Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 11 and Jan. 18. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
You can find an additional JSON file here that includes the IOCs in this post, as well as all hashes associated with the cluster. That list is limited to 25 hashes in this blog post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
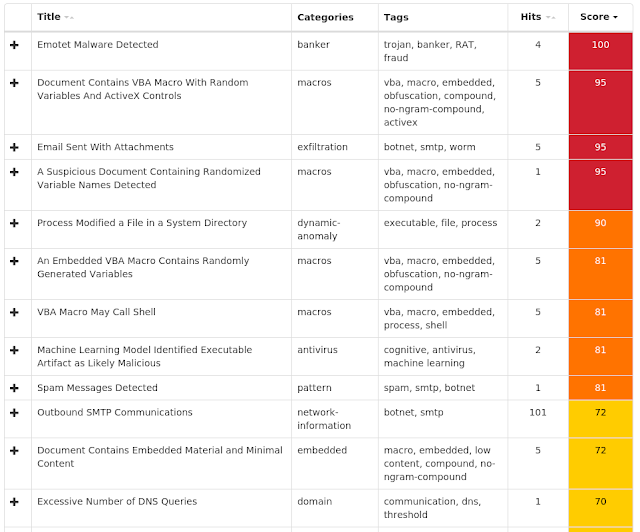
The most prevalent threats highlighted in this roundup are:
- Win.Malware.Emotet-6816461-0
Malware
Emotet is a banking trojan that remains relevant due to its ability to evolve and bypass antivirus products. It is commonly spread via malicious email attachments and links. - Doc.Malware.Powload-6815340-0
Malware
Powload is a malicious document that uses PowerShell to download malware. This campaign is currently distributing the Emotet malware. - Win.Downloader.Upatre-6815606-0
Downloader
Upatre is a trojan that is often delivered through spam emails with malicious attachments or links. It is known to be a downloader and installer for other malware. - Doc.Malware.Sagent-6813871-0
Malware
Sagent launches PowerShell through macros in Microsoft Office documents. The PowerShell then downloads unwanted software from remote websites. - Win.Virus.Sality-6814419-0
Virus
Sality is a file infector that establishes a peer-to-peer botnet. Although it's been prevalent for more than a decade, we continue to see new samples that require marginal attention in order to remain consistent with detection. Once a Sality client bypasses perimeter security, its goal is to execute a downloader component capable of executing additional malware. - Win.Packed.Johnnie-6814043-0
Packed
Johnnie, also known as Mikey, is a malware family that focuses on persistence and is known for its plugin architecture. - Win.Downloader.Powershell-6810733-0
Downloader
This cluster came with spam emails containing zipped JavaScript attachments. Once the user runs the file, these malicious JavaScript attachments use PowerShell and BITSAdmin to download and install the Gandcrab ransomware.
Threats
Win.Malware.Emotet-6816461-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: ErrorControl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: ImagePath
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: WOW64
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: Description
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: ErrorControl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: ImagePath
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: WOW64
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\STARTEDTURNED
- Value Name: Description Mutexes
- Global\I98B68E3C
- Global\M98B68E3C IP Addresses contacted by malware. Does not indicate maliciousness
- 187[.]207[.]58[.]148
- 187[.]178[.]233[.]96 Domain Names contacted by malware. Does not indicate maliciousness
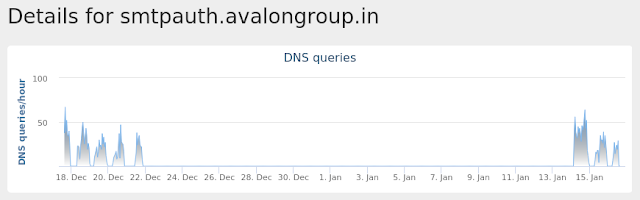
- smtpauth[.]avalongroup[.]in
- smtp[.]weiler-elektro[.]de
- mail[.]yomarbodycolor[.]com[.]mx
- mail[.]theconcordhotels[.]com
- mail[.]migranjita[.]com[.]mx Files and or directories created
- %WinDir%\SysWOW64\t5lKUp7.exe
- %WinDir%\SysWOW64\ohFmRm3hO8ae.exe
- %WinDir%\SysWOW64\XyDDS09O1vT.exe
- %WinDir%\SysWOW64\ouFc.exe File Hashes
- 0353c9149b5f88a330904bb62b32224f04ba58f03d68dd0792757ad775308b55
- 04353446c29fd35b28ee9b67f8bd44979478501cca7c954753a79c52b68d9037
- 04c3f1590c9e9389582e21d7711379cab42d460433a2918bb888ce941bcfeedd
- 0753b4ea09e7c562abacd4d3fbb6ceb8065075fa7e9ac3d53a7d7b9464111d97
- 07a40319b4eab80ad4bc5ddd1d326b380fbd84cb5695436ad973026f10b2ffcf
- 09dfb7b98eb9d84194c786107af24f345ba98abce2264eb350aaa49ec5f0b2a3
- 0a05e728e40d80db4159ced8760ade6cc66cd1d1c3187bc389801f975ea356a5
- 0b664accc6898a9c073ca27deb58abaa597477d88c54559439f9a92a45f8d055
- 0e0838d60693a9fe803d104f97b1513781460a3e0eeedc0add12d9cab9d57b89
- 0e5731849a5274705251a772b9cfc527d4646e5af1d0d8a9c0dc536d3a60ef73
- 11c6c26f9d485fa833fc457cc51a99e9b772c36816fc6c3bd55d3cd10b3722be
- 16d620b02bdf396a3992dc4b2ef8d2508924303e4c013e1fbb49921470008516
- 17061a6389a454eb7b2891b19708d0a2b54a6c4b4ce5fb20070475e0eec94202
- 19b0b0087b81e9c2c6b5c94a7830fcb2674318a32eb7b7f22beac0c21f7afe6e
- 1cea1c276ebbfb7016b71f5c4060ebda6771c82f8a7f7b1de17469f564cdd4ec
- 1fb31fd9d68cdf3e7003c8312920f47279c35d5e6a57072274c347abfa72546f
- 2304f4a6d495ffbe53edf321320c3d9c370f2ed04881481219e54b76877df66f
- 296f421a8f830c9b249dda7b08603ef70b9940165b22c323c81ac63f026e3b14
- 2b9278f08544327a17740022286878835f952b3e419f6eb591d266af5fe9d95e
- 2e26453cbe70950db2ff2866374eb65199158432518df90130d616d2fa0dc0d1
- 32a25295271b2091b10533f3beb8f9b032ef32668f3081c9f1c44e8e6017f325
- 3388ba07c6f77b926395f7638848aae558ea5804e09c82e441e03530e7c69d63
- 33906f0abea0b36325a9fae790527fd5317485426c70801600e129795af7f0f9
- 350f42856e87c939fbc0a994c5ee8df09e056c449931320e7a2ed633b62e7f2e
- 3759184ad0939d60725e52abf38493808986f7ebcf81b8037beceb4a50539602
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Doc.Malware.Powload-6815340-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: ErrorControl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: ImagePath
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: WOW64
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\TABBTNFETCH
- Value Name: Description Mutexes
- Global\I98B68E3C
- Global\M98B68E3C IP Addresses contacted by malware. Does not indicate maliciousness
- 187[.]163[.]213[.]124
- 68[.]66[.]216[.]25 Domain Names contacted by malware. Does not indicate maliciousness
- www[.]dawsonvillepropertymanagement[.]com Files and or directories created
- %WinDir%\SysWOW64\tabbtnfetcha.exe
- %UserProfile%\664.exe
- %LocalAppData%\Temp\drp4vham.v1t.ps1
- %LocalAppData%\Temp\h224jefh.5gj.psm1 File Hashes
- 016449ce658b591c81a660cdf3aa38bfff92a5f107ba172c31e127954b36e344
- 28cf4ee192bfbf24ef0bc9a8eff889501ddaf08031c4c369035ddeec949e2879
- 3356b99748cd869b64a8be09de12dc8af1f417acd040e6ca4d80344ad58eb62c
- 33bc3b2d5e4464eb9a12fcbdd7a4dc0a6e7c02f3e2149325f473e1d59c019022
- 388fe279f421985cb9e147aaf8231a98c832874952c396a13df08894c3a9714d
- 38e53d78bb20c1475bb99e81348df948a7a2a7c54e553f7a07297e53de59ea15
- 581e775919ebf602a88369287a40c6b746ebf0a6e4f631c627091527690ab6c3
- 5a2e46067d3710ece2abdb092e7a3e49075ca19d0849e6499fb7953c28a9ec8e
- 8c2bd29b1fc6bb1e3187ba8cf8329847e419fe62b6ed3f2e054991dcade63dda
- aa800f12bc65cd7580d5f75a3b19de5333ccba6b81a4d7df58556c7878a4d82a
- b5d324893085f52a6b7d750b41d3039462d0e66e2e07f36d7aa07ab53f694790
- c7cb43c0854e5691b41f80496be003f9c1741e2921e5ee039645e220190162a2
- d7e114011982bf58dbd1752874d27895b1716fc1a0a02f8515a3384c9dde7a97
Coverage

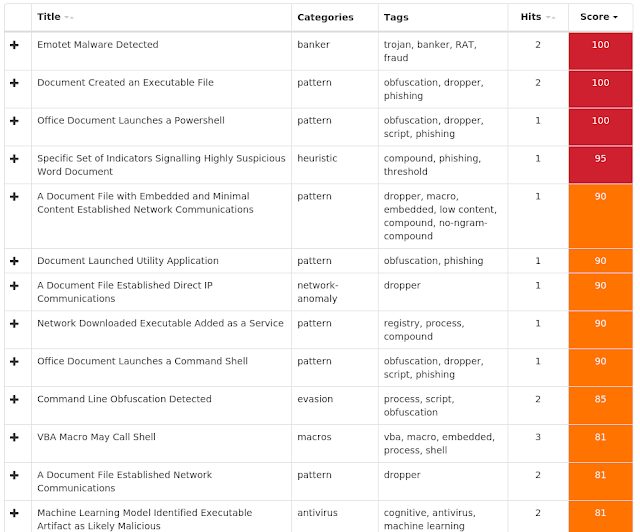
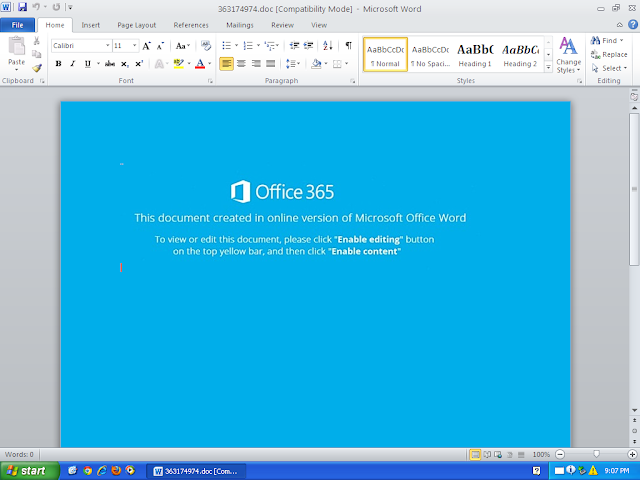
Screenshots of Detection AMP
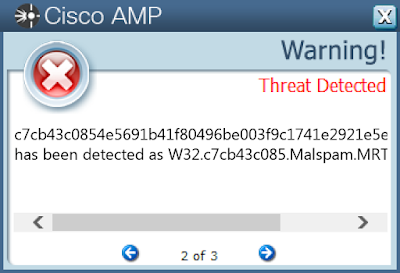
ThreatGrid
Malware
Win.Downloader.Upatre-6815606-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyOverride
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: AutoConfigURL
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: AutoDetect
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: ProxyBypass
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: IntranetName
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: UNCAsIntranet
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: AutoDetect Mutexes
- Local\ZonesCacheCounterMutex
- Local\ZonesLockedCacheCounterMutex
- Local\MSCTF.Asm.MutexDefault1 IP Addresses contacted by malware. Does not indicate maliciousness
- 84[.]22[.]177[.]39 Domain Names contacted by malware. Does not indicate maliciousness
- ce-cloud[.]com Files and or directories created
- %LocalAppData%\Temp\hfdfjdk.exe
- %LocalAppData%\Temp\ddjienn.exe File Hashes
- 0008e3366cdb87658cde4f85f0e5741be774af2694012c5f8502c1d51759dee2
- 0b9fbbdcc9efc61347e0f0c483098d42ec98a6111a8009e5e5ff1447a82e1687
- 1af0f85fde6d7365d4a97557f244cd95138a9803c2761d224fccc0eb0b4ad98e
- 1f6e5f75292636c7188d6f9cdcaa7597e0c251a3be8ce984488d68914f7ec9df
- 26b32472bb1a256a74573ec41e62fd871bb4ea756e4e8d57a941a032f6f405cd
- 285311d3a4d8608b94d4b3cccf3b9af094b5cdb51f7f92820b3b5bda8252137d
- 31db2340ffd8138aa3edaaa8029a30ea69a7e15ddbc1305f358c1478ff86f520
- 3cac1b87633da57b21fc38fc0da4f861e1dce3f8e48a2ced1824466da0b96049
- 3ef053f471053ead09f9b6dd0e54d13d64c83b5cb8141a8bece7acc66b61cca7
- 429612f20949951f879009fd9843668237baf3aaebd55c645f30e4f08d12e203
- 43c983dc9afe5727c47415c4a49ae29ea9ecc0ee902dc1918a9b5b9717f29e54
- 4e57fa6fb7d6ba5604b731123416a1c0f57802c4f2f4b639e1cef7734b14156c
- 4e7249b5bab1568c6f288313c0fae32350aaa909cae234618a5cf2d63a55b9b0
- 505bfa3c9c8e636aea732304b35f433d2293b0d0551c838a1b92f1c3f5fe7c7b
- 5914cd64a76b00d7959492292242ddbf42db9664a12f28aa42ee55c9d1a331c5
- 60d0b3f876b5e3e71a670dcfe60e42fef400122b74c63918fc77a35b31acdf93
- 653d6a96f4df49dc81a7cf2093cc622ebbeedd1a5e7298f61cc7227e8757aa50
- 68f21b90a6486f1288e88f5e00fe69bb35dba3fadba68212c226d4661d6cd6e2
- 6ea9adfb2dd8d038803708173b88f366d79a8de500268f988f9d34a7717ae5d3
- 7266abbcf661e5648958d321114eadd09b05fa00cf7ba67610fbcc97cf5d8094
- 78d18fd4a7d66bd3c6c7b7a6b962f115a1059d7587e933b295621ee4b46813ef
- 83c355f8cc2eb5f2381bfdbfa92db493891b2d08519d575e6a27e677cc60b1e1
- 83fb58f507b34a716b4e2a7b7edfcd184d64ec7577e2fe2c4cf26aaf2ab2ec46
- 8d59f4516f1d894e8b52ec3f4ed5d5ee0e0bbacfc3e51078a9209641e5c0bc02
- a0adfc3962b66d010da50d5fe1821b5a0cdbd85d98b03914655d269eccac44a2
Coverage

Screenshots of DetectionAMP
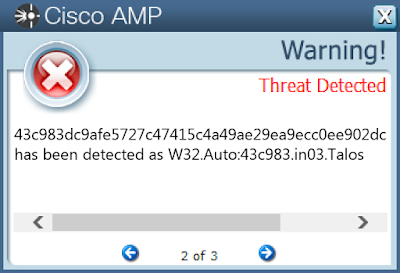
ThreatGrid
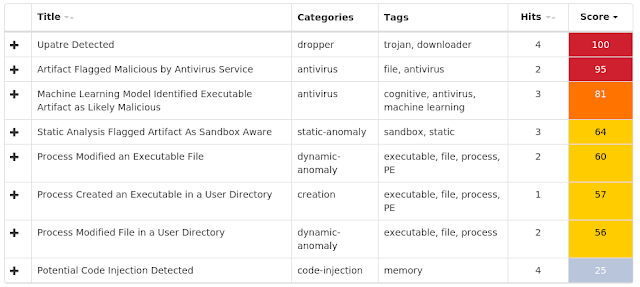
Doc.Malware.Sagent-6813871-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Global\552FFA80-3393-423d-8671-7BA046BB5906
- Global\MTX_MSO_Formal1_S-1-5-21-2580483871-590521980-3826313501-500
- Local\10MU_ACB10_S-1-5-5-0-57527
- Local\10MU_ACBPIDS_S-1-5-5-0-57527
- Local\MSCTF.Asm.MutexDefault1 IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- www[.]richmondchamber[.]com
- madisonda[.]com
- carminewarren[.]com
- chefshots[.]com
- carriedavenport[.]com
- ezpullonline[.]com Files and or directories created
- %TEMP%\cFi.exe
- %LocalAppData%\Temp\lhfpz4cu.e3t.ps1
- %LocalAppData%\Temp\nxli3mbc.5ex.psm1 File Hashes
- 15c651628f4ccd80f1d6ff52a3464610cd9f7fe31ffcc332c15bb4abaa5a3486
- 184ccc288232c76b5589ec0c6aeb280c934a5ad35c0c7155146d71030a040b40
- 20d9a0f8fe27a43d9d99fd593c8d8af9b9799172c5b7179aa5a8cd2219de3b28
- 210999842efd1221eb1973f2f18bdc8e8764ee19bba2680ac931edb357c72c29
- 219520e560a9eb432aba9d319c3c959ff9fe3f4a3ed9eb7f34ff13d1f8fdeaa1
- 2ad4db5a367762fcde6ddaffc4159f16f82c15d0af81b17d445327acfdc896ed
- 2ce7330a70040737397b483674680e27bcbdc67390dc64df11319539f15d4c79
- 3382c6cad4e8edd4f9423bfb6a7c0b2404386274280b9dbc09da6b40c3a976c0
- 37e0df1c725974d8842dbfd1c97c2808174bb13507008056d71acf5dcb16be86
- 3ca90d5bcf6aa92241dbfd3974542febbf325d25458643f2705fa71233445213
- 3fb6a4110c75a5c207da5997ed9b61fa0987d505bcb64aefad0676b1403fcbf6
- 4aa3fa1ef3642be02826ef9466eaf90427857dcdaaca6b7086b842527376f6fa
- 4acbd8ebac5a1cfcb72aad7e5f1ff3b21d2541a931964a07de2a50bcb9325121
- 4b122ed996a80e03a2056abfc84a875b6c3cf2f02081f8546fe62ba9308a8e58
- 57b90075a2a9821278a1ce760e5fd36f35f5ff5e768bef60f04aa4ac3741bc9d
- 58503078fa335ae31c9c405e1ae21f9784a8b1fa397481289fbd387549d1d857
- 58972ab31449176f9d62c6b35bcd63843cbeeb099b374e56b2c1cda373fb880b
- 7bb379b42a8c970753eb37ecfd9e33fc758a9e24cd72594e1463b967552884d7
- 807a8434cc34fb0b2875b8a8edbad637e29225288e8400c58317d6e50a93a2c7
- 8d10a6a99658759428cc5ab65baf57aee16ab607c23e2fb779e60450883aceb3
- 934acd0d0bb2e9dd8c533594fc5b883a5542a7cbfc967a64243810124ae1193d
- 95329196e424d530c8d1871241a630b2bebaf7d7c2ceeda21e1d5634f6fdd721
- 9aaeb10b1fa88e535d1c4d1b4313c0423173489c9e6b90f1922cd86df0c2c316
- 9dae1c9ef8a1bad9c6d708cef1e3f156eb634f406af397c55fca0fd3763311c2
- a50bbe414048cadb53c22770c78fdae9ac730249693ca7d46df239732938b3f1
Coverage

Screenshots of Detection AMP
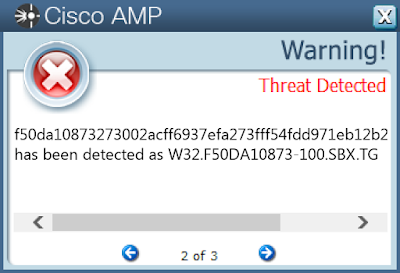
ThreatGrid
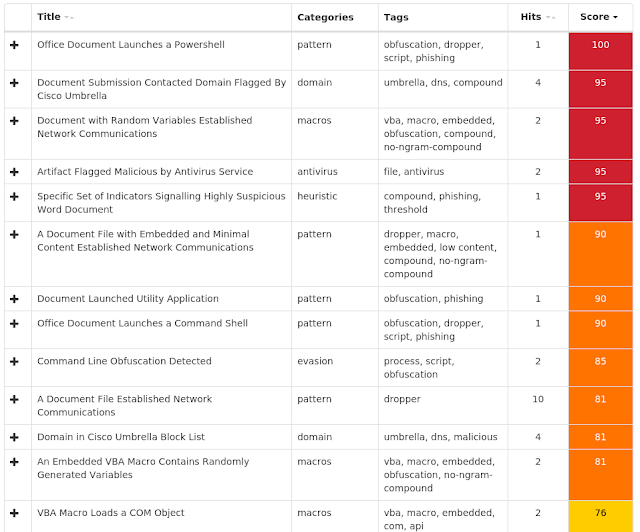
Umbrella
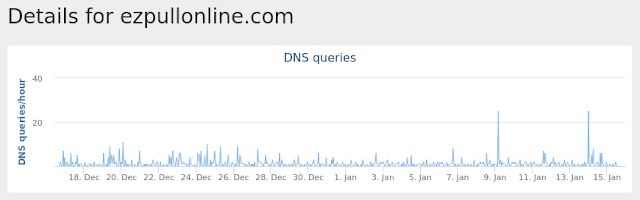
Malware
Win.Virus.Sality-6814419-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value Name: Hidden
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: AntiVirusOverride
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: AntiVirusDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: FirewallDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: FirewallOverride
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: UpdatesDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
- Value Name: UacDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC
- Value Name: AntiVirusOverride
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC
- Value Name: AntiVirusDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC
- Value Name: FirewallDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC
- Value Name: FirewallOverride
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC
- Value Name: UpdatesDisableNotify
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER\SVC
- Value Name: UacDisableNotify
- <HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
- Value Name: EnableLUA
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
- Value Name: EnableFirewall
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
- Value Name: DoNotAllowExceptions
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
- Value Name: DisableNotifications
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: -757413758
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: 1011363011
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: -1514827516
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A3_0
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A4_0
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\SAFEBOOT
- Value Name: AlternateShell
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A3_1
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A4_1
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: 1768776769
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: 253949253
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: 2022726022
- <HKCU>\SOFTWARE\AASPPAPMMXKVS\-993627007
- Value Name: -503464505
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A2_2
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A1_0
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A2_0
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A1_1
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A2_1
- <HKCU>\SOFTWARE\AASPPAPMMXKVS
- Value Name: A1_2 Mutexes
- DBWinMutex
- uxJLpe1m
- dlkjsow832jsxXscx3cxc
- fdlf89dlsd IP Addresses contacted by malware. Does not indicate maliciousness
- 206[.]189[.]61[.]126
- 195[.]38[.]137[.]100
- 213[.]202[.]229[.]103
- 217[.]74[.]65[.]23
- 217[.]74[.]76[.]129
- 91[.]142[.]252[.]26
- 69[.]172[.]201[.]153
- 94[.]73[.]145[.]239
- 173[.]193[.]19[.]14
- 185[.]64[.]219[.]5
- 5[.]101[.]0[.]44
- 49[.]50[.]8[.]31
- 103[.]11[.]74[.]25
- 173[.]0[.]143[.]204
- 107[.]180[.]27[.]158
- 103[.]224[.]182[.]246
- 46[.]30[.]215[.]173 Domain Names contacted by malware. Does not indicate maliciousness
- www[.]litespeedtech[.]com
- pelcpawel[.]fm[.]interia[.]pl
- www[.]interia[.]pl
- chicostara[.]com
- dewpoint-eg[.]com
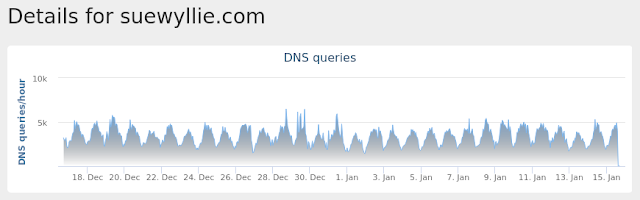
- suewyllie[.]com
- www[.]bluecubecreatives[.]com
- 724hizmetgrup[.]com
- yavuztuncil[.]ya[.]funpic[.]de
- www[.]ceylanogullari[.]com
- cevatpasa[.]com
- pracenadoma[.]wz[.]cz
- tehnik-unggul[.]com
- philanthrope[.]in
- www[.]katenilsson[.]dk
- www[.]best-lab[.]org
- ksaxl[.]com Files and or directories created
- %System16%.ini
- %AppData%\Microsoft\Windows\Cookies\70QUCKJE.txt
- %AppData%\Microsoft\Windows\Cookies\OMAMI620.txt
- %AppData%\Microsoft\Windows\Cookies\XTNNC6UJ.txt
- %AppData%\Microsoft\Windows\Cookies\502SJT1F.txt
- %LocalAppData%\Temp\huies.exe
- %LocalAppData%\Temp\yjoj.exe
- \osipby.exe
- \xcmjc.exe
- %LocalAppData%\Temp\dnbaex.exe
- %LocalAppData%\Temp\whprwx.exe
- %LocalAppData%\Temp\wingahupx.exe
- %LocalAppData%\Temp\winuarv.exe
- %LocalAppData%\Temp\wlpilw.exe
- %LocalAppData%\Temp\ccwus.exe
- %LocalAppData%\Temp\uhmeo.exe
- %LocalAppData%\Temp\winauaepw.exe
- %LocalAppData%\Temp\winkwskn.exe
- %LocalAppData%\Temp\winltmrtj.exe
- \doxioa.exe
- \wbpi.exe File Hashes
- 02e195243af5923dae171d824b63a3d25a2538bc596a971273eb30b0a920b9e5
- 03232668bd0c47073066f155ac5577b0240fcff40eafac864adef86694006e43
- 03bc456b9c91607a9ace1f4d8121d28f51ea3177bc2198fc3a1d76aab20b3620
- 049d7d3d22c12f592379446b2ebb2cd2c894422379421afd4c77986a293760ed
- 06e4245cf5a76061587820f25a5d019663b63cca431e9bb43095d6c09b25a3ea
- 091eb9a5e513328d93d4e46884a210464ebbf3da71be68704bfd3bb00a842724
- 0a8bd011f75fc337eba89d7aa95f293999ca5aa086357abe96555266d952b883
- 0c0999de8b07c0e231326c88f991d068f6d56d9e85a2c386a09ccf2eb8be9ebf
- 0ec786687795fff9476658ca7b29a04949025cdb3fae672a6ae071520313f43c
- 109ec982b35185df989ef3558f704648ff4e4b9c307fba80d238dc546a5ff8d2
- 10c2740264a991ddd1bc1058975565eaa871803647805048c8132d169d34f5ca
- 11b75d4bb7cdc3938d884da59da1885e70b8bc995bbf528ffd1c02d5876214f8
- 13971272ef6b82c6b5ef9de3eb33f2dc439048c4eacd388faf2de37d89d25bb1
- 15b9de1e80e24edb459847e427edbee34734d9950db2c84f30175ba46eb5d208
- 168fce02cad1cfd3ac578f3ccfb023c6ea76f8c402ab160f0271863c66279af0
- 1692102392f7d3552307ae0b1e081b862650272d22a3823134cc9a2bfc6866c3
- 16e8fc998564cd4272795782a371fad13fca160f9427f85e0a8591d56c9a5248
- 1a93a65e01aecd981c300f7877d51c1b4907fccb4acced53c3e70bb7c1884e61
- 1c2479ad95ad5ec5944d10fc4222b0f7b9c40e4f3e940515c18773205a6129c8
- 1c7a9720df7186f3354799f5f7b17139e20d8c9233ef796c1f8a9a4a61a3eb73
- 1f747322ea42c2d20d19d3f0b9b2afe1f143910006163a6f08d27b97b2927ff7
- 2012be50bc465db1fee01bcd1183590e9d22a1fb3105efa1005f9da81adc7a5c
- 238f6f0376a19f92bfb2e616bac4da36f5eb922e2e93bba8bb61d0a0dfa18f18
- 252fe2be1234ed2028a28650daa61a2a5e90f40598c52b97226d67c8e701b97b
- 256fd9777738e64c2dc9279a398a24cc2382d95eb94d760d081fee71d8daa32b
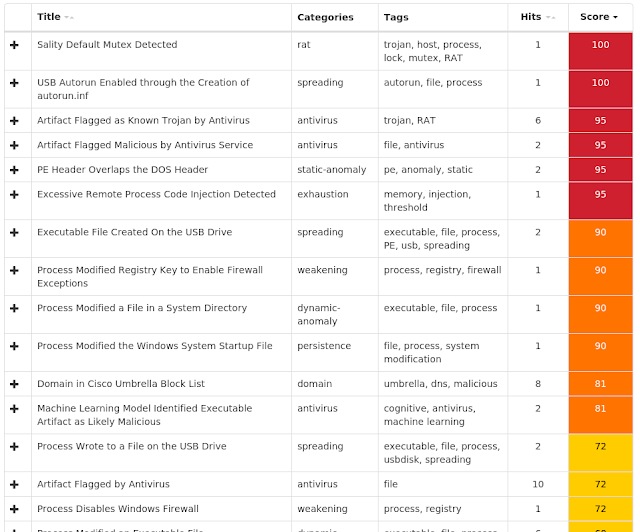
Coverage

Screenshots of Detection AMP
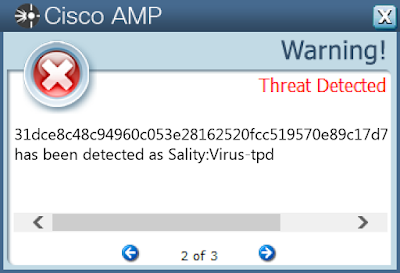
ThreatGrid
Umbrella
Win.Packed.Johnnie-6814043-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: internat.exe
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
- Value Name: C:\Users\Administrator\AppData\Roaming\Window Updates\winupdt2.exe
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
- Value Name: C:\Users\Administrator\AppData\Roaming\Windows Updater.exe
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: WinUpdt
- <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\SRVID\ID
- Value Name: DZ85WJDHN3
- <HKCU>\SOFTWARE\VB AND VBA PROGRAM SETTINGS\INSTALL\DATE
- Value Name: DZ85WJDHN3 Mutexes
- DZ85WJDHN3 IP Addresses contacted by malware. Does not indicate maliciousness
- 204[.]95[.]99[.]61 Domain Names contacted by malware. Does not indicate maliciousness
- havefunnuke[.]servequake[.]com Files and or directories created
- %AppData%\Window Updates\winupdt2.exe
- %AppData%\Window Updates\winupdt2.txt
- %AppData%\Windows Updater.exe
- %AppData%\data.dat
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kAZSM.bat
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\kAZSM.txt
- %AppData%\Window Updates\
- %AppData%\Window Updates\winupdt2.exe
- %AppData%\Window Updates\winupdt2.txt
- %AppData%\Window Updates\winupdt2.exe
- %AppData%\Window Updates\winupdt2.txt
- %AppData%\Windows Updater.exe
- %AppData%\data.dat
- %AppData%\Windows Updater.exe
- %AppData%\data.dat
- %LocalAppData%\Temp\AlgRz.bat
- %LocalAppData%\Temp\AlgRz.txt
- %LocalAppData%\Temp\AlgRz.bat
- %LocalAppData%\Temp\AlgRz.txt File Hashes
- 1091dadfa59fe9530292e18818036f6e8ea754664a29665427f357f5ab75d4e1
- 2d00dce46e197f8fb90ee6ac49d4a671fbf4a5a52965021df8b18f787974b8e5
- 3086d7d8c8d73a9d6e010edef5be6741be609120c7a6d5500b75d38157c65b40
- 30e11e19fae9d52645c3d39f2988880cc7a92361cfd4cc16887efc2533eccaa3
- 3c5550e2547c2b34dd54755a102c118884cc5eade31a455240f6d728f1fa142e
- 42649ce0c2c923fc667921078c999d6bf0f83d41d5cff1fca4f3bcbab825609f
- 468a2974e88fdbd3e43e9bb1fbb4e706e83215ea7af6d792ce818173d7eb91a2
- 4a835d5e7c4293b6ac0fcd277051c6718397a425ae0b9e87f836927b5aaf5bfc
- 542e1acae7a25e27803e5e48ef2bf6bad70edc79d1d0861d420c812bc41000d9
- 54842caa37882cfc0aa7d565f4d2d1c6c77b9af259ae051c380fe08337576cd0
- 795dd2ce39784bafcbda7b5fd364f7ca70ea9bcc9ea87cc9b46a4d8c0cf320b6
- a94bc5d6fa3117328c19a9da7325a788ffc89ad481e63e761e875f10ee1910bc
- aa75c45c4b182f44f265665905956827474e1da5fb002ced185cf679830772e3
- cb5698b07a75086cb1aaddff5a451b3dfbcf07407ba0da9376cfe69a51c2b38b
- d4825d1956ccf52a7e8043f28af9f2942e08c16bcee2785c51717047c89d1a92
- da665cdf12e4e77c8383c37497e36f34bd5794273df879109774065bfbbec40f
- ec0638880ff60664c2ffe5417342297f90b9df3df8b7e0c063387f8eb69f633b
- ef405428d8e6f3bc8db642f36192e9684982ff4a6fa507259e8a63b832a72f8d
Coverage

Screenshots of Detection AMP
ThreatGrid
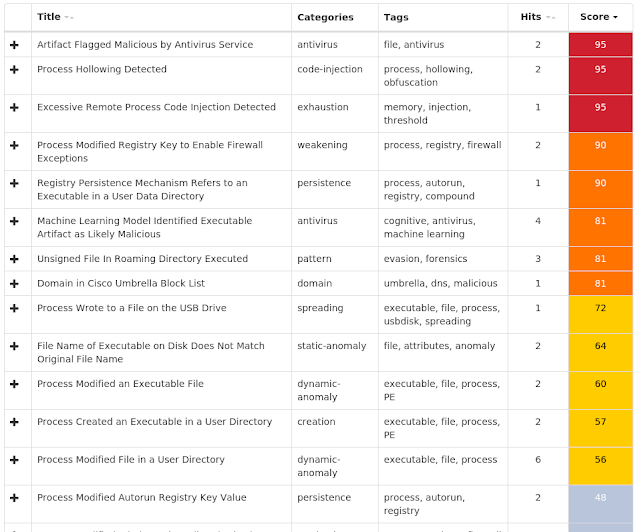
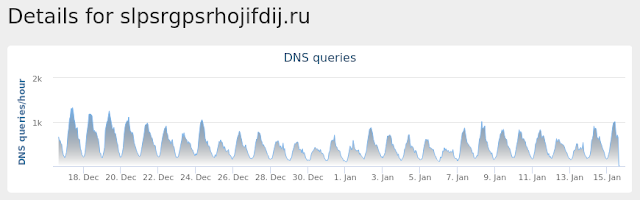
Win.Downloader.Powershell-6810733-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\BITS
- Value Name: Start
- <HKLM>\SOFTWARE\MICROSOFT\TRACING\POWERSHELL_RASMANCS
- Value Name: EnableFileTracing Mutexes
- RasPbFile IP Addresses contacted by malware. Does not indicate maliciousness
- 92[.]63[.]197[.]48Domain Names contacted by malware. Does not indicate maliciousness
- slpsrgpsrhojifdij[.]ru Files and or directories created
- %LocalAppData%\Temp\979574639568794.exe
- %LocalAppData%\Temp\jqlrdsf3.aw2.ps1
- %LocalAppData%\Temp\qg25nwiz.upp.psm1 File Hashes
- 08523df3d1943edaeddde63d82ef9883c647fa0e32e6dd38b6ea132e5e67a938
- 0ece442fd0f210407f128e1cd0c32fcac42f18a7490be62f6ef445725ec6c08e
- 14eb1abed6c28c1b3f34d15f663cbad4ccd35f586e72dd6bdb68cc2295f46ed4
- 15d55efbcadf80890653db8d710f5dbd8af0a15aa02174287864b76dbac711e2
- 4525956fa304c39359981f0a0541985395b52f33bcb3bffba82576abad5d83da
- 4e60c907247bb3dc206de6c9a59fcd2dc108cd0f7e3109a41eed3b29b0e2dc6b
- 61c1822c8e0feeff2e35a6f821d634a9306c9c6fcebce3459a43c9eb3e482b04
- 7ee9421633c1cf45b855551025d7c8b5eccca16a32a569ef62265b067e142d65
- 82b4b7bb6a74ac688b563543f1720bdbe2c91319e9eede5c4b9fd0979c99dd03
- 864586f404a45319aa1b921f460f6b672b0f0f384442366dcca7a9b8deeb0cfe
- 8a48ab287acb6260e4ec3d1e59631d8ec91f3a8bf848dc5f1e97657fd2be5112
- b41d6173c4a345c945451a444954a44569984fe4695047155e8f5328fa0fa0b5
- bc2f6a4105f310dde0bd1ebc80e0453f6cf660d55414ee8638eaba339e372696
- e23b6494912529d6339e9922048214a2dc0162489e33a3c1750c99348865b68e
- e5cef04fdb9f9a47979db41eb80e5fc148b2b374c6ad28bd831283ac538e9c77
- f92034a3417a6f0506dc7392fd745731be810b21f9dffb4e3b6b0b1b794f45fb
- fc378a5892438ed05fcbdfc422eb4de13f1cab8fd30385c96c19532a9c974ee1
Coverage

Screenshots of Detection AMP
ThreatGrid
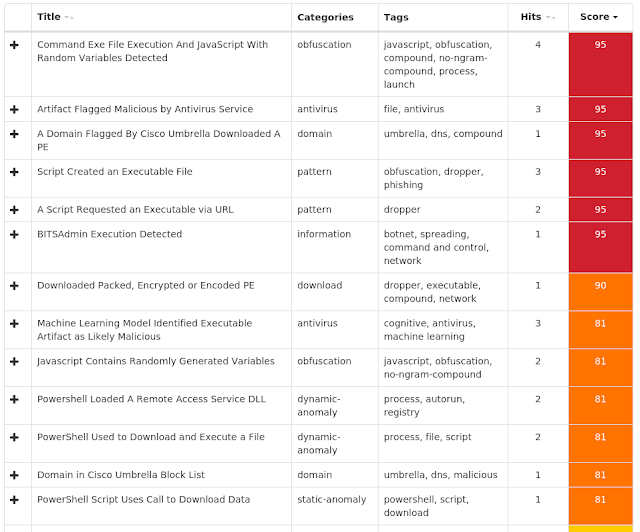
Umbrella