Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 19 and April 26. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
Win.Malware.Gandcrab-6954107-0 Win.Malware.Kovter-6953553-0 Win.Packed.Scar-6952917-0 Win.Dropper.Lydra-6952708-0 Win.Trojan.Zeroaccess-6952579-0 Doc.Downloader.Powload-6952235-0 Win.Ransomware.Cerber-6952131-0 Win.Packed.Tofsee-6952124-0 Win.Malware.Emotet-6947486-0 Win.Malware.Mikey-6953803-0 Threats Win.Malware.Gandcrab-6954107-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: mrtauqkjwnb
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: taiqbyxzlxk
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: kgdxylqkehn
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: wthkafbhnnz
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: csrzoywxadl
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: wyvcshrzmzp
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: htiqstanrob
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: wpxojreokly
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: blyfivnejxn
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: lrrnacksfnc
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: kamceprdczy
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: itqfvoapacm
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: ncqtnmbrepx
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: wiuqosifjbq
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: sktkqyirmst
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: bwipaxisell
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: hdcpovptyus
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: jquurrwhzkq
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
Value Name: ysblnuivkrs
1
Mutexes Occurrences Global\pc_group=WORKGROUP&ransom_id=4a6a799098b68e3c
19
\BaseNamedObjects\Global\pc_group=WORKGROUP&ransom_id=ab8e4b3e3c28b0e4
19
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 66[.]171[.]248[.]178
19
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 1[.]1[.]168[.]192[.]in-addr[.]arpa
19
ipv4bot[.]whatismyipaddress[.]com
19
1[.]0[.]168[.]192[.]in-addr[.]arpa
19
malwarehunterteam[.]bit
19
ns1[.]virmach[.]ru
19
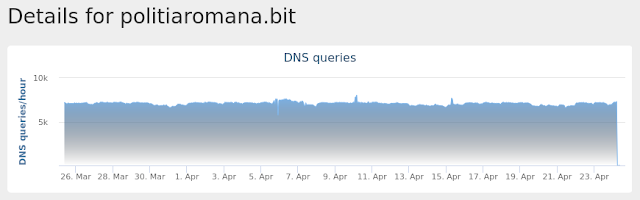
politiaromana[.]bit
19
gdcb[.]bit
19
ns2[.]virmach[.]ru
19
Files and or directories created Occurrences %APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c5
19
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\O1OD133V.htm
19
%HOMEPATH%\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\desktop.ini
15
%HOMEPATH%\Local Settings\Temporary Internet Files\Content.IE5\C5MZMU22\ipv4bot_whatismyipaddress_com[1].htm
15
%APPDATA%\Microsoft\hghbta.exe
1
%APPDATA%\Microsoft\gknrwh.exe
1
%APPDATA%\Microsoft\fpimav.exe
1
%APPDATA%\Microsoft\menqqw.exe
1
%APPDATA%\Microsoft\yajjhk.exe
1
%APPDATA%\Microsoft\fttqrq.exe
1
%APPDATA%\Microsoft\ggxike.exe
1
%APPDATA%\Microsoft\lxhknn.exe
1
%APPDATA%\Microsoft\aojsiy.exe
1
%APPDATA%\Microsoft\nsxpnb.exe
1
%APPDATA%\Microsoft\tywgei.exe
1
%APPDATA%\Microsoft\ucihie.exe
1
%APPDATA%\Microsoft\odrxqe.exe
1
%APPDATA%\Microsoft\clhbpq.exe
1
%APPDATA%\Microsoft\vacwir.exe
1
%APPDATA%\Microsoft\pzgooz.exe
1
%APPDATA%\Microsoft\ivnaov.exe
1
%APPDATA%\Microsoft\yvudxg.exe
1
%APPDATA%\Microsoft\lfkjbm.exe
1
\Win32Pipes.0000052c.00000017
1
\Win32Pipes.0000052c.00000019
1
See JSON for more IOCs
File Hashes
1156e142aafbd439ee6bd2a9d0e8cd9fd4719ee9d9242b9c1916bfe1b45db99a14f1688ab3d4c0866797ad43dc7df51d913a5df763fb12c7b72391075945cd8d194966a4700fbad5d329b75df3794730255ec8afe5c2f385e45c79337f1cbb391f2a5163a9b3206f45a03c23bb05ad6c71d22add96374d9c127db58fe72289a23c8cdaf3626ede0754ea0f16a67c079ef4670cba8d0e1c4a88bd47856dbd49cb45376d6ccfe68d1b2b82ad50f59f376917e17a09e2be48da015770f6a549f7af468ea3dc192ff158b09e6cc09c8d4a190d5744dff6225edb93ae2385a75d91204cd88fe74eabf6fff9bcf700cae21da6021a1b45ad2c759b873f00031ec2f60d5783f8f86692861ff73c02a84860086940a1dc31aa9c821804188f0e8e8ff1d05e0171a3a7832430d85b4681a247bb0f82aa3f07f024fa8605d3e9f7836ca6ec7db58ac99c57662954d7f4183a5945bd352e7db6a0e3aebf31c19c29bc78a7d98745527a3c123b9155ae7d470cc549fcecbd97be2c515b8711412e93071c1babb1a195b1dc49ec6adaed3f6a9eb1e3a1089106ab8503f5e541897230c9c2fd5ec6a7fa1f1f89d235957ce7fd38051a7e9a921847a30c6309da1c5e8cffb71e5ed3cd9d746c796dc68b4dfae7657fcec9bad4c00cf2addb4f90ac1480beb8e0b2d8752dbe07dd9642d6bb7f65701338d99ce8fb718ae803eb12ea41ff5ca15671e1f314bc382f2163df72cd7aa083a2d3a4a78b0e6315689359bb543b5ee872aef1f63b367f7731f515f3076835426af9086e950b218b5371bc23d8c51e3a7c02f8fd3c82782868205270cdc0b2edfd8c51a5da900bede625a16c1943b4ccd1e3 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Kovter-6953553-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WindowsUpdate
29
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUpgrade
29
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: internat.exe
28
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE
Value Name: DisableOSUpgrade
28
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\OSUPGRADE
Value Name: ReservationsAllowed
28
<HKLM>\SOFTWARE\WOW6432NODE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
28
<HKCU>\SOFTWARE\3a91c13ab1
28
<HKLM>\SOFTWARE\WOW6432NODE\3a91c13ab1
28
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: 656f27d6
28
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: 656f27d6
28
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: 96f717b3
28
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: 96f717b3
28
<HKLM>\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION
27
<HKLM>\SOFTWARE\WOW6432NODE\3A91C13AB1
Value Name: 01b2a448
25
<HKCU>\SOFTWARE\3A91C13AB1
Value Name: 01b2a448
25
<HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
2
<HKLM>\SYSTEM\LastKnownGoodRecovery\LastGood
2
<HKLM>\SOFTWARE\WOW6432NODE\8A6FD29F760019C2A
1
<HKLM>\SOFTWARE\WOW6432NODE\S191vn
1
<HKLM>\SOFTWARE\WOW6432NODE\8A6FD29F760019C2A
Value Name: 22F2A9371858821393B
1
<HKLM>\SOFTWARE\WOW6432NODE\3E4A82EF50861857D
1
<HKLM>\SOFTWARE\WOW6432NODE\LM7zAclcB
1
<HKLM>\SOFTWARE\WOW6432NODE\S191VN
Value Name: noVD3r8i
1
<HKLM>\SOFTWARE\WOW6432NODE\S191VN
Value Name: Ja8WDQ2COI
1
<HKLM>\SOFTWARE\WOW6432NODE\3E4A82EF50861857D
Value Name: B6FAE5718727427E545
1
Mutexes Occurrences B3E8F6F86CDD9D8B
28
A83BAA13F950654C
28
EA4EC370D1E573DA
28
Global\7A7146875A8CDE1E
28
\BaseNamedObjects\408D8D94EC4F66FC
24
\BaseNamedObjects\Global\350160F4882D1C98
23
\BaseNamedObjects\053C7D611BC8DF3A
23
\BaseNamedObjects\Global\ServicePackOrHotfix
2
\BaseNamedObjects\Global\F7E10F769B0682E7
1
\BaseNamedObjects\2594BA9F8AA549A0
1
\BaseNamedObjects\95780D7FD6724D3D
1
\BaseNamedObjects\93444A15B4316C7F
1
\BaseNamedObjects\8AD0B80D27B7A6E8
1
\BaseNamedObjects\Global\CE758B9A90197724
1
\BaseNamedObjects\3E54017756DC8D88
1
\BaseNamedObjects\Global\E04DD8EC68AC932B
1
\BaseNamedObjects\254092C2E3B50CC1
1
\BaseNamedObjects\1AF828CB730214EA
1
\BaseNamedObjects\6CF52592B2A80076
1
\BaseNamedObjects\Global\15907BF02B9082CF
1
Global\ebcd2841-665f-11e9-a007-00501e3ae7b5
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 23[.]10[.]207[.]183
2
96[.]16[.]151[.]89
2
23[.]96[.]52[.]53
2
23[.]196[.]183[.]170
2
126[.]51[.]184[.]10
1
104[.]119[.]186[.]70
1
55[.]20[.]15[.]80
1
27[.]121[.]99[.]80
1
166[.]57[.]220[.]214
1
24[.]210[.]219[.]136
1
103[.]83[.]13[.]134
1
192[.]201[.]48[.]88
1
94[.]105[.]89[.]64
1
49[.]27[.]243[.]48
1
31[.]109[.]216[.]73
1
122[.]210[.]74[.]190
1
97[.]158[.]71[.]252
1
177[.]96[.]54[.]160
1
207[.]4[.]93[.]221
1
73[.]58[.]236[.]14
1
51[.]103[.]86[.]160
1
157[.]32[.]43[.]20
1
174[.]135[.]47[.]97
1
59[.]76[.]122[.]178
1
212[.]180[.]197[.]146
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences e10088[.]dspb[.]akamaiedge[.]net
4
e3673[.]dspg[.]akamaiedge[.]net
4
www[.]cloudflare[.]com
1
cpanel[.]com
1
cp[.]aliyun[.]com
1
netcn[.]console[.]aliyun[.]com
1
www[.]timo-ex[.]com
1
Files and or directories created Occurrences %TEMP%\WindowsXP-KB968930-x86-ENG.exe
4
%HOMEPATH%\Cookies\administrator@microsoft[1].txt
4
%HOMEPATH%\Cookies\administrator@microsoft[2].txt
4
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\55F5KQ7B.htm
2
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\BY8YMTTN.htm
2
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\DRMICMKU.htm
2
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\DU14067I.htm
2
%HOMEPATH%\Local Settings\Temporary Internet Files\Content.IE5\KACXHDUX\desktop.ini
2
%SystemRoot%\inf\oem13.PNF
2
%SystemRoot%\inf\oem13.inf
2
%System32%\CatRoot2\dberr.txt
2
%SystemRoot%\KB968930.log
2
%HOMEPATH%\Local Settings\Temporary Internet Files\Content.IE5\KACXHDUX\WindowsXP-KB968930-x86-ENG[1].exe
2
%HOMEPATH%\Local Settings\Temporary Internet Files\Content.IE5\KACXHDUX\en-us[1].htm
2
%APPDATA%\Microsoft\Windows\Cookies\DU14067I.txt
1
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\index[1].htm
1
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\00A87HPC.htm
1
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\9UBKMUJA.htm
1
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\FQVQQJXR.htm
1
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\V69XW46D.htm
1
\5965c0b5c4bb27a5399e\wsmwmipl.dll
1
\5965c0b5c4bb27a5399e\wtrinstaller.ico
1
%HOMEPATH%\Local Settings\Application Data\cacipe\cacipe.exe
1
%HOMEPATH%\Cookies\administrator@104.31.137[1].txt
1
File Hashes
03dae55b56d3cf11136529cd2be296e4d6aa1a017f44a898d11ecc0b1b43e16e06f1a2cffda751ae87026e4d5f54c2767a474b3aca7c9ddd2b1f7247a3ff75f60b01f3a59fcaa6520b12f9e3bdda2615e25b41e1d5c9e23e36a5f61c75e960ba19c78081714b6154ce25bb431959dc537618338038ae30c866afb3d6d00949961f3a83a9744812c5b094691b4a87c4475fd8cbb85e69bf298edf917589261d4a296af0b5e6f6e033108a2a7109f40e1152f1c4ead15db644dc5d0d0973de21f42a5c411fd65bb32f8f72b06ad17d8cb20258fc92dd1a7051e44550c314cc77f53b94d3a36980ad21baaf5c62d669160988880e9aac3c2db29c3f23609a4eaa533cbcc6671e6a7092a8a3f52d3cf93ff3d7c420fe6b0a34ec8bd0071a7d6852173eab679b54cca6b0352b05c821b65dbc34e16f323d60986d728ea955897a55ee44c5491ef99c542e06b1e166e5313dfb0007dd248bd08c6edaf72ce32f45232b4b21ddc1d7e40802368f07299c0634f96323285c829aacea603aefc8f8f97e284f586d783cbd24a2cddee826f172ffeffbb953913721b87090f73cdc20e5da1b5423ba59c1ae44dcd47385f0820c020657f56e2511453937adeb1eb73dcb5b2c54d941b8f77a638074bc1a7f59f8f1650ca7e4e3077b7af6c79ebb9448656d15552d1a03140e12a901753649a8eb234a337ee08dd57c1892f3a641bd7c1e332c613d13d8759215714c4af6dc6f7af9e8984816d10265fc4203e3b87dddc784d77c54f727e0a21feecd3f1f4757050ff27722b0097db4781b25a157376c7e369383779e88704948dc02873d609db5d3efb4a47f968b5ce9d0e5edf02a7b7e56e791441e8775ea05faace24c054d0d913459d9e2d61d9cb2edec9692d2dc099e78a5d9ccde01ee0baee4d86ae8bedce0bee0e6637f818e9707582481fa3459b87ca606074562594ed99706376dec2e0991de42f98dd5c2718253e796b75b7d748cb15ffdd820f05d45e29a1a58a15a0ac04e2c694e0507146de04f2038e52e5187cafc5428cde0b46cc3472becf2a7360c309b6e7fd6b87243238eff0684215b84cb5be428b5adeb1cfd372ea525bc8ee0e6244f05e4a25779e9ba5d1da57b2f12See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Packed.Scar-6952917-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\localNETService
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: Type
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: Start
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: ErrorControl
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: ImagePath
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: DisplayName
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: WOW64
27
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\LOCALNETSERVICE
Value Name: ObjectName
27
<HKLM>\Software\Wow6432Node\localNETService
17
<HKLM>\SOFTWARE\localNETService
15
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_8350
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_31696
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_12733
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_33107
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_24485
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_29347
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_48270
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_58951
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_3373
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_25588
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_8958
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_16087
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_3445
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_2899
1
<HKLM>\SOFTWARE\WOW6432NODE\LOCALNETSERVICE
Value Name: Value_24818
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences %ProgramData%\localNETService
27
%TEMP%\jzq100219.dat
27
%ProgramData%\localNETService\localNETService.exe
27
File Hashes
042b5f70f7211b31877525378d4e96bfe446f8f0e180962446a65c5e8a17eb0808729005569c47f4d36611ac6f04e476e365e17578e6275c71b09b10071629070da7373b6529e881f8de9d33bbe4717b934d3f9eb1159166537ae93f58b02a290e7cccc382e99f10ef64bee8ec7be4c61e5dd2a2b41402e1c824912158e9d0970ec741d2518772fc28534da4da8fbc7581d1cbe14864022412b971ae9fb8febb25782acb55d3cd762558994ac725e31083cb8f10eb483877b3b9c3a178cba927299325258ce603f5cbc78002e165f7b988596b2a626d5e5632c8f7c0b97d9fd02a13a36bc24d110399adde37adcbe1128d66ddf33bdccd3c90e37a5353eb1dcd316803348e02989f019715f85e1f479506a3e74a67744f6dbe589380d8b9ab3d514c836caccb6cf621230443278632465b7b10c4170b8a20109f0fb067444a65572b94765953cd7d0d8a9bc4128b3805327104207af71bccc32f8f0cd580b4ff5c7283a449024ccf30840ebedd11134742695875568e9619cda06b39bec6ec6765d6f8a3358165bdbff21a025d43f182efbe9ea87feead320d5e10eea961fbd265dcb37789486112ef98cd5ce423b36beaa1b7fd1f854348b62d3f76b0f20540694f63471c9fa8220b0312b71a1a268eaf6fc3a9e1c2c2be17c79a000ef0f1ca789b97d71b0ad420bdba65d5da91a82cd3e6a4c5a5f6ed3f2f440e5e3bfed327845f60e36148fd53502baea5c223f8103c1e214fe8fbfaba15c1b57b3ce100c78884ba2c677a3f6280211683ff0c28fd6522044d59f86662fd630ad8311d73538c0a5bdae921786a11fbfe67389a04caffc271fcb67633776cff4fe16d1a47a78d2d5b172a07beee3b67ac16076b89a140f98d189d8ae0873dd110bdc6b286928d34f3d96b6f7eb3f99b865cb449735fe2ec411d44498a5a61e148ffe166a7148e684a3f609ac8e4e47ceabcda4abd75d80f699b313de65fba2e5adedee1f8749161e4bf4085fe4f6256178832565a787e6853b0003dbcbdce3e3777b614cf71990851a27f622a2a4f8d3d818b9383a4551fd29c00ee327dc509fb088bbdc03b9f522963850cbc45dac570eea66a46822c21ea3aed095eb8aa8ec8381eb15bf5See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Win.Dropper.Lydra-6952708-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: internat.exe
42
<HKLM>\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
42
<HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
42
<HKLM>\SOFTWARE\Classes\Wow6432Node\CLSID\{65D5AFFB-D4EF-49AA-GFFG-5DA5E12E300A}
42
<HKCU>\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run
42
<HKLM>\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\RunServices
42
<HKCU>\SOFTWARE\WinRAR\General
42
<HKCU>\SOFTWARE\WinRAR
42
<HKLM>\SOFTWARE\CLASSES\WOW6432NODE\CLSID\{65D5AFFB-D4EF-49AA-GFFG-5DA5E12E300A}
Value Name: ThisEXE
42
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: lsassv
42
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: msrpc
42
<HKCU>\SOFTWARE\WINRAR\GENERAL
Value Name: Sound
42
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE\AUTHORIZEDAPPLICATIONS\LIST
Value Name: c:\windows\servicew.exe
42
<HKLM>\SOFTWARE\Classes\CLSID\{65D5AFFB-D4EF-49AA-GFFG-5DA5E12E300A}
41
<HKU>\Software\Microsoft\Windows\ShellNoRoam\MUICache
41
<HKLM>\SYSTEM\CurrentControlSet\Services\winsys
38
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: winsys
38
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER\RUN
Value Name: winsys
38
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNSERVICES
Value Name: winsys
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSYS
Value Name: DependOnGroup
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSYS
Value Name: DependOnService
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSYS
Value Name: Description
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSYS
Value Name: DisplayName
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSYS
Value Name: Group
38
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINSYS
Value Name: ObjectName
38
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences \Documents and Settings\All Users\Start Menu\Programs\Startup\AdobeGammaLoader.scr
42
%SystemRoot%\mui
42
%ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup\AdobeGammaLoader.scr
42
%SystemRoot%\calc.exe
42
%SystemRoot%\lsassv.exe
42
%SystemRoot%\msrpc.exe
42
%SystemRoot%\mui\rctfd.sys
42
%SystemRoot%\ole32w.dll
42
%SystemRoot%\pool32.dll
42
%SystemRoot%\regedit2.exe
42
%SystemRoot%\servicew.exe
42
%SystemRoot%\setupiwz.dll
42
%SystemRoot%\unrar.dll
42
%SystemRoot%\winsys.exe
38
%SystemRoot%\ieks32.dll
38
%SystemRoot%\viaud.dll
38
%SystemRoot%\woron_scan_1.09_eng.exe
29
%SystemRoot%\smart_scan_eng.exe
13
%SystemRoot%\syswin.exe
4
%SystemRoot%\ikf32.dll
4
%SystemRoot%\iksec.dll
4
File Hashes
0b0700bab86aadc28b8216e487747e1f248b64db255972efd82b8a0b0e9fbaf0134610cf4c7463abd435a7e9e5c3957e1b013d74b73248129f77eda2023bf341149aa87d3b637af6bc98b1b317c88c0faf1aac59d3ae0228f82375dc63668e2716877fdf6baa760ff501d6ffac2d827175debe7d1788bb1d9ebf96359d3ea8ed181fb91a7a3ea5d60862a240abe074d704385a41a4fd2a7c343171452ab207a319ed54738b7eacd638cb8f6c7f41bebce61c596071ff8048c85c2c94ceb9b59d1be2192207e35f4d286154428882707f8fbc947073f87de650e3cae25aac6a531bf0f79aa7076f8e0499646d892b1c883a12b76720ec1ee95583e4f0bd1e2548209c3027ee89df1f9c43caa49f33d2ae796a6e4f75f41fa3d29a6c618236aeb523e8478e532060223d05a4172626d3ce7280d0a50a3c98e55a20f3b67527d5983448fc8f0ba01e5e3f1c2200e09cb8ae7cdd0fb683a078520a8980b7cd8dbfd1385aba59012ba5552914fa5fa5c000d4327631b33eae8173c4c0ed39fdaf86e839b0887601c58b9fa9703611d4a41790db3f5c42eeac30320796005d7cd3149a3ec22bdc7999fdfee532c1f83f3026dd2935b4210325664024c3de0ce60cbd923f927933cb408dc994ce17f3afab04a2b0d6c6f63f13622c92b3466e3502e20f462b020edeec013d02f371189b6e26b868c9058f870de778f3bef56a3dd033ca48c62b14b624255d0887c3c7dcd7d2863b82ece90129b1214abb9a829eeb39a3490204655d5f6a89ee33f2b70efd100edbcc564ea27083cd30ae5bddda319e7e4b2c8b21a1c0350c52740a0e21151dec03786f2a1c2280315dac70815fb6ca23503e790a64d6232628252bb99642e3dbe0da13d6ee748a60ce5ee9bf0b91758d5619dc4d1f452579077dc95c069e9b9a059fc93285f734925133906e1d2bca1b5b2455a6d058652270681d6d7040111e74f468fe771f41588ad8038fe3d598035dfa493f6d6b13c44867ed1e60a90462629383a7330f9fb0ffd1f43c017362e9795f0d8204993cd7c79551555b8b8d37a2d0cbe18ff1d01fc5cb3131c95ee9588267bc6bb334a0f103bc55df5d8a231dc485b76588eb664639cbb16972fef4d6See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Malware
Win.Trojan.Zeroaccess-6952579-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MSASCUI.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\WERFAULT.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\UI0DETECT.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CTFMON.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\WUAUCLT.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\HIJACKTHIS.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MBAM.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MBAMGUI.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MBAMSERVICE.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SBIESVC.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SANDBOXIEWUAU.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SANDBOXIEBITS.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SANDBOXIECRYPTO.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SANDBOXIEDCOMLAUNCH.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SANDBOXIERPCSS.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SBIECTRL.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\COMBOFIX.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\PEV.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\HIDEC.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SWREG.EXE
Value Name: Debugger
28
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\HELPPANE.EXE
Value Name: Debugger
28
<HKCU>\CONTROL PANEL\SOUND
Value Name: Beep
28
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoFile
28
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SR
Value Name: Start
28
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\EXPLORER
Value Name: NoFolderOptions
28
Mutexes Occurrences !PrivacIE!SharedMem!Mutex
28
Local\VERMGMTBlockListFileMutex
28
Local\!BrowserEmulation!SharedMemory!Mutex
28
Local\URLBLOCK_DOWNLOAD_MUTEX
28
Local\URLBLOCK_HASHFILESWITCH_MUTEX
28
UpdatingNewTabPageData
28
{5312EE61-79E3-4A24-BFE1-132B85B23C3A}
28
{66D0969A-1E86-44CF-B4EC-3806DDDA3B5D}
28
!IEFileUpdater!Mutex
28
Local\InternetExplorerDOMStoreQuota
28
©Úü×À»¢Íéõèò©
28
Local\https://www.hugedomains.com/
28
Local\https://tiny.cc/
27
Local\http://mediadiscovery.net/
20
Local\http://widgets.outbrain.com/
13
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1252
3
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1176
3
IsoScope_13c_ConnHashTable<316>_HashTable_Mutex
2
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_316
2
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1604
2
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1876
2
IsoScope_1f0_ConnHashTable<496>_HashTable_Mutex
2
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_496
2
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1932
1
Local\URLBLOCK_FILEMAPSWITCH_MUTEX_1964
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 204[.]79[.]197[.]200
28
172[.]217[.]10[.]4
28
172[.]217[.]12[.]206
28
72[.]21[.]81[.]200
28
216[.]87[.]78[.]25
28
172[.]217[.]3[.]106
27
172[.]217[.]7[.]3
27
23[.]20[.]239[.]12
27
192[.]35[.]177[.]64
27
192[.]241[.]240[.]89
27
72[.]52[.]179[.]175
27
107[.]22[.]223[.]163
27
23[.]10[.]130[.]155
26
172[.]217[.]6[.]194
25
104[.]25[.]37[.]108
25
199[.]59[.]242[.]151
25
172[.]217[.]164[.]132
25
107[.]178[.]240[.]89
25
172[.]217[.]15[.]74
25
96[.]6[.]58[.]4
25
67[.]225[.]218[.]50
25
104[.]25[.]38[.]108
22
173[.]192[.]200[.]70
22
199[.]59[.]242[.]168
21
104[.]28[.]29[.]32
21
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences cdnjs[.]cloudflare[.]com
28
www[.]easycaptchas[.]com
28
secure[.]statcounter[.]com
28
cdn[.]pubguru[.]com
28
fonts[.]gstatic[.]com
27
ib[.]adnxs[.]com
27
www[.]googletagservices[.]com
27
bit[.]ly
27
HDRedirect-LB5-1afb6e2973825a56[.]elb[.]us-east-1[.]amazonaws[.]com
27
static[.]hugedomains[.]com
27
www[.]hugedomains[.]com
27
apps[.]digsigtrust[.]com
27
apps[.]identrust[.]com
27
tiny[.]cc
27
fastlane[.]rubiconproject[.]com
27
m2d[.]m2[.]ai
27
cdn[.]convertcart[.]com
27
tinyurl[.]com
27
directorio-w[.]com
27
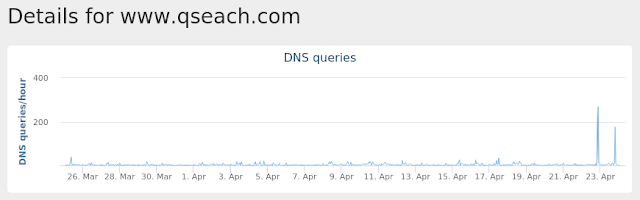
www[.]qseach[.]com
27
www[.]directorio-w[.]com
27
bidder[.]komoona[.]com
27
c[.]statcounter[.]com
26
web[.]hb[.]ad[.]cpe[.]dotomi[.]com
26
securepubads[.]g[.]doubleclick[.]net
25
See JSON for more IOCs
Files and or directories created Occurrences %LOCALAPPDATA%Low\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico
28
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\favicon[2].ico
28
%APPDATA%\Microsoft\Windows\Cookies\A71QDCIP.txt
28
%APPDATA%\Microsoft\Windows\Cookies\VF90XW39.txt
28
%System32%\drivers\etc\hosts
28
%APPDATA%\Microsoft\Windows\Cookies\HW3YF7T7.txt
28
%ProgramFiles(x86)%\Mozilla Firefox\searchplugins\google.xml
28
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\urlblockindex[1].bin
28
%HOMEPATH%\27F6471627473796E696D64614\winlogon.exe
28
%APPDATA%\Microsoft\Windows\Cookies\SISHQLM4.txt
28
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\domain_profile[1].htm
28
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\winlogon.exe
28
%ProgramData%\Microsoft\Windows\Start Menu\Programs\Startup\winlogon.exe
28
%ProgramData%\Microsoft\Windows\Start Menu\Programs\winlogon.exe
28
%ProgramData%\Microsoft\Windows\Start Menu\winlogon.exe
28
%APPDATA%\Microsoft\Windows\Start Menu\Programs\winlogon.exe
28
%APPDATA%\Microsoft\Windows\Start Menu\winlogon.exe
28
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\domain_profile[1].cfm
27
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\6YL4T24G\t[1].gif
27
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\t[1].gif
27
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\domain_profile[1].htm
26
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\1NSKV6K6\domain_profile[1].cfm
26
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\domain_profile[1].htm
26
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\7V3XNPL2\px[1].gif
26
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\SSZWDDXW\t[1].gif
26
See JSON for more IOCs
File Hashes
2e9167886bb73eb0f56b7a64245a5bf4a87b9321cf9c32f2c93c646c32223eef2f6cdf0428403cbefc3d9b4ac5b906b56f202c952eafa49b1a6d4b4394e7ba9d4448b12c3707f70823189f20d310846d2b9de24ca3b76f33e345358d14dfd7c0472fd77b2a880f424513a2b2ec18a1dd6ac8f15f4756787d10818d35c344e8ab558cebedb7814ef92e02b020a444ed6a0dcb23dec761ccd3270548911f646c2b686aa9a0dc49bdd733c78b6ff0f180b2887696365a6304069db8a485913c21de68c892240aee5b55b6b8fb19593b9378fd7f23d42318566d73c4fbc42a77776d80d68a9698e2f598f7c703d78eaa8a500d5f716cb93009d5cc1bacef47f88e2a84aaafc52bd192f0bd17ea8e5dd34318c28a6ac87a84fa3efd629e3f9f3bf0b29994bd60526b01b3631a7b4ec012f50251966a0cb841b7ec583d12a374df24e89abc698de28993cd3f687686e12bca1b185dfb8687c4751b47ce7a265167725a9b45576ccb59e5b083892fe7d6154cd8c3a0795088db2053f770b589f2769108a66292bc2d1c99dfb5e8c870444e603798c923ecba4ac633f88d4430b19731a7aadb0c76ee084384a9acbd3981a5c22e39431a45c82438a8f8b245043b1dc05baec1d3b9323fde4b0d192c7e4b4448d517b180f4776a0cbd266b3c0d843c1214b021e5e867ed34c56aae7007ccdb0965c59d49b621a6aa3f3c4052f69e082b79b05f01500646b2d52b30d146a39d07047311e200a4215afef7c6ff45f1e8279bb156f81c67063ebde12bd89572d4f8fce933e725c2d6b2deab80f767bb5e6fafb322ada9d35b5e884d7c2c63ede85a1e11d1b2ab7d136e0c05b14cdafe8c5423b871a929a4c5bbeed88387296c7270ec20c76f40361ba87e0aa84a63a16c748bbbc346b483d913d44549fcff8e6a240fa3e035bbbd468299d72a7a33b447cb6ebf32e669b25059e41d0f296d183136c796030374a5fc848eb5dcd6b9020283c8c72efd27ec54698b361fae7dceb14bd6dfe8883ffcc29c0d8e25fecd83249ffeca1dbce8a0e3ff901cb022b57267673ee9d1f6f42384189be4eb670c44796e45d0a2e479604e92ece7d75295260f938091a62b807999a993d7c5377a4fbe3ca1See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Doc.Downloader.Powload-6952235-0 Indicators of Compromise Registry Keys Occurrences <HKCR>\INTERFACE\{8BD21D42-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{8BD21D52-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{8BD21D62-EC42-11CE-9E0D-00AA006002F3}
25
<HKCR>\INTERFACE\{7B020EC2-AF6C-11CE-9F46-00AA00574A4F}
25
<HKCR>\INTERFACE\{7B020EC7-AF6C-11CE-9F46-00AA00574A4F}
25
<HKCR>\INTERFACE\{79176FB2-B7F2-11CE-97EF-00AA006D2776}
25
<HKCR>\INTERFACE\{4C5992A5-6926-101B-9992-00000B65C6F9}
25
<HKCR>\INTERFACE\{796ED650-5FE9-11CF-8D68-00AA00BDCE1D}
25
<HKCR>\INTERFACE\{47FF8FE0-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE1-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE2-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE3-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE4-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE5-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE6-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE8-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{47FF8FE9-6198-11CF-8CE8-00AA006CB389}
25
<HKCR>\INTERFACE\{5CEF5613-713D-11CE-80C9-00AA00611080}
25
<HKCR>\INTERFACE\{92E11A03-7358-11CE-80CB-00AA00611080}
25
<HKCR>\INTERFACE\{04598FC9-866C-11CF-AB7C-00AA00C08FCF}
25
<HKCR>\INTERFACE\{7B020EC8-AF6C-11CE-9F46-00AA00574A4F}
25
<HKLM>\SOFTWARE\Classes\Interface\{8BD21D12-EC42-11CE-9E0D-00AA006002F3}
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\sourcebulk
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: Type
25
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: Start
25
Mutexes Occurrences Global\I98B68E3C
25
Global\M98B68E3C
25
Global\Nx534F51BC
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 152[.]168[.]82[.]167
25
197[.]91[.]152[.]93
25
47[.]99[.]85[.]122
25
66[.]228[.]45[.]129
15
77[.]82[.]85[.]35
15
239[.]255[.]255[.]250
1
216[.]98[.]148[.]157
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dudumb[.]com
25
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
25
%HOMEPATH%\778.exe
25
\REGISTRY\MACHINE\SOFTWARE\Classes\Word.Document.8
1
%System32%\en-US\tzres.dll.mui
1
%System32%\WindowsPowerShell\v1.0\FileSystem.format.ps1xml
1
%SystemRoot%\SysWOW64\bVjUjfFnlezvN1Uus.exe
1
%SystemRoot%\SysWOW64\Iv7bzYqWHO4xGd.exe
1
%SystemRoot%\SysWOW64\Kyo1lmFLAsBgZNy.exe
1
%SystemRoot%\SysWOW64\AsiXrqyEtbD.exe
1
%TEMP%\CVRB4E.tmp
1
%SystemRoot%\SysWOW64\4lfjNl8nHPqt1Js4Bp.exe
1
%SystemRoot%\SysWOW64\fVyEM3EWs7XQ.exe
1
%SystemRoot%\SysWOW64\rwzinD3GMw1HRORxO.exe
1
%SystemRoot%\SysWOW64\myqCWvEqggyRaDCYm.exe
1
%SystemRoot%\SysWOW64\QrGtyKE.exe
1
%SystemRoot%\SysWOW64\EWRwGw7IYRd.exe
1
%SystemRoot%\SysWOW64\BDlBrj99pY7wbdknU.exe
1
%SystemRoot%\SysWOW64\ti93nsoZWFJbLoZ.exe
1
%SystemRoot%\SysWOW64\10czIsyY6Qn52PBJ8.exe
1
%SystemRoot%\SysWOW64\gCOkjmOgE39uf7.exe
1
%SystemRoot%\SysWOW64\a9xRIWvuM1dZbNKU.exe
1
%SystemRoot%\SysWOW64\hsCc2.exe
1
%SystemRoot%\splwow64.exe
1
%SystemRoot%\SysWOW64\EFTI4zp.exe
1
%SystemRoot%\SysWOW64\swlZVw2znOToKUOSMk.exe
1
See JSON for more IOCs
File Hashes
01664c310c364946846933f45a9db25326db7133275446e38e7eccd56f2b80b414c53e5330f82bf1449cda84130abcf0b3ffe2ce29d16a6d7a8b3c17601bffea185d2c002d778f0fec20cd7a6cb749d19577b95839be3cb7af13916e6870a7ef1ecfe0e89a380160df4b62d4b56321bfad3624ea07334f4271b9b3a0de323fdf1f2acd076d0c1aaf5832d9c30ca76cd469562fd79625b308714e87e0293790522cdc8b8fa281a4b2ab63a8f8098a71dc05d50dc06858cb0ae701487608bda79f37317c48991a92e9deb17122cc64e572e9dac5402cf89aa47db8866ba9ea93e037f9cc3f495f80e03c1454869205d757959c9f46171ae6cb7ded62bb6a4bc37f3fa5e87f6b8331816fb77091303df6c30a124c8359cdee61127a05353c56196142c76634b3baf9017b152bfd49863669f3aaa5423f084bc4fde730587e07d8fe4832624b2bbc3d9a98ecea0d2e9ae0db57f90d6cc314a7fddc86521edd7bd979500e41605b772679750255bfae4e6c369051ff64ca3aceae7e1d32c859529f1d748968b90d8f84cec298ea1edb0cf037a4eb580b8c0dbcb10f3252f520a3b5a67cbd6f18182bf68d5506a164a42bff14759a2be77b5adc5f35e77a7ba68fbe127d5f2a044fc3fff1aa2053a86da81068c53c12ed8b9ad4b2adf7693a73e134b48284710f69f25d748299231f7764e53fc963049bd46fd0aed36146868d8e3df38f8e289691e3f7a6ad872a72c601d634e825972c9562d8f849bc571026327f6297ec98bb0661fb192eac75f8e184d56dd2ce8395cf1b7420ed2975f372cca267a05e3987b94e0dde5d20f902133a5571ee60ecf7e077e4497be5183bbb472d9ea29afb3beb3244232df4083ba09eac61a60c2f1a23108f60d1205d43a7be59eca791c7c95cb9310ab719abebc47c63424ffaab3ea180ff71ea369f33c1c1061cb0c3ffe7cf0c331ad9a44790ad48c6b57ed7b38d3612aba23e8a02685735531cbf4f44397b89e0103a1422962049db2e6935ee3b89575131baf195aab69c41edc2c3d7e6e279d271edcc78b072b24e0ada5c0f4a83e997a33ed26953bc951f23c5710bc33402f7e096d1518df37b1e43e7a5de4286863f3a5840543e2bae9e9dSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Malware
Win.Ransomware.Cerber-6952131-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: internat.exe
14
<HKCU>\Software\AppDataLow\Software\Microsoft\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
14
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: api-PQEC
14
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: Client
14
<HKCU>\SOFTWARE\APPDATALOW\SOFTWARE\MICROSOFT\D31CC7AF-167C-7D04-B8B7-AA016CDB7EC5
Value Name: {F50EA47E-D053-EF14-82F9-0493D63D7877}
14
Mutexes Occurrences {A7AAF118-DA27-71D5-1CCB-AE35102FC239}
14
Local\{57025AD2-CABB-A1F8-8C7B-9E6580DFB269}
14
Local\{7FD07DA6-D223-0971-D423-264D4807BAD1}
14
Local\{B1443895-5CF6-0B1E-EE75-506F02798413}
14
{8303E239-0653-AD8E-2867-9A31DC8B6EF5}
4
{07C292C9-BA97-D1C3-FC2B-8E95F08FA299}
2
{FB179D42-1E2D-E531-005F-32E93403862D}
2
{6B06C8E1-CEE8-D5D9-30CF-E2D96473361D}
1
{97FA9976-0AD7-E1DA-CCBB-DEA5C01FF2A9}
1
{AFC31B69-429D-B93B-C453-96FD38372A81}
1
{E73AB138-1AFB-B10F-5C0B-EE75506F0279}
1
{C352A3DA-46D9-EDDF-68A7-DA711CCBAE35}
1
{3FA15864-923D-C93F-94E3-E60D08C77A91}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 87[.]106[.]18[.]141
14
Domain Names contacted by malware. Does not indicate maliciousness Occurrences groupcreatedt[.]at
14
Files and or directories created Occurrences %APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\prefs.js
14
%APPDATA%\Microsoft\Dmlogpui
14
%APPDATA%\Microsoft\Dmlogpui\datat3hc.exe
14
%TEMP%\5932\2C99.bat
1
%TEMP%\65B0\B2D8.bat
1
%TEMP%\C924
1
%TEMP%\C924\E492.tmp
1
%TEMP%\C924\E492.bat
1
\TEMP\670E9F~1.EXE
1
%TEMP%\C1A4
1
%TEMP%\C1A4\60D2.tmp
1
%TEMP%\C1A4\60D2.bat
1
\TEMP\708D16~1.EXE
1
%TEMP%\F6A8
1
%TEMP%\F6A8\30.bat
1
\TEMP\AE71FB~1.EXE
1
%TEMP%\752A
1
%TEMP%\752A\BA95.tmp
1
%TEMP%\752A\BA95.bat
1
\TEMP\7634AC~1.EXE
1
%TEMP%\5FB8
1
%TEMP%\5FB8\AFDC.tmp
1
%TEMP%\5FB8\AFDC.bat
1
\TEMP\B89CC6~1.EXE
1
%TEMP%\1724
1
See JSON for more IOCs
File Hashes
55c79a0a7d5bc93ae1e0edcbd6c838fa361e67d404f8f38089939a01d5cc27c5670e9fc88468a253b00e9ca9783baccebcc6effa0c5902026b649da6b72f3249708d163c05a5986c1691f48bbff37ccfda13cda6704d6a1a9ac0e295dc6739ae7634ace88199348cc6bff675c216b9d26c13803d59bc112eae19188cd535a56577517b420d96ac130c586d567b3ce4f12ef34918e268339758cd663a54296806ae71fb978b5abbff24740db3a7e083392f3301e46ad2b904064e9f48825bc52eb36d27dd1a266aa0e29131e78835a4b00ff337bc4ccd72af1cc16af93d252cc7b89cc647d71b28c7bd382299e7b574ad6dfd7ecbcf6dae011513874c5a5ddab6ba0bbae843fd8675f57e7cf62b1f48781de38c25adb33e64083cd1af1b2b2f69c7f6fb53efdb5080fdb1fa29c84c66eb7e63369a1525dc84586eaee5ec942589c8e133e78982e35707b339263fdbb89e41c8b02e9eb80a89255c982fe07374bacd16db51872581108c2e9beb6a2ba93153c67f85db299f10b4fe11f6e7a8a19dd9891ebd33d5b507598c11c6855c5dae0c10e4c8a41069020ca9c786960b30d4ee85ff6ee5b001904f3ba1be01d3e7f67e7fdcf222a39f5a1e451be999b8e18c Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Packed.Tofsee-6952124-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\System\CurrentControlSet\Services\NapAgent\Shas
17
<HKLM>\System\CurrentControlSet\Services\NapAgent\Qecs
17
<HKLM>\System\CurrentControlSet\Services\NapAgent\LocalConfig
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\Enroll\HcsGroups
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\NAPAGENT\LOCALCONFIG\UI
17
<HKU>\.DEFAULT\Control Panel\Buses
17
<HKU>\Software\Microsoft\Windows\ShellNoRoam\MUICache
17
<HKU>\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config0
17
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config1
17
<HKU>\Control Panel\Buses
17
<HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
16
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config2
16
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\yrflksyn
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\yrflksyn
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: Type
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: Start
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: ErrorControl
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: DisplayName
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: WOW64
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: ObjectName
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: Description
6
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\YRFLKSYN
Value Name: ImagePath
6
<HKLM>\SYSTEM\ControlSet001\Services\ylrseput
3
Mutexes Occurrences Global\3a886eb8-fe40-4d0a-b78b-9e0bcb683fb7
17
liqbftsowkinegql
17
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 69[.]55[.]5[.]250
17
144[.]76[.]199[.]43
17
98[.]136[.]96[.]73
17
98[.]136[.]101[.]116
17
176[.]111[.]49[.]43
17
46[.]4[.]52[.]109
17
144[.]76[.]199[.]2
17
85[.]25[.]119[.]25
17
117[.]53[.]114[.]15
17
67[.]195[.]228[.]87
17
66[.]218[.]85[.]151
17
64[.]98[.]36[.]4
17
43[.]231[.]4[.]7
17
98[.]137[.]157[.]43
17
52[.]73[.]137[.]222
17
167[.]206[.]4[.]79
17
34[.]212[.]80[.]54
17
18[.]209[.]118[.]139
17
172[.]217[.]164[.]132
17
94[.]23[.]27[.]38
17
65[.]20[.]0[.]49
16
35[.]162[.]106[.]154
16
167[.]206[.]4[.]77
16
74[.]208[.]5[.]4
16
208[.]89[.]132[.]27
16
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences smtp[.]secureserver[.]net
17
mx-aol[.]mail[.]gm0[.]yahoodns[.]net
17
mx[.]lycos[.]com[.]cust[.]b[.]hostedemail[.]com
17
hotmail-com[.]olc[.]protection[.]outlook[.]com
17
cxr[.]mx[.]a[.]cloudfilter[.]net
17
aol[.]com
17
mx[.]optimum[.]net
17
comcast[.]net
17
mail[.]com
17
ntlworld[.]com
17
naver[.]com
17
earthlink[.]net
17
cox[.]net
17
optonline[.]net
17
netzero[.]com
17
gmx[.]net
17
lycos[.]com
17
netscape[.]net
17
doctor[.]com
17
mx[.]bt[.]lon5[.]cpcloud[.]co[.]uk
16
btinternet[.]com
16
mx0[.]charter[.]net
16
tiscalinet[.]it
16
mx0[.]gmx[.]com
16
peoplepc[.]com
16
See JSON for more IOCs
Files and or directories created Occurrences \net\NtControlPipe10
17
%HOMEPATH%
17
%SystemRoot%\SysWOW64\config\systemprofile:.repos
17
%SystemRoot%\SysWOW64\config\systemprofile
17
%SystemRoot%\SysWOW64\yrflksyn
6
%SystemRoot%\SysWOW64\IPHLPAPI.DLL
3
%TEMP%\wdqqtewr.exe
1
%TEMP%\nmyuzjtg.exe
1
%TEMP%\vmfipcon.exe
1
%TEMP%\awqwcewn.exe
1
%TEMP%\vrlrxzri.exe
1
%TEMP%\euatucsb.exe
1
%TEMP%\mmlrcqxa.exe
1
%TEMP%\mkrnmvtk.exe
1
%TEMP%\cahdclja.exe
1
%TEMP%\nuhhkvni.exe
1
%TEMP%\vlrkltjs.exe
1
%System32%\huabnydc\younowmv.exe (copy)
1
%TEMP%\mreehgwb.exe
1
%TEMP%\wwvbmahk.exe
1
%TEMP%\lkwsxhre.exe
1
%TEMP%\tfgavrsp.exe
1
%TEMP%\sefzuqro.exe
1
%TEMP%\amnhcyzw.exe
1
%System32%\sflmyjon\amnhcyzw.exe (copy)
1
See JSON for more IOCs
File Hashes
0cc2e91e71b1e5fef8599413fbc7c8b3fa3a4cdaa92452304bdbb38cdb6d116115bf8fc46b91cb25730330dfbefcae2cb478e7ecbc18ac15d13b7b8eec01b6971d045908a196354bf1c0f0da5c4eeff5e7aaa36a1b5ee7f21764a7133e6ec4c832a5d89a77130e01c19a58a0d3ff639d02c05ef2442f4e6b55a2e2b0a886926c32bce81459bff859b7adff1113f6bda122a804a25e44c0d38951ee3ed39a155733e921f8c006374a78ab957ac1ce13183d65b4c633d2c7538c585d902f90ff443d97b118c14ce36766873e178c9ef124936767dec5312806213dd295ed0d54485c7ef91e7e96515dd59d0a252eca92d0d93a1bd9fa914eaf8c71933fcf7c80777509fa7e6294d05e0f25f96ea99fb9ea8b791a08128580ae86dda44fcb6c6d5577cd1c22bb9099c666721a639bb980c1a5cde86cbc6323bc221f9184f6d9c09277da1a87f241047d70d54b5a3e85e8bab4e349b32c58818766b9965c9fd40949a69d1518f15d8d435010727797a40d687be8069de1edc522facb0669ffda324ecfb237792af9dea590b59278d9ec73c301309d961cb78f15651c7757782c0671d20e573316508252a71fe9b8c7f32fbbb9daf110a9e7aa13188f713509aedaaada359fbb459923a0e385cbd80d5d7c7505d8596a32f777e280b5784c4ba9a382df134bd359722960fdcd67d79900ff8350616e73f25ab1204e7a7a0232cdafecf267501b0cd9862743e760e2c0686968019a68bf1a69843cea19b14c51773440 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Emotet-6947486-0 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: ProxyEnable
40
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: ProxyServer
40
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: ProxyOverride
40
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: AutoConfigURL
40
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS
Value Name: AutoDetect
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\sourcebulk
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: Type
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: Start
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: ErrorControl
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: ImagePath
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: DisplayName
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: WOW64
40
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SOURCEBULK
Value Name: ObjectName
40
<HKU>\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
39
<HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
39
<HKLM>\SOFTWARE\Microsoft\ESENT\Process\guiddefribbon\DEBUG
39
<HKU>\.DEFAULT\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\{E54C0DDD-6FAB-4796-8BBE-EE37AF7CD25A}\9c-aa-fb-e9-56-c8
2
Mutexes Occurrences Global\I98B68E3C
40
Global\M98B68E3C
40
\BaseNamedObjects\Global\M3C28B0E4
39
\BaseNamedObjects\Global\I3C28B0E4
39
Global\Nx534F51BC
2
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 152[.]168[.]82[.]167
16
189[.]166[.]20[.]113
16
103[.]11[.]83[.]52
16
197[.]91[.]152[.]93
15
77[.]82[.]85[.]35
11
66[.]228[.]45[.]129
10
216[.]98[.]148[.]156
10
177[.]231[.]157[.]189
6
65[.]49[.]60[.]163
4
201[.]248[.]5[.]197
4
82[.]0[.]19[.]40
4
165[.]255[.]52[.]192
4
31[.]172[.]86[.]183
3
45[.]33[.]35[.]103
3
181[.]37[.]126[.]2
3
239[.]255[.]255[.]250
2
209[.]85[.]144[.]109
2
74[.]6[.]141[.]43
2
81[.]169[.]145[.]103
2
104[.]236[.]185[.]25
2
181[.]30[.]126[.]66
2
179[.]62[.]249[.]189
2
204[.]232[.]250[.]252
1
81[.]19[.]78[.]83
1
216[.]128[.]11[.]5
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences smtpout[.]secureserver[.]net
2
imap[.]strato[.]de
2
SMTP[.]AMAZON[.]COM
1
mail[.]strato[.]de
1
mail[.]gmx[.]a
1
MAIL[.]CLOVER[.]COM
1
mail[.]hotmail[.]de
1
mail[.]fsfsc[.]org
1
mail[.]pearl[.]ch
1
mail[.]hub[.]afsinc[.]org
1
smtp[.]gatehousesupplies[.]com
1
smtp[.]bonuscard[.]ch
1
smtp[.]cranespotters[.]com
1
mail[.]securemail[.]us[.]cibc[.]com
1
smtp[.]employmentsolutionsinc[.]org
1
mail[.]tecnoparaguay[.]com[.]py
1
www[.]chetgreen[.]com
1
smtp[.]account[.]zopim[.]com
1
smtp[.]prodxbm[.]co
1
smtp[.]creditkarma[.]com
1
smtp[.]my[.]yotpo[.]com
1
SMTP[.]PERX[.]COM
1
smtp[.]bobjohnson[.]com
1
smtp[.]facturacioncapufe[.]com[.]mx
1
smtp[.]app[.]intercom[.]io
1
See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat
40
%System32%\guiddefribbon.exe (copy)
3
%SystemRoot%\SysWOW64\UtHbYIvdhlNvu.exe
1
%SystemRoot%\SysWOW64\R597iayBjMdh.exe
1
%SystemRoot%\SysWOW64\C7eHkb20PeU6wpDtjp.exe
1
%SystemRoot%\SysWOW64\1MEitC9prK.exe
1
%SystemRoot%\SysWOW64\kmnu.exe
1
%SystemRoot%\SysWOW64\4I7gXzdy4.exe
1
%SystemRoot%\SysWOW64\5x2P.exe
1
%System32%\HwVezokkuv.exe
1
%SystemRoot%\SysWOW64\ISUH5rlS.exe
1
%SystemRoot%\SysWOW64\xFkV4xOuG.exe
1
%SystemRoot%\SysWOW64\7tooAA2H.exe
1
%SystemRoot%\SysWOW64\dqhwpEfDiqdYk3.exe
1
%SystemRoot%\SysWOW64\98SvoQAlyGHCi.exe
1
%SystemRoot%\SysWOW64\Y9t7.exe
1
%SystemRoot%\SysWOW64\OEkk.exe
1
%SystemRoot%\SysWOW64\QEeaZTtWugEn.exe
1
%SystemRoot%\SysWOW64\faEA7KV70hn5.exe
1
%System32%\hLikoqY.exe
1
%SystemRoot%\SysWOW64\oURffFdtgFONll.exe
1
%SystemRoot%\SysWOW64\b1zR.exe
1
%SystemRoot%\SysWOW64\bEjEWEYxmjgCJVecQcp.exe
1
%SystemRoot%\SysWOW64\yVYv57xuqKB.exe
1
%SystemRoot%\SysWOW64\oglx98jdm6.exe
1
See JSON for more IOCs
File Hashes
0106fad7a1ceb64a7d2ebed424ce86d979ac976cb352326c0fca9c7d0ac5330f0123e3c82d1b40e5b1ec1cb62a30317cb209371dc8fe546f10b96c6113e372290911c843ef0b50a6b7359384d774350c43ea81970e47b6390782a3b59619df230b5980e79cb0b4565db500cdb5b15970624aa8f3fce0bc14a13a097fc9c098ca0fe4721f05bcae958a1e294f92832144acd17791a850507bd98572347968eb6e14e5b08440e75c48bd1ff1486c8b36f32fb0cd4d21dbc138861a0b9af90aba7f1cd3db53176d88f4b7244429ef03ee120373c066335a8a5b81f94e25971886361cda16c8d2e935d3ed762d5c7d18c945ebcfc183898ac5b87846dca084e043cf1ec9145cc88f7e619398955d6377ea4a6aa2f5fc8d53b87a467468d284352d6122d4075bf5828ede0c20dbea9023775ebbffb6e867272945a6a69697ea015c8c2430252f3c13ab866847db4905ff53380375d818085358a6f2d158f5ca6f984725806bac5ca5b7b3dc6f1cdcbc4d72ade84828ae4173a858c3e9fe028d51b7e9270696e681aae3f24c7a3886f75952fd82c2bc94374c7fa1e72c5ae1583efcc02d979f92140e9b7ad385cfe47c59e960ef5df19bff9388313908a14464bc00643286340a92b48cf2a64c066f4cec1b078d9c23df987dd9aa07f249fffc5a9cbf377ca271dd3000fe310674488c93822601be7434325661f4158e8e64e83ab2473e77f7b1c2a160ebd1f6bda9235c9ae43f057cba38f6ef77f50df7dd1bd6d229448d67c96c008988d24046abb6a7e736db585c79b83c1e831023649133d83dad45ee3965183c5fecff0268fa7480aad3f4b0364b3e63fbc4259a1669f1cc48f8478968aeea42221e0c760a811af1560eeaa6489b77cdf69b4ae3763c59e60be048900a85a1a4afcf216ea9912176bb20edab059d1bb27d02caa6fbbcc060d35e4937ac330845c1504e65a3655050ffa5a8cfc3602298ecef627ca8d4114631fe5ca10a11eb88b1c5e38e0359419fe8d39a321571e89268a578d2a0e272004caf61ffe36301e722b85088cfceb5d5a703e57eff907119ef305dc92da45c254aaf65eb33dbb0f1a4e78ffdcc5dbed725ac929c7c917923544af329226ddecf0f14See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Malware.Mikey-6953803-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\Software\Wow6432Node\Microsoft\Tracing\RASAPI32
15
<HKLM>\Software\Wow6432Node\Microsoft\Tracing\RASMANCS
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: EnableFileTracing
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: EnableConsoleTracing
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: FileTracingMask
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: ConsoleTracingMask
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: MaxFileSize
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASAPI32
Value Name: FileDirectory
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: EnableFileTracing
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: EnableConsoleTracing
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: FileTracingMask
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: ConsoleTracingMask
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: MaxFileSize
15
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\TRACING\RASMANCS
Value Name: FileDirectory
15
<HKLM>\System\CurrentControlSet\Control\SecurityProviders\Schannel
2
Mutexes Occurrences DSKQUOTA_SIDCACHE_MUTEX
14
.NET CLR Data_Perf_Library_Lock_PID_378
6
.NET CLR Networking 4.0.0.0_Perf_Library_Lock_PID_378
6
.NET CLR Networking_Perf_Library_Lock_PID_378
6
.NET Data Provider for Oracle_Perf_Library_Lock_PID_378
6
.NET Data Provider for SqlServer_Perf_Library_Lock_PID_378
6
.NET Memory Cache 4.0_Perf_Library_Lock_PID_378
6
.NETFramework_Perf_Library_Lock_PID_378
6
ASP.NET_1.1.4322_Perf_Library_Lock_PID_378
6
ASP.NET_4.0.30319_Perf_Library_Lock_PID_378
6
ASP.NET_Perf_Library_Lock_PID_378
6
BITS_Perf_Library_Lock_PID_378
6
ESENT_Perf_Library_Lock_PID_378
6
Lsa_Perf_Library_Lock_PID_378
6
MSDTC Bridge 3.0.0.0_Perf_Library_Lock_PID_378
6
MSDTC Bridge 4.0.0.0_Perf_Library_Lock_PID_378
6
MSDTC_Perf_Library_Lock_PID_378
6
Outlook_Perf_Library_Lock_PID_378
6
PerfDisk_Perf_Library_Lock_PID_378
6
PerfNet_Perf_Library_Lock_PID_378
6
PerfOS_Perf_Library_Lock_PID_378
6
PerfProc_Perf_Library_Lock_PID_378
6
RemoteAccess_Perf_Library_Lock_PID_378
6
SMSvcHost 3.0.0.0_Perf_Library_Lock_PID_378
6
SMSvcHost 4.0.0.0_Perf_Library_Lock_PID_378
6
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 64[.]188[.]12[.]182
3
185[.]212[.]130[.]14
2
185[.]212[.]129[.]184
2
46[.]249[.]59[.]122
2
185[.]225[.]69[.]101
2
52[.]36[.]131[.]229
1
54[.]248[.]125[.]247
1
104[.]18[.]39[.]18
1
103[.]11[.]102[.]48
1
104[.]28[.]16[.]149
1
202[.]181[.]185[.]162
1
43[.]241[.]73[.]221
1
202[.]181[.]196[.]26
1
202[.]155[.]223[.]18
1
103[.]13[.]50[.]180
1
54[.]183[.]102[.]22
1
116[.]251[.]204[.]136
1
206[.]218[.]248[.]173
1
203[.]185[.]61[.]196
1
101[.]78[.]151[.]172
1
192[.]185[.]5[.]69
1
103[.]13[.]50[.]28
1
115[.]160[.]155[.]94
1
118[.]143[.]28[.]56
1
103[.]13[.]50[.]62
1
See JSON for more IOCs
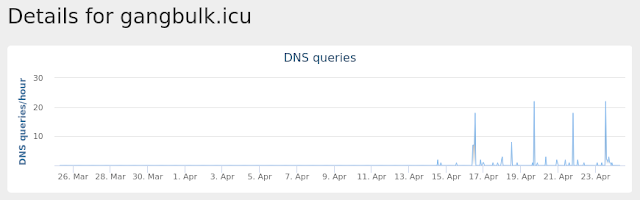
Domain Names contacted by malware. Does not indicate maliciousness Occurrences gangbulk[.]icu
2
striblingm[.]pw
2
SHOP[.]HPINH[.]HK
1
ajqqn[.]hk
1
SHOP[.]HPC[.]HK
1
SHOP[.]HYHEB[.]HK
1
ALODRINK[.]HK
1
SHOP[.]ICAN[.]HK
1
ALIVECOR[.]HK
1
SHOP[.]IAN[.]COM[.]HK
1
shop[.]imylv[.]hk
1
shop[.]ina[.]hk
1
SHOP[.]HY[.]COM[.]HK
1
SHOP[.]ICXLB[.]HK
1
SHOP[.]HOTFROG[.]HK
1
SHOP[.]HYY[.]COM[.]HK
1
shop[.]icfp[.]hk
1
SHOP[.]HYPOXI[.]HK
1
shop[.]htv[.]hk
1
AIR[.]HK
1
SHOP[.]IHK[.]HK
1
shop[.]imore[.]hk
1
SHOP[.]HUGOMAX[.]HK
1
shop[.]hps[.]com[.]hk
1
shop[.]hoops[.]hk
1
See JSON for more IOCs
Files and or directories created Occurrences %APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\cookies.sqlite.bak
10
%APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\places.sqlite.bak
10
\??\scsi#disk&ven_red_hat&prod_virtio#4&2556063a&0&000000#{53f56307-b6bf-11d0-94f2-00a0c91efb8b}
1
%TEMP%\tmpA4A.tmp
1
%TEMP%\tmp2BCD.tmp
1
%TEMP%\4a5beb4e303c4a1a9bcd3624dfec7cbe.exe
1
%TEMP%\tmp4167.tmp
1
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\svchostsw.exe
1
%TEMP%\4a5beb4e303c4a1a9bcd3624dfec7cbe.exe.pid
1
%TEMP%\s.bat
1
%TEMP%\tmpCAF3.tmp
1
%TEMP%\tmpB734.tmp
1
%TEMP%\tmpB63A.tmp
1
%TEMP%\tmp77F3.tmp
1
%TEMP%\tmp742C.tmp
1
%TEMP%\tmp6695.tmp
1
%TEMP%\tmp717E.tmp
1
File Hashes
0ee1dc48bdc775152554357cbb9190834a58a5ccbc01e27d20f2cf00642112060ffa3428f95f2a5c79a169976d3c5d58fa885cc05265c41fa4dcf4e33be17a121ee4c1201f038a48a854fd993455142b15acbf44b41a8820af4790f17c31fba545945d97bf9f1cb63b1b7a74629bb90567933a981d2cc77f4dc46018c6f8c169471f646bc59743f27f1bb08ef688a699c3ff268eeab403cea8ec7467f303c2f34725b43862585b4e78f06ef7209a32434dcfe809986a19cb9b89bcb673a6a55549065e33bbdf2b25f4cdd1a8994df53135a9b41b725bd94958682325fb8c237a58fb3bc46e231b9ad07f5f8210a2acf1d225c25e287eee73553ae280ac9e89d96f79069e751211f3077e90bd4e20c7116f8c3c9c41fa1ce7eacbd7710fdecf0e96667406cc9e8bb5e9da9e418a4b4196900364cc100d965b5d2714c62eb5e4029ac94b8404ee4300330c56257c66f77662904a2dc7f732125f36365c4a7881299e87a651befb171f0145718bc52d4d8b1a40f420cbb8d66d3e8b60e4377fa8c7be140dfc59df6e21eb3b799cfe6511b9b8c5d010be0079b5f64a2b1dc3ab4fcbf1e262b02e2b357f56225184539e2a3c35623b15397a85f343a368c5999dbd5df7f5d6e71a69332960e2025790db65c9bd29037157930a599c28969645bec5c9 Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Madshi injection detected (3400)Kovter injection detected (2256)PowerShell file-less infection detected (1079)Process hollowing detected (503)Gamarue malware detected (190)Atom Bombing code injection technique detected (107)Suspicious PowerShell execution detected (100)Dealply adware detected (87)Excessively long PowerShell command detected (85)Trickbot malware detected (75)