Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Jan. 18 and Jan. 25. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicate maliciousness.
The most prevalent threats highlighted in this roundup are:
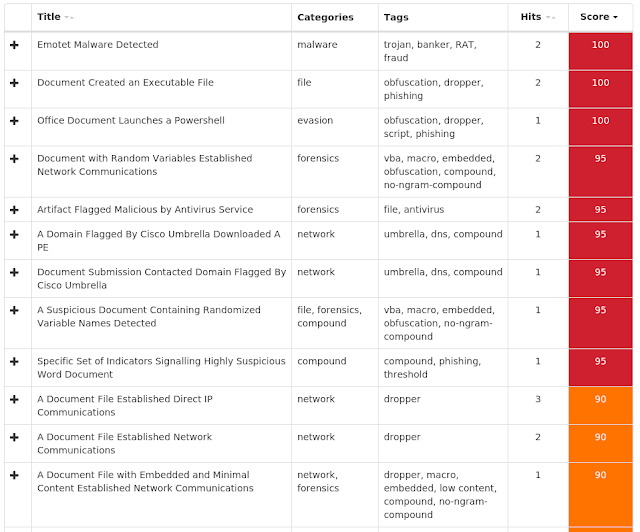
- Doc.Downloader.Emotet-6826494-0
Downloader
Emotet is a banking trojan that has remained relevant due to its continual evolution to bypass antivirus products. - Win.Worm.Vobfus-6825980-0
Worm
Vobfus is a worm that copies itself to external drives and attempts to gain automatic code execution via autorun.inf files. It also modifies the registry so that it will launch when the system is booted. Once installed, it attempts to download follow-on malware from its command and control (C2) servers. - Win.Packed.Razy-6824365-0
Packed
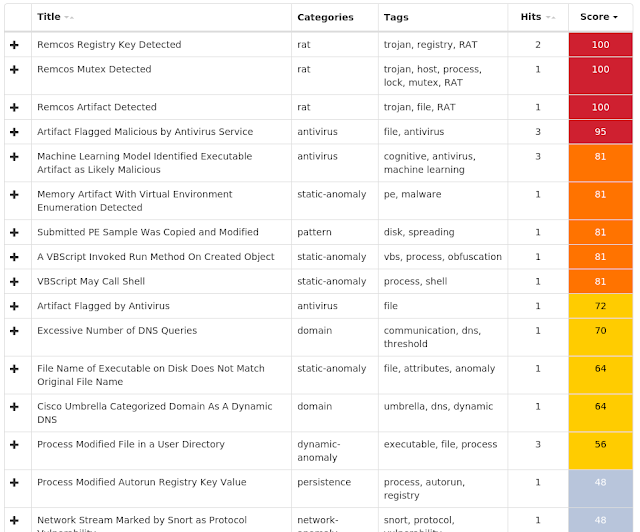
Razy is oftentimes a generic detection name for a Windows trojan. Although more recent cases have found it attributed to ransomware that uses the .razy file extension when writing encrypted files to disk, these samples are the former case. They collect sensitive information from the infected host, format and encrypt the data, and send it to a C2 server. - Win.Ransomware.Genkryptik-6824111-0
Ransomware
Win.Malware.Genkryptik is oftentimes a generic detection name for a Windows trojan. Some of the malicious activities that could be performed by these samples, without the user's knowledge, include collecting system information, downloading/uploading files and dropping additional samples. - Win.Malware.Ponystealer-6823878-0
Malware
Ponystealer is known to be able to steal credentials from more than 100 different applications and may also install other malware such as a remote access tool (RAT). - Doc.Malware.Valyria-6821700-0
Malware
These variants of Valyria are malicious Microsoft Office files that contain embedded VBA macros used to distribute other malware. - Win.Malware.Zusy-6822787-0
Malware
Zusy is a trojan that uses man-in-the-middle attacks to steal banking information. When executed, it injects itself into legitimate Windows processes such as "explorer.exe" and "winver.exe". When the user accesses a banking website, it displays a form to trick the user into submitting personal information. - Win.Malware.Ursu-6822222-0
Malware
Ursu is a generic malware that has numerous functions. It contacts a C2 server and performs code injection in the address space of legitimate processes. It is able to achieve persistence and collect confidential data. It is spread via email.
Threats
Doc.Downloader.Emotet-6826494-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Local\10MU_ACB10_S-1-5-5-0-57527
- Local\10MU_ACBPIDS_S-1-5-5-0-57527 IP Addresses contacted by malware. Does not indicate maliciousness
- 52[.]31[.]99[.]185
- 47[.]52[.]19[.]221
- 91[.]209[.]78[.]110
- 46[.]30[.]213[.]132Domain Names contacted by malware. Does not indicate maliciousness
- www[.]seine-et-marne[.]fr
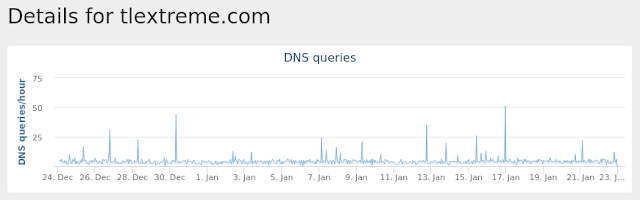
- TLEXTREME[.]COM
- vanherreweghen[.]be
- www[.]tzen2[.]com
- www[.]addthis[.]com
- www[.]iledefrance[.]fr
- www[.]stif[.]info
- www[.]camenisch-software[.]ch
- tlextreme[.]com
- sh2017[.]chancemkt[.]com Files and or directories created
- %LocalAppData%\Temp\736.exe
- %LocalAppData%\Temp\j02khkb2.lmy.ps1
- %LocalAppData%\Temp\q30h0dfn.q03.psm1
- %LocalAppData%\Temp\CVR8B7E.tmp File Hashes
- 02961b9b1846411364a0c00b6546aeaceec7e7156a89662ae81a2223c9a612ca
- 0acd52e7f92f125d8fec5d78db296ee3c88079456dfb66b84fa92be944dc1293
- 11d52b1ee5c330911ed98ba86a4560c67cba2bd70427c8d33a0b793ddeb5c11e
- 16ef10e1f741ca1cb22b657dda69b7d15e6c016a667602fb8fe825b5846eb4b5
- 175b20d5f2079f86b1fe4ef91d5a84ce3fb71939b3c8297e4de6587875dca6d5
- 18c74f2852985acd6a5b35d21d12e8e852d54003b4e5d3714243e045969c434f
- 1a4dc5022a6b5296fe5d03597782a985bd721e3651b010c06b9be205b5c9f97d
- 1c7813fcdec02ae9bf9bb816d87f66eca49cffa1df2de22aac19d2b365e59df2
- 1f5e9f1c173cc8611a5d34e801c0a26ce7365cb1c7b660bcd88816153b76d467
- 2210bb4262bd6f02c2c1b836ea7372c28b35f7e31d81dcf4749fbd4fe71676fb
- 22b521f4fad5c39e0d84729f3e194782f2a802c03f6e24ef013e7e33d299703f
- 2311a0274a3edf0a79d422ba126d2a1e23e98b13c40762e2aac7b40686a308c2
- 26fba2bd9792cbe6aa14f3baa9a2ffb57344d7348805648a53dcf92644a8b973
- 3cebbd85235c819ec92210572035f2973b54740f306b8b0607e03c84eb7b0914
- 3ebc758a0186db99545ab2614b2a96544ab4509bf7d24c8d11dca06b2d17adbd
- 42df2ceda548dbd95ed4cf8176dfb8817e7350ea9b296adb33a3e6c3f2fb272e
- 4dfb9830a14e1e92ca88b40189fb05be60a42be886c9ca1cd2f6a3f5f09e0208
- 51cd6bdb18da6dc94549e067b04e727b9e947f2f189f5c27da67eb56f77c5f54
- 547ee4142a9088eba58961d0bfdae6a32f501affcff9dce7e3f424f47b8fd4a1
- 5d3e5a9b7730bd40f0cd4392367744bb7a3ddefd3b316d603e56369a7813ee68
- 680d56d915ec028d4d0e33cd63e90f58c1f67c4e8b92d11eabf2576702d5b3bd
- 687d3887779bf147f8ab6637c28f76559f3a1cbe0899cfa07d0ac33733fc74ef
- 6c9f60643913ae688fc163d8e09a71268c0bd527ca5e9330c163108aafac5944
- 729777e3d2a3bc3e6846bdf89f4480052c3e5877a8dbd3d93c7a7d9f38d90311
- 7575b3de182b5ad8b92eabad4f5307e27280729f81ab692d20633dac2f786d8c
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Malware
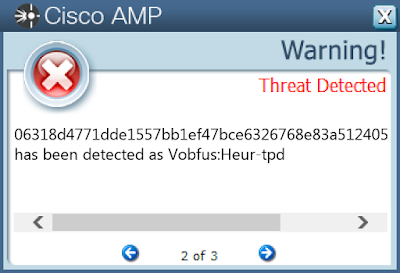
Win.Worm.Vobfus-6825980-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: internat.exe
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
- Value Name: ShowSuperHidden
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: raaitay Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- ns1[.]boxonline2[.]net
- ns1[.]boxonline3[.]com
- ns1[.]boxonline1[.]com
- ns1[.]boxonline3[.]org
- ns1[.]boxonline2[.]com
- ns1[.]boxonline3[.]net
- ns1[.]boxonline1[.]net
- ns1[.]boxonline1[.]org
- ns1[.]boxonline2[.]org Files and or directories created
- \??\E:\autorun.inf
- \autorun.inf
- \??\E:\System Volume Information.exe
- \??\E:\$RECYCLE.BIN.exe
- \Secret.exe
- \??\E:\Passwords.exe
- \??\E:\Porn.exe
- \??\E:\Secret.exe
- \??\E:\Sexy.exe
- \??\E:\x.mpeg
- \Passwords.exe
- \Porn.exe
- \Sexy.exe
- %UserProfile%\Secret.exe
- %UserProfile%\Sexy.exe
- %UserProfile%\c\Passwords.exe
- %UserProfile%\c\Porn.exe
- %UserProfile%\c\Secret.exe
- %UserProfile%\c\autorun.inf
- %UserProfile%\Passwords.exe
- %UserProfile%\Porn.exe
- %UserProfile%\Secret.exe
- %UserProfile%\Sexy.exe
- %UserProfile%\c\Sexy.exe
- %UserProfile%\raaitay.exe
- %UserProfile%\RCX6E9B.tmp
- %UserProfile%\c\RCX7DE8.tmp
- %UserProfile%\c\RCX7E08.tmp
- %UserProfile%\c\RCX7E38.tmp
- %UserProfile%\c\RCX7E68.tmp
- %UserProfile%\c\RCX7E97.tmp
- %UserProfile%\c\RCX7ED7.tmp
- \??\E:\raaitay.exe
- %UserProfile%\RCX6D8D.tmp
- %UserProfile%\RCX6DDC.tmp
- %UserProfile%\RCX6E0C.tmp
- %UserProfile%\RCX6E3C.tmp
- %UserProfile%\RCX6E6B.tmp
- \raaitay.exe File Hashes
- 0037d65faac14ac7334d7945e27569d7cc3d5dc523721e6663250a12cae30970
- 004cc9d4425a0e10fff6239ae475488707ebaf7f2a6e4a3dee7b34ce5695c321
- 0067963d2aceffee9ef4f6e721810751dca83d21d0712abfa833a25e22ba4dbb
- 0095c53a8472b4a6c607cb35a3c6a1a6b6b9bdb73411982877cd36bb337fe622
- 012f637a2ecc4fcd7bb899d15bd3154da2e57990b06a2220a70275e4d71f6f1b
- 014a73b4e83e353606d90832f8ed0531621a9f1b18ff8886f6ae4f0ac7fea1f9
- 0168589ab988762e304160c1185d9f0cfda9fbae862d49b287151e2867434698
- 0174a979de62c49713dc26bf492bfb8e938663b6678718b31b93a1ccf74a7c0a
- 01833d63634a87bc656d3cb19e81a595c1ff2f9b576881d938d94276a3b19421
- 01bb231426f9f04f1fcc15816758ae71cbbfaa4402ae208f2d97393f5e169eaa
- 01f729500c940572e0fffc33813e6b390a11702f0023fa23e2a699f090843ca8
- 01fabdf325a2cc93b441ad0f6fd5045d60f4948d1a675efab4ae6b6dd3d09e84
- 033634d5e256d0c401521f689f02298c03161d93a73d6ee7516728e312346e59
- 0405dd8730790632cc9af7a163bcf2edfe53dca323e2bbe51eebb1176e3d88c8
- 040f4aa4129dbbc8fc35fa755d54819cd879cc1df72717c7326b3dfd2419fe68
- 047a78afc2d81bf8c214cd3ec65c993f8a20d530e317e75364a6a8406b527259
- 04cdd36585f184a6f00628a41e06df4e6d48e14405bdb1cfeefd32d6abece39d
- 06180c973c1907270017c6c4d49f75fdedce5e0b303324b001db54321776bfc6
- 06237a002970ae7de3bf9f30e3d7555366cb10f3e56a2df9a8cd19ed682f138a
- 06318d4771dde1557bb1ef47bce6326768e83a5124051e296ca2463f9693bd50
- 07ba24b2c6e0d1480180221ddb1854cfd5ccfef50487e13f71134669d0027e0e
- 0885ba5f2be768f907c88b520c412d76734e90cd2104f36cbc14bf59c28875a3
- 08876ed5bb3db929653ebd493da0bcd89d876d3ed96f0f8d897daa31719cf150
- 0939e8b87435767e67f2b6850a54d6abe3b037639e8c076465a167f1f4673306
- 0a9b4d6c0f1b0f87cf7e953c06d4684607e688252cd6d8b9bda28ea4bf8c871f
Coverage

Screenshots of Detection AMP
ThreatGrid
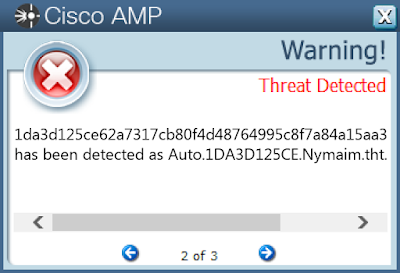
Win.Packed.Razy-6824365-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\GOCFK
- <HKCU>\SOFTWARE\MICROSOFT\GOCFK
- Value Name: mbijg Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 66[.]220[.]23[.]114
- 64[.]71[.]188[.]178
- 184[.]105[.]76[.]250 Domain Names contacted by malware. Does not indicate maliciousness
- kwowwauubfk[.]com
- bqwzunofd[.]pw Files and or directories created
- %AllUsersProfile%\ph
- %AllUsersProfile%\ph\fktiipx.ftf
- %LocalAppData%\Temp\gocf.ksv
- %AllUsersProfile%\b95c
- %AllUsersProfile%\gvpax
- %LocalAppData%\1596
- %AppData%\f2s9398
- %AllUsersProfile%\0n48x8
- %LocalAppData%\o1me3
- %AppData%\d991m59
- %AllUsersProfile%\3qy3
- %LocalAppData%\7a92
- %AppData%\98u3
- %LocalAppData%\31m53w
- %AppData%\4o5w356 File Hashes
- 00958b0eb7138a5cc3901f47ce902f6216b076fa341f9f7cda1bcfc62191b42b
- 0ddb4e64337d7a3b5e7980bc3d8b2e3d1a8870bac611de6b7fd4ea04e4b13834
- 16981b12217330adebe7b6d4ff08649f5ca2559b18331a0d0a6b79bc6f65cdcc
- 1b2c133834c1edf5a9696671bc555209abcdf17936c851942892015622f21c50
- 1da3d125ce62a7317cb80f4d48764995c8f7a84a15aa3a37abef6e03b4d8d071
- 30bc3bf1588a0ffa91ca8e494a5e7e40cc35c80eeb3a77c23d9fb98a251a7e98
- 3a1b58d54b6580a3d81fc5fc9cddd6f7eccfcab8f9f41fff81e45200d9d9294a
- 449c7ac8be0256b2ca573101eeb65cb0a5be0af883974f68574625f2f6bff7f8
- 44d438154cee044e36cb2a539261b3549d9cd16bfbf4d512073bba36a21d92d8
- 5033ca548036bc7fc8a988dafab88c0e7694701b12202522207d5cf3d194a31c
- 5c36d36a367eb555fcf3373121ec0ba2884ef92741471a65643cbd29f2877b9c
- 65a753ef5c366e3c79c989948d25504822ae31754d2af381c2c2039a2f5d52cc
- 78058316dd668f0052f9c8753cfb2c85c31a86bf9cf17fb9989de7efa6f34f3e
- 7ca95a22275a3f76ab51720871d3fff23b57a640c628e940230efb05cd0a32f8
- 7de1ddc87cc6956e6e20231d708073b011f5d03f79acd7dbc40052a3f05d60ea
- 856dd8f3138a9dc5858bcb80efa1abe8634b995b7f597eb6235002f13371c176
- 88528338d3eb4452c37548280f1c36d7e13eaf63cac1c320ea72f1f99403fa57
- 891088ed7a0e386a1c84b332b0aadce6f4709958aa07614c7cc83797518a95f7
- 9e5a684a10fb0f567bed0cbb71488bc9bb79d7fc15500a0da48c34caee6a804f
- 9ef872a783502bb47d5a461d231e26e301cc9f6e4625e7bd0ef7a01620f89b47
- a8cd581c54ecf14da45460fa8fd8e5f5e43133b78135df9e2e8ae5c36af635a3
- af7b095f795a599e83c94d41432b2755d7289159075147aae6931cc622dac30a
- bd354725cb308fe831075414d4e9f2a2dcddbd16c900484f9aa9e1bcf2bfc6cc
- c03a12f494da082c5c108fd80c1e1a2a1bd8be7cc8dcf3fae02f8bb39bb11944
- c088e5a96993d5361c5c0b138dd17d658de50a4c1007b4d6e5a971df8a8c39bb
Coverage

Screenshots of Detection AMP
ThreatGrid
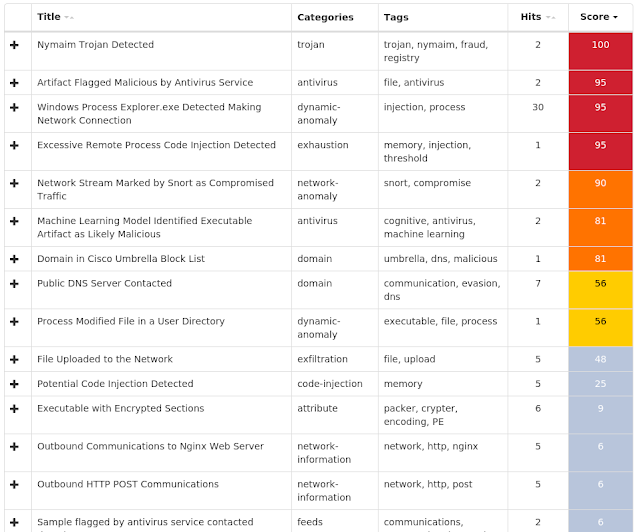
Umbrella
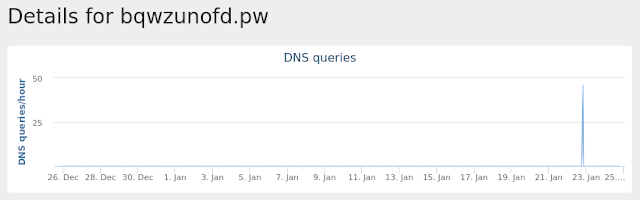
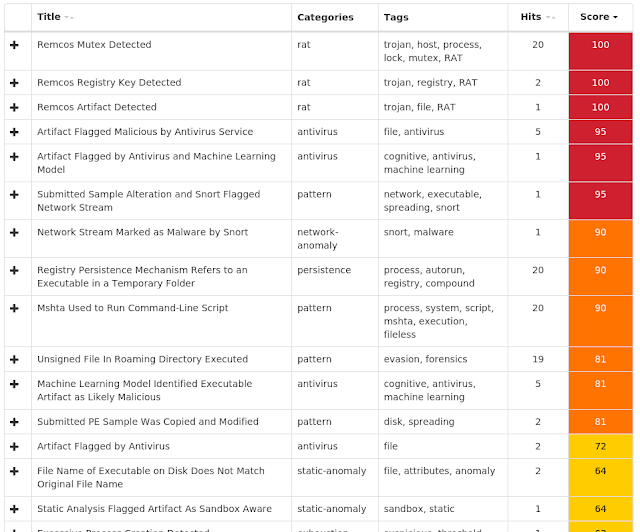
Win.Ransomware.Genkryptik-6824111-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: internat.exe
- <HKCU>\Software\Remcos-69PU1K\
- <HKCU>\SOFTWARE\REMCOS-69PU1K
- Value Name: exepath
- <HKCU>\SOFTWARE\REMCOS-69PU1K
- Value Name: licence
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
- Value Name: SKIVESKYDNINGENunenterpris Mutexes
- Remcos_Mutex_Inj
- Remcos-69PU1K IP Addresses contacted by malware. Does not indicate maliciousness
- 84[.]38[.]135[.]91 Domain Names contacted by malware. Does not indicate maliciousness
- top[.]pubgplayzonejoco[.]waw[.]pl Files and or directories created
- %AppData%\remcos
- %AppData%\remcos\logs.dat
- %AppData%\Imgburn\imgburn.exe
- %LocalAppData%\Temp\WEALTH2019.exe
- %AppData%\Imgburn
- %LocalAppData%\Temp\Mirijana9nyhedsgruppeskitte.exe
- %LocalAppData%\Temp\~DFE751F75B3A32A556.TMP
- %LocalAppData%\Temp\~DFDEB24D10F9017BE2.TMP
- %LocalAppData%\Temp\~DFE5FA503DE0D2D852.TMP
- %LocalAppData%\Temp\~DFEE43B3EEDEE2644E.TMP
- %LocalAppData%\Temp\~DFD949DB000F4368B2.TMP
- %LocalAppData%\Temp\~DFCD42A77CD5F06772.TMP File Hashes
- 049f02b69493dcfa1c2740519a965f5b3cdad94319480787f608df39646d4a45
- 08703057fe22c4df53c83e1406c772d24148a570efb9b636307420c56a506fea
- 0f52ae41d65fb4790aa778431fa32cc037cc4d31f734b6a540bd37668deb4df5
- 1102ae383bafc64ff90b952f8f96797801396ad00b12e62ece8c5bf667bd7917
- 136c0293daba6aecf870d253aa9393c085b8ff1dd6d47d71ae7aebd296c715b3
- 149022bc418cf2110bc02bd03d65bc5c8e62c811b94361afe48a95c5a2649e64
- 300c7f5229eccb18cef38365f7567ffa0d5a2226b2a338083f069e4349ee83d9
- 311da3fa5daee4b28327edd53ab5aa57f061708b2dfa8fb755fd08854e2798a6
- 4d652ede13a7424582090164c5d453a08610848aa6c2b34a2cd9641f2f9e4761
- 5147bffb5e30bf2e6b0c38af954aa7de64ff15964b32df334a2881b3d34a88c9
- 546c3e1bb5b13f369f8aa7333d7209d736c90edb7db2f41410ce42ceb264bf30
- 561c6fadb78eb3c1ab18596a61a348af4e052b0a33754b1587f7e8f07ebb864d
- 5724e9dbdc024c683ea3bfc2726c951fbbaf8faf46f4c61d7f1b5d24e0df0c19
- 5bdb3e691c8f07c16392e5077601bb445110cc6e0aea0d5547b4469d82e06f42
- 5d5d0f07cc4358b44291c6ee3455a3bc19ccea06fa66364bacd3ad051a368758
- 5dc30dc295fd5a286c6ab6ba287d4b04373c16e1de75182a6ea221394dae1137
- 6178f9c685e131ec20d7981f461e9947201b8ed5edd7ff64514d4b0daac78a7b
- 6447cb09817b37ddb3b107e97060e9becac9ccfca8662cd3a193eec06ba1c35e
- 6d5ff7b6af5fcab6b9a12a5213426b1d2fe93c06a039d25676bb00f2b3ea1231
- 74625b4620d8233adf151b7c7797384e12e22df6fb67006482bcc8437c070838
- 7733201b8330bffd8a41dee35a3ef2005e8424df477a5fd08fb52651093e7700
- 77b8aa573a3967891d4cd3e93ec76a1004ec8294f0c479ae8043e821d06dc78a
- 7ee37ca283d2cb7ef6fa8a8e507de85875b5796d5c006ea599d55c11f5e6a7ec
- 86b98581605b1b0c5286f307bfd79338c74fc5bc73ac11e1abb0cb37f97d98d5
- 8bf4d086da3f18e4c537e107ebc802056d0b0dc4813eee8c884671c9a68d587b
Coverage

Screenshots of Detection AMP
ThreatGrid
Win.Malware.Ponystealer-6823878-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
- Value Name: Adobe
- <HKCU>\Software\Remcos-L409SR\
- <HKCU>\SOFTWARE\REMCOS-L409SR
- Value Name: exepath
- <HKCU>\SOFTWARE\REMCOS-L409SR
- Value Name: lic Mutexes
- Remcos_Mutex_Inj
- Remcos-L409SR IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- 1010[.]http01[.]com Files and or directories created
- %AppData%\remcos
- %AppData%\remcos\logs.dat
- %LocalAppData%\Temp\subfolder
- %LocalAppData%\Temp\subfolder\adobepdf.scr
- %LocalAppData%\Temp\subfolder\adobepdf.vbs File Hashes
- 057500aaa50232337866b4470e930a698d96c97d446f2737bb9e69807e13fcd0
- 26df92ebf43f0dda98bd34d5f72841717bbe9c524bded8d3d77bede19baedfc2
- 2a5608a0d642fd23f0b49c6436886e937d4ba4a40e048bcd57338e74d7815a81
- 2aee79633fda123830fe7061900dc9deb2af0c45d1ad97bebea2e853e0f6ce17
- 424217fcced5f9a8a35c9de9a66e0c06b761cd2e46db6a042f325835104fcc47
- 439e2e22cb2ff1879dd19c1efe2c2d8e2897d6cef866ce6fb9a33c84165253fe
- 539c084c60d1d5e901aea6240f113a021c7cd7e447ac9cf35953d05666f3cc22
- 634dc330090c9f2b5d7b1c670102d5c1cd3389cb676ff04cdbe87df50bfcfba7
- 736b02c049a77d35435fb18fab0067544c4d6cc0cb2e0bfb9bf5152f65a8db93
- 8269d87f90e2d401e0ac70d2f9e32aef62db5a70f7a0165646f44534edc9c265
- 93411f9ee4535cba7e1c0e288a3188d9d1679d5b2b0bdd4e3b862d49e53510e4
- a1436dfb3efb320afadb5355b305794a330284c5515283dceaaf70dc09450c73
- c1e8d791958e9943798a6f28fa6a9563519d0d5a49d37f834af14b4074f2efec
- c920ed42aae02a1536408fd3513dc1694fed093091a5655529149c989c7d6744
- c95d501830e87c470c7d731a7be78fae90b38d4eb8aa8365d981d8397407fbac
- d59d2b4a4b6473f7a82109b6768d3ce62fde8ec8f6da786986a2545da0245e49
- ec8abd35fd1e3c8f29f4187d9ddcb7c6c3c35a838c688d8a08553d46ca091cd1
Coverage

Screenshots of Detection AMP
ThreatGrid
Doc.Malware.Valyria-6821700-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 191[.]6[.]194[.]81
- 177[.]185[.]194[.]161
- 157[.]7[.]188[.]229
- 45[.]60[.]22[.]20
- 54[.]164[.]54[.]199 Domain Names contacted by malware. Does not indicate maliciousness
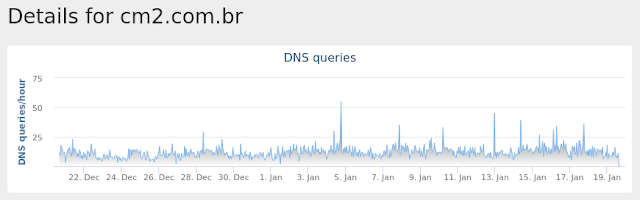
- cm2[.]com[.]br
- heteml[.]jp
- secure[.]heteml[.]jp
- snowdoll[.]net
- www[.]plano-b[.]com[.]br
- ecojusticepress[.]com
- craftww[.]pl
- lavoroproducoes[.]com[.]br Files and or directories created
- %LocalAppData%\Temp\619.exe
- %LocalAppData%\Temp\rucrrluq.3nn.psm1
- %LocalAppData%\Temp\wjyt5a53.3uh.ps1
- %LocalAppData%\Temp\CVRD0AC.tmp File Hashes
- 006527ed4540d3e8b684bdc110cb1f738ca696e8706b748892930994de3dedef
- 11f7710f8cabe988168078cd6ba83c2544d1d06c9a8a3583fabe164e87f7048b
- 23f1b03ee66fb8dd1a515afd7adeb8f85b260ef5e20a7d80ad1697865f59f794
- 243a87a44e767e8d5b788c29bb0dbec9986956b40c407074f670bcc9b206d730
- 2b201210a7ea524a3d65c7d2ee2e7d322479657076a1c30f8ec6994eb97f269b
- 3f7f15af2c3736d94f62e8d58bad269d29198eaffc40ccdbfd166878daeef652
- 400d6b89b8026f39de9c80b89aae66e49afebf153c8b5b9d480307ada0f4c428
- 5bdac880fac6d0b90751b1f2f7dd97b50ddf2759926a414b940dff6fb8117833
- 5fefc488c0bb534fe5de5eb5244524ab5138474609c6363f959845a35b2fa94e
- 73d4c1dafc168a36218d215548bdcc87b0ecb667acaf685b044b680f4f678dca
- 775b96aa12728bfc5f6f68bf11d8ff34e252107d8f63440a471495e8ecd9f1f7
- 79f220cc40a6d9d27adc27374ebf0263792e86b64061a709357233b88bb847e0
- 7ca6572429e9aeeedaeb810c5752f1ee4f300435eedb55efc6128a3c5cb40028
- 7d1452ab28a32b82e29a27b02f3881ed4eb7e33e47c65791753b6f9f6b0da364
- 7d50253b1168a61a502890fdd13e7245b5f7aa8465da25e3bed00a8fa0a3b4fd
- 8f0dae9f191c55289ab80783e68c0e03e97f391cd86ae283304555f20d8f2d31
- a09a6e4a65a174787ec889f5e9d9024cdce88d46577d022a012ee4f86fb472cb
- a77b90d16bbdd99569309b37cdae642159e8761ae9f8fb0853b193c0d3db7565
- a8e856a69c9eb0074a418c67d575b91b49caea488574529a40e3b129cefde689
- b438c81b2ada4914b77fb936ca70aa4fa1cb4cb6867c2171e9d21989a4419350
- bd48756252ebf449627761f36c813dde9d57c0cdb82210e864afe4530353a362
- c0c3c539411f9d602316f053a8c68bc78461be9c7b305107c2da072ebe1384a6
- c77196231630b535ef5f0d46f78b7be22a27954daf395065b8f448829bcbbdff
- caa71fe55c039c34b917a568a5325dee1ab6bbd7e343672b23dd3a498b2c21c6
- e8f63eab9292aeb9f3b6adb62df6eb338ff28ff06faefa7fbbeae10e7e04927b
Coverage

Screenshots of Detection ThreatGrid
Umbrella
Malware
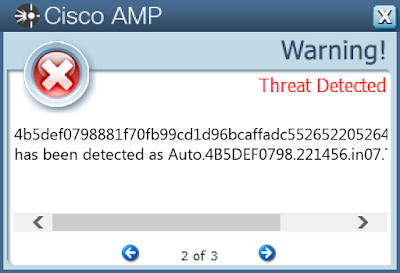
Win.Malware.Zusy-6822787-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %System32%\config\SYSTEM
- %System32%\config\SOFTWARE
- %System32%\Tasks\Update
- %LocalAppData%\Temp\A1DE8592.tmp
- %LocalAppData%\Microsoft Help\restewbes.exe File Hashes
- 066d2ec864546e803031799ceb753c0729fd3fea5fee39ea32c7663cbc49ac4c
- 0acd289c882b13ee2ab19fc065e675257f1be2795c5a9335db1be072b91137cc
- 131c42eed549e4ac2995b6490cf5850e8713c7cacd3a5f6e8e0663d6e66a8bdb
- 17ee81bccd57621bfaf7da158b68c11da1d3fd633f632ee1505823b022b7aeaa
- 1deea19fa1060fdd6c5be36b6e8fd0dab37d17f4bf8e3adc418d4a28bc2e7753
- 1f794910366228e4e66c3accd298d7159de6709370060edab157dceff6366fd9
- 383c76d17194d3f95579b607f472f8b7eeef27280ab71f17c13f6d02c5e9891d
- 4292bb14f28f0b6c2caf51f765a2c923caf4ff23f4ded0d791859b295cd8ca6f
- 47b371a3cdeb0aff41456ba7597044a01f1aaac1ede2070fe6549b1cbda78f39
- 4b5def0798881f70fb99cd1d96bcaffadc552652205264a6a14b7661dd5c260f
- 5189b875f1f85c6b6d6ae3cc6d2922df8d8126269c32904e66af2f93081cb0f5
- 51ef4bd2753e8ca2eefcf0c106110bb5e0191270ba94852d0df9267e7545535d
- 558980fb1ae5ebef3efab8dfec1659a0407b243e3ea80ce9206cdbb821e8307a
- 5664f44cf690e8084108f87f63ec9485cf7197846eed744a0e6d5a9a50b727e3
- 5aabbed6b1e0973a02a33e35317b8acd09902b009c2bd6d1826098c1399ca1b8
- 5fbe5fa066cb326ad3449dda72d41c3f7c13e7e53994f8783c398cf50b565bbb
- 5ff9243d8d9d9d91a0b808e5a48e49577673a7bc490ff2d932c95ad97861e260
- 6e0e7073accb6f820d47af977f502ae090c9a485a01e2f4844fa23b630aba3b5
- 7df09dd5811ae5b81ff5a7b8f24058fde4d4033774733b9c944f9333636eca4a
- 7eabab9ef1146639dc2c5ff6b81745741483a62df6453386f045f5ac011e2fbd
- 82b95a38e9b61a85ef38b821f1f061bf2e089f21e53b39a76b040358f0803c5f
- 8a61accd073ef7868fdfed4e18833f8edcfca716afac37cec88e03130617d3ca
- 8eb4332282fde7742e91f4e4652842d95e953e9921b0580a17e2f9fa70a0bcf3
- 8f3b61b93e8f2a2e5c20cfd9dfefd836ab5fc1fff5e60bba7e4d291c190afb87
- 92c07c6c53d2eceba6b5563c6b701b10a5d74af3e82f06e7caddeb5e74ae7f0f
Coverage

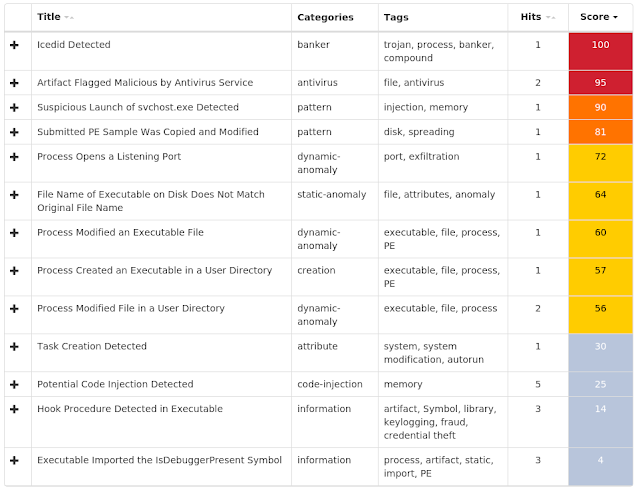
Screenshots of Detection AMP
ThreatGrid
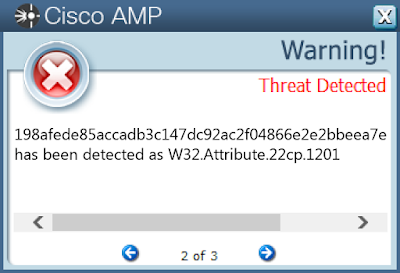
Win.Malware.Ursu-6822222-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\ibpvucix
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: Type
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: Start
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: ErrorControl
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: DisplayName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: WOW64
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: ObjectName
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: Description
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
- Value Name: ImagePath Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 216[.]239[.]34[.]21
- 255[.]255[.]255[.]255
- 239[.]255[.]255[.]250
- 69[.]55[.]5[.]250
- 68[.]178[.]213[.]37
- 172[.]217[.]6[.]196
- 66[.]218[.]85[.]52
- 66[.]218[.]85[.]151
- 212[.]82[.]101[.]46
- 104[.]47[.]2[.]33
- 74[.]6[.]141[.]40
- 74[.]6[.]137[.]65
- 98[.]136[.]102[.]54
- 5[.]9[.]32[.]166
- 46[.]4[.]52[.]109
- 208[.]71[.]35[.]137
- 98[.]137[.]159[.]25
- 74[.]6[.]137[.]63
- 176[.]111[.]49[.]43
- 85[.]25[.]119[.]25
- 144[.]76[.]199[.]2
- 144[.]76[.]199[.]43
- 98[.]137[.]159[.]26
- 104[.]47[.]44[.]33
- 172[.]217[.]197[.]27
- 66[.]218[.]85[.]139
- 67[.]195[.]228[.]141
- 212[.]227[.]17[.]8
- 98[.]137[.]157[.]43
- 208[.]76[.]51[.]51
- 144[.]160[.]235[.]144
- 104[.]47[.]9[.]33
- 98[.]137[.]159[.]27
- 43[.]231[.]4[.]7
- 194[.]25[.]134[.]72
- 213[.]209[.]1[.]129
- 188[.]125[.]73[.]87
- 64[.]136[.]52[.]37
- 193[.]201[.]76[.]57
- 98[.]136[.]101[.]117
- 67[.]195[.]229[.]59
- 98[.]137[.]159[.]28
- 74[.]208[.]5[.]20
- 74[.]208[.]236[.]137
- 104[.]47[.]10[.]33
- 192[.]0[.]47[.]59
- 216[.]146[.]35[.]35
- 74[.]6[.]137[.]64
- 208[.]76[.]50[.]50
- 144[.]160[.]159[.]22
- 82[.]165[.]229[.]15
- 40[.]76[.]4[.]15
- 67[.]195[.]229[.]58
- 8[.]20[.]247[.]20
- 89[.]39[.]105[.]12
- 213[.]180[.]147[.]146
- 68[.]114[.]188[.]69
- 203[.]138[.]180[.]240
- 195[.]46[.]39[.]40
- 199[.]212[.]0[.]46
- 157[.]240[.]18[.]174
- 167[.]181[.]46[.]232
- 109[.]69[.]8[.]51
- 212[.]77[.]101[.]4
- 209[.]85[.]203[.]26
- 17[.]133[.]229[.]14
- 17[.]133[.]229[.]13
- 17[.]57[.]8[.]135
- 17[.]57[.]8[.]138
- 17[.]57[.]8[.]136
- 17[.]178[.]97[.]79
- 17[.]172[.]34[.]70
- 216[.]40[.]42[.]4
- 17[.]142[.]163[.]10
- 195[.]4[.]92[.]217
- 173[.]194[.]76[.]27
- 117[.]46[.]9[.]103
- 157[.]240[.]18[.]63
- 142[.]169[.]1[.]45
- 64[.]233[.]166[.]26
- 87[.]240[.]190[.]68
- 87[.]240[.]180[.]136
- 172[.]217[.]192[.]26
- 207[.]69[.]189[.]229
- 104[.]47[.]53[.]36
- 69[.]168[.]106[.]65
- 104[.]44[.]194[.]232
- 104[.]44[.]194[.]236
- 168[.]95[.]5[.]113
- 168[.]95[.]5[.]218
- 207[.]46[.]8[.]199
- 70[.]169[.]223[.]215
- 168[.]95[.]6[.]60
- 85[.]13[.]131[.]232
- 208[.]80[.]206[.]91
- 204[.]96[.]26[.]100
- 94[.]229[.]138[.]130
- 79[.]96[.]161[.]121
- 66[.]175[.]131[.]136
- 204[.]246[.]122[.]94
- 74[.]126[.]144[.]79
- 212[.]159[.]9[.]200
- 52[.]206[.]51[.]15
- 185[.]164[.]14[.]22 Domain Names contacted by malware. Does not indicate maliciousness
- t-online[.]de
- sbcglobal[.]net
- myway[.]com
- searchsingleshere[.]com
- emig[.]freenet[.]de
- charter[.]net
- ff-ip4-mx-vip2[.]prodigy[.]net
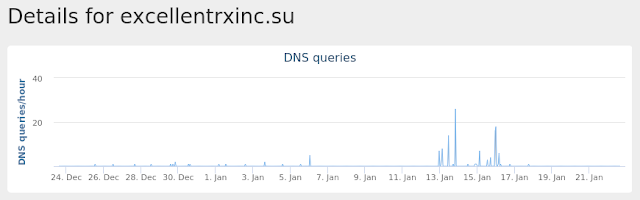
- excellentrxinc[.]su
- freenet[.]de
- fastonlinevalue[.]com
- ev1[.]net
- cableone[.]net
- globetrotter[.]net
- relay[.]globetrotter[.]net
- bexldo[.]net
- e-timetoroar[.]net
- genericpillsinc[.]com
- buziaczek[.]pl
- rulovers[.]cn
- karina[.]rubeauty[.]cn
- kristina93[.]loversru[.]cn
- bestprivateinc[.]ru
- bestdrugassist[.]ru
- bestfamilyeshop[.]com
- hb[.]tinkerfcu[.]org
- curingbestvalue[.]com
- fastfastvalue[.]su
- fastpharmeshop[.]com
- acninc[.]net
- curinghotsale[.]su
- fastgenericsdeal[.]su
- goodbestdeal[.]su
- globalcarestore[.]su
- fastremedymall[.]ru
- ameritech[.]net
- classoneequipment[.]com
- chiclleida[.]com
- ferbravo[.]euskalnet[.]net
- scan-associates[.]net
- condor2[.]telapex[.]com
- commonhouse[.]net
- codasoundusa[.]com
- newonthenet[.]net
- e-wholesaler[.]net
- cgce[.]net
- chopanov[.]com
- westbournehouse[.]w-sussex[.]sch[.]uk
- spideroak[.]com
- cfw[.]me[.]uk
- banking[.]achievacu[.]com
- lucky-star[.]com[.]pl
- franjadeponent[.]net
- coffincheatersmc[.]org Files and or directories created
- %WinDir%\SysWOW64\config\systemprofile:.repos
- %WinDir%\SysWOW64\config\systemprofile
- %WinDir%\SysWOW64\ibpvucix\
- %LocalAppData%\Temp\gphgpbfw.exe File Hashes
- 06331cb6eb8673a49614b3cf67f302cf7a3b5ea18b8bb7d004884cea8f196a83
- 15ce5b3be486d7fe23f3115531ed6642587e3dff9bbfb5fef43ece0ed0cdb3f4
- 198afede85accadb3c147dc92ac2f04866e2e2bbeea7ec1333f73e6a8d76a04d
- 20edb680512a8741667e2652de74649da18542399acdd8dbdc9bc7121f422f40
- 23c8d65f46d2aeb395e25e63dcf0d417703f7a54b501fb40aebc554061384bfa
- 25f41a5ebb1175763d5eeb509a9b2fe559fdfd94a0d1a4736b7b766f9ba6363b
- 2c224aa21be4c3f8bce2e13c0ddb04ce5ec9cdc1480c172d5e0e4e15fdee2c44
- 2e889d267181a338b3c100a69417ee0a145820ab2aea59939d8bb6ccf56f3aef
- 3223a9b86a93b8869b44d7d8d2a7e98de99ddd0e1a5050dd7d708c087f18458e
- 32d7daae4063be4c3cf70d4cb43f0079d53c66170edbcba8282da98d49a7dbbe
- 33def1029bdf7c6675d05d5f224749026a32717392ef848bb0a35b7d6a8f29b9
- 40ad8820abac31fcf2219adb68218cb93765895995cb66f50dca15908d364752
- 471866dd10a5be75f2119d718325aa4026ed267bae3ad29cb08cec747b11e4ea
- 49f79b464c4130f0ff3a0c2b0d3336b0f6b8f51f56164f21b5ca7315424ea39e
- 536c227b86419e3a60bc53b317001b6b8cb9894215a8431542867f4fd10f98ec
- 53802104e558d3689a2f99347a69302fd459ee82615428cde09c28b4f7543541
- 54064cacc8929ef3581370dd311be773d6f3cc45fab81d3a37552b1e854b770d
- 61cfcad8b188a5dda449b76b070092eaa48ecad62c059b4795d3bcbb1e9581e6
- 66ed081ce04cc7e9b321695e153f237f0f430a1dd103e719c8a3812afe148455
- 6fb3f86955fd966f04ede90e33d2b9ae749b7b44a0a5fea78dca6a66387b5b92
- 747cae3430aeeecc86f846ba3bcaad9645ac6a6c0cedc5c027c2b8b3ad1d561e
- 75d9e8e6bc72e53881b4b8cd9daba1c13da9761cfafa560f57410ec8078ad675
- 7e08971c510b3fd9d85876a9a057ba601c38da13173bbda1abe54e05074b22b1
- 8a0b4a3b97122043e1ab8225b331fc4069ba150a275bc77316abc23841feda69
- 8c3de5bbdd6542a6d0c828764b1f47a37a4cad07834bec2fc9c7ac31316834f0
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella