Today, Talos is publishing a glimpse into the most prevalent threats we've observed between Feb. 01 and Feb. 08. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
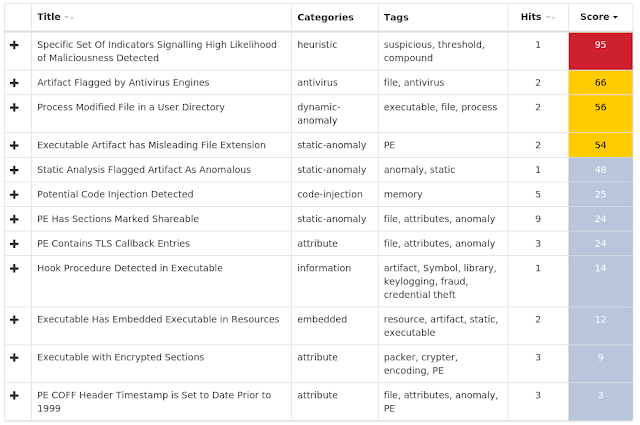
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
- PUA.Win.Adware.Softpulse-6848587-0
Adware
SoftPulse is an adware that installs malicious software, leverages anti-virtual machine techniques and may access potentially sensitive information from local browsers. - Doc.Downloader.Emotet-6846065-0
Downloader
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails. - PUA.Win.Adware.Razy-6847375-0
Adware
Razy is oftentimes a generic detection name for a Windows trojan. This cluster of samples contains encrypted code in the resources section that could be injected to a legitimate process. - PUA.Win.Trojan.00519ead-6847245-0
Trojan
PUA.Win.Trojan.00519ead is the denomination of a set of malicious adware samples that could leverage the AppInit DLL technique to achieve persistence and perform several DNS queries. - PUA.Win.Adware.Sanctionedmedia-6818436-0
Adware
This cluster includes .NET adware samples capable of code injection, opening a port to listen for incoming connections, disabling system restore, modifying files inside system directories, contacting blocklisted domains, modifying the registry and, in some cases, even copying itself to USB drives. - Win.Ransomware.Gandcrab-6843341-0
Ransomware
GandCrab is ransomware that encrypts documents, photos, databases and other important files using the file extension ".GDCB", ".CRAB" or ".KRAB". GandCrab is spread through both traditional spam campaigns, as well as multiple exploit kits, including Rig and GrandSoft.
Threats
PUA.Win.Adware.Softpulse-6848587-0
Indicators of Compromise
Registry Keys
- <HKLM>\SYSTEM\CONTROLSET001\CONTROL\NETWORK\{4D36E972-E325-11CE-BFC1-08002BE10318}\{9EB90D23-C5F9-4104-85A8-47DD7F6C4070}\CONNECTION
- Value Name: PnpInstanceID
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: ProxyBypass
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONEMAP
- Value Name: IntranetName Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Namescontacted by malware. Does not indicate maliciousness
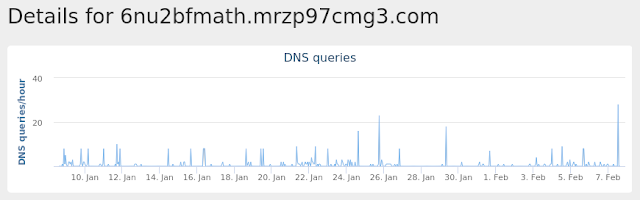
- 6nu2bfmath[.]mrzp97cmg3[.]com Files and or directories created
- %LocalAppData%\Temp\~DF38A714DABA77BAE2.TMP File Hashes
- 1a74519d1568dece3bc64889f177df271b1bf93c0db86d97bb81e44a45403c2f
- 1a93550fd9e061d7b572ca6269934ae5d0747e82855420895d41547680e372b7
- 1e8a9c8f07050897420bccfc612fe39dc11acec47dbb11a9b6d17876c0f1c748
- 22db5127ccb49f274ab3f46f6a845bcbe693e2ed4069220c9b33c4ba7cb6e7db
- 2da64c580965f9d0454b9004181ed7fdd5903e93cc41d06578cc968ac4215836
- 30ff57307b5d4456c64ee80eaacb717cdc1804c1f1c49409c7d583ec9f3de1e3
- 3ff2a4f01f7bfc31db3a54ecb98c0df737cd575cc11301af3b19ed99bc0e075b
- 473f7dd0173bafa5de751493de7c7e2cc57fc290aac0ae4d2947cc57dcb8008d
- 5492869d71c62c3ade2750e79de155104329cc08fdd9e65f9ba7d213868714c8
- 54d8cb379579ab2063b223f0011d8fa2838368b4b68f070a54b7e06ca62c1f03
- 5b5c9fd28470e81d23fcd6e5b2ea1bdf7c537ca610535d2f69a23fbd11f8d0cb
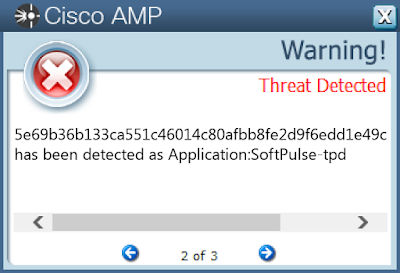
- 5e69b36b133ca551c46014c80afbb8fe2d9f6edd1e49cebcd22ca7bbec82d9ff
- 6e43c79b858a27b93c87498faba5f60edd11d6472da142229bef6fb1d1310372
- 78ca808e8428963d80d651655c6f79c8df44448a0d0613eb442a20a3081d0b21
- 7db57b97495b59e84bca9e7f48b472e7412751b20780f17f453e4cf8c9694543
- 7fbd028726e320fddbf67a00ac1a43e8d2f7fdc98dcb53c84fbbd77871c88afb
- 881497c1db786286caae56f5055909c1bba6ccb24628773805f0f3a3a91c0993
- 8a70ba0afe5efa6f633d97f51043d6be2ff3b3a2e6c5fba979f88a6bce4813e3
- 92fbd91b969e6f94853430cb11a7ab2eaeaa05faefd2856a4aa55861f035beb0
- 93b2e125a810723a7bc4e268dccbd784cd95e593077ae59fd9ac4daa9e1a8094
- 99b1320bd421b716118e2aa11ff0044be4bb8849f96b099c6d7ff106ad80833b
- 9ec1af22463376ceaf3468b88b000a155aa674ff27910c4a2d7188fb4ed5b315
- a0ea6c233f4da2e161eb3108b9534d297cb15ec8d17eaf2d22132b0e67e99c4a
- a1caca2e8b3b96935fcde41509753f4531ec3b9c5f436c7291c422fdf4c1d7ec
- b2917e4031446976cdba6958df9d7c2d594f657232e0786b0e39039477b13534
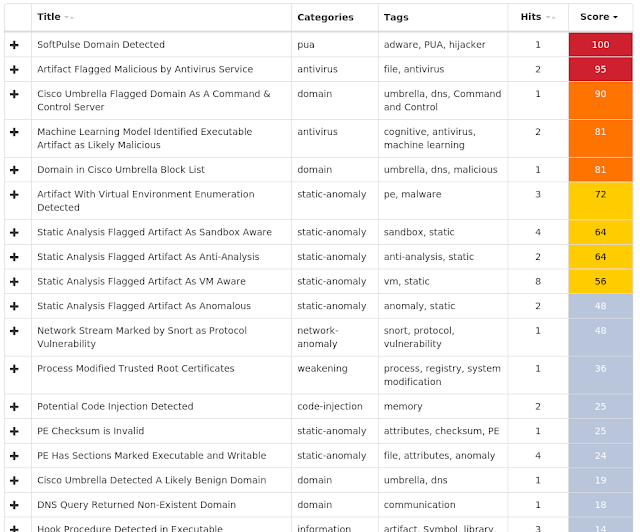
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella
Malware

Doc.Downloader.Emotet-6846065-0
Indicators of Compromise
Registry Keys
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyEnable
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyServer
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyOverride
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: AutoConfigURL
- <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: AutoDetect Mutexes
- Global\I98B68E3C
- Global\M98B68E3C
- Global\552FFA80-3393-423d-8671-7BA046BB5906
- PEMD4
- PEM19C
- PEM4F0
- PEM240 IP Addresses contacted by malware. Does not indicate maliciousness
- 177[.]11[.]50[.]52
- 195[.]201[.]46[.]139
- 216[.]119[.]181[.]170
- 71[.]78[.]24[.]146
- 217[.]78[.]5[.]120 Domain Names contacted by malware. Does not indicate maliciousness
- estacaogourmetrs[.]com[.]br
- www[.]intelhost[.]com[.]br
- restauranthub[.]co[.]uk
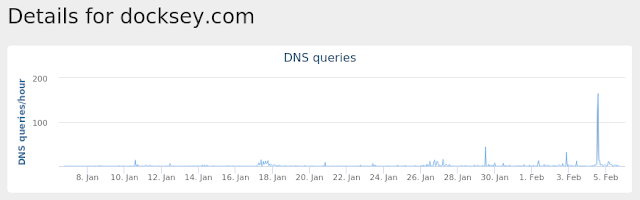
- docksey[.]com Files and or directories created
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{B106E8EE-597B-49CA-A6A4-5BA8ABCC8F6A}.tmp
- %SystemDrive%\TEMP\~$LE1922193.doc
- %LocalAppData%\Temp\CVR3B09.tmp
- %LocalAppData%\Temp\~DF0EC263132EE87D9F.TMP
- %LocalAppData%\Temp\~DF93E860FA48DCAA9A.TMP
- %LocalAppData%\Temp\~DFCEAA78F57CC3DA47.TMP
- %LocalAppData%\Temp\~DFDE0E179FA1A94A5D.TMP
- %AppData%\Microsoft\Office\Recent\FILE1922193.LNK
- %LocalAppData%\Temp\p24is3bq.j0q.ps1
- %LocalAppData%\Temp\zjkgwiwg.sq0.psm1
- %UserProfile%\Documents\20190204
- %UserProfile%\Documents\20190204\PowerShell_transcript.PC.0Py_SQrs.20190204204359.txt
- %WinDir%\temp\putty.exe
- %AppData%\Microsoft\Office\Recent\366814370.doc.LNK
- %TEMP%orary Internet Files\Content.Word\~WRS{E2A82E27-8296-44EC-B019-FE52D18D73F1}.tmp
- %SystemDrive%\~$6814370.doc File Hashes
- 03591121dcf83a4aeb5e5fa12a1c1b75c93f5a215780eb1ebf209cc9518f12d3
- 04c6555af6871c7818d3df3f0d5bbf9b85efac94e979c58234310b9a36079e78
- 09be75647f21e12c0c4948ed45c68eb1db6667beece4e1d9748cddd5b4c38eaa
- 15968dcbcb0514e7fd5bb68ced13112a3f1d8b31cd948b967f3becce9283508a
- 1920f3315544295d13a8c3366216b74514369bb31cea90a4659506c0c4c549a1
- 1a4c6a9c9e4bcce9f83776f87f158d39cb21eb78ea839afaa01abf3f93c49a4c
- 1a7211b1d27124d3409b2d1346ba93fc2a91fd00ed3899c95c1e16fc849c54a7
- 1e83dfa18cc1ccff50dd5118f710bcc16e6c4e178977435c62b4238554bcf7f4
- 2287689165547b27ed983152dd781bc53777060a8dd911b18671b60509329ebf
- 247adbdf9950ad6e592f0276ae72625818f87b41ce1bb7596aa89181e0ce99d4
- 267af9baaa1401ae4034200940bad6c1f8cb622a7e731ed28fe84fe0682a6616
- 3bc75dd152bea2d4670d22e2844731646cc4a83024a3cd2349d465d5c16020ef
- 607f94f56ab7d2e2b01a0b8ee0bed7379144363d65e3040f44a197e8245b842c
- 72da32c1bec496a54885f38802c429bc1aed434651bc67dc4acbac637c0c94ce
- 76b02247cf6c9a6c436532a536ccd2711fa876c15312dd6e0b3863e070e8595c
- 7fb24419176dd9aa58bb53a4246398d40c260c253b4772cb8fdc600324f24318
- ad6b9cb00268157013c2b547a379a836609f5c7e01ce6893df16cf1db8fd3965
- af8e1169f130baf122b25aae81d95d62cd3506bae39673652d91ac4c4936049d
- b5d83480ad61ce204743ef0904cbd2995991944efd3d0d2c9daaca9385f4b290
- b9cbad9b3cd4a1f08c3284d479ff40093454e9f76d23783901087cd0add5d468
- fd46fb328e72ebe81cb97846b846051a95d2012630a3ee37bf55002c3908883e
Coverage

Screenshots of Detection AMP
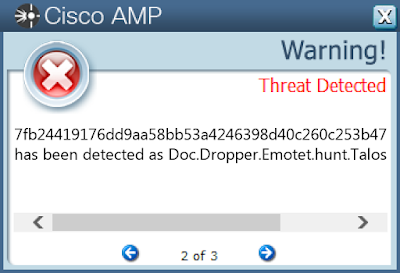
ThreatGrid
Umbrella
Malware
PUA.Win.Adware.Razy-6847375-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Local\MSCTF.Asm.MutexDefault1
- Local\RstrMgr-3887CAB8-533F-4C85-B0DC-3E5639F8D511-Session0000
- Local\RstrMgr3887CAB8-533F-4C85-B0DC-3E5639F8D511 IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- %System32%\drivers\etc\hosts
- %LocalAppData%\Temp\is-51KNV.tmp
- %LocalAppData%\Temp\is-51KNV.tmp\09131ddb2cac0b4d4483b4bbbc76a26f244ab5a884350f733e1f60fc684da039.tmp
- %LocalAppData%\Temp\is-9EHP6.tmp\_isetup\_isdecmp.dll
- %LocalAppData%\Temp\is-9EHP6.tmp\_isetup\_setup64.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-CA60C.tmp\367042276.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\Asian.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\Asian.exe.config
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\FallOffLone.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\FallOffLone.exe.config
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\_isetup\_isdecmp.dll
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\is-0J9ED.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\is-D4UQV.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\is-ECQFB.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\is-JAN27.tmp\is-T0KA5.tmp
- %ProgramFiles%\Luckey\213384307.exe
- %ProgramFiles%\Luckey\213384307.exe.config File Hashes
- 09131ddb2cac0b4d4483b4bbbc76a26f244ab5a884350f733e1f60fc684da039
- 3c6a39eee1d6b61e2c1d94332b55819182bc189fcdbe06d79bcafa2ea0febc43
- 47d1bd0892f91a1c65f5e6f06fe6969cd8db1f1473760c23e668ac1cb831bc7f
- 4e5e5d3bea988e7c39542245f3a1bc1046153ebefc18ee0b4d743dd8b2f93e28
- 51c839a1fe25c31ba3903cc47f32880741dd1e708c9e97c81a2ea050802f84db
- 68b15033f398389c45903085677e375dcaed3a3225d0854f6cbb5a2b45217cb7
- 6985e3313e82b8cc6b450bb4cb6fcdebfc1b26ec83b0ace499c836d79b0b4fbe
- 72a1cb206beae974f8d3504128e7892ba6fcbba38f31d7714f0fd811618bb439
- 7384060612fcb8c40a324c136c571295f361a2e6d7f5b470206b574aed5fe0f4
- 817ee49531f980991336c020e3d99f67796a38ff88aff948f07f658b083e6801
- 888888ec0980085d2a89f43fc32f543dfbe283d7ad0186e5c1089a08795d86b8
- 9d6c6642a75a6328ef321212b482519ef74c767d9a02d1538debc53f031ee293
- b0d1ef5415c13028a6fbe16900e255b599781bf3824144413f9364e619480194
- bb87882c8e8c87e3f0f2accf837d141550fc0a048409b6c0a4aaec4b9829f1a0
- fa64e7db69b070ef8bad8046cd7539dd1fca1bb63349f04c0e94584cf0a2a7d7
Coverage

Screenshots of Detection AMP
ThreatGrid
Malware
PUA.Win.Trojan.00519ead-6847245-0
Indicators of Compromise
Registry Keys
- <HKCR>\LOCAL SETTINGS\MUICACHE\3E\52C64B7E
- Value Name: LanguageList
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
- Value Name: AppInit_DLLs
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
- Value Name: LoadAppInit_DLLs
- <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
- Value Name: RequireSignedAppInit_DLLs Mutexes
- {5312EE61-79E3-4A24-BFE1-132B85B23C3A}
- {66D0969A-1E86-44CF-B4EC-3806DDDA3B5D}
- Local\RstrMgr3887CAB8-533F-4C85-B0DC-3E5639F8D511
- IsoScope_10c_IESQMMUTEX_0_274
- IsoScope_10c_IESQMMUTEX_0_519
- IsoScope_10c_IESQMMUTEX_0_303
- IsoScope_10c_IESQMMUTEX_0_331 IP Addressescontacted by malware. Does not indicate maliciousness
- 13[.]107[.]21[.]200
- 104[.]200[.]23[.]95
- 204[.]79[.]197[.]200
- 209[.]197[.]3[.]15
- 188[.]72[.]202[.]44
- 34[.]226[.]238[.]42
- 158[.]69[.]244[.]165
- 212[.]32[.]250[.]31
- 144[.]202[.]40[.]125
- 104[.]16[.]13[.]194 Domain Names contacted by malware. Does not indicate maliciousness
- maxcdn[.]bootstrapcdn[.]com
- 5isohu[.]com
- done[.]witchcraftcash[.]com
- thegoodcaster[.]com
- www[.]theoffertop[.]com
- myecomworld[.]net
- wonderfulworldnow[.]club
- images[.]clickfunnels[.]com
- tac25[.]com
- track[.]rightsearchsmooth[.]club Files and or directories created
- %LocalAppData%\Microsoft\Internet Explorer\imagestore\aowwxkh\imagestore.dat
- %LocalAppData%\Temp\A1D26E2
- %LocalAppData%\Temp\update.exe
- %LocalAppData%\Temp\~DF32A074D75E28FF74.TMP
- %ProgramFiles% (x86)\Internet Explorer\IEShims.dll.tmp
- %ProgramFiles% (x86)\Internet Explorer\ieproxy.dll.tmp
- %ProgramFiles% (x86)\Java\jre7\bin\ssv.dll.tmp
- %LocalAppData%\Temp\~DF832EC54C42A76DA7.TMP
- %AppData%\Microsoft\Windows\Cookies\2XVNLMCY.txt
- %LocalAppData%\Temp\is-0UA26.tmp\idp.dll.tmp
- %LocalAppData%\Temp\is-B01CK.tmp
- %LocalAppData%\Temp\is-B01CK.tmp\c1f44c795198b23f8058492bb82a29addd2eeae623a53296f0195777d6a5fde5.tmp
- %LocalAppData%\Temp\A1D26E2\116E56C6A8.tmp
- %LocalAppData%\Temp\is-0UA26.tmp\_isetup\_setup64.tmp
- %LocalAppData%\Temp\is-0UA26.tmp\idp.dll
- %LocalAppData%\Temp\is-0UA26.tmp\itdownload.dll
- %LocalAppData%\Temp\is-0UA26.tmp\psvince.dll
- %LocalAppData%\Temp\~DF12E5A698F292B5F8.TMP
- %AppData%\Microsoft\Windows\Cookies\YO092G24.txt File Hashes
- 06386d249ae1b3cc4bc96281ae89e10a85f68dd7e350e3e52fab4c88a7c02375
- 1e81d5888f17947bcbe31a74b3761c31c4fd6b49cb02d3eb4f85e065d8729e08
- 298b8e26c83ba9fd1bb1faeb5b0df909f1d163e7896e26c48d35e041aae6320e
- 641432c889189c393edf97cda9b08e5b083cbb8eecc5ac09b9d476f8872ecf3b
- 6fbe635039debcb4eccf4d9c24cf009b8405fbe8cf9fcc5c5f24d0ca8bffd53a
- a073171d46e57c4e308b6a62c0d14e597e95c030c019f428a26ee6c07f43557d
- a5b2ea50f8dceec4752888c5e50e364b16253160dd7fb20932d8e5e5a56ac719
- c1f44c795198b23f8058492bb82a29addd2eeae623a53296f0195777d6a5fde5
- c488c9a61f7be3a4e7b9c51dbefa36c2fe7b53904d30c38f58dcc1900aec098b
- c72e78abc54e7b785e666e0e61181c107a4cf6b9c0519146f9f2b9fbf47ba841
- f1aa892c158ea1779a210d52b9a4311245544868343d27c91454566d730aa4ee
Coverage

Screenshots of Detection AMP
ThreatGrid
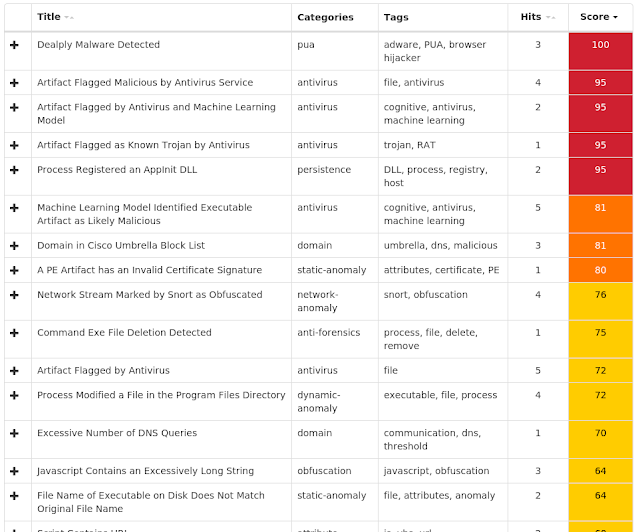
Umbrella
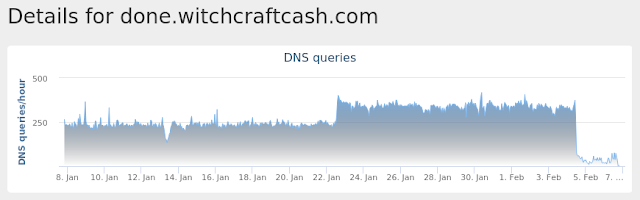
PUA.Win.Adware.Sanctionedmedia-6818436-0
Indicators of Compromise
Registry Keys
- <HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\appsvc.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rstrui.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avconfig.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AvastUI.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avscan.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\instup.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbam.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\mbamservice.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\hijackthis.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\spybotsd.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avcenter.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avguard.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgnt.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgui.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgidsagent.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgrsx.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avgwdsvc.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\egui.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\zlclient.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\bdagent.exe
- <HKLM>\SYSTEM\CONTROLSET001\SERVICES\SCHEDULE
- Value Name: Start
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\keyscrambler.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\avp.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wireshark.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ComboFix.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MpCmdRun.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\blindman.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDFiles.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDMain.exe
- <HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SDWinSec.exe
- <HKU>\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
- <HKU>\Software\Microsoft\Windows\CurrentVersion\RunOnce
- <HKU>\Software\Microsoft\Windows\CurrentVersion\ime Mutexes
- Global\CLR_CASOFF_MUTEX
- \BaseNamedObjects\Global\.net clr networking
- RV_MUTEX
- \BaseNamedObjects\RV_MUTEX IP Addresses contacted by malware. Does not indicate maliciousness
- 158[.]69[.]30[.]89
- 188[.]70[.]31[.]241 Domain Names contacted by malware. Does not indicate maliciousness
- x11[.]zapto[.]org
- sambosaxzx[.]ddns[.]net Files and or directories created
- %SystemDrive%\AUTOEXEC.BAT.exe
- %SystemDrive%\boot.ini.exe
- \??\E:\$RECYCLE.BIN.exe
- \??\E:\$RECYCLE.BIN
- %LocalAppData%\Temp\xkkr5i_9.out
- %AllUsersProfile%\miner
- %AllUsersProfile%\miner\sHXJvbCG.ico
- %LocalAppData%\Temp\xkkr5i_9.0.vb
- %LocalAppData%\Temp\xkkr5i_9.cmdline
- %LocalAppData%\Temp\xkkr5i_9.tmp
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\Torrent.exe
- %SystemDrive%\miner
- %SystemDrive%\miner\nvidia.exe
- \??\E:\miner
- \??\E:\miner\nvidia.exe
- \miner\nvidia.exe
- \$Recycle.Bin.exe
- %SystemDrive%\Documents and Settings.exe
- \Documents and Settings.exe
- %SystemDrive%\Recovery.exe
- %SystemDrive%\366832936.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\RESE.tmp
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\vbcF.tmp
- %TEMP%\_ecw9cm3.0.vb
- %TEMP%\_ecw9cm3.cmdline
- %TEMP%\_ecw9cm3.out
- %TEMP%\n02x2nc3.0.vb
- %TEMP%\n02x2nc3.cmdline
- %TEMP%\n02x2nc3.out
- %TEMP%\nyf8h2nv.0.vb
- %TEMP%\nyf8h2nv.cmdline
- %TEMP%\nyf8h2nv.out
- %TEMP%\q8tnr4an.0.vb
- %TEMP%\q8tnr4an.cmdline
- %TEMP%\q8tnr4an.out
- %TEMP%\rykc4pie.0.vb
- %TEMP%\rykc4pie.cmdline
- %TEMP%\rykc4pie.out
- %TEMP%\yjua3drf.0.vb
- %TEMP%\yjua3drf.cmdline
- %TEMP%\yjua3drf.out
- %SystemDrive%\Documents and Settings\Administrator\Start Menu\Programs\Startup\ Torrent.exe
- %SystemDrive%\I386.exe
- %SystemDrive%\IO.SYS.exe
- %AllUsersProfile%.exe
- %AllUsersProfile%\miner\366832936.ico
- %AllUsersProfile%\miner\CONFIG.ico
- %AllUsersProfile%\miner\IO.ico
- %AllUsersProfile%\miner\MSDOS.ico
- %AllUsersProfile%\miner\NTDETECT.ico
- %AllUsersProfile%\miner\boot.ico
- %AllUsersProfile%\miner\ntldr.ico
- %SystemDrive%\RECYCLER.exe
- %SystemDrive%\Temp.exe
- %SystemDrive%\Users.exe
- %SystemDrive%\c2d124b8466cec6b3e47c4.exe File Hashes
- 0489f71417400080c1ebf6f5cf76655470a83f0f964a2ad54c242daf3012fa7a
- 0e15e99295dcf13eae0d5a4d7a04a55f7fab24e8f189f5ac37cc1007346007ad
- 1127cc0f06797cd128aa3724b5ecead3613c41fabebd143fcbf19a8d236a8fef
- 137b894b7f9992f26dd4e6c8d8c2a09e886466305384b444aac2e2d9e3ee7a19
- 1f5b1a8b9f7fb4d83bbd012d42fdc725468dc0ed29341bee4c5aa122d83f69f2
- 3357239b0cb8a4683eca02fd8bf8c0de9cd3372a2222f096d7b527b39fcf8987
- 372a2fde40ef021834c7d7718f2f2faf63ee372ee75a795ce3ff0e1156c57a8d
- 39bbcd06380d793eb655a015e04ed122d160b6d469495a3b172a89809e5c1c1c
- 3b3db732aa7ea25346da5ac1a4f0cb56357baf265259c9046885f889b56830da
- 3cf72a19a5dbca5da318ca758b07f8c1e729dd3035f1f31223c8c05fa8826faa
- 3f7eb77d67e6a7e2e410993234cc2bf649b3efb311931774e4c5dff3bbfcb1f7
- 43983381c09f51babb1b684db1c0f804c3f00ba6c5159e99bb5a68b32e4718f5
- 4a7bdf882b10e093cb0d82c61e71daaff97971f0cbaf16f61093acdfe149734f
- 4b08ea2461afbf58ef946d1897ee5d4b2873ad2b261db005a85c4aa43ffeca09
- 5a85a897a9e5aabf518bd1ff19339cca80543a90cefdcca5397ac09014fc71be
- 5da2bf905b77f3b9c4d957458cfb9f133860ddfe5dec741aac55bced51184c1c
- 5e01d3fbd260656eaf2eb22631ec30ce8433f8288911ef552855108c773580bd
- 638c303a097d02c40e3790e506234cd36ea4c907166f4447f50e6f92b7429436
- 63af1d420682171b535f222861b3bcc90c4da86363ad94a4b666bf489a245e11
- 66a2ed3db3c55603be3a2ce301cdc71be803b18da51731373a4d23c1d5b0b1a5
- 6e0a7315797b5add6dc3b23abdc8d96d0d43e9470bee64f3f5fd12721acd62f9
- 7051fca8dfa96b8ee78111d72f6945d14f82aceb94f93a891dfe6e5641512b1e
- 71a577218ae440efb0c6b2a624d90a8713e60ab01c525a180c15b5b2b9fa8d4e
- 726787ed97a97d4057caa986bd0956a80ecb446bcbdd9a1c009fb4d1ebccaee2
- 76b63d0d32b961663c20a01bd478d5cb1358eb1441bea38e2cb8e57c36e0ac41
Coverage

Screenshots of Detection AMP
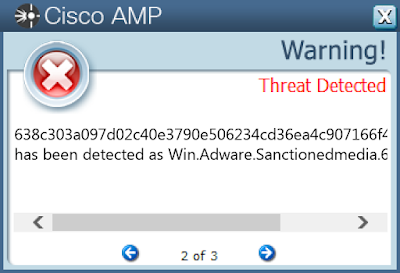
ThreatGrid
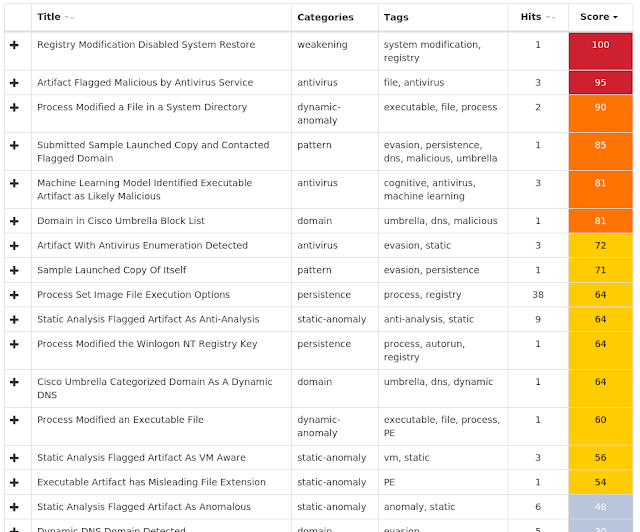
Umbrella
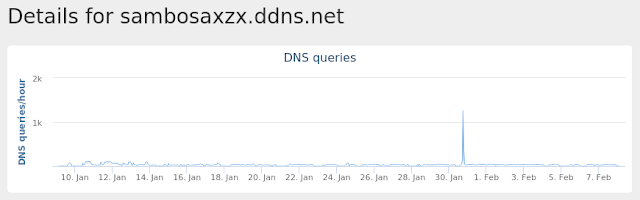
Malware
Win.Ransomware.Gandcrab-6843341-0
Indicators of Compromise
Registry Keys
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyEnable
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyServer
- <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
- Value Name: ProxyOverride
- <HKU>\Software\Microsoft\Windows\CurrentVersion\RunOnce Mutexes
- Global\pc_group=WORKGROUP&ransom_id=4a6a799098b68e3c
- \BaseNamedObjects\Global\pc_group=WORKGROUP&ransom_id=ab8e4b3e3c28b0e4 IP Addresses contacted by malware. Does not indicate maliciousness
- 66[.]171[.]248[.]178 Domain Names contacted by malware. Does not indicate maliciousness
- ipv4bot[.]whatismyipaddress[.]com
- nomoreransom[.]coin
- nomoreransom[.]bit
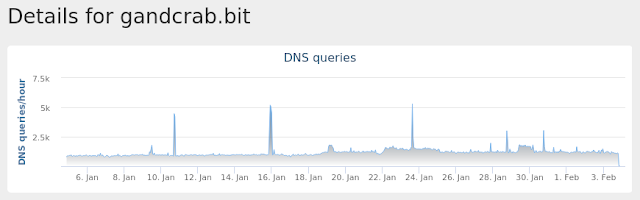
- gandcrab[.]bit
- dns1[.]soprodns[.]ru
- dns2[.]soprodns[.]ru Files and or directories created
- %AppData%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\Preferred
- %TEMP%orary Internet Files\Content.IE5\C5MZMU22\ipv4bot_whatismyipaddress_com[1].htm
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\A71QDCIP.htm
- %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\A71QDCIP.htm
- %AppData%\Microsoft\psznzp.exe
- \Win32Pipes.00000328.0000003d
- \Win32Pipes.00000328.00000041
- \Win32Pipes.00000328.00000049
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\bb5ca9a3-5378-4a8e-8196-42a28d9ef0c9
- %AppData%\Microsoft\hjunhw.exe File Hashes
- 00e77dd692525ac51843e571dc4401ad383b01f3789a96ad952ad46e9bc30d5d
- 01ad099c08042d05bcc5c708aeca7a3479f93def36318469c05b3fe2c25a202d
- 01d3aedbbcfde336cf132fa52fb87f0a39a7e1c55cf8e30e8f79df6fa6cf2a28
- 021f152e82d84617ac2ba999f436fcf85f35c9c17da8f7adff51d6f6c332c63f
- 072a1a933df1fe1e0c90b07b30bf82dcc16fd860e47ac94877c25c05b89a1147
- 087af2abcf44ec68d9f1f55bcbae03e12ff0380ceea4f2197fff9b8d353f417e
- 098af1ba0b5cf4d27f8122eb37bc7ab009be4f6c812e990639931d8504d3619c
- 0d20371ebb39d45616ecdc0ebd1ae457f98641a14c8cd3c94e553fe5cb71e128
- 0e90f5195c0f0c81cd631c90809790490a7a5cac5eae61bf27332b9707f9e3f3
- 0ffd01cae290d5ff33af6dcd087646bf86a065fd02f196b7dd3afe0bb5c08d75
- 103f6e49c97ec73d623231fa92f418032ad223c565a7fadb238cc676a6bee79a
- 110084e96789b6e657a8453d8614c14344e03ca4dac55076afe7ba605a68ca06
- 112dcf3ef406642f9b2459a27dc79f626d28ac93db3482691eda8db3bbafd80b
- 119238f37579434b540e2a4cda59261d86e9a9ac0c059dfd2daf699c5a3e6094
- 1388310e5f683da4ad3e774923c2616a7137dc1da691efea313fccd2a0f88da1
- 1694e9584805e55badf8da9ce6f8b4122e3bf419bfb22070d3e97b83be0caa73
- 17517aac50cfcb9b6cd779f466d6ece0ec930071fc58e7b4b391a8e79a7ef49d
- 1c4b31ea552e67d0e573cc3c4f4c93387e79e931e41742129dcf7b1cdc55d4d5
- 1c700576a51cdbee44a25972503a64ebc9d4fef602b4702fca9eb02e8622a7dc
- 1ced683893408d370315083efe988043cb72a864a03a3ded4a94d047d2bec262
- 1d4f89c1ecd931c4b5cecfba15b76f1d6607417af487654da1d50497bcda1cd9
- 1e1b83c79a5d2ff5ec3ca325debdb29f66d83f362d2bf0ec4e18c6fbafd6c179
- 1eff09710c639869bef51b90404569a7917aa23afdd290c8668e617b1757a231
- 20be9f6a086f07dfc3fbd8a5e6a060e50f360629e428077665980f6e6e401079
- 20c45b4970eddc186e8e77266e5b2282c6faf4d53559482200c4d43404d23f7a
Coverage

Screenshots of Detection AMP
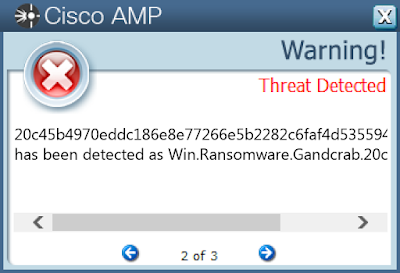
ThreatGrid
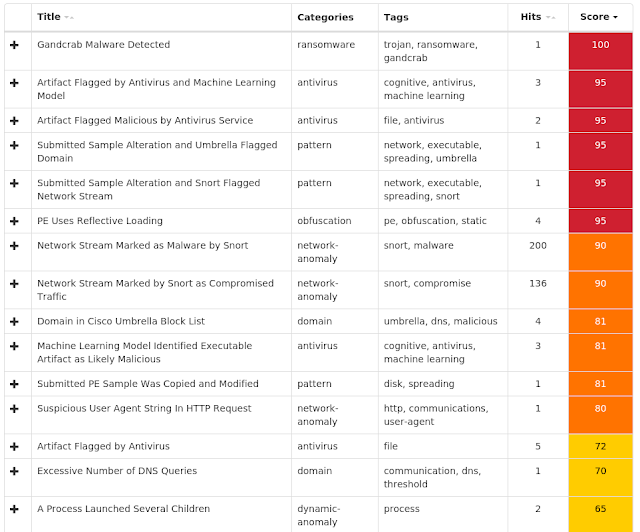
Umbrella