Today, Talos is publishing a glimpse into the most prevalent threats we've observed between May 03 and May 10. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org, or ClamAV.net.here that includes the complete list of file hashes, as well as all other IOCs from this post. As always, please remember that all IOCs contained in this document are indicators, and one single IOC does not indicated maliciousness.
The most prevalent threats highlighted in this roundup are:
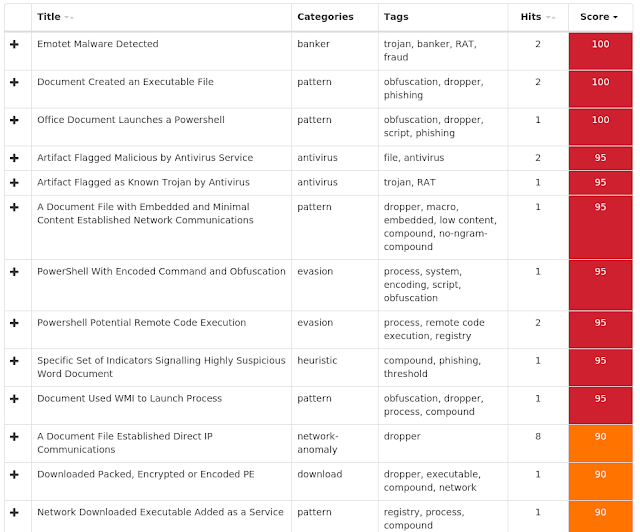
Win.Trojan.Tofsee-6965613-0 Win.Trojan.Zeroaccess-6965107-0 Win.Dropper.Emotet-6964837-0 Win.Trojan.Darkkomet-6964750-0 Win.Malware.Kryptik-6964485-1 Win.Packed.Kovter-6964099-0 Win.Malware.Python-6964012-0 Win.Ransomware.Cerber-6963958-0 Doc.Downloader.Powload-6959926-0 Win.Dropper.Qakbot-6962757-0 Threats Win.Trojan.Tofsee-6965613-0 Indicators of Compromise Registry Keys Occurrences <HKU>\.DEFAULT\Control Panel\Buses
24
<HKU>\.DEFAULT\CONTROL PANEL\BUSES
Value Name: Config3
24
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\fymsrzfu
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\fymsrzfu
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: Type
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: Start
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: ErrorControl
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: DisplayName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: WOW64
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: ObjectName
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\FYMSRZFU
Value Name: Description
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\TMAGFNTI
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\TMAGFNTI
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\TMAGFNTI
Value Name: Description
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\jcqwvdjy
2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS DEFENDER\EXCLUSIONS\PATHS
Value Name: C:\Windows\SysWOW64\zsgmltzo
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\zsgmltzo
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: Type
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: Start
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: ErrorControl
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: DisplayName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: WOW64
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: ObjectName
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\ZSGMLTZO
Value Name: Description
2
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\jcqwvdjy
2
Mutexes Occurrences \BaseNamedObjects\ServiceEntryPointThread
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 239[.]255[.]255[.]250
24
69[.]55[.]5[.]250
24
46[.]4[.]52[.]109
24
96[.]114[.]157[.]80
24
176[.]111[.]49[.]43
24
85[.]25[.]119[.]25
24
144[.]76[.]199[.]2
24
144[.]76[.]199[.]43
24
212[.]227[.]15[.]9
24
43[.]231[.]4[.]7
24
74[.]208[.]5[.]20
24
192[.]0[.]47[.]59
24
207[.]69[.]189[.]229
24
94[.]23[.]27[.]38
24
64[.]136[.]44[.]37
23
172[.]217[.]10[.]228
23
47[.]43[.]18[.]9
23
64[.]98[.]36[.]4
22
212[.]54[.]56[.]11
22
65[.]20[.]0[.]49
20
208[.]89[.]132[.]27
19
117[.]53[.]114[.]15
15
74[.]208[.]5[.]4
15
125[.]209[.]238[.]100
15
213[.]33[.]98[.]149
14
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences 250[.]5[.]55[.]69[.]dnsbl[.]sorbs[.]net
24
mx00[.]emig[.]gmx[.]net
24
mx1[.]comcast[.]net
24
whois[.]iana[.]org
24
250[.]5[.]55[.]69[.]bl[.]spamcop[.]net
24
verizon[.]net
24
comcast[.]net
24
whois[.]arin[.]net
24
mx-aol[.]mail[.]gm0[.]yahoodns[.]net
24
250[.]5[.]55[.]69[.]sbl-xbl[.]spamhaus[.]org
24
hotmail-com[.]olc[.]protection[.]outlook[.]com
24
cxr[.]mx[.]a[.]cloudfilter[.]net
24
microsoft-com[.]mail[.]protection[.]outlook[.]com
24
cox[.]net
24
mx00[.]mail[.]com
24
earthlink[.]net
24
mx[.]optimum[.]net
24
optonline[.]net
24
mx1[.]mail[.]icloud[.]com
24
mx6[.]earthlink[.]net
24
victoria1999[.]hotrusgirls[.]cn
24
irina1993[.]hotlovers[.]cn
24
hot-beauty[.]cn
24
hotladies[.]cn
24
mx[.]dca[.]untd[.]com
23
See JSON for more IOCs
Files and or directories created Occurrences %SystemRoot%\SysWOW64\config\systemprofile:.repos
24
%SystemRoot%\SysWOW64\config\systemprofile
24
%SystemRoot%\SysWOW64\IPHLPAPI.DLL
10
%SystemRoot%\SysWOW64\fymsrzfu
3
%SystemRoot%\SysWOW64\winnsi.dll
2
%SystemRoot%\SysWOW64\kdrxwekz
2
%SystemRoot%\SysWOW64\nguazhnc
2
%SystemRoot%\SysWOW64\tmagfnti
2
%SystemRoot%\SysWOW64\zsgmltzo
2
%SystemRoot%\SysWOW64\jcqwvdjy
2
%SystemRoot%\SysWOW64\xqekjrxm
2
%TEMP%\chuuxwmr.exe
2
%TEMP%\tpjpvxpg.exe
2
%System32%\mzfgsdih\tpjpvxpg.exe (copy)
2
%TEMP%\nnmsdryb.exe
1
%TEMP%\vqxutqmn.exe
1
%TEMP%\nmyuzjtg.exe
1
%TEMP%\dtzstbra.exe
1
%TEMP%\tvqhyszs.exe
1
%TEMP%\gidulfmf.exe
1
%TEMP%\qtbbzxbk.exe
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\04fa61ce-e4d7-48c8-9def-427199d4e004
1
%TEMP%\vyggecgp.exe
1
%TEMP%\hcjgfcyz.exe
1
%TEMP%\omtpoxvm.exe
1
See JSON for more IOCs
File Hashes
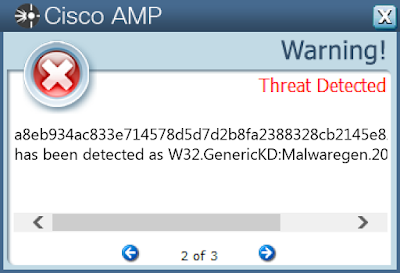
0647fc954ed93c7ea544d83e63a40d502f5fffd8a13f30017a73b67e9a45f1b206cd974d945d25823b35d71c42c63223e70e3117e457e93dee236b32767bd7ec0780495fcad283f3b4d0a8c67ab1f899901a411609e5d418c32d63ea341ab02510d8ca95e213491b05ec904bb8632212e22886d66c45525c104678dc80f670ae125c11dec65eb1649338f5ed9442a65f79a0bcfd386e7db297de44ac7674c0b6243c7f05dc3569c907f03ed8a84d215ff9aa72c83cf3a2204d60e82c66d9aaff2db74b28c8d6fb6cd5dc708a4f63b5f0552edfdef708c2f86ea3a40361e963fd3a9fc763818d743f0b87fffc92d2fd29f6e76f182142a43a6b65c9d12dd3efd43f057b371908761ce99846fe561f0c86376ee18ad0124fd8e848d7f2862e8c0543726985501f447b624194119724d9bf9673a6ec4a9b4d4367d8157569f5dc7f456d4a6d6fbdc25b6c9cafde2af81b6023293e564ddd6473e42f8e420f1fcdd54623e1ce31a8671e59640e83fc545a5f19e167c31cfc6e8d097864c7a4c27859539975f3e33f6b41f3038ed1101633ce5635004bce96ca7764c19a79fb4f83ca5a0f61ab9e096aa16c514f37f60853a708b3eed62dfe8c14643dcc2652141d9661baf3c68654787eab765e7361c07270cac1b7041a07062dff7485aa860fc4b563f7598a21986a406d2a1ac946184140a80558bc7598bebabfcff82214895d75658a040596a2b67e36bd8af81037fefd039eae1bcf63b99928f3b5125e414019751ac2eb414eba0c3f93245c865f2162e328c461c5c844271ffb299df5d1e4df79c2cfd759cc6d1727c7f7015e40333900bda4571e91d18899b98025c0480b947f5b069015e694544a2a693ddc7815c82c9ac6ec0d523ae9ed06d77b78965be482fbb918e0d47f7d9992cd3c5479ee1468d608d1e176f7570994e99ffc66e6b0858f2612c45ad1bb0b986f74274f61224b827912f4e1a80f9121cad40edabacf8ac67c280615873b5aec89d5bd5838d2a23552e7c47511a99b64799d28d659ff8ad48911e8594b3530022ae45fbe12e40438c71cca38d2a7e85a8d3efd22018093cb0db5f5aecff9574b756b557280b61d557724591817013c016a3a68096be5See JSON for more IOCs Coverage
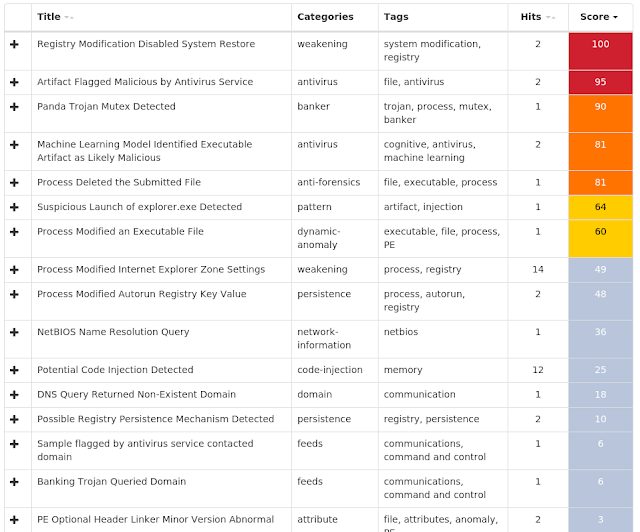
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Trojan.Zeroaccess-6965107-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: DeleteFlag
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: Start
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
17
<HKLM>\SYSTEM\CurrentControlSet\Services\SharedAccess\Epoch
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: Start
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: DeleteFlag
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: DeleteFlag
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: DeleteFlag
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\Epoch
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\BROWSER
Value Name: Start
17
<HKCU>\Software\Classes\clsid
17
<HKCR>\CLSID\{fbeb8a05-beee-4442-804e-409d6c4515e9}
17
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\InprocServer32
17
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32
Value Name: ThreadingModel
17
<HKCR>\CLSID\{FBEB8A05-BEEE-4442-804E-409D6C4515E9}\INPROCSERVER32
17
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
17
<HKLM>\SOFTWARE\CLASSES\CLSID\{5839FCA9-774D-42A1-ACDA-D6A79037F57F}\INPROCSERVER32
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Type
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: ErrorControl
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: Type
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS
Value Name: ErrorControl
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: Type
17
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\IPHLPSVC
Value Name: ErrorControl
17
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 64[.]210[.]151[.]32
17
77[.]52[.]81[.]243
17
72[.]47[.]100[.]38
17
89[.]228[.]63[.]37
17
65[.]30[.]151[.]36
17
98[.]247[.]217[.]244
17
173[.]217[.]71[.]246
17
101[.]63[.]15[.]35
17
209[.]195[.]111[.]246
17
87[.]218[.]204[.]33
17
115[.]240[.]123[.]32
17
114[.]75[.]62[.]32
17
96[.]26[.]208[.]30
17
70[.]64[.]83[.]30
17
82[.]22[.]40[.]30
17
75[.]224[.]240[.]29
17
84[.]228[.]113[.]26
17
119[.]149[.]38[.]25
17
212[.]72[.]112[.]24
17
46[.]194[.]56[.]24
17
84[.]231[.]16[.]23
17
72[.]192[.]54[.]21
17
117[.]217[.]106[.]247
17
91[.]67[.]192[.]19
17
77[.]11[.]149[.]19
17
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences promos[.]fling[.]com
17
Files and or directories created Occurrences @
17
L
17
U
17
\$Recycle.Bin\S-1-5-18
17
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f
17
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f
17
n
17
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\@
17
\$Recycle.Bin\S-1-5-18\$0f210b532df043a6b654d5b43088f74f\n
17
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\@
17
\$Recycle.Bin\S-1-5-21-2580483871-590521980-3826313501-500\$0f210b532df043a6b654d5b43088f74f\n
17
%System32%\LogFiles\Scm\e22a8667-f75b-4ba9-ba46-067ed4429de8
17
\RECYCLER\S-1-5-18\$ad714f5b8798518b3ccb73fd900fd2ba\@
15
\RECYCLER\S-1-5-18\$ad714f5b8798518b3ccb73fd900fd2ba\n
15
\RECYCLER\S-1-5-21-1258710499-2222286471-4214075941-500\$ad714f5b8798518b3ccb73fd900fd2ba\@
15
\RECYCLER\S-1-5-21-1258710499-2222286471-4214075941-500\$ad714f5b8798518b3ccb73fd900fd2ba\n
15
File Hashes
07c405ee534570f541b59cdaa0f96ff7504589dd26b9e2c6f71e5b89b70fe77f105a3a1a379be2fc1efe05678726a2ff34183a3f6453af7fe11d3c93b00a06c11f286fca031ace5bcd5d09af6aa0bbe2e01d709274ac02db69409b24d1605f632334dabfb999ed340bb820f8db859248c8bda0345c044271effb482e0866339723b236a0c3a4f078b90afb13fb32d0c3f6bdd11b301cad889729699664f2e5e82a7ec665835825ff43db2b82df1884ee5d481ef371ad4c3f8ce0e4e18bd9a2a4550ad9dda25a0f1130dd0da04ddef0621a1158db98a5c5ebf90113842c2164e868ec8422d27625d1af4e31d6fccadd07f71cc055761b417d141a1865e58e6886a68f8aa154a3c12d066e1876619eeee00034692251e4e1edd23c8c7028e9518da7f5fe66ec05e1672d7ce83e0745c028fb366c3341c8e1a907c99087dab346fcb08915d6e08d92a3de5977effd344b6e22b2b0aafce2479a1aadd4842c159ab3b7540ca2429a0ea057c84962b1ddb211dc20ac018b593dec8cb2501a74ab11a4bdfb9125073845bdc6bebf19a27fa02d248dac1f7fe4c59fd0b677e8a0ec9f65c2dc4f333f3ae35f5d40363a69639756e7b4533db364cb20f838543935510d1dcdc9f0d84b8813ae03d846bf7596130a85151683e65bae067a7a1f44d066561ffc84363a134bd0b2c3686c226773bc9a93e33189b2c606815e909b7d7fff79f7feb2afe93c29bba4bf068e198b1e91ae95add4c104430969ae89f2f4202ba65a Coverage
Screenshots of Detection AMP ThreatGrid
Win.Dropper.Emotet-6964837-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
5
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusOverride
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallDisableNotify
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: FirewallOverride
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UacDisableNotify
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DoNotAllowExceptions
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
3
<HKLM>\SYSTEM\CurrentControlSet\Services\VSS\Diag\Registry Writer
3
<HKLM>\SYSTEM\CurrentControlSet\Services\VSS\Diag\COM+ REGDB Writer
3
<HKLM>\SYSTEM\CurrentControlSet\Services\VSS\Diag\ASR Writer
3
<HKLM>\SYSTEM\CurrentControlSet\Services\VSS\Diag\Shadow Copy Optimization Writer
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND
Value Name: Start
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC
Value Name: Start
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION
Value Name: jfghdug_ooetvtgk
3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: JudCsgdy
3
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV
Value Name: Start
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Defender
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: Userinit
3
<HKLM>\SOFTWARE\Microsoft\Windows NT\CurrentVersion
3
Mutexes Occurrences 60F16AAB662B6A5DA3F649835F6E212598B68E3C
4
{7930D12C-1D38-EB63-89CF-4C8161B79ED4}
3
\BaseNamedObjects\{137A1518-4964-635A-544B-7A4CB2C11D0D}
3
\BaseNamedObjects\{137A1A2C-4964-635A-544B-7A4CB2C11D0D}
3
\BaseNamedObjects\{137A2419-4964-635A-544B-7A4CB2C11D0D}
3
\BaseNamedObjects\{137A1A2D-4964-635A-544B-7A4CB2C11D0D}
3
Global\I98B68E3C
2
Global\M98B68E3C
2
\BaseNamedObjects\Global\M3C28B0E4
2
\BaseNamedObjects\Global\I3C28B0E4
2
MC8D2645C
2
\BaseNamedObjects\M19FB434
1
\BaseNamedObjects\111OurStarterProcessMutex111
1
\BaseNamedObjects\222OurMainProcessMutex222
1
98B6-8E3C
1
M1CC2778A
1
M10F36403
1
\BaseNamedObjects\A0E8BDA3AF02242419905B05DA0C46C13C28B0E4
1
\BaseNamedObjects\M10E3D08B
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB4C11D0D}
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CBC291D0D}
1
\BaseNamedObjects\MEE09898
1
\BaseNamedObjects\{137A1956-4964-635A-544B-7A4CB7411D0D}
1
\BaseNamedObjects\3C28-B0E4
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 23[.]41[.]248[.]194
4
23[.]5[.]231[.]225
4
23[.]52[.]7[.]20
4
104[.]88[.]26[.]245
4
173[.]223[.]236[.]215
4
13[.]107[.]21[.]200
3
96[.]6[.]27[.]90
3
87[.]106[.]190[.]153
3
172[.]217[.]12[.]174
2
178[.]162[.]217[.]107
2
166[.]78[.]144[.]80
2
204[.]79[.]197[.]200
1
172[.]217[.]10[.]110
1
178[.]162[.]203[.]226
1
85[.]17[.]31[.]82
1
172[.]217[.]5[.]238
1
136[.]243[.]154[.]86
1
23[.]221[.]50[.]122
1
23[.]218[.]141[.]31
1
209[.]34[.]241[.]202
1
23[.]218[.]127[.]164
1
23[.]46[.]53[.]71
1
5[.]196[.]73[.]150
1
184[.]107[.]147[.]18
1
23[.]6[.]69[.]99
1
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences outlook[.]com
4
www[.]java[.]com
4
www[.]onenote[.]com
4
dev[.]windowsphone[.]com
4
www[.]msn[.]com
4
web[.]skype[.]com
4
java[.]com
4
BROMNTUUD[.]XYZ
4
trenkulotd[.]xyz
4
QBULINTULU[.]XYZ
4
TRETITNUNI[.]TOP
4
www[.]torproject[.]org
3
supp7[.]freshdesk[.]com
3
n224ezvhg4sgyamb[.]onion
3
ygqqaluei[.]com
2
atw82ye63ymdp[.]com
2
warylmiwgo[.]com
2
caosusubld[.]com
2
bekvfkxfh[.]com
2
ydchosmhwljjrq[.]com
2
xomeommdilsq[.]com
2
xxsmtenwak[.]com
2
wwyreaohjbdyrajxif[.]com
2
grbjgfprk[.]com
2
mdofetubarhorbvauf[.]com
2
See JSON for more IOCs
Files and or directories created Occurrences %HOMEPATH%\NTUSER.DAT
4
%HOMEPATH%\ntuser.dat.LOG1
4
%APPDATA%\Microsoft\gawbgrrs
4
%APPDATA%\Microsoft\gawbgrrs\jisgivdt.exe
4
%LOCALAPPDATA%\bolpidti\judcsgdy.exe
3
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe
3
%HOMEPATH%
3
%PUBLIC%\{846ee340-7039-11de-9d20-806e6f6e6963}
3
%PUBLIC%\Pictures\Read_ME.html
3
%PUBLIC%\Pictures\Sample Pictures\Read_ME.html
3
%PUBLIC%\Read_ME.html
3
%PUBLIC%\Recorded TV\Read_ME.html
3
%PUBLIC%\Recorded TV\Sample Media\Read_ME.html
3
%PUBLIC%\Videos\Read_ME.html
3
%PUBLIC%\Videos\Sample Videos\Read_ME.html
3
%LOCALAPPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\jumpListCache\Read_ME.html
2
%LOCALAPPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\safebrowsing\Read_ME.html
2
%LOCALAPPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\startupCache\Read_ME.html
2
%LOCALAPPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\thumbnails\Read_ME.html
2
%LOCALAPPDATA%\Read_ME.html
2
%APPDATA%\Adobe\Acrobat\9.0\JavaScripts\Read_ME.html
2
%APPDATA%\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\Read_ME.html
2
%APPDATA%\Mozilla\Firefox\Profiles\1lcuq8ab.default\Read_ME.html
2
%APPDATA%\Mozilla\Firefox\Read_ME.html
2
%HOMEPATH%\Contacts\Read_ME.html
2
See JSON for more IOCs
File Hashes
1e04bcdb51abfed7d2093115cbcaec092b5e8840556f172f368c0a62057c7a3720c8e37dd60b38bbc9af1f55478e1d7618131bcc5bf383378a2bf00c6ffc1a082d7102eb62f9f8c523b7500c5b47eb4cadeff07b2980552e5f8f59aede506eb142697c161579c4e96b49f91935b12b3ec042ce5bfc5a583e8b44b416eb5fcf8f433ad951f81e55b63f14fafe5c606532dc08343bb803d149867c767953a94a665550f5e1a7f27b537a1de8c945877755f8a89c28376c12ed2a635a6cc6f375b37dbcdbf63ed234c18481358441ee78e0c156f3da60bee606c6c52eafa25fe4998196fe92cc4b2a674b7014b4505ba3339e8ad36a004d03d77b125e1f9aec76ad8b2699e4d5ac77bdd3674321b114c05e674f30979b0f032c53a4fcf5a3b11aa5bd86fa60126d2c23abd5e75dbd4b6b952550a7ab1c17139ff009bca37729d7d7cdc8557f6b22789a9d4e10149f9c60f94f217bcb1f695b239fe7a12a0dffaa67d77d9f14025de5483c623673b3f5c4bbe8cdd01c55658c25b62970bf1be6a736d9d2d222e053edc845ce56cdc0ff3516f8e962ee226434772609ee8ce6edfc91e63d957b42d76bc73d03a937d1e2267e4f92c0d9ac0b678124785ea14ce9b991e6c00d963b75e7e5e3f037d54dd3d7099f92dfae0cda82fb5d483e6e8ce8b33bf00a7ca48e367919a09a255d040f3321e3a189ecf7533b0233b3299c9f61f207f1e2beb854ed706d5837ebb789373b83ff0a658f717173227f02bcb4e40ad1b8f88c591028ab0a8084ae15fdeee2afcc87be6980198d9c0ff863e9ac4c5a807f Coverage
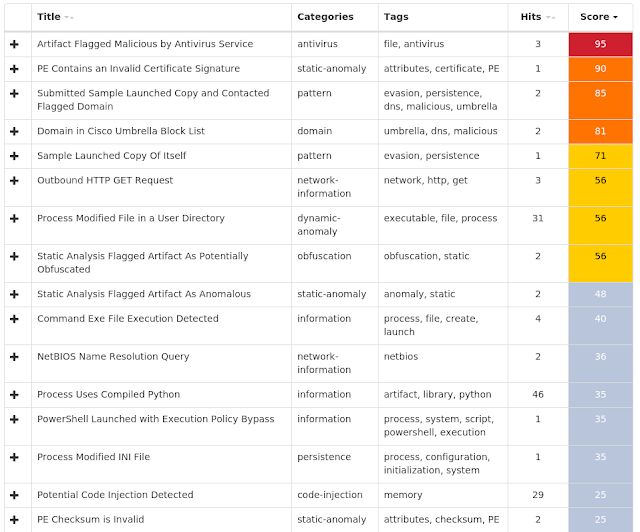
Screenshots of Detection AMP ThreatGrid
Umbrella
Win.Trojan.Darkkomet-6964750-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\DC3_FEXEC
9
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON
Value Name: UserInit
8
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: EnableFirewall
5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\System
5
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE
Value Name: DisableNotifications
5
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM
Value Name: EnableLUA
5
<HKU>\Software\Microsoft\Windows\CurrentVersion\Policies\System
5
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: AntiVirusDisableNotify
4
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC
Value Name: Start
4
<HKLM>\SOFTWARE\Microsoft\Security Center
4
<HKU>\Software\Microsoft\Windows\CurrentVersion\Run
4
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\Policies
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CurrentVersion
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\Explorern
3
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER
Value Name: UpdatesDisableNotify
3
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\CURRENTVERSION\EXPLORERN
Value Name: NoControlPanel
3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Microsoft
3
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MicroUpdate
2
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: MicrosoftUpdateService
2
<HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
1
<HKLM>\SOFTWARE\Microsoft\SystemCertificates\CA\Certificates\189271E573FED295A8C130EAF357A20C4A9F115E
1
<HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
1
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: Windows Data Serivce
1
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: winupdate
1
Mutexes Occurrences DC_MUTEX-C6LXJS9
2
DCPERSFWBP
1
DC_MUTEX-5E3YFKY
1
52hfxfx52
1
DC_MUTEX-75QQLTV
1
DC_MUTEX-P1ZGY19
1
DC_MUTEX-MZMFQQS
1
DC_MUTEX-CNAFSEW
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 69[.]55[.]5[.]250
1
12[.]167[.]151[.]119
1
216[.]146[.]43[.]70
1
162[.]88[.]193[.]70
1
104[.]27[.]193[.]92
1
104[.]27[.]192[.]92
1
51[.]38[.]231[.]9
1
Domain Names contacted by malware. Does not indicate maliciousness Occurrences dezgorm[.]ddns[.]net
2
250[.]5[.]55[.]69[.]in-addr[.]arpa
1
checkip[.]dyndns[.]org
1
119[.]151[.]167[.]12[.]in-addr[.]arpa
1
www[.]whatismyip[.]com
1
checkip[.]dyndns[.]com
1
worgodd[.]no-ip[.]org
1
oliwierze[.]ddns[.]net
1
testezinho250[.]no-ip[.]org
1
weath[.]ddns[.]net
1
sr3u[.]und3rgr0nd[.]tk
1
Files and or directories created Occurrences %APPDATA%\dclogs
7
%HOMEPATH%\Documents\MSDCSC
3
%APPDATA%\MSDCSC
2
%APPDATA%\MSDCSC\msdcsc.exe
2
%HOMEPATH%\My Documents\MSDCSC\ Microsoft Update
2
%HOMEPATH%\Documents\MSDCSC\ Microsoft Update
2
%SystemRoot%\SysWOW64\MSDCSC
1
%SystemRoot%\SysWOW64\MSDCSC\msdcsc.exe
1
%HOMEPATH%\Documents\MSDCSC\msdcsc.exe
1
%ProgramData%\Microsoft\Windows\Start Menu\MSDCSC
1
\Documents and Settings\All Users\Start Menu\MSDCSC\msdcsc.exe
1
%ProgramData%\Microsoft\Windows\Start Menu\MSDCSC\msdcsc.exe
1
%HOMEPATH%\My Documents\MSDCSC\msdcsc.exe
1
%System32%.exe
1
nigzss.txt
1
%APPDATA%\svcost
1
%APPDATA%\svcost\svcost.exe
1
File Hashes
28b4c182eede85890244ea0678da95e9744cdf175dd8748e257064e6e867824d32f509646e99c7aea9d15d180ec891328fcba9dd156750d370f481dc586d674c548d4d3ee7271c7b57f7b99c0b1348da5d1c94e7acfe1adc47f296a562af47d0725fc28899391ced1970b4caffa22f4b92a636a4a5596c587855f4040f93e557a3117c0c2a3d2bbe0bb4bdf2ee37d3bd461c3116ff018277c70aad51498552d5a7e82cc0def7a4884816f9a97e85675cc0d1d4d8db8ea0c01f35f26de41b654eb1c674e44363aae15e87840db0f5a1123e98228a1c33110b41270318cd2f4adad5f888e61113f8cef35692be3a876caf5ac1bbb6fa7983a28e0a1de0f964cd92f78968d304d87b83e759cedde480ba74011e92fd9701c77207bcdc0935735940f99d91a32c833a44ff5d8f938251401eae021320777e2e6f217948a50f8af428 Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Kryptik-6964485-1 Indicators of Compromise Registry Keys Occurrences <HKLM>\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
10
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: mbihas
9
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN
Value Name: anblid
1
Mutexes Occurrences OneiricOcelot
10
OnlineShopFinder
10
P79zA00FfF3
10
PCV5ATULCN
10
PJOQT7WD1SAOM
10
PSHZ73VLLOAFB
10
QuantalQuetzal
10
RaringRingtail
10
RaspberryManualViewer
10
RedParrot
10
RouteMatrix
10
SSDOptimizerV13
10
SoloWrite
10
StreamCoder1.0
10
Tropic819331
10
UEFIConfig
10
UtopicUnicorn
10
VHO9AZB7HDK0WAZMM
10
VRK1AlIXBJDA5U3A
10
VideoBind
10
VirtualDesktopKeeper
10
VirtualPrinterDriver
10
VividVervet
10
WinDuplicity
10
WireDefender
10
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences N/A
-
File Hashes
06aa0afbdfa537fa2a213bc400553e62935911ff40b2e899c839109b3aa763430a8dbca58db6fd04e3b0fcb3ba3a08843676eb43362794b13d2b294b1428a8e5310433c733a765de4ebad4517cc227c0aa326bd496e9a0971a2c5fb2cc080e05516873875312e95e415216eecdbb0fe3799559cd774d68dd10f67b2e413cb6466155690a39ca14c04877424c2292c638910cce74e766d55036e6c3f8133f0c8c70b6964498ad91dc5cf69bca30abec8c65f549e6f11ce47b62cc999bfe16737485d7d87f0fa1cd3a5d405274286f4298ac9d66c6cd17bf90d7245bb2e0bc5b8b94c981cfdc9ec45d961a33c802e24c3c8c50771ed36e66fc5d06e7faaaba602bab44bd641e6fabcb49e6f7febd81073e296b8df9b868cf6cbadcc8515c089355e1abb836355f1085113d6e4605b0eb941c965720eea05092993b8180756fb738 Coverage
Screenshots of Detection AMP ThreatGrid
Win.Packed.Kovter-6964099-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: svchost.exe
16
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_BROWSER_EMULATION
Value Name: explorer.exe
16
<HKLM>\SOFTWARE\WOW6432NODE\Policies
16
<HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows NT\SystemRestore
16
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
Value Name: DisableConfig
16
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS NT\SYSTEMRESTORE
Value Name: DisableSR
16
<HKCU>\SOFTWARE\MICROSOFT\Internet Explorer\Main\FeatureControl\FEATURE_AJAX_CONNECTIONEVENTS
16
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\Windows\CurrentVersion\Policies\Explorer\Run
16
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\RATINGS
Value Name: .Default
16
<HKCU>\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\FEATURECONTROL\FEATURE_AJAX_CONNECTIONEVENTS
Value Name: svchost.exe
16
<HKLM>\SOFTWARE\Wow6432Node\Policies\Microsoft\Windows\Safer\CodeIdentifiers\0\Paths
16
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\Safer
16
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\WINDOWS
Value Name: þ
16
<HKLM>\SYSTEM\ControlSet001\Control\Windows
16
<HKLM>\SOFTWARE\WOW6432NODE\D1B9ACC6
16
<HKCU>\SOFTWARE\D1B9ACC6
16
<HKLM>\SOFTWARE\WOW6432NODE\D1B9ACC6
Value Name: 3
16
<HKCU>\SOFTWARE\D1B9ACC6
Value Name: 3
16
<HKLM>\SOFTWARE\WOW6432NODE\D1B9ACC6
Value Name: 5
16
<HKCU>\SOFTWARE\D1B9ACC6
Value Name: 5
16
<HKLM>\SOFTWARE\WOW6432NODE\D1B9ACC6
Value Name: 2
16
<HKCU>\SOFTWARE\D1B9ACC6
Value Name: 2
16
<HKCU>\SOFTWARE\D1B9ACC6
Value Name: 4
16
<HKLM>\SOFTWARE\Policies\Microsoft\Windows NT\SystemRestore
15
<HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Ratings
15
Mutexes Occurrences D1B9ACC6
16
D1B9ACC6E1
16
D1B9ACC6C2
16
D1B9ACC6C1
16
83EA3AF0E3D35BA8DAAEABE15EF52FFB
16
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences fastfront80[.]com
15
Files and or directories created Occurrences %APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\Preferred
16
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f7a-10cabfeabcac
2
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f7a-2ccabfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f77-20cabfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f7a-24cabfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f7b-10cabfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f77-14cabfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f79-13cbbfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f78-13cbbfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\bb5ca9a3-5378-4a8e-a195-7aa28d9ef0c9
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-8f79-2acabfeabcac
1
%ProgramData%\Microsoft\{5c7b6c54-f92c-e302-cc6c-11c738737558}\{5c7b6c54-f92c-e302-cc6c-11c738737558}.exe
1
%ProgramData%\Microsoft\{51f28878-5ee4-7fc7-2641-51d5b1ab0163}\{51f28878-5ee4-7fc7-2641-51d5b1ab0163}.exe
1
%ProgramData%\Microsoft\{2c1f2442-de97-b471-1e5a-e1b8cd979bac}\{2c1f2442-de97-b471-1e5a-e1b8cd979bac}.exe
1
%ProgramData%\Microsoft\{98b64c08-f14e-d5bc-4a88-5494c78ae8b5}\{98b64c08-f14e-d5bc-4a88-5494c78ae8b5}.exe
1
%ProgramData%\Microsoft\{c5ca3f16-fae8-6d16-a509-2b3ce12f8839}\{c5ca3f16-fae8-6d16-a509-2b3ce12f8839}.exe
1
%ProgramData%\Microsoft\{03cb90f2-8403-8565-a4ee-fbb9c4bec76b}\{03cb90f2-8403-8565-a4ee-fbb9c4bec76b}.exe
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\bb5ca9a3-5378-4a8e-8196-7ea28d9ef0c9
1
%ProgramData%\Microsoft\{9f9c3524-008c-a947-9125-69a3e6df8b87}\{9f9c3524-008c-a947-9125-69a3e6df8b87}.exe
1
%ProgramData%\Microsoft\{5590699f-0760-ca35-28f0-aed17ac9b62a}\{5590699f-0760-ca35-28f0-aed17ac9b62a}.exe
1
%ProgramData%\Microsoft\{c1735532-f3d2-0705-27fb-c9515444a59c}\{c1735532-f3d2-0705-27fb-c9515444a59c}.exe
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-af75-13cbbfeabcac
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\bb5ca9a3-5378-4a8e-8199-78a28d9ef0c9
1
%ProgramData%\Microsoft\{349d3e26-16cd-3c5a-17e8-a6b5712e298a}\{349d3e26-16cd-3c5a-17e8-a6b5712e298a}.exe
1
%APPDATA%\Microsoft\Protect\S-1-5-21-2580483871-590521980-3826313501-500\5731e7cd-8311-408b-af7b-2ccabfeabcac
1
See JSON for more IOCs
File Hashes
967d47c136b9b0572999085bdf88035b47ac413a0fcc643379235a656c7b19bfbaf12e28c9f22bbc6343d8fd52ec0f9bdbec595887a3bb86ac8276b73a6149f0c97d5b490cdb6a003c7fbc4f01d6e96b6eb7daa401fabb91159df441a7c3a414d0e6edab6f229bddae3ba675045d31dae31ecfebc5071bcef6fb5bb75d7114bfd101f5b175f474b2e8f7768e8ae0492f3732a776367b1df256412d2918edeabbd229bf0e951fbb466a7a695021ff001f29b8a14e9236386fa23d64c0292fcabbd7bfc27b9cae97fd12fc37aca51e72e11ad55a545d8fc1ef1cf1262b3a75d1cfe09390b6cac41111e9573db97340727c493b7d61db4bd5f7be5e298bce1feb61e7cf854f13c13b4356b79196b1703033ea820eb9d9c0539202774cfa62f4ddc1ea4109825ea5dd469b35237206639f261ab9dbbc9029f6ff5cbe245e19708253eeb139134e8f9ae9a06f2b88a5d710aff711ba5ad5f653300a2bf4f874d8cf90f26f413104736c1e442bf3fc3d90f7e7ebf37015b8c81c8c8d8a3cb98ca17112f644f06fe38ad3643c026e0a2eda3e0fd17b8dc3e248699d824df192455310e5f76268c3dff77dddabcec092f5bc236cdacab5d052f5bac4ab3b1be932fe2f1ef857b7ea2d8a195080fef9a188eceddd5c35d88bcad8cdc0ad074b937b0b4d71fc8fce6392c14f721d61f41f1fdb794bd3abf8c0edbbe84e6b5f0efed38ca9d7 Coverage
Screenshots of Detection AMP ThreatGrid
Win.Malware.Python-6964012-0 Indicators of Compromise Registry Keys Occurrences <HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\RFC1156AGENT\CURRENTVERSION\PARAMETERS
Value Name: TrapPollTimeMilliSecs
20
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\RFC1156Agent
20
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\RFC1156AGENT\CurrentVersion
20
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\RFC1156AGENT\CURRENTVERSION\Parameters
20
<HKLM>\SOFTWARE\Microsoft\RFC1156Agent\CurrentVersion\Parameters
19
Mutexes Occurrences Global\D0E858DF-985E-4907-B7FB-8D732C3FC3B8}
20
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 79[.]98[.]145[.]42
17
45[.]79[.]77[.]20
16
153[.]92[.]4[.]49
5
Domain Names contacted by malware. Does not indicate maliciousness Occurrences info[.]abbny[.]com
19
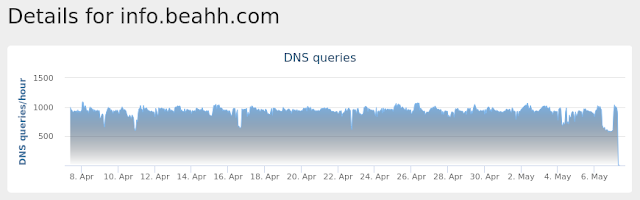
info[.]beahh[.]com
19
info[.]ackng[.]com
19
42[.]pl
17
ip[.]42[.]pl
17
jsonip[.]com
16
Files and or directories created Occurrences \TEMP\m2.ps1
20
\TEMP\mkatz.ini
20
\m2.ps1
19
\mkatz.ini
19
%TEMP%\_MEI19082\Crypto.Cipher._AES.pyd
4
%TEMP%\_MEI19082\Crypto.Cipher._ARC4.pyd
4
%TEMP%\_MEI19082\Crypto.Cipher._DES.pyd
4
%TEMP%\_MEI19082\Crypto.Cipher._DES3.pyd
4
%TEMP%\_MEI19082\Crypto.Hash._MD4.pyd
4
%TEMP%\_MEI19082\Crypto.Hash._SHA256.pyd
4
%TEMP%\_MEI19082\Crypto.Random.OSRNG.winrandom.pyd
4
%TEMP%\_MEI19082\Crypto.Util._counter.pyd
4
%TEMP%\_MEI19082\Crypto.Util.strxor.pyd
4
%TEMP%\_MEI19082\Include\pyconfig.h
4
%TEMP%\_MEI19082\Microsoft.VC90.CRT.manifest
4
%TEMP%\_MEI19082\_ctypes.pyd
4
%TEMP%\_MEI19082\_hashlib.pyd
4
%TEMP%\_MEI19082\_mssql.pyd
4
%TEMP%\_MEI19082\_multiprocessing.pyd
4
%TEMP%\_MEI19082\_socket.pyd
4
%TEMP%\_MEI19082\_ssl.pyd
4
%TEMP%\_MEI19082\bz2.pyd
4
%TEMP%\_MEI19082\ii.exe.manifest
4
%TEMP%\_MEI19082\msvcm90.dll
4
%TEMP%\_MEI19082\msvcp90.dll
4
See JSON for more IOCs
File Hashes
2d5c9619b85111c8af13ad75bc334b26713839eed3ac96e9b22447039296aa0e30117d30a63aaf64648199e3874762f0a31d1c45f35ff73820d3bb65827dbc894af89e0f76d112342c2ac7e5cd3696974027a5c771fb4655faa78fefae4774e85304995ff9b9ca3d6f597fc2eb1e456125eb5c42dc42df234173e47184df71f2568db055c4fb8890fe7f3ef0ef3d32c250ac4d997e94571f84b3463805befedb5795c318c70fd3009a470198ce1ccb6a7d74af59f3758385fe034520d657c45c59a6c6c90be9cd113afafad6261fce0f23decc1c453ffd3f135e028073fde5015f6a3155166e492a8acf391d70b334e985d24dfd43b9ea12f5e47a2d7222ea496059747fb8a2c5429313d835f610d9c4a6965c5f63719c694ba20533450da3f7605cbd5701cbbc4a36935599525e6d0d5c1a043c9252aa081cb9c2f3724fc8ba613531d0a4eeffaca1e34fc90de6ce2a042dac8983fe8ac30d5868f2d400d4e2619b34db1e2b672ab7709c581a43ecc902b4f36fc817c007cd557b75d7dc67bf64c06234473e62abe6b4dd9dcb8c0df812344f4808fa8d2c594e3117bb22ac8e6503fd5020dc940cb38a647c1d6ee211259e418593d6bdf9db3aeb79621a4a6c6859d6615d5de8f981ee996de57b6f2c838420c2b21cf328b8a258a500e2ebc56921860fd202f8de479af08511a6b5ddfb9c84654a89020f133243cebf0bee9a693df72f101e68cb4a19a921c89301779552e4215830498bc8b5c7843e35e5e26a2a3089e6adf58b64a3800b94bc53d0e2b6b05a21aa6127ce57620268b49f0870c258ff7c21f6319d1434480d5ae6f2e111feb864a5e33b81b01f8364247d1170e53a2ffa43d9d4426fc703c04d7d610aa0346c2fb7e37dc234167c613dd5157149016c8e6cdeb9494dea17b743b298d12adbc35c77dcf7bc0a1e12f8ddea2d7246bf9b6fdb3b49ce33ff7b0a3f2bae33eb1e0301db635ccb74608313c719e1763571d4fc7e3d4738941599d41a665bcb859c0180de80ac99765edbe47f93a97895313b35d27c7d5bc0fca556736f63e800e99feb6dcde910c76c743d4634ac79582a03488d2c8a1a14ce512034f65727e4a921f7420e18078d92bf1dd085acSee JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Malware
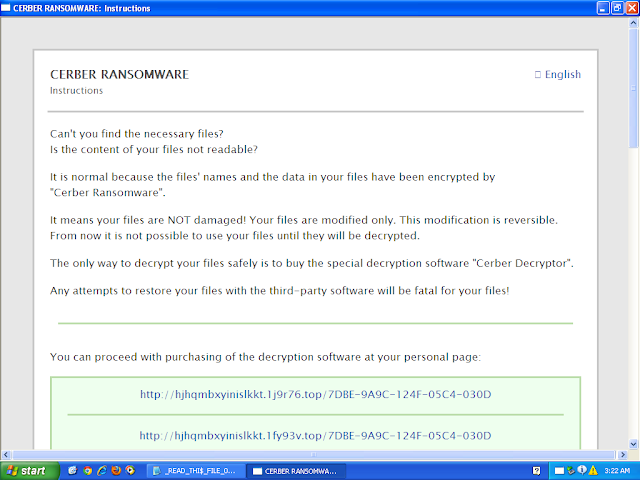
Win.Ransomware.Cerber-6963958-0 Indicators of Compromise Registry Keys Occurrences <HKCU>\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage2
11
<HKLM>\System\CurrentControlSet\Control\Session Manager
11
<HKLM>\SYSTEM\CONTROLSET001\CONTROL\SESSION MANAGER
Value Name: PendingFileRenameOperations
11
<HKU>\Software\Microsoft\Windows NT\CurrentVersion\Winlogon
10
<HKU>\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Extensible Cache\ietld
10
<HKU>\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
10
<HKU>\Software\Microsoft\Internet Explorer\IETld
10
<HKU>\Software\Microsoft\Internet Explorer\BrowserEmulation
10
<HKLM>\SOFTWARE\Microsoft\ESENT\Process\mshta\DEBUG
10
Mutexes Occurrences shell.{381828AA-8B28-3374-1B67-35680555C5EF}
11
\BaseNamedObjects\shell.{D31FFF46-7264-2F11-86F6-D577904717A2}
1
\BaseNamedObjects\shell.{009333F1-551C-9DAC-1759-5B4919375F70}
1
\BaseNamedObjects\shell.{AC607669-1359-523E-095D-A88DA96FD1D1}
1
\BaseNamedObjects\shell.{8F606D68-4B19-E718-0DBB-45B7697D4BDA}
1
\BaseNamedObjects\shell.{4A4E1DA9-250C-6EB9-DF1C-D339CF8305B9}
1
\BaseNamedObjects\shell.{93742F5C-F907-5D2F-E50F-7DDF1F2F0F9C}
1
\BaseNamedObjects\shell.{98B816E3-E44E-C421-229A-B8F7963D0F05}
1
\BaseNamedObjects\shell.{33BDE317-B098-C54C-1E87-AECB2544252C}
1
\BaseNamedObjects\shell.{D98CB22B-6CC2-5E4F-BC2F-152CBBE6DA5B}
1
\BaseNamedObjects\shell.{31C26804-8082-BCD2-AE9A-2E0E343C4A11}
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 94[.]23[.]173[.]239
11
94[.]23[.]173[.]236
11
94[.]23[.]173[.]237
11
94[.]23[.]173[.]242
11
94[.]23[.]173[.]243
11
94[.]23[.]173[.]240
11
94[.]23[.]173[.]241
11
94[.]23[.]172[.]190
11
94[.]23[.]173[.]24
11
94[.]23[.]173[.]25
11
94[.]23[.]173[.]127
11
94[.]23[.]172[.]191
11
94[.]23[.]174[.]76
11
94[.]23[.]174[.]77
11
94[.]23[.]172[.]218
11
94[.]23[.]175[.]153
11
94[.]23[.]175[.]152
11
94[.]23[.]172[.]50
11
94[.]23[.]172[.]51
11
94[.]23[.]175[.]142
11
94[.]23[.]175[.]143
11
94[.]23[.]173[.]235
11
94[.]23[.]173[.]234
11
94[.]23[.]172[.]199
11
94[.]23[.]172[.]197
11
See JSON for more IOCs
Domain Names contacted by malware. Does not indicate maliciousness Occurrences api[.]blockcypher[.]com
11
hjhqmbxyinislkkt[.]1j9r76[.]top
8
chain[.]so
6
p27dokhpz2n7nvgr[.]1j9r76[.]top
3
bitaps[.]com
3
btc[.]blockr[.]io
3
Files and or directories created Occurrences %TEMP%\d19ab989
11
%TEMP%\d19ab989\4710.tmp
11
%TEMP%\d19ab989\a35f.tmp
11
\DAV RPC SERVICE
10
\Device\Null
10
%TEMP%\8f793a96\4751.tmp
10
%TEMP%\8f793a96\da80.tmp
10
\I386\DRVMAIN.SDB
10
\I386\EULA.TXT
10
\I386\HWCOMP.DAT
10
\I386\SECUPD.DAT
10
\I386\SETUPLDR.BIN
10
\I386\WIN9XMIG\ICM\SYMBOLS.PRI\RETAIL\DLL\MIGRATE.PDB
10
\I386\WIN9XMIG\ICM\SYMBOLS\RETAIL\DLL\MIGRATE.PDB
10
\I386\WIN9XMIG\IEMIG\SYMBOLS.PRI\RETAIL\DLL\MIGRATE.PDB
10
\I386\WIN9XMIG\IEMIG\SYMBOLS\RETAIL\DLL\MIGRATE.PDB
10
\I386\WIN9XMIG\PWS\SYMBOLS.PRI\RETAIL\DLL\MIGRATE.PDB
10
\I386\WIN9XMIG\PWS\SYMBOLS\RETAIL\DLL\MIGRATE.PDB
10
\I386\WIN9XUPG\E95ONLY.DAT
10
File Hashes
7019c1e1802915ac18691419d277a94b5e30a11209dd445f234ca14b35f5d72072316d031bea130d9475d57d97f96b05cf11190101b219b106eadbb7ffb41b4a8518d800daf5c94937948b6f1ca696a7e03faa6f86a689e809218f81f697b80e860ee1bc900c05313d12f50f17620c330f642a9dcfce66b8dd8141897bd4ed09a8eb934ac833e714578d5d7d2b8fa2388328cb2145e8207553a0f124da942f48ac4851b671d4ecf728681c9587bd7d14bc011c682e6957124aba87660882377cbccbc893aef7ecee4eebeeb2c386e43abb1deaa78d4f03dc54e8f7f409d73b6fc3e5d39b17b60def951d6c0829ed1bf887cc0e71c9d24c9dc14a02d6bdf23c86cf557bc47899bdec8b94a0e8b0b00d73390be2c1c404a973b65828e264c26c77e2e487d62c6c9ef0a965fbb0d99e0af7752a11738a9ef3e1d9d193862b28e118f0e79e62922ddf62d71c4e44aa2e927ad111b4437df9adcf0c28c491b22d633a Coverage
Screenshots of Detection AMP ThreatGrid
Malware
Doc.Downloader.Powload-6959926-0 Indicators of Compromise Registry Keys Occurrences N/A
-
Mutexes Occurrences Global\I98B68E3C
24
Global\M98B68E3C
24
Global\SyncRootManager
1
Local\ShimViewer
1
Local\C9E8AF12-FA27-4748-EC04-38CA71239739_RegisterDevice
1
5CAC3FAB-87F0-4750-984D-D50144543427-VER15
1
Local\{F99C425F-9135-43ed-BD7D-396DE488DC53}
1
CicLoadWinStaWinSta0
1
Global\RecentDocumentsUpdate
1
Global\b48161dd-6c92-11e9-bdf9-00501e3ae7b5
1
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences 37[.]211[.]38[.]50
22
75[.]177[.]169[.]225
22
50[.]99[.]132[.]7
22
189[.]134[.]78[.]42
21
31[.]14[.]103[.]164
12
91[.]231[.]87[.]78
12
45[.]40[.]251[.]243
12
103[.]229[.]72[.]59
10
209[.]134[.]25[.]170
3
200[.]58[.]171[.]51
2
189[.]196[.]140[.]187
2
Domain Names contacted by malware. Does not indicate maliciousness Occurrences protemin[.]com
12
moda-blog[.]com
12
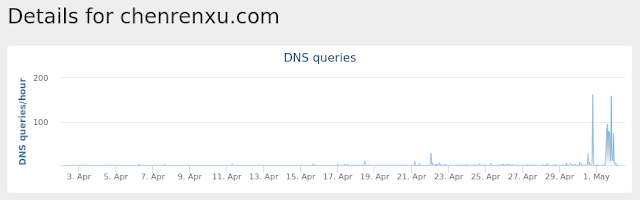
chenrenxu[.]com
12
depobusa[.]com
10
webaphobia[.]com
3
Files and or directories created Occurrences %HOMEPATH%\820.exe
12
%HOMEPATH%\438.exe
10
%HOMEPATH%\813.exe
3
\TDLN-2060-41
1
\Device\NamedPipe\Sessions\1\AppContainerNamedObjects\S-1-15-2-1861897761-1695161497-2927542615-642690995-327840285-2659745135-2630312742
1
%System32%\WindowsPowerShell\v1.0\Help.format.ps1xml
1
%SystemRoot%\SysWOW64\7Dvm.exe
1
%TEMP%\CVR550.tmp
1
%SystemRoot%\SysWOW64\9LObZfUjohYq.exe
1
File Hashes
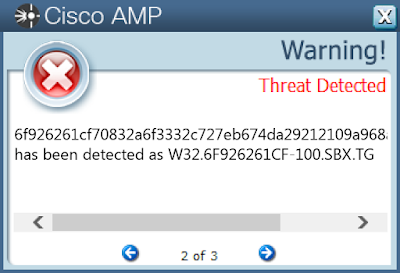
07ad82ee6f552024b89e9569759078672295762694af017f35f64bb7284b93c31a6641086b78035d6c9ba38c7199aac02d37dafbadf96059a81b6f4c35e49f841f4a46bf19d090bee1282d5920e1ce502620c0a50cb4d5165d735d5b52e4a79e224d99639dbb488494e23f7fd8a60c75630ffc694a3114a6d4f596da2062fbe02ade167cc02b318750feb789c0476581e4f2e0864c3a51fd65bd74c25534a74e3606c54dbaba863109929191dfda5771de069a4fdbdc6322ae75c549aeec3ddd394d047267664ca7feaa87df65b83ef559a4a97d7660e855fd84ad39ca15c17f3f832fc27ebcc0391c302aedbc3f8d3dfe7473679d5d9aa0176f9623d4306d683f90bc319f969145e499fa90a32a81f0fed988320b255b0febc18befca735484404f20fabcaf9c4c086a38eb1cb139e49e2e08d6249ef41b88d7eb2c0e628bbc42981d37b50801d5cdc23d5d9f0a1e0e20f3787e24c4d20f606d2250ce5bf804438757f58f956c0bf3c4d88c3270f25c6bef6cc6c7599d01e2050871e1c7cced49b5e70a242f984eadee49435aac4371ca3cb65b02b2f6fbcbfcbfbd9d98578251d6fab6ccf8fb3460ce156af02cfcbaf6098f74d37e5d323a3d9e2c07e4b8f4567c4f99a489d6e26cdd76b719f290108f558cb49b7f5f7e2d84dc8929f7613b571210656adbfe8cde574bb15f96232169cdfb487f4597ce1a4532c7a0258f4658c44d575aa6041c0d0e87372288f96804c1fa141ee903a67f668e73cb690dec5f401aefe65751c9e09131d50f1a6ea3f86f542552ecab2973a334a36035769961e933a06b4a2af4239c378c84211b2ff1baab4effe6b5bf044ac4f2d3371c3264b75110604d920b41da5dedf56cabebac63da64a209a35cb664ba69764fb8a868e686c3f2b87d3169766ffe4bba021a8acd7648ca38c6c75be829a864558ecb6a817c04b3ec3fb6f85801ecf4999db95505445ecbc8f741cf2985972f2d6f756f926261cf70832a6f3332c727eb674da29212109a968a25cab4cb92fced769472f28f83d17f71068693f8f34ea40d09dc75d111635427f1b58fa9d4cad295587416ebc5373fd8a3ec9ece1dff46c15699738491d703b47f20ae4de8c59bcef0See JSON for more IOCs Coverage
Screenshots of Detection AMP ThreatGrid
Umbrella
Malware
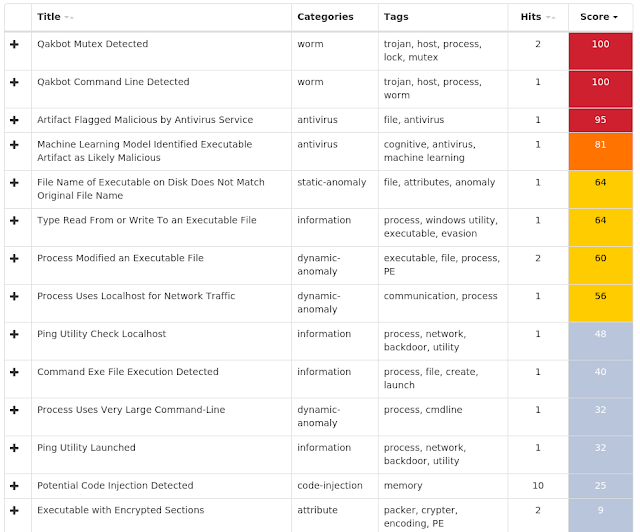
Win.Dropper.Qakbot-6962757-0 Indicators of Compromise Registry Keys Occurrences N/A
-
Mutexes Occurrences Global\eqfik
15
Global\ufwao
15
llzeou
15
4737f7e7a483154476a69b4f5a4a
1
4737f7e7a483154476a69b4f5a4/C
1
f23982a726efd837a3fb23d770ea
1
85ff1bf1196b88d85f7f7092fc8a
1
f23982a726efd837a3fb23d770e/C
1
b274a28e4ad451b106c78e64d91a
1
85ff1bf1196b88d85f7f7092fc8/C
1
ecd2fdff63d752ee98eb1e0dd18a
1
b274a28e4ad451b106c78e64d91/C
1
ecd2fdff63d752ee98eb1e0dd18/C
1
8c5f802a24045fc230207298aa8a
1
8c5f802a24045fc230207298aa8/C
1
908889c25ce86b55fc08b790b42a
1
666d680dfc69cb8931cc724a81ca
1
908889c25ce86b55fc08b790b42/C
1
666d680dfc69cb8931cc724a81c/C
1
d7c6d675543ec8fc13cb6e169f7a
1
d7c6d675543ec8fc13cb6e169f7/C
1
a4be182a1dc5815e8a932795631a
1
a4be182a1dc5815e8a932795631/C
1
99cfbb31846bd275123aa1ab920a
1
99cfbb31846bd275123aa1ab920/C
1
See JSON for more IOCs
IP Addresses contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Domain Names contacted by malware. Does not indicate maliciousness Occurrences N/A
-
Files and or directories created Occurrences N/A
-
File Hashes
4737f7e7a483154476a69b4f5a48fb4551ac02ac240a784c4f3377c436dbd203666d680dfc69cb8931cc724a81cdb588d16602788f7d3bd7955803ce224d6f806c4d27124a279c0f49eb46852ea440fdd482bd8798126bfe0b526361f370253185ff1bf1196b88d85f7f7092fc8f3905a9ded0e14e06b17475163df47a079e298c5f802a24045fc230207298aa825e0fca94d7dd7d8e9f06abd59836d0ed373e908889c25ce86b55fc08b790b42ab405a485dc498821249c10d5517c47470e359258e1004f3ddbf9bc72a4764a77d174b090faf1288afaa2f7b1d16f96fbb1a699cfbb31846bd275123aa1ab9206e92b71556ea269e8eeceffff3b3dc27385b5a4be182a1dc5815e8a9327956310222b714dac52ba4c5aa4ba0f72975c716218b274a28e4ad451b106c78e64d917f9da3d1ab46d7e450a3a3908351b25718b3cc6f26163d2c2dc499ffdb86d649e95301329db9d908888b909f4190d3d51ca1fd7c6d675543ec8fc13cb6e169f7df286f33187ee96a3163252c607aa16e7bbf1ecd2fdff63d752ee98eb1e0dd185a1919d2ff72c23c80a7a8c057d4b9f5e9ad5f23982a726efd837a3fb23d770ed2e1eba1cf2629b4466b76ef205b52c19e540f9d48c419ad4ea015efa8258f323a5242b46da80c1755ff2b551592a3b54d0bd Coverage
Screenshots of Detection AMP ThreatGrid
Exprev Cisco AMP for Endpoints protects users from a variety of malware functions with exploit prevention. Exploit prevention helps users defend endpoints from memory attacks commonly used by obfuscated malware and exploits. These exploits use certain features to bypass typical anti-virus software, but were blocked by AMP thanks to its advanced scanning capabilities, even protecting against zero-day vulnerabilities. Madshi injection detected (3477)Kovter injection detected (2818)PowerShell file-less infection detected (1467)Process hollowing detected (521)Gamarue malware detected (172)Atom Bombing code injection technique detected (146)Suspicious PowerShell execution detected (97)Installcore adware detected (69)Dealply adware detected (40)Excessively long PowerShell command detected (26)