Cisco Talos is continually working to ensure that our threat intelligence not only accounts for the latest threats but also new versions of old threats, such as spam. This often means pursuing cybercriminals wherever they congregate. However, instead of wheeling-and-dealing using hidden servers on some mysterious dark web address, a surprisingly large number of cyber scofflaws prefer to operate right out in the open using social media. For example, Facebook is host to dozens of groups that serve as online marketplaces and exchanges for cybercriminals. Talos saw spam from services advertised in these Facebook groups show up in our own telemetry data, indicating a potential impact to Cisco customers from these groups.
Over the past several months, Cisco Talos has tracked several groups on Facebook where shady (at best) and illegal (at worst) activities frequently take place. The majority of these groups use fairly obvious group names, including "Spam Professional," "Spammer & Hacker Professional," "Buy Cvv On THIS SHOP PAYMENT BY BTC 💰💵," and "Facebook hack (Phishing)." Despite the fairly obvious names, some of these groups have managed to remain on Facebook for up to eight years, and in the process acquire tens of thousands of group members.
In all, Talos has compiled a list of 74 groups on Facebook whose members promised to carry out an array of questionable cyber dirty deeds, including the selling and trading of stolen bank/credit card information, the theft and sale of account credentials from a variety of sites, and email spamming tools and services. In total, these groups had approximately 385,000 members.

These Facebook groups are quite easy to locate for anyone possessing a Facebook account. A simple search for groups containing keywords such as "spam," "carding," or "CVV" will typically return multiple results. Of course, once one or more of these groups has been joined, Facebook's own algorithms will often suggest similar groups, making new criminal hangouts even easier to find. Facebook seems to rely on users to report these groups for illegal and illicit activities to curb any abuse.
Talos initially attempted to take down these groups individually through Facebook's abuse reporting functionality. While some groups were removed immediately, other groups only had specific posts removed. Eventually, through contact with Facebook's security team, the majority of malicious groups was quickly taken down, however new groups continue to pop up, and some are still active as of the date of publishing. Talos continues to cooperate with Facebook to identify and take down as many of these groups as possible.
This is not a new problem for Facebook. In April 2018, security reporter Brian Krebs alerted the social media site to dozens of Facebook groups wherein hackers routinely offered a variety of services including carding (the theft of credit card information), wire fraud, tax refund fraud and distributed denial-of-service (DDoS) attacks. Months later, though the specific groups identified by Krebs had been permanently disabled, Talos discovered a new set of groups, some having names remarkably similar, if not identical, to the groups reported on by Krebs.
Inside the online criminal flea market
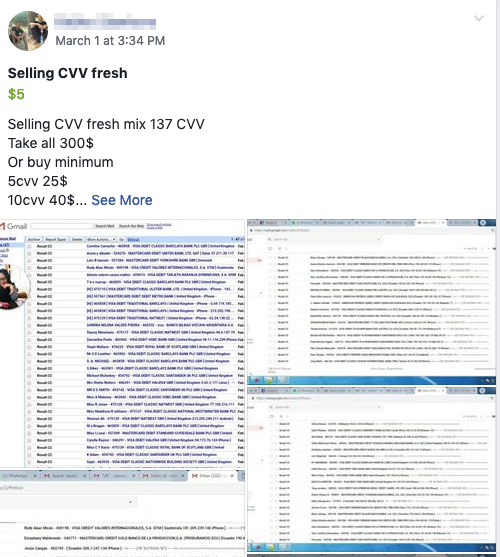
Many of the activities on these pages are outright illegal. For example, we discovered several posts where users were selling credit card numbers and their accompanying CVVs, sometimes with identification documents or photos belonging to the victims.

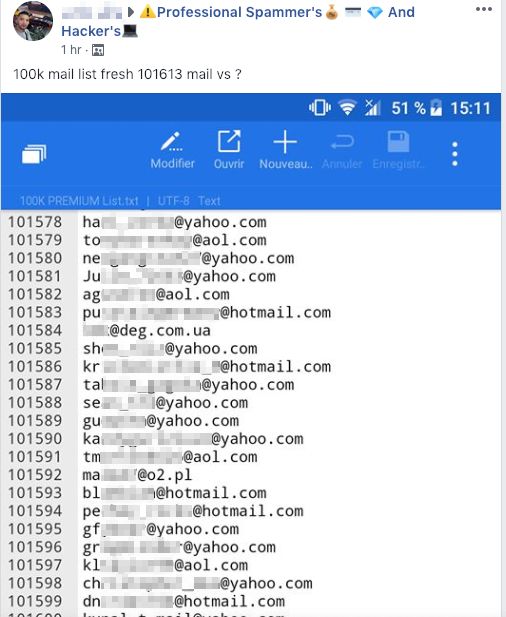
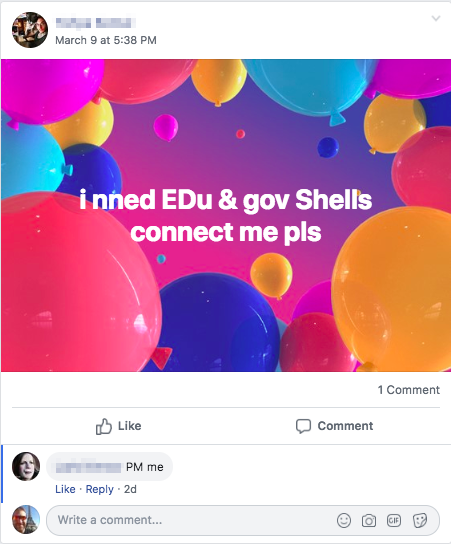
Others products and services were also promoted. We saw spammers offering access to large email lists, criminals offering assistance moving large amounts of cash, and sales of shell accounts at various organizations, including government.
We even saw users offering the ability to forge/edit identification documents.
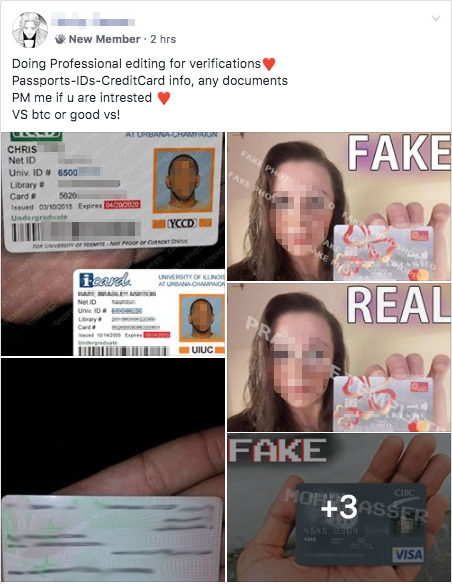
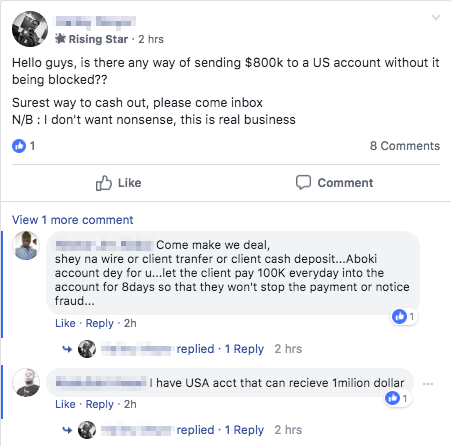
The majority of the time, these sellers asked for payment in the form of cryptocurrencies. Others employ the use of so-called "middlemen" who act as a go-between between the buyer and the seller of the information and take a cut of the profits. These users usually promoted the use of PayPal accounts to complete the transaction.
It's unclear based on these groups how successful or legitimate some of the users are. There are often complaints posted by group members who have been scammed by other group members. In most groups, there is a particular etiquette and form to the posts. Typically sellers will describe what they have versus what they want. Almost all transactions are "you first" (written as "U_f," "uf," etc.), meaning the person interested in making the purchase or trade has to pay or provide their service or product up front. Like many other Facebook groups, these scammer groups also exist as a forum for scammers to share jokes about some of their less successful campaigns.

Scammers in the wild
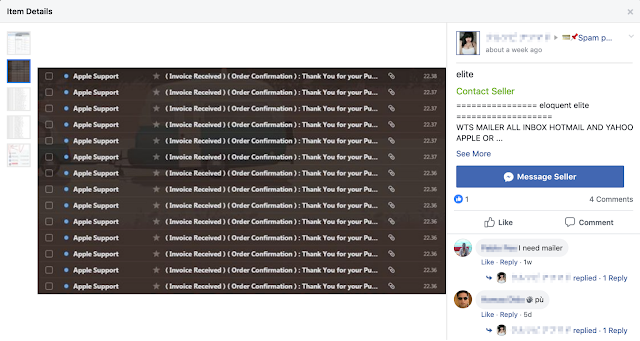
One thing is certain, even though some group members only seem to be out to scam other members, others are out in the wild committing crimes that show up in Talos' data. For example, below is a post from one of the Facebook groups that Talos was monitoring. In the post, the spammer is advertising spamming services, promising to land their Apple-themed phish into the inbox folder at Hotmail and Yahoo. They helpfully included a screenshot demonstrating the spam they received into their inbox.
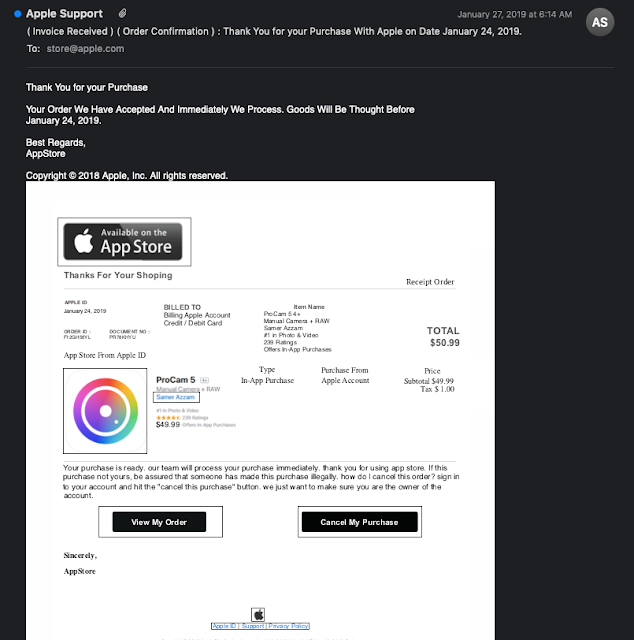
Talos was able to locate examples of this same phish in our telemetry data. Based on the email samples Talos recovered for analysis, the attackers had attached a PDF file that claimed to be an invoice for a purchase at Apple. The PDF included links to view or cancel your order.
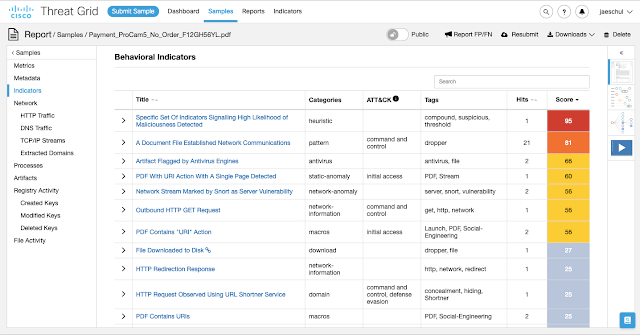
An analysis inside the ThreatGrid malware sandbox indicates that when the user selects to either view or cancel the order, the link directs the victim to a phishing website that was located at a recently registered domain: appleid[.]apple.com.verifysecureinfomanage.info. The phishing website itself was created using "16Shop," an infamous phishing kit that is known to target Apple users.
Cisco Umbrella's Investigateindicates that the IP address used to host the phishing domain is also home to many other suspicious-looking domain names that have likely been used for similar scams in the past.
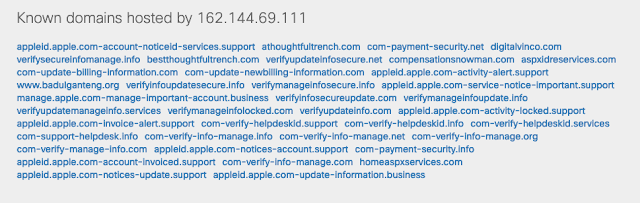
This is not the only example in our data that we found regarding this type of illicit activity that was followed by posts in Facebook groups selling the same tools, techniques or services used by the scammer. Some group members do indeed "walk the walk" when it comes to perpetrating these sorts of online crimes.
Conclusion
Social media has provided tools enabling individuals from all over the globe to congregate and share ideas. This is one of social media's defining features. However, the underlying computer algorithms that help us connect, suggesting new friends or networks, are not intelligent enough to distinguish benign activities from unethical or outright illegal. So far, Facebook has apparently relied on these communities to police themselves, which for obvious reasons, these criminal communities are reticent to do. As a consequence of this, a substantial number of cyber-scammers have continued to proliferate and profit from illegal activities. Operating with impunity, these attackers relentlessly probe cyber-defenses of enterprises everywhere. This is a high-stakes endeavor because an attacker with even the smallest foothold inside an organization can do considerable damage.
To combat these motivated adversaries, we need to work together. Social media platforms should continue their efforts, both manual and automated, aimed at identifying and removing malicious groups. Security teams and vendors must work together to actively share information, take action and inform our customers. Businesses need to be diligent about their protection and cyber hygiene efforts. And finally, consumers need to become as informed and skeptical as possible. Attacks like spam prey on the individual as an entry point.
Note: If users encounter malicious groups on Facebook, they can always report the groups through Facebook's "report" function, which is located at the top of the group's page in the drop-down menu under the "... More" button.
