Today, Talos is publishing a glimpse into the most prevalent threats we've observed between August 10 and August 17. As with previous round-ups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
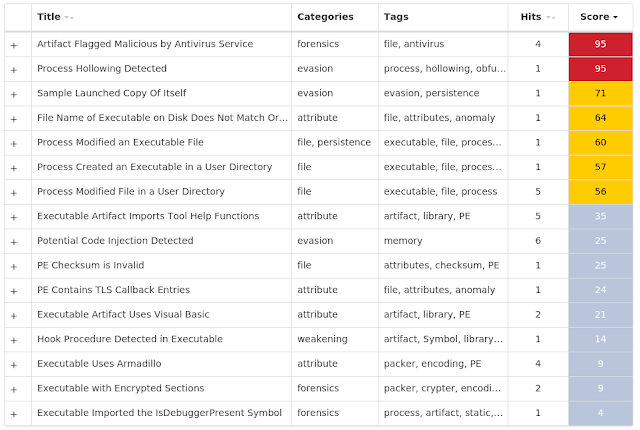
The most prevalent threats highlighted in this round up are:
- Win.Dropper.Tovkater-6646868-0
Dropper
This malware is able to download and upload files, inject malicious code, and install additional malware. - Win.Dropper.Ainslot-6646850-0
Dropper
Ainslot appears to be a dropper for PonyStealer, a bot that attempts to steal passwords from a plethora of applications on an infected device (web browsers, email clients, instant messaging applications, and many others). Also, once on an infected machine, it attempts to spread itself to other computers on the network. - Win.Dropper.Shakblades-6646807-0
Dropper
Shakblades appears to be another dropper for PonyStealer, a bot that attempts to steal passwords from web browsers, email clients, instant messaging applications, and other applications. - Win.Dropper.Cerber-6646769-0
Dropper
Cerber is a ransomware variant which encrypts a user's personal data such as office documents, pictures, and music. Cerber also attempts to exfiltrate browser history. - Win.Dropper.Bublik-6646706-0
Dropper
Bublik appears to be a dropper that in this outbreak is used to drop CoinMiner, a cryptojacking virus that aims to use the computing resources of the infected machine to mine cryptocurrency. - Win.Dropper.Zbot-6646698-0
Dropper
Zbot (AKA Zeus bot) is info stealing malware targeting users banking credentials. You can read more on our blog https://talosintelligence.com/zeus_trojan.
Threats
Win.Dropper.Tovkater-6646868-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: UNCAsIntranet Mutexes
- N/A IP Addresses
- 185[.]80[.]54[.]18
- 5[.]149[.]255[.]178 Domain Names
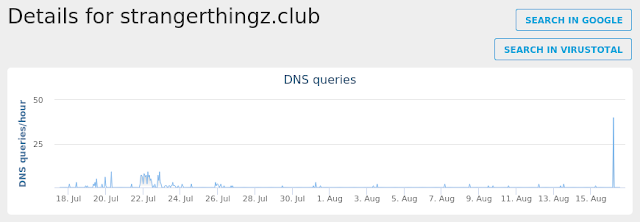
- strangerthingz[.]club
- chubbyoasis[.]top Files and or directories created
- %LocalAppData%\Temp\nso9D20.tmp
- %LocalAppData%\Temp\nst9D40.tmp\INetC.dll
- %LocalAppData%\Temp\nst9D40.tmp\crub.exe
- %LocalAppData%\Temp\nst9D40.tmp\nsJSON.dll
- %LocalAppData%\Temp\nst9D40.tmp\boima765.exe File Hashes
- 122715db6467d64ff21864afc1d5e15f5780ed05dafda8085fad323ca5dd02f2
- 13de4d085dfb857c5580425dcc787ee73b4dd78d0272e8a72d25915b6dedf9bd
- 27dd184fb1b5505f6bc76c72395a50070c7b594963ad591b265cec17a3b4a6ca
- 2a6753ea1a7a2289589550672980137480eadfc3c5d2a4135cbe152a72817b00
- 2c72964b8a701a9aa90f6cc46adbf5da695f990f707e48fe62b5de48c4ea51ed
- 359c2d5d7ebb5b6805c91951d0eb557027e6524795e144625eec951981199b0b
- 44822b0f38e0a15c2128bc1c58afeccf45916539bede62501117e8ce106b95ce
- 575fb1eca107f6999105302e60ae24992c335260c8761c9cdf676a3ca56bf389
- 5c0a9f3375eff3b50d58092e17c2c9b464cbabbbb531b77069dbdcce59d6e05e
- 63aecefbe9adc433f873e5ead9b846e3bc7aa35997594194b1fe3174ec42b84d
- 66f336a2616a16d8891503dd145fb12835497a13f19a65946d6aa68242cc23ae
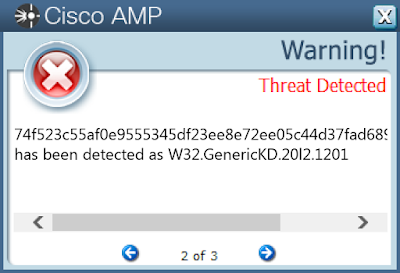
- 74f523c55af0e9555345df23ee8e72ee05c44d37fad68950732c033b27aab0e2
- 8ba4e8b2677e8bff0e3d527fffa0540b5a7ce4eb8dad4667f9426b9b224fab19
- 9362f6da347323c27790bf53e2423299962a42ba11baec0a9efca344277ae027
- 9db3546b5f6f8d60b1f635d07a10e8fc11e3b72f66161ee8621d29829fcbffbe
- a1e41d046f3a8386c3115edc57a16c4da82d9607b35d7a635b1c14f1d94d2242
- a70f8fd943406144850ce26d3a6103c32200dabd95563a2040d73ecf1b37ef2b
- a7de2542cfb82d489531efc49f65fbc31b1808f2353c7f20b781a66c727a50f6
- b760a4cea26c261519ed2a3a0814ae8e56ea10414e10213980e7eb34509fe571
- d265dcde9fe14ca5524b4fdce20bcf31ff5a010376cb174df5c3a4ce819ef82d
- da88d9c7c8010ea49472872d29c9c2d542a82a1f41e5726529dbdc34c363b6a3
- dc265fc791815328bb9df123c19bced472b4d5621f9331ab679b710fb0da608e
- ebb6267a01b66d6741497c9d780da069d6a7d3f17d2bfe287470da5ecee3975d
- eedfbfa60755288a140b84ee00957c0032baba0bf299cea18d5fcca85e7d41f5
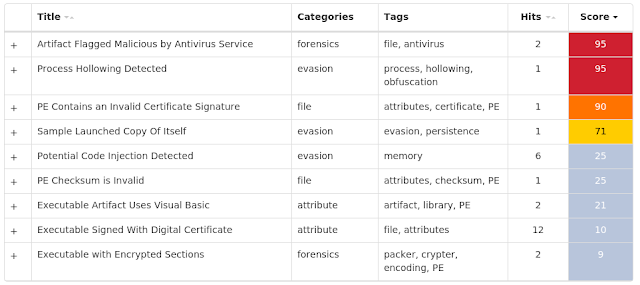
Coverage
Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Dropper.Ainslot-6646850-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Windows\Currentversion\Run
- <HKCU>\Software\VB and VBA Program Settings\SrvID\ID
- <HKCU>\Software\VB and VBA Program Settings\INSTALL\DATE
- <HKLM>\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
- <HKLM>\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
- Value Name: DoNotAllowExceptions Mutexes
- 944S06VZFP IP Addresses
- 94[.]73[.]22[.]65 Domain Names
- facebookwanker[.]no-ip[.]biz
- 5facebookwanker[.]no-ip[.]biz
- 4facebookwanker[.]no-ip[.]biz
- 7facebookwanker[.]no-ip[.]biz
- 1facebookwanker[.]no-ip[.]biz
- 2facebookwanker[.]no-ip[.]biz
- 6facebookwanker[.]no-ip[.]biz
- 9facebookwanker[.]no-ip[.]biz
- 8facebookwanker[.]no-ip[.]biz
- 3facebookwanker[.]no-ip[.]biz Files and or directories created
- %LocalAppData%\Temp\MQVCD.bat
- %LocalAppData%\Temp\MQVCD.txt
- %AppData%\winlogonr\winlogonr.exe
- %AppData%\Bot.exe
- %AppData%\Wow Logs File Hashes
- 05dd67a86f9b9d5afe4c069798350d8114784f25199777bf459fbd244e600200
- 0cc20f105cf4630239cbb192b5085c5323ccddafe2804420d07bdc84e9f69f74
- 18778b49fc35aec08184cd4426dc698bd7b89a47dce15861bb9fa4384641d6c9
- 5908a9ebe9fc15e751f7ef39c2479413a96f6086899927d23ea7faa83b521fca
- 5c4cd71d85e9fc4dabd709b64691acec25c9fba77b3ed6bbee63fc454ed77883
- 637967a9e3b007d0007035df3344060ac332aed97f5b4a170a1fcfc5e1438672
- 72967919bec8028198f4a79997dcd957a6d6c0a9dfb7dbe5b2ca29a00debb41f
- 7659c69ab75e087038e59f6e60a2d7927503c390b212787342b4ba53e6f72fe8
- 7b8fd7667a87cf87691feb2727ed78f832e8b84f4edb123057ac21fc173bdfcf
- b411c969228d3324eae00e9468a05bf37ecef76fb81e41620dfc9d19bd067f47
- d20f23c05b7781d2e5866336693f81041b8b20ab7135812a495d5f8dfb1e5ac5
- d333daefccd7d188cffda7c75d589389140f24bfab759368217f2514ded312da
- db3ff8db6b2387a8b4be629c96f4de36288a8945e6b0910ff9823ecaef92d96d
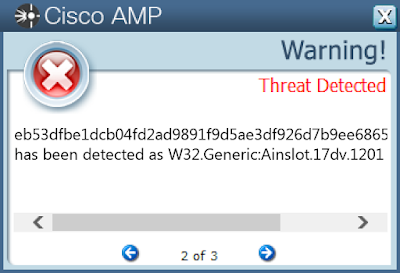
- eb53dfbe1dcb04fd2ad9891f9d5ae3df926d7b9ee6865b06e040ca3ed91019e7
- ec72aff9d0f5d5e8735589b554e2659ef8cb1f462057415f8c6219a1ae1b90a9
- f7c8bec61762fa31fb766f50144cfeecabea3aad4d12818b4ee8969777181f87
- f92ed6167aa17d2d242d5c0a15b63d5a2b2ab354ac0c9988d34dbe47d5138719
- fccbb20a19943cac05429361f6ffb51b494e02b86748761e5d26d4bdac3a7ab3
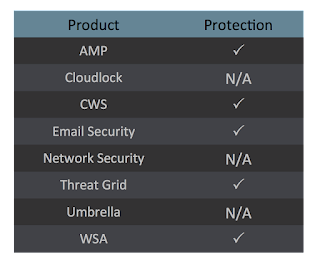
Coverage
Screenshots of Detection AMP
Win.Dropper.Shakblades-6646807-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- MSXLJHYHDS IP Addresses
- N/A Domain Names
- kreuz[.]hopto[.]org Files and or directories created
- %AppData%\1HVMD5254F.exe
- %AppData%\DAVID
- %AppData%\wrinlogfon\winlogfron.exe
- %LocalAppData%\Temp\HIDBE.bat
- %LocalAppData%\Temp\HIDBE.txt File Hashes
- 016c6537acdbef9cca85e500e9a9ab650c62cfe0e05cd37663cd3b5668864a9d
- 0c4170015c7a48b55416dc02fbd0a85d885547bedd2356898f5380c6fd7ab085
- 0d429037ed21d35c4fdded8e65ee9d6d0c548937c28369d838e2e1211222a83a
- 10b618f4c85c7a514f5c50bd46e68c413d4388f461c1966b1617f4c4ae22afbb
- 1ce376ab7dcfa447ba60f8904d137cd498a8d931097b0d06b53201993ad1011b
- 27b3826f6176760489fcaa575178076427de6d56db4c9050825e511647fc1cea
- 2c879e03a6e84026f9dd4e2606ed53896ac202c4a442d4cd558f5dd7758eb9be
- 2e7446954c517685771f6fb8ee3a6752c83d1705246f63291c3de596d509b3a8
- 356ec18e7dc92a42a958b046d77390e4427f8cfb9d7a8b380c8b31e1bac8b227
- 4f67dac4052c730e52f56e620c43ceb4b222e20a3ce40f2822f8e8bbd4fdbc5d
- 676920425645985a36c17bc77a80ee9b7d13d15a65ffa25663da28b78ed5d275
- 907f25a969725e7af3b8de2399314d89e09b6c47f39aaa9855362e69e11fff2f
- a00b05b4d45feaadaddf847ae826d8c0d2d11bf301ac60b2f1371bf6fed747a2
- a2a0ff0c895c2ee15787172fda8daec61e52423a61eb912726caad17fbad16b2
- a62256b872b872d532e918977dc5cfb86a33b1a547c63df0a0ab5a9cf3fcae80
- ab0d49a0a4753fec8440ea5d8a8840e1109fb87eedc57b6a411b0cf670f6fb3c
- b838fc5bc77d7fe32d47c5a462833254ce6707649191418670390d7cdb61e041
- c1abce71c3c7e5db2f246734317cbef66382b532faff075145f5dbf417fa4a69
- c737b0fd6f3ee58298a7080fe5033b66cb85387209c27e7eb69c0154b2efc5ef
- c8d7c48180f999411d4cc3c6fdf07a7f4c3e94a9371924789144e9225cfab613
- cde4c0a0c599c4310a717224db5f379c977f96b541f9e60fb0d7e3b3cabba206
- d52a70c87a7a813d46bdf712a852ecf082b920b22b86b981f51702bdc91f42d5
- d8383a3bbedd188751d368426527a848582c4c7b52f5985fc279da2130740ad7
- e202fee1655a34f268f29f2c2748742e155c10adbc7af56096dc0e7721352522
- e5fa827dc03d7f86c9a40f74c7446789fae1c1c719fde7401477b7a8b8a0e49f
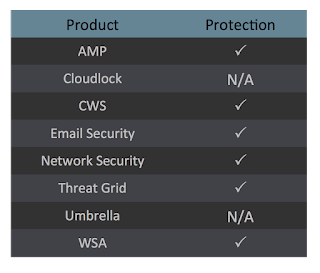
Coverage
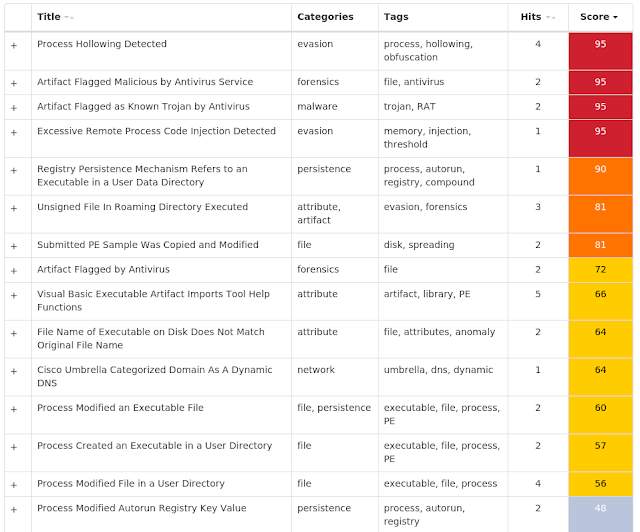
Screenshots of Detection AMP
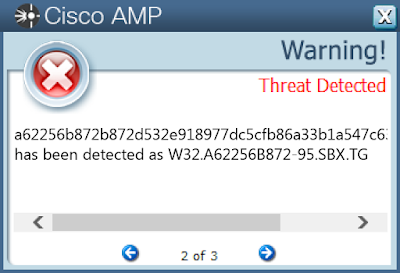
ThreatGrid
Win.Dropper.Cerber-6646769-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7
- shell.{381828AA-8B28-3374-1B67-35680555C5EF} IP Addresses
- 94[.]21[.]172[.]0/27
- 94[.]22[.]172[.]0/27
- 94[.]23[.]172[.]0/24
- 94[.]23[.]173[.]0/24
- 94[.]23[.]174[.]0/24
- 94[.]23[.]175[.]0/24 Domain Names
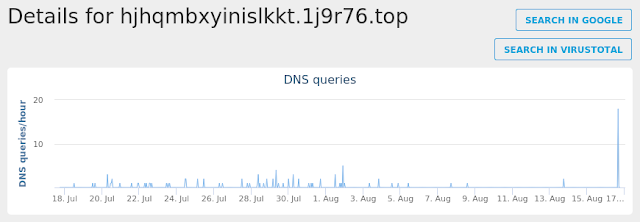
- p27dokhpz2n7nvgr[.]1j9r76[.]top
- hjhqmbxyinislkkt[.]1j9r76[.]top Files and or directories created
- %LocalAppData%\Temp\d19ab989
- %LocalAppData%\Temp\d19ab989\4710.tmp
- %LocalAppData%\Temp\d19ab989\a35f.tmp
- %LocalAppData%\microsoft\office\groove\system\_READ_THI$_FILE_Y3VYE_.txt
- %LocalAppData%\microsoft\office\groove\system\_READ_THI$_FILE_YPEAM_.hta
- %LocalAppData%\microsoft\onenote\14.0\onenoteofflinecache_files\f173a3a2-bd1a-460f-b78a-faf2a51f6d91.png
- %AppData%\microsoft\onenote\14.0\_READ_THI$_FILE_3SN82PK_.hta
- %AppData%\microsoft\onenote\14.0\_READ_THI$_FILE_WMTDNF_.txt
- %AppData%\microsoft\outlook\_READ_THI$_FILE_6GURWE_.txt
- %AppData%\microsoft\outlook\_READ_THI$_FILE_WJ3WX_.hta
- %UserProfile%\desktop\_READ_THI$_FILE_0H82B5G_.hta
- %UserProfile%\desktop\_READ_THI$_FILE_AU0XA34M_.txt
- %UserProfile%\documents\_READ_THI$_FILE_8F6J2D_.txt
- %UserProfile%\documents\_READ_THI$_FILE_E96X_.hta
- %UserProfile%\documents\onenote notebooks\notes\_READ_THI$_FILE_BUSBRQ4_.hta
- %UserProfile%\documents\onenote notebooks\notes\_READ_THI$_FILE_C8LD5O_.txt
- %UserProfile%\documents\onenote notebooks\personal\_READ_THI$_FILE_BMFXHU_.txt
- %UserProfile%\documents\onenote notebooks\personal\_READ_THI$_FILE_OCWSSKQ_.hta
- %UserProfile%\documents\outlook files\_READ_THI$_FILE_A5RM_.txt
- %UserProfile%\documents\outlook files\_READ_THI$_FILE_LT8MXL_.htaFile Hashes
- 01ccc0ce21b27ef9f5c3971ebf16704a52566732c504aae14955bcea007c1360
- 31a011aa4c6a4577319aeaebe9bc63d8571740fbab18455129da760501006f3a
- 3897f90f821df8386201a1d14aa1d5d6de338a64f5c6cf51da3c96931fb787d8
- 48f69ba14e9d3b4762d853419928f39a7a70cd48e8bb56b716ceb957e23cd3a6
- 4d51bf97c73d48dd9304575bbd3494c33dcf3c85d53aed0f4f901fe96895d810
- 53f20f30c24cf8942eb192524454f61f068ee83aa5bb02b7a89f16f3e70a8b5f
- 57a13d2976e4e6a9394a90f5da3bdb42714fb0cab74d43b860fb0e80c3208d97
- 5f492095de7265801ba48b55ca6741b74968f1a96b18e3704274001c9e6c8f04
- 5f58f99bbfa81bdff6d2e73220a714b1efdc90ecb48a392b5f2d8206724832ef
- 614b7efd98f2d075340628671dbb67048279669bb835e2b61c3a31af9d18ca00
- 6e928eafd030a58fa9ac593653d05d743e99b7bb97b5b9141a019d028378b72a
- 7127c13fd230b22bec5bf65d5e4663009b7e22d59fcb29ed74ff8c069ca6e6c2
- 756db69df59743a929b996fe3e5052e0842b07f5cac8b44e78ad0ec3b167707b
- 839786a3b6ba6b684eb0f4750ed496b67a942f1f3ff1878dd0178fe77ce849ba
- 9e1588b5a752155f4343c8570231c2316dddabf0be40f4fb875f5b00f14f17ea
- a5a7ec4e789279b99184b11a1afc57d2c3d2e3cdde3dd09e0445bb362f3871d3
- b73e496aba15e6b803cc3ccf15bb6dddca12c620aae79044fe6ddfbb6a181540
- d052caefcf6257c84e81cb098313a22dbf87e52fe2311f3b42acb271154a858f
- dbf302b95d80c5d7071d082aab51318e313353df5c0ce3cff661259378b8d261
- e050ff33f3702c8498b67d3ff41c45755ad5c94e559bff7ef0ce447b2424bef1
- e15393009c141d5d79f9021efb836faace4533da414fb35731f1ea9097fa73db
- ee727012e1069ea62d388ace8e341e33a679295ad3eed5076372b64f7ea2015c
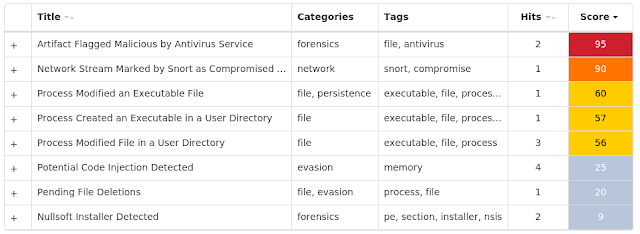
Coverage

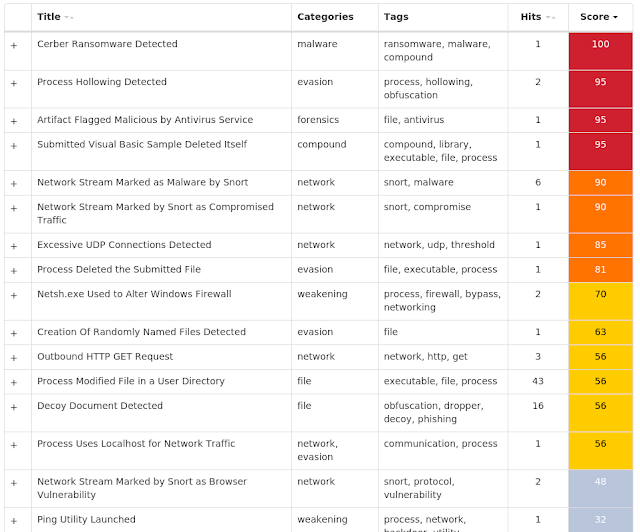
Screenshots of DetectionAMP
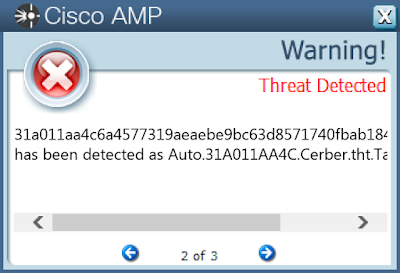
ThreatGrid
Umbrella
Win.Dropper.Bublik-6646706-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- DBWinMutex IP Addresses
- N/A Domain Names
- N/A Files and or directories created
- %AppData%\COIN-MINER.EXE
- %AppData%\COINUTIL.DLL
- %AppData%\MINER.DLL
- %AppData%\PHATK.PTX
- %AppData%\USFT_EXT.DLL
- \SystemRoot\AppPatch\sysmain.sdb File Hashes
- 01b6b22ab179d3718bb936f9bd71a33ab75ce980fbcb16a7aef10135204ceb1c
- 049a1fd2db0b1c3d821df7ac882417c951a8a3be6531a05bc284b2373bcd0566
- 0672fe319c7296a01b04973c0455c4a07691a16a2c933f15c071bba72b155b0c
- 1e2c6e7c4a4986a3d9b30fb8aecb4cbacacc103251c9ba35e14905231f104dda
- 30cf07a5ec3d0300ba8e7ce94ebdcde0a3c3539aede029cb39a353e7e26fcc7b
- 425e43eafe61586cd6a4867031f40c390ed4958ca35c2a8d368fb61f479a596b
- 489bede16e3b6142ba3bd19e7a151ff68a19e6fcc7cdaff4013a9f0753e62bbb
- 49ba74297aa04e0a4167e9c93c4c42a2db7b8019d4cc2cef4e7cd1908d133d31
- 520e488e3f6cbebd0369e024a852cb340920806d40a03e7cc3dfeb7b1502ccce
- 58f94794c8deb918c75d14db29ec2858e7289a0dde7bc1adc8e2f889d50acddc
- 5a4984a7a98b0fc04b3540d637daa744d0b597174408ce72cb685bf0e2f47710
- 632a3d98fc2b2c1e2b7c733f0e1bc87b9c55b8dce9308f23a459d2d68cb26da2
- 65e7cea81c182922f11360de35f4102b81baaff17ab6fa98125e9397fb867817
- 6e693ce84c1d99035b703791b5bd8708a4ba6510f334907f82fe3d6e674e052d
- 71e3922788784923e9648eb00b51700ca16752fa0fb41a0e50e98bafd1611f09
- 73f2be7461e84cc88415bbe44340a09e02d6bd3dbc396c708b5282da3e589064
- 79653c2fffae7dac30fb798f011c7b96c348a9b1aad37f2a3ef54d29e03e33d0
- 804e649a4ec4c60b27ccf828188322b42552e416e84f810177f856c514ca6d60
- 8a82e6490ddd36681e95e2e1079229fe07831279c3c4ec96cb159fb176f276fe
- 8c6b650941754525d9d0bec9356940af5860fefcc335507a82742e91c1c182db
- 9b1131872b4d42f9a5540fdcfe06eaa6591ae216eca749f4a98e5fefdc9f5fd4
- 9b5e56c14b1b66d3da0f2535a83b3498c7fb2e41d44b68f3474eaf6921afbbb7
- 9f4b64e4d8ac9c139f226c7ee53f86ba7285aeaf83818c0c5408c4814a8daf77
- a42ce1c1929e461d7f695a3790d4021286f03ed8a011013282400c5368ca2965
- b1dc3244cf44aa70d30fa06f7367c90240638c0f0f98ac419dd603b101c10eac
Coverage

Screenshots of Detection AMP
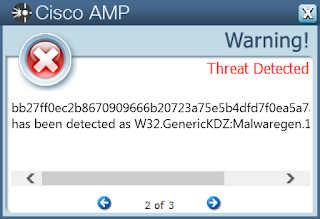
ThreatGrid
Win.Dropper.Zbot-6646698-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections
- <HKCU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\
- <HKCU>\SOFTWARE\MICROSOFT\Exeboz
- <HKCU>\Software\Microsoft\Windows\Currentversion\Run Mutexes
- Global\Instance0: ESENT Performance Data Schema Version 85
- Local\Identity CRL v1 File Access
- Local\MSIdent Logon
- Local\microsoft_thor_folder_notifyinfo_mutex
- Global\{2514E002-3297-704B-6F6E-B811A843C5E5}
- Global\{2514E002-3297-704B-7365-B811B448C5E5}
- Global\{2514E002-3297-704B-776C-B811B041C5E5}
- Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7 IP Addresses
- N/A Domain Names
- blessedgroup[.]biz Files and or directories created
- %LocalAppData%\Temp\ppcrlui_248_2
- %LocalAppData%\Temp\ppcrlui_248_2.ui
- %LocalAppData%\Temp\tmp5a3b8626.bat
- %LocalAppData%\Temp\tmpb0cd0744.bat
- %AppData%\Coviwys\mehotie.exe
- %AppData%\Uwgav\ymyrus.kuq File Hashes
- 00987def616457475aac07bba673d78c8bef8f84a4062320afe37486353c5e5f
- 0165b6625c320d2af053f6ff1b529fc2579eaaec575b3868fb23a6c8ab8c8799
- 0295ba8a376efa16ea7183a23cc5cf652b2ea39ea8f89e0835d926d68a42f5cb
- 02a7a8e854a02aac1b6db03a4951587e1516838674e6259f595d9d7dabb9df51
- 02b3e32d1631794411c090d5acaf95a2d7aa7e9c6dd07c221894610ad24c6110
- 038004cf5ba6490879f516dcc3574d2e283bd617cfa78cbe71883c6015ff1e72
- 04a00b5e202eeddeaf642be882fb803044dbfc20c241d6bb5900164daa45377a
- 05956361e1a11da5ebb290f27e493959870d9b93cd58df1156f90d17e24f1b76
- 07230d5a078c77c5f722ca323d738b437d5b038aa966b4078c332228bc8d13eb
- 0a5dbd0ec79d4d713760e7108a856e4325c7046ad183ebcfab674b129b661378
- 0aad831be57fac0cc9a3d5ec8aec0cebac077b0ef8fa3120af392ddef1b659fc
- 0d4bef2706a84bf9f123b40e3f582fa6dcc52eecab81e9e5f4e646a5cfe844da
- 0d6be142355a17c5231f292278a0e68ab1dab8d150e697261b9f26938bc82f54
- 0fbe2e9f72532608295e24cdf23d7aad1b1112a566099099f4d5120bb8821637
- 14bbd281ac544bae80c3349167c29adfa821734d064532bdadc8146a5818ddc7
- 15a35d117cbdb6b02c152a0a40136846ae2e49d98aab039a53396054858b659b
- 16dbf776fa3fad4a630e5fed8c73819ba2a5316305463975c26f8cb06aace207
- 1725beb1344e48940ab5668e04cfa6e713acfe6384d11f4cc4539f2fd771019a
- 19190ecd3ec953b37bdce918ca4c82791f70bdb6f7be3d2aeaa4e3c134cdecf4
- 1adea3431604c725da1c887c0622c8d8f69fe5658682b2f002ac024d0d34e759
- 1b6e18cc6a94f26e3ad362a03f4fa61a6085c90b0a3945dc56115a7a45a65ca1
- 1d30657d8443af8f5a1d914d109b3d7ee5042d55df0e395b1418ea86647fc818
- 200fc49b5f8541fb16e82a4d5d53d14abd8612a8e5212dbdd06d509c9df3bef2
- 229776dbe35f9e7845d0ca164d0b3d54462d4cdd8e0fe365cb032ef7fe43cea5
- 248cedb88ee7bdd359f952b3dac1f93dab607a33b8b4d0dcb4c9e1c09e317e43
Coverage

Screenshots of DetectionAMP
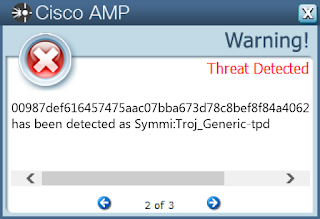
ThreatGrid