467e7307bbdc75d097aef50fcd21
- 71f19b06d95ec1e2947c012008bda50e23fca9a8707ccef53f2b3d4c496d179e
- 7985460fa754edcbc2e3aa499d0dacf771a60d8a2c53e05113faeccae1496542
- a28fabc26c7bf6da4e8a7ae712c89fa173de94787aa612a245a1452a8fb4d497
- c2d7be6d4ab0d11a3cae4872db6fd104f1cdfcf6516e3b3548297e3b86795bf9
- da56e0abc288d01462844de42eeac4c7a14f76f09028ffb2d55909beace24504
- eafe26e115ca9bf982d3b579f7970e3ffa4307b9e9ab5794dd14f192941360c6
- ed5478099263686e19bf1fc7f5c169f84afb05ecc44008e3056d913e20edc6a6
Coverage

Screenshots of Detection
AMP
ThreatGrid