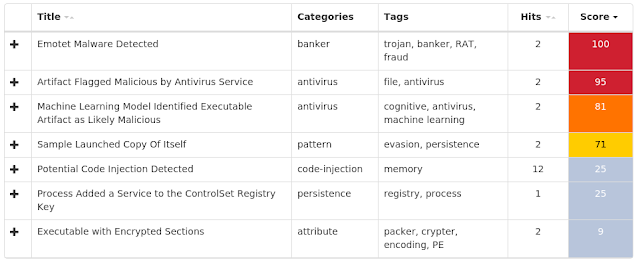
Today, Talos is publishing a glimpse into the most prevalent threats we've observed between March 08 and March 15. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
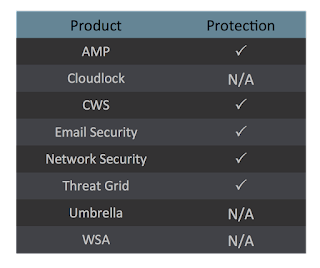
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.
For each threat described below, this blog post only lists 25 of the associated file hashes. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
- Win.Malware.Emotet-6888316-0
Malware
Emotet is one of the most widely distributed and active malware families today. It is a highly modular threat that can deliver a wide variety of payloads. Emotet is commonly delivered via Microsoft Office documents with macros, sent as attachments on malicious emails. - Win.Packed.Bladabindi-6888152-0
Packed
njRAT, also known as Bladabindi, is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes and remotely turn on the victim's webcam and microphone. njRAT was developed by the Sparclyheason group. Some of the largest attacks using this malware date back to 2014. - Win.Packed.Kovter-6888122-0
Packed
Kovter is known for it's fileless persistence mechanism. This family of malware creates several malicious registry entries which store its malicious code. Kovter is capable of reinfecting a system even if the file system has been cleaned of the infection. Kovter has been used in the past to spread ransomware and click-fraud malware. - Win.Malware.Ircbot-6887900-0
Malware
Ircbot, also known as Eldorado, is known for injecting into processes, spreading to removable media, and gaining execution via Autorun.inf files. - Win.Downloader.Dofoil-6887823-0
Downloader
Dofoil, aka SmokeLoader, is primarily used to download and execute additional malware. Read more about this threat on our blog /smoking-guns-smoke-loader-learned-new. - Win.Malware.Upatre-6887803-0
Malware
Upatre is a trojan that is often delivered through spam emails with malicious attachments or links. It is known to be a downloader and installer for other malware.
Threats
Win.Malware.Emotet-6888316-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- Global\I98B68E3C
- Global\M98B68E3C
- MC8D2645C
- MFA4F69B7 IP Addresses contacted by malware. Does not indicate maliciousness
- 82[.]211[.]30[.]202
- 119[.]59[.]124[.]163
- 37[.]97[.]135[.]82
- 69[.]45[.]19[.]251
- 217[.]13[.]106[.]16
- 160[.]16[.]109[.]161 Domain Names contacted by malware. Does not indicate maliciousness
- N/A Files and or directories created
- N/A File Hashes
- 14873aa714a65cf71fc4fcf0b22aeb6d98718e56c6b30abf0b88313abb7096cf
- 2aa82a27cfbd810db7a1989f7a854dcf8f0470854f64cbe5a6e66b426d4f5d39
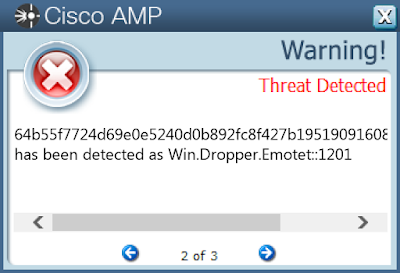
- 64b55f7724d69e0e5240d0b892fc8f427b1951909160821d890860b9502c0184
- 756ce0947db75cee371d64495e3c371a5d81c99191f695568b3fdeadc9c31fb4
- 77c23c37835701bea789493bda50a6270f477407afc5a51766124e0d7d98c183
- 7a5cc102dd6b2a6a6560cd9413915e9a0331bdb94d9614a5ec8231080b1d47a3
- 87c41d1f7fb8539eb5a3c819c89a29d2efdc09c336388b49b4e7ea2fb143a732
- 8953cb59046bb2d303057684612a98c3de56e016d7a47c2b47eaa4dddd254f9b
- a267997c229e0ca3dc27d27bf34c55dab32dfc9c3505cd3dcc1d778badf32fee
- a6eb96882eea810dda7cea793c53d0e1cd651d52287c61f641b4891e0c110c1d
- a77d91f122316c2be0e344c8a2de00ef2ac17650c3ab353de6b12c313f2927a8
- c4cd6fbdc2f37be8c6ed3d165839c7f993ca6cc5614e770523ca6fda775819fa
- e33695b999b2a53ebad043fb88165a59c5b623059a2f9b1e3c4aa26226eb5aaa
- e36d39ae360f17a3c1987c71b7c43c537549481cb0e26ab32de3110eeb3417d2
- e82c81df777d002701a31f6942ecfbb72fdf08386e7c4f7520e15eada3c7b649
- f92e9016c5dc3903edf3fd6d1bed1d095da9dbf8e817e6497290aa40f617c776
Coverage

Screenshots of Detection AMP
ThreatGrid
Win.Packed.Bladabindi-6888152-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\5cd8f17f4086744065eb0992a09e05a2 Mutexes
- \BaseNamedObjects\5cd8f17f4086744065eb0992a09e05a2
- 9B737EAE3B0C796AE23ED0068C79CF59
- be7bd1af3359996ed9bf IP Addresses contacted by malware. Does not indicate maliciousness
- N/A Domain Names contacted by malware. Does not indicate maliciousness
- paste[.]ee
- pastebin[.]com
- mine[.]moneropool[.]com Files and or directories created
- %System32%\Tasks\Administrator
- %LocalAppData%\Administrator_.jpeg
- %LocalAppData%\MQMQ
- %LocalAppData%\_foldernamelocalappdata_\msrating32.exe
- %LocalAppData%\_foldernamelocalappdata_\msrating32.exe.config
- %WinDir%\Tasks\Administrator.job File Hashes
- 0081ac22b9b1c8070970ab4d1edfad5cf0df57206ac9f35675ce96c914d9a35e
- 009b727284d9b7fb948273254c104ccc07df738f7f9ac4034b8035b11e1c8b73
- 02fa5b2eb08fa878de231c1e1aadb8ae890d1205d75c6e78704ccc656072a521
- 03574be4fab0b0dfbc4a08474bac9ec5face953e96f274e284d85f23e0394572
- 039d0a85df67a302f8403b1ab5d829ad95ca1f6bd16c712fcfff924953aea417
- 04eb8ea0cc1e3f1bb8420ffb41ca73650e17647b5a125b4e0b50ebcbe3e2586f
- 05e2b0b5b303a6f0a4255728075cd57d6cb9512c6784a3d9841431f81d17fbd1
- 07366374c7531cf8931f983c48d200ce64ca9ef1e2b8e7beda93f00494e9c4be
- 07bbd30ebede3f32346869773bfffd7a03561a237d0b155659881c6bfcf2bcbe
- 087f983881da308a40887d48ff51a47dc2653006b347bad377b06560bdedf54e
- 0aafa85fde357b5468bd161e4dbf5ad281f4b65a8a6e8fac8ea61b6b97fb401a
- 0ae37610706265b32944bde963a021536ddeb3ef2a46fba7a2dd506a84122aaf
- 0af299fa65082907eaf022655a1d297f0bcebf9cc4299fa3e09712b9f6f3638b
- 0b3cddec065917def4974c7e6c2db4a68bd66c240afcc6788f042fcf370dda0a
- 0b7584dbe453ba56a37362502ad8362c7806ad55f93f459bb1520ba8b7e83260
- 0cc3468620a282282493373cab6e0147414ab8b45b9207c135fc0ca2ced4a6a8
- 0cc3ec52a4cccd7f66c39b0598ee3cd5057bbae5f76b6f53ba1dc7b244528d7d
- 0d833bdb0a327257282952658f4022615da662b26ce96c7d7daa745123b539a7
- 0e3f846a7e867311a3a4b5c3cd12e2cf3cd6e53dac743bf169922e5d5522c56b
- 0eb558acbf404a8498bd62d39f915dc8878cab06b42110254bb0f95fed1a1cfb
- 0f06812951241534a7de2f68d72178512bf8dd2fcaad68fc08361e09d936a0d2
- 0f3110996e2c6dcafab54e881b4ae20b79a9a8a9e4bdea4e9282c59dceeba1de
- 0fb34201e918d0b82093836b00a3f28e14b915b4458500206054c0ff89ff4386
- 10ff1192d5f400ba24dc35c92cf93ee6f4d907f6a91d73960db9de6f9b6d908e
- 12ff945a104096e2e33bff767e20f3fa1954261932d5b547632a2fa4b3532fa3
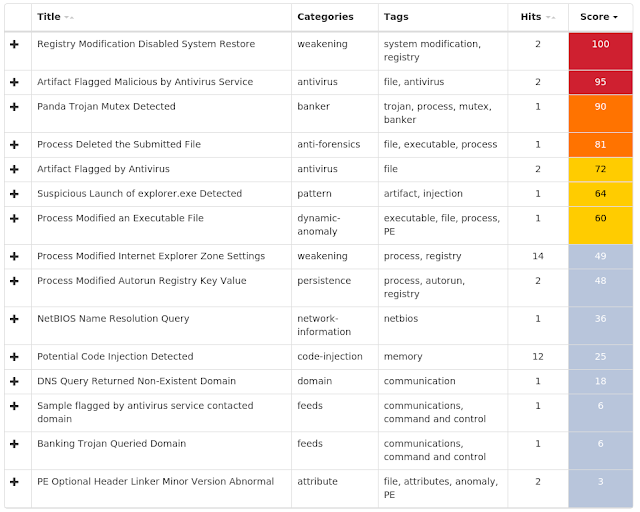
Coverage
Screenshots of Detection AMP
ThreatGrid
Win.Packed.Kovter-6888122-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- 3F102AB2
- 3F102AB2C2
- 3F102AB2C1
- \BaseNamedObjects\FBB4FA59C1
- \BaseNamedObjects\CD5F8C5651203DDA8FEF88477479E431
- \BaseNamedObjects\FBB4FA59
- \BaseNamedObjects\FBB4FA59C2 IP Addresses contacted by malware. Does not indicate maliciousness
- N/ADomain Names contacted by malware. Does not indicate maliciousness
- a15-smo[.]biz Files and or directories created
- %AppData%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f7b-20cabfeabcac
- %AllUsersProfile%\Microsoft\{aeb72b63-4072-2739-ee13-f68145a36fd1}\{aeb72b63-4072-2739-ee13-f68145a36fd1}.exe
- %AllUsersProfile%\Microsoft\{1ddc6d11-74a9-a07d-cfb7-a965c7d68cea}\{1ddc6d11-74a9-a07d-cfb7-a965c7d68cea}.exe File Hashes
- 0266eb0181e6d3cd1112bd582f87711cd0dddc3131f8cd961ef38911958d4d83
- 037ac73363dda68d628670db90cf1d5baee2614545c633fe7a5ef80ded8833d3
- 04052b00ab52dbb2bbbadc9b60122437dfcf1b82a399e1bd6dc868a7764e1622
- 0446028c1c63060111c2f507ade24abf198eeb990c853f75fc285ab55e7e93c4
- 0ea33d1365678ed238613d44f6154b3090728b073cbab653bd0cb851be70b357
- 112e3cd76f74cc5611da59df8b3d07ef643915dc118bc8a8fa7ec6470c3c2918
- 13c46670e8501c9de948fb75a227486299afc6c9f195979a304a3d89bd0f2860
- 1d4cd9c8380430ea3786fd0a3ebb2f369b4db7779662eaf85997876708f5e0ed
- 25ad560fdec751db9190cdaa21467ade949e5f555a213a583c0d59b809d1ffea
- 263e9704f5d4d81c9de6459df0e3bb07571a94e96eaaf6e7978466e83c804c77
- 29f77d861fcea9116cc943b853a54b44449e9f3722e692c8216ec223b96d2b3e
- 3d27db6491de2111b9e47776e7b8913d37f967bd592f0d8b15d8b2abf25fe5c8
- 45ce1cdd1f531667e6ec61341890d2ce5d6dc8ef827cd8b87fa90c1b482a864c
- 476ba0cafaf6caab3d3065c54088cdbeaaf62581e371aa6b7a5add2c66a4c63b
- 4c30f1f40076abac7cd30ed0f1a586d841d5f8e619bec01ed415d7dc181e0e7b
- 4eda50c6c2b19e0871a703d29573c819b16581e59e76743eff31c8581a4f1479
- 5015414e220101ebebef92b8780cebd51e41ba04f6e880a531807f96a58bf463
- 511802d4ba18e098a313a7b5f21adf485632352ad84e9bb9620b85451cc8738e
- 528c4c72ddc84ff3c6cba7ff634b9444c639b5eb435dbac1eb085a6e20531b89
- 5297a054165c283ecc468f500eeadadf21fa0f8fedbe678cf94c578a134b5b2f
- 530cb7062f46e9778d8797930d114f685f1ecd161a20e930c4649682e32758ee
- 5f65eb86f57c979ed006ae5c8f1eddd52729a09f1a80efb092f10ccfa3a7dc99
- 61bc6c41e2184f6c876d11d786bd83bcf330b2f867471457e295ed7e9bf6a4e1
- 690f078af59858cd6d1ebf87104f84831c75eb3eb00c36cfc5a40af4cf52ee97
- 6cf0017b223337ea77ec0a6452fcd68b3d5f79006212baadef5dc1ae8deabaf5
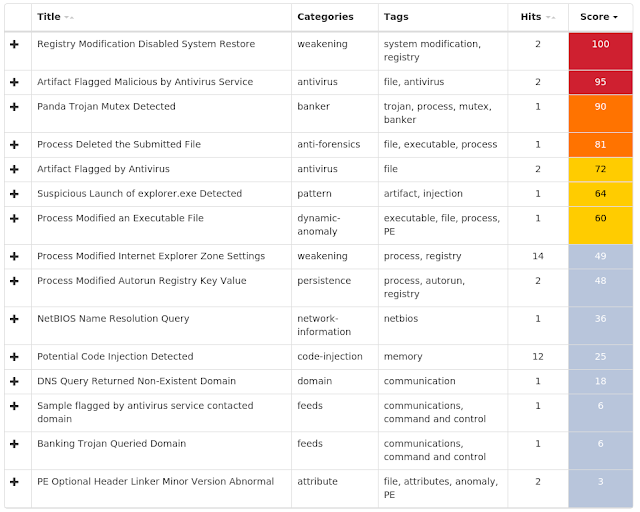
Coverage

Screenshots of Detection AMP
ThreatGrid
Win.Malware.Ircbot-6887900-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 220[.]181[.]87[.]80
- 192[.]42[.]119[.]41 Domain Names contacted by malware. Does not indicate maliciousness
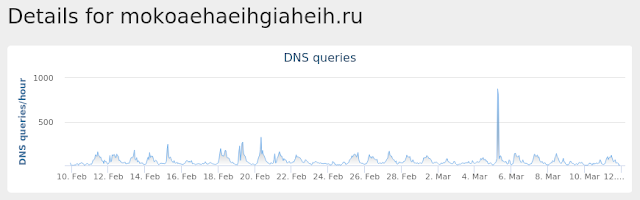
- mokoaehaeihgiaheih[.]ru Files and or directories created
- \??\E:\autorun.inf
- \??\E:\.lnk
- \??\E:\DeviceConfigManager.vbs
- \??\E:\_\DeviceConfigManager.exe
- %LocalAppData%\Temp\edakubnfgu
- %LocalAppData%\Temp\gwhroqkhwu
- %LocalAppData%\Temp\phqghumeay
- %LocalAppData%\Temp\rgjqmvnkyr
- %LocalAppData%\Temp\sxstlbzalm.bat
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\tinwmbkjsh.bat File Hashes
- 0d1408f43b64724f4e1bc689af06c76a7a8bad4f4cc4accb697680827a2e8401
- 11f919f38f7ffc654a9ae3ebc00bd8055f0540fc34742c6c41b3a6cc770e86a1
- 13ad8720c3dc6997a728d970e7e8d8da3bdf47a9aa7122f2062418efbcba8067
- 1450123a608b6f6b0c459e42733c33aef85df3d592424254ad793631c650724d
- 176f000c04ad54f98af1b6fa78caeff969ba9fec1747416a6089717208f4e6bb
- 224c6cdb3319d4ce8dbddafa7db57357a05ff6d25b3cf938e3a277e83415473a
- 22ae2800578ea95c8439851ae40a20535cd13290aa93d78e9fd4f335c7bfcd06
- 240865fcbc40ec209ee7ab43f0ac8a11d4c3c0a994b829097d0ee7e7c9cd0398
- 25ab25d5887e3786532a15211c54143dffe27b27a1794fc0caa2fac26b814441
- 25b97ddb73ec779f09b9d663a1c5695ab1e54857e83a03c719a71c464aa339b7
- 34bde6576413b381f10540db6a5b0c0b2e42c60c5f29cb97d35712f38d9b2348
- 37b5d81e2b9fb2fa99c5ec7c116675a132485549917ae75f19e9a037e4b85831
- 3e537425161e844c07baf229e8e040d2be2337ad465f90082aa143ba890a87ca
- 3fd4652e7dd1c445d4541d4da1c6e4a0eb13534579f1ce0c95733721423257b8
- 4689813970088424400a2e073afa152d5d1ec8a8a200dbed4da70fcfcdde04d3
- 4cecc5c73e73ff45d634919a4546f1f8cfbfb1ba0944da0fafd9ee8383704c1e
- 4d8fa8c3d41f0cead59eb47a536dde17c90758872262c1e772ec65da5b5e3a2b
- 51f7c74fda3ed980e6172b57d38b230bf77630ad3c687b6457c8a3475cee9b7e
- 55eed01902268734a6fad2dc9b7a23bbd3e660f93f848d316468f50f47492ffa
- 618798e167c8afd92bac52d42e9cb6d7abc85ff562d67411ee4732c761753670
- 6c320dc8cfba148f2fa62eb938b5e9273130960ab65f83d9b754788cd643d1fe
- 6dfabdef4c67f0e7770cd07e1ea60ca3f0f1c75e670ea47062086507be61b958
- 70cf498d687c2c36198c4102115632debb42780e2e482cc1bfbf7613210cb870
- 7dffd571164c077f38221c9a45dcbd36f069fb684c8f4e9164f8cc7a3253d9b9
- 83e85a70bef91092a6030a7bd4f8d6caea9f10d58993b1d03321b7083bc6b827
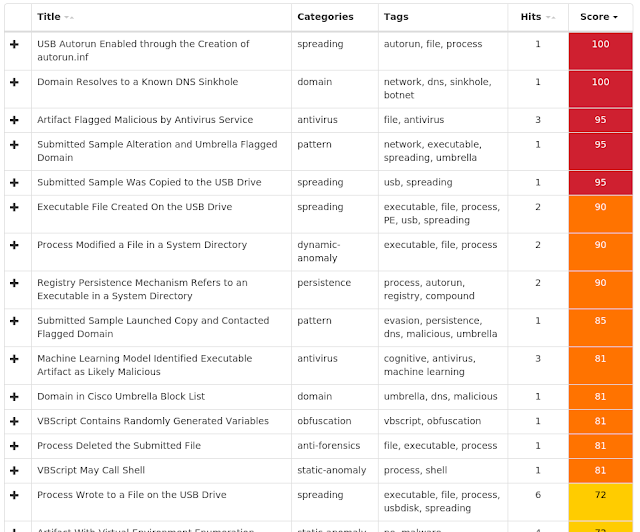
Coverage

Screenshots of Detection AMP
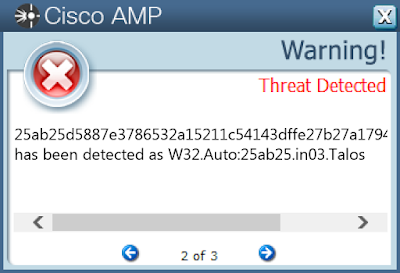
ThreatGrid
Umbrella
Win.Downloader.Dofoil-6887823-0
Indicators of Compromise
Registry Keys
- N/A Mutexes
- D19AB989A35F471083DFB IP Addresses contacted by malware. Does not indicate maliciousness
- 51[.]15[.]93[.]62 Domain Names contacted by malware. Does not indicate maliciousness
- pagefinder52[.]uz Files and or directories created
- %LocalAppData%\Temp\D19AB989A35F471083DFB
- %AppData%\D19AB989A35F471083DFB
- %AppData%\D19AB989A35F471083DFB\D19AB989A35F471083DFB.exe
- %LocalAppData%\Temp\D19AB989A35F471083DFB32
- %LocalAppData%\Temp\D19AB989A35F471083DFB64 File Hashes
- 06141533408e6052c57801bc1a13d9eae0c5473cbd4daefc3c82cc16df02121b
- 0da877fa450e61c35f184f935c866b85adf087aa36840c7bb6d4f5e78caeee3d
- 10a60d91d0993fc42fc0e2dcaf23c6292a6fe3992d30b9a070aff9e901a476d8
- 18a51f34d616573e350344420b4fbca5cf5a22b2c58af39f240beeafeb32272a
- 1f361e3172998b311ef8e688807e6e7ab2b1e08ba779518e5d596dac0459c1c9
- 20562a37ce8338817ef3b2cf00c9aca6aaa22efb90462d29a8276e6fb4a8b4fd
- 284aca36a9bca682b5285d5ce746813b309708d421f4b64f3ad88053a5fb585e
- 35923a5c4509b0cb4c0b0d157ba573387b098cc8fea83f91b075c2cd73c0246e
- 395c3f755c6350037b89f1147496896938fdc3bda6d3113fde3714696e1c022e
- 3c61461aa0f49596538c971740ce8e1b4ba2591233b7f3084acb8b48befde56d
- 473df910306146759bc2478ee77f50cbf944e23a37c82f05563902b752a993de
- 4de2facda43622ed776a0e38d8c7f913acfb700fbeb454d51199159249023840
- 4f05ede1bbf72903141b54089f41b1f5ecfbf68b195acfa0ff73771219ae7245
- 52cf86ed74dce82133c38b4cc0e2804878307925c293d00e19bdeabb5e78aa8a
- 563a88feb872206c770fd6e9efabe66d48ceb34b4bc5cbc482042e33fe9b76e3
- 586e3a4f9bcea6f8759dbb01dceae9c9ec195c9f275c78fd884cb29e3b707c08
- 5ede64cb3093932c752defc4223d596fd6733e945d002785f15b4b2756bb899c
- 6139f943467db8cfffa485c55c891cce2d181df869fc22e6b4a4bf2361e062a3
- 9a8f38571026845836851fa780c25f7f48960b5e248610a42e3ccdad8495852d
- 9cbd93cb77e64c6df894a34ad850f1777f7792729e9029ce3fb34dfc807d616e
- 9dd88df8e9581bbca947def5ca7c835290a59bfd2e8f7a9647e2e58ad9800fbf
- af8a6165044affaec01d741f87df3688c6da82aa636f7aaafc53cc13e2c616ff
- b5de32f4ad9759d3175a2e55817c1f129645d530503f52a2e01501e9a2dcd78e
- b84b1a2bb33df715eef75ab45554d69efe40704bc59b54a798bbd84c9824ddd8
- b94aa2b5628ad5b1944b92485a760427babe9e4de12b66c8e22d89bf8ba904e6
Coverage

Screenshots of Detection AMP
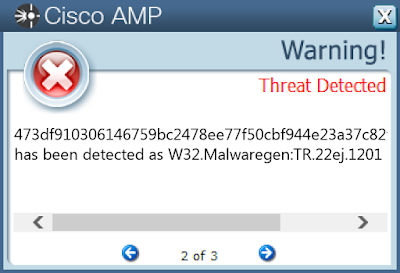
ThreatGrid
Win.Malware.Upatre-6887803-0
Indicators of Compromise
Registry Keys
- <HKCU>\Software\Microsoft\Umqitiexdeuq Mutexes
- N/A IP Addresses contacted by malware. Does not indicate maliciousness
- 172[.]217[.]6[.]228
- 184[.]168[.]131[.]241
- 184[.]168[.]131[.]241
- 68[.]235[.]37[.]83
- 68[.]235[.]37[.]83
- 94[.]64[.]68[.]197
- 190[.]37[.]207[.]199
- 71[.]91[.]43[.]179
- 79[.]187[.]164[.]155
- 63[.]227[.]34[.]28
- 178[.]116[.]48[.]217
- 86[.]135[.]144[.]6
- 94[.]189[.]230[.]78
- 206[.]190[.]252[.]6
- 86[.]140[.]35[.]54
- 59[.]90[.]26[.]49
- 123[.]203[.]139[.]252
- 86[.]158[.]144[.]27
- 75[.]87[.]87[.]199
- 84[.]234[.]151[.]23
- 222[.]96[.]81[.]59
- 172[.]245[.]217[.]122
- 58[.]252[.]57[.]193
- 103[.]14[.]195[.]20
- 108[.]230[.]237[.]240
- 18[.]207[.]122[.]59 Domain Names contacted by malware. Does not indicate maliciousness
- kofinyame[.]com
- www[.]california89[.]com
- pnknjhuxsskskonvohioau[.]info
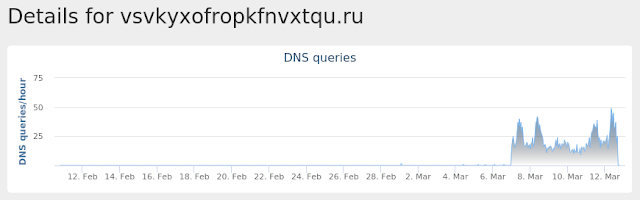
- vsvkyxofropkfnvxtqu[.]ru
- ypijaiuofuwgijcaqwohzttg[.]org
- mzguonizaiofcwgxnzvwherszlmz[.]com
- nzvoeikvdmpinoozhamd[.]com
- lkbeyypifvcjvxwgsgdrcwkvydrc[.]com
- jsodtcfuieijvpbyfewgyybmpj[.]info
- lndnbibwojvpttjrlheuxby[.]info
- vggaprxwdaqkrlvkeanrjnrwgmj[.]com
- bamfzxfhazxfefylreaytvgulf[.]biz
- eylinjbhuypwgtwqgovwstbyqcpj[.]net
- pzfihbalfharxouokrlcuzxhtpr[.]biz
- zhibylozydfqtukeamzpzppvif[.]org
- lvwodonehibqsdprllgapjoriz[.]biz
- zlursovdmvtgekqwozlwgmhgu[.]com
- vsjfljuktcprpzcixtdamljdqztdy[.]ru
- gebypvkbqstqsscizdheyxpfi[.]com
- ppjjvfmjntoxsttbihhofizofiv[.]ru
- lmzamkfmfaejfkvinkjkjtdznf[.]net
- kfduojjrzxqkirtdgamjydpjtgil[.]net
- skzaegitbqjnxczwvxkciqkxwha[.]biz
- daovdoztdyskzppxkbyiaipr[.]ru
- plphqnbubqifdmjfyekr[.]com
- ayaytgarstgcmgyqhluouoduxp[.]info
- thmxtkrgibmntaqprzusph[.]org
- fyskhabnfxkzxhztpjpzobtwl[.]net
- eawomrwysotslhbudmlbtspbrlv[.]org
- amifxopfwnrpfvnzprculnwomjwo[.]com
- ijpjzqlflonhqsckydtjib[.]com
- hqjbkngeugdmzthvdixhmtd[.]ru
- julnlfxcdlzxssciayeydphq[.]biz
- dyqcdmnameilrprtgefydmvlrkb[.]ru
- usxsplvoaucmcqzhylvydpbvoux[.]net Files and or directories created
- %LocalAppData%\Temp\budha.exe
- %SystemDrive%\DOCUME~1\ADMINI~1\LOCALS~1\Temp\budha.exe
- %LocalAppData%\Temp\kilf.exe
- %LocalAppData%\Temp\mciD000.tmp
- %LocalAppData%\Temp\mciD212.tmp
- %LocalAppData%\Temp\QQQ19A.bat
- %LocalAppData%Low\yquv.sij
- %AppData%\Siig\zuquzi.exe File Hashes
- 0166c9039455db0ea98683386b70f50b0112762e382ea4abd1e93b06c92def5e
- 0167c644b8865c63304aaee76387e7a6e3b6cb02cc842c8fb8501ee8f77e1289
- 07e28bf1b7435b3720b71b7746e4e80500c83be05af84d2d00a029af3a50e12b
- 08c11779eaef3d77856505245682b893de88d564cb72c089ba6868a67bb5b615
- 098aaeb04eacd88d2f1e015e99ba27bfdfc7a7e546baebe5a7e2973ea906834a
- 0faa654f47498dad4ba37edbf51e139b403950901036b4b20965ece482a227b4
- 10bc9653e8caa085a6f4c5b8138304322218c038707b0d96370aaf7b763f3c63
- 188b97e1357a61019cee3f7f1922f884a8a11e5bd844c244524355053a2a91a6
- 1c3ac82f646e2f984514b6a1df33b5cb1afce9822636c3cab7cf22556a215996
- 25df09d4d6d8ef905b0024af40e8ca2f28a95c6ffb67bbd5e377d11f2a324b81
- 265f68069c3f4f37ba64b18464a9d5ebb6db7c2bcfa43b4f7c3c01e08d8f979b
- 27d134dc861c927028d13eebe67b15bf15258fdf58af6f54e2fdf4862bc5332d
- 28d4d14611715adf25229f528c5c904c7a476b547d748b54e75e25d453daaca5
- 2c7d97a3194c69de640bf7dd22ecc6bb887db6ac45fe51f73e983fd251f75305
- 309617ae45a709d3be67aa9e14ec5d00731c6e4ae46960465fea0f4ed7433da4
- 32253daaf93f636af8e995ecc02865927affd0f2f403691079040785e90acabb
- 34ecfb02a49a5bc13a1872ab9ae31fef8a58b688c87faead979ad242e4bc27d2
- 3c1577927878cbb48b0e9d6cf00c031de57af45d019cf3ffb079990cc5f21adc
- 40da8071021b3bc12cada1ae026799d035b6b42d7aeca3d82a820e777f5a56fd
- 43819962ad29ae185caefd004c718c78503203f643c750904f8fcc4ccb4c21f6
- 4b7fac51617a8b03da4061ce21dea06d3ccca2bf06c962dd5222ca8f74731910
- 4de920bcddd350ee1571d8cc96ed4875ca92f4095e63147b949859f498ade1dd
- 55ec12cd22820605e1e4d28f9bce981434bed569b4677fd16d0ec3f6477839ea
- 5a3c39384578544a4ee7f6bc4357b6c1c22d8f08e58181e4f766dabdf07fc3b1
- 5f2b23d3795f5ee5be46948471d9ebe3f940e9d90bbd61099f06809770d99659
Coverage

Screenshots of Detection AMP
ThreatGrid
Umbrella