Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 12 and April 19. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
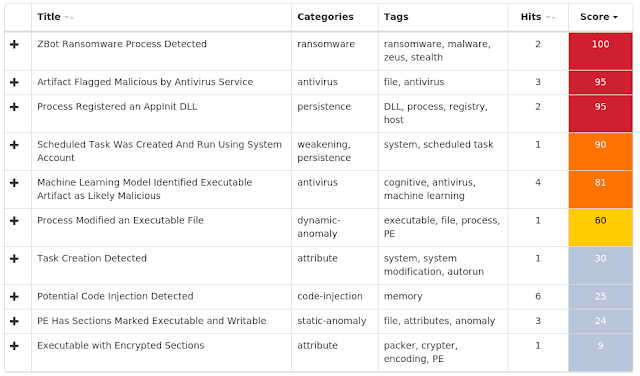
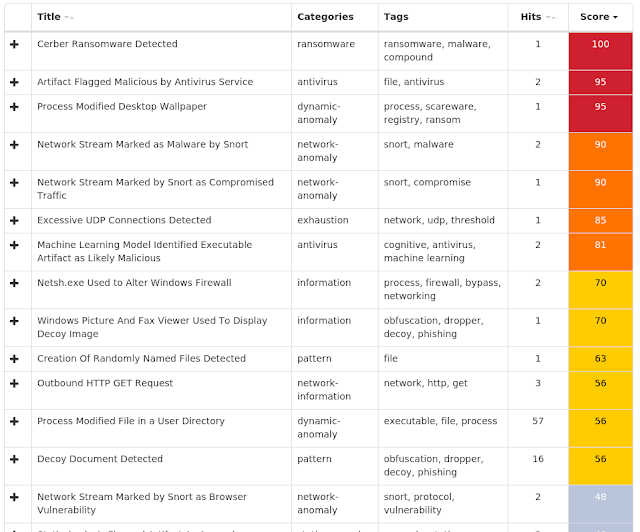
Win.Malware.Dvee-6943598-0 Win.Worm.Vobfus-6943588-0 Win.Malware.Trickster-6943552-0 Win.Packed.Razy-6943334-0 Win.Ransomware.Cerber-6941980-0 Win.Malware.Tofsee-6940401-1 Win.Malware.Ponystealer-6939264-0 Doc.Downloader.Emotet-6938868-0 Win.Malware.Fareit-6938631-0 Win.Malware.Ircbot-6938570-0 Threats Win.Malware.Dvee-6943598-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
13
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
13
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
13
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
13
<HKLM>\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
13
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: bikfir
13
Mutexes Occurrences NetRegistry
13
NetworkLighter
13
OMXBJSJ3WA1ZIN
13
OneiricOcelot
13
OnlineShopFinder
13
P79zA00FfF3
13
PCV5ATULCN
13
PJOQT7WD1SAOM
13
PSHZ73VLLOAFB
13
QuantalQuetzal
13
RaringRingtail
13
RaspberryManualViewer
13
RedParrot
13
RouteMatrix
13
SSDOptimizerV13
13
SoloWrite
13
StreamCoder1.0
13
Tropic819331
13
UEFIConfig
13
UtopicUnicorn
13
VHO9AZB7HDK0WAZMM
13
VRK1AlIXBJDA5U3A
13
VideoBind
13
VirtualDesktopKeeper
13
VirtualPrinterDriver
13
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]218[.]206[.]69
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences N/A
-
File Hashes
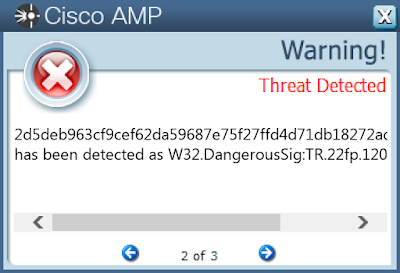
2d5b33a32e4df1169b09c06fe13f98e93cb108cc9163f322001a2db3b8a765192d5deb963cf9cef62da59687e75f27ffd4d71db18272add942a93952a8920eb233a36a0172595eedf4a682ffe173662b3092bfe71fbdfdf4e5f4dcd365513564357208a511d7d0277e467719036d801c91ae6b66a9988a5092db9b6af99603b845aeda204fa240e37b87d8c183343aa617ba7e8fd42bedbfc4ebcf7e3385e3be4859cb4bc26d257e2720dacb777895b2541f72a8848dfa554665e1b04e1a9f7a566e1ee0d6ab08685f722c041c635894d0169f30accf5325d5f0413717c1beab600b00554ff77da736f199efa7338cabc92307d32dc527f096e00ec718039778767fab90d7e27102d3208766baa0f5956073c36fc31b93b854c2afbdc25b6c15ad1a5597477817161619ea4b0dbdf92186260947f808ced5e18f60990b229795c3c4acdb0f7164a8c3095df6fa5932d5d8617254856576372b86238c092dac80ef87f15fb3383455cbd86bb5c1c792535d06c334499025ab8c5091c33a722f1cfdf5bae149683eff434f734295693723dd83b3769b63e5317e137c4ac4aff6ae Coverage
Screenshots of Detection AMP ThreatGrid
Win.Worm.Vobfus-6943588-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WindowsUpdate
44
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\EXPLORER\ADVANCED
Value Name: ShowSuperHidden
44
<HKLM>\SOFTWARE\WOW6432NODE\Policies
44
<HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\WindowsUpdate\AU
44
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU
44
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU
Value Name: NoAutoUpdate
44
<HKLM>\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU
44
Mutexes Occurrences \BaseNamedObjects\A
43
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]11[.]56[.]48
43
Domain Names contacted by malware. Does not indicate maliciousness Occurrences ns1[.]helpupdated[.]com
44
ns1[.]helpupdates[.]com
43
ns1[.]helpupdated[.]net
43
ns1[.]helpupdater[.]net
43
ns1[.]helpupdates[.]org
43
ns1[.]helpupdated[.]org
42
ns1[.]helpupdates[.]net
42
Files and or directories created Occurrences \autorun.inf
44
\??\E:\System Volume Information.exe
44
\System Volume Information.exe
44
\$RECYCLE.BIN.exe
44
\Secret.exe
44
\??\E:\Passwords.exe
44
\??\E:\Porn.exe
44
\??\E:\Secret.exe
44
\??\E:\Sexy.exe
44
\??\E:\x.mpeg
44
\Passwords.exe
44
\Porn.exe
44
\Sexy.exe
44
\??\E:\autorun.inf
41
\??\E:\$RECYCLE.BIN.exe
40
%HOMEPATH%\tuoopiv.exe
1
%HOMEPATH%\yeeideg.exe
1
%HOMEPATH%\xoaqoz.exe
1
%HOMEPATH%\fooucax.exe
1
%HOMEPATH%\doohuoh.exe
1
%HOMEPATH%\maasie.exe
1
%HOMEPATH%\hoila.exe
1
%HOMEPATH%\rwfiik.exe
1
%HOMEPATH%\luuaj.exe
1
%HOMEPATH%\komaq.exe
1
See JSON for more IOCs
File Hashes
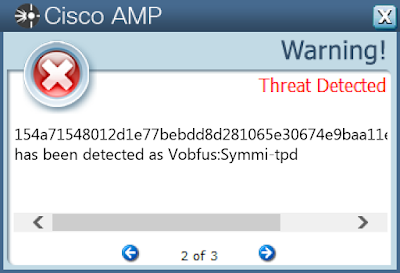
0825d12566ab439528f23e43a5268df5134fc940a710b9a54327c5369ff1d77908d7d577fd9e974f243d39882b99c9416da3d8831e6238e2ef106c71a085c3020956747c94a2b20b1dae5aed1abe13027da1b1f28035bdf93d8d5d8f5f6598191145bd1a3139aa595289cdeb70cc33cf5bde8a6c2119011047d70be952fbc6d511999ae5f6b5b76ac23baeba3bbcae5e4221fe668fb1c49d682ba1443cb9259a154a71548012d1e77bebdd8d281065e30674e9baa11ef4c5329e152531d2327f18c99727bdf696c45c0ba482a0c6cb79b73db287ab22f8df80fec32a2f1058b120eaee1add9c704bf9f371bb8fee3c1a2a5038cd30092a99fc0a106fdf6183b52144a184f0b1a3ef768942be09775cbdfd84c467a4bd397165a18d7a5ae8e267236572e8b2d5319387857ecdb6b4ba967fe5e981c68af50bee606ccb539c434c24515511e533db6e0e92aec65514245f4e406fe627dc3b913d8726f82d9af7fc266379bcf89611d7d42aa3226b02f7184f2feac15112574586ceeb2611ddf2112808712ea60de5e30f5106e69bef8a536f42c712d9c98ae0ebbc6fc1f44fbcd728eeb9fcb82a4063d33cb67cdda99b9b253d7b0f5cdb4970dba6ab823dca0c6f2c61c72f6244f95c47ed4322724341584f52935af862d12fca3f59392a229b9730bc3619ccb44ee0bcadfd87c8df627404f4d550974f0a16bdd6d77fa5d608bd317081b5d0d9097985f8682d1433633fc7ac4a26dd2be1b4c60c67f282ca87f94adb34d87cdfae0d680ad483f94a809165151d3f0dbb3943dd0851038e40b9ac4ee4b51be1b2333b8e75608db3401b5f30f18b4ce805fd1291caa11660e2e8f24ffd7a68634b4e0a28407e6755d288cb29e19780b10e874aff0286dee745427a5e785cf0e1bba5392c31815cf1f8e46f5f5757f0a0364dc4ef949bf30c97dc91631e4dd3820d5ff217e521ea60af0e886846d38a576b1e1a2b9a34d6c0218bc1642d7d5280ca3ac5e18f1c2b9a9de7e5137fb477b5dac9299cd54d76752fcae46e660d002f74fb282d2913c0cb340e3c9adc607a2b6b6d24aff0b625c0ce014a731c3e7ca6703700fefd3461f6191bf69808adac97274fe15f83a5a48ed3f415See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Trickster-6943552-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: DeleteFlag
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
25
<HKLM>\SOFTWARE\Wow6432Node\ODBC\ODBCINST.INI\ODBC Connection Pooling
25
<HKLM>\SOFTWARE\WOW6432NODE\ODBC\ODBCINST.INI\ODBC CONNECTION POOLING
Value Name: Retry Wait
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\COMPATIBILITYADAPTER\SIGNATURES
Value Name: DefragWinSysTask.job
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\COMPATIBILITYADAPTER\SIGNATURES
Value Name: DefragWinSysTask.job.fp
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\DEFRAGWINSYSTASK
Value Name: Id
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\DEFRAGWINSYSTASK
Value Name: Index
25
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\DEFRAGWINSYSTASK
Value Name: Id
25
<HKLM>\SOFTWARE\ODBC\ODBCINST.INI\ODBC Connection Pooling
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{63696C4F-E894-414D-8EDD-EC59133E665B}
12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{F95BF9F7-D3F3-4AC5-8A3F-4B59850DD369}
Value Name: Path
12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{C6E23691-91D5-4EF1-9A0F-35831712CA4D}
5
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{6FBD3206-3711-4788-B386-E054AB1B035A}
Value Name: Path
5
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{A2E3CD1A-FC1F-429E-AE42-F10FC0FE5F62}
4
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{DD4D0EA2-1AA6-4E9E-8929-8DA13093B023}
Value Name: Path
4
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{B78E9CED-C151-484D-9668-62B5883DF1B7}
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{39B6E100-0C7A-4C93-B02D-9BC71BBE7971}
Value Name: Path
3
Mutexes Occurrences Global\316D1C7871E10
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]218[.]206[.]69
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %APPDATA%\SysDefrag
25
%System32%\Tasks\DefragWinSysTask
25
%APPDATA%\SysDefrag\151d29112be976edc69713a9269b5562e18a31ade8c9b98a5ae60f09cb2f858b.exe
1
%APPDATA%\SysDefrag\3f87dc3b929d5e58c30e15da96dd77c21fa9aefb3ddc087f109d6680bf997f3a.exe
1
%APPDATA%\SysDefrag\53c7b976b0d39d8dd909a9038e677ac2d7cb970a721565fbdcfbb30d97830a1a.exe
1
%APPDATA%\SysDefrag\57c93c6821a88699c08a1929fcd808b1da5b80a569216763c9c9d3a06bed1df1.exe
1
%APPDATA%\SysDefrag\62aedc09e819fea0f5319805cba90ce295053770ea3235393109c5ebcdb76589.exe
1
%APPDATA%\SysDefrag\9e1707e022f96e7bb30ec79e7703bcb8b1007ca9da320533290a95021a36399e.exe
1
%APPDATA%\SysDefrag\e91f21aa3b75d5c3aae321e81005199f85722179aa16921afb8fc12b30558d3d.exe
1
%APPDATA%\SysDefrag\8c2ae5c96c7e6e895b618260bab3eba68a02a7363dc712eff67939a0fa7839dd.exe
1
%APPDATA%\SysDefrag\96fe099171c5f9fb6982cb999b2becc60920c1d03308ee70680dd28e0a97d92d.exe
1
%APPDATA%\SysDefrag\29116de521ff86e6a59e92399b19a99f6e053b85b962e1b816c8c727c890a397.exe
1
%APPDATA%\SysDefrag\32a0138dad1d09a3cf8b697788bd3393e37d6f6a95383ac7d91885987990f29e.exe
1
%APPDATA%\SysDefrag\69275638617690fc15a678c89d00eb3611660b95e653ff7c72686209ffff2b5b.exe
1
%APPDATA%\SysDefrag\8957796c69be68666c6fb97ca9dce0c22b7b9ca1f6efe02fd196cb12f55f07ad.exe
1
%APPDATA%\SysDefrag\9889c90b3091da0fdd1e071bcd9f2797cb38619fde119707ab260852ae50eb65.exe
1
%APPDATA%\SysDefrag\caa17a1902c1eaac7d569a772237ae18e968c1cf87a9599e6578982ccc0bf05d.exe
1
%APPDATA%\SysDefrag\f288eaba7c1f39f12bd260056b2cde93c93cc26750039e788ae128382ea2fb38.exe
1
%APPDATA%\SysDefrag\35e93b5912e9b821eac37a208cb6d3aa2d68d9ff8ab886e1ee80f7673b1e16e1.exe
1
%APPDATA%\SysDefrag\07611835c7de0d9a33e818d9f18d863cde06a0f135d36f87d2bf698db0092ff7.exe
1
%APPDATA%\SysDefrag\017ee1979fd82e3b35b79cf6e856a698eb20e9b8eea8979960651dbb6138f9d2.exe
1
%APPDATA%\SysDefrag\2518d5b9b191b697770b317a9eed51e193b6bf6d9cdf0e92ec165ef80e80a519.exe
1
%APPDATA%\SysDefrag\39858ba2395da39a12c59cd8653e80179f65b53b7216c278da215989ea922a9d.exe
1
%APPDATA%\SysDefrag\51916f6519d320dceb1fe899cf93279ba9b5d2a896bdc9fdb7692969a62b9fa3.exe
1
%APPDATA%\SysDefrag\66d3703ef85b217fd5af05b99eb87e0930d8bef9a9261b51e183a5ee9c3d7997.exe
1
See JSON for more IOCs
File Hashes
016ee1969fd72e3b34b68cf5e745a597eb20e9b7eea7968850541dbb5137f8d206511734c6de0d8a33e717d9f17d753cde05a0f134d35f76d2bf597db0092ff6141d28112be865edc58613a8258b4452e17a31ade7c9b87a4ae50f09cb2f747b2417d4b8b181b596660b316a8eed41e183b5bf5d9cdf0e82ec154ef70e70a41829115de421ff75e5a49e82389b19a88f5e043b74b952e1b715c7c626c790a38632a0137dad1d09a3cf7b586677bd3393e36d5f5a84373ac6d81774976890f28e34e83b4812e9b721eac36a207cb5d3aa2d57d8ff7ab775e1ee70f6563b1e15e138747ba2394da38a12c48cd7543e70168f54b43b6215c267da214878ea922a9d3f76dc3b828d4e47c30e14da95dd66c21fa9aefb3ddc076f109d5570bf996f3a41915f5418d320dceb1fe798cf83268ba8b4d2a795bdc9fdb6582958a52b8fa343c6b865b0d39d7dd808a8037e566ac2d6cb960a621454fbdcfbb30d86730a1a46c83c5721a77598c07a1828fcd707b1da4b70a458215653c8c8d3a05bed1df152aedc08e719fea0f4318704cba80ce294043660ea3234393108c4ebcdb6547955d3603ef74b216fd4af04b98eb76e0830d7bef8a9251b41e173a4ee8c3d688659264537516580fc14a567c79d00eb3511550b94e543ff6c62575208ffff2b4b7846685c58be57555c5fb86ca9dce0c22b6b9ca1f5efe02fd185cb12f44f06ad7c2ae4c85c6e5e784b517250bab3eba57a02a6353dc612eff56838a0fa6738dd8779c80b3081da0fdd1e061bcd9f2686cb37518fde118606ab250742ae40eb548f033f102dc0118bbd47521a8ccd7726434d48efb335de3e35deeaabc33432f895fe099161c4f8fb5872cb898b2becc50920c1d03307ee60570dd27e0a86d92d9e1606e022f95e6bb30ec68e6603bcb7b1006ca9da320433280a94021a35399eae65a52a9a6300794ef837776a979abeaf9901d6250ac6531a50c0668dac1213caa16a1902c1eaac6d459a662236ae17e857c1cf76a9489e5467972ccc0bf04de81f21aa3b64d4c3aae321e71004188f74622168aa15921afb7fc12b30447d3df277eaba6c1f39f12bd250045b2cde83c93cc25640038e677ae127372ea2fb37See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Packed.Razy-6943334-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: LoadAppInit_DLLs
18
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\COMPATIBILITYADAPTER\SIGNATURES
Value Name: aybbmte.job
18
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\COMPATIBILITYADAPTER\SIGNATURES
Value Name: aybbmte.job.fp
18
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\AYBBMTE
Value Name: Index
18
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINDOWS
Value Name: AppInit_DLLs
18
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TREE\AYBBMTE
Value Name: Id
18
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{F2B28AC6-1443-43F4-9832-8315397F35E8}
14
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{FF46FC7D-1E0D-46F8-87EC-94D0FDA83668}
Value Name: Path
14
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{FF46FC7D-1E0D-46F8-87EC-94D0FDA83668}
Value Name: Hash
14
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{FF46FC7D-1E0D-46F8-87EC-94D0FDA83668}
Value Name: Triggers
14
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{F2B28AC6-1443-43F4-9832-8315397F35E8}
Value Name: data
14
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{FF46FC7D-1E0D-46F8-87EC-94D0FDA83668}
Value Name: DynamicInfo
14
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{F95BF9F7-D3F3-4AC5-8A3F-4B59850DD369}
Value Name: Triggers
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{088B2EE3-A639-491E-B1E6-84AE447D785F}
Value Name: DynamicInfo
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{94669170-5F40-43E0-9D77-69BC9146DF72}
Value Name: data
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{9C9693B0-E894-414D-8675-6B58133E665B}
Value Name: DynamicInfo
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{6E1FF505-4705-412B-825D-ECE026885614}
Value Name: data
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{ADB65317-3AC3-40D4-B863-464193D5CE9A}
Value Name: data
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS\{F95BF9F7-D3F3-4AC5-8A3F-4B59850DD369}
Value Name: DynamicInfo
1
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\HANDSHAKE\{63696C4F-E894-414D-BED2-EC59133E665B}
Value Name: data
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]218[.]206[.]69
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %ProgramData%\Mozilla\thfirxd.exe
18
%System32%\Tasks\aybbmte
18
%ProgramData%\Mozilla\lygbwac.dll
18
%HOMEPATH%\APPLIC~1\Mozilla\kvlcuie.dll
18
%HOMEPATH%\APPLIC~1\Mozilla\tfbkpde.exe
18
%SystemRoot%\Tasks\kylaxsk.job
18
File Hashes
35710fe9a0ec701c957212d177d324fdd050832eac5cb442e436b7bdcb26f39277fd8af54d16227311e6ca62676bf962af369f6d075e5a6a3dedc265af0bab0c83ea8be6378a758ec38762fe40592c84239e4ebe3b510ab1df01ec921dfe8b079ffc7b464bf4765508d05add71f1f10dfc66e517559d8363921aa57fbe7696b6b892d7bb57e4ee61445909254f25572c610bafd2cdf3408fa9f8ea236791dae3be5b92a7e91b011a21c17c3c32129a54af5230b23d1f1ad2a775501e322fa775d902082b5f30414b39ef79518073f8773d0bfaca11ba9beba6441ee4ffe21abadb5d2eced0976f4197f8758a1691c114085d53dd5385750435e45327c2516ea0dec4f733431b69f73148544a081af866fd9a03cf0ff5f65c348c7d8dbcc47289e25612c0c5772ccf29413be32a6b01e41bd631c4b184f04b47c0ba086aee17d1e3286f3d9925e28013ecaa3d5ccda334334f459419a1bd059d86ed8ffc2fb23ce36e6d8efe3baf2a42b195b59088c0344381047d90d4f01d992d502b49ff0a38e75ffd7b1bd0b66bd2ebe13c700968347992b4660155eab5f4013076ae6d86fde8a7ff6379cd66dfb2da571b3cd44e2949ed96cefa033159405cea7a37c0f9fbeec0bbaf2fd315ffa23175f0e1825b57e9770bd212406efd0fa288d5f37853c9f3522c4d6ce273c536daef88b0d7700f24a311a5a03670b6524f341beb42dbaff6e6a821eba38e8aed36ad58e628b1aae848bb5ef0397298705e3fc98a77ae08fd7540d177ec11cfa63ba3d2328a57b53d614d91f63fc10be65f93360df8aa81 Coverage
Screenshots of Detection AMP ThreatGrid
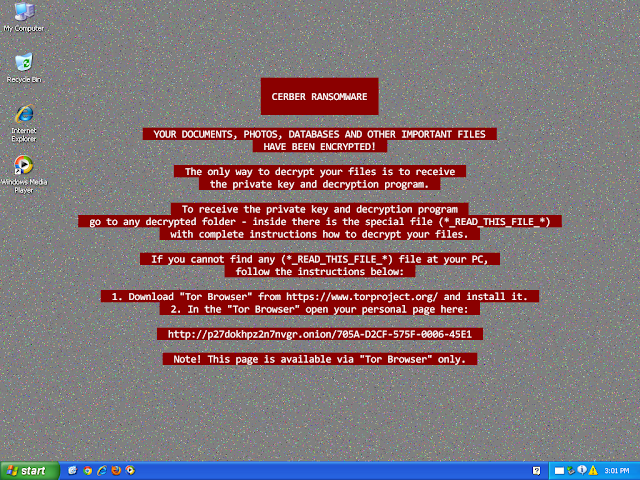
Win.Ransomware.Cerber-6941980-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
15
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
15
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
15
<HKLM>\Software\Wow6432Node\Microsoft\Tracing\RASAPI32
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: EnableFileTracing
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: EnableConsoleTracing
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: FileTracingMask
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: ConsoleTracingMask
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: MaxFileSize
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: FileDirectory
15
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
15
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
15
<HKCU>\SOFTWARE\Microsoft\Speech\Voices
15
<HKCU>\SOFTWARE\Microsoft\Speech\CurrentUserLexicon
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON\AppLexicons
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON\{C9E37C15-DF92-4727-85D6-72E5EEB6995A}
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON\{C9E37C15-DF92-4727-85D6-72E5EEB6995A}\Files
15
<HKCU>\SOFTWARE\Microsoft\Speech\AppLexicons
15
<HKCU>\SOFTWARE\Microsoft\Speech\PhoneConverters
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\VOICES
Value Name: DefaultTokenId
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON
Value Name: CLSID
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\CURRENTUSERLEXICON
Value Name: Generation
15
<HKCU>\SOFTWARE\MICROSOFT\SPEECH\PHONECONVERTERS
Value Name: DefaultTokenId
15
Mutexes Occurrences Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7
15
Local\MSIMGSIZECacheMutex
15
shell.{381828AA-8B28-3374-1B67-35680555C5EF}
15
Local\30F1B4D6-EEDA-11d2-9C23-00C04F8EF87C
15
Local\HKEY_CURRENT_USER_SOFTWARE_Microsoft_Speech_CurrentUserLexicon_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_Chinese_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_English_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_French_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_German_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_Japanese_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_Spanish_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_TraditionalChinese_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_PhoneConverters_Tokens_Universal_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_Voices_Tokens_MS-Anna-1033-20-DSK_Lex_Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_Voices_Tokens_MS-Anna-1033-20-DSK_Mutex
15
Local\{12F67A48-DB8F-46C1-A266-4AD55A97951D}-Mutex
15
Local\HKEY_LOCAL_MACHINE_SOFTWARE_Microsoft_Speech_AudioOutput_TokenEnums_MMAudioOut_Mutex
1
\BaseNamedObjects\shell.{E34ADEF1-7E97-F83F-B563-5CB2AEB03228}
1
\BaseNamedObjects\shell.{5ED88314-B21B-6A1E-9E28-1194C46E655A}
1
\BaseNamedObjects\shell.{009333F1-551C-9DAC-1759-5B4919375F70}
1
\BaseNamedObjects\shell.{AC607669-1359-523E-095D-A88DA96FD1D1}
1
\BaseNamedObjects\shell.{5D9CA089-73FE-FB93-A29C-5A0F541ABED9}
1
\BaseNamedObjects\shell.{1095E0BC-41F3-CF2A-1232-3CB5F90C4677}
1
\BaseNamedObjects\shell.{573F0F01-C284-E3E4-B166-E3C39544ED56}
1
\BaseNamedObjects\shell.{18D0266F-2D74-3F5C-79BE-40E45584D13C}
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 149[.]202[.]251[.]65
14
149[.]202[.]251[.]64
14
149[.]202[.]251[.]67
14
149[.]202[.]251[.]66
14
149[.]202[.]251[.]69
14
149[.]202[.]251[.]68
14
149[.]202[.]251[.]61
14
149[.]202[.]251[.]60
14
149[.]202[.]251[.]63
14
149[.]202[.]251[.]62
14
149[.]202[.]251[.]76
14
149[.]202[.]251[.]75
14
149[.]202[.]251[.]78
14
149[.]202[.]251[.]77
14
149[.]202[.]251[.]79
14
149[.]202[.]251[.]70
14
149[.]202[.]251[.]72
14
149[.]202[.]251[.]71
14
149[.]202[.]251[.]74
14
149[.]202[.]251[.]73
14
149[.]202[.]249[.]207
14
149[.]202[.]249[.]208
14
149[.]202[.]249[.]209
14
149[.]202[.]250[.]8
14
149[.]202[.]250[.]7
14
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences p27dokhpz2n7nvgr[.]1j9r76[.]top
15
api[.]blockcypher[.]com
14
chain[.]so
14
bitaps[.]com
14
btc[.]blockr[.]io
14
crl[.]comodoca4[.]com
9
crl[.]usertrust[.]com
9
w3z5q8a6[.]stackpathcdn[.]com
9
Files and or directories created Occurrences %APPDATA%\Microsoft\OneNote\14.0\Preferences.dat
15
%TEMP%\d19ab989
15
%APPDATA%\Microsoft\Speech
15
%APPDATA%\Microsoft\Speech\Files
15
%APPDATA%\Microsoft\Speech\Files\UserLexicons
15
%TEMP%\d19ab989\4710.tmp
15
%TEMP%\d19ab989\a35f.tmp
15
%LOCALAPPDATA%\Microsoft\Office\Groove\System\CSMIPC.dat
15
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\1016d7ceff188e9fe32e68e9761bd811f354cfb31d7d106ec3c4f3ebce7f7a50[1].json
15
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\all[1].json
15
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\17gd1msp5FnMcEMF1MitTNSsYs7w7AQyCt[1]
15
%APPDATA%\Microsoft\Outlook\Outlook.srs
15
%TEMP%\8f793a96\4751.tmp
14
%TEMP%\8f793a96\da80.tmp
14
\I386\DRVMAIN.SDB
14
\I386\EULA.TXT
14
\I386\HWCOMP.DAT
14
\I386\SECUPD.DAT
14
\I386\SETUPLDR.BIN
14
\I386\WIN9XMIG\ICM\SYMBOLS.PRI\RETAIL\DLL\MIGRATE.PDB
14
\I386\WIN9XMIG\ICM\SYMBOLS\RETAIL\DLL\MIGRATE.PDB
14
\I386\WIN9XMIG\IEMIG\SYMBOLS.PRI\RETAIL\DLL\MIGRATE.PDB
14
\I386\WIN9XMIG\IEMIG\SYMBOLS\RETAIL\DLL\MIGRATE.PDB
14
\I386\WIN9XMIG\PWS\SYMBOLS.PRI\RETAIL\DLL\MIGRATE.PDB
14
\I386\WIN9XMIG\PWS\SYMBOLS\RETAIL\DLL\MIGRATE.PDB
14
See JSON for more IOCs
File Hashes
065ac3b439cf9dfb68574e401b22b854cdded61d57ae9894b0a99915e8f76ee5308c49353001e49e9fbeca1718de74fa0a53d060685f5eeb38fcc0f7c92aac8647e1595cd742e27fa1d89d3bf0de13a1063a44fda27c18fa163da61305953c774afe49d7696926c71f2a702b16fab4525b19eacfa533deff7c7a6222b25b1cc0608a69274b844a4917b03476b84253fbb4dbf98b6f78fd04bb184fc8155fcc50611f4163f797a393b0820f38b72f0ccd4a3d4d2f2606c3bc444f5d850f1b4a587cd8be5830f54b0ac9edf6ef52bcb1aec00527470c615b2eb789085dcadf24e7956ecfd8da6da76db5fd5d3cf0cfdbe9713ee420bcf4d95252e74a834c1b6f04a217aea41ad86b341541765ae803df9bcc4dfda4152eceb576faeb697ebbe970a4573c6717b09a88b1e96037778d1744012990520f26deefd75770a2505b4d4cad8293b33649f28b8d0557ec8ef250d10e1879d20d8ca12bb06f1cd7f18f20e2b276202d46ee89c90e0accfa1998666b0960aa8dc44689ff065d8343698b7ad2c4b25bcea6a8abf8bdff79259c70f7618343550f1d89dd5181467a694e1dc299e16be5f2bc24c321b206ad34563a6f69987dd2ed6884763d01c95cccf66f8ca6eb332302914a3e098767fcca4a9836cab1d87947e56c946301bc0605dbf003f9 Coverage
Screenshots of Detection AMP ThreatGrid
Malware
Win.Malware.Tofsee-6940401-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
29
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
29
<HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
29
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
29
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
29
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
29
<HKU>\.DEFAULT\Control Panel\Buses
29
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
29
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
29
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
Value Name: DisplayName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
Value Name: WOW64
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
Value Name: ObjectName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IBPVUCIX
Value Name: Description
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\haoutbhw
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: Type
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: Start
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: ErrorControl
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: DisplayName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: WOW64
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: ObjectName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\HAOUTBHW
Value Name: Description
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\jcqwvdjy
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\jcqwvdjy
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\JCQWVDJY
Value Name: Type
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\JCQWVDJY
Value Name: Start
3
Mutexes Occurrences Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7
29
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
29
69[.]55[.]5[.]250
29
5[.]9[.]32[.]166
29
46[.]4[.]52[.]109
29
176[.]111[.]49[.]43
29
85[.]25[.]119[.]25
29
144[.]76[.]199[.]2
29
144[.]76[.]199[.]43
29
43[.]231[.]4[.]7
29
65[.]20[.]0[.]49
29
192[.]0[.]47[.]59
29
64[.]98[.]36[.]4
29
172[.]217[.]12[.]164
28
96[.]114[.]157[.]80
28
74[.]208[.]5[.]20
28
74[.]208[.]5[.]4
28
207[.]69[.]189[.]229
27
208[.]89[.]132[.]27
25
148[.]163[.]156[.]1
25
213[.]33[.]98[.]149
25
117[.]53[.]114[.]15
24
213[.]209[.]1[.]129
21
47[.]43[.]18[.]9
21
212[.]54[.]56[.]11
20
64[.]136[.]52[.]37
18
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]in-addr[.]arpa
29
250[.]5[.]55[.]69[.]zen[.]spamhaus[.]org
29
250[.]5[.]55[.]69[.]cbl[.]abuseat[.]org
29
250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
29
whois[.]iana[.]org
29
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
29
whois[.]arin[.]net
29
mx[.]bt[.]lon5[.]cpcloud[.]co[.]uk
29
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
29
cxr[.]mx[.]a[.]cloudfilter[.]net
29
microsoft-com[.]mail[.]protection[.]outlook[.]com
29
gmx[.]net
29
mx[.]lycos[.]com[.]cust[.]b[.]hostedemail[.]com
29
btinternet[.]com
29
lycos[.]com
29
cox[.]net
29
earthlink[.]net
29
mail[.]com
29
ntlworld[.]com
29
victoria1999[.]hotrusgirls[.]cn
29
irina1993[.]hotlovers[.]cn
29
hot-beauty[.]cn
29
hotladies[.]cn
29
mx1[.]comcast[.]net
28
comcast[.]net
28
See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile:.repos
29
%SystemRoot%\SysWOW64\config\systemprofile
29
%SystemRoot%\SysWOW64\IPHLPAPI.DLL
7
%SystemRoot%\SysWOW64\dhcpcsvc.dll
5
%SystemRoot%\SysWOW64\nlaapi.dll
5
%SystemRoot%\SysWOW64\winnsi.dll
5
%SystemRoot%\SysWOW64\dhcpcsvc6.dll
5
%SystemRoot%\SysWOW64\NapiNSP.dll
5
%SystemRoot%\SysWOW64\mswsock.dll
5
%SystemRoot%\SysWOW64\pnrpnsp.dll
5
%SystemRoot%\SysWOW64\dnsapi.dll
3
%SystemRoot%\SysWOW64\ibpvucix
3
%SystemRoot%\SysWOW64\haoutbhw
3
%SystemRoot%\SysWOW64\jcqwvdjy
3
%SystemRoot%\SysWOW64\mftzygmb
3
%SystemRoot%\SysWOW64\winrnr.dll
3
%SystemRoot%\SysWOW64\wpdjiqwl
2
%SystemRoot%\SysWOW64\zsgmltzo
2
%SystemRoot%\SysWOW64\buionvbq
2
%SystemRoot%\SysWOW64\yrflksyn
2
%TEMP%\npkbsmtm.exe
2
%TEMP%\wdqqtewr.exe
1
%TEMP%\fvbuvdtc.exe
1
%TEMP%\resvxxvi.exe
1
%TEMP%\wngjqdpo.exe
1
See JSON for more IOCs
File Hashes
04ad7dc786eee3e32597af6e50c2305f8b47dedd301d2b9fb721a3419c20125e0eabacede3f60e0d1b08c067d12235f47aa610430e47942f570384204d628ce5168db0956ca974da7a3bea33079602dc86341864e7e035a759809a3876544a112934437617803ab26d7e3c836dd1f86c2239302858dbd4cea975dc16932cb53031f71a927a3121b3708e882fe7d7b464abd72ac9833e6a73aade0c2dffe764fb33b9a9b19767a412b37562a9afa071fd6f5590bd4c5c4f25601ac7f7f7aeae2134ab18dbba7d262495b87c114771c62cfe0bdfcb2a70a97a44518280755393e940cc91ab3a8622bca860e93c1048708db75adfc3ceb599e94976115e42f6501543d0885a552ae3eef56ea141745368119a8532577c9c83004c68a03f89c7d27c5257a586503417963b3191e628a4031e9f6c0898310f4c249aa0f3225279e42954234890364c48ea705b30e13e259190259ee4f576e5398e817d6da1fe3fa96359270c4ff4bf0587dc14b4f4430d6d6992e812d966cfa5501af0ca2aaf49c1625b57bf741ac611232855c94a3bae104606940df4f44790178f14e8c3561b7a5a5ce7c6c51748e96f7e233ba3d5bd5a9739a55ca39b86e5c8de41d835c91e3b6c5eda0d87fb85b91dc15c23aecb339cfa8bffefee25b634fe7101d8783a6e99a561a0c30166cab5d8786e060c44c683377f8e94feb66ccd79416c64e8c5a4e9316481910b15bfaee39bc53aa2cb3058e8f93eb40ba1b7f9a63672b7486c0306eb649954ed70b3840321ac3414bdbd8b855c1871d466550d51c9c86bcd8e208c4565279c4a75937f653d2c0085eba669da128d354770c88e50281a583caa8418f365410da84d1f3e53d6f79b15f20ebada17bcbf3c33712c7c7031b807c85e45c36aa1731105b6c97e17511811233db5d76ba52b814a73725412af8076d3f921df6ea680d3d212e30b3e7980643c928aee25acd508cca40191bafcd0db4804a13d75704499b50651600e0df6451e1347bd306d623eed175f64c9e35f77b9b9ee9e7a74f27ca0c5448590d25125d3cf8b5cc2229295a26200fcf3e9144b1d2f9a9b7ae435cdd61433c743865c8e6c042fc9f5e7c1b896faaf7cf0d02d6fa397748aSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Ponystealer-6939264-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Remcos-2EVC58
25
<HKCU>\SOFTWARE\REMCOS-2EVC58
Value Name: EXEpath
25
<HKU>\Software\Remcos-2EVC58
1
Mutexes Occurrences Remcos_Mutex_Inj
25
Remcos-2EVC58
25
\BaseNamedObjects\Remcos-2EVC58
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 216[.]58[.]218[.]238
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences sammorisok55[.]ddns[.]net
25
Files and or directories created Occurrences %APPDATA%\remcos
25
%APPDATA%\remcos\logs.dat
25
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\notepad.vbe
25
%APPDATA%\notepad.exe
25
%HOMEPATH%\Start Menu\Programs\Startup\notepad.vbe
1
File Hashes
3df9897978b990410d530cebb46dca6b9acebfe6d25c89ca5ccadded65382bee402c2d2e333274e70fe04c5a3784b122d11115a37125a2726a5150baceb83b9d4b5996517061fc375ed46ee7ac47a2b562fa15b0a27394cc3eaa5957d31295154ba609c949ff60a4cb2745733dd910f12cac8c4a5c70949a3494d1aae5cfae064f032372da2e85f0d8ab81544dcdb83dc86939b351cffbaea4f430ceac9ca58555db966fb0bb785b70b9fe8ddf85884f21078df2390b1753eaafd8db5cad41925b732616e7563a3053b4e239300e5bcc23806eb34edf2f3a36f858cabd60baf967048f4248d2a7ca781df81d1a1805edcea02997f2b669ae59e12020548ab89a6aabfba3cc6a28b5e8d1ef2d6fdaf1baf2aa8b4ea5e50e1497b393cf7abdbf4286abc8ddb3c2ee5d144f19fd5136e7204406b623ff62d62000fc02b23940bd4e93cf058391c6f9a1c08f4e6e3dcc3cf8ffffbdf8ccc53c6f96f1216565f254dcab9f396fe8f8f95ead229a868ca8bd4759cda466631b5875aff23947f11af642b3f8290ab9931c9bc66087ba675090f929ed10a08406e4e777c7510139ff873fb5e265d77dbbb68dc78e3af0424fc08e557d73b7b7606c74045275cddabf5c1bb9ba42465c13db17773063cfc38e1af8ae2432f076eb636c2198abb808095531c35ce41bb8126e2939f6d2e48700cd3c0693ec8c63c320dbd88497e6396981e4d21e953d19cfd0c341d20a69ab8e0d8c8065d6f8b25a183af68ea15da7179a61dd19360d5d44f2d11f7d49a6199d3574a59c84b181273f00a98019bc5cc5cb7deaffe74478f09ab236b8b2947bc9922b61735bf5aef9bbc3502d1b8349f0b2d3f3b9f50bb71c876d1d1d0c699e9d6de33c2e72bf43e2737b0f832dae4a869414f42f148da1774e2a94a281e7f5ccbd1d9acae7e6daad8fee93ee56a53ea3e3d4fa29a663720797cb031e1edd64879f1841bb90082976c4456d011df4b30037d5fd51df072b783b2614c811d4915c8ed17ef5f4d45310189a5953ccd77e7737cefda04458f2c2aa2da575f8ee68801398d2a1ca8753ef47f21187c49686bdf558ff6138f7829b95f1d545f3d361a98c1f494fd4c7915ccbc19392d074ae47fda7 Coverage
Screenshots of Detection AMP ThreatGrid
Doc.Downloader.Emotet-6938868-0 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: AutoDetect
25
<HKCR>\INTERFACE\{8BD21D22-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{8BD21D32-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{8BD21D42-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{8BD21D52-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{8BD21D62-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{7B020EC2-AF6C-11CE-9F46-00AA00574A4F}
25
<HKCR>\INTERFACE\{7B020EC7-AF6C-11CE-9F46-00AA00574A4F}
25
<HKCR>\INTERFACE\{79176FB2-B7F2-11CE-97EF-00AA006D2776}
25
<HKCR>\INTERFACE\{4C5992A5-6926-101B-9992-00000B65C6F9}
25
<HKCR>\INTERFACE\{796ED650-5FE9-11CF-8D68-00AA00BDCE1D}
25
<HKCR>\INTERFACE\{47FF8FE0-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE1-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE2-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE3-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE4-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE5-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE6-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE8-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE9-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{5CEF5613-713D-11CE-80C9-00AA00611080}
25
<HKCR>\INTERFACE\{92E11A03-7358-11CE-80CB-00AA00611080}
25
<HKCR>\INTERFACE\{04598FC9-866C-11CF-AB7C-00AA00C08FCF}
25
<HKCR>\INTERFACE\{7B020EC8-AF6C-11CE-9F46-00AA00574A4F}
25
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CONNECTIONS
Value Name: DefaultConnectionSettings
25
Mutexes Occurrences Global\I98B68E3C
25
Global\M98B68E3C
25
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 103[.]18[.]109[.]161
25
190[.]8[.]176[.]146
25
187[.]188[.]166[.]192
25
88[.]215[.]2[.]29
24
187[.]137[.]162[.]145
19
65[.]49[.]60[.]163
15
72[.]18[.]130[.]128
1
50[.]87[.]144[.]137
1
169[.]61[.]113[.]80
1
74[.]124[.]214[.]228
1
195[.]186[.]120[.]53
1
23[.]229[.]190[.]0
1
200[.]147[.]41[.]245
1
177[.]70[.]110[.]119
1
192[.]185[.]223[.]55
1
200[.]68[.]105[.]32
1
217[.]26[.]49[.]199
1
195[.]186[.]198[.]217
1
158[.]69[.]189[.]204
1
190[.]183[.]222[.]139
1
200[.]58[.]120[.]2
1
167[.]250[.]5[.]2
1
85[.]10[.]205[.]9
1
138[.]118[.]172[.]253
1
192[.]185[.]148[.]208
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences aussiescanners[.]com
25
fumicolcali[.]com
25
smtp[.]vendwidias[.]com[.]br
1
smtp[.]cl-seguros[.]arnetbiz[.]com[.]ar
1
mail[.]bhz[.]terra[.]com[.]br
1
imap[.]nazaria[.]com[.]br
1
pop[.]jfwtransportadora[.]com[.]br
1
mail[.]agroconsultsrl[.]com[.]py
1
pop[.]naqua[.]com[.]br
1
mail[.]jroveda[.]com[.]br
1
mail[.]totalms[.]co[.]uk
1
mail[.]haciendachiapas[.]gob[.]mx
1
mail[.]dieselwheels[.]com
1
mail[.]amaralvidros[.]com[.]br
1
smtp[.]vivaceramica[.]com[.]br
1
smtp[.]umbler[.]com
1
mail[.]comerciallyb[.]cl
1
mail[.]negociosinternacionales[.]com
1
mail[.]procegas[.]com
1
smtp[.]sor[.]terra[.]com[.]br
1
pop[.]avante[.]com[.]mx
1
mail[.]abatsa[.]com[.]mx
1
gator4113[.]hostgator[.]com
1
dtcwin055[.]ferozo[.]com
1
uscentral434[.]accountservergroup[.]com
1
See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
25
%APPDATA%\Microsoft\Forms
25
%APPDATA%\Microsoft\Forms\WINWORD.box
25
%HOMEPATH%\480.exe
25
%SystemRoot%\SysWOW64\version.dll
1
%SystemRoot%\SysWOW64\wtsapi32.dll
1
%SystemRoot%\SysWOW64\cryptsp.dll
1
%System32%\en-US\tzres.dll.mui
1
%System32%\WindowsPowerShell\v1.0\DotNetTypes.format.ps1xml
1
%System32%\WindowsPowerShell\v1.0\HelpV3.format.ps1xml
1
%SystemRoot%\SysWOW64\aY7vprZGHT2Qh.exe
1
%SystemRoot%\SysWOW64\8aP4tvN3RT8.exe
1
%SystemRoot%\SysWOW64\H1r53NRGp.exe
1
%SystemRoot%\SysWOW64\HjMdJgmjW15bz.exe
1
%SystemRoot%\SysWOW64\2E60ntwKpo.exe
1
%SystemRoot%\SysWOW64\OGnsYK.exe
1
%SystemRoot%\SysWOW64\ZH6MNgKJytF.exe
1
%SystemRoot%\SysWOW64\tgRT5a3mCza.exe
1
%SystemRoot%\SysWOW64\Ne3EjNKGuuhmY6jFW.exe
1
%SystemRoot%\SysWOW64\TfGf.exe
1
%SystemRoot%\SysWOW64\rK4xjEqhKGACuL.exe
1
%SystemRoot%\SysWOW64\xmASsy4Qf.exe
1
%SystemRoot%\SysWOW64\4C3Cp6cy40lUnD2SKBU.exe
1
%SystemRoot%\SysWOW64\T5klBSN2QHk.exe
1
%SystemRoot%\SysWOW64\vkU5YM.exe
1
See JSON for more IOCs
File Hashes
061fd00e92e9bc6a34db2a6ab27dad3ec9f759b34c72146c1f0aa2adc3413de7112278e446cc3c7f538089cae3eaf962b06218cae4bcd8fb9a0b493bc380507f17a8cd33792dff1c0b4b8cfac6b53461fa2d4f5936215e47897ea73103666c831cb1730670ec3dce6db6afa0762f9bfa74d06df041829c68a6f161ec6cf6bdf51eb3cc2781765f1c81bdef0390ba79fc2066fd1bd8ff5571baa64f4b0ca3441f24851bfbaf8226566a06e642ecf7ea697b93a492d0022f82ba7d140ae03789303044f43b040d476ac859f7f55a35f0e2332c86b60ae6703054b811e28ac61ed638caefbe8cf358d241edef7d33775c6825699282a79bc1eb9691b1f918f277dd4558edbe3b57be5c595405ba601a13ae09c679a01f851ae43f8c34e6d3c34be05017ececeb4d4f7c8483dd8178df693760ad227e94053b560ac60cd81870b199609fffab37310c162348ebbf3b967e490753d85d08ad725863f98d9cc87582c6636c93930f056e403a2bdb2298f18c0b14542c0224fd0ba6ba3056d1367f9c756962bc3a08ec27c0012e28caea3c39da8e89bd67d8baf383a940b17d6ada848f69a5f2c702ee4b623edca48860362335c590b4ae3ef2af6aaf3d66875f00461a7bfa97ac3d0200757d0ea1aa8ef25e6d8babf1d5549e4e1bb269fd08139c53608fa2a91359b44c86c77775b3227c8ae0ccf1f882dafaa3309d0b8fb31543727492e7309c19b46a017c46f81c0d423a581c28e41e3b956b223c3be6834c0251be96786504ad52978d682b65996187b87e60297bf202a1ef9a9c150a06f0b87e4c9bb3d3a40c0a57ee9a52bab10b2ec0efbf7d665238c421a68c266d356b81a671ab80799e4eb0b2f4f44a4ea326b87ca16e2ffd1fb7ca60691cb2e338fca8c147ac3eb7028c680b1e8810b55350e64a8f30f4de2135fcd6b18ad55a779fd4619daf77939a3206c6beeb32606423daeb8236413630ddd3846ac300d741d8809108b9a0e0d4946ccf898e50182d2fd64fb05abfb37aa19b9d66288db57d6a6f8a8cbb96f404b090c1e4c7853dadaad4846d135969a401747c87ee93b760fc844331be2ce66817fc6408bbbdfd5d9207a57acb66c190308b5a4a21eab7c1f3846193See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Fareit-6938631-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\WINRAR
Value Name: HWID
9
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003E9
Value Name: F
9
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000001F5
Value Name: F
9
<HKLM>\SAM\SAM\DOMAINS\ACCOUNT\USERS\000003EC
Value Name: F
9
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
1
<HKLM>\Software\Wow6432Node\Microsoft\Tracing\59af6fd2267a663fcc7f2a9e1e4bc131_RASAPI32
1
<HKLM>\Software\Wow6432Node\Microsoft\Tracing\59af6fd2267a663fcc7f2a9e1e4bc131_RASMANCS
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\59AF6FD2267A663FCC7F2A9E1E4BC131_RASAPI32
Value Name: FileDirectory
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\59AF6FD2267A663FCC7F2A9E1E4BC131_RASMANCS
Value Name: FileDirectory
1
<HKCU>\Software\windowupdate2-4UUS6W
1
<HKCU>\SOFTWARE\WINDOWUPDATE2-4UUS6W
Value Name: Inj
1
<HKCU>\Software\Remcos-EEMFAJ
1
<HKLM>\SOFTWARE\Wow6432Node\Microsoft\Active Setup\Installed Components\{7616H3MP-B552-KB3O-PIO3-3PP888E55KW5}
1
<HKCU>\SOFTWARE\REMCOS-EEMFAJ
Value Name: licence
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{7616H3MP-B552-KB3O-PIO3-3PP888E55KW5}
Value Name: StubPath
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: BOOKS
1
Mutexes Occurrences Remcos_Mutex_Inj
3
A16467FA7-343A2EC6-F2351354-B9A74ACF-1DC8406A
3
Global\LOADPERF_MUTEX
1
A16467FA-7343A2EC-6F235135-4B9A74AC-F1DC8406A
1
DSKQUOTA_SIDCACHE_MUTEX
1
-
1
.NET CLR Data_Perf_Library_Lock_PID_640
1
.NET CLR Networking 4.0.0.0_Perf_Library_Lock_PID_640
1
.NET CLR Networking_Perf_Library_Lock_PID_640
1
.NET Data Provider for Oracle_Perf_Library_Lock_PID_640
1
.NET Data Provider for SqlServer_Perf_Library_Lock_PID_640
1
.NET Memory Cache 4.0_Perf_Library_Lock_PID_640
1
.NETFramework_Perf_Library_Lock_PID_640
1
ASP.NET_1.1.4322_Perf_Library_Lock_PID_640
1
ASP.NET_4.0.30319_Perf_Library_Lock_PID_640
1
ASP.NET_Perf_Library_Lock_PID_640
1
BITS_Perf_Library_Lock_PID_640
1
ESENT_Perf_Library_Lock_PID_640
1
Lsa_Perf_Library_Lock_PID_640
1
MSDTC Bridge 3.0.0.0_Perf_Library_Lock_PID_640
1
MSDTC Bridge 4.0.0.0_Perf_Library_Lock_PID_640
1
MSDTC_Perf_Library_Lock_PID_640
1
Outlook_Perf_Library_Lock_PID_640
1
PerfDisk_Perf_Library_Lock_PID_640
1
PerfNet_Perf_Library_Lock_PID_640
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 62[.]173[.]140[.]44
1
2[.]59[.]41[.]199
1
80[.]90[.]39[.]2
1
178[.]124[.]140[.]134
1
95[.]167[.]151[.]246
1
213[.]226[.]126[.]118
1
89[.]223[.]91[.]211
1
195[.]133[.]144[.]169
1
213[.]226[.]68[.]93
1
167[.]88[.]160[.]146
1
77[.]221[.]144[.]122
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences wellgam[.]com
6
WELLGAM[.]COM
4
frupidgi[.]cn
3
silfa[.]pw
3
SILFA[.]PW
3
wttiredfc[.]com
1
arispedservices[.]eu
1
Files and or directories created Occurrences %ProgramData%\Microsoft\Vault\AC658CB4-9126-49BD-B877-31EEDAB3F204\Policy.vpol
4
%LOCALAPPDATA%\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28\Policy.vpol
4
%TEMP%\37FFCBBC\api-ms-win-core-datetime-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-debug-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-errorhandling-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-file-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-file-l1-2-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-file-l2-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-handle-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-heap-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-interlocked-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-libraryloader-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-localization-l1-2-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-memory-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-namedpipe-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-processenvironment-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-processthreads-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-processthreads-l1-1-1.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-profile-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-rtlsupport-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-string-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-synch-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-synch-l1-2-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-sysinfo-l1-1-0.dll
2
%TEMP%\37FFCBBC\api-ms-win-core-timezone-l1-1-0.dll
2
See JSON for more IOCs
File Hashes
073cb94ad50991e82bfa04d55bc03afdf3a56962ee5dd750dae0719250e8ae651f4b210d95c8579399cd740a2887ad5dcdeceb97833a0be187815b1404cca34a243079480c0b1b3738c95610a384faf49bf4da2d206938570814d1f7d0a48447384ccd374a7b0ad96c05c598a8805af2c0171554a8caa56b383b60f7a847e26f3970c631a11302aa2769cf03e54b7f58fc09f7d8ed1590b48efcdef468cc7af73cded376ba5039cedca137403ea8abeae60a98ee666954e2d148f4cd13f446df6d3088bc9c809f752614aca0bd966758e0bde32ec5e1a7b75d4bbc544ed13cda79a9506b375a4728a84203ca601f4e561973de51421e28b37d7e56625134d6df87ae6f32cea09d6664c923e32aa24041fef9787e74a5cd6f5e20c058c16c7ffe9475131e5c57dbc60beb45669b58a26ee28af7aa65b90bb53b2646a86f4aad399b9e07d8b709b5257125bfdc04848d1d28232fcfcc0caf22bb58b9ddb1c3d3aea1c1ed52d04468d58c5d51f35718ada1b1f1d7ddb4c637bdb7c887dc0966b407a552f5070d93037fffaec488750b3f000d46fedc7f70e42c0b0cdd42d4ae4805b47dd06ed3f8512f0a7dfddd76d6ebce52be75d4bdf7350aa625ae441efe9637b89daf58637c8023e41b6bac95969df87a2d259187436ba64023a97b8bf2085cbc6d99b1311f8ecb6b60ba7379c4ab9e568bc4f232d214eb23abfef555929efcc6d76a61f441862a7b6880c7faf093a185a723825e22ef8df5a772889f7302a7cd476668e2348c443630d7c52b75f67e8d7ec1b86a5a65a614b52fb62e019928cf7c5ad0aee65aae567e53cceb53c954712377d4958da6f0a45983b279d279a0d6996f7c5e6db6805bf893a5d5b1259cf9acf9c30cdca120d25416063c46bd68e739c021bdd5165827e4c5e2c118bd9a7107487515e4ab182e4b99d03c3701cfeac79f944bdbd92c73cb179b61d2e34495d050e929e5068143e22bf0d31fa693ebd9171d7fd10bb3c5234458f33df42a5d4a652a3a1c6bb5a045d94a29c40529ec681af368a0a3cbbdfea9744ed80ad37bc9166be9a8698310ba18276450047ffb77150a54a4f0cb5b495bd24927e70cd6a0dd519d9e8192a729d08753a48eefSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Ircbot-6938570-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: *-334428029
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: *-334428029
1
Mutexes Occurrences gcc-shmem-tdm2-fc_key
16
gcc-shmem-tdm2-sjlj_once
16
gcc-shmem-tdm2-use_fc_key
16
UPDATE__
16
BACKUP_1295690263
1
MAIN_1295690263
1
BACKUP_-959641963
1
MAIN_-959641963
1
BACKUP_953815319
1
MAIN_953815319
1
BACKUP_2070810229
1
MAIN_2070810229
1
BACKUP_895421598
1
MAIN_895421598
1
BACKUP_1582140582
1
MAIN_1582140582
1
BACKUP_-1913070738
1
MAIN_-1913070738
1
BACKUP_-334428029
1
MAIN_-334428029
1
BACKUP_839036346
1
MAIN_839036346
1
BACKUP_-813287923
1
MAIN_-813287923
1
BACKUP_175490003
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 104[.]200[.]23[.]95
1
153[.]92[.]0[.]100
1
204[.]74[.]99[.]100
1
88[.]99[.]150[.]216
1
185[.]53[.]178[.]6
1
141[.]8[.]197[.]42
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 3ASH2[.]COM
2
3ash2[.]com
2
www[.]mydomaincontact[.]com
1
iyfsearch[.]com
1
site[.]com
1
www[.]bplaced[.]net
1
bociklocik[.]ye[.]vc
1
f0164361[.]xsph[.]ru
1
wolfayoub[.]3eeweb[.]com
1
MARSON42[.]COM
1
marson42[.]com
1
mydankmemes[.]club
1
myfreedomainlol[.]tk
1
vitusend[.]net84[.]net
1
time-by123[.]esy[.]es
1
argenfull[.]com
1
ARGENFULL[.]COM
1
WWW[.]TOR4FUN[.]FR
1
www[.]tor4fun[.]fr
1
update-sam[.]square7[.]ch
1
urminenow[.]0xhost[.]net
1
holdbet[.]ru
1
HOLDBET[.]RU
1
Files and or directories created Occurrences %System32%\config\SOFTWARE.LOG1
16
%HOMEPATH%\NTUSER.DAT
16
%HOMEPATH%\ntuser.dat.LOG1
16
%APPDATA%\1295690263
1
%APPDATA%\1295690263\unsecapp
1
%APPDATA%\-959641963
1
%APPDATA%\-959641963\realsched
1
%APPDATA%\953815319
1
%APPDATA%\953815319\unsecapp
1
%APPDATA%\2070810229
1
%APPDATA%\2070810229\winsys
1
%APPDATA%\895421598
1
%APPDATA%\895421598\ctfmon
1
%APPDATA%\1582140582
1
%APPDATA%\1582140582\spoolsv
1
%APPDATA%\-1913070738
1
%APPDATA%\-1913070738\realsched
1
%APPDATA%\-334428029
1
%APPDATA%\-334428029\BCU
1
%APPDATA%\839036346
1
%APPDATA%\839036346\winlogon
1
%APPDATA%\-813287923
1
%APPDATA%\-813287923\csrss
1
%APPDATA%\175490003
1
%APPDATA%\175490003\winlogon
1
See JSON for more IOCs
File Hashes
1a8935840e4fa3db5ef5945efdccffcbbb92d569955ee3c0076d41da33845d5545e7c5547dcb5181ad47ca2e8690e2cb9a024744c3da6159ab3ed1ea39d460134a5d82ef0f2ecc204d6c83f837fe6be561a36b58c077e444b9525e42bcf6cb084e02e5fc44bba1091e0768b74f551c0a6af232ac0458c5a21006fff81e49bffd52793b260576e44014dc48d2ef2d8f517b0460542b35070d71b3d12cecbb468e956936346a4be7bd07369448077a059ae70d270c04e9b3c019e5d7997c084fa698be103bf04ceed1678baca10755c149df93c57185c5c387ecd27f3ebb2242cba20fb11ec04d7bfadfd1758fa6d6103522fa60b6a590217d48d093655f6ec132a2da28c09898396c073b3e7078b2bcad1f16b0b22ec8c0727936ffedb45027a4d8bce14120c6cc44e057a6ef8986fd5cd5a647f2c720051cce7ce6704fef3a56db2199becac0af02a28f968555d78a6699cf2f13660774616995a08428eba89edbd2ea95e8a86edf7ef5b62c266b1746dc9e4936754d7fdd867184c6f13a53daea3eb5b6e80c6b3ab6aaa65677ae28426f8bf92439a3f6820ed7ec57f71efebced045c078e29caa8cd44174965c2d5470cbe84a46751bfd7d45a6264d3d59ebaf23f0cf834d3b8d97cb707fae3296787f665c35dd1e7abf27c007e9a50697381ff7ca213e6af53e15883fc8fd07ec6a1d9b9bc3a99554d7888558680e2238710 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Madshi injection detected (4097)Kovter injection detected (2923)PowerShell file-less infection detected (1334)Process hollowing detected (494)Dealply adware detected (193)Gamarue malware detected (173)Atom Bombing code injection technique detected (168)Trickbot malware detected (137)Suspicious PowerShell execution detected (114)Excessively long PowerShell command detected (87)