Today, Talos is is publishing a glimpse into the most prevalent threats we've observed between Oct. 19 and Oct. 26. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
You can find an additional JSON file here that includes the IOCs in this post, as well as all hashes associated with the cluster. That list is limited to 25 hashes in this blog post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
- Win.Virus.Sality-6727001-0
Virus
Sality is a file infector that establishes a peer-to-peer botnet. Although it's been prevalent for more than a decade, we continue to see new samples that require marginal attention in order to remain consistent with detection. Once a Sality client bypasses perimeter security, its goal is to execute a downloader component capable of executing additional malware. - Win.Malware.Nymaim-6726894-0
Malware
Nymaim is malware that can be used to deliver ransomware and other malicious payloads. It uses a domain generation algorithm to generate potential command and control (C2) domains to connect to additional payloads. - Win.Malware.Xcnfe-6725509-0
Malware
This cluster provides generic detection for the Dridex banking trojan that's downloaded onto a target's machine. - Doc.Dropper.Stratos-6724145-0
Dropper
This is an obfuscated Microsoft Office macro downloader that attempts to download a malicious payload executable. The sample was unable to download the next stage, so no further analysis is available. - Win.Downloader.Upatre-6726679-0
Downloader
Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware. - Win.Malware.Cerber-6725830-0
Malware
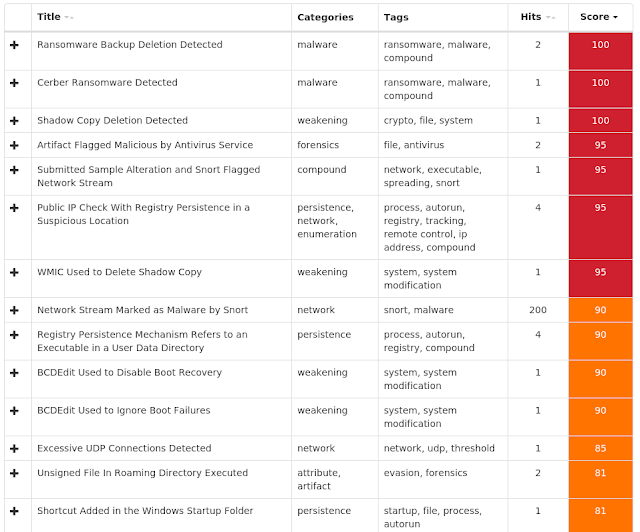
Cerber is ransomware that encrypts documents, photos, databases and other important files using the file extension ".cerber." - Doc.Malware.00536d-6731394-0
Malware
Doc.Malware.00536d-6731394-0 is a malicious Word document that drops malware. It attempts to download and run a second-stage executable from a number of known malicious domains and IP addresses.
Threats
Win.Virus.Sality-6727001-0
Indicators of Compromise
Registry Keys
- N/AMutexes
- uxJLpe1m
- \BaseNamedObjects\uxJLpe1m IP Addresses contacted by malware. Does not indicate maliciousness
- 206[.]189[.]61[.]126
- 195[.]38[.]137[.]100
- 213[.]202[.]229[.]103
- 217[.]74[.]65[.]23
- 199[.]59[.]242[.]151 Domain Names contacted by malware. Does not indicate maliciousness
- dewpoint-eg[.]com
- suewyllie[.]com
- 724hizmetgrup[.]com
- www[.]ceylanogullari[.]com
- cevatpasa[.]com Files and or directories created
- %SystemDrive%\autorun.inf
- %System16%.ini
- %LocalAppData%\Temp\ose00000.exe
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@dewpoint-eg[1].txt
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@dewpoint-eg[2].txt
- %SystemDrive%\Documents and Settings\Administrator\Cookies\administrator@www.ceylanogullari[1].txt
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kokfo.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\ogtfa.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\plkvrx.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\qwet.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\vfhqbt.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wdieh.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winauey.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winbmfbc.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winehogdk.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wineplbg.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winfeas.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wingwtgg.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winhsgjxg.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winiiff.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winlamr.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winmucoe.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winoyjfrn.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winqvpnb.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winskeoqt.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wintilmn.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winwlbet.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winwnwhq.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\winybmal.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\wooydt.exe
- %LocalAppData%\Temp\jlwdt.exe
- %LocalAppData%\Temp\ssink.exe
- %LocalAppData%\Temp\ukpvl.exe
- %LocalAppData%\Temp\winlobd.exe
- %LocalAppData%\Temp\winmjeu.exe
- %LocalAppData%\Temp\wintqpup.exe
- %AppData%\Microsoft\Windows\Cookies\XTNNC6UJ.txt
- %LocalAppData%\Temp\winlobd.exe
- \sgfdr.pif
- \vqwf.exe File Hashes
- 007474f524c04bcfef7bff656f7d673e22496caff0490a111596b5c1a60b61ef
- 0abf15a831537bd86b7e16ae5032a4813c6e9e9df4f1da7c074c4daa3672c3dd
- 0e82ae0199228f54e8308755024fa78e0a568f1423cec3cf21d9341a7c99dcb9
- 18a859dee990feefdcc6196052c1d2becba64fb43d07623e1e573b0f39e63095
- 18bce4611a9668a2660b0471459cd070361c85d71a4989c1bc967fe04bc54795
- 2642e382a6a216b518471ac182891b6973a4f4eb569ad4d13cb02b8a840d3f07
- 5b4c4e796a0e1c9344c3165af210d2b9edd2980de25bfec656bc918809b0be4c
- 689bdd8a91c2bfaa00de235933b38ca9477ea9aa2eaa880cba50235641376add
- 865e10fa2439380d7048a0ec2eebdef487f706239e464c47dadf930b22028b11
- 905e701032eaaa944ccb70d3db97a200d85befefe7faf99d525c9767e5c5d615
- a2ca43843f5c03adbdb03b91e4cafc162781d8c7e707c7bc161b03f4163218e2
- ad68745733f455935188c0100aaf057bf1d3454a24e0be0ffff262d2318f6265
- b535ea6cc31dd9f8a66fbbedb61ed021520ff74f5b42f815eb84022cfb3e4435
- c38b955f4a4eee3cca1c1bf1ae0f915f75080772c4ae597c2ed76649a056a5dc
- c40d8c58cc63dc606a9fa854f1774d7f17546170fdfc2679c3b8f6387fa4be6d
- c5fb97f7e577795bdc7a6076efca8f09e83bd4fb9e68c40916c6784040dbb485
- d0381f5c52b605b7b43c8b9dce2341b622ed2528df6bd65d527104f3fc1f2f16
- da77ddf6e01c4cb2694f055a5c69f48bf6546b6831f145297a5cfbb5f64c5563
- f001f25a35fb04298750c58f37ca4158085c454d784778f9a9c601d9bbbf6b40
- f0d47851346c738dd836fb6f43005a57305f04e078d07af3a6d84ee586dfdfc0
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
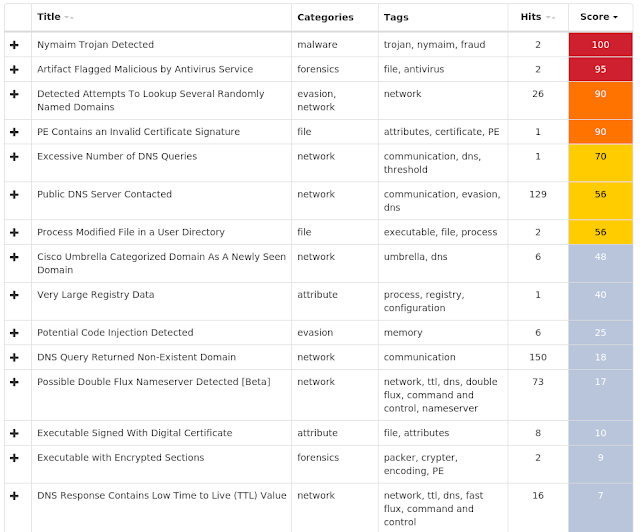
Win.Malware.Nymaim-6726894-0
Indicators of Compromise
Registry Keys
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value Name: LanguageList
- <HKCU>\Software\Microsoft\GOCFK
- <HKCU>\Software\Microsoft\KPQL Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- IOCXRQNM[.]COM
- ZJGGMKGGA[.]COM
- YEFHBEVI[.]PW
- DCORFRLWW[.]NET
- kercnnlwtg[.]in
- JYWVEW[.]PW
- ZQQSUQRPEJK[.]IN
- xhphblba[.]pw
- FSHAJK[.]COM
- maffuwnln[.]net
- RQMNLOKS[.]COM
- MRHNDJI[.]IN
- hbdfmtj[.]pw
- GZKISDVBZQFE[.]IN
- efntvrhq[.]net
- QGWKUGNMSJF[.]PW
- MAFFUWNLN[.]NET
- dcorfrlww[.]net
- NWAFZV[.]IN
- usrhd[.]com
- HBDFMTJ[.]PW
- fshajk[.]com
- QCNRQ[.]NET
- iocxrqnm[.]com
- firohrakais[.]in
- nizrjl[.]in
- vnouya[.]in
- EFNTVRHQ[.]NET
- zqqsuqrpejk[.]in
- srdhfsdiju[.]com
- gzkisdvbzqfe[.]in
- OHMAQTXG[.]IN
- jywvew[.]pw
- jpltxxpcojo[.]in
- MNEZKYAK[.]NET
- euqsvd[.]net
- jtcesxohkgm[.]net
- JPLTXXPCOJO[.]IN
- QMNMG[.]NET
- swvpzwktpdxs[.]net
- dzwuczn[.]net
- bsedcx[.]pw
- KERCNNLWTG[.]IN
- FIROHRAKAIS[.]IN
- myxnowb[.]com
- jhfahntxtnus[.]in
- JTCESXOHKGM[.]NET
- XHPHBLBA[.]PW
- zjggmkgga[.]com
- iknvjbze[.]in
- QGMBJF[.]IN
- EUQSVD[.]NET
- NIZRJL[.]IN
- rwxryhij[.]net
- qmnmg[.]net
- nwafzv[.]in
- USRHD[.]COM
- mrhndji[.]in
- IKNVJBZE[.]IN
- ohmaqtxg[.]in
- cprdqjxpp[.]net
- SRDHFSDIJU[.]COM
- yefhbevi[.]pw
- VNOUYA[.]IN
- LNTBF[.]COM
- DZWUCZN[.]NET
- cmmwoqknklxn[.]com
- rqmnloks[.]com
- mnezkyak[.]net
- BSEDCX[.]PW
- MYXNOWB[.]COM
- qgwkugnmsjf[.]pw
- RWXRYHIJ[.]NET
- qcnrq[.]net
- CPRDQJXPP[.]NET
- qgmbjf[.]in
- lntbf[.]com
- JHFAHNTXTNUS[.]IN Files and or directories created
- %AllUsersProfile%\ph
- %AllUsersProfile%\ph\eqdw.dbc
- %LocalAppData%\Temp\gocf.ksv
- %LocalAppData%\Temp\kpqlnn.iuy
- %AllUsersProfile%\ph\fktiipx.ftf
- %LocalAppData%\Temp\gocf.ksv File Hashes
- 00570d9bd558b25ac628d4de140897954e3cc1ed3dae8818e3ef580544626e8f
- 006e51c87642cb26a7d6fb534d37c1d4c4d015934e67284e8e35053b0da8971c
- 007b40dab88434b29a0c3b92cca04cb13d9f1ddb29202770a2f657becfc939d2
- 01e202a72e6bf3954e98acf6c4cd8fe660de710e129cd9de425e1e5dcc876232
- 01fc65a13f2f8f6033e55f860b835361442dfd0ec1443c134b2a6558964a2a2d
- 0340d472ea1bf41f75e1cf94fc499ca3960518d5dc9fe8cc85f6f56a955ad702
- 03d97452886804d0bc32e0723b4024d91cc1a64357a74b529452ca007f1b07d4
- 0491517063ca33e47b325ba2c304f4c8fc3b45956b1bfdff0555936a3bb3678f
- 064173410c2ca5781a785fccc9457fdd59b25ba2c14aca5bee71f83f136c279d
- 0679f7d954654a74c02dca0754cffacdce6d4c7887f4976c85b6148033b9942d
- 06f001ddf5d2c3827b6f28936b2939f16df62745699551a155572433827ec381
- 07814f096bd2a889317ac70e66cadfe443df1ad96ed2b6452d4252d11d60c8b3
- 088dce2464cfa134fd0317a2e75f0057de8d60b547d72e66fc1926e9ad355074
- 08b4430a48bdebc89092cb4f90ad407e51002098a0eeb08574f92a8327e5a140
- 09007a9eedbb6b7116add49671499f238301ccd3fa763904512517d003cd3625
- 0d42e7f0984ea9b0be200420bd7221a92c76466c85ded7321cb69a8386db17ff
- 0de3ad246b5c52c96135f5804ae1118f7df1af1c6f937740d598334214fc1943
- 0e5b9ae6ee3041d89eefb88c6c868a1c9931391e91068de26720008c6b0c0bf2
- 0f59a622eb9998369364b47ddae969698a7975b877ce025b1214ccff8b59e7a7
- 0f724bbd47c80a2feb1f376d282ed84f39306293522656241abbf19532154928
- 0fa66bd126cb02a367d8ad392b6c446cc8f50922930804526d245784be001c51
- 0fff0dad13446c46cd2ff79c4fcc6e545df3e6e269917892d3d22bcbdbb7b741
- 140aa25448483a45722b1c874fbed44f70e2dd8ea9fe9ce1fb479de397c8a95e
- 1532bc5fd39a7f0a35d9f94bcbf0be36d5f04acfb46829d4163b00abb3c5eb04
- 15c03875c741546f5eb5d843c7515b1b10201ad5f9495b2f1eb91de5473602f1
Coverage

Screenshots of Detection AMP
ThreatGrid
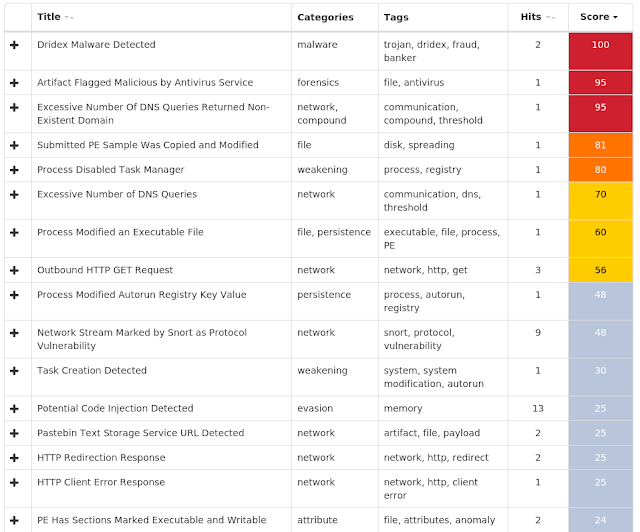
Win.Malware.Xcnfe-6725509-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- HOejWmqMur
- HPN518Ik4R
- Lat3nHFoEE
- OaLnVql4Xa
- RsyK1I3lWG
- V7BLDkG8tf
- XQeR5Zn1SJ
- hND27SW0LW
- qJkjChBhfG
- vXnp0AXNfH
- wDSifyYhV5
- wbQpF7mWCE
- wcX8yaYh6B
- wfwyjaJYsW
- wxK54uwMfc IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- www[.]brmbyczdra[.]com
- www[.]pn8mtahzna[.]com
- www[.]tqttwzog79[.]com
- www[.]ril14w0qvn[.]com
- www[.]mvbkhpmqux[.]com
- www[.]uyrhnkdozb[.]com
- www[.]nutatq5wla[.]com
- www[.]tpu9fiuayd[.]com
- www[.]5bc5xh1p5p[.]com
- www[.]we3jnll0va[.]com
- www[.]hrwzs9ake4[.]com
- www[.]knx3hbiwyu[.]com
- www[.]txovxotdxc[.]com
- www[.]ean1heykxa[.]com
- www[.]qjfvz6swvg[.]com
- www[.]stq1ji6cas[.]com
- www[.]xoiejztmpo[.]com
- www[.]cldhtlfyhs[.]com
- www[.]zhya3boggv[.]com
- www[.]qvchgu0aax[.]com
- www[.]brh6bbhql8[.]com
- www[.]dirmuszaet[.]com Files and or directories created
- %SystemDrive%\345791583.exe
- %SystemDrive%\old_345791583.exe (copy)
- %SystemDrive%\TEMP\55ddbadda5fe5c7f86a8f8ea7c9405413682686f8057e2b5369adee284e2ace2.exe
- \TEMP\old_55ddbadda5fe5c7f86a8f8ea7c9405413682686f8057e2b5369adee284e2ace2.exe File Hashes
- 0462beb83c7410501f0fe309335b63bdb2197c828d8b3cac860329613fb92f18
- 07f0c7d1726aa998261db29451ea668364bd226080caf6ebc1e7cd1f65de1864
- 0eddfc2b11eabf9cf0186363f4727270cdc5ed3619cf8318caaeaf7370da5e10
- 1748dd5f70ed569ec358f707587718e8a980871e076aa1b1f344f84b7eee0587
- 255c3d259351d43392c8b01db2a830f50515e0c2672f5421934ade0433cbd6c3
- 3ea74553c24024b94412137d0337f1b22226af398579bb7f44e674649c18b480
- 55ddbadda5fe5c7f86a8f8ea7c9405413682686f8057e2b5369adee284e2ace2
- 68b35209e61e6558069706af6cfda39cbe24366c28e68d36279ce314f922d9b4
- 6af842bca80ca04a5c65e6fa9fbf85a3c7bf34a49b580397cc5955a0b9aa1134
- 6c75d30fa43d15ca9f2632e6a794d26de4fc35fcc1ba9fc250afea06f27ad653
- 719e40a705ffe31bff643a5254f52ca051d0657b59ee920f4b3e75fc83e3fe0c
- 77b11d472658825617c8520bc75e5084fa3a26a85f90b845270615ddff6622f4
- 8689c50f5e4cd1fd590a9c5eebc28ba81b5f0a1b52e357811975ac0f59d278db
- 95e82e623d7f1b34725c1c11026f8149741a4c506379954c6c9d171791302df6
- 9a624de996ba6e99eb59b50b2631e86057feb3bee9c54d1282705c4486530fbf
- c556d0c97ae7b7be22f685e829394652401971a0e468eb0824b5ba5537928b96
- f392f2e34534ef1e74cb911124ebfb531dbd045e4b6e20afc30e878674459131
- ffc643e3c595c64053e50e0a1ccc2dace32134c3892fbb1a60e215410cdaf428
Coverage

Screenshots of Detection AMP
ThreatGrid
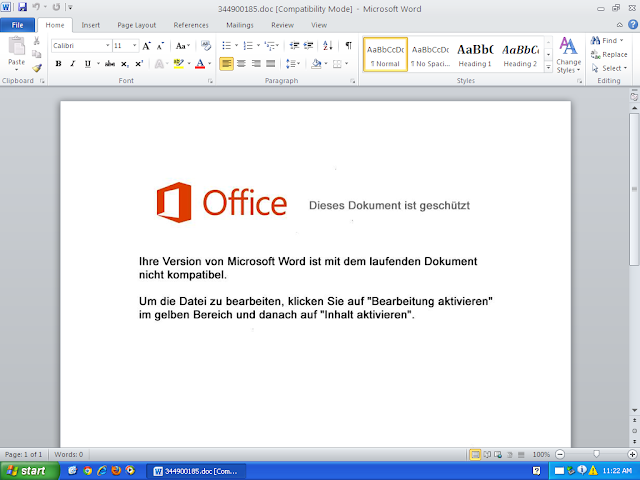
Doc.Dropper.Stratos-6724145-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 88[.]217[.]189[.]35 Domain Names contacted by malware. Does not indicate maliciousness
- www[.]kum[.]net Files and or directories created
- %UserProfile%\Documents\20181025
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\PowerShellTrace.format.ps1xml
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\QsheHY.exe (copy)
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\Registry.format.ps1xml
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\System.Management.Automation.dll-Help.xml
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\WSMan.format.ps1xml
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\about_execution_policies.help.txt
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\powershell.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\powershell.exe.mui
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\powershell_ise.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\powershell_ise.resources.dll
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\pspluginwkr.dll
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\pwrshsip.dll
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kdinwwrgg\ONSEXGA\types.ps1xml
- %TEMP%orary Internet Files\Content.Word\~WRS{68695D36-6967-4FDB-A2FF-84784E101F5C}.tmp
- %SystemDrive%\~$4900185.doc
- %LocalAppData%\Temp\kdinwwrgg\ONSEXGA\powershell.exe
- \TEMP\~$a24d5a55e3d33b0a4d183141758c409b639fcd077cfcd062dc53cb8d03d378.doc
- %LocalAppData%\Temp\onexzlc.exe
- %LocalAppData%\Temp\kdinwwrgg\ONSEXGA\QsheHY.exe
- %LocalAppData%\Temp\onexzlc.exe File Hashes
- 00d3e76c7614df1533cbb40d0b3977cfce6e5f01b8cc0aa6ea858891ef104715
- 16079ba3e75ebbc34e3ef692277332d41ee0d1aa248a24c7f5ba74d88f28d01b
- 1ded830b66a15ef7288f088b3b4b1a84fa55bf0700538953614f5e2369128fdc
- 217d2260555214d8e6e72dd5dd7ade95b206efebdd948ad05a1dd88e4e39730e
- 33a99f39eb8a1d9fe223b4ca61d21fe8086b2a908e00954959b971868424e46b
- 35a24d5a55e3d33b0a4d183141758c409b639fcd077cfcd062dc53cb8d03d378
- 3927bc5e8064ab1fedd6e0b9826aef4fda01e6be3b218b9b482d4ae60d929d67
- 402a1bd3bd18102d3955b0e5dcab8b76b8c1025fb828d410c1fa93a872a2f1f9
- 42c74a8a4e195017753e917153702bbd4d6812576cd94f0fc0035bed6aa1ce1f
- 42ff1fdd87f84e321a4348a5b113ba72634fade79646df750ec72f907d787db9
- 523de9a89e6d2f5713fcc4b7e3ea1d27fa27d13e5d17a0f08aab6d86d9e2a9b6
- 55953f034bc3edf5248b9c978916a2eb45bbf641892baffd7744ce0027cdaa2c
- 5ed8c51ce0a7706599d5f7bbe843fbdb8fed579591012146fb2fbd92bfece4f8
- 616d166cd0fc20ce5e583b9c0c306833fc4a371214bc9a3b5f9d33deac385c68
- 781c06eeafa87a7a27b573fde822faae4ac0ebd7a19ad7400ac8595e1a89fcaa
- 83245b8849c886659767d6227051ea8b48ead681cbe62c12a4557cf8c3a2b61d
- 934a7d7edf49198d685569e2f5e40e225f90e407a87478243379ef71d7f4f6c2
- 9653288c0ca91e1b968a39e2f8b2e7c7b5b881e064c0bf2d234ea0b0619911ce
- b15f383006ceff832ef575057a0a75cba726822864d37aef5feabc43ca316971
- b41b3a7b83f22af9892cc69801086343924d8ee23f5bf8062cc2748c9301f1a8
- c08ea9800cdb66012a4adfc3a5bba200f7f1db8cc37f50c133201f5ce46660c3
- d182a022ed754bb7c963540d0a8d9cd7579b458d4c2057d5f72caeb11566b2b9
- d3a40ec14f52e1e7e1494ee7e04ad651e38618e29284d3205ec21cef6e9699f2
- da9f374901e55c225f03ec68dadc672e13e9f0dc36508fe416cec8faf87795af
- e8c4870bb9d6e7cb597a86c97f2a64c71734aecbd9c72f7302b730dcdeffabe0
Coverage

Screenshots of Detection AMP
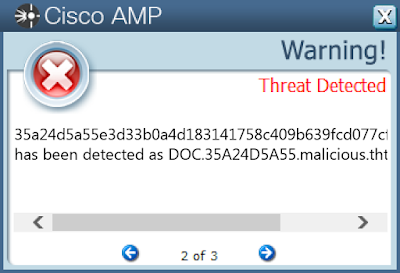
ThreatGrid
Umbrella
Malware
Win.Downloader.Upatre-6726679-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 83[.]136[.]254[.]57 Domain Names contacted by malware. Does not indicate maliciousness
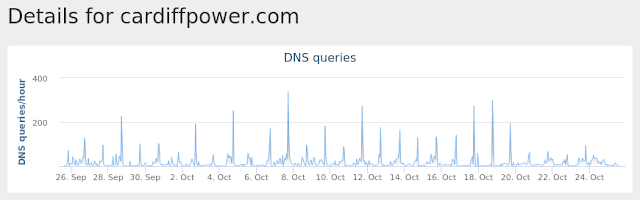
- cardiffpower[.]com Files and or directories created
- %LocalAppData%\Temp\kgfdfjdk.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kgfdfjdk.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\lrtsdnn.exe File Hashes
- 02c04966bbd775626d1738bf454148543e8cc4564ff9f1ba3110395f96b05ab9
- 031edbb534d9bf394bebf4cc7f64338d7212b05a7a7bf2a75f5348feaeabb9c5
- 11e046d9a88238806a7458c5f17dfec74c1038dcacb7a345f492f5d9b285255f
- 1273cdf1e5440ec05d61930132df0152be89eff4e28ac59de8e653022f664579
- 184e4171672a8eba20a357aabd274a454ed1c71a0aed1efbb028b9676c53ccd3
- 2556e8e75d5c1cb3f6fd2e716242c991dc9af8138561483993ce179c3d50e48b
- 2eb229efaa5a043263e6546583c811738d5695a8afbb035f3c76fe80929c18eb
- 32867f896bd20600c6712759889c031984e933ef1b0b4dfa9e061bfa0b6e994a
- 4b8d61f0af68f03e586773b1226e635df5f6b2a417c88131885aa4201ad96c6b
- 4caf12084718881f7d0fee2c4655b7afb8c27803f0c1bbeceb4c48a9532cb3c8
- 4e07e7190e98511ba11637eeff341227aaed60ca58e96bbd69fd5659f808b56c
- 6d8fabfefcb131b3535940fab547c10e5de430a079113671d2d09cf0c9582ed1
- 826a5879182924c1f00f72885583baddcb8cd3ce9596a5bdab44abeea5f02ab9
- 9c7e51d51513e337bba8b4fcb88264203986e387a8b9d820b9d6a0f2cfca26ef
- c71f83b153fb1e488930375d7a62eb77c34493f617b415447cd6b6e7cefb68e3
- f1a99a424971247e557d9f2d6c90e1e27f1c3407ced0913701f5f6bd40cdc4bb
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Win.Malware.Cerber-6725830-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- ip-api[.]com
- ipinfo[.]io
- freegeoip[.]net Files and or directories created
- %SystemDrive%\Temp\HncDownload\# DECRYPT MY FILES #.html
- %SystemDrive%\Temp\HncDownload\# DECRYPT MY FILES #.txt
- %SystemDrive%\Temp\HncDownload\# DECRYPT MY FILES #.url
- %SystemDrive%\Temp\HncDownload\# DECRYPT MY FILES #.vbs
- %SystemDrive%\Temp\HncDownload\Update.log
- %SystemDrive%\Temp\HncDownload\Rmp7-WGqEy.cerber (copy) File Hashes
- 0015a572f00b8ec6f68bb6a3683f7741a1a35d436c868ef545e016a279c7740d
- 00200aac1922a420afc4390974ad1f099bf86eb6294e757ab22004628f2be226
- 00528962871098906eb33d0422c1a9b7bdd0cbe481af1bc058d1c2a09793f055
- 01ef8b829770bea681075ea9b9ad648c5cf8c9db42aba719d921c6841d0ffa6f
- 04eb627d86eeff6c9314fac423f535d798ed95d3384df9e0944447af7898ab0a
- 05506752a964566bc3ec936db6da6e577bf3e1c04d2dadb1143cd137ff66e715
- 059eced85a1c189ec1eceb9cb642e801db20cc61d40782afd7fc479169e0a799
- 0655f2a8831b5aaece1fe2af39583c6261564a13fffec7354857ae440c824786
- 065c909c3c855be6646202eaaaad38e47c234be5927f8b635b9e9a0482c99965
- 06f20532a0285a7e01634e319a78db15d3eb08e39c72ee92412c161be3c87d33
- 072114ad12468fb6610c20c9912bd40b5e25e0183dab9edff8b93aff79cfa846
- 078d4a7287160344439bd701f2fbf027c76dbc85e2d9ae98a586d69ebdca712f
- 07bbda40f1bfd84bc619fdaa05ac029251d919b8bd100f724905400fb107beb7
- 07d09bac351855dd383ed882657241b3db150d1a24019af08233b1b73795cdb6
- 081f9d0b1bd3ea8e7b69d0ff6c93c27e9e76c29124cdb539141a439bdb2bf8ab
- 08b4cd3370515fe4936d3126b12c738b2acd704ce24830119b1d69faef6c7291
- 08c0234c26c9b8576d428b2fc177ca4e9140ddfae8c213369a86bb4ae2fc4b06
- 097db35097f7ef2d8b91a517980e399c92e9938208110846561581d2bf5bb96f
- 09abc80ec4c160755e133f356e909219b2939f78ebb7896973094c78de55f42b
- 0b07fbacc4450198d6f430bff653791c43417af9e6d11f46b6ac75711e89c2a1
- 0b4123bc026cc6ac0282295c5d7bd9271514cdc771c9a84e359f3ee5858bf811
- 0b62139f8be2e7640c17e4c6ddc5c4c7812fd061480ea112718ac5e12ea70838
- 0bf510cbc1ee26748f285b6dd9f5e8d96b26ba5d732e6f9b1ad4e6b1695292ed
- 0c90601d82e2725a11bba65b9eb98c2154d6e2b27aa813936e75e7f740128971
- 0cdc982e7c0fe5c5d9100ff621c424af79ec3dd49e718a454af3a14f9add4c54
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Doc.Malware.00536d-6731394-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Local\WinSpl64To32Mutex_e162_0_3000
- Local\MSIMGSIZECacheMutex
- Local\VERMGMTBlockListFileMutex
- Local\URLBLOCK_DOWNLOAD_MUTEX
- Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1860
- Local\URLBLOCK_HASHFILESWITCH_MUTEX
- Local\URLBLOCK_FILEMAPSWITCH_MUTEX_576
- Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1224
- Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1560 IP Addresses contacted by malware. Does not indicate maliciousness
- 204[.]79[.]197[.]200
- 144[.]217[.]0[.]194
- 54[.]39[.]74[.]124
- 8[.]208[.]9[.]98 Domain Names contacted by malware. Does not indicate maliciousness
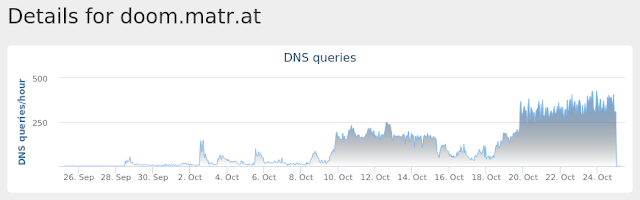
- tt[.]zicino[.]at
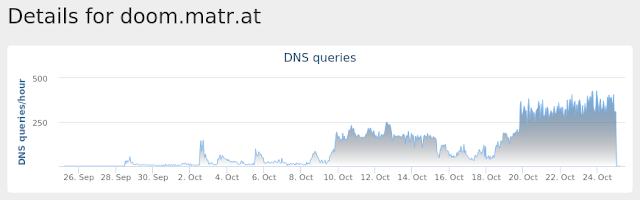
- doom[.]matr[.]at
- ovellonist[.]com
- ut[.]ritpur[.]at
- app[.]xenope[.]at
- u2[.]tip5top[.]atFiles and or directories created
- %LocalAppData%\Temp\~DFA1AFEB97E8C0B1FD.TMP
- %LocalAppData%\Temp\~DFFFF0E8FCA29DD7E1.TMP
- %AppData%\20938.exe
- %AppData%\Microsoft\Office\Recent\346748415.doc.LNK
- %LocalAppData%\Temp\n3j5vfst.vvc.psm1
- %AppData%\99fc8a68.exe
- %LocalAppData%\Temp\1fxpdoag.uzv.ps1 File Hashes
- 4e6c2a6715fd91a76a06321eebd22430fa47e1a298a12e6d5134327e62215c07
- 57b3f97cf7f8d8bfc4aef53f82cc1b1e154d7fcad2302048192e44afd47cf07b
- 6ca1773b14b136dd7b3e7906f73d0d05f21d00e1f829303ac9167454f1b22bee
- 7ca67da6488d5e5acf74919348ebfe4a780a7f70cc3b49455d0f588a2150ad8e
- 88fe8fc07008bdbd6a87f96184cc3ced3e2df8a1678d7d145ef6affb62683cbb
- a3c3656b7c7471d26a98acc02233ef906cb3bc20f4225c81fd3ff07111498ce5
- a72f70f2b0ea6638b3da69ed3807059ec98bc258deeb17fe3fdfa392b3c606a8
- c9aade2865566b50d1827c45b070f32c1db891101ed4783fcb471f43fa043958
- ca9b78bb32da00431081f4385ac85ee341e7e668aa934dbea8f5ab44b9621179
- ce31ffafe8ea619a703e04f7b16559999530f89ddb8fc78545bcee8f4e3c45ec
- f6feed4b063c2e25fdaf7af79954d78fbd6db361916f512a8e73f6665f8fb3e4
Coverage

Screenshots of Detection AMP
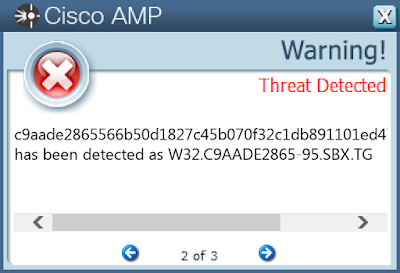
ThreatGrid
Umbrella